Data Security And Protection

Protected Globe Network Security PowerPoint Templates And PowerPoint Backgrounds 0211
Microsoft PowerPoint Template and Background with protected global network the internet

Protected Email Security PowerPoint Templates And PowerPoint Backgrounds 0211
Microsoft PowerPoint Template and Background with brass key inserted into a large chrome at/email symbol

Protected Folder Security PowerPoint Templates And PowerPoint Backgrounds 0211
Microsoft PowerPoint Template and Background with folder
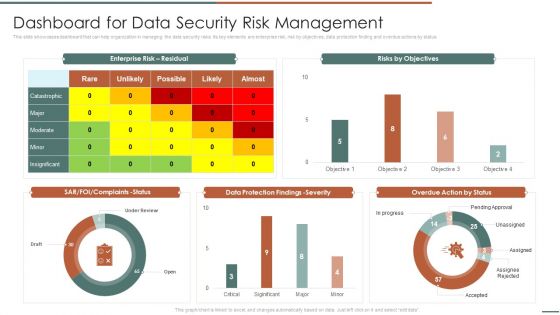
Information Security Risk Evaluation Dashboard For Data Security Risk Management Template PDF
This slide showcases dashboard that can help organization in managing the data security risks. Its key elements are enterprise risk, risk by objectives, data protection finding and overdue actions by status.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Dashboard For Data Security Risk Management Template PDF bundle. Topics like Complaints Status, Protection Findings, Overdue Action can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Series Of Cyber Security Attacks Against Ukraine 2022 How Can We Protect Ourselves From Cyberattacks Slides PDF
This slide depicts cyberattacks protection methods to follow throughout the country, such as multi-factor authentication, data backup, to keep a copy of all the backup information. Create an editable Series Of Cyber Security Attacks Against Ukraine 2022 How Can We Protect Ourselves From Cyberattacks Slides PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Series Of Cyber Security Attacks Against Ukraine 2022 How Can We Protect Ourselves From Cyberattacks Slides PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Email Security Encryption And Data Loss Prevention Your Problem E Mail Security Proposal Rules PDF
This slide covers the problems that are faced by the clients. Presenting email security encryption and data loss prevention your problem e mail security proposal rules pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security confidential data, protection against malware, protection phishing scams, threat weak password. In addtion, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

Series Of Cyber Security Attacks Against Ukraine 2022 How To Protect Yourself From Ongoing Cybersecurity Attacks Mockup PDF
This slide talks about how to protect yourself from ongoing russian cybersecurity attacks, including being on high alert, choosing a strong password, keeping antivirus software up to data, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Series Of Cyber Security Attacks Against Ukraine 2022 How To Protect Yourself From Ongoing Cybersecurity Attacks Mockup PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
Security Solutions Powerpoint Templates
This is a security solutions powerpoint templates. This is a four stage process. The stages in this process are site preparation, networking solutions, security solutions, it system integration.

Information Security How Is Automation Used In Data Security Ppt Model Graphics Template PDF
This slide depicts the cyber protection of an organization through artificial intelligence and how it can be helpful in threat detection, threat response, and human augmentation. Presenting information security how is automation used in data security ppt model graphics template pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like threat detection, threat response, human augmentation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Lock Your Computer To Protect Data PowerPoint Templates Ppt Backgrounds For Slides 0513
Drink from the fountain of our Lock Your Computer To Protect Data PowerPoint Templates PPT Backgrounds For Slides. Refresh your audience with your bubbling ideas. Bottle your thoughts in our Computer PowerPoint Templates. Pass it around for your audience to sip. Let your audience drink in your thoughts. Our Security PowerPoint Templates will pick up the tab.

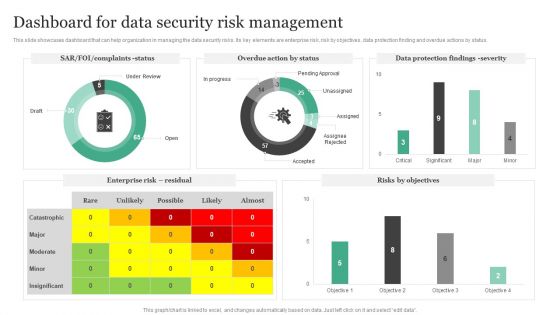
Information Systems Security And Risk Management Plan Dashboard For Data Security Risk Management Information PDF
This slide showcases dashboard that can help organization in managing the data security risks. Its key elements are enterprise risk, risk by objectives, data protection finding and overdue actions by status. If you are looking for a format to display your unique thoughts, then the professionally designed Information Systems Security And Risk Management Plan Dashboard For Data Security Risk Management Information PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Information Systems Security And Risk Management Plan Dashboard For Data Security Risk Management Information PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Information Security GDPR Law Governing Data Privacy Formats PDF
This slide explains the General Data Protection Regulation it is the most extensive data protection law applied to each member of the EU. Welcome to our selection of the Information Security GDPR Law Governing Data Privacy Formats PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
Dashboard For Data Security Risk Management Information Security Risk Administration Formats PDF
This slide showcases dashboard that can help organization in managing the data security risks. Its key elements are enterprise risk, risk by objectives, data protection finding and overdue actions by status.Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Dashboard For Data Security Risk Management Information Security Risk Administration Formats PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
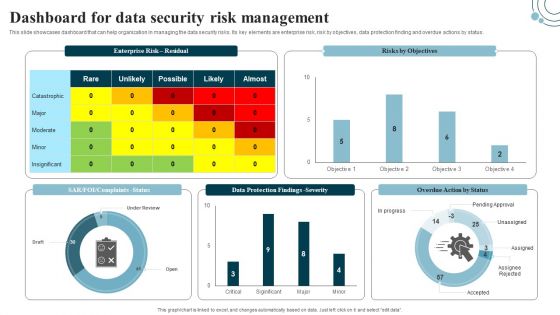
Developing IT Security Strategy Dashboard For Data Security Risk Management Pictures PDF
This slide showcases dashboard that can help organization in managing the data security risks. Its key elements are enterprise risk, risk by objectives, data protection finding and overdue actions by status. Slidegeeks has constructed Developing IT Security Strategy Dashboard For Data Security Risk Management Pictures PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
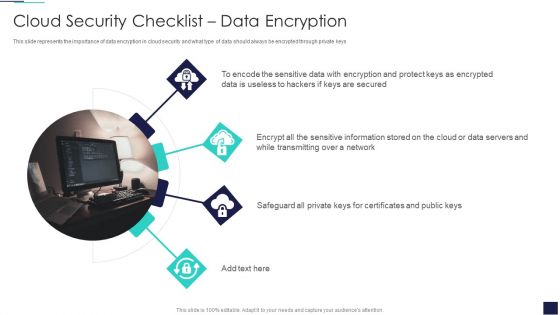
Cloud Information Security Cloud Security Checklist Data Encryption Ppt Summary Shapes PDF
This slide represents the importance of data encryption in cloud security and what type of data should always be encrypted through private keys. This is a Cloud Information Security Cloud Security Checklist Data Encryption Ppt Summary Shapes PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Sensitive Data, Protect Keys, Data Servers. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Information Security Complete Data Security Implementation Checklist Ppt Icon Clipart PDF
This slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. This is a information security complete data security implementation checklist ppt icon clipart pdf template with various stages. Focus and dispense information on eleven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like strong passwords, antivirus software, frequent staff training, recovery planning, device security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Data Encryption Method In Application Security Testing Ppt Powerpoint Formats
This slide discusses the introduction of encryption in application security for protection of specific fields in an application. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Data Encryption Method In Application Security Testing Ppt Powerpoint Formats to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Winning Strategies To Improve Organization Data Security Pictures PDF
The following slide highlights a winning strategy to avoid data security breach in the organization. Businesses can protect the confidential data by following strategies such as security audit, establishing strong password, back up sensitive data, and improve cyber-security. Presenting Winning Strategies To Improve Organization Data Security Pictures PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Security Audit, Establish Strong, Sensitive Data. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Building Trust With IoT Security IoT Data Security Vulnerabilities And Privacy Concerns IoT SS V
This slide includes common IoT security vulnerabilities and risk that helps organization implement security measures. It includes vulnerabilities such as lack of privacy protection, improper device management approach, default settings, weak credentials, etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Building Trust With IoT Security IoT Data Security Vulnerabilities And Privacy Concerns IoT SS V from Slidegeeks and deliver a wonderful presentation.
Encrypted Business Data Cyber Security Assessment Icon Professional PDF
Presenting Encrypted Business Data Cyber Security Assessment Icon Professional PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Manage Handy Backups, Incorporate Multi Layer Security, Train Employees, Invest In Protective Software. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Factors Responsible For Cloud Security Data Security In Cloud Computing Ppt Example
The purpose of this slide is to explain the various misconceptions and mistakes of organization while integrating cryptographic solutions into cloud. These include dependence on low-level encryption, reliance on cloud service providers for data protection, poor key management, etc. The Factors Responsible For Cloud Security Data Security In Cloud Computing Ppt Example is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
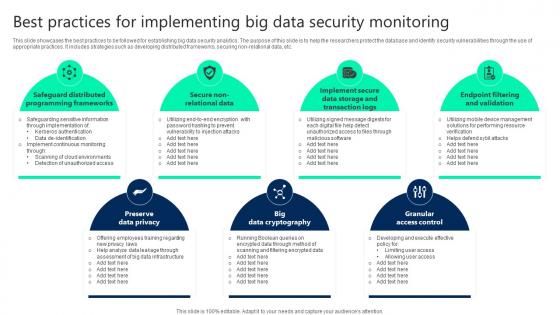
Best Practices For Implementing Big Data Security Monitoring Sample pdf
This slide showcases the best practices to be followed for establishing big data security analytics. The purpose of this slide is to help the researchers protect the database and identify security vulnerabilities through the use of appropriate practices. It includes strategies such as developing distributed frameworks, securing non-relational data, etc. Showcasing this set of slides titled Best Practices For Implementing Big Data Security Monitoring Sample pdf. The topics addressed in these templates are Preserve Data Privacy, Big Data Cryptography, Granular Access Control. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Factors Responsible For Cloud Security Cloud Data Security Using Cryptography Formats Pdf
The purpose of this slide is to explain the various misconceptions and mistakes of organization while integrating cryptographic solutions into cloud. These include dependence on low level encryption, reliance on cloud service providers for data protection, poor key management, etc. Take your projects to the next level with our ultimate collection of Factors Responsible For Cloud Security Cloud Data Security Using Cryptography Formats Pdf. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest
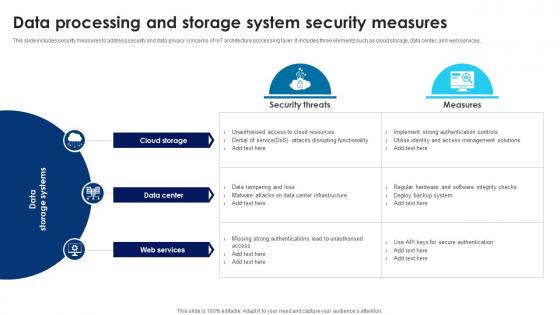
Building Trust With IoT Security Data Processing And Storage System Security Measures IoT SS V
This slide includes security measures to address security and data privacy concerns of IoT architecture processing layer. It includes three elements such as cloud storage, data center, and web services. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Building Trust With IoT Security Data Processing And Storage System Security Measures IoT SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Enterprise Data Encryption Internet Of Things Security Technology Summary Pdf
This slide exhibits the role of encryption technology and IoT that assists businesses and organizations to protect the confidentiality of digital data storage and transmission. Major elements are authentication, data privacy, compliance management, and security. Showcasing this set of slides titled Enterprise Data Encryption Internet Of Things Security Technology Summary Pdf The topics addressed in these templates are Authentication, Data Privacy, Compliance Management All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

CASB 2 0 IT Cloud Access Security Broker Pillar Data Security
This slide talks about the data security pillar of the cloud access security broker pillar. This slide highlights how CASB data security can help organizations improve their IT requirements and business operations and detect security breaches before they happen. The CASB 2 0 IT Cloud Access Security Broker Pillar Data Security is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Cloud Security Enhancement Using Cloud Data Security Using Cryptography Elements Pdf
This slide talks about the various applications of hash algorithm in cloud cryptography. The purpose of this slide is to explain how hash technique can help in providing security in cloud computing. These are password storage, data integrity, digital signatures, etc. This Cloud Security Enhancement Using Cloud Data Security Using Cryptography Elements Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Cloud Security Enhancement Using Cloud Data Security Using Cryptography Elements Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Risk Management Model For Data Security Current Security Infrastructure Performance Analysis Pictures PDF
Mentioned slide displays performance analysis of current security infrastructure based on NIST core functions. Core functions included are identify, protect, detect, respond, recover. Deliver and pitch your topic in the best possible manner with this Risk Management Model For Data Security Current Security Infrastructure Performance Analysis Pictures PDF. Use them to share invaluable insights on Identify, Protect, Detect, Respond, Recover and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
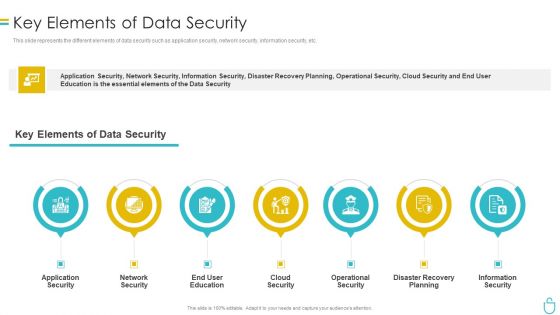
Information Security Key Elements Of Data Security Ppt Pictures Show PDF
This slide represents the different elements of data security such as application security, network security, information security, etc. Presenting information security key elements of data security ppt pictures show pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like network security, application security, cloud security, operational security, information security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cryptographic Cloud Security Solution Cloud Data Security Using Cryptography Inspiration Pdf
This slide demonstrates the top cloud cryptography solution providers. The purpose of this slide is to outline the price and features of these service providers. These include Amazon Web Services Key Management Service AWS KMS, Microsoft Azure Key Vault, Google Cloud KMS, etc. The Cryptographic Cloud Security Solution Cloud Data Security Using Cryptography Inspiration Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
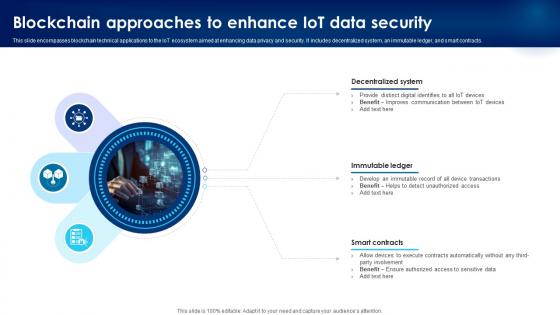
Building Trust With IoT Security Blockchain Approaches To Enhance IoT Data Security IoT SS V
This slide encompasses blockchain technical applications to the IoT ecosystem aimed at enhancing data privacy and security. It includes decentralized system, an immutable ledger, and smart contracts. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Building Trust With IoT Security Blockchain Approaches To Enhance IoT Data Security IoT SS V a try. Our experts have put a lot of knowledge and effort into creating this impeccable Building Trust With IoT Security Blockchain Approaches To Enhance IoT Data Security IoT SS V. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today

Cloud Security Enhancement Using Data Security In Cloud Computing Ppt Presentation
This slide talks about the various applications of hash algorithm in cloud cryptography. The purpose of this slide is to explain how hash technique can help in providing security in cloud computing. These are password storage, data integrity, digital signatures, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Cloud Security Enhancement Using Data Security In Cloud Computing Ppt Presentation and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Risk Management Model For Data Security Setting Scenario For Security Control Designs PDF
Following slide shows the current security management capabilities of the firm. It covers details about core functions, its description, key enablers, required and actual standard ratings. Deliver an awe inspiring pitch with this creative Risk Management Model For Data Security Setting Scenario For Security Control Designs PDF bundle. Topics like Identify, Protect, Detect, Response, Recovery can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Risk Management Model For Data Security Impact On Security Infrastructure Performance Elements PDF
Mentioned slide shows performance impact on security infrastructure after introducing risk assessment process. Deliver and pitch your topic in the best possible manner with this Risk Management Model For Data Security Impact On Security Infrastructure Performance Elements PDF. Use them to share invaluable insights on Identify, Protect, Detect, Respond, Recover and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information Security What Is Data Security And How Does It Work Ppt Professional Infographics PDF
This slide defines the meaning of data security and how it helps to prevent data through different methods and techniques. Presenting information security what is data security and how does it work ppt professional infographics pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like techniques, computer systems, protect. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cryptographic Cloud Security Solution Data Security In Cloud Computing Ppt Template
This slide demonstrates the top cloud cryptography solution providers. The purpose of this slide is to outline the price and features of these service providers. These include Amazon Web Services Key Management Service AWS KMS, Microsoft Azure Key Vault, Google Cloud KMS, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Cryptographic Cloud Security Solution Data Security In Cloud Computing Ppt Template to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Project Security Administration IT Information Security Process To Manage Firms Sensitive Data Summary PDF
This slide provides information about information security process in order to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc. Deliver an awe inspiring pitch with this creative project security administration it information security process to manage firms sensitive data summary pdf bundle. Topics like privileged password management, daily tasks performed by network administrator, network security audit checklist can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Developing Firm Security Strategy Plan Information Security Process To Manage Firms Sensitive Data Introduction PDF
This slide provides information about information security process in order to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc. This is a developing firm security strategy plan information security process to manage firms sensitive data introduction pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like privileged password management, daily tasks performed by network administrator, network security audit checklist. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
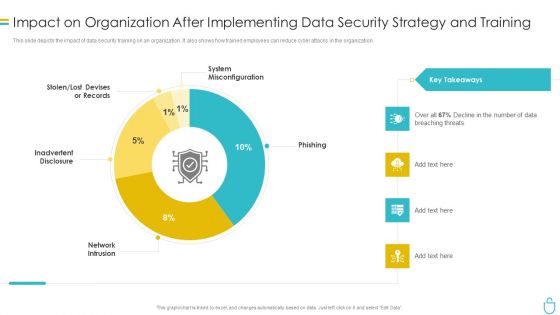
Information Security Impact On Organization After Implementing Data Security Strategy And Training Ppt Ideas Images PDF
This slide depicts the impact of data security training on an organization. It also shows how trained employees can reduce cyber attacks in the organization. Deliver and pitch your topic in the best possible manner with this information security impact on organization after implementing data security strategy and training ppt ideas images pdf. Use them to share invaluable insights on organization, data security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
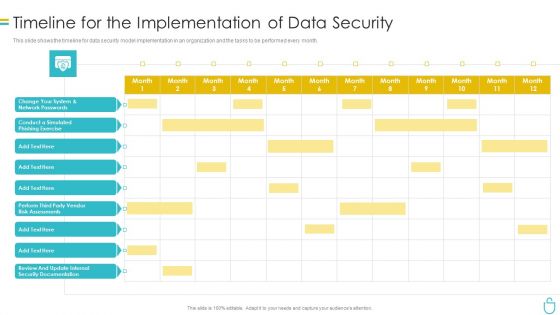
Information Security Timeline For The Implementation Of Data Security Ppt Gallery Topics PDF
This slide shows the timeline for data security model implementation in an organization and the tasks to be performed every month. Deliver and pitch your topic in the best possible manner with this information security timeline for the implementation of data security ppt gallery topics pdf. Use them to share invaluable insights on timeline for the implementation of data security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
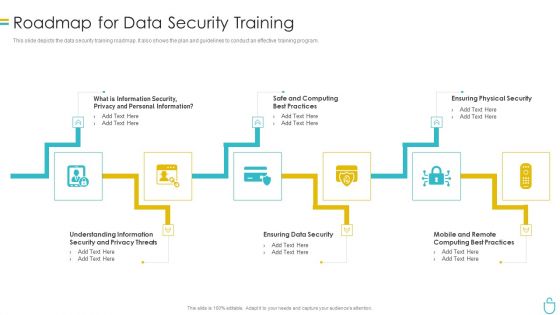
Information Security Roadmap For Data Security Training Ppt Model Show PDF
This slide depicts the data security training roadmap. It also shows the plan and guidelines to conduct an effective training program. This is a information security roadmap for data security training ppt model show pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information security, ensuring data security, ensuring physical security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Business Data Encryption Security Management Technology Ideas PDF
This slide highlights the role of encryption technology which is used by business and organisation to protect the confidentiality of digital data storage and transmission. Key components are authentication, privacy, regulatory compliance and security. Presenting Business Data Encryption Security Management Technology Ideas PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Authentication, Privacy, Regulatory Compliance, Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
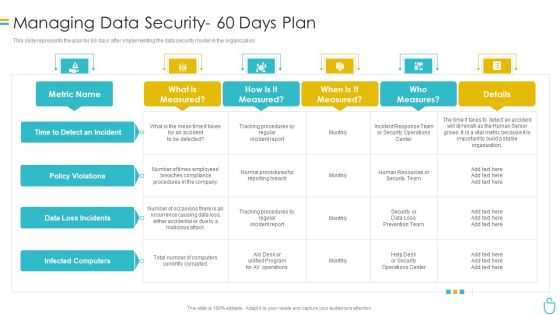
Information Security Managing Data Security 60 Days Plan Ppt Inspiration Slide Download PDF
This slide represents the plan for 60 days after implementing the data security model in the organization. Deliver and pitch your topic in the best possible manner with this information security managing data security 60 days plan ppt inspiration slide download pdf. Use them to share invaluable insights on measured, procedures, team, security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
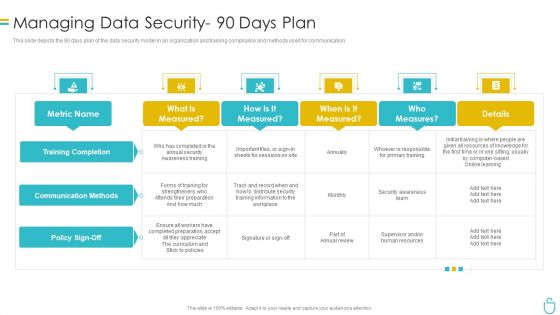
Information Security Managing Data Security 90 Days Plan Ppt Infographic Template Slides PDF
This slide depicts the 90 days plan of the data security model in an organization and training compliance and methods used for communication. Deliver an awe inspiring pitch with this creative information security managing data security 90 days plan ppt infographic template slides pdf bundle. Topics like security, measured can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
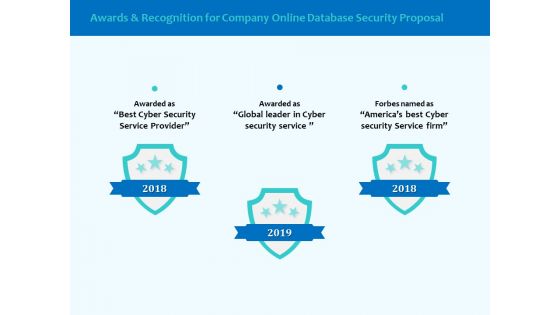
Best Data Security Software Awards And Recognition For Company Online Database Security Proposal Clipart PDF
Presenting this set of slides with name best data security software awards and recognition for company online database security proposal clipart pdf. This is a three stage process. The stages in this process are awarded as best cyber security service provider, awarded as global leader in cyber security service, forbes named as americas best cyber security service firm. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
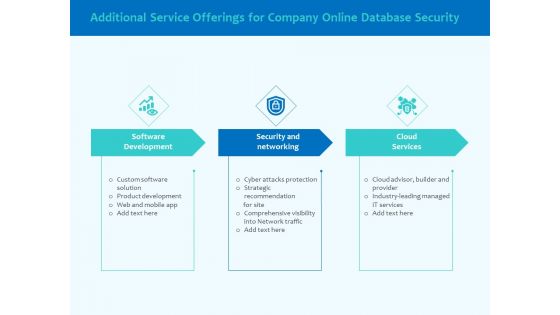
Best Data Security Software Additional Service Offerings For Company Online Database Security Designs PDF
Presenting this set of slides with name best data security software additional service offerings for company online database security designs pdf. This is a three stage process. The stages in this process are software development, security and networking, cloud services. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
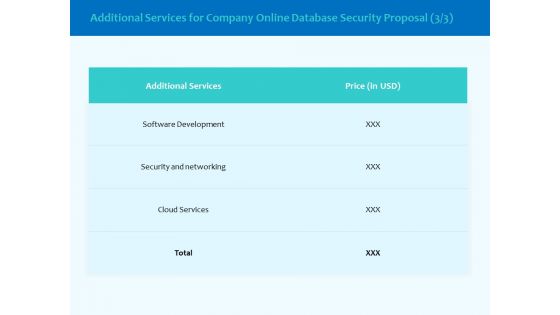
Best Data Security Software Additional Services For Company Online Database Security Proposal Pictures PDF
Presenting this set of slides with name best data security software additional services for company online database security proposal pictures pdf. The topics discussed in these slides are software development, security and networking, cloud services. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Information Security Compliance Dashboard Of Data Security Ppt Icon Vector PDF
This slide depicts the data security compliance report on how data and hardware are monitored in different categories such as standard, regulation, and asset type control. Deliver an awe inspiring pitch with this creative information security compliance dashboard of data security ppt icon vector pdf bundle. Topics like asset type control, control issues by standard, control issues by regulation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
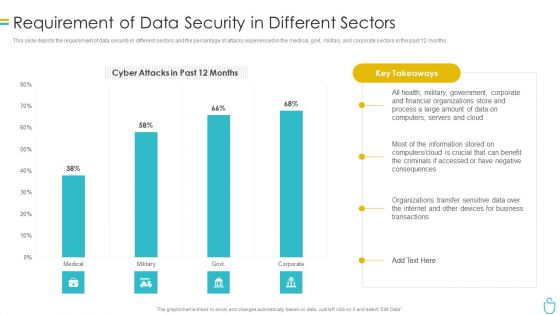
Information Security Requirement Of Data Security In Different Sectors Ppt File Infographic Template PDF
This slide depicts the requirement of data security in different sectors and the percentage of attacks experienced in the medical, govt, military, and corporate sectors in the past 12 months. Deliver an awe inspiring pitch with this creative information security requirement of data security in different sectors ppt file infographic template pdf bundle. Topics like process, financial, organizations, data, servers can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Security Checklist Data Encryption Cloud Computing Security IT Ppt Summary Tips PDF
This slide represents the importance of data encryption in cloud security and what type of data should always be encrypted through private keys. This is a cloud security checklist data encryption cloud computing security it ppt summary tips pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like safeguard, data servers, network, encryption. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
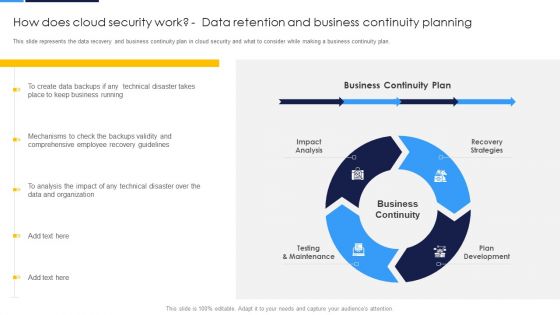
Cloud Security Assessment How Does Cloud Security Work Data Retention And Business Continuity Planning Sample PDF
This slide describes how a cloud security system works and what controls or measures are implemented to secure the data over the cloud.This is a Cloud Security Assessment How Does Cloud Security Work Data Retention And Business Continuity Planning Sample PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Data Security, Access Management, Business Continuity. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
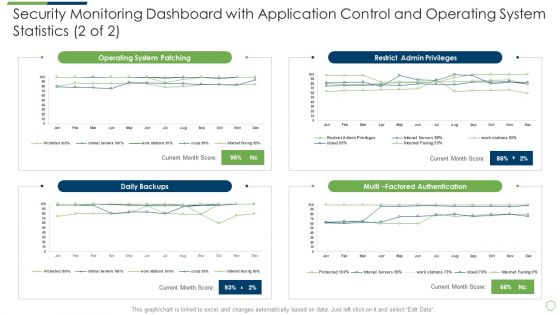
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Security Monitoring Dashboard Sample PDF
Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach security monitoring dashboard sample pdf bundle. Topics like security monitoring dashboard with application control and operating system statistics can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
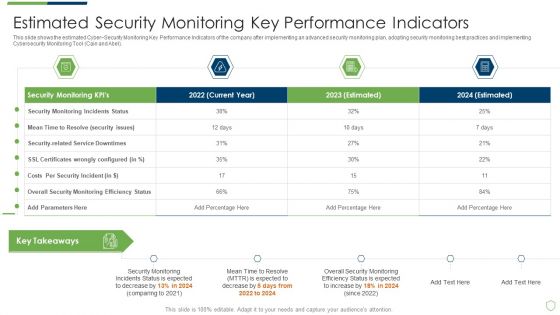
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Estimated Security Monitoring Guidelines PDF
This slide shows the estimated Cyber Security Monitoring Key Performance Indicators of the company after implementing an advanced security monitoring plan, adopting security monitoring best practices and implementing Cybersecurity Monitoring Tool Cain and Abel. Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach estimated security monitoring guidelines pdf. Use them to share invaluable insights on estimated security monitoring key performance indicators and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
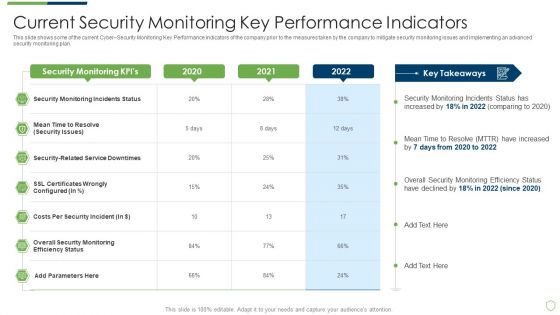
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Current Security Monitoring Pictures PDF
This slide shows some of the current Cyber Security Monitoring Key Performance Indicators of the company prior to the measures taken by the company to mitigate security monitoring issues and implementing an advanced security monitoring plan. Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach current security monitoring pictures pdf. Use them to share invaluable insights on current security monitoring key performance indicators and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
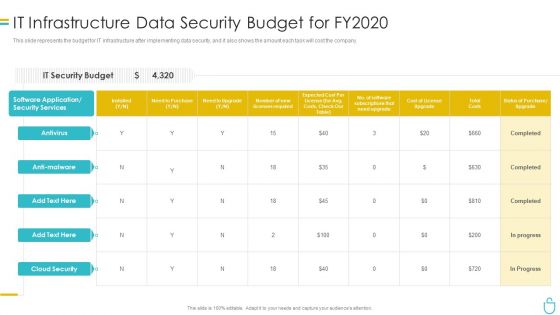
Information Security It Infrastructure Data Security Budget For FY2020 Ppt Inspiration File Formats PDF
This slide represents the budget for IT infrastructure after implementing data security, and it also shows the amount each task will cost the company. Deliver and pitch your topic in the best possible manner with this information security it infrastructure data security budget for fy2020 ppt inspiration file formats pdf. Use them to share invaluable insights on costs, need to purchase, required, application and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Best Data Security Software Client Testimonials For Company Online Database Security Guidelines PDF
Presenting this set of slides with name best data security software client testimonials for company online database security guidelines pdf. This is a three stage process. The stages in this process are client testimonials, company, online database security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Best Data Security Software Cover Letter For Company Online Database Security Proposal Designs PDF
Presenting this set of slides with name best data security software cover letter for company online database security proposal designs pdf. This is a one stage process. The stages in this process are cover letter, company, online database security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Best Data Security Software Roadmap For Company Online Database Security Proposal Graphics PDF
Presenting this set of slides with name best data security software roadmap for company online database security proposal graphics pdf. This is a five stage process. The stages in this process are roadmap, company, online database security, 2016 to 2020. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Best Data Security Software Timeline For Company Online Database Security Proposal Graphics PDF
Presenting this set of slides with name best data security software timeline for company online database security proposal graphics pdf. This is a five stage process. The stages in this process are timeline, company, online database security, 2017 to 2020. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Information Security Data Security Awareness Training For Staff Ppt Visual Aids Pictures PDF
This slide represents the data security awareness training program for staff, including the name of the participants and what modules would be covered under training daily. Deliver and pitch your topic in the best possible manner with this information security data security awareness training for staff ppt visual aids pictures pdf. Use them to share invaluable insights on project managers, developers, senior executives, planning and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

 Home
Home