Data Security And Protection

Developing IT Security Strategy Matrix For Threat Solution And Risk Management Topics PDF
This slide showcases matrix that can help organization to formulate solutions for different types of information security attacks. It can help organization to mitigate the risks and safeguard information in case of any attack. Find highly impressive Developing IT Security Strategy Matrix For Threat Solution And Risk Management Topics PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Developing IT Security Strategy Matrix For Threat Solution And Risk Management Topics PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
Online Settlement Revolution Payment Security And Fraud Management Solutions Browser Icons PDF
Payment security and fraud management solutions for the user to limit losses while maintain a high level of customer satisfaction. Presenting online settlement revolution payment security and fraud management solutions browser icons pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like costs, process, analytics, development. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Where Is The Gap In Security Programs Ppt Icon Layout Ideas PDF
This slide covers the problems in the organization regarding security awareness training along with the gap and solution to overcome those gaps Presenting where is the gap in security programs ppt icon layout ideas pdf. to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like problems, gap, solution. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
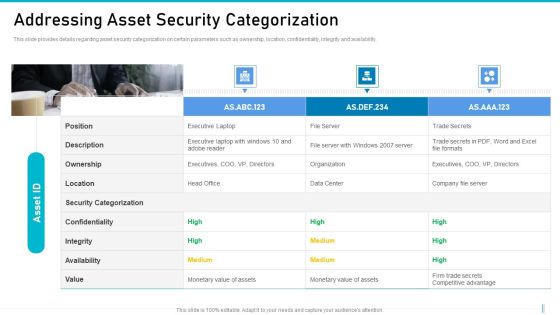
Risk Management For Organization Essential Assets Addressing Asset Security Categorization Diagrams PDF
This slide provides details regarding asset security categorization on certain parameters such as ownership, location, confidentiality, integrity and availability. Presenting risk management for organization essential assets addressing asset security categorization diagrams pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like ownership, location, confidentiality, integrity, availability. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Practices To Improve Security Awareness Level Amongst The Employees Contd Structure PDF
The purpose of this slide is to outline multiple ways which can be used by the organization to improve the cyber security awareness level of employees. The key practices mentioned in the slide are involving top level management, developing robust policies, and setting guidelines. Presenting Practices To Improve Security Awareness Level Amongst The Employees Contd Structure PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Management Involved, Develop Robust, Set Guidelines. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security Evaluation Scorecard With It Cost Break Down Ppt Infographics Slideshow PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver an awe inspiring pitch with this creative IT Security Evaluation Scorecard With It Cost Break Down Ppt Infographics Slideshow PDF bundle. Topics like Spend Vs Budget, Return On Investment, IT Department Revenue, IT Costs Vs can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
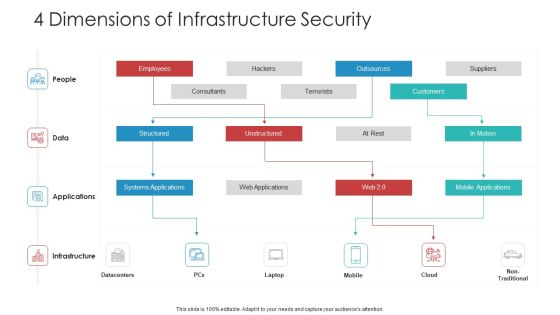
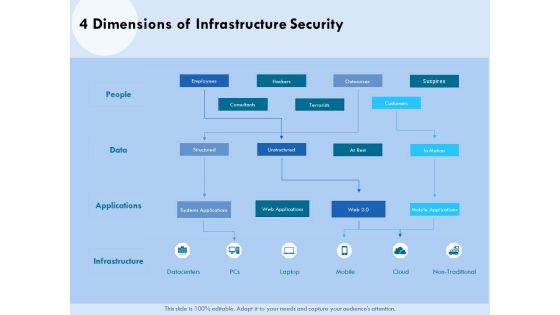
Landscape Architecture Planning And Management 4 Dimensions Of Infrastructure Security Sample PDF
Deliver an awe inspiring pitch with this creative landscape architecture planning and management 4 dimensions of infrastructure security sample pdf bundle. Topics like people, data, applications, infrastructure can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
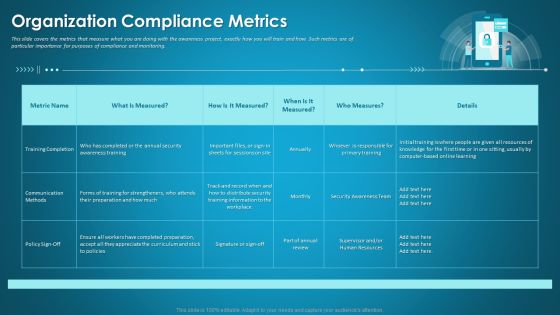
Organizational Network Security Awareness Staff Learning Organization Compliance Metrics Introduction PDF
This slide covers the metrics that measure what you are doing with the awareness project, exactly how you will train and how. Such metrics are of particular importance for purposes of compliance and monitoring. Deliver an awe inspiring pitch with this creative organizational network security awareness staff learning organization compliance metrics introduction pdf bundle. Topics like training completion, communication methods, security training information can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Security Evaluation Scorecard With Server Status Ppt Professional Images PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver an awe inspiring pitch with this creative IT Security Evaluation Scorecard With Server Status Ppt Professional Images PDF bundle. Topics like Operations Status Tool, Management Services Managed can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
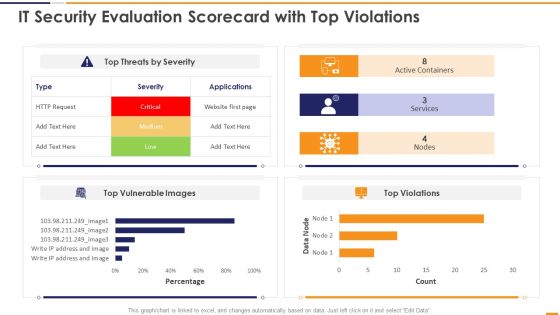
IT Security Evaluation Scorecard With Top Violations Ppt Portfolio Deck PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver an awe inspiring pitch with this creative IT Security Evaluation Scorecard With Top Violations Ppt Portfolio Deck PDF bundle. Topics like Top Threats Severity, Active Containers Services, Top Vulnerable Images can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Dashboard To Track IT Security Incidents Prevailing Across Firm Elements PDF
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Dashboard To Track IT Security Incidents Prevailing Across Firm Elements PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Dashboard To Track IT Security Incidents Prevailing Across Firm Elements PDF.
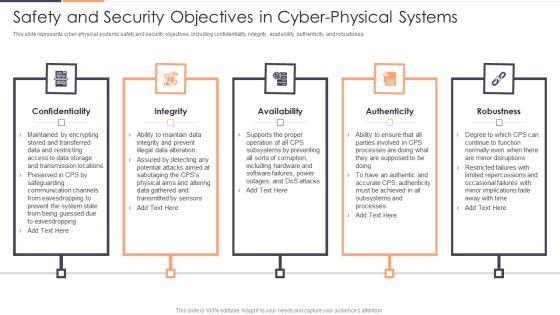
Safety And Security Objectives In Cyber Physical Systems Ppt Slides Themes PDF
This slide represents cyber physical systems safety and security objectives, including confidentiality, integrity, availability, authenticity, and robustness. Presenting Safety And Security Objectives In Cyber Physical Systems Ppt Slides Themes PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Availability, Authenticity, Confidentiality. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Organizational Assets Security Management Strategy Determine User Access Controls Levels Diagrams PDF
This slide provides information about information user access controls levels for access critical assets and information associated to firm and levels of access for administrator, maintainer, guest or disabled. Get a simple yet stunning designed Organizational Assets Security Management Strategy Determine User Access Controls Levels Diagrams PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Organizational Assets Security Management Strategy Determine User Access Controls Levels Diagrams PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
IT Security Evaluation Scorecard With Server Uptime And Downtime Icons PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver an awe inspiring pitch with this creative IT Security Evaluation Scorecard With Server Uptime And Downtime Icons PDF bundle. Topics like IT Support Employee, Per Thousand End, user Over Time, Uptime And Downtime can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Security Evaluation Scorecard With Bar Graph Ppt Gallery Design Templates PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver and pitch your topic in the best possible manner with this IT Security Evaluation Scorecard With Bar Graph Ppt Gallery Design Templates PDF. Use them to share invaluable insights on CPU Utilization Memory, Utilization Packet Loss and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Security Evaluation Scorecard With Impact Status Ppt Portfolio Guidelines PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver and pitch your topic in the best possible manner with this IT Security Evaluation Scorecard With Impact Status Ppt Portfolio Guidelines PDF. Use them to share invaluable insights on Device Availability Application, Performance Port Health, Devices Reference Firmware and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
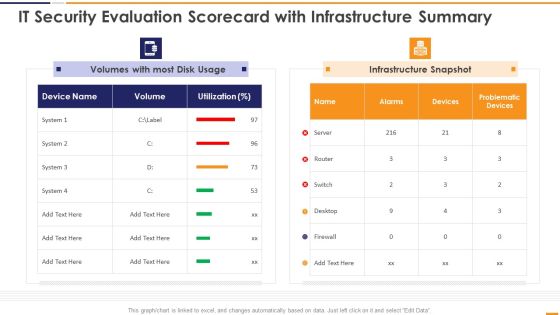
IT Security Evaluation Scorecard With Infrastructure Summary Ppt Slides Portrait PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver an awe inspiring pitch with this creative IT Security Evaluation Scorecard With Infrastructure Summary Ppt Slides Portrait PDF bundle. Topics like Volumes Most Disk, Usage Infrastructure Snapshot can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Security Evaluation Scorecard With Ip Availability Ppt Pictures Portrait PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver and pitch your topic in the best possible manner with this IT Security Evaluation Scorecard With Ip Availability Ppt Pictures Portrait PDF. Use them to share invaluable insights on Devices Memory Utilization, Interfaces Errors Discards, IP Availability Summary and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Security Evaluation Scorecard With System Details Ppt Inspiration Vector PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver and pitch your topic in the best possible manner with this IT Security Evaluation Scorecard With System Details Ppt Inspiration Vector PDF. Use them to share invaluable insights on System Details Availability, System Metrics Memory, Pressure Memory Leak and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Security Evaluation Scorecard With Recent Alarms Raised By Devices Guidelines PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver an awe inspiring pitch with this creative IT Security Evaluation Scorecard With Recent Alarms Raised By Devices Guidelines PDF bundle. Topics like Devices CPU Utilization, Device Details Raised can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
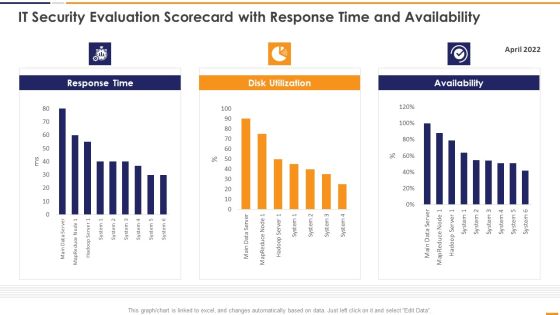
IT Security Evaluation Scorecard With Response Time And Availability Brochure PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver and pitch your topic in the best possible manner with this IT Security Evaluation Scorecard With Response Time And Availability Brochure PDF. Use them to share invaluable insights on Response Time 2022, Disk Utilization Availability and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security And Human Resource Services Business Profile Executive Summary Infographics PDF
This slide highlights the executive summary of security company that includes company overview, founder, USP, company shareholding, achievements, key facts and figures. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Security And Human Resource Services Business Profile Executive Summary Infographics PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Security And Human Resource Services Business Profile Executive Summary Infographics PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

IT Security Employee Awareness Training Budget For FY2020 Ppt Pictures Example PDF
This slide represents the organizations staff training budget through a graph covering trainer name, date, and capability levels. Deliver an awe inspiring pitch with this creative information technology security employee awareness training budget for fy2020 ppt gallery information pdf bundle. Topics like employee awareness training budget for fy2020 can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Reducing Costs And Management Tips How Management Enables Effective Corporate Security Governance Mockup PDF
This slide portrays information regarding the management role in effective corporate security governance by highlight management level, strategic alignment, risk management, etc. Get a simple yet stunning designed IT Reducing Costs And Management Tips How Management Enables Effective Corporate Security Governance Mockup PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit IT Reducing Costs And Management Tips How Management Enables Effective Corporate Security Governance Mockup PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Dashboard To Track IT Security Incidents Prevailing Across Firm Infographics PDF
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Dashboard To Track IT Security Incidents Prevailing Across Firm Infographics PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Dashboard To Track IT Security Incidents Prevailing Across Firm Infographics PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Dashboard To Track IT Security Incidents Prevailing Across Firm Demonstration PDF
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Dashboard To Track IT Security Incidents Prevailing Across Firm Demonstration PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Dashboard To Track IT Security Incidents Prevailing Across Firm Demonstration PDF today and make your presentation stand out from the rest

Impact On Organization After Implementing Computer Security Strategy And Training Ideas PDF
This slide depicts the impact of cyber security training on an organization. It also shows how trained employees can reduce cyber attacks in the organization. This is a impact on organization after implementing computer security strategy and training ideas pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like network intrusion, system misconfiguration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security Analysis To Enable Safe Technology Transformation Ppt PowerPoint Presentation Visual Aids Styles PDF
Persuade your audience using this cyber security analysis to enable safe technology transformation ppt powerpoint presentation visual aids styles pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including cyber security assessment, identify risks. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Network Security Devices Computer Network Ppt PowerPoint Presentation Visual Aids Background Images Cpb Pdf
Presenting this set of slides with name network security devices computer network ppt powerpoint presentation visual aids background images cpb pdf. This is an editable Powerpoint three stages graphic that deals with topics like network security devices computer network to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Table Of Contents For Cloud Information Security Ppt Slides Vector PDF
Deliver and pitch your topic in the best possible manner with this Table Of Contents For Cloud Information Security Ppt Slides Vector PDF. Use them to share invaluable insights on Cloud Management, Cloud Responsibilities, Shared Vulnerabilities and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

5 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Portrait PDF
Presenting 5 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Portrait PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Business Goals, Management Program, Secure Corporate. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Agenda For Information Security Risk Evaluation And Administration Plan Pictures PDF
This is a Agenda For Information Security Risk Evaluation And Administration Plan Pictures PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Agenda. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Security Management With Actions And Interactions Ppt PowerPoint Presentation Gallery Graphics PDF
Showcasing this set of slides titled information security management with actions and interactions ppt powerpoint presentation gallery graphics pdf. The topics addressed in these templates are causal, consequences, interactions. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Net Banking Channel And Service Management Major Types Of E Banking Security Threats Inspiration PDF
This slide represents types of e banking security threats. It includes brute force, phishing, pharming, cross site scripting and trojan horse. The Net Banking Channel And Service Management Major Types Of E Banking Security Threats Inspiration PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Key Steps To Create Role Specific Cyber Security Training Program Structure PDF
This slide highlights various steps to develop role based training program for cyber security risk management. It includes key steps such as assess existing training, identify employee roles, define role-specific security risks, outline process and technology, etc. Persuade your audience using this Key Steps To Create Role Specific Cyber Security Training Program Structure PDF This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Process, Description, Elements. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Mobile Device Management For Android Platform Mobile Device Security Management Demonstration PDF
This slide provides information regarding mobile device management for android platform with device settings policy, device security settings, etc. Presenting Mobile Device Management For Android Platform Mobile Device Security Management Demonstration PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Device Security, Application Control, Remote Management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Officer Service Company Profile Executive Leadership And Management Team Background PDF
This slide highlights the security guard company management team which includes companys chairman and MD, head of security operations, training, strategic growth and site. Presenting Security Officer Service Company Profile Executive Leadership And Management Team Background PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Human Resource Management, Business Strategist, Management Consultant, Strategizing Business. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Addressing Confidentiality Integrity And Availability In Iot Security Compliance Ppt Portfolio Deck PDF
This slide provides information regarding security objectives such as confidentiality, integrity and availability and their role in IoT security compliance. Boost your pitch with our creative Addressing Confidentiality Integrity And Availability In Iot Security Compliance Ppt Portfolio Deck PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

What Role Does SDN Play In Customer Security Ppt Outline Portrait PDF
This slide represents the role of software-defined networking in customer security. It allows clients to have separate settings for each type of network traffic and permits a low-security public-facing network for regular information. Do you know about Slidesgeeks What Role Does SDN Play In Customer Security Ppt Outline Portrait PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
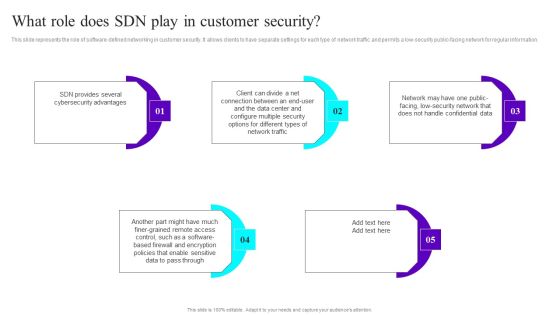
What Role Does SDN Play In Customer Security Ppt Infographic Template Slides PDF
This slide represents the role of software-defined networking in customer security. It allows clients to have separate settings for each type of network traffic and permits a low-security public-facing network for regular information. Do you know about Slidesgeeks What Role Does SDN Play In Customer Security Ppt Infographic Template Slides PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
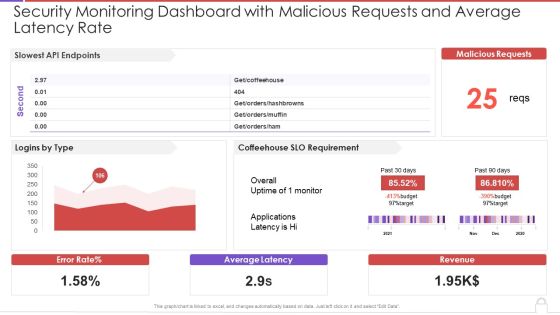
Security Monitoring Dashboard With Malicious Requests And Average Latency Rate Topics PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver an awe inspiring pitch with this creative security monitoring dashboard with malicious requests and average latency rate topics pdf bundle. Topics like slowest api endpoints, malicious requests, coffeehouse slo can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Functional Analysis Of Business Operations 4 Dimensions Of Infrastructure Security Designs PDF
Presenting this set of slides with name functional analysis of business operations 4 dimensions of infrastructure security designs pdf. The topics discussed in these slides are employees, infrastructure, data, mobile, cloud. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Functioning Of Serverless Computing Security Related Challenges In Serverless Technology Graphics PDF
The purpose of the following slide is to show the various challenges that may present to the organization, these issues can be authentication issues, no-proper monitoring, and third-party dependency. This is a functioning of serverless computing security related challenges in serverless technology graphics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like authentication issues, dependency third party, improper monitoring and controlling. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security Administration In Organization Addressing Various Ways To Handle Insider Cyber Threats Designs PDF
This slide provides details regarding various ways to handle insider cyber threats in terms of periodic risk assessment, end user informing, etc. This is a cyber security administration in organization addressing various ways to handle insider cyber threats designs pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like assessment, networks, individuals, determine. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
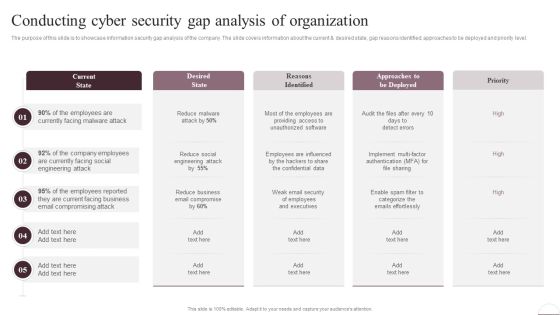
Prevention Of Information Conducting Cyber Security Gap Analysis Of Organization Information PDF
The purpose of this slide is to showcase information security gap analysis of the company. The slide covers information about the current and desired state, gap reasons identified, approaches to be deployed and priority level. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Prevention Of Information Conducting Cyber Security Gap Analysis Of Organization Information PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Prevention Of Information Conducting Cyber Security Gap Analysis Of Organization Information PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today
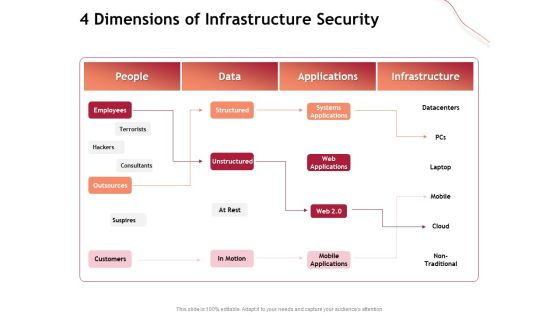
Performance Measuement Of Infrastructure Project 4 Dimensions Of Infrastructure Security Infographics PDF
Presenting this set of slides with name performance measuement of infrastructure project 4 dimensions of infrastructure security infographics pdf. The topics discussed in these slides are people, data, applications, infrastructure. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Dashboard Incident Tracking Ppt Gallery Infographics PDF
Presenting this set of slides with name computer security incident handling dashboard incident tracking ppt gallery infographics pdf. The topics discussed in these slides are application whitelisting, patch applications, patch operating systems, restrict admin privileges, user application hardening, daily backup of important data. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Key Features For Effective Business Management 4 Dimensions Of Infrastructure Security Ppt Icon Gridlines PDF
Presenting this set of slides with name key features for effective business management 4 dimensions of infrastructure security ppt icon gridlines pdf. This is a four stage process. The stages in this process are people, data, applications, infrastructure, mobile applications, suspires, outsources, systems applications, cloud. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cybersecurity Risk Administration Plan Information Security Decision Framework PRISM Workflow Topics PDF
Deliver and pitch your topic in the best possible manner with this Cybersecurity Risk Administration Plan Information Security Decision Framework PRISM Workflow Topics PDF Use them to share invaluable insights on Prioritization Weighting, Resource Allocation, Risk Management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

ISO 27001 Organizational Qualifying Procedure ISO 27001 Information Security Management Standard Mockup PDF
Deliver an awe inspiring pitch with this creative ISO 27001 Organizational Qualifying Procedure ISO 27001 Information Security Management Standard Mockup PDF bundle. Topics like Leadership Requirements, Contextual Requirements, Planning Requirements can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Software Company Investor Funding Pitch Deck Investment Ask Clipart PDF
This slide represents the information related to the investment requirements to the investors for seeking needed funds and the purpose of seeking finance. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Security Software Company Investor Funding Pitch Deck Investment Ask Clipart PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Security Software Company Investor Funding Pitch Deck Investment Ask Clipart PDF today and make your presentation stand out from the rest.
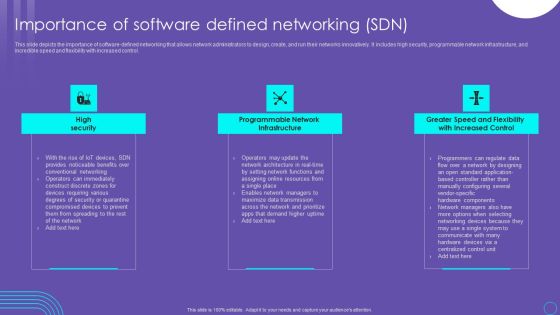
SDN Security Architecture Importance Of Software Defined Networking SDN Graphics PDF
This slide depicts the importance of software defined networking that allows network administrators to design, create, and run their networks innovatively. It includes high security, programmable network infrastructure, and incredible speed and flexibility with increased control. Are you searching for a SDN Security Architecture Importance Of Software Defined Networking SDN Graphics PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download SDN Security Architecture Importance Of Software Defined Networking SDN Graphics PDF from Slidegeeks today.

Checklist For Testing Of Application Programming Interface Security Testing Practices Microsoft PDF
This slide illustrates list of best practices for API security testing to ensure it is thorough. It includes budget resources and time, define the test types to run, etc. Showcasing this set of slides titled Checklist For Testing Of Application Programming Interface Security Testing Practices Microsoft PDF. The topics addressed in these templates are Application Programming, Interface Security, Testing Practices. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
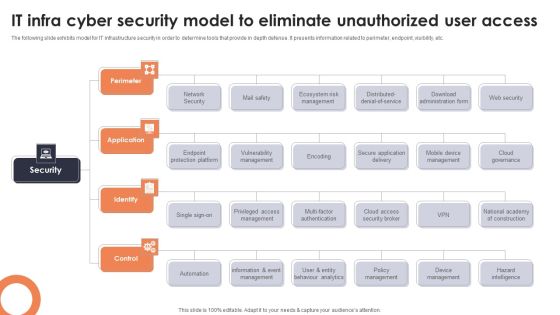
IT Infra Cyber Security Model To Eliminate Unauthorized User Access Topics PDF
The following slide exhibits model for IT infrastructure security in order to determine tools that provide in depth defense. It presents information related to perimeter, endpoint, visibility, etc. Presenting IT Infra Cyber Security Model To Eliminate Unauthorized User Access Topics PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Perimeter, Application, Identify. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Security Agency Business Profile Executive Leadership And Management Team Elements PDF
This slide highlights the security guard company management team which includes companys chairman and MD, head of security operations, training, strategic growth and site. Presenting Security Agency Business Profile Executive Leadership And Management Team Elements PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Business Economist, Resource Management, Manufacturing. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Developing IT Security Strategy Probability Assessment Matrix For Risk Management Formats PDF
This slide showcase matrix that can help organization to identify the probability of different information security attacks and formulate mitigation strategy in advance. It can help organization to manage the major risks and safeguard the information. Make sure to capture your audiences attention in your business displays with our gratis customizable Developing IT Security Strategy Probability Assessment Matrix For Risk Management Formats PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

5G Network Applications And Features Security In 5G Technology Architecture Download PDF
This slide depicts the security in 5G architecture, including the standards detailed by 3GPP 3rd Generation Partnership Project, such as SUPI, unified authentication, extensible authentication standards, and flexible security policies. Find highly impressive 5G Network Applications And Features Security In 5G Technology Architecture Download PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download 5G Network Applications And Features Security In 5G Technology Architecture Download PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Major Saas Cloud Security Risk Summary Ppt PowerPoint Presentation File Guidelines PDF
The following slide illustrates some SaaS security threats to enhance security practices and eliminate them. It includes elements such as phishing, account takeovers, lack of transparency etc. Showcasing this set of slides titled Major Saas Cloud Security Risk Summary Ppt PowerPoint Presentation File Guidelines PDF. The topics addressed in these templates are Comprehending Risks, Phishing, Account Takeovers. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
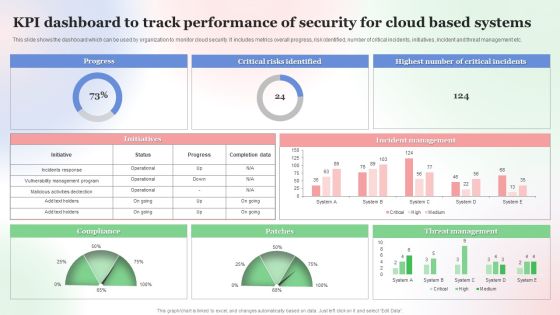
KPI Dashboard To Track Performance Of Security For Cloud Based Systems Clipart PDF
This slide shows the dashboard which can be used by organization to monitor cloud security. It includes metrics overall progress, risk identified, number of critical incidents, initiatives, incident and threat management etc. Showcasing this set of slides titled KPI Dashboard To Track Performance Of Security For Cloud Based Systems Clipart PDF. The topics addressed in these templates are Kpi Dashboard To Track, Performance Of Security, Cloud Based Systems . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cloud Security KPI Dashboard With Key Statistics Ppt Icon Examples PDF
Pitch your topic with ease and precision using this Cloud Security KPI Dashboard With Key Statistics Ppt Icon Examples PDF. This layout presents information on Compliance Trend, Risk Status, Risk Severity. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

IT Security Hacker Hacking Of Our Social Media Accounts Formats PDF
This slide represents the hacking of a companys social media accounts such as Facebook and Instagram by hackers in 2019 and the amount of money by running scam ads.Presenting IT Security Hacker Hacking Of Our Social Media Accounts Formats PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Scammers Gained, Business Manager, Altered The Password. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Management Roadmap With Program Maturity And Cost Ppt PowerPoint Presentation File Graphic Tips PDF
This slide covers quarterly cyber security planning roadmap by management to reduce risk with program maturity and cost .It consist secure , defend, contain, manage and anticipate. Persuade your audience using this Cyber Security Management Roadmap With Program Maturity And Cost Ppt PowerPoint Presentation File Graphic Tips PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Security Management, Level Risk Reduction. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Dashboard To Track IT Security Incidents Prevailing Across Firm Inspiration PDF
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Dashboard To Track IT Security Incidents Prevailing Across Firm Inspiration PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Artificial Intelligence For IT Operations Playbook Stage Five Security Breach Readiness Checklist Rules PDF
Purpose of this slide is to illustrate readiness checklist that will assist businesses in countering any security breach in advance. Readiness level will be evaluated based on different questions.Presenting Artificial Intelligence For IT Operations Playbook Stage Five Security Breach Readiness Checklist Rules PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Management Training, Potential Mitigation, Already Developed In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Mobile Device Management For Improving IT Operations Effective Mobile Device Security Mockup PDF
This slide portrays information regarding how firm is successful in handling security issues or events and is able in reducing the occurrence of events associated to mobile device. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Mobile Device Management For Improving IT Operations Effective Mobile Device Security Mockup PDF from Slidegeeks and deliver a wonderful presentation.

Information Security Integrity And Confidentiality Principle Of GDPR Law Structure PDF
This slide describes the integrity and confidentiality principle of GDPR, which implies putting suitable technologies and organizational safeguards to avoid hazards. Do you know about Slidesgeeks Information Security Integrity And Confidentiality Principle Of GDPR Law Structure PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

Global Cyber Terrorism Incidents On The Rise IT Timeline For Implementation Of Cyber Security Download PDF
This slide shows the timeframe for implementing a cyber security model in a business and the monthly activities that must be completed to fight cyber terrorism. Deliver and pitch your topic in the best possible manner with this global cyber terrorism incidents on the rise it timeline for implementation of cyber security download pdf. Use them to share invaluable insights on business, network, perform and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Project Security Administration IT Technological Assessment Of Firm Current Management Capabilities Professional PDF
This slide provides information regarding present management capabilities technological assessment based on several parameters such as incidents and service requests handling rate, service failure rate, customer satisfaction score, etc. Deliver and pitch your topic in the best possible manner with this project security administration it technological assessment of firm current management capabilities professional pdf. Use them to share invaluable insights on technological assessment of firm current management capabilities and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Workforce Security Realization Coaching Plan Idea Generation Ppt Infographics Display PDF
This is a workforce security realization coaching plan idea generation ppt infographics display pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like idea generation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Camera Services Proposal Template Table Of Contents One Pager Sample Example Document
Presenting you an exemplary Security Camera Services Proposal Template Table Of Contents One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Security Camera Services Proposal Template Table Of Contents One Pager Sample Example Document brilliant piece now.

Table Of Contents Security Camera Services Proposal Template One Pager Sample Example Document
Presenting you an exemplary Table Of Contents Security Camera Services Proposal Template One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Table Of Contents Security Camera Services Proposal Template One Pager Sample Example Document brilliant piece now.

Information Technology Security Program Ppt PowerPoint Presentation Complete Deck With Slides
Boost your confidence and team morale with this well-structured Information Technology Security Program Ppt PowerPoint Presentation Complete Deck With Slides. This prefabricated set gives a voice to your presentation because of its well-researched content and graphics. Our experts have added all the components very carefully, thus helping you deliver great presentations with a single click. Not only that, it contains a set of twelve slides that are designed using the right visuals, graphics, etc. Various topics can be discussed, and effective brainstorming sessions can be conducted using the wide variety of slides added in this complete deck. Apart from this, our PPT design contains clear instructions to help you restructure your presentations and create multiple variations. The color, format, design anything can be modified as deemed fit by the user. Not only this, it is available for immediate download. So, grab it now.
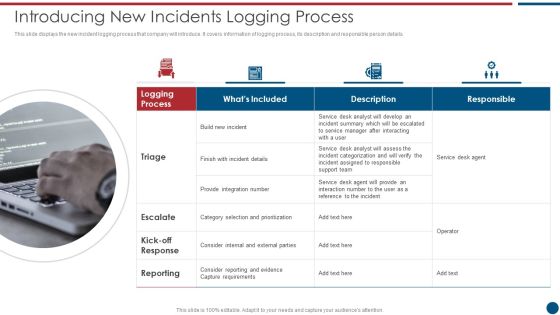
Risk Based Procedures To IT Security Introducing New Incidents Logging Process Microsoft PDF
This slide displays the new incident logging process that company will introduce. It covers information of logging process, its description and responsible person details. This is a Risk Based Procedures To IT Security Introducing New Incidents Logging Process Microsoft PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Service Desk, Support Team, Provide Integration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Info Security Minimize Administrative And Staff Privileges Ppt PowerPoint Presentation Icon Files PDF
This slide shows the importance of minimizing the administrative and staff privilege by showing its benefits for the company. Presenting info security minimize administrative and staff privileges ppt powerpoint presentation icon files pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like employees, prevent cyber attacks, administrative staff. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Developing IT Security Strategy Assessing Cost Of Information Breach In Different Countries Guidelines PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select edit data. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Developing IT Security Strategy Assessing Cost Of Information Breach In Different Countries Guidelines PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Developing IT Security Strategy Assessing Cost Of Information Breach In Different Countries Guidelines PDF.

Table Of Contents Safety And Security System Services Proposal One Pager Sample Example Document
Presenting you an exemplary Table Of Contents Safety And Security System Services Proposal One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Table Of Contents Safety And Security System Services Proposal One Pager Sample Example Document brilliant piece now.
Network Monitoring Management Security Ppt PowerPoint Presentation Summary Clipart Images Cpb
Presenting this set of slides with name network monitoring management security ppt powerpoint presentation summary clipart images cpb. This is an editable Powerpoint five stages graphic that deals with topics like network monitoring management security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Computer Network Security Training Ppt PowerPoint Presentation Slides Portfolio Cpb Pdf
Presenting this set of slides with name computer network security training ppt powerpoint presentation slides portfolio cpb pdf. This is an editable Powerpoint six stages graphic that deals with topics like computer network security training to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Insider Threat In Cyber Security Detection And Prevention Dashboard Diagrams PDF
This slide shows dashboard for detecting and preventing insider threats. It provides details about antivirus, vector detection, patch, admin access, email security, network and endpoint threat, etc. Pitch your topic with ease and precision using this Insider Threat In Cyber Security Detection And Prevention Dashboard Diagrams PDF. This layout presents information on Active Clients, Network Threat Prevention, Endpoint Threat Prevention. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

IT Risk Management Approaches Organizations Risk Management And IT Security Graphics PDF
This slide highlights the information technology risks management approaches which includes risk avoidance, risk sharing, risks reduction and risk retention. Want to ace your presentation in front of a live audience Our IT Risk Management Approaches Organizations Risk Management And IT Security Graphics PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.
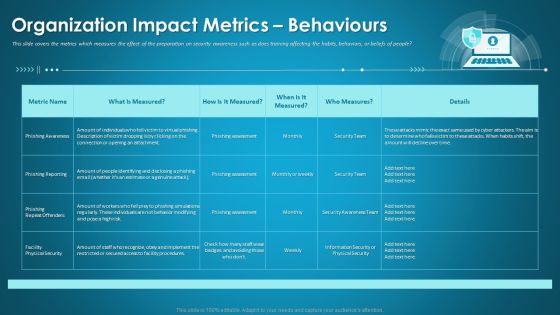
Organizational Network Security Awareness Staff Learning Organization Impact Metrics Behaviours Portrait PDF
This slide covers the metrics which measures the effect of the preparation on security awareness such as does training affecting the habits, behaviors, or beliefs of people. Deliver an awe-inspiring pitch with this creative organizational network security awareness staff learning organization impact metrics behaviours portrait pdf bundle. Topics like organization impact metrics behaviours can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Robotic Process Automation Security Best Practices To Minimize Cybercrime Risk Themes PDF
This slide outlines strategies to minimize security failure in RPA projects. Some of the best practices such as maintain accountability for BOT actions, prevent fraud and abuse, preserve log integrity, and authorize secure RPA development. Presenting Robotic Process Automation Security Best Practices To Minimize Cybercrime Risk Themes PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Maintain Accountability, Prevent Fraud And Abuse, Preserve Log Integrity. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Facts Assessment BI Design And Development Security Ppt PowerPoint Presentation Slides Master Slide PDF
Presenting this set of slides with name facts assessment bi design and development security ppt powerpoint presentation slides master slide pdf. This is a four stage process. The stages in this process are web based access, component based architecture, service oriented architecture, ssl security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Laptop With Security Shield And Lock Vector Icon Ppt PowerPoint Presentation Gallery Professional PDF
Presenting this set of slides with name laptop with security shield and lock vector icon ppt powerpoint presentation gallery professional pdf. This is a three stage process. The stages in this process are laptop with security shield and lock vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
User With Lock For Security Vector Icon Ppt PowerPoint Presentation Model Show PDF
Presenting this set of slides with name user with lock for security vector icon ppt powerpoint presentation model show pdf. This is a three stage process. The stages in this process are user with lock for security vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

KYC Transaction Monitoring System Business Security Suspicious Activity Reporting Process Flow Summary PDF
This slide showcases process flow of suspicious activity reporting SAR. It provides information about transaction alert, purpose, patterns, customer behavior, client lifestyle, negative news, adverse media, sanctions, anti money laundering AML, etc. Get a simple yet stunning designed KYC Transaction Monitoring System Business Security Suspicious Activity Reporting Process Flow Summary PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit KYC Transaction Monitoring System Business Security Suspicious Activity Reporting Process Flow Summary PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Proposal For Security Guard Services Table Of Contents One Pager Sample Example Document
Presenting you an exemplary Proposal For Security Guard Services Table Of Contents One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Proposal For Security Guard Services Table Of Contents One Pager Sample Example Document brilliant piece now.

Table Of Contents Security Services Proposal One Pager Sample Example Document
Presenting you an exemplary Table Of Contents Security Services Proposal One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Table Of Contents Security Services Proposal One Pager Sample Example Document brilliant piece now.

Table Of Contents Security And Safety System Proposal One Pager Sample Example Document
Presenting you an exemplary Table Of Contents Security And Safety System Proposal One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Table Of Contents Security And Safety System Proposal One Pager Sample Example Document brilliant piece now.
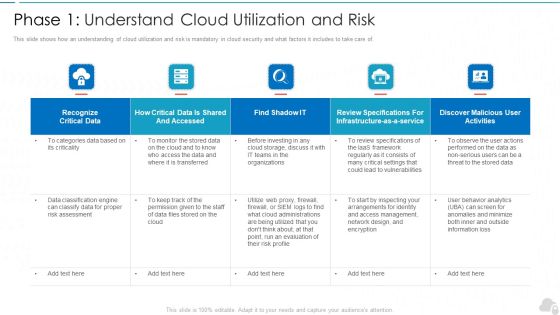
Phase 1 Understand Cloud Utilization And Risk Cloud Computing Security IT Ppt Summary Smartart PDF
This slide shows how an understanding of cloud utilization and risk is mandatory in cloud security and what factors it includes to take care of. Deliver and pitch your topic in the best possible manner with this phase 1 understand cloud utilization and risk cloud computing security it ppt summary smartart pdf. Use them to share invaluable insights on recognize critical data, infrastructure, evaluation, vulnerabilities, organizations and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Crime Threat To Security Ppt PowerPoint Presentation Visual Aids Files
Presenting this set of slides with name cyber crime threat to security ppt powerpoint presentation visual aids files. This is a one stage process. The stage in this process is cyber crime threat to security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Threat Detection Online Security Computer Program Ppt PowerPoint Presentation Professional Icon PDF
Presenting this set of slides with name threat detection online security computer program ppt powerpoint presentation professional icon pdf. This is a three stage process. The stages in this process are threat detection online security computer program. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

ERM Plan For Cyber Security Ppt PowerPoint Presentation File Ideas PDF
This slide displays the steps that helps to stay away from the threats of cyber security and makes clients feel safe from the cyber attacks. The steps includes Identifying digital assets, audit data, perform assessments, analyze risk level, establish committee ,etc. Persuade your audience using this ERM Plan For Cyber Security Ppt PowerPoint Presentation File Ideas PDF. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including Establish Risk Assessment Committee, Create Response Plan, Educate Employees On Policies. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

IT Security Minimize Administrative And Staff Privileges Ppt Inspiration Summary PDF
This slide shows the importance of minimizing the administrative and staff privilege by showing its benefits for the company. This is a it security minimize administrative and staff privileges ppt inspiration summary pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like minimize administrative and staff privileges. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Intelligent Computing System Security Strategic Planning Process For CPS Icons PDF
This slide represents the security strategic planning process for CPS, including business strategy, technology roadmap, vision statement environment trends, current state assessment, and so on. Deliver an awe inspiring pitch with this creative Cyber Intelligent Computing System Security Strategic Planning Process For CPS Icons PDF bundle. Topics like Gap Analysis, Environmental Trends, Business Strategy can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
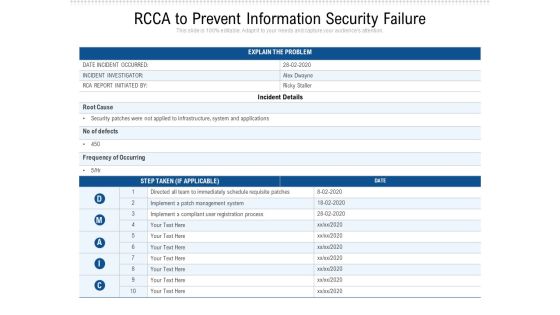
RCCA To Prevent Information Security Failure Ppt PowerPoint Presentation File Design Templates PDF
Showcasing this set of slides titled rcca to prevent information security failure ppt powerpoint presentation file design templates pdf. The topics addressed in these templates are implement, process, infrastructure. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
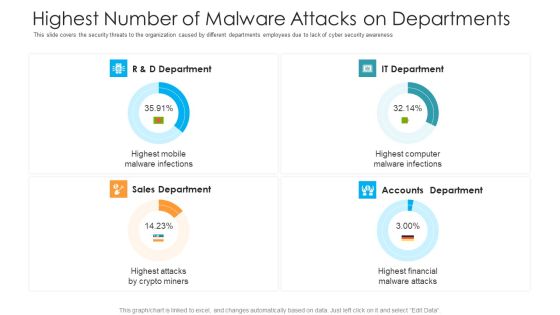
Highest Number Of Malware Attacks On Departments Hacking Prevention Awareness Training For IT Security Themes PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver and pitch your topic in the best possible manner with this highest number of malware attacks on departments hacking prevention awareness training for it security themes pdf. Use them to share invaluable insights on r and d department, it department, accounts department, sales department and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Assessment Of Internet Security Model Audit Report Ppt PowerPoint Presentation Portfolio Information PDF
Showcasing this set of slides titled assessment of internet security model audit report ppt powerpoint presentation portfolio information pdf. The topics addressed in these templates are cybersecurity framework function identify, manual check or medium, failed or high. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
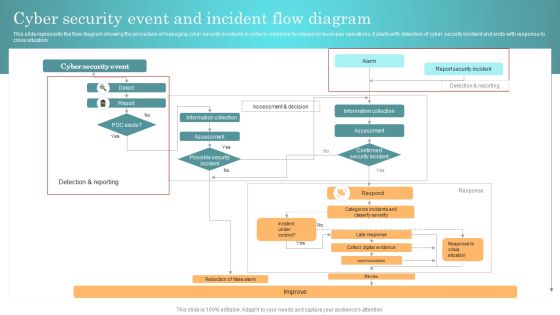
Incident Response Techniques Deployement Cyber Security Event And Incident Flow Diagram Structure PDF
This slide represents the flow diagram showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It starts with detection of cyber security incident and ends with response to crisis situation. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Incident Response Techniques Deployement Cyber Security Event And Incident Flow Diagram Structure PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Incident Response Techniques Deployement Cyber Security Event And Incident Flow Diagram Structure PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.

Table Of Contents For One Page Yearly Report For Internet Security Company One Pager Documents
Presenting you an exemplary Table Of Contents For One Page Yearly Report For Internet Security Company One Pager Documents. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Table Of Contents For One Page Yearly Report For Internet Security Company One Pager Documents brilliant piece now.

Proposal For Enterprise Security System Table Of Contents One Pager Sample Example Document
Presenting you an exemplary Proposal For Enterprise Security System Table Of Contents One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Proposal For Enterprise Security System Table Of Contents One Pager Sample Example Document brilliant piece now.

Proposal For House Security Devices Installation Table Of Contents One Pager Sample Example Document
Presenting you an exemplary Proposal For House Security Devices Installation Table Of Contents One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Proposal For House Security Devices Installation Table Of Contents One Pager Sample Example Document brilliant piece now.
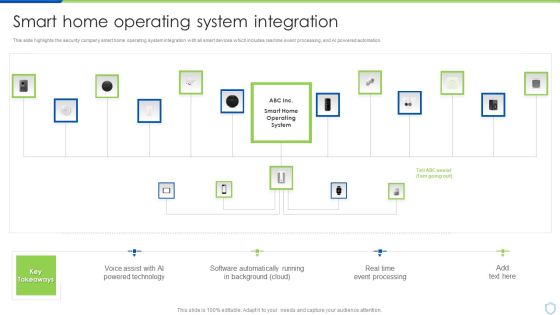
Security And Surveillance Company Profile Smart Home Operating System Integration Clipart PDF
This slide highlights the security company smart home operating system integration with all smart devices which includes real time event processing, and AI powered automation.Deliver an awe inspiring pitch with this creative Security And Surveillance Company Profile Smart Home Operating System Integration Clipart PDF bundle. Topics like Powered Technology, Software Automatically, Event Processing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
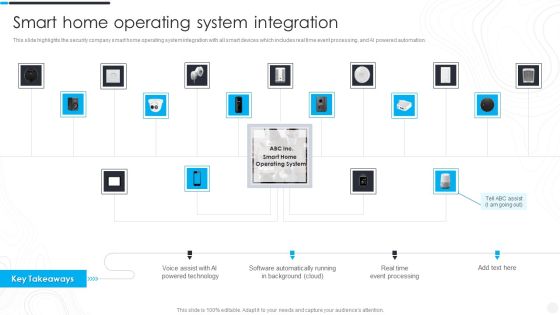
Security Camera System Company Profile Smart Home Operating System Integration Background PDF
This slide highlights the security company smart home operating system integration with all smart devices which includes real time event processing, and AI powered automation.Deliver an awe inspiring pitch with this creative Security Camera System Company Profile Smart Home Operating System Integration Background PDF bundle. Topics like Powered Technology, Software Automatically, Event Processing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Quarterly IT Innovation Approach Roadmap For Value And Security Benefit Elements
We present our quarterly it innovation approach roadmap for value and security benefit elements. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched quarterly it innovation approach roadmap for value and security benefit elements in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Cyber Security Technology Trends Ppt PowerPoint Presentation Model Graphics Download Cpb
Presenting this set of slides with name cyber security technology trends ppt powerpoint presentation model graphics download cpb. This is an editable Powerpoint four stages graphic that deals with topics like cyber security technology trends to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Operational Technology Cyber Security Ppt PowerPoint Presentation Inspiration File Formats Cpb
Presenting this set of slides with name operational technology cyber security ppt powerpoint presentation inspiration file formats cpb. This is an editable Powerpoint four stages graphic that deals with topics like operational technology cyber security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Technology Overview Cloud Access Security Ppt PowerPoint Presentation Model Ideas Cpb Pdf
Presenting this set of slides with name technology overview cloud access security ppt powerpoint presentation model ideas cpb pdf. This is an editable Powerpoint three stages graphic that deals with topics like technology overview cloud access security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

New Technology Handle Cyber Security Ppt PowerPoint Presentation Infographics Graphics Pictures Cpb
Presenting this set of slides with name new technology handle cyber security ppt powerpoint presentation infographics graphics pictures cpb. This is an editable Powerpoint three stages graphic that deals with topics like new technology handle cyber security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Laptop Showing Security Shield Vector Icon Ppt PowerPoint Presentation Gallery Example Topics PDF
Presenting this set of slides with name laptop showing security shield vector icon ppt powerpoint presentation gallery example topics pdf. This is a three stage process. The stages in this process are laptop showing security shield vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Laptop With Security Shield Vector Icon Ppt PowerPoint Presentation File Microsoft PDF
Presenting this set of slides with name laptop with security shield vector icon ppt powerpoint presentation file microsoft pdf. This is a three stage process. The stages in this process are laptop with security shield vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Supplier Risk Assessment In Procurement Information Security Ppt PowerPoint Presentation Complete Deck With Slides
Boost your confidence and team morale with this well-structured supplier risk assessment in procurement information security ppt powerpoint presentation complete deck with slides. This prefabricated set gives a voice to your presentation because of its well-researched content and graphics. Our experts have added all the components very carefully, thus helping you deliver great presentations with a single click. Not only that, it contains a set of ninteen slides that are designed using the right visuals, graphics, etc. Various topics can be discussed, and effective brainstorming sessions can be conducted using the wide variety of slides added in this complete deck. Apart from this, our PPT design contains clear instructions to help you restructure your presentations and create multiple variations. The color, format, design anything can be modified as deemed fit by the user. Not only this, it is available for immediate download. So, grab it now.

Cyber Attacks Experienced By Company In Previous Financial Year IT Security IT Ppt Icon Information PDF
This slide shows the impact on the organizations financial condition due to cyber attacks in the past financial year 2021. Deliver and pitch your topic in the best possible manner with this cyber attacks experienced by company in previous financial year it security it ppt icon information pdf. Use them to share invaluable insights on cyber attacks experienced by company in previous financial year and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Update And Installation Of Antivirus Software IT Security IT Ppt Information PDF
This slide depicts the benefits of using antivirus software in the organization, different antivirus software available in the market, and their usage by a graph. Deliver and pitch your topic in the best possible manner with this update and installation of antivirus software it security it ppt information pdf. Use them to share invaluable insights on organization, devices, antivirus software, software periodically and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Smart Phone Device With Security Lock Placed On Table Ppt Professional Inspiration PDF
Persuade your audience using this smart phone device with security lock placed on table ppt professional inspiration pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including smart phone device with security lock placed on table. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
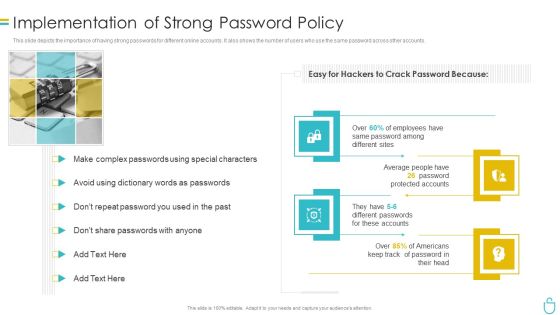
Information Security Implementation Of Strong Password Policy Ppt Styles Brochure PDF
This slide depicts the importance of having strong passwords for different online accounts. It also shows the number of users who use the same password across other accounts. This is a information security implementation of strong password policy ppt styles brochure pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like implementation of strong password policy. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
IT Security Analysis Checklist With Software And Hardware Risk Ppt PowerPoint Presentation Icon Examples PDF
Pitch your topic with ease and precision using this it security analysis checklist with software and hardware risk ppt powerpoint presentation icon examples pdf. This layout presents information on hardware risk, software risk. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

AI Risk Mitigation Framework For Information Security Ppt PowerPoint Presentation Gallery Slides PDF
Presenting ai risk mitigation framework for information security ppt powerpoint presentation gallery slides pdf to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including governance, independent validation, ongoing performance monitoring. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Business Information Security Management Board Ppt PowerPoint Presentation Gallery Designs Download PDF
Presenting business information security management board ppt powerpoint presentation gallery designs download pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including shareholders, enterprise, regulators. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
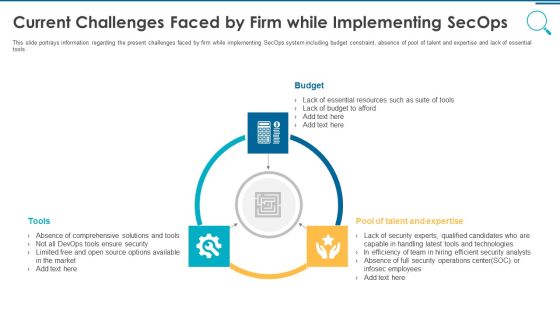
Information And Technology Security Operations Current Challenges Faced By Firm While Implementing Secops Slides PDF
This slide portrays information regarding the present challenges faced by firm while implementing SecOps system including budget constraint, absence of pool of talent and expertise and lack of essential tools. Presenting information and technology security operations current challenges faced by firm while implementing secops slides pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like budget tools, pool of talent and expertise. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

 Home
Home