Data Security

Implementing Smart Manufacturing Technology To Increase Productivity Major Impact Of Smart Factory On Enterprises Elements PDF
This slide represents major impacts of smart factory. It includes production process monitoring, asset visibility, data analysis and employee and asset security. Welcome to our selection of the Implementing Smart Manufacturing Technology To Increase Productivity Major Impact Of Smart Factory On Enterprises Elements PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

Steps For Information System Network And Communication Auditing Topics PDF
The following slide highlights the steps for information system network and communication audit illustrating key headings which includes basic network security, internet security, email security, cyber attack security, security patch and wireless security Presenting Steps For Information System Network And Communication Auditing Topics PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Basic Network Security, Internet Security, Security Patch. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully
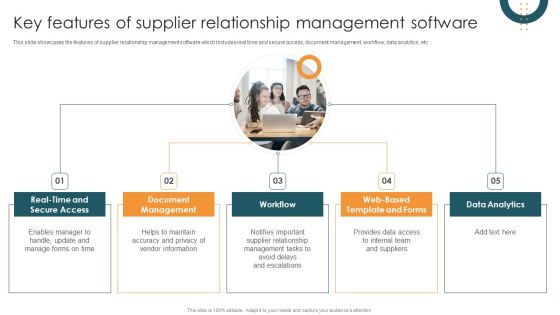
Vendor Relation Management Techniques Key Features Of Supplier Relationship Management Software Download PDF
This slide showcases the features of supplier relationship management software which includes real time and secure access, document management, workflow, data analytics, etc. Do you know about Slidesgeeks Vendor Relation Management Techniques Key Features Of Supplier Relationship Management Software Download PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
Systematic Concentric Process Diagram Business Plan Outline PowerPoint Templates
We present our systematic concentric process diagram business plan outline PowerPoint templates.Use our Process and Flows PowerPoint Templates because Our PowerPoint Templates and Slides will Embellish your thoughts. They will help you illustrate the brilliance of your ideas. Use our Network Diagrams PowerPoint Templates because Our PowerPoint Templates and Slides will generate and maintain the level of interest you desire. They will create the impression you want to imprint on your audience. Download our Shapes PowerPoint Templates because Your success is our commitment. Our PowerPoint Templates and Slides will ensure you reach your goal. Download and present our Business PowerPoint Templates because It can Bubble and burst with your ideas. Use our Marketing PowerPoint Templates because Our PowerPoint Templates and Slides ensures Effective communication. They help you put across your views with precision and clarity.Use these PowerPoint slides for presentations relating to Login, cyber, radar, protocol, elimination, secure, corporate, future, concept, lan, infrastructure, data, process, scan, viral, technology, security, wan, abstract,creative, illustration, system, up, focus, terrorism, futuristic, recognition, precaution, check, processing, zoom, information, background, virus, conceptual,precautionary, pattern, systematic, measure. The prominent colors used in the PowerPoint template are Blue, Blue light, White.

Cloud Computing Technology For Healthcare Industry Topics PDF
The following slide highlights the alignment of cloud computing technology and medical industry which provides high data availability by transforming healthcare domain. Key components are collaboration, security, cost, speed and scalability. Presenting Cloud Computing Technology For Healthcare Industry Topics PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Healthcare Stakeholders, Remote Medical Reports, Mechanism Against. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
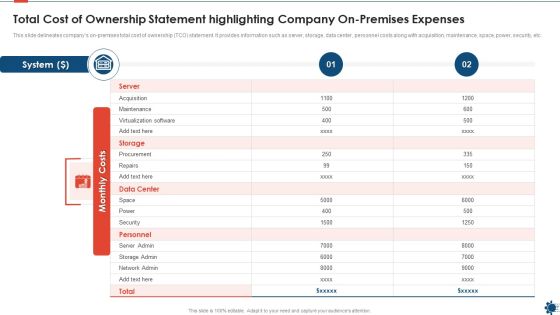
Total Cost Of Ownership Statement Highlighting Company On Premises Expenses Professional PDF
This slide delineates companys on premises total cost of ownership TCO statement. It provides information such as server, storage, data center, personnel costs along with acquisition, maintenance, space, power, security, etc. Showcasing this set of slides titled total cost of ownership statement highlighting company on premises expenses professional pdf. The topics addressed in these templates are total cost of ownership statement highlighting company on premises expenses. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Stock Photo 3d Combination Lock For Safety Image Graphics For PowerPoint Slide
This image slide has been crafted with graphic of combination lock on database icon. This image explains the concept of security. Define total security concept with this exclusive image. Use this image slide for business and security related presentations.
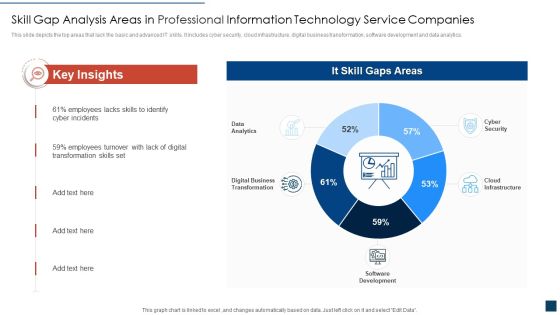
Skill Gap Analysis Areas In Professional Information Technology Service Companies Ideas PDF
This slide depicts the top areas that lack the basic and advanced IT skills. It includes cyber security, cloud infrastructure, digital business transformation, software development and data analytics. Showcasing this set of slides titled skill gap analysis areas in professional information technology service companies ideas pdf. The topics addressed in these templates are skill gap analysis areas in professional information technology service companies. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Determinants Of Product Quality Ppt PowerPoint Presentation Infographic Template Files
This is a determinants of product quality ppt powerpoint presentation infographic template files. This is a seven stage process. The stages in this process are performance, reliability, durability, evaluation, safety.

Cybersecurity Risk Administration Plan Framework Ideas PDF
This slide showcases a cyber security risk management framework to increase system capability to protect, detect and react under uncertain security threats. It includes steps such as categorize system, select security control, apply security controls, evaluate security controls, etc. Presenting Cybersecurity Risk Administration Plan Framework Ideas PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Categorise System, Select Security Controls, Apply Security Controls. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Convergence Strategy Information IT OT Team Responsibilities Based On Target Slides PDF
This slide covers IT or OT cyber security Team responsibilities including security department, security functions etc. Deliver an awe inspiring pitch with this creative Convergence Strategy Information IT OT Team Responsibilities Based On Target Slides PDF bundle. Topics like OT Security Functions, Security Architecture And Engineering, Primary Responsibility, Shared Responsibility can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

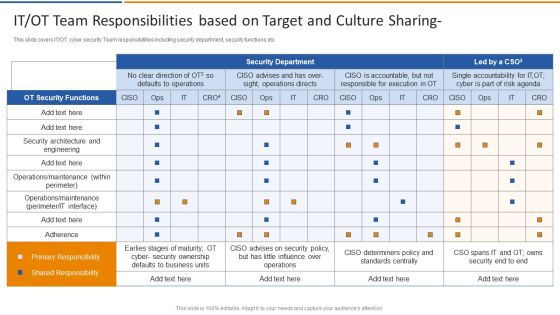
Digitalization Of Operative Enterprises IT OT Team Responsibilities Based On Target And Culture Sharing Microsoft PDF
This slide covers IT or OT cyber security team responsibilities including security department, security functions etc. Deliver and pitch your topic in the best possible manner with this Digitalization Of Operative Enterprises IT OT Team Responsibilities Based On Target And Culture Sharing Microsoft PDF. Use them to share invaluable insights on Security Functions, Security Ownership, Determiners and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Smart Venture Digitial Transformation IT OT Team Responsibilities Based On Target Structure PDF
This slide covers IT or OT cyber security Team responsibilities including security department, security functions etc. Deliver an awe inspiring pitch with this creative Smart Venture Digitial Transformation IT OT Team Responsibilities Based On Target Structure PDF bundle. Topics like OT Security Functions, Security architecture, Primary Responsibility can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

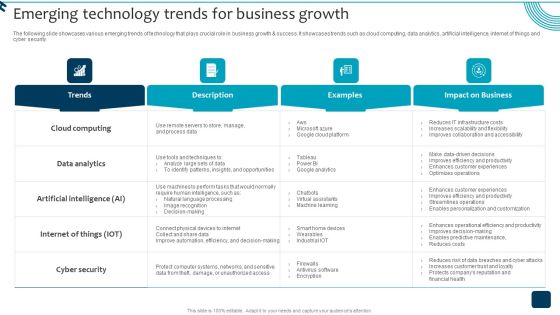
Emerging Technology Trends For Business Growth Diagrams PDF
The following slide showcases various emerging trends of technology that plays crucial role in business growth and success. It showcases trends such as cloud computing, data analytics, artificial intelligence, internet of things and cyber security. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Emerging Technology Trends For Business Growth Diagrams PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Emerging Technology Trends For Business Growth Diagrams PDF.

Designing Strategies For Company Growth And Success Emerging Technology Trends For Business Growth Introduction PDF
The following slide showcases various emerging trends of technology that plays crucial role in business growth and success. It showcases trends such as cloud computing, data analytics, artificial intelligence, internet of things and cyber security. This Designing Strategies For Company Growth And Success Emerging Technology Trends For Business Growth Introduction PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Designing Strategies For Company Growth And Success Emerging Technology Trends For Business Growth Introduction PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
Strategic Brand Growth Plan For Market Leadership Emerging Technology Trends For Business Background PDF
The following slide showcases various emerging trends of technology that plays crucial role in business growth and success. It showcases trends such as cloud computing, data analytics, artificial intelligence, internet of things and cyber security. Do you know about Slidesgeeks Strategic Brand Growth Plan For Market Leadership Emerging Technology Trends For Business Background PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

Business Information Protection Methodologies For Organizational Facilities Demonstration PDF
This slide covers business security methodologies for organizational facilities which are security plan documentation, access control, installing surveillance system and reinforce data security.Presenting Business Information Protection Methodologies For Organizational Facilities Demonstration PDF to dispense important information. This template comprises one stage. It also presents valuable insights into the topics including Plan Documentation, Implement Access, Surveillance System. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
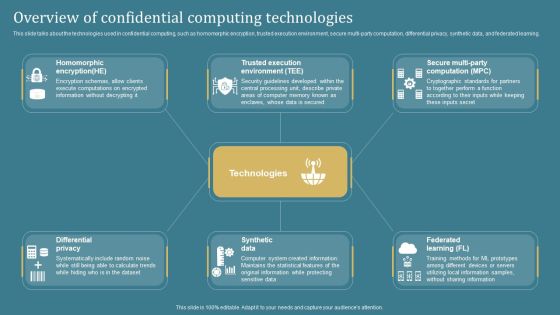
Overview Of Confidential Computing Confidential Computing System Technology Portrait PDF
This slide talks about the technologies used in confidential computing, such as homomorphic encryption, trusted execution environment, secure multi-party computation, differential privacy, synthetic data, and federated learning. Welcome to our selection of the Overview Of Confidential Computing Confidential Computing System Technology Portrait PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

Top To Down Approach For Business Information Protection Demonstration PDF
This slide covers top to down approach for business security which includes security leadership, program, policies and management. Further, it includes user management and information asset security.Pitch your topic with ease and precision using this Top To Down Approach For Business Information Protection Demonstration PDF. This layout presents information on Security Leadership, Security Program, Security Policies. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Smart Venture Digitial Transformation Single Database For Two Separate IT OT Socs Inspiration PDF
This slide covers single database structure for two IT or OT socs including network security, multi cloud security, security operations , open ecosystems etc. Presenting Smart Venture Digitial Transformation Single Database For Two Separate IT OT Socs Inspiration PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Network Security, Multi Cloud Security, Device Access, Application Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Five Steps Risk Management Process Of Insurance Process Mockup PDF
This slide show the risk management process which can be used by banking insurance company. It includes information security program, security codes, cyber security and training. Pitch your topic with ease and precision using this Five Steps Risk Management Process Of Insurance Process Mockup PDF. This layout presents information on Information Security Program, Security Codes, Cyber Security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

E Commerce Circle Examples Ppt Powerpoint Slides
This is a e commerce circle examples ppt powerpoint slides. This is a seven stage process. The stages in this process are business e commerce, security services, web hosting, shopping cart, web design, merchant processing, online marketing, data storage.
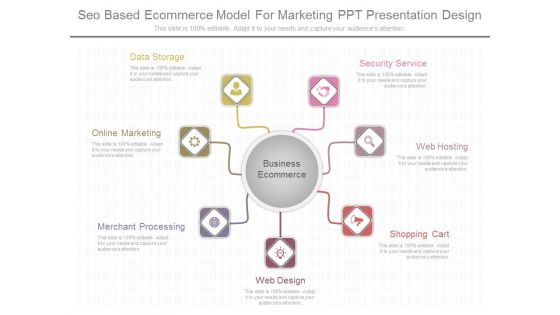
Seo Based Ecommerce Model For Marketing Ppt Presentation Design
This is a seo based ecommerce model for marketing ppt presentation design. This is a seven stage process. The stages in this process are security service, web hosting, shopping cart, web design, merchant processing, online marketing, data storage.

Cashless Payment Strategies To Enhance Business Performance Impact Assessment Of Mobile Wallet Application Professional PDF
Mentioned slide provides information about mobile wallet payment implementation impact on business activities. It includes impacts such as easy customer data analytics, offer reward and loyalty points, smooth workflow, and improved security. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cashless Payment Strategies To Enhance Business Performance Impact Assessment Of Mobile Wallet Application Professional PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cashless Payment Strategies To Enhance Business Performance Impact Assessment Of Mobile Wallet Application Professional PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers

Quarterly Cybersecurity Training Program And Schedule Timeline Rules PDF
This slide covers the roadmap for various courses in security awareness programs. It includes cyber system management, password security program, insider threats program, e mail security program.Presenting Quarterly Cybersecurity Training Program And Schedule Timeline Rules PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Risk Assessment, Security Program, Threats Program. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
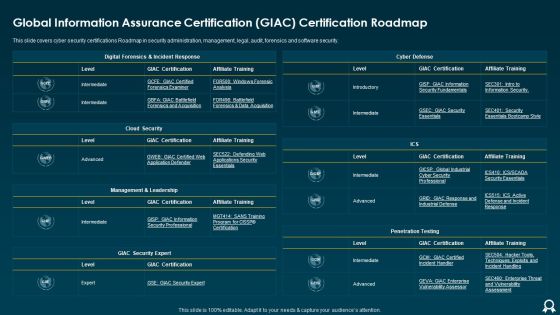
Global Information Assurance Certification GIAC Certification Roadmap Formats PDF
This slide covers cyber security certifications Roadmap in security administration, management, legal, audit, forensics and software security. Deliver an awe inspiring pitch with this creative Global Information Assurance Certification GIAC Certification Roadmap Formats PDF bundle. Topics like Cloud Security, Cyber Defense, Management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
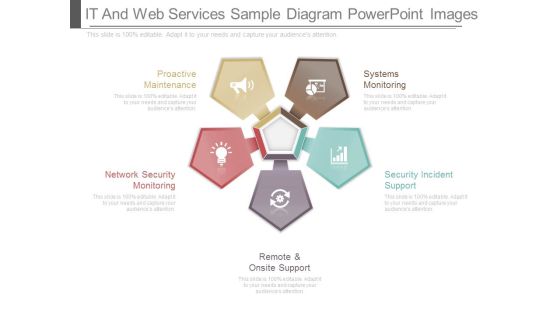
It And Web Services Sample Diagram Powerpoint Images
This is a it and web services sample diagram powerpoint images. This is a five stage process. The stages in this process are systems monitoring, security incident support, remote and onsite support, network security monitoring, proactive maintenance.

Info Sphere Streams Streaming Computing Example Of Ppt
This is a info sphere streams streaming computing example of ppt. This is a four stage process. The stages in this process are security directory server, security access, streaming computing, info sphere streams.

Stock Photo Blue Umbrella Over Usa Flag Print Text PowerPoint Slide
This Power Point slide has been designed with graphic of blue umbrella and US flag design. This image slide contains the concept of USA security and protection schemes. Use this professional design to build presentation for security related topics.

Profile Monitoring Methodology Sample Diagram Sample Ppt Presentation
This is a profile monitoring methodology sample diagram sample ppt presentation. This is a five stage process. The stages in this process are macro analysis, security screening, gaussian kernel, security screening, sector and asset class focus.

Cyber Exploitation IT Interview Schedule For New Professionals Icons PDF
This slide represents the interview schedule for new employees, including ethical hackers, security consultants, and IT security analysts to be hired to prevent hacking. Deliver and pitch your topic in the best possible manner with this cyber exploitation it interview schedule for new professionals icons pdf. Use them to share invaluable insights on it security analyst, certified ethical hacker, security consultant and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT OT Team Responsibilities Based On Target Managing Organizational Transformation Microsoft PDF
This slide covers IT OT cyber security Team responsibilities including security department, security functions etc. Deliver an awe inspiring pitch with this creative IT OT Team Responsibilities Based On Target Managing Organizational Transformation Microsoft PDF bundle. Topics like Security Department, Team Responsibilities, Target can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
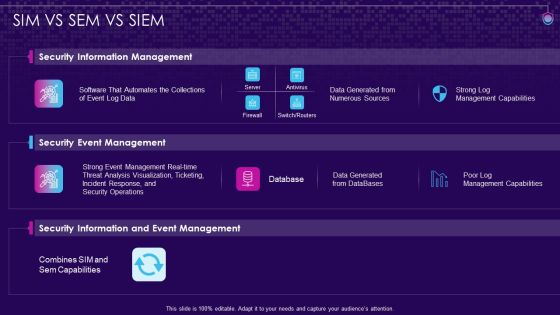
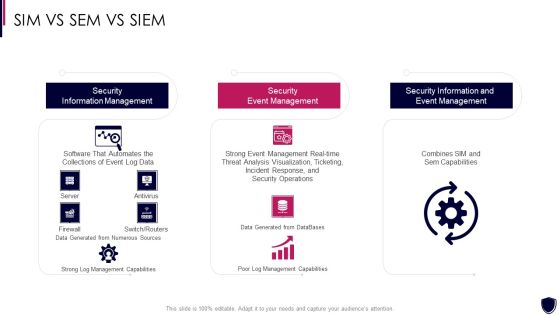
SIM VS SEM VS SIEM SIEM Services Ppt Show Slides PDF
Deliver and pitch your topic in the best possible manner with this sim vs sem vs siem siem services ppt show slides pdf. Use them to share invaluable insights on security information management, security event management, security information and event management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Risk Recognition Automation Sim Vs Sem Vs Siem Ppt Professional Background Designs PDF
Deliver and pitch your topic in the best possible manner with this risk recognition automation sim vs sem vs siem ppt professional background designs pdf. Use them to share invaluable insights on security information management, security event management, security information and event management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Table Of Contents Ppt Inspiration Guide PDF
Deliver an awe inspiring pitch with this creative table of contents ppt inspiration guide pdf bundle. Topics like security awareness program, security strategies, budget, communication plan, security awareness, cost can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Risk Control Strategies Risk Management Framework Mockup PDF
This slide shows the framework for information technology risk management which includes cyber security governance, IT and security risk assessment, training and awareness, security operation centre, independent audit and gap analysis. Persuade your audience using this IT Risk Control Strategies Risk Management Framework Mockup PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Security Governance, IT Risk Assessment, Security Assessment. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
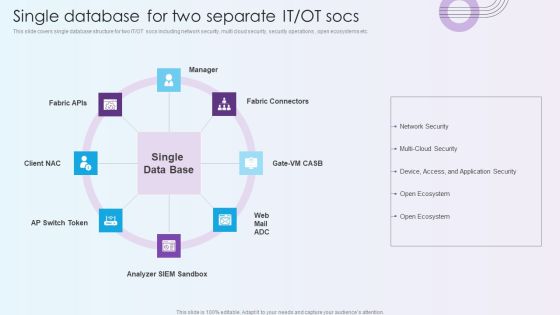
Digitalization Of Operative Enterprises Single Database For Two Separate IT OT Socs Structure PDF
This slide covers single database structure for two IT or OT socs including network security, multi cloud security, security operations , open ecosystems etc.This is a Digitalization Of Operative Enterprises Single Database For Two Separate IT OT Socs Structure PDF template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Analyzer, Network Security, Multi Cloud Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Five Steps Insurance Risk Management Procedure Professional PDF
This slide show the risk management process of an insurance company. It includes information security program, security codes, cyber security and training. Persuade your audience using this Five Steps Insurance Risk Management Procedure Professional PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Security Codes, Cyber Security, Stay Informed. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Current Market Trends Sample PDF
This slide provides information about the current market trends that are increasing the importance of security monitoring and motivating the company to implement a security monitoring plan in the company and follow monitoring strategies. Presenting continuous development evaluation plan eliminate cyber attacks current market trends sample pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like increasing digitization of sensitive data, general data protection laws, data breach notification laws. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Business Information Application Protection Testing Flow Chart Themes PDF
This slide covers business application security testing flow chart which includes secure application model, security standard recognition and privacy testing.Pitch your topic with ease and precision using this Business Information Application Protection Testing Flow Chart Themes PDF. This layout presents information on Security Consistency, Target Weighting, Target Recognition. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Collection Of Information Technology Certifications Global Information Assurance Designs PDF
This slide covers cyber security certifications Roadmap in security administration, management, legal, audit, forensics and software security. Deliver and pitch your topic in the best possible manner with this collection of information technology certifications global information assurance designs pdf. Use them to share invaluable insights on global information assurance certification giac certification roadmap and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information Technology Strategy IT Professional Upskilling For Cybersecurity Guidelines PDF
This slide displays the upskilling for cybersecurity which covers chief information security officer, cloud security architect, etc. This is a information technology strategy it professional upskilling for cybersecurity guidelines pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like chief information, security officer, cloud security architect, identify and access management architect. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Business Information Integrated Protection Control For Threat Prevention Graphics PDF
This slide covers business integrated security control for threat prevention which includes Business process and security system.Pitch your topic with ease and precision using this Business Information Integrated Protection Control For Threat Prevention Graphics PDF. This layout presents information on Incident Response, Security Policy Distribution, Threat Information. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Business Information Protection Risk Management Process Structure PDF
This slide covers business security risk management process which includes setting context, security risk assessment and implementation with monitoring. Pitch your topic with ease and precision using this Business Information Protection Risk Management Process Structure PDF. This layout presents information on Organizational Business, Security Risk Assessment, Performance Indicators. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Business Information Protection Through Product Improvement Infographics PDF
This slide cover business security through product improvement which includes product, infrastructure ,people security. Pitch your topic with ease and precision using this Business Information Protection Through Product Improvement Infographics PDF. This layout presents information on Improve Product, Scale Business, Infrastructure Security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Business Information Strategic Objectives And Protection Procedures Portrait PDF
This slide covers business strategic objectives and security procedures which includes security process controlling.Pitch your topic with ease and precision using this Business Information Strategic Objectives And Protection Procedures Portrait PDF. This layout presents information on Business Security, Business Strategic, International Standards. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Solutions To Overcome Saas Protection Issues Management Information PDF
This slide shows various solutions to prevent protection risks and issues. These solutions include risk evaluation, protection awareness, security checklist, policies and regulation. Presenting Solutions To Overcome Saas Protection Issues Management Information PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Policies And Regulation, Security Awareness, Security Checklist, Risk Evaluation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Corporate Governance Operating Framework To Improve Decision Making Diagrams PDF
This slide signifies the business governance operating model to improve decision making. It includes steps like security management plan, executive security board, strategic direction and operations.Pitch your topic with ease and precision using this Corporate Governance Operating Framework To Improve Decision Making Diagrams PDF. This layout presents information on Executive Security, Direction Governance, Communications Technology. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Cyber Exploitation IT Ethical Hacker And Why We Need Ethical Hacker Information PDF
This slide depicts the reasons to describe the need for ethical hacking, including identification and correction of security flaws, aid in development and quality control, and evaluation of the companys security and regulatory compliance. This is a cyber exploitation it ethical hacker and why we need ethical hacker information pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security flaws, development and quality control, evaluate security and regulatory compliance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
SIEM Sim Vs Sem Vs SIEM Ppt Icon Format Ideas PDF
This is a siem sim vs sem vs siem ppt icon format ideas pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security information management, security event management, security information and event management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
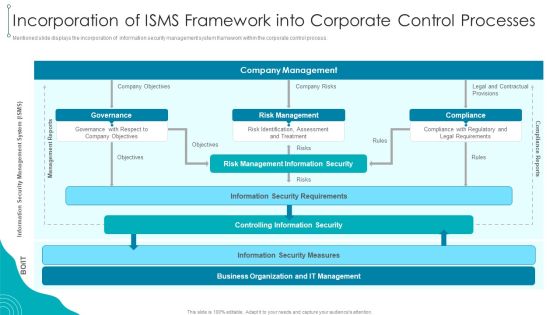
Incorporation Of ISMS Framework Into Corporate Control Processes Download PDF
Mentioned slide displays the incorporation of information security management system framework within the corporate control process.Deliver and pitch your topic in the best possible manner with this Incorporation Of ISMS Framework Into Corporate Control Processes Download PDF. Use them to share invaluable insights on Management Information, Security Requirements, Information Security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Exploitation IT Techniques To Keep Our Website Protected Brochure PDF
This slide represents the techniques to protect our website from hacking and cyber-attacks, including enhanced access controls, increased network security, installation of security software, etc. This is a cyber exploitation it techniques to keep our website protected brochure pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like install security software, hide administrator pages, enhance access control, update everything, increased network security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Essential Roles And Responsibilities Involved In Secops Elements PDF
This slide portrays information regarding the roles and responsibilities, qualification associated to staff available at Tier1, 2, 3, and 4 level at SOC structure.Deliver an awe inspiring pitch with this creative essential roles and responsibilities involved in secops elements pdf bundle. Topics like security incident responder, security alert investigator, security engineers can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Effective IT Risk Management Process Roles And Responsibilities For Managing Elements PDF
Following slide demonstrates various roles and responsibilities for information security management. Responsibilities covered are security policy development, asset classification and security framework development. This is a effective it risk management process roles and responsibilities for managing elements pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like implementation, development, security, organizational, risk. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Weekly Cybersecurity Awareness Training Program Schedule Timeline Guidelines PDF
This slide covers various courses for employees to aware about IT security threats. It includes identification of compliance stands, audit standards, incident trends, organisations security awareness, etc.Showcasing this set of slides titled Weekly Cybersecurity Awareness Training Program Schedule Timeline Guidelines PDF. The topics addressed in these templates are Compliance Standards, Identify Audit Standards, Security Training. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
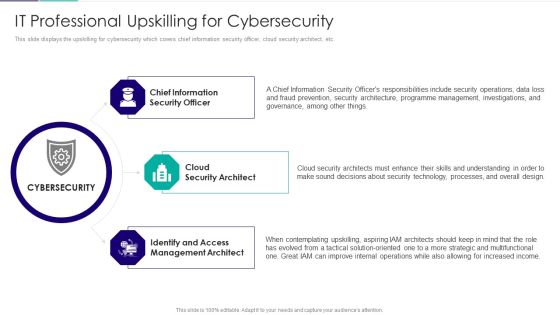
Role Of Technical Competence In Organizational It Professional Upskilling Inspiration PDF
This slide displays the upskilling for cybersecurity which covers chief information security officer, cloud security architect, etc.Presenting Role Of Technical Competence In Organizational It Professional Upskilling Inspiration PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Chief Information Security, Cloud Security Architect, Identify And Access Management Architect In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
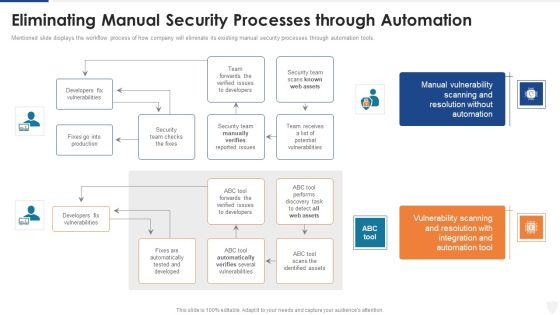
Defining Risk Events Based On Impact Size And Likelihood Of Occurrence Ppt Pictures Background PDF
Mentioned slide displays the workflow process of how company will eliminate its existing manual security processes through automation tools. Deliver and pitch your topic in the best possible manner with this eliminating manual security processes through automation ppt styles images pdf. Use them to share invaluable insights on security, team, production, developers and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Enhancing Cyber Safety With Vulnerability Administration SIM Vs SEM Vs SIEM Brochure PDF
Presenting enhancing cyber safety with vulnerability administration sim vs sem vs siem brochure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like security information management, security event management, security information and event management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Quarterly Cybersecurity Training Program And Assessment Schedule Sheet Elements PDF
This slide covers annual awareness training program schedule for employees. It includes training for network security, cyber security fundamentals, insider threats, malicious code, etc.Showcasing this set of slides titled Quarterly Cybersecurity Training Program And Assessment Schedule Sheet Elements PDF. The topics addressed in these templates are Insider Threats, Network Security, Risk Assessment. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Revolution In Online Business Steps Required To Demonstrating Cybersecurity Risk Mitigation Template PDF
This graph covers the variety of activities such as enforcing policy, providing appropriate funding, mandating awareness training, etc. to avoid cybersecurity risks. Deliver and pitch your topic in the best possible manner with this Revolution In Online Business Steps Required To Demonstrating Cybersecurity Risk Mitigation Template PDF. Use them to share invaluable insights on Enforcing Security Policy, Providing Security Appropriate, Funding Mandating Security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Key Pillars Of Identify And Access Management Technique Topics PDF
This slide shows main features of an effective IAM strategy. The purpose of this strategy is to highlight major components of IAM strategy. It include features such as provisioning identities, access security certification and security management , etc. Presenting Key Pillars Of Identify And Access Management Technique Topics PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Provisioning Identities, Security Certification, Security Management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Vendor Selection Steps For Digital Risk Assessment Ppt Visual Aids Show PDF
The following slide highlights the Vendor selection steps for cyber security risk depicting assessment methodology, tailor assessment, risk questions, risk threshold and cyber security assessment, it helps company to select cyber security framework and customize it to their requirements. Presenting Vendor Selection Steps For Digital Risk Assessment Ppt Visual Aids Show PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Assessment Methodology, Risk QuestionsCyber Security Assessment. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Methods To Develop Advanced Cybersecurity Monitoring Tools To Be Implemented Guidelines PDF
This slide provides information about some of the best security monitoring tools that are available with the security monitoring manager and what tool is selected by the security monitoring manager based on tool implementation costs, tool implementation time etc. Deliver an awe inspiring pitch with this creative methods to develop advanced cybersecurity monitoring tools to be implemented guidelines pdf bundle. Topics like network security monitoring, encryption tool, web vulnerability scanning tool can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Computing Cyber Threat Prevention Flowchart Slides PDF
The below slide provides a cloud security framework which encourages security companies to clarify the roles played by the various cloud security stakeholders within their organization and enhance overall security compliance. Major stages are visibility, governance, resolve violation, etc. Showcasing this set of slides titled Cloud Computing Cyber Threat Prevention Flowchart Slides PDF. The topics addressed in these templates are Visibility, Governance, Resolve Violations. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Phishing Attacks Awareness Training Program Plan Inspiration PDF
This slide covers phishing awareness training program plan to enhance effectiveness. It involves training topics such as cloud security, public Wi-Fi, removable media, mobile device security and passwords and authentication. Persuade your audience using this Phishing Attacks Awareness Training Program Plan Inspiration PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Cloud Security, Mobile Device Security, Awareness. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
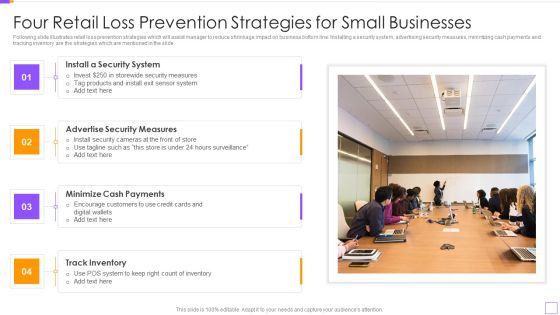
Four Retail Loss Prevention Strategies For Small Businesses Themes PDF
Following slide illustrates retail loss prevention strategies which will assist manager to reduce shrinkage impact on business bottom line. Installing a security system, advertising security measures, minimizing cash payments and tracking inventory are the strategies which are mentioned in the slide. Persuade your audience using this Four Retail Loss Prevention Strategies For Small Businesses Themes PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Install A Security System, Advertise Security Measures, Minimize Cash Payments, Track Inventory. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Major Social Media Protection And Privacy Issues Template PDF
The following slide highlights some social media security threats to safeguard unauthorized access. It includes elements such as data mining, hacking, harassment, cyberbullying, privacy loophole etc. Presenting Major Social Media Protection And Privacy Issues Template PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Data Mining, Harassment And Cyberbullying, Privacy Loophole. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Customer Server Network Design Structure Model Ppt PowerPoint Presentation Gallery Graphics PDF
Presenting this set of slides with name customer server network design structure model ppt powerpoint presentation gallery graphics pdf. This is a one stage process. The stages in this process are central data base, data and information, internet, control switch, providing connection to server, common control switch, wireless access point server, providing internet medium, security firewall acting, threat and viruses. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Banking Overview Diagram Sample Ppt Slides
This is a banking overview diagram sample ppt slides. This is a one stage process. The stages in this process are banking and finance, wealth management, network security and solution, systems integration, commercial banking, database development and administration, data warehouse solutions, consumer banking, ui, ux, application design and development, project management, business analysis and quality assurance, investment banking, architecture services, big data and cloud computing.

Comprehensive Business Safety Analysis Tasks Ppt PowerPoint Presentation Pictures Background Image PDF
Presenting comprehensive business safety analysis tasks ppt powerpoint presentation pictures background image pdf. to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including security program, networking security, penetration testing. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Six Steps Of Concept Of Risk Management Framework Introduction Professional PDF
Presenting Six Steps Of Concept Of Risk Management Framework Introduction Professional PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Information System Categorization, Security Control Selection, Security Control Implementation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
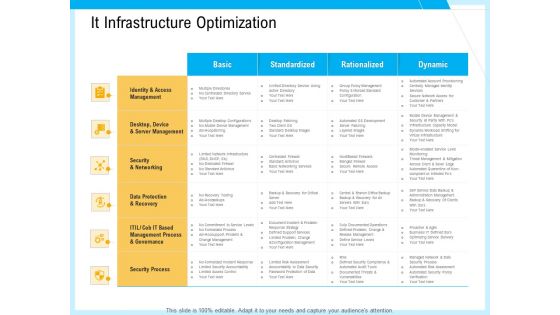
IT And Cloud Facilities Management It Infrastructure Optimization Ppt Model Slide PDF
Deliver an awe-inspiring pitch with this creative it and cloud facilities management it infrastructure optimization ppt model slide pdf bundle. Topics like standardized, rationalized, dynamic, identity and access management, security and networking, security process can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Key Leading Drivers To Adopt Consumer Information Platform Information PDF
This slide shows the key drivers that leads companies to adopt customer data platform software such as maximizing marketing returns, ,meeting customer expectations, creating accountability, improving efficiency, mitigating security and privacy risks, etc. Presenting key leading drivers to adopt consumer information platform information pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including maximize marketing returns, meets customer expectations, creates accountability, improves it efficiency, mitigates security risks. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Information Protection Risk Management Committee Diagram Information PDF
This slide shows flow chart of cyber protection risk management team of an organization. It includes cyber protection system deployment team, data center management, network member, etc. Persuade your audience using this Information Protection Risk Management Committee Diagram Information PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Information Security Head, Information Security Audit Scan, Network Member. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Business Diagram Magnifying Glass With Puzzle Pieces Slide Presentation Template
This business plan power point template has been designed with graphic of lock which is made by puzzles pieces and with one missing puzzle. This PPT contains the concept of security and solution development. Add this PPT in your presentations and display solution and security related topics.

Organization Impact Metrics Strategic Themes PDF
This slides the metrics That assess how your security awareness plan serves the overall security system of your company, and therefore the organizations mission.Presenting organization impact metrics strategic themes pdf. to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like data loss incidents, infected computers, total number of computers currently corrupted. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Classification Of Banking Credit And Advance Services Summary PDF
Following slide illustrates types of credit facilities offered by banks. Purpose of this slide to provide knowledge of services to cater client financial needs. It includes security bank credit types secured and unsecured advances with loan uses. Presenting Classification Of Banking Credit And Advance Services Summary PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Security Bank Credit, Security Requirement, Education Loan This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Incident Response Techniques Deployement Impact Of Cybersecurity Incidents On Organization Clipart PDF
This slide represents the impact of events which indicates that organizations data has been compromised for unlawful activities. It includes impact of cyber security events such as increased costs, operational disruption, reputational damage etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Incident Response Techniques Deployement Cyber Security Incident Management Team Structure Diagrams PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Incident Response Techniques Deployement Cyber Security Incident Management Team Structure Diagrams PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Reactive And Proactive Business Information Protection Evaluation Process Sample PDF
This slide covers reactive and proactive business security evaluation process which includes evaluating security based on set standards. Persuade your audience using this Reactive And Proactive Business Information Protection Evaluation Process Sample PDF. This PPT design covers one stage, thus making it a great tool to use. It also caters to a variety of topics including Conventional Reactive, Proactive Security, Evaluation Process. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Table Of Contents Risk Management For Organization Essential Assets Brochure PDF
Presenting table of contents risk management for organization essential assets brochure pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like current scenario assessment, secure digital assets, natural calamity threats, ensuring physical security, security against workplace. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Role IT Team Digital Transformation It Professional Upskilling For Cybersecurity Introduction PDF
This slide displays the upskilling for cybersecurity which covers chief information security officer, cloud security architect, etc. This is a role it team digital transformation it professional upskilling for cybersecurity introduction pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information, security, management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
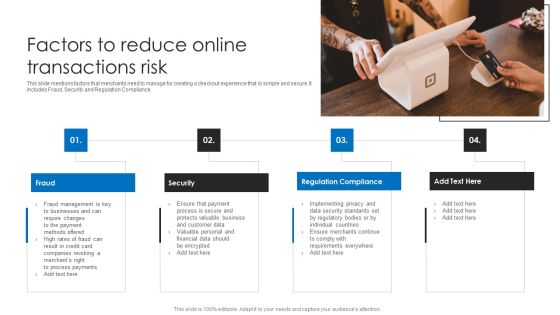
Factors To Reduce Online Transactions Risk Ppt Ideas Graphics Design PDF
This slide mentions factors that merchants need to manage for creating a checkout experience that is simple and secure. It includes Fraud, Security and Regulation Compliance. Presenting Factors To Reduce Online Transactions Risk Ppt Ideas Graphics Design PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Fraud, Security, Regulation Compliance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
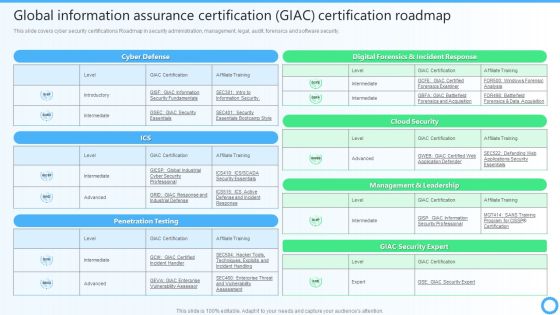
Global Information Assurance Certification GIAC Certification Roadmap IT Certifications To Enhance Template PDF
This slide covers cyber security certifications Roadmap in security administration, management, legal, audit, forensics and software security.This Global Information Assurance Certification GIAC Certification Roadmap IT Certifications To Enhance Template PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Convergence Strategy Information Single Database For Two Separate IT OT Socs Rules PDF
This slide covers single database structure for two IT or OT socs including network security, multi cloud security, security operations , open ecosystems etc. Presenting Convergence Strategy Information Single Database For Two Separate IT OT Socs Rules PDF to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like Fabric Connectors, Analyzer SIEM Sandbox, AP Switch Token, Client NAC, Fabric APIs. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Steps Of Digital Risk Assessment In Organisation Ppt Infographics Templates PDF
The following slide highlights the steps of cyber security in organisation depicting network security, awareness, malware, external media, configuration, user privilege, incident management, monitoring and distant working. Presenting Steps Of Digital Risk Assessment In Organisation Ppt Infographics Templates PDF to dispense important information. This template comprises nine stages. It also presents valuable insights into the topics including Network Security, Awareness, Malware, External Media. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Digital Risk Assessment Threat Mitigation Strategies Ppt Show Images PDF
The following slide highlights the six strategies for cyber security threat mitigation illustrating risk assessment, access control, security solution, patch management, traffic monitoring and incident response. Presenting Digital Risk Assessment Threat Mitigation Strategies Ppt Show Images PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Risk Assessment, Access Control, Patch Management, Security Solution. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
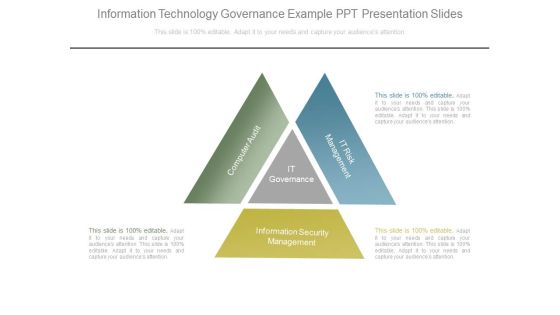
Information Technology Governance Example Ppt Presentation Slides
This is a information technology governance example ppt presentation slides. This is a three stage process. The stages in this process are computer audit, it governance, it risk management, information security management.

Global Cyber Terrorism Incidents On The Rise IT Techniques To Protect SCADA Elements PDF
This slide depicts the techniques to protect SCADA from cyber-attacks which include security training of employees, strict firewalls. This is a global cyber terrorism incidents on the rise it techniques to protect scada elements pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security training of employee, access controls, strict firewalls, network security procedures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
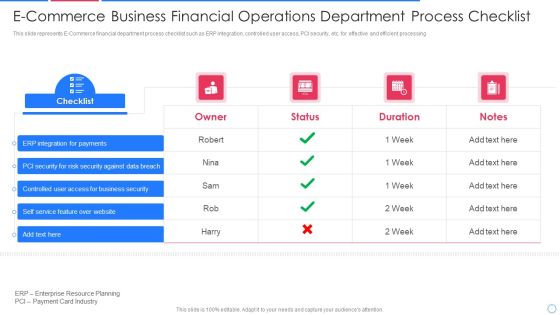
E Commerce Business Financial Operations Department Process Checklist Information PDF
This slide represents E-Commerce financial department process checklist such as ERP integration, controlled user access, PCI security, etc. for effective and efficient processing Pitch your topic with ease and precision using this e commerce business financial operations department process checklist information pdf This layout presents information on integration for payments, security for risk security against, controlled user access It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

CIO Role In Digital Evolution IT Professional Upskilling For Cybersecurity Themes PDF
This slide displays the upskilling for cybersecurity which covers chief information security officer, cloud security architect, etc. This is a CIO Role In Digital Evolution IT Professional Upskilling For Cybersecurity Themes PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Chief Information, Management Architect, Cloud Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Embedding Risk Based Approach Into Product Development Process Ppt Model Files PDF
Purpose of this slide is to highlight the risk based approach and process efficiency along with the cost incur details. It also shows that company will develop agile security and privacy models. Presenting embedding risk based approach into product development process ppt model files pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like technology controls, information security processes, security organization, economic. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Single Database For Two Separate IT OT Socs Managing Organizational Transformation Professional PDF
This slide covers single database structure for two IT OT socs including network security, multi cloud security, security operations , open ecosystems etc. Presenting Single Database For Two Separate IT OT Socs Managing Organizational Transformation Professional PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Single Database, Two Separate, Fabric Connectors. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Portable Home Safety Systems Company Profile Awards And Accolades Brochure PDF
This slide highlights the awards and allocates received by security company which includes best smart home security systems, best leak and smoke detectors, and innovative product of the year. Presenting Portable Home Safety Systems Company Profile Awards And Accolades Brochure PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Digital Trends, Consumer, Technology Association, Consumer Technology Association, Security Today. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Technology Transformation Playbook Strategic IT Infrastructure Enhancement Elements PDF
This slide provides information regarding IT infrastructure enhancement roadmap tracking activities associated to testing, improvements, integrations, security, etc. Deliver and pitch your topic in the best possible manner with this information technology transformation playbook strategic it infrastructure enhancement elements pdf. Use them to share invaluable insights on required, infrastructure, security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Features Of WAF Protection Against The Owasp Vulnerabilities WAF Platform Summary PDF
This slide represents one of WAFs features that is protection against the top 10 open web application security project vulnerabilities such as injection, XSS, XXE, and so on. This is a Features Of WAF Protection Against The Owasp Vulnerabilities WAF Platform Summary PDF template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Misconfigurations, Session Management, Security Project. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Portable Home Safety Systems Company Profile Executive Leadership And Management Team Rules PDF
This slide highlights the security company leadership and management team which includes president and CEO, executive vice president of finance, EVP home security, chief administration officer. This is a Portable Home Safety Systems Company Profile Executive Leadership And Management Team Rules PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Finance, Home Security, Management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
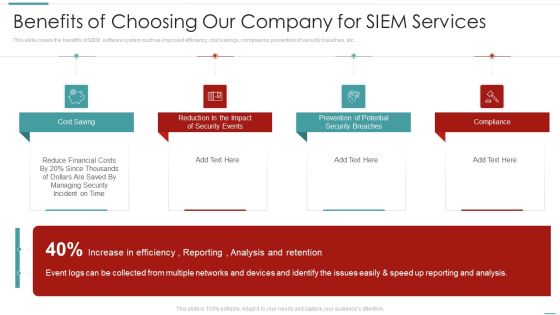
Risk Recognition Automation Benefits Of Choosing Our Company For Siem Services Ppt Gallery Design Inspiration PDF
This slide covers the benefits of SIEM software system such as improved efficiency, cost savings, compliance, prevention of security breaches, etc. This is a risk recognition automation benefits of choosing our company for siem services ppt gallery design inspiration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cost saving, prevention of potential security breaches, compliance, reduction in the impact of security events. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Individual And Organizational Practices For Digital Terrorism Attacks Microsoft PDF
This slide shows best practices on individual and organizational level for preventing cyber terrorism attacks. It include practices such as Choose complicated password, Invest in cyber security plan etc. Pitch your topic with ease and precision using this Individual And Organizational Practices For Digital Terrorism Attacks Microsoft PDF. This layout presents information on Organization, Promote Security, Security Insurance. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
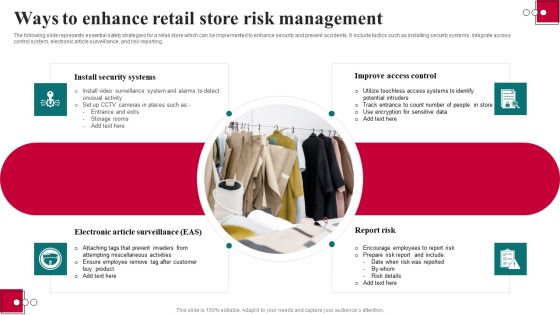
Ways To Enhance Retail Store Risk Management Introduction PDF
The following slide represents essential safety strategies for a retail store which can be implemented to enhance security and prevent accidents. It include tactics such as installing security systems, integrate access control system, electronic article surveillance, and risk reporting. Pitch your topic with ease and precision using this Ways To Enhance Retail Store Risk Management Introduction PDF. This layout presents information on Electronic Article Surveillance, Report Risk, Install Security Systems. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Need For Ethical Hacking Ppt Gallery Portfolio PDF
This slide depicts the reasons to describe the need for ethical hacking, including identification and correction of security flaws, aid in development and quality control, and evaluation of the companys security and regulatory compliance. This is a need for ethical hacking ppt gallery portfolio pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like quality control, development, security, system, measures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

NIST Cybersecurity Framework Implementation Tier Categories Rules PDF
The slide showcases Nist cyber security framework tiers which categorize your organizations security processes, it helps to analyze which tier your organization belongs to and what your current systems security requirements are. The tiers are as following partial, risk informed, repeatable and adaptive. Persuade your audience using this NIST Cybersecurity Framework Implementation Tier Categories Rules PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Partial, Risk Informed, Repeatable . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Protection And Privacy Issues In Cloud Technology Rules PDF
The following slide depicts some security and privacy concerns associated with clout network to meet compliance and protect individual interest. It includes elements such as underdeveloped saas safety, infrastructure, control etc. Persuade your audience using this Protection And Privacy Issues In Cloud Technology Rules PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Absence Of Control, Saas Security, Security Model. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
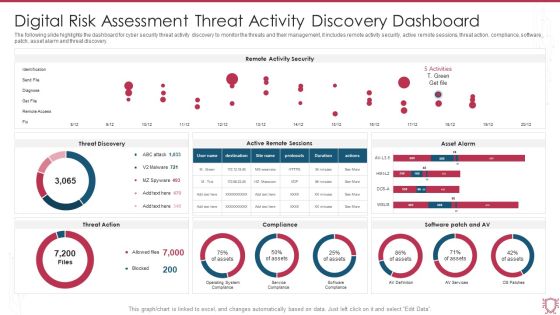
Digital Risk Assessment Threat Activity Discovery Dashboard Ppt Ideas Skills PDF
The following slide highlights the dashboard for cyber security threat activity discovery to monitor the threats and their management, it includes remote activity security, active remote sessions, threat action, compliance, software patch, asset alarm and threat discovery. Pitch your topic with ease and precision using this Digital Risk Assessment Threat Activity Discovery Dashboard Ppt Ideas Skills PDF. This layout presents information on Remote Activity Security, Threat Discovery, Asset Alarm. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Process Of Digital Risk Assessment Management Ppt Summary Graphics PDF
The following slide highlights the process of cyber security asset management depicting four steps which include asset inventory, synchronization, security gaps and response to save assets and mitigate the risk in minimum time. Presenting Process Of Digital Risk Assessment Management Ppt Summary Graphics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Asset Inventory, Synchronization, Response, Security Gaps. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

ESO System Center Team Roles And Responsibilities Ppt PowerPoint Presentation File Slides PDF
This slide covers enterprise security operation center team roles and responsibilities. It involves key roles such as incident responder, security investigator, advanced security analyst and SOC manager. Pitch your topic with ease and precision using this ESO System Center Team Roles And Responsibilities Ppt PowerPoint Presentation File Slides PDF. This layout presents information on SOC Team Roles, Responsibilities, Tier. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Inclusion Of Automation In ESO System Ppt PowerPoint Presentation File Maker PDF
This slide covers inclusion of automation in enterprise security operations. It involves key roles such as automation, security analysts, incident responder, threat hunter and security operation manager. Pitch your topic with ease and precision using this Inclusion Of Automation In ESO System Ppt PowerPoint Presentation File Maker PDF. This layout presents information on Mission, Role, Tier. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Tools Diagrams PDF
This slide provides information about some of the best security monitoring tools that are available with the security monitoring manager and what tool is selected by the security monitoring manager based on tool implementation costs, tool implementation time etc. Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring tools diagrams pdf bundle. Topics like cybersecurity monitoring tools to be implemented can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Three Approaches To Improve Workplace Protection And Precaution Background PDF
This slide shows three strategies to increase safety and security of workplace. These are reduce manual security, reliance on technology and monitor. Persuade your audience using this Three Approaches To Improve Workplace Protection And Precaution Background PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Reduce Manual Security, Reliance On Technology, Monitor. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Enhancing Cyber Safety With Vulnerability Administration Benefits Of Choosing Our Company Inspiration PDF
This slide covers the benefits of SIEM software system such as improved efficiency, cost savings, compliance, prevention of security breaches, etc. Presenting enhancing cyber safety with vulnerability administration benefits of choosing our company inspiration pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like cost saving, reduction in the impact of security events, prevention of potential security breaches, compliance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Web App Firewall Services IT Dashboard For Web Application Firewall Performance Microsoft PDF
This slide describes the dashboard for web application firewall performance monitoring by covering details of application attack distribution, HTTP transaction per second, application security events source map, DDOs protected traffic, and application security events. Deliver and pitch your topic in the best possible manner with this web app firewall services it dashboard for web application firewall performance microsoft pdf. Use them to share invaluable insights on application, source, security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Influencer Marketing 4 Months Project Status Update Icon Slides PDF
This slide covers the four months project status update of software implementation project undertaken by the IT team. It includes various activities to be performed under IT help desk, web server, network and global security.Showcasing this set of slides titled Influencer Marketing 4 Months Project Status Update Icon Slides PDF. The topics addressed in these templates are Global Security, Network Speed, Security Plan . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Information Technology Threat Mitigation Methods Classification Of IT Risks With Threats Diagrams PDF
This slide highlights the classification of information technology risks which includes technology, security, political and legal, personnel, and infrastructure with key threats. Deliver an awe inspiring pitch with this creative Information Technology Threat Mitigation Methods Classification Of IT Risks With Threats Diagrams PDF bundle. Topics like Risks Description, Technology, Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

SIEM Benefits Of Choosing Our Company For SIEM Services Ppt File Outfit PDF
This slide covers the benefits of SIEM software system such as improved efficiency, cost savings, compliance, prevention of security breaches, etc. Presenting siem benefits of choosing our company for siem services ppt file outfit pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like cost saving, reduction in the impact of security events, prevention of potential security breaches, compliance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Dashboard For Web Application Firewall Performance WAF Platform Diagrams PDF
This slide describes the dashboard for web application firewall performance monitoring by covering details of application attack distribution, HTTP transaction per second, application security events source map, DDOs protected traffic, and application security events. Deliver an awe inspiring pitch with this creative Dashboard For Web Application Firewall Performance WAF Platform Diagrams PDF bundle. Topics like Application Attack Distribution, Application Security Events, Transactions Per Second can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Business Initiatives For Information Protection Management Designs PDF
This slide covers business initiatives for information security management which includes security and governance guidelines for implementing, monitoring process. Pitch your topic with ease and precision using this Business Initiatives For Information Protection Management Designs PDF. This layout presents information on Technologies Strategically, Assessing Vulnerability, Implementing Process. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Challenges Faced During Technology Implementation Infographics PDF
This slide shows three challenges faced by an organization in technology implementation. It includes training, security and monitoring. Presenting Challenges Faced During Technology Implementation Infographics PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Training, Security, Monitoring. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Engagement Plan Disclosure And Consultation Phase Activities Timing Pictures PDF
This is a table of contents for companys data safety recognition ppt professional shapes pdf template with various stages. Focus and dispense information on fourteen stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like tracking, impact, budget, communication plan, security awareness. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Use Cases Of Comprehensive Risk Management System For A Blockchain Network Ppt PowerPoint Presentation Outline Background Designs PDF
Presenting use cases of comprehensive risk management system for a blockchain network ppt powerpoint presentation outline background designs pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including filtering the security alerts, provide distribution of the public key, providing decentralized data storage. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Portable Home Safety Systems Company Profile Paid Subscribers By Channel Demonstration PDF
This slide highlights the security company paid subscribers count by channel in bar graph format. It includes data of dealer or retailer and direct channel from 2018 to 2022. Deliver an awe inspiring pitch with this creative Portable Home Safety Systems Company Profile Paid Subscribers By Channel Demonstration PDF bundle. Topics like Total Subscribers, Dealer, Retailer, Direct, 2018 To 2022 can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Terrorism Assault Managing Cyber Terrorism 60 Days Plan Clipart PDF
This slide depicts the plan for the next 60 days after the firm has implemented the cyber security model to tackle cyber terrorism.Deliver and pitch your topic in the best possible manner with this cyber terrorism assault managing cyber terrorism 60 days plan clipart pdf Use them to share invaluable insights on time to detect an incident, data loss incidents, infected computers and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

 Home
Home