Data Security

Essential Elements To Be Included In A Security Management Plan Rules PDF
This slide provides information about the essential elements parts that must be included in security management plan by the company and IT security manager. Deliver an awe inspiring pitch with this creative essential elements to be included in a security management plan rules pdf bundle. Topics like program management, prevention, preparedness can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Techniques And Strategies To Reduce Security Management Risks Essential Elements To Be Included Pictures PDF
This slide provides information about the essential elements or parts that must be included in security management plan by the company and IT security manager.Deliver an awe inspiring pitch with this creative techniques and strategies to reduce security management risks essential elements to be included pictures pdfc bundle. Topics like program management, preparedness, contingent procedures can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

MDM Strategies At Office Implementing Mobile Device Security Framework Roadmap Rules PDF
This slide portrays information regarding optimization of current mobile device security framework. The IT department will require to fulfill crucial activities in specific timeframe. Deliver an awe inspiring pitch with this creative MDM Strategies At Office Implementing Mobile Device Security Framework Roadmap Rules PDF bundle. Topics like Implement Enterprise, Security Program, Implement Control can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
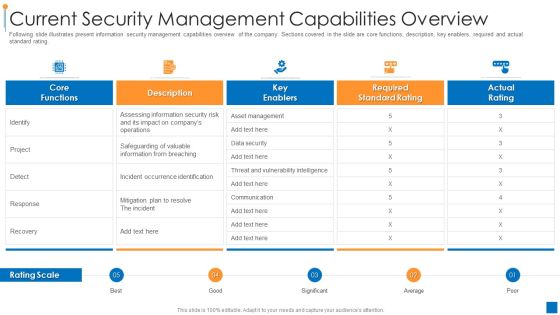
International Organization Standardization 270001 Current Security Management Capabilities Overview Pictures PDF
Following slide illustrates present information security management capabilities overview of the company. Sections covered in the slide are core functions, description, key enablers, required and actual standard rating. Deliver and pitch your topic in the best possible manner with this international organization standardization 270001 current security management capabilities overview pictures pdf. Use them to share invaluable insights on current security management capabilities overview and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
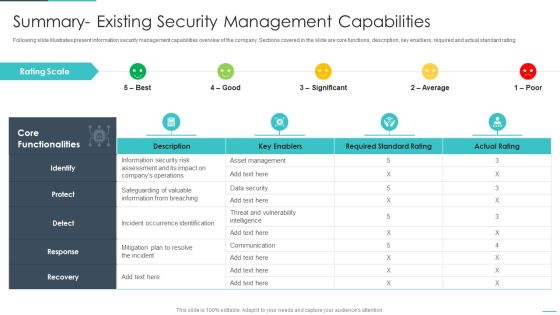
Handling Cyber Threats Digital Era Summary Existing Security Management Capabilities Ppt File Demonstration PDF
Following slide illustrates present information security management capabilities overview of the company. Sections covered in the slide are core functions, description, key enablers, required and actual standard rating. Deliver an awe inspiring pitch with this creative handling cyber threats digital era summary existing security management capabilities ppt file demonstration pdf bundle. Topics like summary existing security management capabilities can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

MDM Strategies At Office Effective Mobile Device Security Management Ideas PDF
This slide portrays information regarding how firm is successful in handling security issues or events and is able in reducing the occurrence of events associated to mobile device. Deliver an awe inspiring pitch with this creative MDM Strategies At Office Effective Mobile Device Security Management Ideas PDF bundle. Topics like Incidents Damaging, Security Incidents, Malicious Codes can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
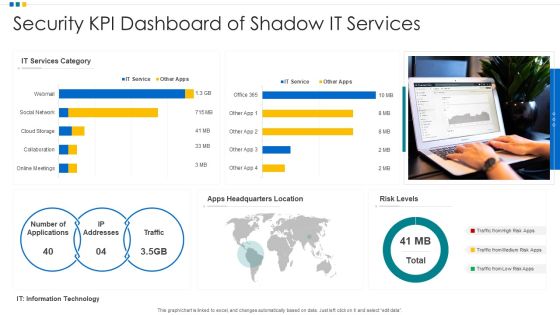
Security KPI Dashboard Of Shadow It Services Ppt Ideas Deck PDF
Pitch your topic with ease and precision using this Security KPI Dashboard Of Shadow It Services Ppt Ideas Deck PDF. This layout presents information on Security KPI Dashboard, Shadow It Services, Risk Levels. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Minimum Cloud Security Standards For Saas And Paas Ppt PowerPoint Presentation Gallery Skills PDF
The following slide depicts the minimum security standards to protect software and platform as a service SaaS and PaaS. It includes elements such as encryption, authentication, security and privacy etc. along with high, medium and low risk level. Pitch your topic with ease and precision using this Minimum Cloud Security Standards For Saas And Paas Ppt PowerPoint Presentation Gallery Skills PDF. This layout presents information on Required Actions, Encryption, Security And Privacy. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Cybersecurity Risk Scorecard Information Security Scorecard For Company With Risk Gap Professional PDF
Presenting cybersecurity risk scorecard information security scorecard for company with risk gap professional pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like protective technology, continuous security monitoring, training of employees. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
IT Security Awareness Training Program Plan Icon Ppt Ideas Graphics PDF
Presenting IT Security Awareness Training Program Plan Icon Ppt Ideas Graphics PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including IT Security Awareness, Training Program Plan, Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Multiple Types Of Managed Cyber Security Solutions Services Ppt Styles Layout Ideas PDF
This slide exhibits the different types of managed security services such as risk management, virtual CISO and security awareness education. It also provides information about the multiple offerings of each service. Persuade your audience using this Multiple Types Of Managed Cyber Security Solutions Services Ppt Styles Layout Ideas PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Risk Management, Offerings, Security Awareness Education, Virtual CISO. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Prevention Of Information Evaluating IT System Security Using Swot Analysis Download PDF
The purpose of this slide is to outline the strength, weakness, opportunities and threat SWOT evaluation of organization cyber security. Organization can detect the potential risks and opportunities in the cyber security using SWOT model. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Prevention Of Information Evaluating IT System Security Using Swot Analysis Download PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Prevention Of Information Evaluating IT System Security Using Swot Analysis Download PDF today and make your presentation stand out from the rest

Four Step Process Of Digitization Of Security Systems Ppt Icon Show PDF
The following slide highlights multistep process of digitization of security systems. The company can detect security breach after following steps such as investigating the steps of IT analyst, determining responsive action, eradication and closing the ticked. Presenting Four Step Process Of Digitization Of Security Systems Ppt Icon Show PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Investigating Steps, Security Analysts, Determining Responsive Action. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Security Management Plan Steps In Detail Adopting Access Controls Download PDF
This slide provides information about the fifth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Adopting Access Controls. Deliver an awe inspiring pitch with this creative security management plan steps in detail adopting access controls download pdf bundle. Topics like logical access controls, control implementation costs, physical access controls can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Techniques And Strategies To Reduce Security Management Risks Measures And Ways To Mitigate Clipart PDF
This slide provides information about the ways and measures through which the company and IT security managers can overcome the problems and issues related to Security Management.Deliver and pitch your topic in the best possible manner with this techniques and strategies to reduce security management risks measures and ways to mitigate clipart pdf Use them to share invaluable insights on potential insider threats, external security breaches, centric breaches and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Five Levels Of Cyber Digitization Of Security Systems Ppt Infographics Graphics Tutorials PDF
The following slide highlights 5 levels of cyber digitization of security systems, type and key description. Each level of security automation defines the current level of organization. Presenting Five Levels Of Cyber Digitization Of Security Systems Ppt Infographics Graphics Tutorials PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Investigating Steps, Security Analysts, Determining Responsive Action. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Multistep Digitization Of Security Systems Checklist Ppt Portfolio Example File PDF
The following slide highlights a comprehensive checklist for digitization of security systems. The checklist covers key points such as deciding the budget, selecting the right tools, deciding the tasks for automation etc. Presenting Multistep Digitization Of Security Systems Checklist Ppt Portfolio Example File PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Security Automation, Checklist, Security Automation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Risk Evaluation Of Information Technology Systems Financial Burden To Company From IT Security Breaches Inspiration PDF
This slide highlights the financial burden of information technology security breaches which includes professional services, lost business opportunities, down time from multiple offices with losses. Present like a pro with Risk Evaluation Of Information Technology Systems Financial Burden To Company From IT Security Breaches Inspiration PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Information And Technology Security Operations Secops Dashboard To Track Vulnerabilities Information PDF
This slide provides information regarding the SecOps dashboard which is used to track and monitor various vulnerabilities identified. Deliver and pitch your topic in the best possible manner with this information and technology security operations secops dashboard to track vulnerabilities information pdf. Use them to share invaluable insights on assets, vulnerabilities, severity and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information Technology Security IT Attacks Experienced By Company Ppt Show Grid PDF
This slide shows the impact on the organizations financial condition due to network attacks in the past financial year 2021. Deliver an awe inspiring pitch with this creative information technology security it attacks experienced by company ppt show grid pdf bundle. Topics like it attacks experienced by company in previous financial year can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Steps To Ensure Robotic Process Automation Security Robotic Process Automation Technology Icons PDF
This slide defines steps to ensure the security of robotic process automation, and it covers guarantee accountability for bot activities, protection from abuse, frauds, logs and bot development.This is a Steps To Ensure Robotic Process Automation Security Robotic Process Automation Technology Icons PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Guarantee Accountability, Empower Secure, Log Respectability. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Systems Security And Risk Management Plan Meet Our Team Template PDF
Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Information Systems Security And Risk Management Plan Impact Of Information Security Loss On Organization Clipart PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Information Systems Security And Risk Management Plan Impact Of Information Security Loss On Organization Clipart PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Prevention Of Information Comparison Of Various Security Awareness Training Software Template PDF
The purpose of this slide is to drawn comparison of multiple software which can be used to provide cyber security training to the key stakeholders. Information covered in this slide is related to phishing simulations, security reporting, individualized security training plan etc. There are so many reasons you need a Prevention Of Information Comparison Of Various Security Awareness Training Software Template PDF. The first reason is you cant spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Application Security Approaches To Manage Cyber It Service Solution Ppt Styles Slide Portrait PDF
This slide exhibits the various application security approaches which can be implemented by organization to manage their IT services. The key approaches are design review, code review and application security audit Showcasing this set of slides titled Application Security Approaches To Manage Cyber It Service Solution Ppt Styles Slide Portrait PDF. The topics addressed in these templates are Design Review, Code Review, Approaches, Application Security Audit. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Information Systems Security And Risk Management Plan Post It Notes Diagrams PDF
Get a simple yet stunning designed Information Systems Security And Risk Management Plan Post It Notes Diagrams PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Information Systems Security And Risk Management Plan Post It Notes Diagrams PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
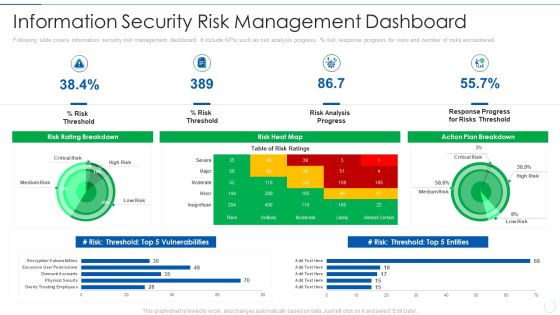
Effective IT Risk Management Process Information Security Risk Management Brochure PDF
Following slide covers information security risk management dashboard. It include KPIs such as risk analysis progress, percentage risk, response progress for risks and number of risks encountered. Deliver an awe inspiring pitch with this creative effective it risk management process information security risk management brochure pdf bundle. Topics like analysis, plan, risk, progress can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Safety Tips Protection Against Cyberattacks IT Security IT Ppt File Aids PDF
This slide represents various tips or procedures that can be followed to prevent an organizations cyber security from cyberattacks or cybercriminals. Presenting cyber safety tips protection against cyberattacks it security it ppt file aids pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like cyber safety tips protection against cyberattacks. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security Cyber Safety Tips Protection Against Cyberattacks Ppt Portfolio Diagrams PDF
This slide represents various tips or procedures that can be followed to prevent an organizations cyber security from cyberattacks or cybercriminals. This is a it security cyber safety tips protection against cyberattacks ppt portfolio diagrams pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cyber safety tips protection against cyberattacks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
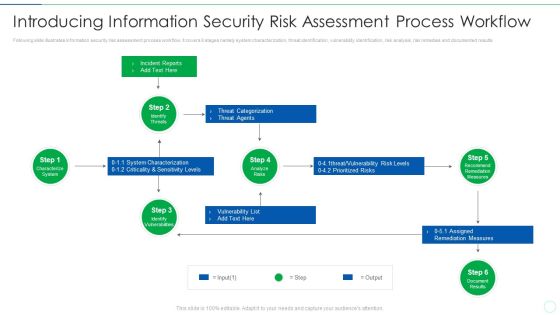
Effective IT Risk Management Process Introducing Information Security Risk Designs PDF
Following slide illustrates information security risk assessment process workflow. It covers 6 stages namely system characterization, threat identification, vulnerability identification, risk analysis, risk remedies and documented results Deliver an awe inspiring pitch with this creative effective it risk management process information security risk assessment formats pdf bundle. Topics like system, risks, measures can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Info Security Hardware And Software Update In Company Ppt PowerPoint Presentation File Mockup PDF
This slide depicts the hardware or software update measure under the cyber security model. It also tells the current status of the devices that need to update in the organization. Presenting info security hardware and software update in company ppt powerpoint presentation file mockup pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like peripheral devices, technology, computers and servers. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Playbook For Advancing Technology Play 11 Administering Security And Privacy Elements PDF
This slide provides information regarding digital services play which helps in managing security and privacy through reusable processes. During initial phase of new service designing, team leader engage with privacy, security and legal officer to assess type of information to be collected, how to secure it, etc. Retrieve professionally designed Playbook For Advancing Technology Play 11 Administering Security And Privacy Elements PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Estimated Security Monitoring Designs PDF
This slide shows the estimated Cyber Security Monitoring Key Performance Indicators of the company after implementing an advanced security monitoring plan, adopting security monitoring best practices and implementing Cybersecurity Monitoring Tool Cain and Abel. Deliver and pitch your topic in the best possible manner with this continuous development evaluation plan eliminate cyber attacks estimated security monitoring designs pdf. Use them to share invaluable insights on estimated security monitoring key performance indicators and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Machine To Machine Communication Outline Iot Security Challenges Ppt File Background Designs PDF
The slide highlights key Challenges in IoT security. Presenting machine to machine communication outline iot security challenges ppt file background designs pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like authentication, access control, privacy, policy enforcement, trust, mobile security, secure middleware, confidentiality. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

Strategies To Enhance Retail Store Security Retail Outlet Performance Assessment Professional PDF
This slide provides information regarding the strategies to enhance retail store security such as integrate access control technology, deploy video surveillance, utilizes electronic article surveillance, install monitored alarms.Deliver an awe inspiring pitch with this creative Strategies To Enhance Retail Store Security Retail Outlet Performance Assessment Professional PDF bundle. Topics like Integrate Access, Control Technology, Prevent Shoplifting can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cios Methodologies To Improve IT Spending Role Of Management In Effective Information Security Microsoft PDF
This slide provides information regarding role of management in effective information security governance in strategic alignment , risk management, integration, value delivery, etc. Deliver an awe inspiring pitch with this creative Cios Methodologies To Improve IT Spending Role Of Management In Effective Information Security Microsoft PDF bundle. Topics like Risk Management, Measuring Performance, Managing Resource can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

CIO For IT Cost Optimization Techniques Role Of Management In Effective Information Security Governance Themes PDF
This slide provides information regarding role of management in effective information security governance in strategic alignment , risk management, integration, value delivery, etc. Deliver and pitch your topic in the best possible manner with this CIO For IT Cost Optimization Techniques Role Of Management In Effective Information Security Governance Themes PDF. Use them to share invaluable insights on Management Level, Strategic Alignment, Risk Management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Spend Management Priorities By Cios Role Of Management In Effective Information Security Governance Graphics PDF
This slide provides information regarding role of management in effective information security governance in strategic alignment , risk management, integration, value delivery, etc. Deliver an awe inspiring pitch with this creative IT Spend Management Priorities By Cios Role Of Management In Effective Information Security Governance Graphics PDF bundle. Topics like Senior Executives, Strategic Alignment, Risk Management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Statistics Showing Growth Rate Of Managed Cyber Security Solutions Service Market Ppt Show Inspiration PDF
This slide exhibits key statistics highlighting overview of managed security service market with expected market growth rate from 2020 to 2030 along with key insights. Pitch your topic with ease and precision using this Statistics Showing Growth Rate Of Managed Cyber Security Solutions Service Market Ppt Show Inspiration PDF. This layout presents information on Statistics Showing Growth, Cyber Security, Solutions Service Market. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Table Of Contents Developing Information Technology Security Awareness Training Program For Employees Graphics PDF
If you are looking for a format to display your unique thoughts, then the professionally designed Table Of Contents Developing Information Technology Security Awareness Training Program For Employees Graphics PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Table Of Contents Developing Information Technology Security Awareness Training Program For Employees Graphics PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Information And Technology Security Operations Impact Of Successful Implementation Of Secops System Download PDF
This slide portrays information regarding the impact of successful implementation of SecOps system in terms alert fatigue reduction, threat hunting improvement, etc. Presenting information and technology security operations impact of successful implementation of secops system download pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like security, analyst, improvement, reduction. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
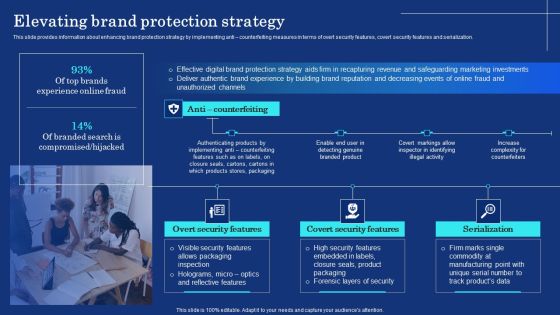
Organizational Assets Security Management Strategy Elevating Brand Protection Strategy Guidelines PDF
This slide provides information about enhancing brand protection strategy by implementing anti counterfeiting measures in terms of overt security features, covert security features and serialization. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Organizational Assets Security Management Strategy Elevating Brand Protection Strategy Guidelines PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Online Security Lock To Prevent Internet Threats Ppt PowerPoint Presentation File Layouts PDF
Presenting online security lock to prevent internet threats ppt powerpoint presentation file layouts pdf to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including online security lock to prevent internet threats. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Types Of Threats In IT Security IT Ppt Summary Graphics Tutorials PDF
This slide depicts the main types of threats in cyber security, such as cybercrime, cyber terrorism, and cyberattacks to an organization and the purpose of each category threat. Presenting types of threats in it security it ppt summary graphics tutorials pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like cyber crime, cyber terrorism, cyber attack. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Pathway Of Change Framework For Food Security And Sustainable Agriculture Clipart PDF
Pitch your topic with ease and precision using this Pathway Of Change Framework For Food Security And Sustainable Agriculture Clipart PDF. This layout presents information on Pathway Change Framework, Food Security Sustainable. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Icon Showcasing Application Of Computer Vision Technologyin Digital Security Sample PDF
Pitch your topic with ease and precision using this Icon Showcasing Application Of Computer Vision Technologyin Digital Security Sample PDF. This layout presents information on Showcasing Application, Computer Vision, Technologyin Digital Security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Email Security Market Research Report Industry Trends Ppt Infographics Styles PDF
Presenting this set of slides with name email security market research report industry trends ppt infographics styles pdf. This is a six stage process. The stages in this process are balance between risk and resilience, supply chain security, security adaptive approach. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Global Cloud Based Email Security Market Industry Trends Ppt Professional Example PDF
Presenting this set of slides with name global cloud based email security market industry trends ppt professional example pdf. This is a six stage process. The stages in this process are balance between risk and resilience, supply chain security, security adaptive approach. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

IT Security Automation Tools Integration Managed Detection And Response Layer For Expert Microsoft PDF
This slide highlights the slide Managed Detection and Response security layer which include alter monitoring, attack investigation, threat hunting, and incident response. This is a IT Security Automation Tools Integration Managed Detection And Response Layer For Expert Microsoft PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Alert Monitoring, Attack Investigation, Threat Hunting, Incident Response. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Agenda For Developing Information Technology Security Awareness Training Program For Employees Elements PDF
Find highly impressive Agenda For Developing Information Technology Security Awareness Training Program For Employees Elements PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Agenda For Developing Information Technology Security Awareness Training Program For Employees Elements PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now

Benefits Of Information Technology Security Ppt PowerPoint Presentation Layouts Layouts PDF
Presenting benefits of information technology security ppt powerpoint presentation layouts layouts pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including evade loss of crucial data, valuable information protection, risk mitigation, recovery time is improved, privacy of customer and employee is ensured, increase productivity by avoiding website to go down. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Analyzing And Protecting Against Cyber Security Attack Ppt Pictures Background Designs PDF
This slide defines the techniques of analyzing and protecting against websites attack. It includes information related to automated scanning, security testing, web application firewalls WAFs and secure development testing SDT. Presenting Analyzing And Protecting Against Cyber Security Attack Ppt Pictures Background Designs PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Web Application Firewalls, Secure Development Testing, Automated Scanning, Security Testing. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Security And Surveillance Company Profile Market Positioning With Technology Mockup PDF
This slide highlights the smart home security company market positioning model on the basis of digital technology and physical service capabilities of organization. Deliver an awe inspiring pitch with this creative Security And Surveillance Company Profile Market Positioning With Technology Mockup PDF bundle. Topics like Monitoring, Bluestone Security, Launched Integrated can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Operations Certifications And Training Courses For IT Professionals Topics PDF
This slide exhibits training courses for security operations administrators to enhance their cyber threat management skills. It includes elements such as course, course outline, rating, pricing, frequency, and mode of training. Showcasing this set of slides titled Security Operations Certifications And Training Courses For IT Professionals Topics PDF. The topics addressed in these templates are Security Operations, Fundamental, Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

5 Benchmarks Visual For Mobile Security Ppt PowerPoint Presentation Gallery Tips PDF
Presenting 5 benchmarks visual for mobile security ppt powerpoint presentation gallery tips pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including 5 benchmarks visual for mobile security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

7 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Mockup PDF
Presenting 7 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Mockup PDF to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including Security Plan, Business Goals, Risk. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

9 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Microsoft PDF
Presenting 9 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Microsoft PDF to dispense important information. This template comprises nine stages. It also presents valuable insights into the topics including Security Plan, Business Goals, Management Program. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

12 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Infographics PDF
Presenting 12 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Infographics PDF to dispense important information. This template comprises tweleve stages. It also presents valuable insights into the topics including Continuously Improve, Business Goals, Security Plan. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Icon For Strategic Plan Roadmap To Improve Cyber Security Clipart PDF
Presenting Icon For Strategic Plan Roadmap To Improve Cyber Security Clipart PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Strategic Plan, Roadmap Improve, Cyber Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Information And Technology Security Operations Various Metrics To Measure Secops System Performance Mockup PDF
This slide portrays information regarding the various metrics that considered in order to assess SecOps system performance such as mean time to detection, mean time to resolution, total cases per month, etc. Presenting information and technology security operations various metrics to measure secops system performance mockup pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security, analyst, escalation, management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Standards And Control Frameworks Ppt PowerPoint Presentation File Icon PDF
This slide provides an overview of the cloud security protocols and control frameworks. The purpose of this slide is to showcase the various information security standards and control frameworks, including ISO-27001, ISO-27017, ISO-27018, GDPR, SOC reporting, PCI DSS, and HIPAA. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Cloud Security Standards And Control Frameworks Ppt PowerPoint Presentation File Icon PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.
 Home
Home