Data Security
IT Policies And Procedures Overview Of Network Security Policy For Workers Icons PDF
This slide describes the network security policy, which ensures systems have the proper hardware, software, and auditing processes. It logs details of activities such as failed log-in attempts, information starts up or shutdown, etc. Are you searching for a IT Policies And Procedures Overview Of Network Security Policy For Workers Icons PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort youve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download IT Policies And Procedures Overview Of Network Security Policy For Workers Icons PDF from Slidegeeks today.

We Provide The Following Services For Your Convenience In Security Guard Services Proposal Professional PDF
This is a we provide the following services for your convenience in security guard services proposal professional pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employs prior law enforcement, military or seasoned agents, with special firearms training. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Officer Service Company Profile Company Overview With Key Services Background PDF
This slide highlights security company background information which includes key services and solutions, industries served, headquarter, website ranking, along with the key stats. This is a Security Officer Service Company Profile Company Overview With Key Services Background PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like ABC Securities, Services And Solutions, Quality And Certifications. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Prevention Of Information How To Overcome The Security Awareness Training Introduction PDF
The purpose of this is to highlight various solutions which can be used to overcome the cyber security awareness challenges. The key solutions covered in the slide are introducing dynamic courses, fully managed training. If you are looking for a format to display your unique thoughts, then the professionally designed Prevention Of Information How To Overcome The Security Awareness Training Introduction PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Prevention Of Information How To Overcome The Security Awareness Training Introduction PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Handling Cyber Threats Digital Era Information Security Program Values To Business Ppt Slides Background Designs PDF
Following slide displays the major program values to companys business. Values here are divided in two areas namely detection and response and attack surface management. This is a handling cyber threats digital era information security program values to business ppt slides background designs pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information security program values to business. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
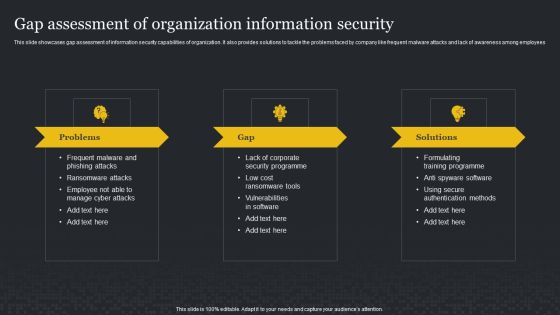
Gap Assessment Of Organization Information Security Cybersecurity Risk Assessment Ideas PDF
This slide showcases gap assessment of information security capabilities of organization. It also provides solutions to tackle the problems faced by company like frequent malware attacks and lack of awareness among employees. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Gap Assessment Of Organization Information Security Cybersecurity Risk Assessment Ideas PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Gap Assessment Of Organization Information Security Cybersecurity Risk Assessment Ideas PDF.

Prevention Of Information Strategies We Will Implement To Make Security Awareness Ideas PDF
The purpose of this slide is to exhibit variety of strategies which can be used to engage employees in the security awareness training plan. The strategies highlighted in the slide are gamification, personalization, high-quality content and variety. Get a simple yet stunning designed Prevention Of Information Strategies We Will Implement To Make Security Awareness Ideas PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Prevention Of Information Strategies We Will Implement To Make Security Awareness Ideas PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Implementing Cybersecurity Awareness Program To Prevent Attacks Evaluating IT System Security Formats PDF
The purpose of this slide is to outline the strength, weakness, opportunities and threat SWOT evaluation of organization cyber security. Organization can detect the potential risks and opportunities in the cyber security using SWOT model. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Implementing Cybersecurity Awareness Program To Prevent Attacks Evaluating IT System Security Formats PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Implementing Cybersecurity Awareness Program To Prevent Attacks Evaluating IT System Security Formats PDF today and make your presentation stand out from the rest.
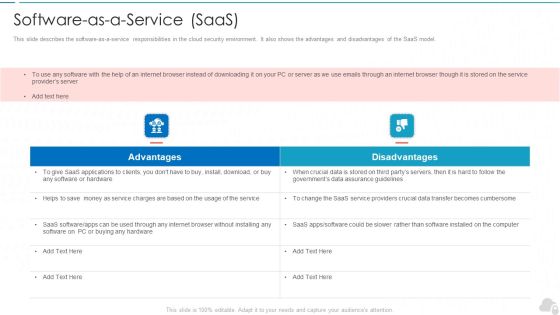
Software As A Service Saas Cloud Computing Security IT Ppt Background Image PDF
This slide describes the software-as-a-service responsibilities in the cloud security environment. It also shows the advantages and disadvantages of the SaaS model. This is a software as a service saas cloud computing security it ppt background image pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like advantages, disadvantages. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Platform As A Service Paas Cloud Computing Security IT Ppt Professional Portfolio PDF
This slide defines the platform-as-a-service model of cloud security and the various advantages and disadvantages of the PaaS model. This is a platform as a service paas cloud computing security it ppt professional portfolio pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like advantages, disadvantages. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
IT Security With Laptop And Shield Icon Ppt PowerPoint Presentation File Graphics PDF
Persuade your audience using this it security with laptop and shield icon ppt powerpoint presentation file graphics pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including it security with laptop and shield icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Security For Cloud Based Systems Management Icon For IT Project Rules PDF
Persuade your audience using this Security For Cloud Based Systems Management Icon For IT Project Rules PDF. This PPT design covers Three stages, thus making it a great tool to use. It also caters to a variety of topics including Security For Cloud, Based Systems Management, IT Project. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
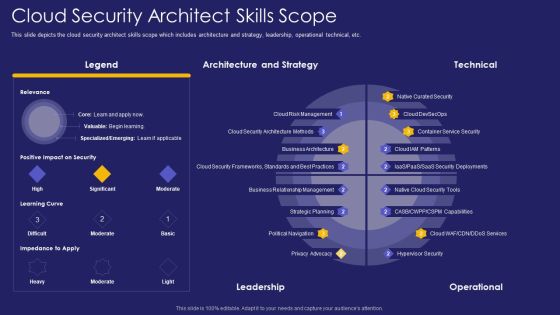
Role IT Team Digital Transformation Cloud Security Architect Skills Scope Rules PDF
This slide depicts the cloud security architect skills scope which includes architecture and strategy, leadership, operational technical, etc. Deliver an awe inspiring pitch with this creative role it team digital transformation cloud security architect skills scope rules pdf bundle. Topics like architecture, strategy, leadership can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
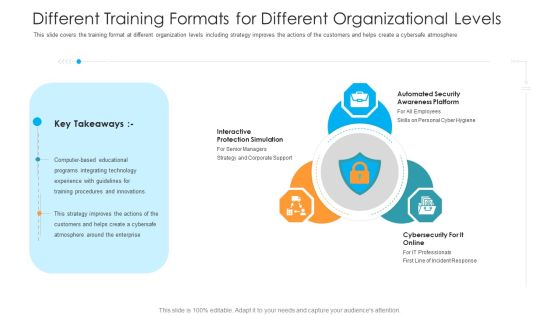
Different Training Formats For Different Organizational Levels Hacking Prevention Awareness Training For IT Security Rules PDF
This slide covers the training format at different organization levels including strategy improves the actions of the customers and helps create a cybersafe atmosphere. This is a different training formats for different organizational levels hacking prevention awareness training for it security rules pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like interactive protection simulation, automated security awareness platform, cybersecurity for it online. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Timeline For Information Security Risk Management Training Cybersecurity Risk Assessment Pictures PDF
This slide showcases timeline that can help organization to conduct training for information security risk management programme. It also showcases weekly and step progress. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Timeline For Information Security Risk Management Training Cybersecurity Risk Assessment Pictures PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Timeline For Information Security Risk Management Training Cybersecurity Risk Assessment Pictures PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Prevention Of Information Impact Of Cyber Security Breach Lost Revenue Slides PDF
The purpose of this slide is to showcase the consequences of cyber security breach on the company revenue. It provides information about the revenue lost over different months caused by different cyber attack such as malware, social engineering attack, business email compromise etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Prevention Of Information Impact Of Cyber Security Breach Lost Revenue Slides PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Prevention Of Information Impact Of Cyber Security Breach Lost Revenue Slides PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers
Post It Notes IT Security IT Ppt Icon Infographic Template PDF
This is a post it notes it security it ppt icon infographic template pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like post it notes. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Information Security Phase 3 Respond To Cloud Protection Issues Ppt Layouts Influencers PDF
This slide represents phase 3 of cloud security, such as respond to cloud protection issues. It includes an advanced authentication process, manages cloud access standards when new services come up, and eliminates malware from cloud services. Deliver and pitch your topic in the best possible manner with this Cloud Information Security Phase 3 Respond To Cloud Protection Issues Ppt Layouts Influencers PDF. Use them to share invaluable insights on Advanced Authentication, Cloud Access, Eliminate Malware and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Organizations Risk Management And IT Security Classification Of IT Risks With Threats Structure PDF
This slide highlights the classification of information technology risks which includes technology, security, political and legal, personnel, and infrastructure with key threats. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Organizations Risk Management And IT Security Classification Of IT Risks With Threats Structure PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Cyber Attacks Faced By Organization In Previous Financial Year Information Security Risk Administration Topics PDF
This slide showcases information security attacks faced by organization in past financial year. It can help company to assess different types of cyber attacks and formulate strategies to tackle them.Create an editable Cyber Attacks Faced By Organization In Previous Financial Year Information Security Risk Administration Topics PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Cyber Attacks Faced By Organization In Previous Financial Year Information Security Risk Administration Topics PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
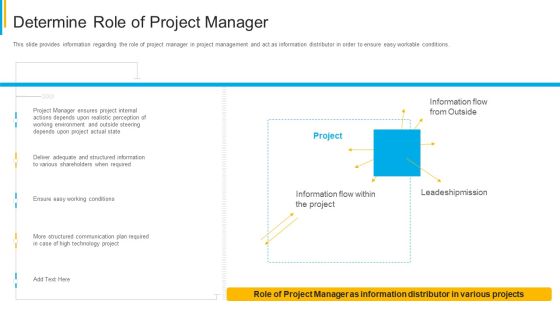
Project Security Administration IT Determine Role Of Project Manager Clipart PDF
This slide provides information regarding the role of project manager in project management and act as information distributor in order to ensure easy workable conditions. Deliver an awe inspiring pitch with this creative project security administration it determine role of project manager clipart pdf bundle. Topics like technology, communication, plan, leadeshipmission, environment can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Problem Faced By The Organization Hacking Prevention Awareness Training For IT Security Rules PDF
This slide covers the problem faced by organization caused by employees due to lack of security awareness training programs. This is a problem faced by the organization hacking prevention awareness training for it security rules pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like corporate, cybersecurity, financial. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Post It Notes Cloud Computing Security IT Ppt Portfolio Graphics Example PDF
This is a post it notes cloud computing security it ppt portfolio graphics example pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like post it notes. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Info Safety And ISO 27001 Current Security Management Capabilities Overview Ideas PDF
Following slide illustrates present information security management capabilities overview of the company. Sections covered in the slide are core functions, description, key enablers, required and actual standard rating. Deliver an awe inspiring pitch with this creative Info Safety And ISO 27001 Current Security Management Capabilities Overview Ideas PDF bundle. Topics like Core Functions, Rating Scale, Key Enablers, Required Standard Rating, Actual Rating can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Developing IT Security Strategy Cyber Attacks Faced By Different Departments Download PDF
This slide showcase information security attacks faced by different departments of organization. Its key elements are department, number of cyber attacks and type of cyber attacks. Are you searching for a Developing IT Security Strategy Cyber Attacks Faced By Different Departments Download PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Developing IT Security Strategy Cyber Attacks Faced By Different Departments Download PDF from Slidegeeks today.

IT Security Assessment Matrix Of IT Risks Ppt Slides Visual Aids PDF
This slide depicts the cyberattacks surface based on different property types. It also covers the attacks based on web mobile applications, online payments, employee devices. Deliver an awe inspiring pitch with this creative information technology security assessment matrix of it risks ppt outline objects pdf bundle. Topics like assessment matrix of it risks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Desktop Security Management Cyber Safety Tips Protection Against Cyberattacks Download PDF
This slide represents various tips or procedures that can be followed to prevent an organizations cyber security from cyberattacks or cybercriminals. Presenting desktop security management cyber safety tips protection against cyberattacks download pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like systems, network, sources. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

ISO 27001 Organizational Qualifying Procedure Dashboard For Information Security Risk Management Background PDF
This slide displays dashboard for information security risk management. It includes KPIs such as risk analysis progress, persent risk, response progress for risks and number of risks encountered.Deliver and pitch your topic in the best possible manner with this ISO 27001 Organizational Qualifying Procedure Dashboard For Information Security Risk Management Background PDF. Use them to share invaluable insights on Analysis Progress, Response Progress, Plan Breakdown and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Financing Catalogue For Security Underwriting Agreement Post It Notes Sample PDF
This is a financing catalogue for security underwriting agreement post it notes sample pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like post it notes. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Based Email Security Market Report Market Share Ppt File Background PDF
This slide displays a division of market share of the entire E Mail security Industry. Deliver an awe inspiring pitch with this creative cloud based email security market report market share ppt file background pdf bundle. Topics like market share can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
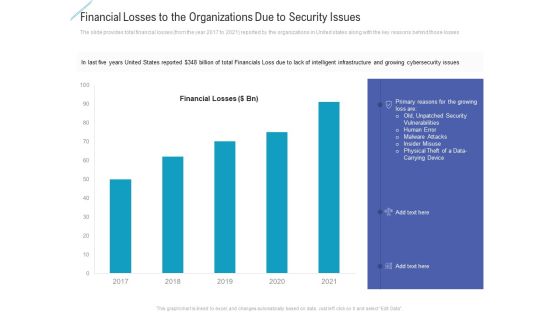
Financial Losses To The Organizations Due To Security Issues Themes PDF
Deliver an awe inspiring pitch with this creative financial losses to the organizations due to security issues themes pdf bundle. Topics like financial losses to the organizations due to security issues can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Management Dashboard With Downtime Issues And Unsolved Tickets Introduction PDF
Deliver an awe inspiring pitch with this creative Security management dashboard with downtime issues and unsolved tickets introduction pdf bundle. Topics like security management dashboard with downtime issues and unsolved tickets can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Management Dashboard With Downtime Issues And Unsolved Tickets Designs PDF
Deliver and pitch your topic in the best possible manner with this security management dashboard with downtime issues and unsolved tickets designs pdf. Use them to share invaluable insights on security management dashboard with downtime issues and unsolved tickets and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
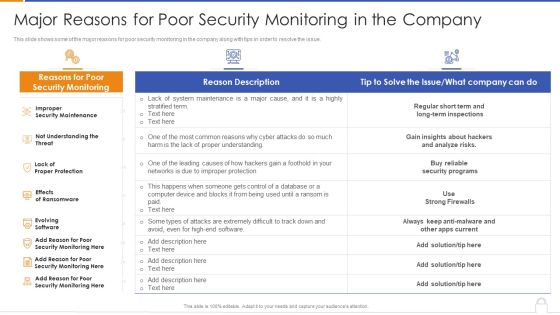
Major Reasons For Poor Security Monitoring In The Company Designs PDF
Deliver and pitch your topic in the best possible manner with this major reasons for poor security monitoring in the company designs pdf. Use them to share invaluable insights on security maintenance, effects of ransomware, evolving software and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
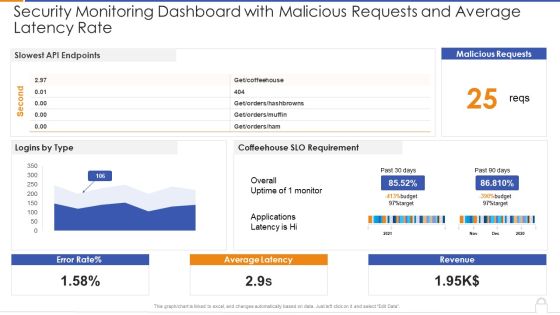
Security Monitoring Dashboard With Malicious Requests And Average Latency Rate Introduction PDF
Deliver an awe inspiring pitch with this creative security monitoring dashboard with malicious requests and average latency rate introduction pdf bundle. Topics like security monitoring dashboard with malicious requests and average latency rate can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Management Dashboard With Downtime Issues And Unsolved Tickets Structure PDF
Deliver and pitch your topic in the best possible manner with this security management dashboard with downtime issues and unsolved tickets structure pdf. Use them to share invaluable insights on security management dashboard with downtime issues and unsolved tickets and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Security Monitoring Dashboard Rate Summary PDF
Deliver and pitch your topic in the best possible manner with this continuous development evaluation plan eliminate cyber attacks security monitoring dashboard rate summary pdf. Use them to share invaluable insights on security monitoring dashboard with malicious requests and average latency rate and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Managed Cyber Security Solutions Service Strategies For Effective Content Management Ppt Styles Example File PDF
The following slide highlights various managed security services strategies used for effective content management. Clean up plugins, scanning CMS platforms, and using the latest version are some of the key strategies which are highlighted in this template. Persuade your audience using this Managed Cyber Security Solutions Service Strategies For Effective Content Management Ppt Styles Example File PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Managed Cyber Security, Solutions Service Strategies, Effective Content Management. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Portable Home Safety Systems Company Profile Our Security Services And Solutions Information PDF
This slide highlights the security company services which includes CCTV, mobile app and software, occupancy sensor, audio video solution. Co2 monitor, door sensor, leak detector, smoke detector and indoor camera. Deliver and pitch your topic in the best possible manner with this Portable Home Safety Systems Company Profile Our Security Services And Solutions Information PDF. Use them to share invaluable insights on Window Sensor, Door Sensor, Occupancy Sensor, Display Solutions and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Vulnerabilities With Threat Source And Action Organizations Risk Management And IT Security Download PDF
The following slide highlights the information technology vulnerabilities which includes the thread source from terminated employees and unauthorized users and threat action. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our IT Vulnerabilities With Threat Source And Action Organizations Risk Management And IT Security Download PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into IT Vulnerabilities With Threat Source And Action Organizations Risk Management And IT Security Download PDF.

IT System Risk Management Guide Financial Burden To Company From IT Security Breaches Background PDF
This slide highlights the financial burden of information technology security breaches which includes professional services, lost business opportunities, down time from multiple offices with losses. Present like a pro with IT System Risk Management Guide Financial Burden To Company From IT Security Breaches Background PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Impact On Organization After Implementing Information Security Strategy Ppt PowerPoint Presentation Gallery Deck PDF
This slide depicts the impact of cyber security training on an organization. It also shows how trained employees can reduce cyber attacks in the organization. Deliver and pitch your topic in the best possible manner with this impact on organization after implementing information security strategy ppt powerpoint presentation gallery deck pdf. Use them to share invaluable insights on system misconfiguration, phishing, network intrusion, inadvertent disclosure and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Attacks Faced By Different Departments Information Security Risk Administration Clipart PDF
This slide showcase information security attacks faced by different departments of organization. Its key elements are department, number of cyber attacks and type of cyber attacks.Boost your pitch with our creative Cyber Attacks Faced By Different Departments Information Security Risk Administration Clipart PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
Managing IT Operating System 4 Dimensions Of Infrastructure Security Template PDF
Presenting this set of slides with name managing it operating system 4 dimensions of infrastructure security template pdf. The topics discussed in these slides are infrastructure, applications, data, people. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
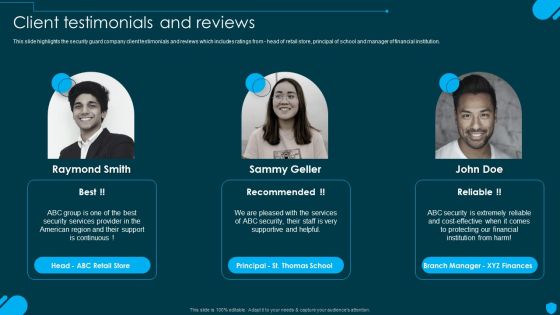
Security And Human Resource Services Business Profile Client Testimonials And Reviews Information PDF
This slide highlights the security guard company client testimonials and reviews which includes ratings from - head of retail store, principal of school and manager of financial institution. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Security And Human Resource Services Business Profile Client Testimonials And Reviews Information PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
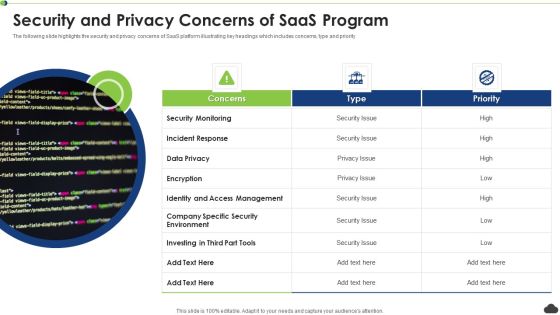
Security And Privacy Concerns Of Saas Program Ppt PowerPoint Presentation File Background PDF
The following slide highlights the security and privacy concerns of SaaS platform illustrating key headings which includes concerns, type and priority. Persuade your audience using this security and privacy concerns of saas program ppt powerpoint presentation file background pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including security monitoring, incident response, encryption. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Deploying Corporate Aligned IT Strategy How Management Enables Effective Corporate Security Governance Topics PDF
This slide portrays information regarding the management role in effective corporate security governance by highlight management level, strategic alignment, risk management, etc. The Deploying Corporate Aligned IT Strategy How Management Enables Effective Corporate Security Governance Topics PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
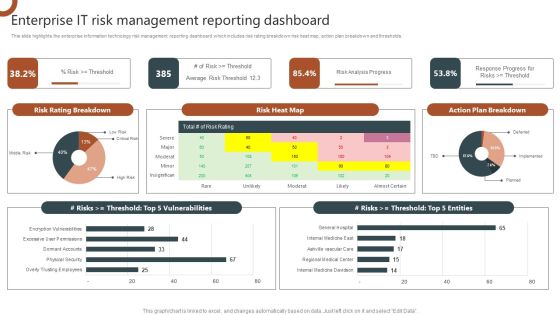
Organizations Risk Management And IT Security Enterprise IT Risk Management Reporting Dashboard Diagrams PDF
This slide highlights the enterprise information technology risk management reporting dashboard which includes risk rating breakdown risk heat map, action plan breakdown and thresholds. This Organizations Risk Management And IT Security Enterprise IT Risk Management Reporting Dashboard Diagrams PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Organizations Risk Management And IT Security Enterprise IT Risk Management Reporting Dashboard Diagrams PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today.

Comparative Analysis Of Various Security For Cloud Based Systems Tools Formats PDF
This slide shows comparison amongst various cloud security tools which can be used by the organization to select the best suitable tool. it also includes details about features, price and ratings. Showcasing this set of slides titled Comparative Analysis Of Various Security For Cloud Based Systems Tools Formats PDF. The topics addressed in these templates are Comparative Analysis, Various Security For Cloud, Based Systems Tools. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Security And Human Resource Services Business Profile Company Timeline From 1992 To 2022 Pictures PDF
This slide highlights the security company journey which showcases founding year, add armed security services in 2004, acquire GS security on 2015, add cash vans in 2016 and recruit personal protection officers. Get a simple yet stunning designed Security And Human Resource Services Business Profile Company Timeline From 1992 To 2022 Pictures PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Security And Human Resource Services Business Profile Company Timeline From 1992 To 2022 Pictures PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Evolving BI Infrastructure Determine Overview Of Established Security Centre Slides PDF
This slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. Presenting evolving bi infrastructure determine overview of established security centre slides pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like management staff, steering committee, internal systems, backup, functional business units. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Security Risk Evaluation Probability Assessment Matrix For Risk Management Demonstration PDF
This slide showcase matrix that can help organization to identify the probability of different information security attacks and formulate mitigation strategy in advance. It can help organization to manage the major risks and safeguard the information.Deliver and pitch your topic in the best possible manner with this Information Security Risk Evaluation Probability Assessment Matrix For Risk Management Demonstration PDF. Use them to share invaluable insights on Accidental Intentional, Unauthorized, Critical Information and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information Security Risk Evaluation Matrix For Threat Solution And Risk Management Ideas PDF
This slide showcases matrix that can help organization to formulate solutions for different types of information security attacks. It can help organization to mitigate the risks and safeguard information in case of any attack.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Matrix For Threat Solution And Risk Management Ideas PDF bundle. Topics like Privilege Abuse, Storage Exposure, Database Activity can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
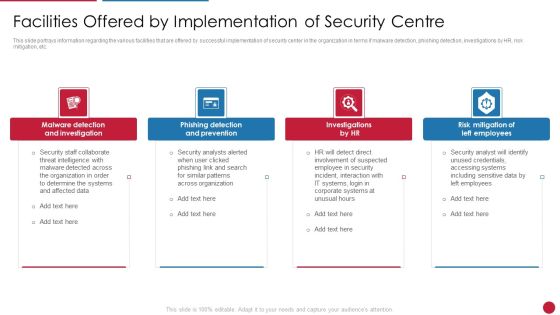
Facilitating IT Intelligence Architecture Facilities Offered By Implementation Of Security Centre Demonstration PDF
This slide portrays information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. This is a Facilitating IT Intelligence Architecture Facilities Offered By Implementation Of Security Centre Demonstration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Malware Detection And Investigation, Phishing Detection And Prevention, Risk Mitigation Of Left You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
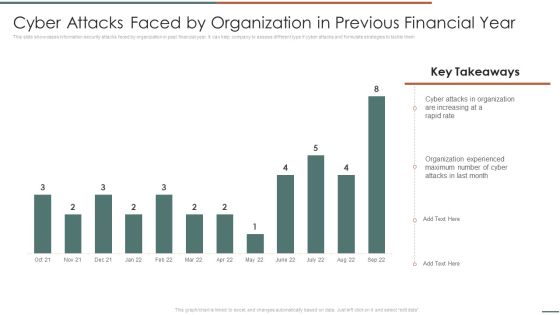
Information Security Risk Evaluation Cyber Attacks Faced By Organization In Previous Financial Year Template PDF
This slide showcases information security attacks faced by organization in past financial year. It can help company to assess different type if cyber attacks and formulate strategies to tackle them.Deliver and pitch your topic in the best possible manner with this Information Security Risk Evaluation Cyber Attacks Faced By Organization In Previous Financial Year Template PDF. Use them to share invaluable insights on Attacks In Organization, Organization Experienced, Attacks Last and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Allocating Budget For Information Security Risk Management Programme Cybersecurity Risk Assessment Brochure PDF
This slide showcase budget to be allocated for conducting training for information security risk management. It showcases budget for areas like cybersecurity awareness, threat detection and risk management. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Allocating Budget For Information Security Risk Management Programme Cybersecurity Risk Assessment Brochure PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Current Information Security Issues Faced By Organization Cybersecurity Risk Assessment Guidelines PDF
This Current Information Security Issues Faced By Organization Cybersecurity Risk Assessment Guidelines PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Current Information Security Issues Faced By Organization Cybersecurity Risk Assessment Guidelines PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Cybersecurity Risk Administration Plan Budget For Information Security Management Elements PDF
Mentioned slide shows budget for managing information security. It includes information such as functional area, software name, training duration, training cost, number of employees and total training cost.Presenting Cybersecurity Risk Administration Plan Budget For Information Security Management Elements PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Incident Management, Asset Management, Risk Management In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Systems Security And Risk Management Plan Matrix For Threat Solution And Risk Management Microsoft PDF
This slide showcases matrix that can help organization to formulate solutions for different types of information security attacks. It can help organization to mitigate the risks and safeguard information in case of any attack. There are so many reasons you need a Information Systems Security And Risk Management Plan Matrix For Threat Solution And Risk Management Microsoft PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Cybersecurity What Are The Benefits Of Electronic Information Security Ppt Infographics Ideas PDF
This slide depicts the different benefits of deploying a cyber security model in an organization and how it can minimize the risk and save a companys time, money, and efforts. Presenting cybersecurity what are the benefits of electronic information security ppt infographics ideas pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like management, process, cybersecurity, environment, potential. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cybersecurity Requirement Of Electronic Information Security In Different Sectors Ppt Slides Summary PDF
This slide depicts the requirement of cyber security in different sectors and the percentage of attacks experienced in the medical, govt, military, and corporate sectors in the past 12 months. Deliver and pitch your topic in the best possible manner with this cybersecurity requirement of electronic information security in different sectors ppt slides summary pdf. Use them to share invaluable insights on financial, organizations, process, information and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information Systems Security And Risk Management Plan Venn Diagram Topics PDF
Whether you have daily or monthly meetings, a brilliant presentation is necessary. Information Systems Security And Risk Management Plan Venn Diagram Topics PDF can be your best option for delivering a presentation. Represent everything in detail using Information Systems Security And Risk Management Plan Venn Diagram Topics PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
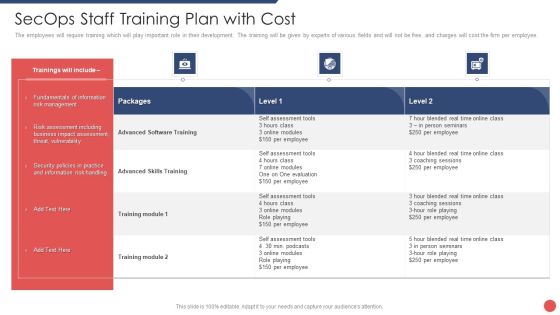
Security Functioning Centre Secops Staff Training Plan With Cost Information PDF
The employees will require training which will play important role in their development. The training will be given by experts of various fields and will not be free, and charges will cost the firm per employee. Deliver an awe inspiring pitch with this creative security functioning centre secops staff training plan with cost information pdf bundle. Topics like risk assessment, business, security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Organizations Risk Management And IT Security Integration Of Risk Management Into SDLC Inspiration PDF
This slide highlights the risk management integration with software development life cycle which includes SDLC phases Initiation, development, implementation and maintenance with risk management activities. The Organizations Risk Management And IT Security Prioritized Cyber Security Threats With Risk Mitigation Plan Demonstration PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
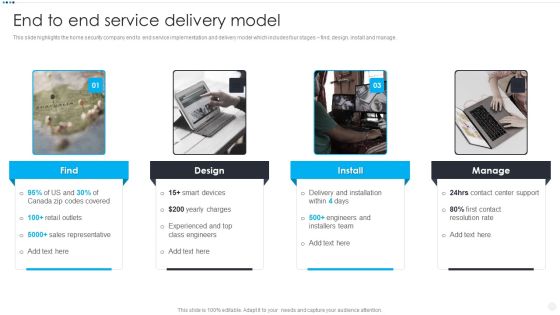
Smart Home Security Solutions Company Profile End To End Service Delivery Model Slides PDF
This slide highlights the home security company end to end service implementation and delivery model which includes four stages find, design, install and manage. Presenting Smart Home Security Solutions Company Profile End To End Service Delivery Model Slides PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Delivery And Installation, Contact Center Support, Contact Resolution Rate, Engineers And Installers. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security And Surveillance Company Profile End To End Service Delivery Model Topics PDF
This slide highlights the home security company end to end service implementation and delivery model which includes four stages find, design, install and manage.Presenting Security And Surveillance Company Profile End To End Service Delivery Model Topics PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Sales Representative, Experienced Engineers, Engineers Installers. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Digitalization Of Operative Enterprises IT OT Convergence Security Objectives Challenges Catalysts And Benefits Download PDF
This slide covers objectives challenges catalysts and benefits of the security in IT or OT convergence and reduce systems cyberattack surface. This is a Digitalization Of Operative Enterprises IT OT Convergence Security Objectives Challenges Catalysts And Benefits Download PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Objectives, Challenges, Benefits. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
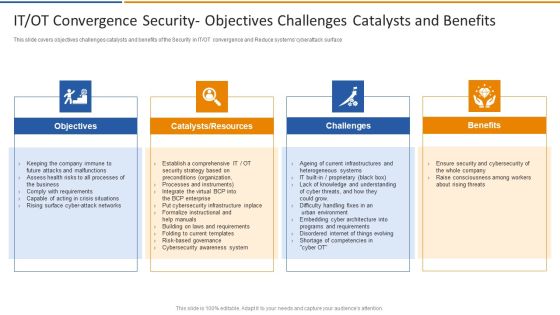
IT OT Convergence Security Objectives Challenges Smart Venture Digitial Transformation Designs PDF
This slide covers objectives challenges catalysts and benefits of the Security in IT or OT convergence and Reduce systems cyberattack surface. This is a IT OT Convergence Security Objectives Challenges Smart Venture Digitial Transformation Designs PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Objectives, Catalysts, Resources, Challenges, Benefits. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT OT Convergence Security Objectives Challenges Managing Organizational Transformation Professional PDF
This slide covers objectives challenges catalysts and benefits of the Security in IT OT convergence and Reduce systems cyberattack surface. This is a IT OT Convergence Security Objectives Challenges Managing Organizational Transformation Professional PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Objectives, Catalysts Resources, Challenges, Benefits. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Monitoring Dashboard With Application Control And Operating System Statistics Template PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver and pitch your topic in the best possible manner with this security monitoring dashboard with application control and operating system statistics template pdf. Use them to share invaluable insights on application control, restrict office macros, application patching, application hardening and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Developing IT Security Strategy Matrix For Threat Solution And Risk Management Topics PDF
This slide showcases matrix that can help organization to formulate solutions for different types of information security attacks. It can help organization to mitigate the risks and safeguard information in case of any attack. Find highly impressive Developing IT Security Strategy Matrix For Threat Solution And Risk Management Topics PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Developing IT Security Strategy Matrix For Threat Solution And Risk Management Topics PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
Online Settlement Revolution Payment Security And Fraud Management Solutions Browser Icons PDF
Payment security and fraud management solutions for the user to limit losses while maintain a high level of customer satisfaction. Presenting online settlement revolution payment security and fraud management solutions browser icons pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like costs, process, analytics, development. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Where Is The Gap In Security Programs Ppt Icon Layout Ideas PDF
This slide covers the problems in the organization regarding security awareness training along with the gap and solution to overcome those gaps Presenting where is the gap in security programs ppt icon layout ideas pdf. to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like problems, gap, solution. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
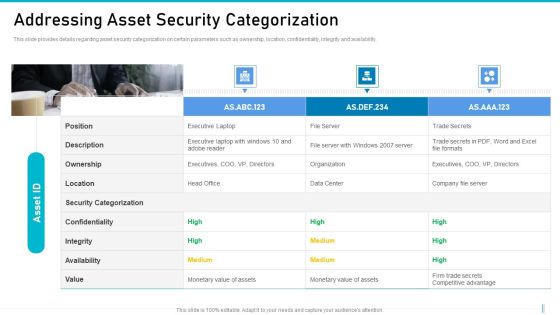
Risk Management For Organization Essential Assets Addressing Asset Security Categorization Diagrams PDF
This slide provides details regarding asset security categorization on certain parameters such as ownership, location, confidentiality, integrity and availability. Presenting risk management for organization essential assets addressing asset security categorization diagrams pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like ownership, location, confidentiality, integrity, availability. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Practices To Improve Security Awareness Level Amongst The Employees Contd Structure PDF
The purpose of this slide is to outline multiple ways which can be used by the organization to improve the cyber security awareness level of employees. The key practices mentioned in the slide are involving top level management, developing robust policies, and setting guidelines. Presenting Practices To Improve Security Awareness Level Amongst The Employees Contd Structure PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Management Involved, Develop Robust, Set Guidelines. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Dashboard To Track IT Security Incidents Prevailing Across Firm Elements PDF
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Dashboard To Track IT Security Incidents Prevailing Across Firm Elements PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Dashboard To Track IT Security Incidents Prevailing Across Firm Elements PDF.

Organizational Assets Security Management Strategy Determine User Access Controls Levels Diagrams PDF
This slide provides information about information user access controls levels for access critical assets and information associated to firm and levels of access for administrator, maintainer, guest or disabled. Get a simple yet stunning designed Organizational Assets Security Management Strategy Determine User Access Controls Levels Diagrams PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Organizational Assets Security Management Strategy Determine User Access Controls Levels Diagrams PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

IT Security Evaluation Scorecard With Bar Graph Ppt Gallery Design Templates PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver and pitch your topic in the best possible manner with this IT Security Evaluation Scorecard With Bar Graph Ppt Gallery Design Templates PDF. Use them to share invaluable insights on CPU Utilization Memory, Utilization Packet Loss and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Security Evaluation Scorecard With Impact Status Ppt Portfolio Guidelines PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver and pitch your topic in the best possible manner with this IT Security Evaluation Scorecard With Impact Status Ppt Portfolio Guidelines PDF. Use them to share invaluable insights on Device Availability Application, Performance Port Health, Devices Reference Firmware and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Security Evaluation Scorecard With Ip Availability Ppt Pictures Portrait PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver and pitch your topic in the best possible manner with this IT Security Evaluation Scorecard With Ip Availability Ppt Pictures Portrait PDF. Use them to share invaluable insights on Devices Memory Utilization, Interfaces Errors Discards, IP Availability Summary and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Security Evaluation Scorecard With System Details Ppt Inspiration Vector PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver and pitch your topic in the best possible manner with this IT Security Evaluation Scorecard With System Details Ppt Inspiration Vector PDF. Use them to share invaluable insights on System Details Availability, System Metrics Memory, Pressure Memory Leak and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
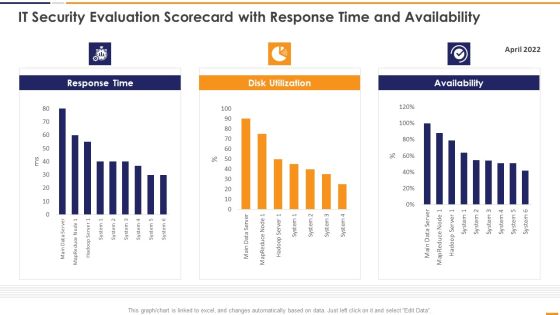
IT Security Evaluation Scorecard With Response Time And Availability Brochure PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver and pitch your topic in the best possible manner with this IT Security Evaluation Scorecard With Response Time And Availability Brochure PDF. Use them to share invaluable insights on Response Time 2022, Disk Utilization Availability and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Security Employee Awareness Training Budget For FY2020 Ppt Pictures Example PDF
This slide represents the organizations staff training budget through a graph covering trainer name, date, and capability levels. Deliver an awe inspiring pitch with this creative information technology security employee awareness training budget for fy2020 ppt gallery information pdf bundle. Topics like employee awareness training budget for fy2020 can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security And Human Resource Services Business Profile Executive Summary Infographics PDF
This slide highlights the executive summary of security company that includes company overview, founder, USP, company shareholding, achievements, key facts and figures. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Security And Human Resource Services Business Profile Executive Summary Infographics PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Security And Human Resource Services Business Profile Executive Summary Infographics PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

IT Reducing Costs And Management Tips How Management Enables Effective Corporate Security Governance Mockup PDF
This slide portrays information regarding the management role in effective corporate security governance by highlight management level, strategic alignment, risk management, etc. Get a simple yet stunning designed IT Reducing Costs And Management Tips How Management Enables Effective Corporate Security Governance Mockup PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit IT Reducing Costs And Management Tips How Management Enables Effective Corporate Security Governance Mockup PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Dashboard To Track IT Security Incidents Prevailing Across Firm Infographics PDF
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Dashboard To Track IT Security Incidents Prevailing Across Firm Infographics PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Dashboard To Track IT Security Incidents Prevailing Across Firm Infographics PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Dashboard To Track IT Security Incidents Prevailing Across Firm Demonstration PDF
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Dashboard To Track IT Security Incidents Prevailing Across Firm Demonstration PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Dashboard To Track IT Security Incidents Prevailing Across Firm Demonstration PDF today and make your presentation stand out from the rest
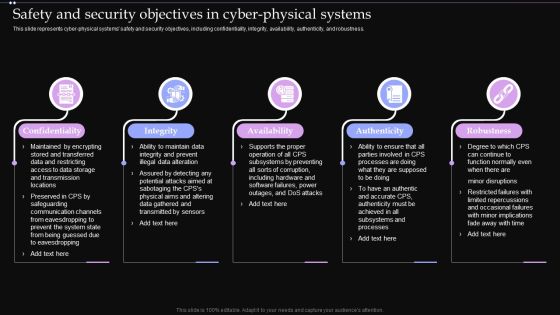
Safety And Security Objectives In Cyber Physical Systems Ppt PowerPoint Presentation File Example PDF
This slide represents cyber physical systems safety and security objectives, including confidentiality, integrity, availability, authenticity, and robustness. The Safety And Security Objectives In Cyber Physical Systems Ppt PowerPoint Presentation File Example PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Integration Of Digital Technology In Organization Need Of Cyber Security In Organization Information PDF
This slide covers the need of introducing cybersecurity in the business and how can organization integrate cybersecurity with digital transformation.Presenting Integration Of Digital Technology In Organization Need Of Cyber Security In Organization Information PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Confidential Data, Protection Phishing, Protection Against In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Analysis To Enable Safe Technology Transformation Ppt PowerPoint Presentation Visual Aids Styles PDF
Persuade your audience using this cyber security analysis to enable safe technology transformation ppt powerpoint presentation visual aids styles pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including cyber security assessment, identify risks. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
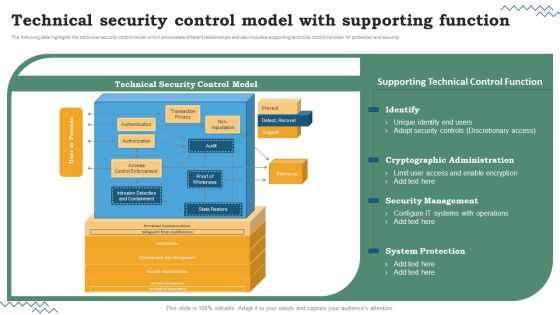
Software Development Life Cycle Planning Technical Security Control Model With Supporting Function Inspiration PDF
The following slide highlights the technical security control model which showcases different relationships and also includes supporting technical control function for protection and security. Are you searching for a Software Development Life Cycle Planning Technical Security Control Model With Supporting Function Inspiration PDF that is uncluttered, straightforward, and original. Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort youve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Software Development Life Cycle Planning Technical Security Control Model With Supporting Function Inspiration PDF from Slidegeeks today.

Table Of Contents For Cloud Information Security Ppt Slides Vector PDF
Deliver and pitch your topic in the best possible manner with this Table Of Contents For Cloud Information Security Ppt Slides Vector PDF. Use them to share invaluable insights on Cloud Management, Cloud Responsibilities, Shared Vulnerabilities and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cybersecurity Guidelines IT Overview Of Network Security Policy For Workers Portrait PDF
This slide describes the network security policy, which ensures systems have the proper hardware, software, and auditing processes. It logs details of activities such as failed log-in attempts, information starts up or shutdown, etc. Boost your pitch with our creative Cybersecurity Guidelines IT Overview Of Network Security Policy For Workers Portrait PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Agenda For Information Security Risk Evaluation And Administration Plan Pictures PDF
This is a Agenda For Information Security Risk Evaluation And Administration Plan Pictures PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Agenda. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

5 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Portrait PDF
Presenting 5 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Portrait PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Business Goals, Management Program, Secure Corporate. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Firewall As A Service Fwaas Working And Security Features Ppt File Guidelines PDF
This slide describes the working and security features of the firewall as a service. The purpose of this slide is to demonstrate the working of the firewall as a service, including its security features such as packet filtering, network monitoring, IPsec, SSL VPN support, DPI, and IP mapping. Create an editable Firewall As A Service Fwaas Working And Security Features Ppt File Guidelines PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Firewall As A Service Fwaas Working And Security Features Ppt File Guidelines PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Information Security Management With Actions And Interactions Ppt PowerPoint Presentation Gallery Graphics PDF
Showcasing this set of slides titled information security management with actions and interactions ppt powerpoint presentation gallery graphics pdf. The topics addressed in these templates are causal, consequences, interactions. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Security Awareness Checklist To Ensure It Asset Protection Ppt Model Shapes PDF
The purpose of this slide is to outline a comprehensive checklist which can be used to ensure information technology IT asset protection. It cover points such as operating system is up to date, employees are using strong password policy etc. Create an editable Cyber Security Awareness Checklist To Ensure It Asset Protection Ppt Model Shapes PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Cyber Security Awareness Checklist To Ensure It Asset Protection Ppt Model Shapes PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Mobile Device Management Ensuring Checklist For Mobile Security Deployment Elements PDF
This slide provides information regarding mobile device compliance and policy enforcement with automated device setup, dynamic workflows and policies, etc. This slide provides information regarding mobile device security deployment checklist in terms of device security, protection against malicious codes. There are so many reasons you need a Mobile Device Management Ensuring Checklist For Mobile Security Deployment Elements PDF. The first reason is you cant spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Net Banking Channel And Service Management Major Types Of E Banking Security Threats Inspiration PDF
This slide represents types of e banking security threats. It includes brute force, phishing, pharming, cross site scripting and trojan horse. The Net Banking Channel And Service Management Major Types Of E Banking Security Threats Inspiration PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Key Steps To Create Role Specific Cyber Security Training Program Structure PDF
This slide highlights various steps to develop role based training program for cyber security risk management. It includes key steps such as assess existing training, identify employee roles, define role-specific security risks, outline process and technology, etc. Persuade your audience using this Key Steps To Create Role Specific Cyber Security Training Program Structure PDF This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Process, Description, Elements. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Mobile Device Management For Android Platform Mobile Device Security Management Demonstration PDF
This slide provides information regarding mobile device management for android platform with device settings policy, device security settings, etc. Presenting Mobile Device Management For Android Platform Mobile Device Security Management Demonstration PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Device Security, Application Control, Remote Management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Officer Service Company Profile Executive Leadership And Management Team Background PDF
This slide highlights the security guard company management team which includes companys chairman and MD, head of security operations, training, strategic growth and site. Presenting Security Officer Service Company Profile Executive Leadership And Management Team Background PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Human Resource Management, Business Strategist, Management Consultant, Strategizing Business. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Addressing Confidentiality Integrity And Availability In Iot Security Compliance Ppt Portfolio Deck PDF
This slide provides information regarding security objectives such as confidentiality, integrity and availability and their role in IoT security compliance. Boost your pitch with our creative Addressing Confidentiality Integrity And Availability In Iot Security Compliance Ppt Portfolio Deck PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
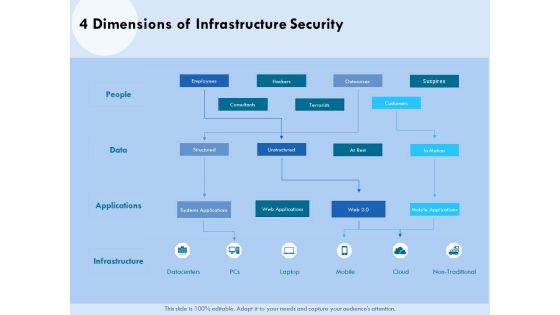
Functional Analysis Of Business Operations 4 Dimensions Of Infrastructure Security Designs PDF
Presenting this set of slides with name functional analysis of business operations 4 dimensions of infrastructure security designs pdf. The topics discussed in these slides are employees, infrastructure, data, mobile, cloud. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
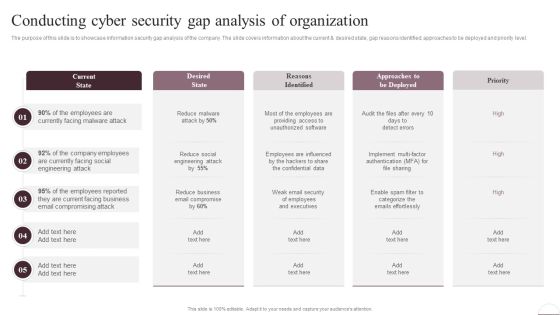
Prevention Of Information Conducting Cyber Security Gap Analysis Of Organization Information PDF
The purpose of this slide is to showcase information security gap analysis of the company. The slide covers information about the current and desired state, gap reasons identified, approaches to be deployed and priority level. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Prevention Of Information Conducting Cyber Security Gap Analysis Of Organization Information PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Prevention Of Information Conducting Cyber Security Gap Analysis Of Organization Information PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today

Workplace Portable Device Monitoring And Administration Ensuring Checklist For Mobile Security Deployment Pictures PDF
This slide provides information regarding mobile device security deployment checklist in terms of device security, protection against malicious codes. Welcome to our selection of the Workplace Portable Device Monitoring And Administration Ensuring Checklist For Mobile Security Deployment Pictures PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
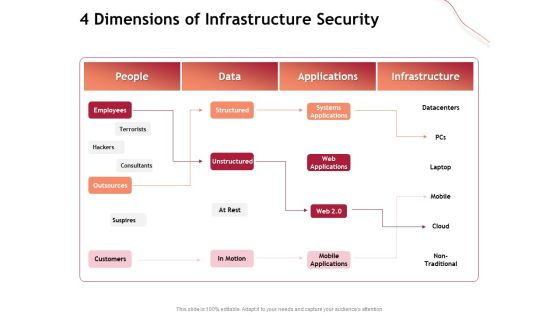
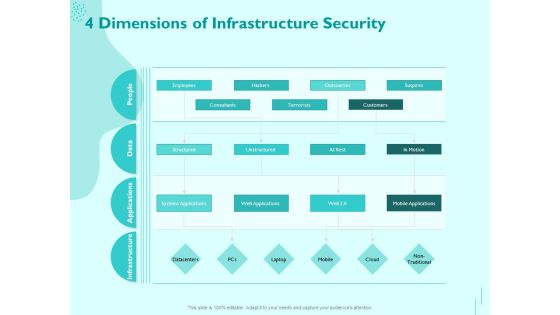
Performance Measuement Of Infrastructure Project 4 Dimensions Of Infrastructure Security Infographics PDF
Presenting this set of slides with name performance measuement of infrastructure project 4 dimensions of infrastructure security infographics pdf. The topics discussed in these slides are people, data, applications, infrastructure. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Dashboard Incident Tracking Ppt Gallery Infographics PDF
Presenting this set of slides with name computer security incident handling dashboard incident tracking ppt gallery infographics pdf. The topics discussed in these slides are application whitelisting, patch applications, patch operating systems, restrict admin privileges, user application hardening, daily backup of important data. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Key Features For Effective Business Management 4 Dimensions Of Infrastructure Security Ppt Icon Gridlines PDF
Presenting this set of slides with name key features for effective business management 4 dimensions of infrastructure security ppt icon gridlines pdf. This is a four stage process. The stages in this process are people, data, applications, infrastructure, mobile applications, suspires, outsources, systems applications, cloud. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Security Software Company Investor Funding Pitch Deck Investment Ask Clipart PDF
This slide represents the information related to the investment requirements to the investors for seeking needed funds and the purpose of seeking finance. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Security Software Company Investor Funding Pitch Deck Investment Ask Clipart PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Security Software Company Investor Funding Pitch Deck Investment Ask Clipart PDF today and make your presentation stand out from the rest.

Cybersecurity Risk Administration Plan Information Security Decision Framework PRISM Workflow Topics PDF
Deliver and pitch your topic in the best possible manner with this Cybersecurity Risk Administration Plan Information Security Decision Framework PRISM Workflow Topics PDF Use them to share invaluable insights on Prioritization Weighting, Resource Allocation, Risk Management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

ISO 27001 Organizational Qualifying Procedure ISO 27001 Information Security Management Standard Mockup PDF
Deliver an awe inspiring pitch with this creative ISO 27001 Organizational Qualifying Procedure ISO 27001 Information Security Management Standard Mockup PDF bundle. Topics like Leadership Requirements, Contextual Requirements, Planning Requirements can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
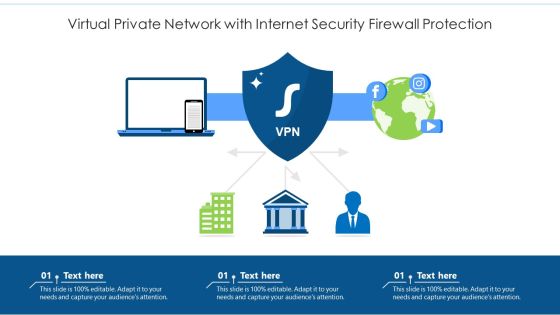
Virtual Private Network With Internet Security Firewall Protection Ppt PowerPoint Presentation File Master Slide PDF
Persuade your audience using this virtual private network with internet security firewall protection ppt powerpoint presentation file master slide pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including virtual private network with internet security firewall protection. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
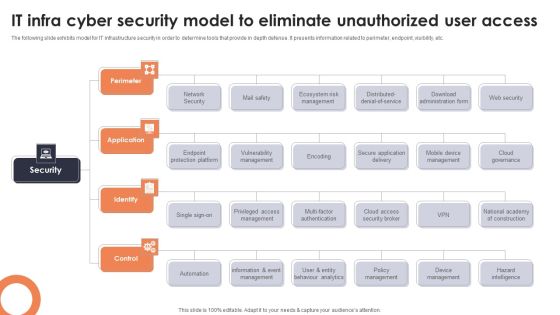
IT Infra Cyber Security Model To Eliminate Unauthorized User Access Topics PDF
The following slide exhibits model for IT infrastructure security in order to determine tools that provide in depth defense. It presents information related to perimeter, endpoint, visibility, etc. Presenting IT Infra Cyber Security Model To Eliminate Unauthorized User Access Topics PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Perimeter, Application, Identify. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Developing IT Security Strategy Probability Assessment Matrix For Risk Management Formats PDF
This slide showcase matrix that can help organization to identify the probability of different information security attacks and formulate mitigation strategy in advance. It can help organization to manage the major risks and safeguard the information. Make sure to capture your audiences attention in your business displays with our gratis customizable Developing IT Security Strategy Probability Assessment Matrix For Risk Management Formats PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Checklist For Testing Of Application Programming Interface Security Testing Practices Microsoft PDF
This slide illustrates list of best practices for API security testing to ensure it is thorough. It includes budget resources and time, define the test types to run, etc. Showcasing this set of slides titled Checklist For Testing Of Application Programming Interface Security Testing Practices Microsoft PDF. The topics addressed in these templates are Application Programming, Interface Security, Testing Practices. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Security Agency Business Profile Executive Leadership And Management Team Elements PDF
This slide highlights the security guard company management team which includes companys chairman and MD, head of security operations, training, strategic growth and site. Presenting Security Agency Business Profile Executive Leadership And Management Team Elements PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Business Economist, Resource Management, Manufacturing. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
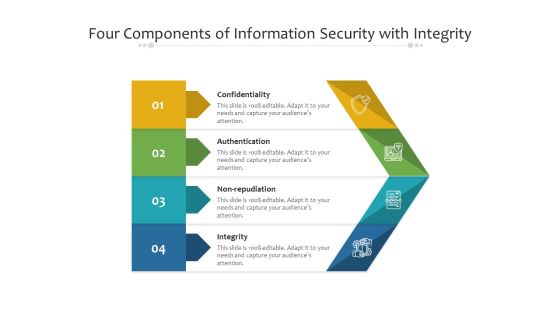
Four Components Of Information Security With Integrity Ppt PowerPoint Presentation File Gallery PDF
Presenting four components of information security with integrity ppt powerpoint presentation file gallery pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including confidentiality, authentication, integrity. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cloud Security KPI Dashboard With Key Statistics Ppt Icon Examples PDF
Pitch your topic with ease and precision using this Cloud Security KPI Dashboard With Key Statistics Ppt Icon Examples PDF. This layout presents information on Compliance Trend, Risk Status, Risk Severity. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

 Home
Home