Data Security
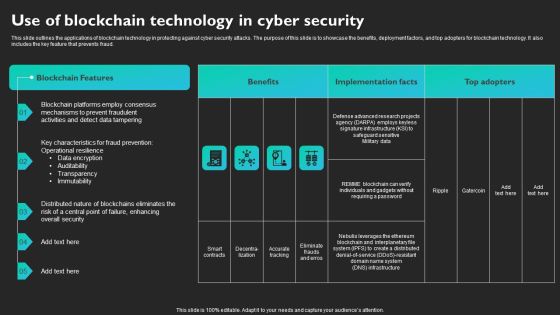
Use Of Blockchain Technology In Cyber Security Slides PDF
This slide outlines the applications of blockchain technology in protecting against cyber security attacks. The purpose of this slide is to showcase the benefits, deployment factors, and top adopters for blockchain technology. It also includes the key feature that prevents fraud. Find a pre-designed and impeccable Use Of Blockchain Technology In Cyber Security Slides PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Cyber Security Incident Response Plan Timeline Inspiration PDF
This slide represents the timeline representing the action plan to effectively respond to cyber security incidents experienced by the organization. It starts with preparation of cyber incident report and ends with return to normal flow. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Cyber Security Incident Response Plan Timeline Inspiration PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Cyber Security Incident Response Plan Timeline Inspiration PDF.

Managing Cyber Security In Manufacturing 30 Days Plan Portrait PDF
This slide describes the first 30 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Are you searching for a Managing Cyber Security In Manufacturing 30 Days Plan Portrait PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Managing Cyber Security In Manufacturing 30 Days Plan Portrait PDF from Slidegeeks today.

5G Network Operations Security In 5G Technology Architecture Template PDF
This slide depicts the security in 5G architecture, including the standards detailed by 3GPP 3rd Generation Partnership Project, such as SUPI, unified authentication, extensible authentication standards, and flexible security policies. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download 5G Network Operations Security In 5G Technology Architecture Template PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the 5G Network Operations Security In 5G Technology Architecture Template PDF.

Comparison Analysis Between Security Operations And Devops Inspiration PDF
This slide summarizes the difference between SecOps and DevOps methodologies that increase the efficiency and scalability of complex operations. It includes parameters such as goal, processing strategy, change implementation, focus on, team involved, etc. Showcasing this set of slides titled Comparison Analysis Between Security Operations And Devops Inspiration PDF. The topics addressed in these templates are Implementation, Processing Strategy, Security Infrastructure. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
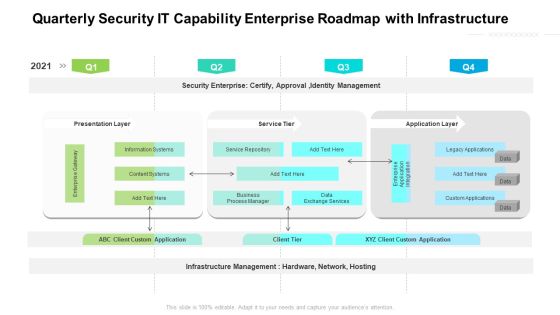
Quarterly Security IT Capability Enterprise Roadmap With Infrastructure Background
Presenting our jaw dropping quarterly security it capability enterprise roadmap with infrastructure background. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
Organizational Network Security Awareness Staff Learning Timeline Download PDF
This is a organizational network security awareness staff learning timeline download pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like timeline, 2018 to 2021. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Home Security Company Services And Contact Information Structure PDF
This slide showcases services provided to insured against losses from insurance company. The services provided are interior and exterior renovation and remodeling, general contracting and new home construction. Showcasing this set of slides titled Home Security Company Services And Contact Information Structure PDF. The topics addressed in these templates are Reimbursement, Contract For Protection, Representing Services Provided. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Damage Security Insurance Proposal Our History Ppt Professional Ideas PDF
This is a damage security insurance proposal our history ppt professional ideas pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like insurance, commercial, businesses, industry. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
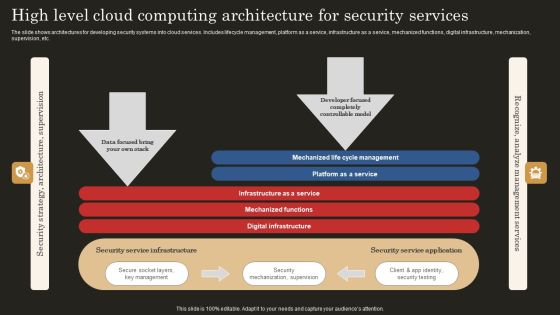
High Level Cloud Computing Architecture For Security Services Ideas PDF
The slide shows architectures for developing security systems into cloud services. Includes lifecycle management, platform as a service, infrastructure as a service, mechanized functions, digital infrastructure, mechanization, supervision, etc. Showcasing this set of slides titled High Level Cloud Computing Architecture For Security Services Ideas PDF. The topics addressed in these templates are Infrastructure Service, Mechanized Functions, Digital Infrastructure. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Organizational Security Solutions Table Of Contents Summary PDF
Deliver an awe inspiring pitch with this creative organizational security solutions table of contents summary pdf bundle. Topics like management, implementation, analysis, technologies can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security And Process Integration Table Of Contents Designs PDF
Deliver an awe inspiring pitch with this creative security and process integration table of contents designs pdf bundle. Topics like management, implementation, analysis, technologies can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Safety And Security Incident Report Writing Tips Pictures PDF
This slide shows tips which can be used to prepare security incident report. These tips are include proof, observe and utilize software. Persuade your audience using this Safety And Security Incident Report Writing Tips Pictures PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Include Proof, Observe, Utilize Software. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Machine To Machine Communication What Is Iot Security Portrait PDF
The slide highlights IoT session layer protocol.This is a machine to machine communication what is iot security portrait pdf. template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like database, command and control center. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Financing Catalogue For Security Underwriting Agreement Timeline Ideas PDF
This is a financing catalogue for security underwriting agreement timeline ideas pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like timeline, 2017 to 2021. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Management Risk And Compliance Model Summary PDF
The following slide presents a GRC model to manage and control cloud cyber security operations and reduce the impact of risk events. It includes key components such as governance, risk and compliance. Showcasing this set of slides titled Cloud Security Management Risk And Compliance Model Summary PDF. The topics addressed in these templates are Governance, Risk, Compliance. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Security Incident Response Process Flow Chart Download PDF
This slide represents the flow chart representing the detection and reaction to cyber security incidents, determination of their scope and risk and reduction of likelihood of incident from reoccurring. It starts with incident declaration and ends with system recovery. This Cyber Security Incident Response Process Flow Chart Download PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
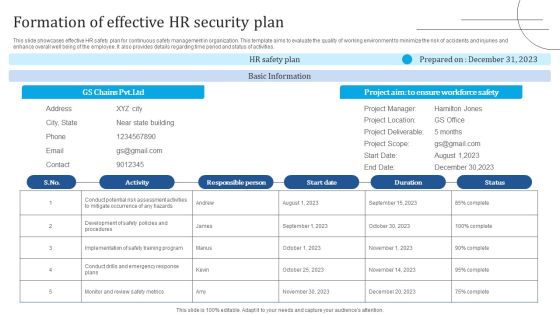
Formation Of Effective HR Security Plan Information PDF
This slide showcases effective HR safety plan for continuous safety management in organization. This template aims to evaluate the quality of working environment to minimize the risk of accidents and injuries and enhance overall well being of the employee. It also provides details regarding time period and status of activities. Presenting Formation Of Effective HR Security Plan Information PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Activity, Responsible Person, Basic Information. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
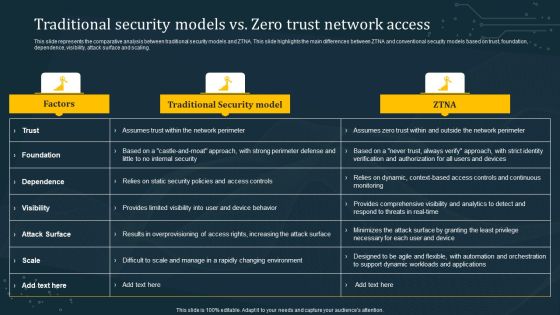
Traditional Security Models Vs Zero Trust Network Access Summary PDF
This slide represents the comparative analysis between traditional security models and ZTNA. This slide highlights the main differences between ZTNA and conventional security models based on trust, foundation, dependence, visibility, attack surface and scaling. This modern and well-arranged Traditional Security Models Vs Zero Trust Network Access Summary PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
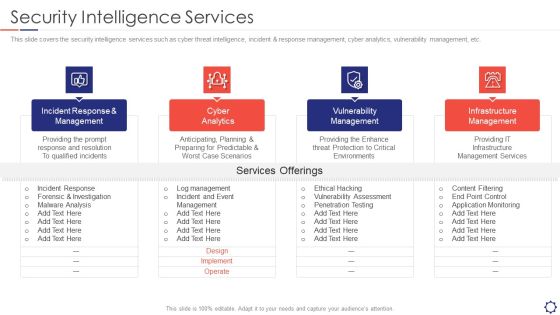
SIEM Security Intelligence Services Ppt Professional Format PDF
This slide covers the security intelligence services such as cyber threat intelligence, incident and response management, cyber analytics, vulnerability management, etc. Presenting siem security intelligence services ppt professional format pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like incident response and management, cyber analytics, vulnerability management, infrastructure management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
File Lock Security Vector Icon Ppt PowerPoint Presentation Infographics Model
This is a file lock security vector icon ppt powerpoint presentation infographics model. This is a one stage process. The stages in this process are computer software, operating system, open source.

Security Analysis And Portfolio Management Ppt PowerPoint Presentation Styles Outfit
This is a security analysis and portfolio management ppt powerpoint presentation styles outfit. This is a four stage process. The stages in this process are mutual funds, funds to buy, investment slide.

Strategic Compliance Safety And Security Management Plan Microsoft PDF
The slide showcases an outline of a plan incorporating compliance strategy that help teams maintain a safe, efficient process, produce quality products and adhere to relevant legal regulations. It covers aspects such as objective, goals, activities, responsible owner, timeframe, status and additional comments. Persuade your audience using this Strategic Compliance Safety And Security Management Plan Microsoft PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Compliance Plan, It Security, Potential. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Role Of Management In Security Governance Across Firm Summary PDF
This slide provides information regarding importance of management in to enable security governance across firm to ensure strategic alignment, risk management, integration, value delivery, resource management, etc. Explore a selection of the finest Role Of Management In Security Governance Across Firm Summary PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Role Of Management In Security Governance Across Firm Summary PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Cyber Security Incident Response Plan Timeline Mockup PDF
This slide represents the timeline representing the action plan to effectively respond to cyber security incidents experienced by the organization. It starts with preparation of cyber incident report and ends with return to normal flow. Make sure to capture your audiences attention in your business displays with our gratis customizable Cyber Security Incident Response Plan Timeline Mockup PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Organizing Security Awareness General Outlook Of Ransomware Attack Structure PDF
The purpose of this slide is to outline an example of ransomware attack. The slide provides information about the working of ransomware attack work and how it can encrypts the victims data. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Organizing Security Awareness General Outlook Of Ransomware Attack Structure PDF can be your best option for delivering a presentation. Represent everything in detail using Organizing Security Awareness General Outlook Of Ransomware Attack Structure PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Effective Digital Security Six Months Strategic Timeline Information
Presenting the effective digital security six months strategic timeline information. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Implementing Cyber Security Incident Enterprise Cyber Risk Dashboard Professional PDF
This slide represents the key metrics dashboard representing details related to management of cyber security incidents by an enterprise. It includes key performance indicators such as risk analysis progress, risk rating breakdown etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Implementing Cyber Security Incident Enterprise Cyber Risk Dashboard Professional PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Implementing Cyber Security Incident Enterprise Cyber Risk Dashboard Professional PDF today and make your presentation stand out from the rest.
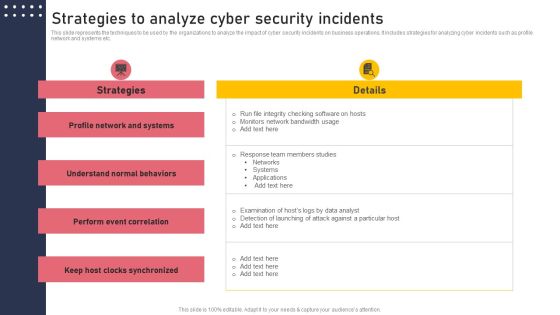
Strategies To Analyze Cyber Security Incidents Structure PDF
This slide represents the techniques to be used by the organizations to analyze the impact of cyber security incidents on business operations. It includes strategies for analyzing cyber incidents such as profile network and systems etc. Find highly impressive Strategies To Analyze Cyber Security Incidents Structure PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Strategies To Analyze Cyber Security Incidents Structure PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
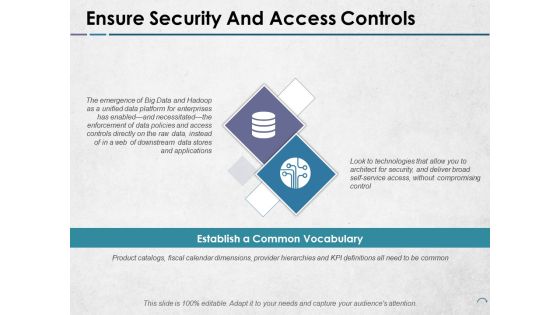
Ensure Security And Access Controls Ppt PowerPoint Presentation Portfolio Images
This is a ensure security and access controls ppt powerpoint presentation portfolio images. This is a two stage process. The stages in this process are icons, strategy, business, management, marketing.

Implementing Cyber Security Awareness Training Program Professional PDF
The purpose of this slide is to delineate a comprehensive security awareness training program that can assist corporates to mitigate cyber attacks and reduce downtime. Information covered in this slide is related to training goals, major topics to cover, and projected result. Make sure to capture your audiences attention in your business displays with our gratis customizable Implementing Cyber Security Awareness Training Program Professional PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Cybersecurity Operations Cybersecops Introduction To Secops Security Operations Introduction PDF
This slide outlines the introduction to security operations. The purpose of this slide is to give an overview of SecOps, including its goals, benefits, and critical functions. The functions include security monitoring, threat intelligence, triage and investigation, incident response, and forensics and root cause analysis. Want to ace your presentation in front of a live audience Our Cybersecurity Operations Cybersecops Introduction To Secops Security Operations Introduction PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Cyber Security Event And Incident Flow Diagram Icons PDF
This slide represents the flow diagram showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It starts with detection of cyber security incident and ends with response to crisis situation. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Cyber Security Event And Incident Flow Diagram Icons PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Vulnerability Assessment And Penetration In Network Security Ppt Powerpoint Slides
This is a vulnerability assessment and penetration in network security ppt powerpoint slides. This is a nine stage process. The stages in this process are mail, maintenance, testing, design, development, database, backup, web, content.

Cyber Security Crisis Management Action Plan Timeline Topics PDF
This slide represents the timeline of effective management and minimization of impact of cyber security incidents on the business of the company. It includes details related to incident response, business continuity and review and recovery. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cyber Security Crisis Management Action Plan Timeline Topics PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cyber Security Crisis Management Action Plan Timeline Topics PDF
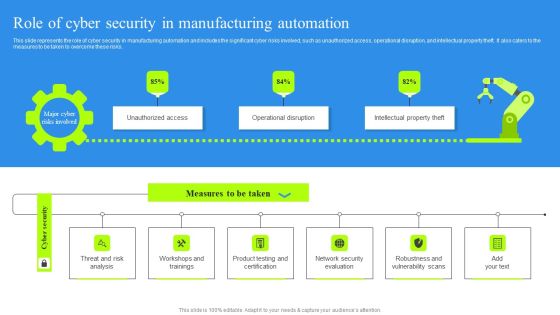
Role Of Cyber Security In Manufacturing Automation Portrait PDF
This slide represents the role of cyber security in manufacturing automation and includes the significant cyber risks involved, such as unauthorized access, operational disruption, and intellectual property theft. It also caters to the measures to be taken to overcome these risks. Find highly impressive Role Of Cyber Security In Manufacturing Automation Portrait PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Role Of Cyber Security In Manufacturing Automation Portrait PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now

Global Peace And Security Ppt PowerPoint Presentation Pictures Structure
This is a global peace and security ppt powerpoint presentation pictures structure. This is a three stage process. The stages in this process are world peace, peace on earth, peaceful environment.

Project Security Administration IT Workplace Employee Assistance Program Structure PDF
The employee assistance program will help firm in enhancing their well being at workplace and enable them to handle critical situations. This program will render services like clinical services, work and life services and employer services, etc. This is a project security administration it workplace employee assistance program structure pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like clinical services, work and life services, employer services. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Operations Compliance And Security Testing Ppt PowerPoint Presentation Summary Icon
This is a operations compliance and security testing ppt powerpoint presentation summary icon. This is a three stage process. The stages in this process are quality assurance, quality analysis, qa, testing process, bugs analysis.

Table Of Contents Food Security Excellence Ppt Model Inspiration PDF
Deliver an awe inspiring pitch with this creative table of contents food security excellence ppt model inspiration pdf bundle. Topics like executive, processing, performance, training, management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Seven Step Ppt PowerPoint Presentation Infographic Template Maker
This is a cyber security seven step ppt powerpoint presentation infographic template maker. This is a seven stage process. The stages in this process are business, management, planning, strategy, marketing.

Major Roles And Responsibilities Of Financial Security Team Sample PDF
The following slide Major roles and responsibilities of financial security department . It includes information about risk level determination, laws and regulations, team training, operational compliance, automatic workflows, red flags, etc. Slidegeeks is here to make your presentations a breeze with Major Roles And Responsibilities Of Financial Security Team Sample PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

IT Security Hacker Purpose Of Hackers Mockup PDF
This slide describes the common types of cybercrime such as identity theft, computer fraud, privacy breach, electronic money laundering, electronic funds transfer, and so on. This is a IT Security Hacker Purpose Of Hackers Mockup PDF template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Identity Theft, Computer Fraud, Privacy Breach. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Management Audits Sample Diagram Ppt Sample Presentations
This is a security management audits sample diagram ppt sample presentations. This is a six stage process. The stages in this process are assets, development, scope, analysis, deploy, replace.

Security Incident Response Plan Template Ppt Design Templates
This is a security incident response plan template ppt design templates. This is a three stage process. The stages in this process are prepare, detection and analysis, post incident activity.

IT Security Hacker Preparation Of Disaster Recovery Plan Template PDF
This slide depicts what factors will be considered while preparing a disaster recovery planning of an organization to come back to business quickly and effectively.This is a IT Security Hacker Preparation Of Disaster Recovery Plan Template PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Natural Disasters, Physical Location, Assessment Report. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Email Security Market Research Report Key Stats Department Topics PDF
Presenting this set of slides with name email security market research report key stats department topics pdf. This is a five stage process. The stages in this process are 95 percent of malware are delivered via e mails, 79 percent of it companies consider phishing most challenging issue. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cloud Computing Application Security Architecture Audit Checklist Structure PDF
The slide shows a checklist containing number of tasks needed to be done while performing application security audit. It includes tasks like developing password policies, making multi factor confirmation mandatory, supervising SaaS license, etc. Showcasing this set of slides titled Cloud Computing Application Security Architecture Audit Checklist Structure PDF. The topics addressed in these templates are Develop Password Policies, Validate Anti Attacking Protections, Set Message Encryption. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Home Security Proposal Form For Insured Elements PDF
The following slide includes proposal form of home insurance for the insured to fulfil the purpose of cover and reimbursement from company against any loss. It includes agents name, number and personal details of proposer. Showcasing this set of slides titled Home Security Proposal Form For Insured Elements PDF. The topics addressed in these templates are Home Security, Proposal Form Insured. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Role Of Management In Security Governance Across Firm Elements PDF
This slide provides information regarding importance of management in to enable security governance across firm to ensure strategic alignment, risk management, integration, value delivery, resource management, etc. Boost your pitch with our creative Role Of Management In Security Governance Across Firm Elements PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Addressing Performance Indicators To Determine Security Standards Introduction PDF
This slide provides information about performance indicators in order to determine security standards at workplace in terms of incidents, offender management, risk assessments. Boost your pitch with our creative Addressing Performance Indicators To Determine Security Standards Introduction PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
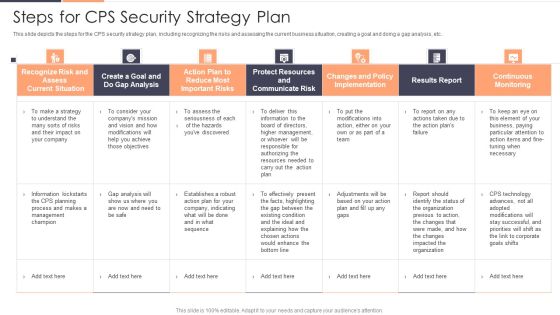
Steps For CPS Security Strategy Plan Ppt Pictures Portfolio PDF
This slide depicts the steps for the CPS security strategy plan, including recognizing the risks and assessing the current business situation, creating a goal and doing a gap analysis, etc. Deliver and pitch your topic in the best possible manner with this Steps For CPS Security Strategy Plan Ppt Pictures Portfolio PDF. Use them to share invaluable insights on Recognize Risk, Communicate Risk, Protect Resources and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
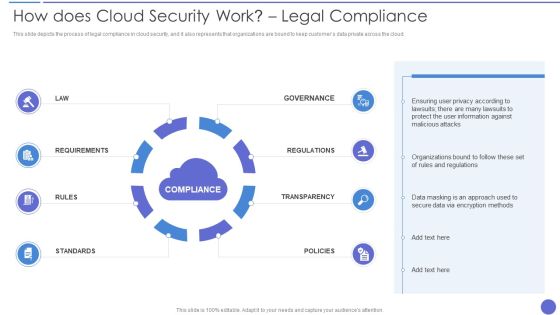
How Does Cloud Security Work Legal Compliance Background PDF
This slide represents the identity and access management in a cloud security system that is based on authentication, authorization, access control, and central user repository. Presenting How Does Cloud Security Work Legal Compliance Background PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Authorization, Authentication, Access Management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Evolution Of Effective Infra Cyber Security Infrastructure Infographics PDF
The following slide showcases evolution of cybersecurity infrastructure with developments in communication strategy. It presents information related to unawareness, reactive, proactive, etc. Presenting Evolution Of Effective Infra Cyber Security Infrastructure Infographics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Unaware, Reactive, Proactive. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
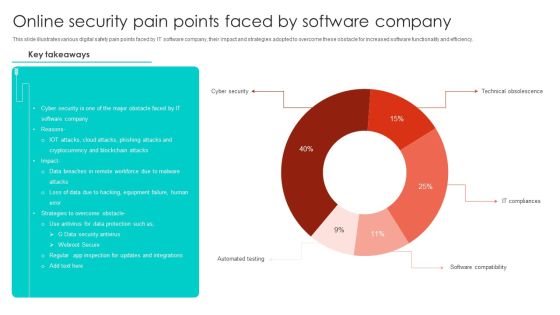
Online Security Pain Points Faced By Software Company Microsoft PDF
This slide illustrates various digital safety pain points faced by IT software company, their impact and strategies adopted to overcome these obstacle for increased software functionality and efficiency. Showcasing this set of slides titled Online Security Pain Points Faced By Software Company Microsoft PDF. The topics addressed in these templates are Cyber Security, Blockchain Attacks, Equipment Failure. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Automated Security Awareness Platform And Cost Graphics PDF
This slide covers the Automated training programs for security awareness that will help educate workers to act appropriately, even when introduced to entirely new risks.Presenting automated security awareness platform and cost graphics pdf. to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like automated learning management, actionable reporting, available anytime. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security And Surveillance Company Profile Business Development Strategy Icons PDF
This slide highlights the security company channel expansion strategy which showcases strategies for retail, multifamily and professional channels including instore lead generation and robust product offerings.Presenting Security And Surveillance Company Profile Business Development Strategy Icons PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Professional Channels, National Operations, Remove Insurance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Agency Business Profile Case Study Elements PDF
This slide highlights the case study of security guard company which includes key problems robberies and theft, with integrated solution and key benefits. Presenting Security Agency Business Profile Case Study Elements PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like The Problem, Solution, Benefits. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Manpower Corporate Security Business Profile Our Business Approach Introduction PDF
This slide highlights the business approach of security company which includes strategic planning, human resource management, participatory management and productivity management. Presenting Manpower Corporate Security Business Profile Our Business Approach Introduction PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Hr Management, Participatory Management, Productivity Management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
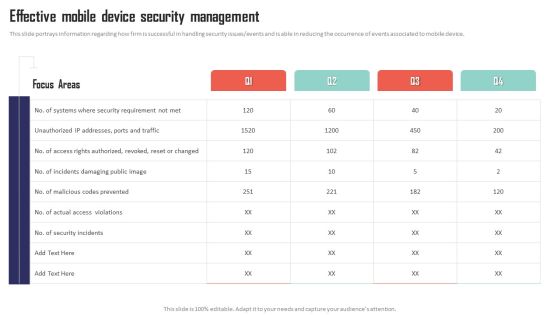
Mobile Device Management Effective Mobile Device Security Management Formats PDF
This slide portrays information regarding how firm is successful in handling security issues or events and is able in reducing the occurrence of events associated to mobile device. Want to ace your presentation in front of a live audience Our Mobile Device Management Effective Mobile Device Security Management Formats PDF can help you do that by engaging all the users towards you.. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

 Home
Home