Data Security

Performance Indicators To Measure Information Security Controls Brochure PDF
Following slide illustrates performance indicators for measuring information security controls. It includes controls details, performance indicator formula, target and periodicity.Deliver an awe inspiring pitch with this creative Performance Indicators To Measure Information Security Controls Brochure PDF bundle. Topics like Information Security, Security Training, Malware Protection can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Security Hacker Interview Schedule For New Professionals Portrait PDF
This slide represents the interview schedule for new employees, including ethical hackers, security consultants, and IT security analysts to be hired to prevent hacking.Deliver and pitch your topic in the best possible manner with this IT Security Hacker Interview Schedule For New Professionals Portrait PDF. Use them to share invaluable insights on Ethical Hacker, Security Consultant, Security Analyst and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
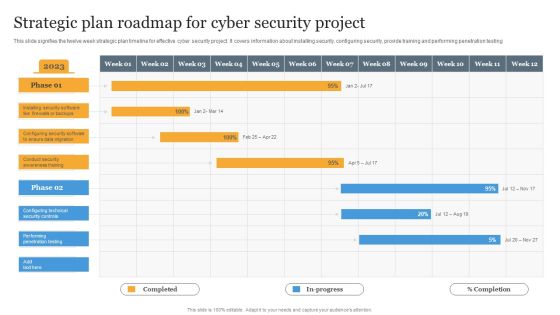
Strategic Plan Roadmap For Cyber Security Project Information PDF
This slide signifies the twelve week strategic plan timeline for effective cyber security project. It covers information about installing security, configuring security, provide training and performing penetration testing Pitch your topic with ease and precision using this Strategic Plan Roadmap For Cyber Security Project Information PDF. This layout presents information on Strategic, Plan, Project. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

IT Security Hacker Ethical Hackers Roles And Responsibilities Background PDF
This slide depicts why organizations recruit ethical hackers, including effective security measures, protecting customer information, raising security awareness, and so on.Deliver and pitch your topic in the best possible manner with this IT Security Hacker Ethical Hackers Roles And Responsibilities Background PDF. Use them to share invaluable insights on Effective Preventative, Information Systems, Security Consciousness and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Information Technology Security KPI Icon With Monitor Pictures PDF
Persuade your audience using this Information Technology Security KPI Icon With Monitor Pictures PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Information Technology, Security KPI, Icon With Monitor. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Information Technology Security Risk Assessment Grid Information PDF
The following slide depicts the analysis of IT security to prevent loss of confidentiality and integrity. The matrix constitutes of elements such as risk, likelihood, its impact and overall threat level. Persuade your audience using this Information Technology Security Risk Assessment Grid Information PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Loss Of Privacy, System Integrity, Loss Of Data. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Example Of Security Testing Services Ppt Powerpoint Guide
This is a example of security testing services ppt powerpoint guide. This is a eight stage process. The stages in this process are security management, access security, application security, networking security, test delivery, results and analysis, technology enablement, test development and publishing.

Information Technology Strategy Cloud Security Architect Skills Scope Background PDF
This slide depicts the cloud security architect skills scope which includes architecture and strategy, leadership, operational technical, etc. Deliver an awe inspiring pitch with this creative information technology strategy cloud security architect skills scope background pdf bundle. Topics like architecture and strategy, technical, leadership, operational can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Google Cloud Services Identity And Security Graphics PDF
This slide describes the identity and security service of google cloud, and it includes cloud resource manager, cloud IAM, cloud security scanner, and cloud platform security. This is a Google Cloud Services Identity And Security Graphics PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Cloud Resource Manager, Cloud Security Scanner, Cloud Platform Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Security Management And Management Program Framework Inspiration PDF
This slide showcases a framework of information security governance and management to develop business specific risk control program. It includes key components such as identify security, infrastructure security, HR security, detection, response and recovery, measurement, etc. Showcasing this set of slides titled Information Security Management And Management Program Framework Inspiration PDF. The topics addressed in these templates are Governance, Management, Key Insights All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Security Domains That Will Be Addressed By ISMS Diagrams PDF
This slide portrays different security domains that will be addressed by ISMS. Domains covered are security policy, asset management, physical and environmental security, cryptography and human resource security.This is a Security Domains That Will Be Addressed By ISMS Diagrams PDF template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Management Support, Resources Security, Prevention Of Unauthorized. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
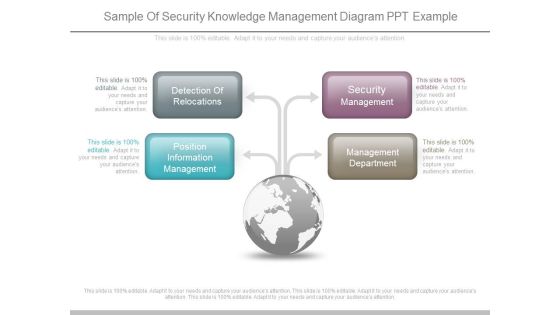
Sample Of Security Knowledge Management Diagram Ppt Example
This is a sample of security knowledge management diagram ppt example. This is a four stage process. The stages in this process are detection of relocations, position information management, security management, management department.

Quarterly Enterprise Information Technology Security Roadmap Through Identification Topics
We present our quarterly enterprise information technology security roadmap through identification topics. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched quarterly enterprise information technology security roadmap through identification topics in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Cloud Computing Security Ppt Portfolio Background Images PDF
Presenting cloud computing security ppt portfolio background images pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like security dimensions, customers, security categories. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Icon Of Computer IT Security Program For Protection Background PDF
Presenting Icon Of Computer IT Security Program For Protection Background PDF to dispense important information. This template comprises one stage. It also presents valuable insights into the topics including Icon Computer, It Security, Program Protection This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Current Security Management Plan Critical Success Factors Guidelines PDF
This slide shows some of the current IT Security Management Critical Success Factors of the company prior to the proactive measures taken by the company to mitigate security management problems and implementing an advanced Information Security Management System. Deliver and pitch your topic in the best possible manner with this current security management plan critical success factors guidelines pdf. Use them to share invaluable insights on security incidents level, security related service downtimes, intrusion attempts and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Current Security Management Plan Critical Success Factors Infographics PDF
This slide shows some of the current IT Security Management Critical Success Factors of the company prior to the proactive measures taken by the company to mitigate security management problems and implementing an advanced Information Security Management System.Deliver an awe inspiring pitch with this creative Current security management plan critical success factors infographics pdf bundle. Topics like security incidents level, security management, critical success factors can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Current Security Management Plan Critical Success Factors Topics PDF
This slide shows some of the current IT Security Management Critical Success Factors of the company prior to the proactive measures taken by the company to mitigate security management problems and implementing an advanced Information Security Management System.Deliver an awe inspiring pitch with this creative current security management plan critical success factors topics pdf bundle. Topics like security management, intrusion attempts, security implementation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Table Of Contents For Cloud Security Assessment Cont Background PDF
This is a Table Of Contents For Cloud Security Assessment Cont Background PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Cloud Security, Security Responsibilities, Security Management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity Security Of Employees Devices Ppt Styles Graphic Images PDF
This slide depicts that the security of employees hardware or devices is also essential while applying the cyber security model. This is a cybersecurity security of employees devices ppt styles graphic images pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security of employees devices. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Service Assessment Icon To Track Network Security Information PDF
Persuade your audience using this Service Assessment Icon To Track Network Security Information PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Service Assessment Icon To Track Network Security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Functional Technology Icon For Security Threat Detection Structure PDF
Presenting functional technology icon for security threat detection structure pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including functional technology icon for security threat detection. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cloud Deployment Security Management Technology Icon Topics PDF
Presenting Cloud Deployment Security Management Technology Icon Topics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Cloud Deployment Security, Management Technology Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Mobile Application Security Management Technology Icon Structure PDF
Presenting Mobile Application Security Management Technology Icon Structure PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Mobile Application Security, Management Technology Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Motion Smart Sensor Technology For Security Improvement Icon Mockup PDF
Presenting Motion Smart Sensor Technology For Security Improvement Icon Mockup PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Motion Smart, Sensor Technology, Security Improvement. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
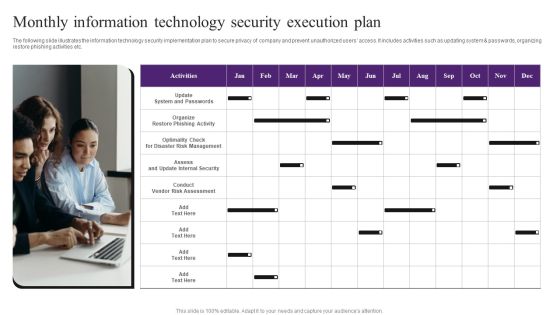
Monthly Information Technology Security Execution Plan Template PDF
The following slide illustrates the information technology security implementation plan to secure privacy of company and prevent unauthorized users access. It includes activities such as updating system and passwords, organizing restore phishing activities etc. Presenting Monthly Information Technology Security Execution Plan Template PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Update System And Passwords, Conduct Vendor Risk Assessment, Risk Management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
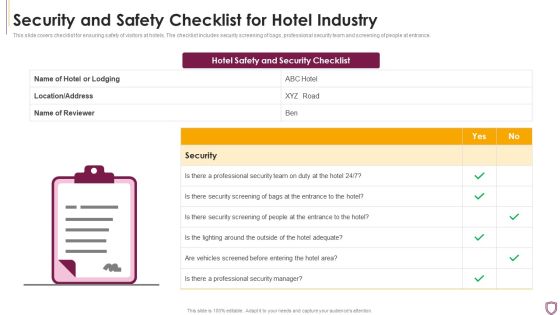
Security And Safety Checklist For Hotel Industry Summary PDF
This slide covers checklist for ensuring safety of visitors at hotels. The checklist includes security screening of bags, professional security team and screening of people at entrance.Showcasing this set of slides titled Security And Safety Checklist For Hotel Industry Summary PDF The topics addressed in these templates are Professional Security, Security Screening, Vehicles Screened All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Steps To Deploy People Centric Work Culture Security Background PDF
The following slide showcases steps to enforce human centric security system to empower employees in handling useful information. It includes elements such as establishing environment for people centric security PCS, promoting culture of cyber security, etc. Presenting Steps To Deploy People Centric Work Culture Security Background PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Converting Cybersecurity, Punishment System, Protection Practices. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Electronic Banking Security Icon With Dollar Sign Information PDF
Persuade your audience using this Electronic Banking Security Icon With Dollar Sign Information PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Electronic Banking Security Icon, Dollar Sign. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Information Technology Security Threat And Weakness Analysis Diagrams PDF
The following slide highlights the IT security assessment to verify the safety status of assets and networks. It includes elements such as threats, weakness, impact and level of risk, current and proposed controls etc. Persuade your audience using this Information Technology Security Threat And Weakness Analysis Diagrams PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Risk, Network Systems, Data. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Security Technology Ppt PowerPoint Presentation File Template Cpb
This is a cyber security technology ppt powerpoint presentation file template cpb. This is a six stage process. The stages in this process are cyber security technology.

Five Elements Of Cloud Services Security Brochure PDF
This slide includes elements of cloud computing security to assure network protection and efficient management. It contains five elements architecture, security, due diligence, authentication, monitor and visibility.Presenting Five Elements Of Cloud Services Security Brochure PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Security Coverage, Intrusion Detection, Computing Regulations. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Types Information Security Ppt PowerPoint Presentation Outline Clipart Cpb
Presenting this set of slides with name types information security ppt powerpoint presentation outline clipart cpb. This is an editable Powerpoint four stages graphic that deals with topics like types information security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Icons Slide For IT Security Ppt Icon Graphics Tutorials PDF
Deliver an awe inspiring pitch with this creative icons slide for information technology security ppt professional slideshow pdf bundle. Topics like icons slide for it security ppt icon graphics tutorials pdf can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Enterprise Security Tools Ppt PowerPoint Presentation Infographics Skills Cpb
This is a enterprise security tools ppt powerpoint presentation infographics skills cpb. This is a four stage process. The stages in this process are enterprise security tools.

Measures And Ways To Mitigate Security Management Challenges Background PDF
This slide provides information about the ways and measures through which the company and IT security managers can overcome the problems and issues related to Security Management. Deliver an awe inspiring pitch with this creative measures and ways to mitigate security management challenges background pdf bundle. Topics like potential insider threats, external security breaches, weak links in the supply chain can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
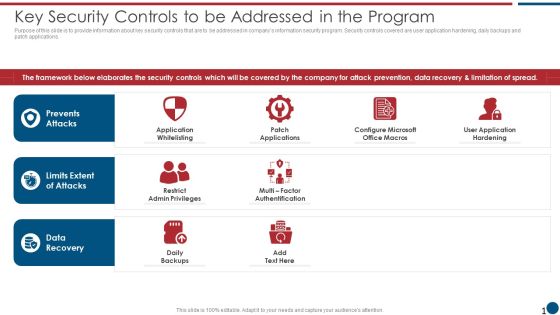
Risk Based Procedures To IT Security Key Security Controls To Be Addressed In The Program Structure PDF
Purpose of this slide is to provide information about key security controls that are to be addressed in companys information security program. Security controls covered are user application hardening, daily backups and patch applications. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Key Security Controls To Be Addressed In The Program Structure PDF bundle. Topics like Prevents Attacks, Limits Extent, Data Recovery can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
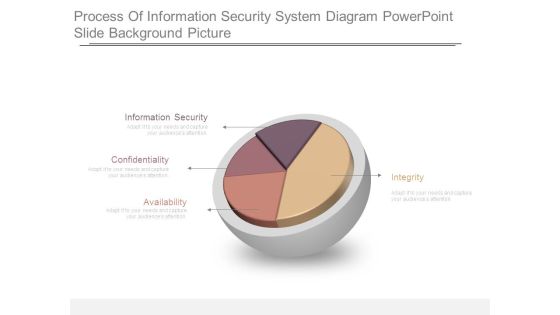
Process Of Information Security System Diagram Powerpoint Slide Background Picture
This is a process of information security system diagram powerpoint slide background picture. This is a four stage process. The stages in this process are information security, confidentiality, availability, integrity.

IT Security Defense Plan Maturity Evaluation Information PDF
This slide represents cyber security defense strategy maturity evaluation mode illustrating culture and organization, governance, visibility and controls, focused defense and intelligence operations. Persuade your audience using this IT Security Defense Plan Maturity Evaluation Information PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Organization, Focused Defense, Intelligence Operations. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Internet Security Threat Icon On Computer Elements PDF
Presenting internet security threat icon on computer elements pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including internet security threat icon on computer. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
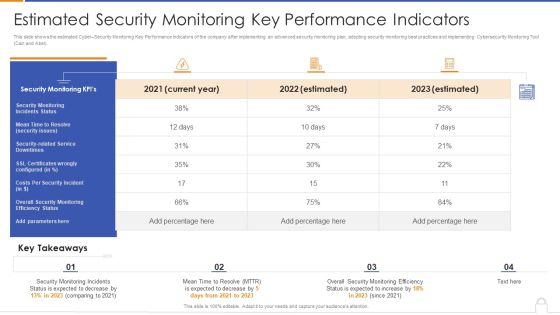
Estimated Security Monitoring Key Performance Indicators Diagrams PDF
Deliver and pitch your topic in the best possible manner with this estimated security monitoring key performance indicators diagrams pdf. Use them to share invaluable insights on security monitoring, security related service downtimes, overall security monitoring and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Business Cyber Security Assessment Protection Icon Ideas PDF
Presenting Business Cyber Security Assessment Protection Icon Ideas PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Protection Icon, Business Cyber Security Assessment. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Information Technology Security Threat Mitigation Strategies Formats PDF
The slide covers strategies to prevent IT security threats for reducing overall impact of risks or attacks on business. It includes four strategies such as risk assessment, network access control, incident response plan and regular network traffic monitoring. Persuade your audience using this Information Technology Security Threat Mitigation Strategies Formats PDF. This PPT design covers Four stages, thus making it a great tool to use. It also caters to a variety of topics including Risk Assessment, Network Access Controls, Incident Response Plan. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Icon For Implementation Of Complete Digital Security Network Professional PDF
Presenting Icon For Implementation Of Complete Digital Security Network Professional PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Icon For Implementation, Complete Digital Security Network. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
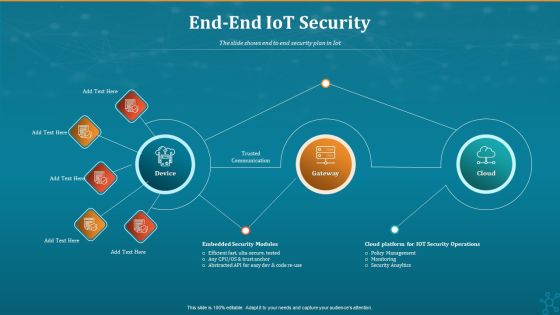
Machine To Machine Communication End End Iot Security Inspiration PDF
The slide shows end to end security plan in Iot.Deliver an awe-inspiring pitch with this creative machine to machine communication end end iot security inspiration pdf. bundle. Topics like trusted communication, gateway, embedded security modules, cloud platform for iot security operations can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Estimated Security Management Plan Critical Success Factors Infographics PDF
Deliver an awe inspiring pitch with this creative Estimated security management plan critical success factors infographics pdf bundle. Topics like security management, security incidents level, security implementation duration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Current Security Monitoring Key Performance Indicators Formats PDF
Deliver and pitch your topic in the best possible manner with this current security monitoring key performance indicators formats pdf. Use them to share invaluable insights on security monitoring incidents, overall security monitoring, costs per security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Communication Plan For Information Technology Asset Security Threats Pictures PDF
This slide consists of a communication plan that can be implemented by managers to safeguard information technology assets from cyber threats and create an effective response plan. Major elements covered are IT security assets, risk, threat, risk impact, etc. Showcasing this set of slides titled Communication Plan For Information Technology Asset Security Threats Pictures PDF. The topics addressed in these templates are ZZZZZZZZZZZZZZZZZZZZIT Servers, Network Systems, ModemZZZZZZZZZZZZZ. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Wireless Network Security System Icon For Car Insurance Professional PDF
Presenting wireless network security system icon for car insurance professional pdf to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including wireless network security system icon for car insurance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Digital Cloud Network Cyber Security Icon Clipart PDF
Presenting Digital Cloud Network Cyber Security Icon Clipart PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Digital Cloud, Network Cyber, Security Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
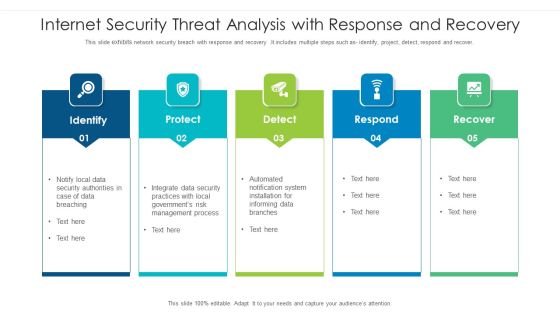
Internet Security Threat Analysis With Response And Recovery Information PDF
This slide exhibits network security breach with response and recovery .It includes multiple steps such as- identify, project, detect, respond and recover. Pitch your topic with ease and precision using this internet security threat analysis with response and recovery information pdf. This layout presents information on internet security threat analysis with response and recovery. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Information Technology Communication Plan For Cyber Security Attack Summary PDF
This slide consists of an information technology communication plan that can be implemented by managers to safeguard from cyber security attacks and create an effective response plan. Major cyber attack elements covered are malware, phishing, ransomware, etc. Presenting Information Technology Communication Plan For Cyber Security Attack Summary PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Incident Reporting Response, Prevention Measures, Incident Reporting. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cloud Computing Safety And Security Architecture Icon Download PDF
Presenting Cloud Computing Safety And Security Architecture Icon Download PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Cloud Computing Safety, Security Architecture Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Information Technology Security Communication Channel Selection Plan Template PDF
Following slide consists of a matrix for selecting information technology security communication channels in order to ensure the seamless delivery of key messages to relevant stakeholders. Key content types are detailed messages, notifications, community feeds, documents, etc. Presenting Information Technology Security Communication Channel Selection Plan Template PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Detailed Message, Notifications, Community Feed. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Six Practices For IT Security Management Program Microsoft PDF
This slide shows the best practices for security management program which includes essential tasks such as risk analysis and identification, manage risk, threat and issues, security consolidation procedure, etc. With assigned owner and frequency.Presenting Six Practices For IT Security Management Program Microsoft PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Analysis Prioritization, Consolidation Procedure, Strategic Initiatives This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Information Technology Security Crisis Communication Plan Checklist Professional PDF
Following slide presents an information technology security crisis communication plan checklist that can be used by information technology managers to ensure the effective preparation of a communication plan. Key elements covered in the checklist are identifying office protocol, creating a list of IT terms, etc. Presenting Information Technology Security Crisis Communication Plan Checklist Professional PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Communications Team, Internal Communication Plan, Dissemination Information. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Security Operations Center Vector Icon Ppt Pictures Shapes PDF
Presenting cyber security operations center vector icon ppt pictures shapes pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including cyber security operations center vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Digital Coverage Policy Icon With Cyber Security Template PDF
Presenting Digital Coverage Policy Icon With Cyber Security Template PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Digital Coverage, Policy Icon, Cyber Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Pin Enabled Smart Phone Security Icon Elements PDF
Presenting Pin Enabled Smart Phone Security Icon Elements PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including PIN Enabled, Smart Phone, Security Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Infra Cyber Security Icon For Eliminating Cyber Threats Designs PDF
Presenting Infra Cyber Security Icon For Eliminating Cyber Threats Designs PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Infra Cyber Security Icon, Eliminating Cyber Threats. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

 Home
Home