Data Security And Protection
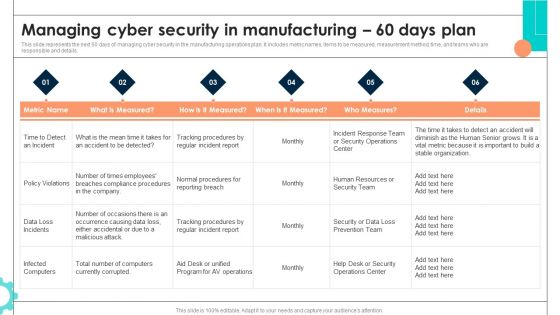
Intelligent Manufacturing Managing Cyber Security In Manufacturing 60 Days Plan Pictures PDF
This slide represents the next 60 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. There are so many reasons you need a Intelligent Manufacturing Managing Cyber Security In Manufacturing 60 Days Plan Pictures PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
Prioritize Cyber Security Risk With Severity Matrix Ppt PowerPoint Presentation File Icon PDF
The following slide depicts cyber security risk assessment grid to prioritize and eliminate occurrence of threats. It includes elements such as moderate, severe, minor, negligible, rate, possible, likely, unlikely etc. Want to ace your presentation in front of a live audience Our Prioritize Cyber Security Risk With Severity Matrix Ppt PowerPoint Presentation File Icon PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Iot Integration In Manufacturing Managing Cyber Security In Manufacturing 30 Days Plan Template PDF
This slide describes the first 30 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. There are so many reasons you need a Iot Integration In Manufacturing Managing Cyber Security In Manufacturing 30 Days Plan Template PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
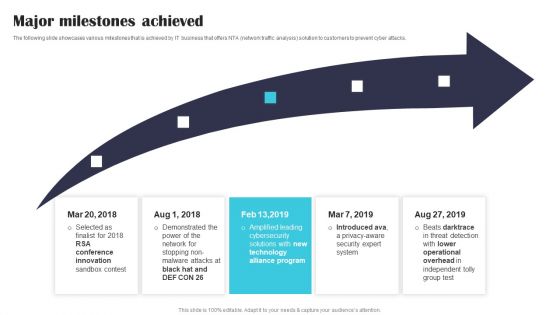
Security Software Company Investor Funding Pitch Deck Major Milestones Achieved Mockup PDF
The following slide showcases various milestones that is achieved by IT business that offers NTA network traffic analysis solution to customers to prevent cyber attacks. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Security Software Company Investor Funding Pitch Deck Major Milestones Achieved Mockup PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Security Software Company Investor Funding Pitch Deck Major Milestones Achieved Mockup PDF.
Weekly Timeline With Task Name Hacking Prevention Awareness Training For IT Security Download PDF
Deliver an awe inspiring pitch with this creative weekly timeline with task name hacking prevention awareness training for it security download pdf bundle. Topics like weekly timeline with task name can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Icons Slide For IT Security Evaluation Scorecard Ppt Icon Good PDF
Introducing our well designed Icons Slide For IT Security Evaluation Scorecard Ppt Icon Good PDF set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
Icons Slide For IT Security Automation Tools Integration Ppt Styles Grid PDF
Download our innovative and attention grabbing Icons Slide For IT Security Automation Tools Integration Ppt Styles Grid PDF template. The set of slides exhibit completely customizable icons. These icons can be incorporated into any business presentation. So download it immediately to clearly communicate with your clientele.
Icons Slide For Developing IT Security Strategy To Prevent Themes PDF
Download our innovative and attention grabbing Icons Slide For Developing IT Security Strategy To Prevent Themes PDF template. The set of slides exhibit completely customizable icons. These icons can be incorporated into any business presentation. So download it immediately to clearly communicate with your clientele.
Icons Slide For Methods To Develop Advanced IT Security Monitoring Plan Slides PDF
Presenting our innovatively structured icons slide for methods to develop advanced it security monitoring plan slides pdf set of slides. The slides contain a hundred percent editable icons. You can replace these icons without any inconvenience. Therefore, pick this set of slides and create a striking presentation.
Icons Slide For Risk Based Procedures To IT Security Ppt PowerPoint Presentation Gallery Vector PDF
Presenting our innovatively structured Icons Slide For Risk Based Procedures To IT Security Ppt PowerPoint Presentation Gallery Vector PDF set of slides. The slides contain a hundred percent editable icons. You can replace these icons without any inconvenience. Therefore, pick this set of slides and create a striking presentation.
Icons Slide For IT Security Risk Management Approach Introduction Template PDF
Presenting our innovatively structured Icons Slide For IT Security Risk Management Approach Introduction Template PDF set of slides. The slides contain a hundred percent editable icons. You can replace these icons without any inconvenience. Therefore, pick this set of slides and create a striking presentation.

Overview Of Blockchain 51 Comprehensive Guide To Blockchain Digital Security Information Pdf
The following slide showcases brief introduction of 51percent attack to analyze hashing power of cryptocurrency users. It includes elements such at mining faster rate, malicious user, along with its workflow, etc. Slidegeeks has constructed Overview Of Blockchain 51 Comprehensive Guide To Blockchain Digital Security Information Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

Corporate Security And Risk Management Determine Sequence Phases For Threat Attack Contd Mockup PDF
This slide provides details regarding sequence phases for threat attack by threat actor in terms of installation, command and control, actions and objectives, covering tracks. This is a corporate security and risk management determine sequence phases for threat attack contd mockup pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like installation, command and control, actions and objectives, covering tracks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Corporate Security And Risk Management Roles And Responsibilities To Ensure Work Professional PDF
This slide provides details regarding roles and responsibilities assigned to ensure minimum violence work environment This is a corporate security and risk management roles and responsibilities to ensure work professional pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employee responsibilities, unit supervisor manager responsibilities, internal investigations unit responsibilities, human resources responsibilities . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
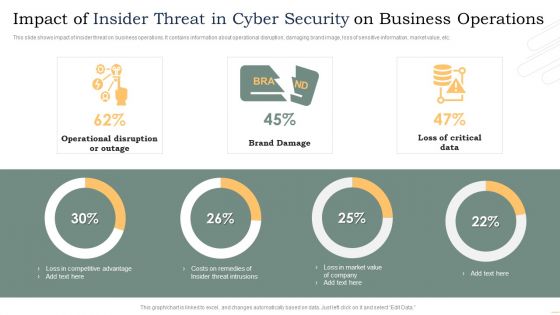
Impact Of Insider Threat In Cyber Security On Business Operations Microsoft PDF
This slide shows impact of insider threat on business operations. It contains information about operational disruption, damaging brand image, loss of sensitive information, market value, etc. Pitch your topic with ease and precision using this Impact Of Insider Threat In Cyber Security On Business Operations Microsoft PDF. This layout presents information on Operational Disruption Or Outage, Brand Damage, Loss Critical Data. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Insider Threat In Cyber Security Tracking Dashboard With User Details Portrait PDF
This slide shows user details tracked by insider threat dashboard. It provides information such as exposure events, file activity, archive, document, image, pdf, ppt, scripts, etc. Pitch your topic with ease and precision using this Insider Threat In Cyber Security Tracking Dashboard With User Details Portrait PDF. This layout presents information on Private Data, Exposure Events, User Activity, File Activity, Over Time. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
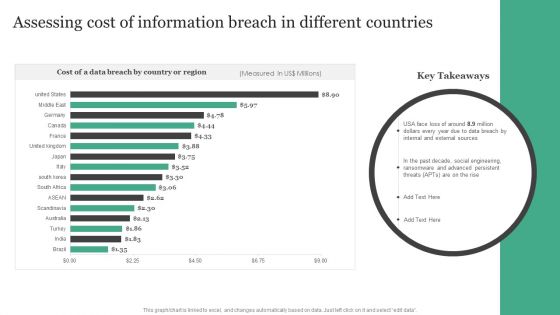
Assessing Cost Of Information Breach In Different Countries Information Security Risk Administration Topics PDF
Retrieve professionally designed Assessing Cost Of Information Breach In Different Countries Information Security Risk Administration Topics PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Organizing Security Awareness Most Common Cyber Attack Faced By Our Employees Mockup PDF
The Organizing Security Awareness Most Common Cyber Attack Faced By Our Employees Mockup PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Table Of Contents Security And Human Resource Services Business Profile Slides PDF
This Table Of Contents Security And Human Resource Services Business Profile Slides PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Performing Threat Assessment Comprehensive Guide To Blockchain Digital Security Professional Pdf
The following slide showcases blockchain cybersecurity threat assessment to determine type and major causes of attacks. It includes elements such as double spending, mining threats, wallet, network, smart contract threats, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Performing Threat Assessment Comprehensive Guide To Blockchain Digital Security Professional Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Performing Threat Assessment Comprehensive Guide To Blockchain Digital Security Professional Pdf.
Mesh Computing Safety Icon Cloud Computing Cloud Security Ppt PowerPoint Presentation Complete Deck
Share a great deal of information on the topic by deploying this mesh computing safety icon cloud computing cloud security ppt powerpoint presentation complete deck. Support your ideas and thought process with this prefabricated set. It includes a set of twelve slides, all fully modifiable and editable. Each slide can be restructured and induced with the information and content of your choice. You can add or remove large content boxes as well, to make this PPT slideshow more personalized. Its high-quality graphics and visuals help in presenting a well-coordinated pitch. This PPT template is also a resourceful tool to take visual cues from and implement the best ideas to help your business grow and expand. The main attraction of this well-formulated deck is that everything is editable, giving you the freedom to adjust it to your liking and choice. Changes can be made in the background and theme as well to deliver an outstanding pitch. Therefore, click on the download button now to gain full access to this multifunctional set.

Best Practices To Create Comprehensive Guide To Blockchain Digital Security Clipart Pdf
The following slide illustrates some tips to develop strong passwords to manage and ensure secure blockchain transactions. It includes elements such as long and strong passwords, never reusing keys, leveraging password managers, avoiding personal information, etc. This Best Practices To Create Comprehensive Guide To Blockchain Digital Security Clipart Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
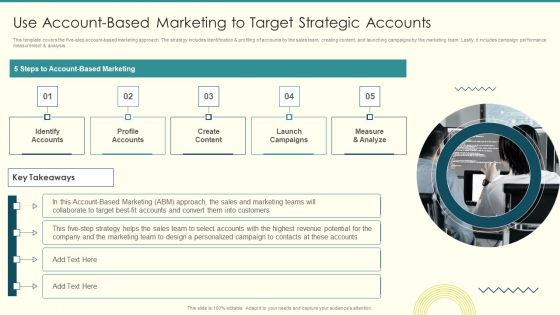
Security And Performance Digital Marketing Use Accountbased Marketing To Target Strategic Accounts Topics PDF
This template covers the five-step account-based marketing approach. The strategy includes identification profiling of accounts by the sales team, creating content, and launching campaigns by the marketing team. Lastly, it includes campaign performance measurement analysis. This is a Security And Performance Digital Marketing Use Accountbased Marketing To Target Strategic Accounts Topics PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Personalized Campaign, Revenue Potential, Launch Campaigns. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
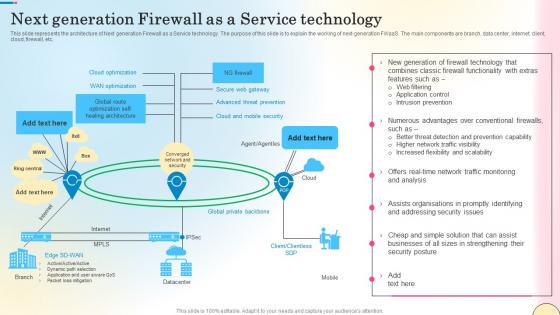
Next Generation Firewall As A Service Technology Network Security Mockup Pdf
This slide outlines the various types of firewalls. The purpose of this slide is to elaborate the use of different firewalls. These include packet filtering, proxy service firewall, stateful inspection, next-generation firewall, threat focusses next-gen firewall, etc. Do you know about Slidesgeeks Next Generation Firewall As A Service Technology Network Security Mockup Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
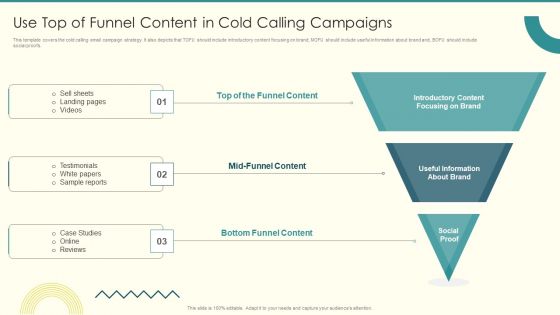
Security And Performance Digital Marketing Use Top Of Funnel Content In Cold Calling Campaigns Template PDF
This template covers the cold calling email campaign strategy. It also depicts that TOFU should include introductory content focusing on brand, MOFU should include useful information about brand and, BOFU should include social proofs.Presenting Security And Performance Digital Marketing Use Top Of Funnel Content In Cold Calling Campaigns Template PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Sample Reports, Testimonials, Landing Pages. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Quarterly Employee Security Coaching Matrix With Variance Analysis Ppt Styles Design Ideas PDF
The given below slide depicts the quarter wise variance analysis of safety training program expenditures to control and spot the reason for the same. It includes elements such as budgeted, actual etc. Presenting quarterly employee security coaching matrix with variance analysis ppt styles design ideas pdf to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including particulars, quarter 4 analysis 2022, consultancy fee, content charges. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Enhancing Cloud Security With CASB Table Of Contents Ppt PowerPoint Presentation File Backgrounds PDF
This Enhancing Cloud Security With CASB Table Of Contents Ppt PowerPoint Presentation File Backgrounds PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The product features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Safety Dominos Business Security PowerPoint Templates Ppt Backgrounds For Slides 1212
We present our Safety Dominos Business Security PowerPoint Templates PPT Backgrounds For Slides 1212.Use our Business PowerPoint Templates because it helps you to project your enthusiasm and single mindedness to your colleagues. Download our Finance PowerPoint Templates because it helps you to satiate the brains of your team with a taste of the final product. Present our Future PowerPoint Templates because this PPt Enlighten others on your team with your views. Use our Marketing PowerPoint Templates because networking is an imperative in todays world. You need to access the views of others. Similarly you need to give access to them of your abilities. Download and present our Shapes PowerPoint Templates because you have an idea of which you are sure.Use these PowerPoint slides for presentations relating to Domino effect and business, business, finance, future, marketing, shapes. The prominent colors used in the PowerPoint template are Green, Yellow, Gray. We assure you our Safety Dominos Business Security PowerPoint Templates PPT Backgrounds For Slides 1212 are Efficacious. Customers tell us our business PowerPoint templates and PPT Slides are Gorgeous. You can be sure our Safety Dominos Business Security PowerPoint Templates PPT Backgrounds For Slides 1212 will help you be quick off the draw. Just enter your specific text and see your points hit home. People tell us our and PowerPoint templates and PPT Slides are Pretty. Presenters tell us our Safety Dominos Business Security PowerPoint Templates PPT Backgrounds For Slides 1212 will make the presenter look like a pro even if they are not computer savvy. People tell us our shapes PowerPoint templates and PPT Slides are One-of-a-kind.

Software Architecture Security Scalability Ppt PowerPoint Presentation Complete Deck With Slides
Share a great deal of information on the topic by deploying this software architecture security scalability ppt powerpoint presentation complete deck with slides. Support your ideas and thought process with this prefabricated set. It includes a set of twelve slides, all fully modifiable and editable. Each slide can be restructured and induced with the information and content of your choice. You can add or remove large content boxes as well, to make this PPT slideshow more personalized. Its high-quality graphics and visuals help in presenting a well-coordinated pitch. This PPT template is also a resourceful tool to take visual cues from and implement the best ideas to help your business grow and expand. The main attraction of this well-formulated deck is that everything is editable, giving you the freedom to adjust it to your liking and choice. Changes can be made in the background and theme as well to deliver an outstanding pitch. Therefore, click on the download button now to gain full access to this multifunctional set.

Addressing Mobile Device Management Approach Mobile Device Security Management Designs PDF
This slide provides information regarding different mobile device management approach such as container and platform approach that can be selected by vendor based on requirement. This is a Addressing Mobile Device Management Approach Mobile Device Security Management Designs PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Container Approach, Platform Approach, Critical Information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Comparative Analysis Of Insider Threat In Cyber Security Detection Software Guidelines PDF
This slide shows comparison of software available for detecting insider threat. It provides information about tools, features, user reviews, detection rate, free trial and pricing. Pitch your topic with ease and precision using this Comparative Analysis Of Insider Threat In Cyber Security Detection Software Guidelines PDF. This layout presents information on User Reviews, Detection Rate, Free Trial. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Security And Performance Digital Marketing Create Content Strategy That Resonates With Targets Clipart PDF
This template covers account based marketing strategy such as create content that provide value to the customers. It also depicts that Different types of target accounts require additional content focuses.Presenting Security And Performance Digital Marketing Create Content Strategy That Resonates With Targets Clipart PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Competitors Customers, Strategic Importance, Different. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
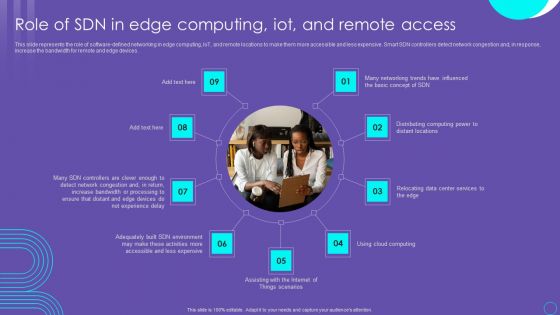
SDN Security Architecture Role Of SDN In Edge Computing Iot And Remote Access Information PDF
This slide represents the role of software defined networking in edge computing, IoT, and remote locations to make them more accessible and less expensive. Smart SDN controllers detect network congestion and, in response, increase the bandwidth for remote and edge devices. Boost your pitch with our creative SDN Security Architecture Role Of SDN In Edge Computing Iot And Remote Access Information PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Financing Catalogue For Security Underwriting Agreement Services Offered By Investment Pictures PDF
The slide comprises key services of the company which includes underwriting, general advisory, merger and acquisition advisory, asset management and sales and trading solutions. This is a financing catalogue for security underwriting agreement services offered by investment pictures pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like underwriting, advisory services, merger and acquisition, assets management, sales and trading. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Investment Banking Security Underwriting Pitchbook Senior Management Biographies And Other Details Microsoft PDF
The slide provides the name and designation of senior management teams CEO, CFO, department head etc. Of the company. It also covers brief information about their work experience, prior industry experience and education. This is a Investment Banking Security Underwriting Pitchbook Senior Management Biographies And Other Details Microsoft PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Industry Experience, Designation, Education You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Financing Catalogue For Security Underwriting Agreement Investment Banking Fee Retainer Success Guidelines PDF
The slide covers the fee structure of the company for its services. The company charges, retainer fee, success fee and other fee minimum fee, ancillary fee, non-cash payments etc. as per the transaction value of the deal. This is a financing catalogue for security underwriting agreement investment banking fee retainer success guidelines pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like minimum fee, breakup fee, ancillary fee, non cash payment. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Real Time Assessment Of Security Threats What Our Clients Say About Us Portrait PDF
This slide covers the client testimonials and what our customers have to say about our company and its services to understand the companys market reputation. This is a real time assessment of security threats what our clients say about us portrait pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like what our clients say about us. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
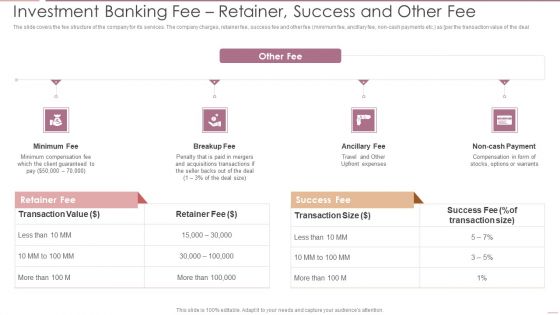
Investment Banking Security Underwriting Pitchbook Investment Banking Feer Retainer Success Demonstration PDF
The slide covers the fee structure of the company for its services. The company charges, retainer fee, success fee and other fee minimum fee, ancillary fee, non cash payments etc. as per the transaction value of the deal.This is a Investment Banking Security Underwriting Pitchbook Investment Banking Feer Retainer Success Demonstration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Minimum Compensation, Acquisitions Transactions, Compensation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security And Performance Digital Marketing Identify The Highest Value Accounts Professional PDF
This template covers the account based marketing strategies. It also depicts that identifying ideal clients and their main challenges would help company to align services suitable to clients needs.This is a Security And Performance Digital Marketing Identify The Highest Value Accounts Professional PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Target Accounts, Makers Influencers, Create Lists. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Financing Catalogue For Security Underwriting Agreement Table Of Contents Mockup PDF
Presenting financing catalogue for security underwriting agreement table of contents mockup pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like company overview, market overview, deal overview. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Corporate Security And Risk Management Workplace Employee Assistance Program Icons PDF
The employee assistance program will help firm in enhancing their well being at workplace and enable them to handle critical situations. This program will render services like clinical services, work and life services and employer services, etc. This is a corporate security and risk management workplace employee assistance program icons pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like clinical services, work and life services, employer services. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Optimization Of IoT Remote Monitoring Smart Doorbells Used For Maintaining Security IoT SS V
This slide provides an overview of the smart displays used in smart homes to monitor home activities. It further includes popular brands and factors to consider that are usage, size, resolution, cost, sound quality and energy use. Are you searching for a Optimization Of IoT Remote Monitoring Smart Doorbells Used For Maintaining Security IoT SS V that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Optimization Of IoT Remote Monitoring Smart Doorbells Used For Maintaining Security IoT SS V from Slidegeeks today.

Security Awareness New Strategies For Learning Ppt Professional Graphics Design PDF
This slide covers effective ways to build cybersafe across an organization including key programs and approaches for the learning programs.This is a security awareness new strategies for learning ppt professional graphics design pdf. template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like human centric training, continuous incremental learning. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
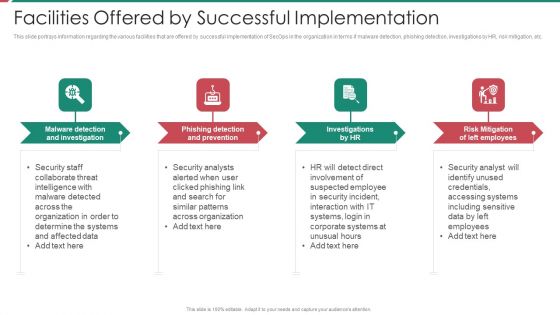
Security And Process Integration Facilities Offered By Successful Implementation Sample PDF
This slide portrays information regarding the various facilities that are offered by successful implementation of SecOps in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. This is a security and process integration facilities offered by successful implementation sample pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like malware detection and investigation, phishing detection and prevention, investigations by hr, risk mitigation of left employees. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Ensuring Nutrition Value Through Our Valuable Partners Food Security Excellence Ppt Layouts Visuals PDF
This slide provides information regarding the valuable partners associated to firm in order to render nutrition value to customers. This is a ensuring nutrition value through our valuable partners food security excellence ppt layouts visuals pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like our filed partners, resource partners, advocacy partners, technical collaboration partners. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Food Receipt And Storage To Ensure Quality Food Security Excellence Ppt Portfolio Guide PDF
This slide provides information regarding food receipt and storage to ensure food quality by handling normal and potentially hazard food. This is a food receipt and storage to ensure quality food security excellence ppt portfolio guide pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like food storage, food receipt. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
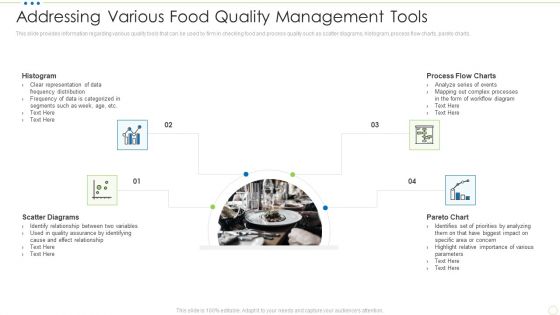
Addressing Various Food Quality Management Tools Food Security Excellence Ppt Inspiration Example PDF
This slide provides information regarding various quality tools that can be used by firm in checking food and process quality such as scatter diagrams, histogram, process flow charts, pareto charts. This is a addressing various food quality management tools food security excellence ppt inspiration example pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like scatter diagrams, histogram, process flow charts, pareto chart. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Key Features Associated To Mobile Device Management Mobile Device Security Management Mockup PDF
This slide provides information regarding key features associated to mobile device management such as mobile device enrolment, user profile management, mobile device management support. This is a Key Features Associated To Mobile Device Management Mobile Device Security Management Mockup PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Device Enrolment, Profile Management, Management Support. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
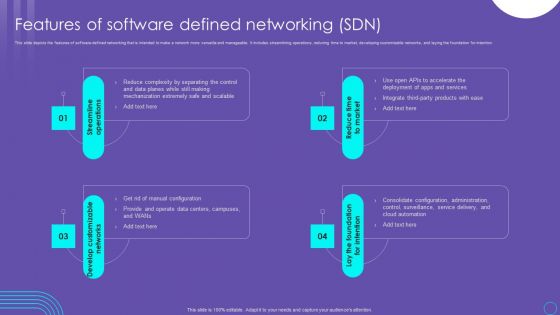
SDN Security Architecture Features Of Software Defined Networking SDN Infographics PDF
This slide depicts the features of software defined networking that is intended to make a network more versatile and manageable. It includes streamlining operations, reducing time to market, developing customizable networks, and laying the foundation for intention. This SDN Security Architecture Features Of Software Defined Networking SDN Infographics PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The SDN Security Architecture Features Of Software Defined Networking SDN Infographics PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
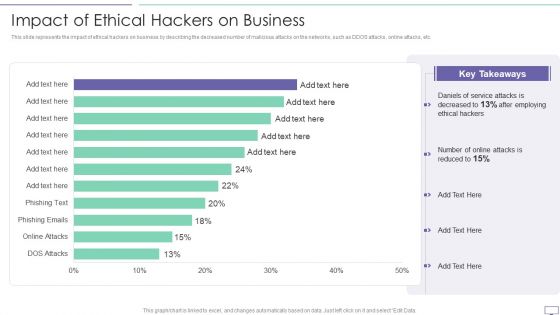
IT Security Hacker Impact Of Ethical Hackers On Business Slides PDF
This slide represents the impact of ethical hackers on business by describing the decreased number of malicious attacks on the networks, such as DDOS attacks, online attacks, etc.Deliver an awe inspiring pitch with this creative IT Security Hacker Impact Of Ethical Hackers On Business Slides PDF bundle. Topics like Key Takeaways, Daniels Of Service, After Employing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
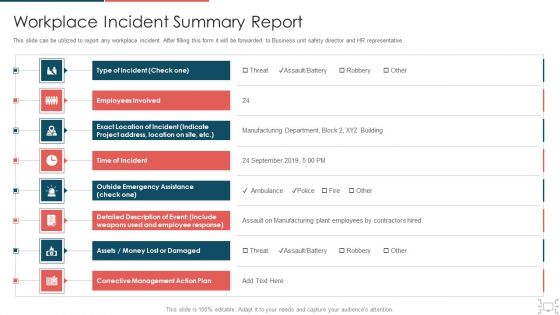
Cyber Security Administration In Organization Workplace Incident Summary Report Brochure PDF
This slide can be utilized to report any workplace incident. After filling this form it will be forwarded to Business unit safety director and HR representative. This is a cyber security administration in organization workplace incident summary report brochure pdf template with various stages. Focus and dispense information on eigt stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like incident, employees, location, emergency, assistance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Real Time Assessment Of Security Threats Fully Managed Service Model Demonstration PDF
This slide covers the SIEM as a service model wherein all the steps are taken care by our company and the client just have to provide us the relevant data. Deliver an awe inspiring pitch with this creative real time assessment of security threats fully managed service model demonstration pdf bundle. Topics like threat and vulnerability management processes, reporting, retention, correlation, collection can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Table Of Contents Exploring Investment Opportunities With Security Token Offerings Graphics Pdf
Do you know about Slidesgeeks Table Of Contents Exploring Investment Opportunities With Security Token Offerings Graphics Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

Comparative Analysis Between Bring Your Own Device Security Policy And CYOD Mobile Device Programs Clipart PDF
This slide showcases distinguish between bring your own device and choose your own device policies and programs for mobile devices. It also includes differentiation on basis such as benefits , challenges, etc. Pitch your topic with ease and precision using this Comparative Analysis Between Bring Your Own Device Security Policy And CYOD Mobile Device Programs Clipart PDF. This layout presents information on Basis, Benefits, Best Practices. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Security And Performance Digital Marketing Launch Multitouch Email Campaigns Icons PDF
This template covers content creation tactics in account based marketing such as launching multi touch campaigns, use of marketing automated tools etc.This is a Security And Performance Digital Marketing Launch Multitouch Email Campaigns Icons PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Campaign Launch, Campaign Workflow, Ensure Prospects. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
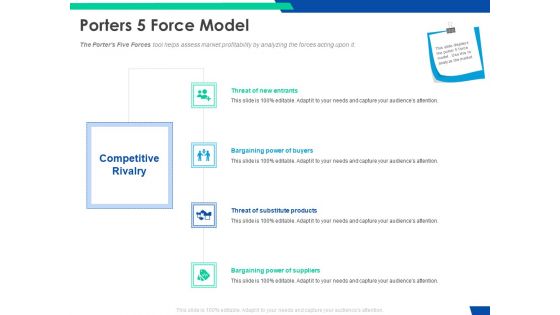
Cloud Based Email Security Market Report Porters 5 Force Model Ppt Inspiration Sample PDF
The Porters Five Forces tool helps assess market profitability by analyzing the forces acting upon it. This is a cloud based email security market report porters 5 force model ppt inspiration sample pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like threat of new entrants, bargaining power of buyers, threat of substitute products, bargaining power of suppliers. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Financing Catalogue For Security Underwriting Agreement Key Competitors Of The Company Slides PDF
The slide provides the key players in the industry by companys size Top or Large companies, mid market companies, small or boutique companies etc. It has also mentioned the companys major competitors, This is a financing catalogue for security underwriting agreement key competitors of the company slides pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like top or large investment banks, mid market investment banks, boutique investment banks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Financing Catalogue For Security Underwriting Agreement Leadership Senior Executive Team Designs PDF
The slide provides the name and designation of the key management team members CEO, CFO, Department head etc. of the company. It also provides the Major Transaction Experience work experience of the executives. This is a financing catalogue for security underwriting agreement leadership senior executive team designs pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like leadership senior executive team. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Investment Banking Security Underwriting Pitchbook Companys Strategic Decisions For IPO Issue Slides PDF
The slide covers the strategic steps taken by the company before introducing its IPO. Key strategic steps include IPO decision, IPO qualification, IPO preparation.This is a Investment Banking Security Underwriting Pitchbook Companys Strategic Decisions For IPO Issue Slides PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Cost And Benefit, Qualification Criteria, Preparation Required You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Investment Banking Security Underwriting Pitchbook Leadership Senior Executive Team Inspiration PDF
The slide provides the name and designation of the key management team members CEO, CFO, department head etc. Of the company. It also provides the major transaction experience work experience of the executives.This is a Investment Banking Security Underwriting Pitchbook Leadership Senior Executive Team Inspiration PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Transaction Experience, Designation, Introduced You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security And Performance Digital Marketing Optimize Onpage SEO Include ALT Tags For Images Infographics PDF
This template covers search engine optimization guidelines for images. It also depicts that Alt Attributes must be added at backend of the images to assists search engine crawlers in indexing. This is a Security And Performance Digital Marketing Optimize Onpage SEO Include ALT Tags For Images Infographics PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Context Descriptions, Search Engine, Assisting Indexing. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
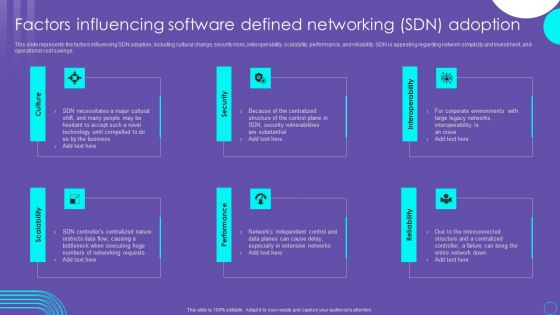
SDN Security Architecture Factors Influencing Software Defined Networking SDN Adoption Summary PDF
This slide represents the factors influencing SDN adoption, including cultural change, security risks, interoperability, scalability, performance, and reliability. SDN is appealing regarding network simplicity and investment, and operational cost savings. This modern and well arranged SDN Security Architecture Factors Influencing Software Defined Networking SDN Adoption Summary PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

SDN Security Architecture Implementation Process Of Software Defined Networking SDN Diagrams PDF
This slide outlines the implementation process of software defined networking that includes creating a use case, forming a multi functional team, testing, and reviewing. The main implementation types of SDN are open SDN, SDN via APIs, and SDN via hypervisor based overlay network. The SDN Security Architecture Implementation Process Of Software Defined Networking SDN Diagrams PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Information Systems Security And Risk Management Plan Swot Analysis Topics PDF
Retrieve professionally designed Information Systems Security And Risk Management Plan Swot Analysis Topics PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
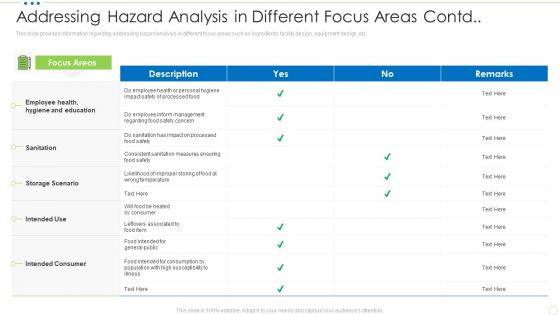
Addressing Hazard Analysis In Different Focus Areas Contd Food Security Excellence Ppt Inspiration Example PDF
This slide provides information regarding addressing hazard analysis in different focus areas such as sanitation, intended use, storage scenario, employee health and hygiene, etc. Deliver and pitch your topic in the best possible manner with this addressing hazard analysis in different focus areas contd food security excellence ppt inspiration example pdf. Use them to share invaluable insights on hygiene and education, sanitation, storage scenario, intended use, intended consumer and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Impact Analysis Overall Food Quality Improvement Food Security Excellence Ppt Gallery Graphics Template PDF
This slide provides information regarding the overall impact of quality improvement. As with quality enhancement, occurrence of defects has reduced, leading to reduction in cost of quality, increased customer satisfaction, etc. Deliver an awe inspiring pitch with this creative impact analysis overall food quality improvement food security excellence ppt gallery graphics template pdf bundle. Topics like cost, customer satisfaction, defect occurrence can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Competitive Analysis Of Home Security Firms With Premium Earned And Claim Incurred Microsoft PDF
This slide shows comparison of different house insurance companies and their net earned premium, amount and ratio of claim incurred. Pitch your topic with ease and precision using this Competitive Analysis Of Home Security Firms With Premium Earned And Claim Incurred Microsoft PDF. This layout presents information on Incurred Claim Ratio, Claims Incurred Net, Net Earned Premium. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Security Software Company Investor Funding Pitch Deck Value Proposition USP Introduction PDF
This slide showcases unique selling propositions of solution offered by IT company differentiates product from others. Differentiators are quick time-to-value , high effectiveness for detection and response , platform-as-a-service technique and have patents for Ava, EntityiQ and adversarial modeling. Explore a selection of the finest Security Software Company Investor Funding Pitch Deck Value Proposition USP Introduction PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Security Software Company Investor Funding Pitch Deck Value Proposition USP Introduction PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Cyber Security Administration In Organization Various Types Of Workplace Violence And Threats Inspiration PDF
This slide provides details regarding various types of workplace violence threats created by people in terms of stalking, physical assault, harassment or intimidation, etc. This is a cyber security administration in organization various types of workplace violence and threats inspiration pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like physical, threatening, behavior, stalking, harassment. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

cyber security administration in organization determine sequence phases for threat attack infographics pdf
This slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. This is a cyber security administration in organization determine sequence phases for threat attack infographics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like internal, threat, perform, phishing, combination . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

cyber security administration in organization how financial risk can be controlled inspiration pdf
This slide provides details regarding various ways through financial risks can be controlled by handling liquidity risk, foreign exchange risk and credit exchange risk. This is a cyber security administration in organization how financial risk can be controlled inspiration pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like handling, liquidity, financial, flexibility, structure . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

cyber security administration in organization roles and responsibilities to ensure work environment slides pdf
This slide provides details regarding roles and responsibilities assigned to ensure minimum violence work environment This is a cyber security administration in organization roles and responsibilities to ensure work environment slides pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like responsibilities, manager, assessment, manager. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Corporate Security And Risk Management Determine Threat Management Team Structure Topics PDF
The threat management team generally comprise of senior management personnel that have authority and resources to accelerate the companys internal incident response. They will be responsible in managing human impacts both employees and community, company reputation, share values, and corporate assets. This is a corporate security and risk management determine threat management team structure topics pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like determine threat management team structure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Real Time Assessment Of Security Threats Our Management Team Graphics PDF
This slide covers the details of the management team along with their job profile and brief description about their work. This is a real time assessment of security threats our management team graphics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like our management team. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
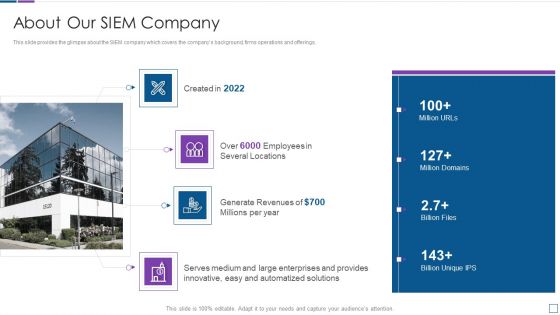
Real Time Assessment Of Security Threats About Our SIEM Company Structure PDF
This slide provides the glimpse about the SIEM company which covers the companys background, firms operations and offerings. This is a real time assessment of security threats about our siem company structure pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like about our siem company. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
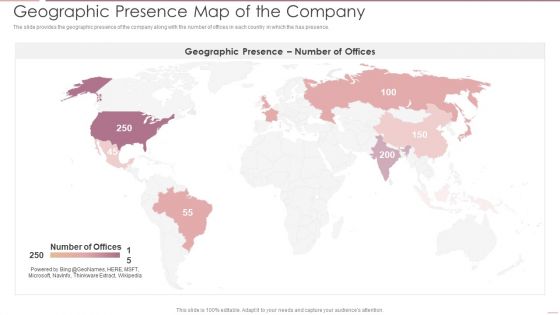
Investment Banking Security Underwriting Pitchbook Geographic Presence Map Of The Company Designs PDF
The slide provides the geographic presence of the company along with the number of offices in each country in which the has presence.This is a Investment Banking Security Underwriting Pitchbook Geographic Presence Map Of The Company Designs PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Geographic Presence, Map Company You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Investment Banking Security Underwriting Pitchbook Investment Bank Underwriting Overview Topics PDF
The slide provides the key points related to underwriting agreement between the company and the investment bank. Key points covered in the slide includes type of offering, underwriting fee, number of banks involved in the deal etc. This is a Investment Banking Security Underwriting Pitchbook Investment Bank Underwriting Overview Topics PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Investment Banks, Firm Commitment, Underwriting Fee You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Assessment Theft Or Loss Of Intellectual Property Formats PDF
This slide represents the loss of intellectual property threat and how organizations get affected by these types of risks.This is a Cloud Security Assessment Theft Or Loss Of Intellectual Property Formats PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Intellectual Property, Examination Uncovered, Danger Presented. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security And Performance Digital Marketing Align And Position Account For Linkedin Marketing Mockup PDF
This template covers first step for LinkedIn marketing such as update company profile and position the company account according to the target audience. This is a Security And Performance Digital Marketing Align And Position Account For Linkedin Marketing Mockup PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Profiles Position, Target Audience, Account According. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security And Performance Digital Marketing Facebook And Instagram Advertising Audit The Company Profile Mockup PDF
This template covers Facebook and Instagram marketing strategy. All these sections on Facebook, Instagram pages add an important value to the business. This is a Security And Performance Digital Marketing Facebook And Instagram Advertising Audit The Company Profile Mockup PDF template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Conducting Events, Regularly Post, Corporate Announcements. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security And Performance Digital Marketing Structure Of Facebook Campaigns Clipart PDF
This template depicts that Facebook Ads needs three parts to run such as a campaign, ad set, and ad. All these parts are called campaign structure and help run ads the way the company wants and reach the right prospects.his is a Security And Performance Digital Marketing Structure Of Facebook Campaigns Clipart PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Powerful Consisting, Features Campaigns, Define Creative. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security And Performance Digital Marketing Use Existing Email Lists To Launch Retargeting Campaigns Clipart PDF
This template depicts that by uploading existing email lists to Google, Facebook, and LinkedIn, user may target those customers with display advertising or create fresh unique lookalike audiences. This is a Security And Performance Digital Marketing Use Existing Email Lists To Launch Retargeting Campaigns Clipart PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Lookalike Audience, Retargeted Advertising, Lookalike Retargeting. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
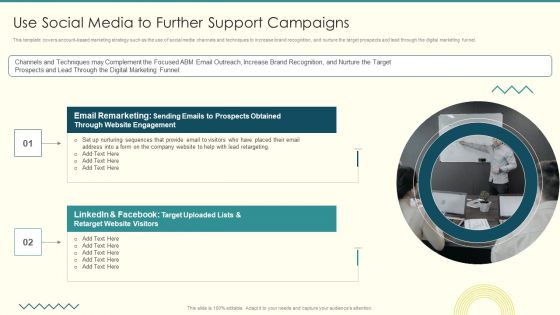
Security And Performance Digital Marketing Use Social Media To Further Support Campaigns Clipart PDF
This template covers account-based marketing strategy such as the use of social media channels and techniques to increase brand recognition, and nurture the target prospects and lead through the digital marketing funnel.This is a Security And Performance Digital Marketing Use Social Media To Further Support Campaigns Clipart PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Prospects Obtained, Nurturing Sequences, Channels Techniques. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Organizational Network Staff Learning Security Awareness New Strategies For Learning Rules PDF
This slide cover effective way to build cybersafe across on organization including key programs and approaches for the learning programs. Deliver an awe-inspiring pitch with this creative organizational network staff learning security awareness new strategies for learning rules pdf bundle. Topics like human centric training, manage and control, targeted training can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Determine Various Mobile Devices Existing At Workplace Mobile Device Security Management Guidelines PDF
The employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. Deliver an awe inspiring pitch with this creative Determine Various Mobile Devices Existing At Workplace Mobile Device Security Management Guidelines PDF bundle. Topics like Corporate Data, Allowed Employees, Consumerization Technology can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Techniques And Strategies To Reduce Security Management Risks Table Of Contents Structure PDF
Presenting techniques and strategies to reduce security management risks table of contents structure pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like identifying goals and objectives, risk assessment and analysis, adopting access controls. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
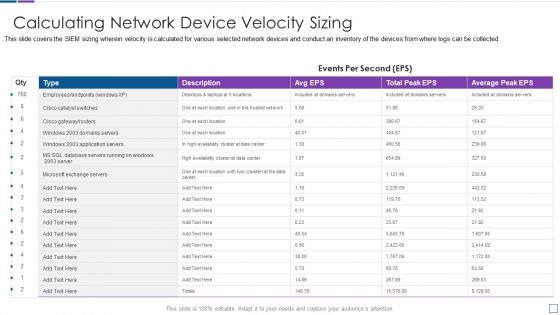
Real Time Assessment Of Security Threats Calculating Network Device Velocity Sizing Portrait PDF
This slide covers the SIEM sizing wherein velocity is calculated for various selected network devices and conduct an inventory of the devices from where logs can be collected. Deliver an awe inspiring pitch with this creative real time assessment of security threats calculating network device velocity sizing portrait pdf bundle. Topics like calculating network device velocity sizing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
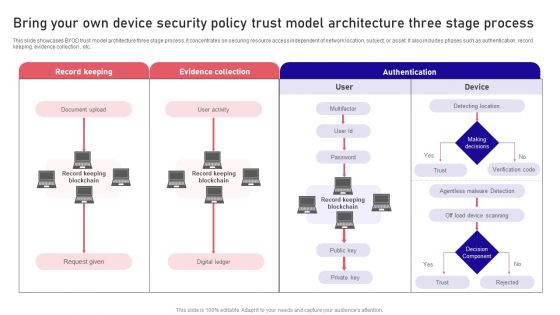
Bring Your Own Device Security Policy Trust Model Architecture Three Stage Process Rules PDF
This slide showcases BYOD trust model architecture three stage process, it concentrates on securing resource access independent of network location, subject, or asset. It also includes phases such as authentication, record keeping. evidence collection , etc. Persuade your audience using this Bring Your Own Device Security Policy Trust Model Architecture Three Stage Process Rules PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Record Keeping, Evidence Collection, Authentication . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Three Levels Vertical Layout For Network Security Phases Ppt PowerPoint Presentation Portfolio Background Designs PDF
Persuade your audience using this three levels vertical layout for network security phases ppt powerpoint presentation portfolio background designs pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including detect block defend, discover enforce harden, scope contain remediate. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

IPO Process Layout For Network Security Issues Ppt PowerPoint Presentation Outline Graphics Template PDF
Persuade your audience using this ipo process layout for network security issues ppt powerpoint presentation outline graphics template pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including processing, output, input. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
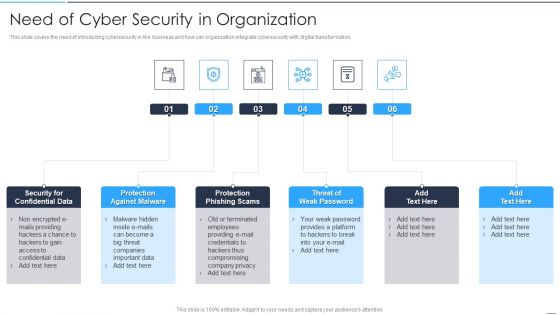
Accelerate Online Journey Now Need Of Cyber Security In Organization Professional PDF
This slide covers the need of introducing cybersecurity in the business and how can organization integrate cybersecurity with digital transformation.Presenting Accelerate Online Journey Now Need Of Cyber Security In Organization Professional PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Confidential Data, Against Malware, Phishing Scams In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Most Common Air Compressor Workplace Safety Protocol And Security Practices Microsoft Pdf
This slide highlights the common air compressor hazards which includes electrical dangers, fumes from diesel air compressor, high pressure injection and high noise form air compressor Are you searching for a Most Common Air Compressor Workplace Safety Protocol And Security Practices Microsoft Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Most Common Air Compressor Workplace Safety Protocol And Security Practices Microsoft Pdf from Slidegeeks today.

Coordination With Contractors Workplace Safety Protocol And Security Practices Ideas Pdf
This slide highlights the coordination with contractors and staffing center by host employer which includes establish effective communication and establish coordination with agencies. If you are looking for a format to display your unique thoughts, then the professionally designed Coordination With Contractors Workplace Safety Protocol And Security Practices Ideas Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Coordination With Contractors Workplace Safety Protocol And Security Practices Ideas Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Table Of Contents For Deploying Cyber Security Incident Response Administration Gap Sample PDF
Find highly impressive Table Of Contents For Deploying Cyber Security Incident Response Administration Gap Sample PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Table Of Contents For Deploying Cyber Security Incident Response Administration Gap Sample PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

KYC Transaction Monitoring System Business Security Analyzing Impact Of Money Laundering Guidelines PDF
This slide analyzing impact of money laundering on economy. It provides information about placement, layering, integration, global GDP, income distribution, tax revenues, growth rate, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable KYC Transaction Monitoring System Business Security Analyzing Impact Of Money Laundering Guidelines PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
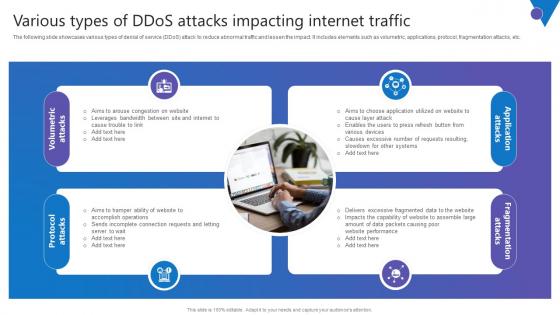
Various Types Of DDoS Attacks Comprehensive Guide To Blockchain Digital Security Introduction Pdf
The following slide showcases various types of denial of service DDoS attack to reduce abnormal traffic and lessen the impact. It includes elements such as volumetric, applications, protocol, fragmentation attacks, etc. Get a simple yet stunning designed Various Types Of DDoS Attacks Comprehensive Guide To Blockchain Digital Security Introduction Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Various Types Of DDoS Attacks Comprehensive Guide To Blockchain Digital Security Introduction Pdf can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Firewall As A Service Technology Solution Providers Network Security Pictures Pdf
This slide demonstrates the top Firewall-as-a-Service technology providers. The purpose of this slide is to outline various solutions available for integrating FWaaS in organizations network. These are Fortinet, Palo Alto, Cisco, Sophos and GFI Software. Make sure to capture your audiences attention in your business displays with our gratis customizable Firewall As A Service Technology Solution Providers Network Security Pictures Pdf. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Mitigation Plan For Resolving Encountered Threat Information Security Risk Administration Diagrams PDF
Mentioned slide shows mitigation plan for resolving encountered threat. It covers details about encountered threat, its description, risk level, mitigation plan, resources required, responsible person, expected resolution time and communication mode.Slidegeeks has constructed Mitigation Plan For Resolving Encountered Threat Information Security Risk Administration Diagrams PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Case Competition Overpower The Obstacle Of Cyber Security In Medicare Table Of Contents Guidelines PDF
Deliver an awe inspiring pitch with this creative case competition overpower the obstacle of cyber security in medicare table of contents guidelines pdf bundle. Topics like swot analysis of abs healthcare company, abs healthcare company competitive analysis, abs healthcare company challenges and their solutions can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Damage Security Insurance Proposal Table Of Content Ppt Styles Graphics Example PDF
Presenting damage security insurance proposal table of content ppt styles graphics example pdf to provide visual cues and insights. Share and navigate important information on twelve stages that need your due attention. This template can be used to pitch topics like prices, insurance, offerings, client testimonials, major clients. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Table Of Contents For Business Mobile Device Security Management And Mitigation Sample PDF
If you are looking for a format to display your unique thoughts, then the professionally designed Table Of Contents For Business Mobile Device Security Management And Mitigation Sample PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Table Of Contents For Business Mobile Device Security Management And Mitigation Sample PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
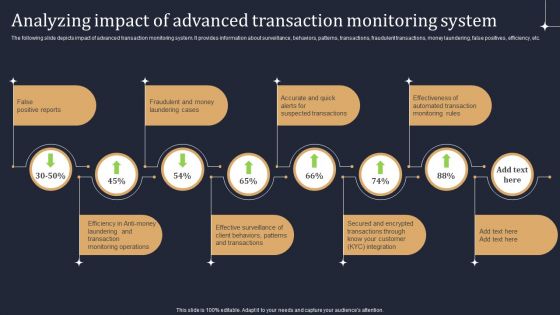
KYC Transaction Monitoring System Business Security Analyzing Impact Of Advanced Transaction Guidelines PDF
The following slide depicts impact of advanced transaction monitoring system. It provides information about surveillance, behaviors, patterns, transactions, fraudulent transactions, money laundering, false positives, efficiency, etc. Boost your pitch with our creative KYC Transaction Monitoring System Business Security Analyzing Impact Of Advanced Transaction Guidelines PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Cyber Security Plan Implementation Timeline Ppt PowerPoint Presentation File Infographic Template PDF
The following slide presents the cyber security program execution timeline to organize tasks and ensure timely execution. It includes activities such as updating systems and passwords, performing penetration test, checking disaster recovery system, conducting training etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Cyber Security Plan Implementation Timeline Ppt PowerPoint Presentation File Infographic Template PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Methods To Ensure Smart Comprehensive Guide To Blockchain Digital Security Mockup Pdf
The following slide showcases some tips and practices to ensure smart contract security. It includes elements such as careful rollouts, keeping them simple, updating and monitoring new developments, reviewing fundamental tradeoffs, etc. This modern and well arranged Methods To Ensure Smart Comprehensive Guide To Blockchain Digital Security Mockup Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Comparative Assessment Of ZTNA Version 10 And 20 Zero Trust Network Security Infographics Pdf
This slide represents the comparison between zero trust network access versions 1.0 and 2.0. The purpose of this slide is to demonstrate the overview of both versions, including differences. It also includes the architecture of both versions of zero-trust network access. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Comparative Assessment Of ZTNA Version 10 And 20 Zero Trust Network Security Infographics Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
Strategies We Will Implement To Make Security Awareness Training Interactive Structure PDF
The purpose of this slide is to exhibit variety of strategies which can be used to engage employees in the security awareness training plan. The strategies highlighted in the slide are gamification, personalization, high-quality content and variety. Explore a selection of the finest Strategies We Will Implement To Make Security Awareness Training Interactive Structure PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Strategies We Will Implement To Make Security Awareness Training Interactive Structure PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Impact Of Eclipse Attack Comprehensive Guide To Blockchain Digital Security Demonstration Pdf
The following slide illustrates the impact of eclipse attack on functioning of blockchain network to plan strategies and action steps. It includes elements such as leading to double spending, centralization, disrupting mining power, network instability, monetary loss, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Impact Of Eclipse Attack Comprehensive Guide To Blockchain Digital Security Demonstration Pdf With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Impact Of Eclipse Attack Comprehensive Guide To Blockchain Digital Security Demonstration Pdf today and make your presentation stand out from the rest
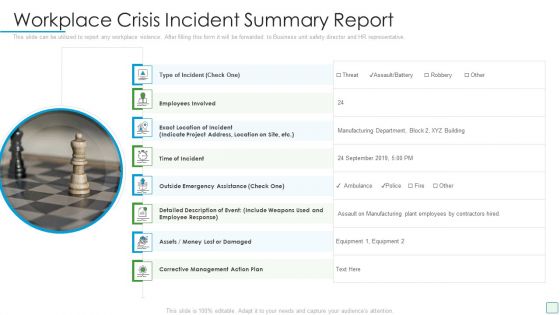
Developing Firm Security Strategy Plan Workplace Crisis Incident Summary Report Professional PDF
This slide can be utilized to report any workplace violence. After filling this form it will be forwarded to Business unit safety director and HR representative. Presenting developing firm security strategy plan workplace crisis incident summary report professional pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like management action plan, time of incident, employees involved, outside emergency assistance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
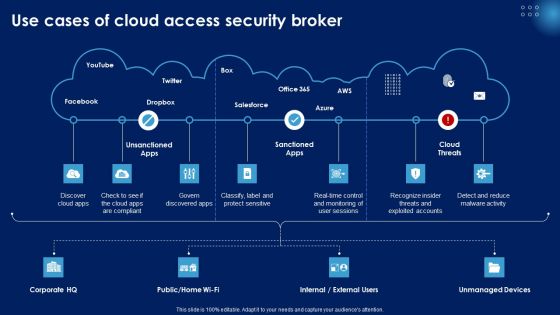
Use Cases Of Cloud Access Security Broker Ppt PowerPoint Presentation Diagram Graph Charts PDF
Find highly impressive Use Cases Of Cloud Access Security Broker Ppt PowerPoint Presentation Diagram Graph Charts PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Use Cases Of Cloud Access Security Broker Ppt PowerPoint Presentation Diagram Graph Charts PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
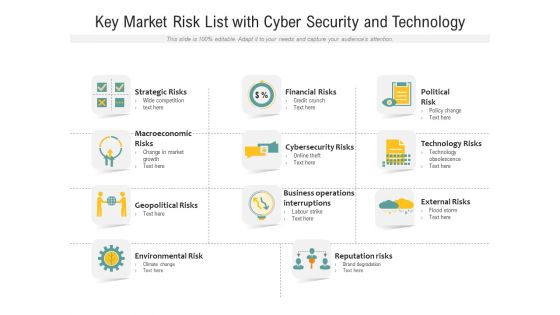
Key Market Risk List With Cyber Security And Technology Ppt PowerPoint Presentation File Show PDF
Showcasing this set of slides titled key market risk list with cyber security and technology ppt powerpoint presentation file show pdf. The topics addressed in these templates are strategic risks, macroeconomic, geopolitical risks, environmental risk, financial risks, cybersecurity risks, political risk, technology risks. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Table Of Contents For Investment Banking Security Underwriting Pitchbook Guidelines PDF
Presenting Table Of Contents For Investment Banking Security Underwriting Pitchbook Guidelines PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Deal Overview, Senior Management, Consolidated IncomeIn addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
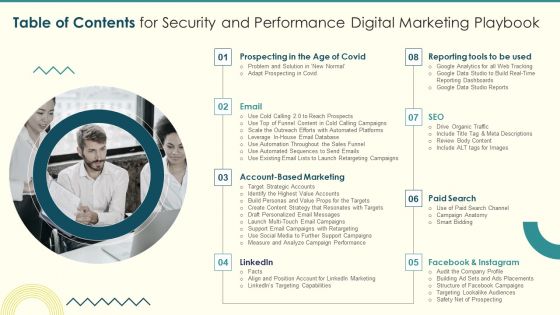
Table Of Contents For Security And Performance Digital Marketing Playbook Rules PDF
Presenting Table Of Contents For Security And Performance Digital Marketing Playbook Rules PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Automation Throughout, Automated Sequences, Reporting Dashboards. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Access Security Broker Pillar Visibility Ppt PowerPoint Presentation File Infographics PDF
This slide outlines the overview of the visibility pillar of cloud access security broker. The purpose of this slide is to showcase the working process of the visibility pillar of CASB and it also represents the topography of CASB visibility. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Cloud Access Security Broker Pillar Visibility Ppt PowerPoint Presentation File Infographics PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Key Points To Choose Zero Trust Solution Zero Trust Network Security Formats Pdf
This slide highlights the main criteria while choosing the right zero trust solution for the organization. The purpose of this slide is to showcase the key points the businesses should keep in mind while selecting the ZTNA vendor. The main points include vendor support, zero trust technology type, and so on. This modern and well-arranged Key Points To Choose Zero Trust Solution Zero Trust Network Security Formats Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Cyber Security Risk Management Plan Incident Management Workflow Process Diagram Infographics PDF
Following slide presents the incident management workflow of the firm. It covers five phases namely incident occurrence, team organizing, action taken, incident resolution and fail over report. Presenting cyber security risk management plan incident management workflow process diagram infographics pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like fail over report, incident resolution, organize your team, incident occurs, team takes action. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
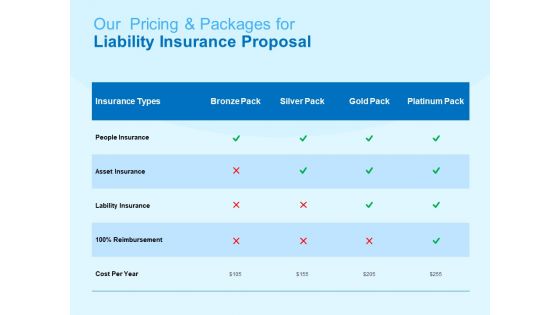
Damage Security Insurance Proposal Our Pricing And Packages For Liability Insurance Proposal Ppt Professional Example PDF
Deliver an awe inspiring pitch with this creative damage security insurance proposal our pricing and packages for liability insurance proposal ppt professional example pdf bundle. Topics like people insurance, assets insurance, liability insurance can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Info Security Update And Installation Of Antivirus Software Ppt PowerPoint Presentation File Designs PDF
This slide depicts the benefits of using antivirus software in the organization, different antivirus software available in the market, and their usage by a graph. Deliver and pitch your topic in the best possible manner with this info security update and installation of antivirus software ppt powerpoint presentation file designs pdf. Use them to share invaluable insights on antivirus software usage chart across us, choose best antivirus, organization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Icons Slide Building Security Awareness Among Workforce To Minimize Cybersecurity Threats Elements PDF
Introducing our well designed Icons Slide Building Security Awareness Among Workforce To Minimize Cybersecurity Threats Elements PDF set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.

Table Of Contents For Working Space And FM Services Security Summary PDF
Find highly impressive Table Of Contents For Working Space And FM Services Security Summary PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Table Of Contents For Working Space And FM Services Security Summary PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Agenda Development And Integration Of Cyber Security Incident Administration Information PDF
Slidegeeks is here to make your presentations a breeze with Agenda Development And Integration Of Cyber Security Incident Administration Information PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Implementing Cybersecurity Awareness Program To Prevent Attacks Key Statistics Showing The Impact Of Security Clipart PDF
This modern and well arranged Implementing Cybersecurity Awareness Program To Prevent Attacks Key Statistics Showing The Impact Of Security Clipart PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Security And Human Resource Services Business Profile Mission Vision And Core Values Pictures PDF
This slide highlights the security company long term and short term objectives which includes trust, collaboration, service, and innovation as base of core values Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Security And Human Resource Services Business Profile Mission Vision And Core Values Pictures PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Security And Human Resource Services Business Profile Mission Vision And Core Values Pictures PDF.
Security And Human Resource Services Business Profile Weapon And Logistics Vehicle Icons PDF
This slide highlights the security company weapon and logistics vehicle details which includes repeater, MG16, doble cabin car, bullet proof vehicle, and patrolling vehicle. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Security And Human Resource Services Business Profile Weapon And Logistics Vehicle Icons PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Security And Human Resource Services Business Profile Weapon And Logistics Vehicle Icons PDF.
Icons Slide For Security Officer Service Company Profile Ppt PowerPoint Presentation File Display PDF
Introducing our well designed Icons Slide For Security Officer Service Company Profile Ppt PowerPoint Presentation File Display PDF set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
Case Study 4 Improving Patient Security And Reducing Risk Of Violence Icons PDF
Deliver an awe inspiring pitch with this creative case study 4 improving patient security and reducing risk of violence icons pdf bundle. Topics like power management, white space management, building management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Table Of Contents IT Security Automation Systems Guide Layer Clipart PDF
Welcome to our selection of the Table Of Contents IT Security Automation Systems Guide Layer Clipart PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

Incident Response Techniques Deployement Cyber Security Crisis Management Action Plan Timeline Rules PDF
This slide represents the timeline of effective management and minimization of impact of cyber security incidents on the business of the company. It includes details related to incident response, business continuity and review and recovery. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Incident Response Techniques Deployement Cyber Security Crisis Management Action Plan Timeline Rules PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Security And Performance Digital Marketing Facts About Linkedin As Number One For Lead Generation Themes PDF
This template covers statistics about LinkedIn as number one social media platform for lead generation, B2B marketing, posting articles, blogs and videos. Deliver an awe inspiring pitch with this creative Security And Performance Digital Marketing Facts About Linkedin As Number One For Lead Generation Themes PDF bundle. Topics like Professionally Relevant, Executives Rate, Media Comes can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
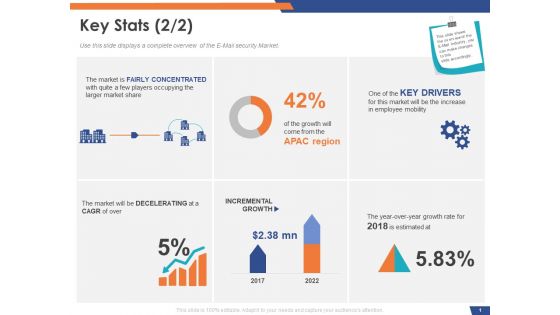
Email Security Market Research Report Key Stats Ppt Gallery Design Inspiration PDF
Presenting this set of slides with name email security market research report key stats ppt gallery design inspiration pdf. The topics discussed in these slides are incremental growth, key drivers, the market is fairly concentrated with quite a few players occupying the larger market share. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Program Evaluation Templates Bundle Security Checklist Ppt Outline Graphics Tutorials PDF
Deliver and pitch your topic in the best possible manner with this program evaluation templates bundle security checklist ppt outline graphics tutorials pdf. Use them to share invaluable insights on project it project, human threats, general threats and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
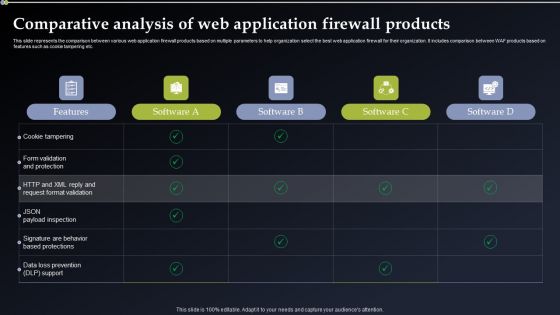
Deploying Cyber Security Incident Response Administration Comparative Analysis Of Web Application Graphics PDF
This slide represents the comparison between various web application firewall products based on multiple parameters to help organization select the best web application firewall for their organization. It includes comparison between WAF products based on features such as cookie tampering etc. This Deploying Cyber Security Incident Response Administration Comparative Analysis Of Web Application Graphics PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Deploying Cyber Security Incident Response Administration Comparative Analysis Of Web Application Graphics PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today.

Table Of Contents For Cyber Physical System To Enhance Security Portrait PDF
Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Table Of Contents For Cyber Physical System To Enhance Security Portrait PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Table Of Contents For Cyber Physical System To Enhance Security Portrait PDF.
Icons Slide For Cloud Based Email Security Market Report Ppt Infographics Graphic Images PDF
Introducing our well designed icons slide for cloud based email security market report ppt infographics graphic images pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.

Construction Engineering And Industrial Facility Management 4 Dimensions Of Infrastructure Security Graphics PDF
Deliver an awe inspiring pitch with this creative construction engineering and industrial facility management 4 dimensions of infrastructure security graphics pdf bundle. Topics like structured, unstructured, systems applications can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Icons Slides For Case Competition Overpower The Obstacle Of Cyber Security In Medicare Microsoft PDF
Deliver an awe inspiring pitch with this creative icons slides for case competition overpower the obstacle of cyber security in medicare microsoft pdf bundle. Topics like Icons can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Management Plan Steps In Detail Adopting Access Controls Clipart PDF
Deliver and pitch your topic in the best possible manner with this Security management plan steps in detail adopting access controls clipart pdf. Use them to share invaluable insights on logical access controls, physical access controls, control implementation costs and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Guidelines To Create An Advanced Security Management Plan Icons Slide Diagrams PDF
Introducing our well designed guidelines to create an advanced security management plan icons slide diagrams pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
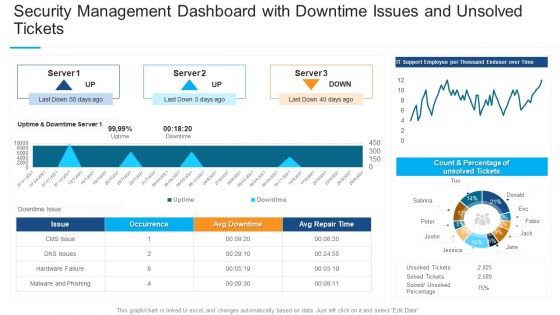
Security Management Dashboard With Downtime Issues And Unsolved Tickets Professional PDF
Deliver and pitch your topic in the best possible manner with this security management dashboard with downtime issues and unsolved tickets professional pdf. Use them to share invaluable insights on occurrence, malware and phishing, count and percentage and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
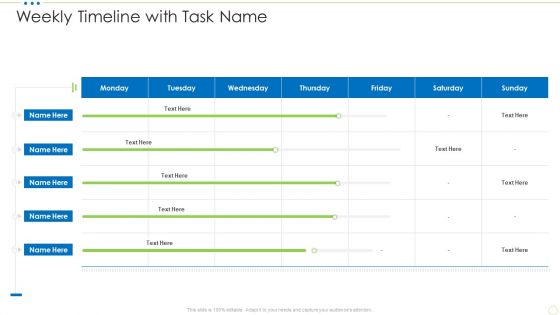
Weekly Timeline With Task Name Food Security Excellence Ppt Ideas Professional PDF
Deliver an awe inspiring pitch with this creative weekly timeline with task name food security excellence ppt ideas professional pdf bundle. Topics like weekly timeline with task name can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Developing Firm Security Strategy Plan Weekly Timeline With Task Name Clipart PDF
Deliver an awe inspiring pitch with this creative developing firm security strategy plan weekly timeline with task name clipart pdf bundle. Topics like weekly timeline with task name can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Icons Slide For Financing Catalogue For Security Underwriting Agreement Pictures PDF
Download our innovative and attention grabbing icons slide for financing catalogue for security underwriting agreement pictures pdf template. The set of slides exhibit completely customizable icons. These icons can be incorporated into any business presentation. So download it immediately to clearly communicate with your clientele.
Icons Slide For Techniques And Strategies To Reduce Security Management Risks Designs PDF
Introducing our well designed icons slide for techniques and strategies to reduce security management risks designs pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
Icons Slide For Smart Home Security Solutions Company Profile Structure PDF
Introducing our well designed Icons Slide For Smart Home Security Solutions Company Profile Structure PDF set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
Icons Slide For Security Alarm And Monitoring Systems Company Profile Inspiration PDF
Introducing our well designed Icons Slide For Security Alarm And Monitoring Systems Company Profile Inspiration PDF set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
Icons Slide For Security Automation To Analyze And Mitigate Cyberthreats Structure PDF
Introducing our well designed Icons Slide For Security Automation To Analyze And Mitigate Cyberthreats Structure PDF set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
Icons Slide For Deploying Cyber Security Incident Response Administration Elements PDF
Introducing our well designed Icons Slide For Deploying Cyber Security Incident Response Administration Elements PDF set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
Icons Slide For SDN Security Architecture Ppt PowerPoint Presentation File Model PDF
Introducing our well designed Icons Slide For SDN Security Architecture Ppt PowerPoint Presentation File Model PDF set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
Icons Slide Development And Integration Of Cyber Security Incident Administration Slides PDF
Introducing our well designed Icons Slide Development And Integration Of Cyber Security Incident Administration Slides PDF set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
Icons Slide For Comprehensive Guide To Blockchain Digital Security Risk Management Professional Pdf
Introducing our well designed Icons Slide For Comprehensive Guide To Blockchain Digital Security Risk Management Professional Pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.

Incident Response Techniques Deployement Comparative Analysis Of Cyber Security Incident Mitigation Software Summary PDF
This slide represents the comparison between various cyber security incident management softwares based on multiple parameters to help organization select the best incident management software for their organization. It includes comparison between softwares based on user rating, price, mobile support etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Incident Response Techniques Deployement Comparative Analysis Of Cyber Security Incident Mitigation Software Summary PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Software Development Life Cycle Planning Prioritized Cyber Security Threats With Risk Mitigation Plan Template PDF
This slide highlights the cyber security threats with key risks and their mitigation plan and owner with risk reduction timeline. Explore a selection of the finest Software Development Life Cycle Planning Prioritized Cyber Security Threats With Risk Mitigation Plan Template PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Software Development Life Cycle Planning Prioritized Cyber Security Threats With Risk Mitigation Plan Template PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Cloud Access Security Broker Working Process Ppt PowerPoint Presentation File Infographic Template PDF
This slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Find highly impressive Cloud Access Security Broker Working Process Ppt PowerPoint Presentation File Infographic Template PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Cloud Access Security Broker Working Process Ppt PowerPoint Presentation File Infographic Template PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Internet Security Threat Analysis With Tactics And Victims Ppt PowerPoint Presentation Infographic Template Format Ideas PDF
Showcasing this set of slides titled internet security threat analysis with tactics and victims ppt powerpoint presentation infographic template format ideas pdf. The topics addressed in these templates are fake installation, hack the bidding models, hack the identity. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Training Plan For Cyber Security Cases Action Plan Response Team Ppt PowerPoint Presentation Gallery Format PDF
This slide highlights schedule for training team to handle cyber security incidents in the company. The purpose of this template is to provide an overview on training program conducted by the company. It includes elements such as training topics covered, requirements along with duration of videos and certification post training. Persuade your audience using this Training Plan For Cyber Security Cases Action Plan Response Team Ppt PowerPoint Presentation Gallery Format PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Training Learnings, Training Requirements, Training Details. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
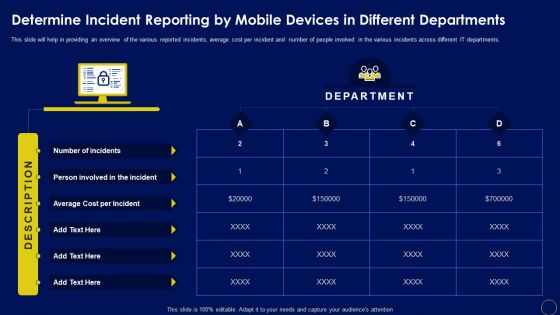
Determine Incident Reporting By Mobile Devices In Business Mobile Device Security Management Designs PDF
This slide will help in providing an overview of the various reported incidents, average cost per incident and number of people involved in the various incidents across different IT departments. Are you searching for a Determine Incident Reporting By Mobile Devices In Business Mobile Device Security Management Designs PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you ve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Determine Incident Reporting By Mobile Devices In Business Mobile Device Security Management Designs PDF from Slidegeeks today.
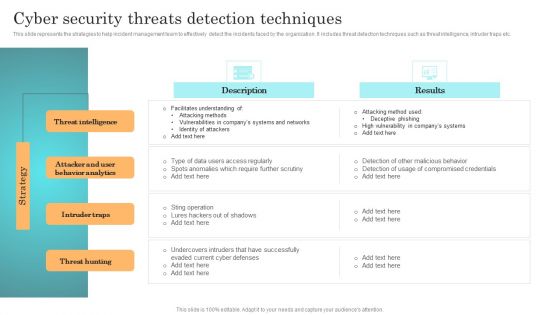
Incident Response Techniques Deployement Cyber Security Threats Detection Techniques Portrait PDF
This slide represents the strategies to help incident management team to effectively detect the incidents faced by the organization. It includes threat detection techniques such as threat intelligence, intruder traps etc. Are you searching for a Incident Response Techniques Deployement Cyber Security Threats Detection Techniques Portrait PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Incident Response Techniques Deployement Cyber Security Threats Detection Techniques Portrait PDF from Slidegeeks today.

Development And Integration Of Cyber Security Incident Administration Ppt PowerPoint Presentation Complete Deck
Landing corporate business deals can be a huge achievement, both in terms of reputation and finance. This highlights the importance of drafting a comprehensive plan for this business segment that this Development And Integration Of Cyber Security Incident Administration Ppt PowerPoint Presentation Complete Deck does perfectly for you. Given below is a perfectly curated service proposal in Seventy slides that is sure to give your presentation the desired edge. It will display all the details enabling the company to analyze standout components and make an informed decision. The presentation template is also equipped to do this with its 100 percent editable and customizable capability. Download now.
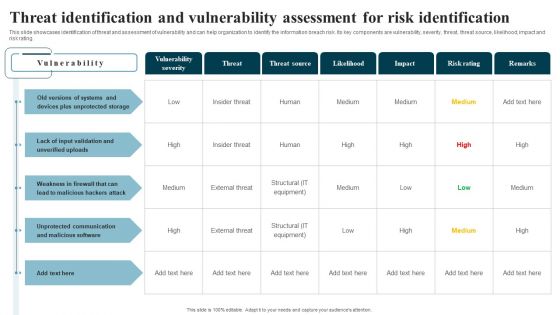
Developing IT Security Strategy Threat Identification And Vulnerability Assessment For Risk Pictures PDF
This slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating. The Developing IT Security Strategy Threat Identification And Vulnerability Assessment For Risk Pictures PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

IT Security Automation Tools Integration Ppt PowerPoint Presentation Complete Deck With Slides
This complete deck covers various topics and highlights important concepts. It has PPT slides which cater to your business needs. This complete deck presentation emphasizes IT Security Automation Tools Integration Ppt PowerPoint Presentation Complete Deck With Slides and has templates with professional background images and relevant content. This deck consists of total of fourty two slides. Our designers have created customizable templates, keeping your convenience in mind. You can edit the colour, text and font size with ease. Not just this, you can also add or delete the content if needed. Get access to this fully editable complete presentation by clicking the download button below.

Dashboard For Insider Threat In Cyber Security Cases Management Background PDF
This slide shows insider threat dashboard for managing multiple cases. It provides information such as active and closed, high and low risk cases, status, user, case time, policy alerts, content update, etc. Showcasing this set of slides titled Dashboard For Insider Threat In Cyber Security Cases Management Background PDF. The topics addressed in these templates are Total Policy Alerts, High, Low, Time Case Opened. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cybersecurity Operations Cybersecops Steps To Build Security Operations Center Structure PDF
This slide represents the main steps to developing a security operations center. The purpose of this slide is to highlight the main building steps involved in a SecOps creation. These steps include selecting a service model, location, technology, people and processes. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Cybersecurity Operations Cybersecops Steps To Build Security Operations Center Structure PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Incident Response Techniques Deployement Key Lessons Learned By Organization From Cyber Security Incident Formats PDF
This slide represents the key takeaways for the cyber security incident management team after they effectively respond to and manage the cyber attacks experienced by the organization. It includes key lessons learned by organization such as ransomware is here to stay etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Incident Response Techniques Deployement Key Lessons Learned By Organization From Cyber Security Incident Formats PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Security Risk Analysis Model With Metrics Ppt PowerPoint Presentation Outline Designs PDF
Persuade your audience using this security risk analysis model with metrics ppt powerpoint presentation outline designs pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including automated discovery, define system relationships, automated asset classification. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Corporate Security And Risk Management Budget For Effective Threat Management At Workplace Portrait PDF
Firm has prepared a budget for managing cybersecurity by optimizing various functional areas. It also provides information about the software used and the duration required for implementation. Deliver an awe inspiring pitch with this creative corporate security and risk management budget for effective threat management at workplace portrait pdf bundle. Topics like incident management, risk management, client onboarding process, document management, information management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Insider Threat In Cyber Security Management Plan With Case Status Graphics PDF
This slide shows plan for managing insider risk with case status. It provides information about users, alert, status, severity, time detected, action plan, etc. Pitch your topic with ease and precision using this Insider Threat In Cyber Security Management Plan With Case Status Graphics PDF. This layout presents information on Requires Review, Action Plan, Case Status. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
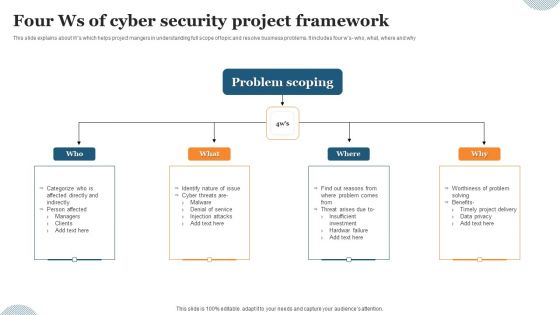
Four Ws Of Cyber Security Project Framework Ppt Pictures Graphic Images PDF
This slide explains about Ws which helps project mangers in understanding full scope of topic and resolve business problems. It includes four ws- who, what, where and why. Presenting Four Ws Of Cyber Security Project Framework Ppt Pictures Graphic Images PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Problem Scoping, Denial Service, Injection Attacks. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
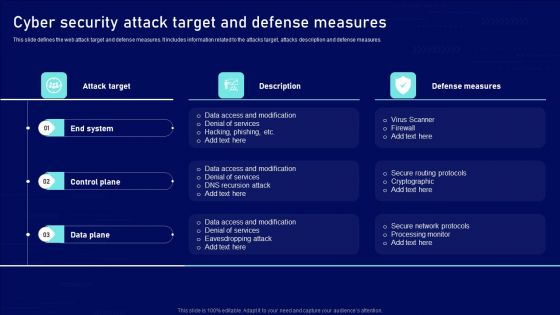
Cyber Security Attack Target And Defense Measures Ppt Infographic Template Background Image PDF
This slide defines the web attack target and defense measures. It includes information related to the attacks target, attacks description and defense measures. Showcasing this set of slides titled Cyber Security Attack Target And Defense Measures Ppt Infographic Template Background Image PDF. The topics addressed in these templates are Attack Target, Defense Measures, End System, Control Plane. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Blockchain Security Solutions Deployment Blockchain Hashing SHA 256 Algorithm Formats PDF
This slide talks about the hashing SHA-256 algorithm used in blockchain technology, including its properties. The purpose of this slide is to give an overview of hashing and its properties, such as collision resistance, deterministic, quick, and irreversible. Create an editable Blockchain Security Solutions Deployment Blockchain Hashing SHA 256 Algorithm Formats PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Blockchain Security Solutions Deployment Blockchain Hashing SHA 256 Algorithm Formats PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
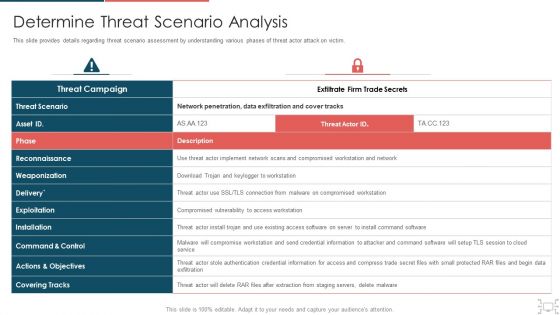
Cyber Security Administration In Organization Determine Threat Scenario Analysis Introduction PDF
This slide provides details regarding threat scenario assessment by understanding various phases of threat actor attack on victim. Deliver an awe inspiring pitch with this creative cyber security administration in organization determine threat scenario analysis introduction pdf bundle. Topics like determine threat scenario analysis can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
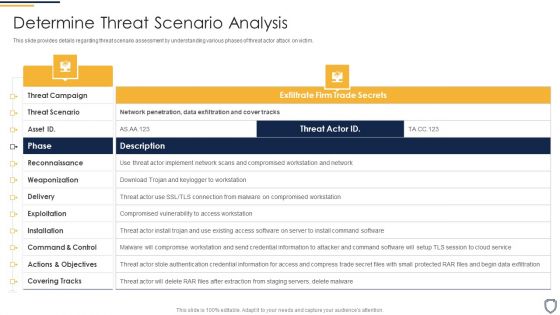
Corporate Security And Risk Management Determine Threat Scenario Analysis Formats PDF
This slide provides details regarding threat scenario assessment by understanding various phases of threat actor attack on victim. Deliver an awe inspiring pitch with this creative corporate security and risk management determine threat scenario analysis formats pdf bundle. Topics like determine threat scenario analysis can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Financing Catalogue For Security Underwriting Agreement Major Investment Banking Deals In Last Summary PDF
The slide provides the top five deals by profit amount of the company in last five years. It comprises, year, client name, deal type and brief information about all the five deals. Deliver an awe inspiring pitch with this creative financing catalogue for security underwriting agreement major investment banking deals in last summary pdf bundle. Topics like automobile, financials services, healthcare, construction can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security And Performance Digital Marketing Interestbased And Safety Net Of Prospecting Diagrams PDF
This template depicts that majority of prospective audiences are lookalikes. If any target customer falls between the gap of the sales funnel, then they will be captured in the broad interest based audience. Deliver and pitch your topic in the best possible manner with this Security And Performance Digital Marketing Interestbased And Safety Net Of Prospecting Diagrams PDF. Use them to share invaluable insights on Browsing Information, Purchasing Devices, Prospective Audiences and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Incident Response Techniques Deployement Cyber Security Incident Response Lifecycle Template PDF
This slide represents the lifecycle of incident response which enables organizations to quickly detect and halt attacks, minimize damage and prevent future attacks of same type. It includes four phases of cyber security incident response such as preparation, detection and analysis etc. Welcome to our selection of the Incident Response Techniques Deployement Cyber Security Incident Response Lifecycle Template PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

Strategies To Mitigate Cyber Security Risks Cybersecurity Contingency Plan Business Impact Analysis Brochure PDF
Presenting this set of slides with name strategies to mitigate cyber security risks cybersecurity contingency plan business impact analysis brochure pdf. This is a three stage process. The stages in this process are determining vital it resources, determining issues impacts and acceptable outage time, assign recovery priorities, settlement agreements, litigation files, department file cabinets. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
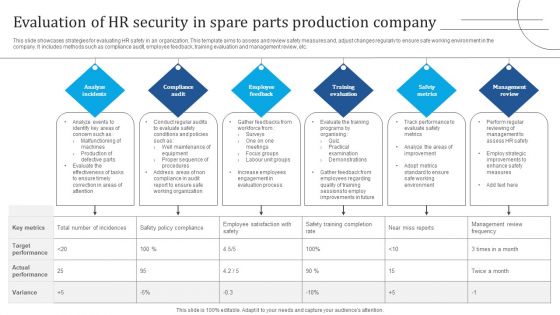
Evaluation Of HR Security In Spare Parts Production Company Demonstration PDF
This slide showcases strategies for evaluating HR safety in an organization. This template aims to assess and review safety measures and, adjust changes regularly to ensure safe working environment in the company. It includes methods such as compliance audit, employee feedback, training evaluation and management review, etc. Presenting Evaluation Of HR Security In Spare Parts Production Company Demonstration PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Analyze Incidents, Compliance Audit, Employee Feedback. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Picture Of Trade Secret Security Merits Ppt PowerPoint Presentation Model Shapes PDF
Pitch your topic with ease and precision using this picture of trade secret security merits ppt powerpoint presentation model shapes pdf. This layout presents information on trade secret doe not require registration cost, they have immediate effect, they do not require compliance with official procedures such as disclosure of information to any government authority, they are not limited with time unless patents are not revealed to the public. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Cyber Security Administration In Organization Addressing Critical Business Functions Recovery Download PDF
This slide provides details regarding business functions recovery as firm needs to retrieve the crucial information based on priorities in various departments and time taken to retrieve the information. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization addressing critical business functions recovery download pdf. Use them to share invaluable insights on addressing critical business functions recovery priorities and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security Administration In Organization Ensuring Vital Records Maintenance Topics PDF
This slide provides information regarding vital record maintenance in order to store crucial information and the location where these records are kept also details about the alternate backup location of the records and the other sources through which records can be retrieved. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization ensuring vital records maintenance topics pdf. Use them to share invaluable insights on ensuring vital records maintenance and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
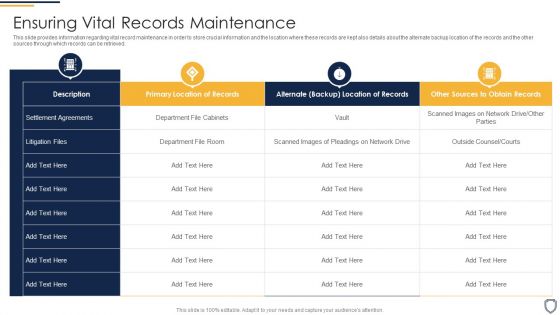
Corporate Security And Risk Management Ensuring Vital Records Maintenance Summary PDF
This slide provides information regarding vital record maintenance in order to store crucial information and the location where these records are kept also details about the alternate backup location of the records and the other sources through which records can be retrieved. Deliver an awe inspiring pitch with this creative corporate security and risk management ensuring vital records maintenance summary pdf bundle. Topics like ensuring vital records maintenance can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
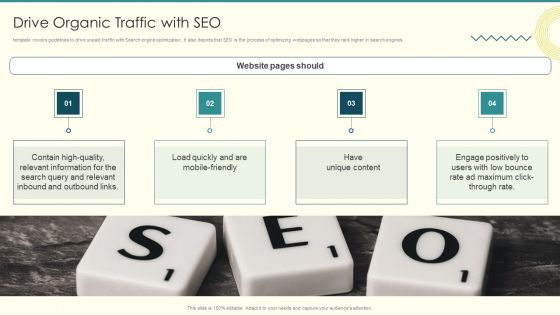
Security And Performance Digital Marketing Drive Organic Traffic With SEO Ideas PDF
template covers guidelines to drive unpaid traffic with Search engine optimization. It also depicts that SEO is the process of optimizing webpages so that they rank higher in search engines.Presenting Security And Performance Digital Marketing Drive Organic Traffic With SEO Ideas PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Relevant Information, Inbound Outbound, Engage Positively. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

 Home
Home