Data Security And Protection

CASB 2 0 IT Cloud Access Security Broker Architectural Components
This slide outlines the main components of cloud access security broker architecture. The purpose of this slide is to showcase the primary elements of CASB architecture, including immediate enterprise core, secondary enterprise core, PaaS, IaaS, PaaS, connectivity gateway, and so on. This modern and well-arranged CASB 2 0 IT Cloud Access Security Broker Architectural Components provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
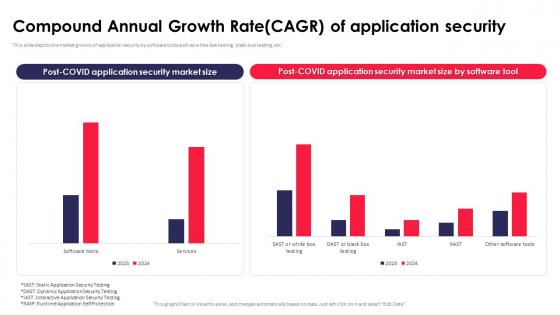
Compound Annual Growth Rate CAGR Of Application Security Testing
This slide depicts the market growth of application security by software tools such as white-box testing, black-box testing, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Compound Annual Growth Rate CAGR Of Application Security Testing template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Compound Annual Growth Rate CAGR Of Application Security Testing that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers

Working Of Security Tokenization In Financial Assets PPT Powerpoint
This slide highlights the phases of security tokenization. The purpose of this slide is to showcase the working of security tokenization along with its phases which include creation, dividend distribution, etc. Find a pre-designed and impeccable Working Of Security Tokenization In Financial Assets PPT Powerpoint. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
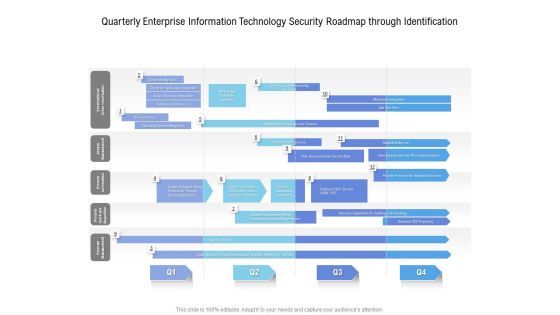
Quarterly Enterprise Information Technology Security Roadmap Through Identification Topics
We present our quarterly enterprise information technology security roadmap through identification topics. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched quarterly enterprise information technology security roadmap through identification topics in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Pricing Strategy Security Service Provider Business Model BMC SS V
slide showcases the companys product and service prices. It includes pricing strategies such as cost-based, competitor-oriented and marketing-led pricing. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Pricing Strategy Security Service Provider Business Model BMC SS V. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Pricing Strategy Security Service Provider Business Model BMC SS V today and make your presentation stand out from the rest

Table Of Contents For Cloud Security Firewall Proposal
Take your presentations to the next level with our Table Of Contents For Cloud Security Firewall Proposal template. With its sleek design and seamless editing features, this single-slide PPT template is a game-changer for professionals who want to make an impact. Impress your audience with stunning visuals and engaging content that will capture their attention from start to finish. Get your hands on our template and elevate your presentations to new heights.

Security Web Development Role Web Designing User Engagement Topics PDF
This slide represents the security development and how developers act as ethical hackers to prevent malicious attacks and reveal their vulnerabilities. Are you searching for a Security Web Development Role Web Designing User Engagement Topics PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Security Web Development Role Web Designing User Engagement Topics PDF from Slidegeeks today.
Information Technology Security KPI Icon With Monitor Pictures PDF
Persuade your audience using this Information Technology Security KPI Icon With Monitor Pictures PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Information Technology, Security KPI, Icon With Monitor. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
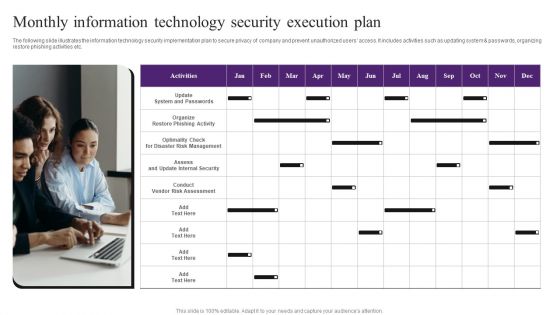
Monthly Information Technology Security Execution Plan Template PDF
The following slide illustrates the information technology security implementation plan to secure privacy of company and prevent unauthorized users access. It includes activities such as updating system and passwords, organizing restore phishing activities etc. Presenting Monthly Information Technology Security Execution Plan Template PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Update System And Passwords, Conduct Vendor Risk Assessment, Risk Management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
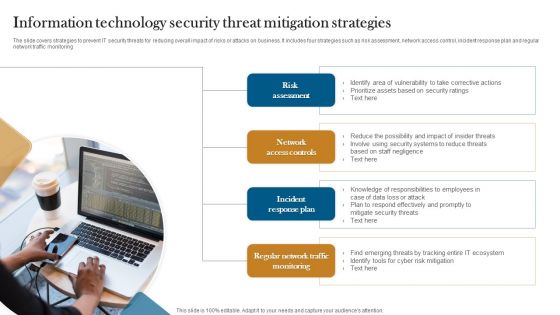
Information Technology Security Threat Mitigation Strategies Formats PDF
The slide covers strategies to prevent IT security threats for reducing overall impact of risks or attacks on business. It includes four strategies such as risk assessment, network access control, incident response plan and regular network traffic monitoring. Persuade your audience using this Information Technology Security Threat Mitigation Strategies Formats PDF. This PPT design covers Four stages, thus making it a great tool to use. It also caters to a variety of topics including Risk Assessment, Network Access Controls, Incident Response Plan. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Verizon Security Report In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Verizon Security Report In Powerpoint And Google Slides Cpb This completely editable PowerPoint graphic exhibits Verizon Security Report that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design.
Security Wireless In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Security Wireless In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Security Wireless that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design.

Cyber Security Paper Presentation In Powerpoint And Google Slides Cpb
Presenting our innovatively-designed set of slides titled Cyber Security Paper Presentation In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Cyber Security Paper Presentation that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design.

Security Playbook Example In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Security Playbook Example In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Security Playbook Example that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design.

Wifi Systems Security In Powerpoint And Google Slides Cpb
Presenting our innovatively-designed set of slides titled Wifi Systems Security In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Wifi Systems Security that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design.

Computer Personal Security In Powerpoint And Google Slides Cpb
Presenting our innovatively-designed set of slides titled Computer Personal Security In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Computer Personal Security that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design.
Smartphones Mobile Security In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Smartphones Mobile Security In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Smartphones Mobile Security that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design.

Suggested Coverage For Security Management Plan Information PDF
This slide provides information about the areas that are covered under the security management plan. This is a suggested coverage for security management plan information pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like governance arrangement, information including ict security, personnel security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Technology Strategy Cloud Security Architect Skills Scope Background PDF
This slide depicts the cloud security architect skills scope which includes architecture and strategy, leadership, operational technical, etc. Deliver an awe inspiring pitch with this creative information technology strategy cloud security architect skills scope background pdf bundle. Topics like architecture and strategy, technical, leadership, operational can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Communication Plan For Information Technology Asset Security Threats Pictures PDF
This slide consists of a communication plan that can be implemented by managers to safeguard information technology assets from cyber threats and create an effective response plan. Major elements covered are IT security assets, risk, threat, risk impact, etc. Showcasing this set of slides titled Communication Plan For Information Technology Asset Security Threats Pictures PDF. The topics addressed in these templates are ZZZZZZZZZZZZZZZZZZZZIT Servers, Network Systems, ModemZZZZZZZZZZZZZ. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

NIST Cybersecurity Framework Process For Security Control Selection Introduction PDF
Mentioned slide showcases the process to choose security controls based on Nist security control. It include steps like security categorization using FIPS 199, identify baseline security controls, tailoring baseline security controls and document the control selection process. Presenting NIST Cybersecurity Framework Process For Security Control Selection Introduction PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Security Controls, Tailoring Baseline, Selection Process. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Develop Security Token Offering Plan Exploring Investment Opportunities Brochure Pdf
The following slide depicts sample security token offering STO plan to enable fundraising and crowd funding activities. It includes elements such as number of tokens, percentage allocated to public, private investors, pre-sale participants, project teams, reserve funds, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Develop Security Token Offering Plan Exploring Investment Opportunities Brochure Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Hazard Prevention Workplace Safety Protocol And Security Practices Ideas Pdf
This slide highlights the hard prevention and control measures which includes check control options, select control plan, measure non routine operations and implement hazard controls. This Hazard Prevention Workplace Safety Protocol And Security Practices Ideas Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Hazard Prevention Workplace Safety Protocol And Security Practices Ideas Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
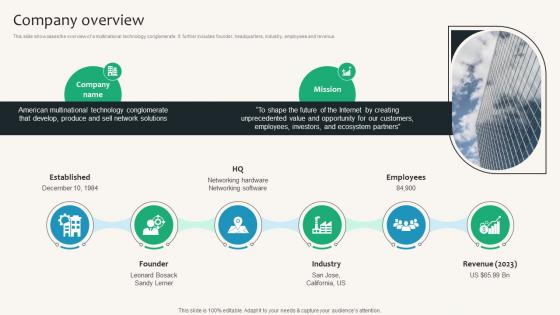
Company Overview Security Service Provider Business Model BMC SS V
This slide showcases the overview of a multinational technology conglomerate. It further includes founder, headquarters, industry, employees and revenue. Create an editable Company Overview Security Service Provider Business Model BMC SS V that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Company Overview Security Service Provider Business Model BMC SS V is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
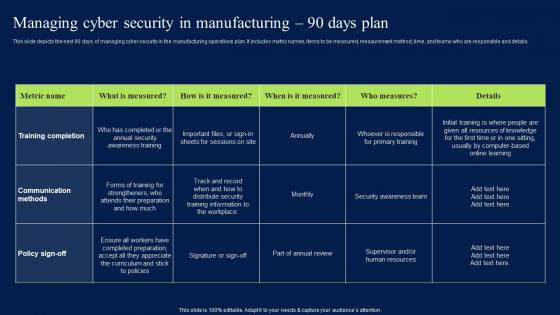
Managing Cyber Security In Manufacturing 90 Days Plan Professional PDF
This slide depicts the next 90 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, andteams who are responsible and details. Slidegeeks has constructed Managing Cyber Security In Manufacturing 90 Days Plan Professional PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
Security Instalation Proposal In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Security Instalation Proposal In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Security Instalation Proposal that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design.
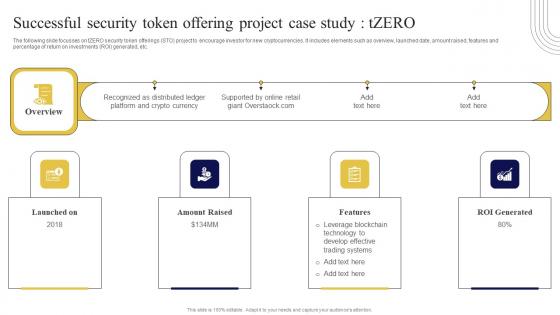
Successful Security Token Offering Exploring Investment Opportunities Background Pdf
The following slide focusses on tZERO security token offerings STO project to encourage investor for new cryptocurrencies. It includes elements such as overview, launched date, amount raised, features and percentage of return on investments ROI generated, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Successful Security Token Offering Exploring Investment Opportunities Background Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Successful Security Token Offering Exploring Investment Opportunities Background Pdf.

Security Challenges Of IoT In Revolutionizing Production IoT Ppt Example
This slide aims to analyze security challenges faced by organizations in IoT in manufacturing. It includes various problems such as insecure web interfaces, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Security Challenges Of IoT In Revolutionizing Production IoT Ppt Example to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Security Challenges Of IoT In Revolutionizing Production IoT Ppt Example.

Example Of Security Testing Services Ppt Powerpoint Guide
This is a example of security testing services ppt powerpoint guide. This is a eight stage process. The stages in this process are security management, access security, application security, networking security, test delivery, results and analysis, technology enablement, test development and publishing.
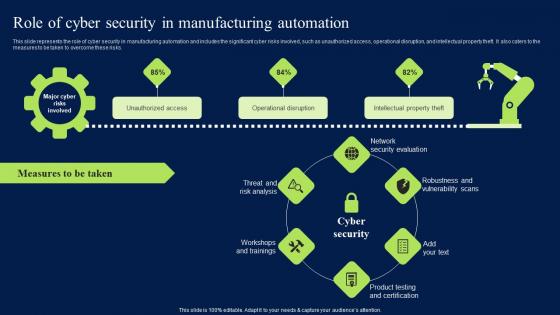
Role Of Cyber Security In Manufacturing Automation Clipart PDF
This slide represents the role of cyber security in manufacturing automation and includes the significant cyber risks involved, such as unauthorized access, operational disruption, and intellectual property theft. It also caters to the measures to be taken to overcome these risks. Find highly impressive Role Of Cyber Security In Manufacturing Automation Clipart PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Role Of Cyber Security In Manufacturing Automation Clipart PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now

Assessing Number Of Security Tokens Exploring Investment Opportunities Introduction Pdf
The following slide depicts the number of security token offerings STOs launched by industry type. It includes elements such as finance, banking, blockchain, real estate, service, technology, healthcare, software, sports, art, energy, etc. Want to ace your presentation in front of a live audience Our Assessing Number Of Security Tokens Exploring Investment Opportunities Introduction Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.
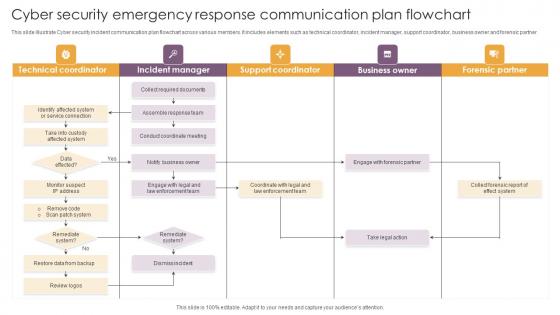
Cyber Security Emergency Response Communication Plan Flowchart Infographics Pdf
This slide illustrate Cyber security incident communication plan flowchart across various members. It includes elements such as technical coordinator, incident manager, support coordinator, business owner and forensic partner Showcasing this set of slides titled Cyber Security Emergency Response Communication Plan Flowchart Infographics Pdf The topics addressed in these templates are Technical Coordinator, Incident Manager, Support Coordinator All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Core Competencies Of Internet Security Threat Portrait Pdf
This slide showcase cyber security risk assessment with core competencies and constantly evolving digital infrastructure. It includes cyber transformation, financial operations, cloud computing and project management.Showcasing this set of slides titled Core Competencies Of Internet Security Threat Portrait Pdf The topics addressed in these templates are Cyber Transformation, Cloud Computing, Financial Operations All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

4 Steps For Developing IT Security Plan Professional PDF
This slide represents 4 steps for developing cyber security strategy such as understanding cyber threats, assessing cyber security maturity, determining steps to improve cyber security program and documentation. Presenting 4 Steps For Developing IT Security Plan Professional PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Documenting Cyber Security Plan, Assessing Cyber Security Maturity, Organizations. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
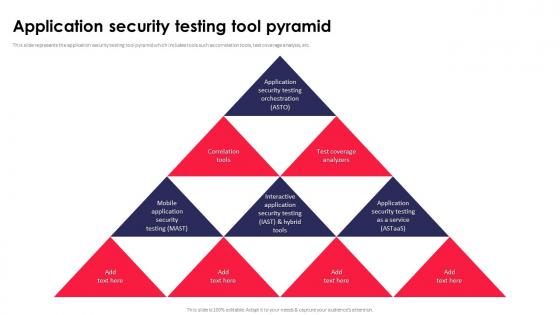
Application Security Testing Tool Pyramid Ppt Powerpoint Download
This slide represents the application security testing tool pyramid which includes tools such as correlation tools, test coverage analysis, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Application Security Testing Tool Pyramid Ppt Powerpoint Download a try. Our experts have put a lot of knowledge and effort into creating this impeccable Application Security Testing Tool Pyramid Ppt Powerpoint Download. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today
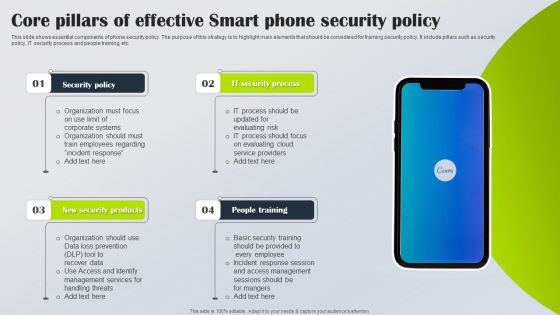
Core Pillars Of Effective Smart Phone Security Policy Slides PDF
This slide shows essential components of phone security policy. The purpose of this strategy is to highlight main elements that should be considered for framing security policy. It include pillars such as security policy, IT security process and people training, etc. Persuade your audience using this Core Pillars Of Effective Smart Phone Security Policy Slides PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Security Policy, IT Security Process, New Security Products. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
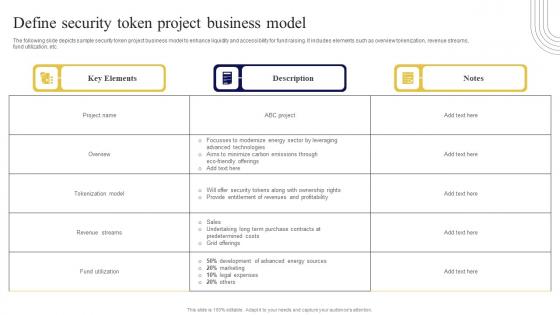
Define Security Token Project Business Exploring Investment Opportunities Ideas Pdf
The following slide depicts sample security token project business model to enhance liquidity and accessibility for fund raising. It includes elements such as overview tokenization, revenue streams, fund utilization, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Define Security Token Project Business Exploring Investment Opportunities Ideas Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Teamwork Security In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Teamwork Security In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Teamwork Security that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design.

Cyber Security Training Roadmap In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Cyber Security Training Roadmap In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Cyber Security Training Roadmap that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design.
Security Reporting Template In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Security Reporting Template In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Security Reporting Template that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design.
Endpoint Security Checklist In Powerpoint And Google Slides Cpb
Presenting our innovatively-designed set of slides titled Endpoint Security Checklist In Powerpoint And Google Slides Cpb This completely editable PowerPoint graphic exhibits Endpoint Security Checklist that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design.
Best Security Management In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Best Security Management In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Best Security Management that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design.

National Security Budget In Powerpoint And Google Slides Cpb
Presenting our innovatively-designed set of slides titled National Security Budget In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits National Security Budget that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design.
Computer Flaw Cyber Security In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Computer Flaw Cyber Security In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Computer Flaw Cyber Security that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design.

Tab Manager Security In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Tab Manager Security In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Tab Manager Security that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design.
Security System In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Security System In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Security System that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design.

Various KPI For Cyber Security Breach Worldwide Pictures Pdf
This template shows the various key performance indicators for malware attacks around the world. The purpose of this slide is to evaluated how much devices get affected within 24 hours The various KPI such as streaming, worldwide, mode of attacks, etc. Showcasing this set of slides titled Various KPI For Cyber Security Breach Worldwide Pictures Pdf The topics addressed in these templates are Cyber Security Breach, Worldwide All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
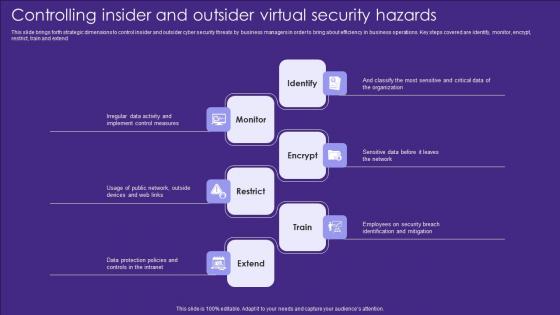
Controlling Insider And Outsider Virtual Security Hazards Designs Pdf
This slide brings forth strategic dimensions to control insider and outsider cyber security threats by business managers in order to bring about efficiency in business operations. Key steps covered are identify, monitor, encrypt, restrict, train and extend Showcasing this set of slides titled Controlling Insider And Outsider Virtual Security Hazards Designs Pdf. The topics addressed in these templates are Identify, Monitor, Encrypt. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Strategic Plan Roadmap For Cyber Security Project Information PDF
This slide signifies the twelve week strategic plan timeline for effective cyber security project. It covers information about installing security, configuring security, provide training and performing penetration testing Pitch your topic with ease and precision using this Strategic Plan Roadmap For Cyber Security Project Information PDF. This layout presents information on Strategic, Plan, Project. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Wireless Network Security System Icon For Car Insurance Professional PDF
Presenting wireless network security system icon for car insurance professional pdf to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including wireless network security system icon for car insurance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Digital Cloud Network Cyber Security Icon Clipart PDF
Presenting Digital Cloud Network Cyber Security Icon Clipart PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Digital Cloud, Network Cyber, Security Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
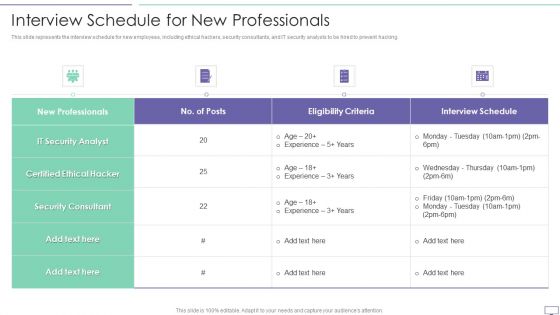
IT Security Hacker Interview Schedule For New Professionals Portrait PDF
This slide represents the interview schedule for new employees, including ethical hackers, security consultants, and IT security analysts to be hired to prevent hacking.Deliver and pitch your topic in the best possible manner with this IT Security Hacker Interview Schedule For New Professionals Portrait PDF. Use them to share invaluable insights on Ethical Hacker, Security Consultant, Security Analyst and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information Security Management And Management Program Framework Inspiration PDF
This slide showcases a framework of information security governance and management to develop business specific risk control program. It includes key components such as identify security, infrastructure security, HR security, detection, response and recovery, measurement, etc. Showcasing this set of slides titled Information Security Management And Management Program Framework Inspiration PDF. The topics addressed in these templates are Governance, Management, Key Insights All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
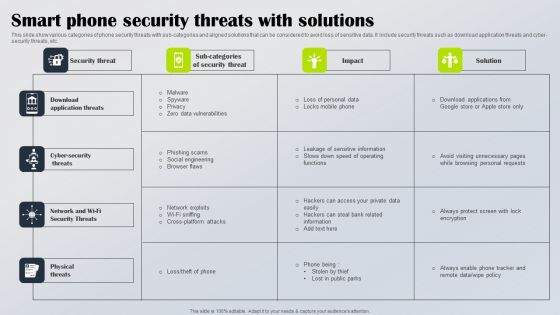
Smart Phone Security Threats With Solutions Diagrams PDF
This slide show various categories of phone security threats with sub categories and aligned solutions that can be considered to avoid loss of sensitive data. It include security threats such as download application threats and cyber security threats, etc. Showcasing this set of slides titled Smart Phone Security Threats With Solutions Diagrams PDF. The topics addressed in these templates are Download Application Threats, Cyber Security Threats, Network Wi Fi Security Threats. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Electronic Banking Security Icon With Dollar Sign Information PDF
Persuade your audience using this Electronic Banking Security Icon With Dollar Sign Information PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Electronic Banking Security Icon, Dollar Sign. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Icons Slide For Zero Trust Security Template Pdf
Introducing our well designed Icons Slide For Zero Trust Security Template Pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.

Implementation Process Of Network Infra Cyber Security Introduction PDF
The following slide showcases process to implement network infra security to ensure that underlying infrastructure remains protected. It presents information related to segmentation networks, validation of hardware, etc. Presenting Implementation Process Of Network Infra Cyber Security Introduction PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Segmentation Networks, Secure Access Infrastructure, Validate Hardware. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Google Cloud Services Identity And Security Graphics PDF
This slide describes the identity and security service of google cloud, and it includes cloud resource manager, cloud IAM, cloud security scanner, and cloud platform security. This is a Google Cloud Services Identity And Security Graphics PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Cloud Resource Manager, Cloud Security Scanner, Cloud Platform Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Sample Of Security Knowledge Management Diagram Ppt Example
This is a sample of security knowledge management diagram ppt example. This is a four stage process. The stages in this process are detection of relocations, position information management, security management, management department.

Internet Security Threat Analysis With Response And Recovery Information PDF
This slide exhibits network security breach with response and recovery .It includes multiple steps such as- identify, project, detect, respond and recover. Pitch your topic with ease and precision using this internet security threat analysis with response and recovery information pdf. This layout presents information on internet security threat analysis with response and recovery. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
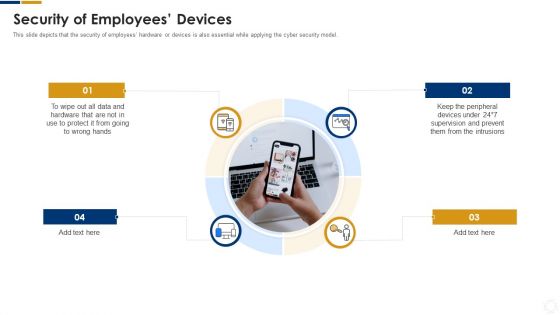
Cybersecurity Security Of Employees Devices Ppt Styles Graphic Images PDF
This slide depicts that the security of employees hardware or devices is also essential while applying the cyber security model. This is a cybersecurity security of employees devices ppt styles graphic images pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security of employees devices. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
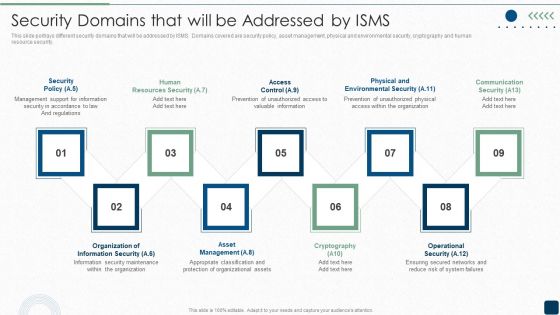
Security Domains That Will Be Addressed By ISMS Diagrams PDF
This slide portrays different security domains that will be addressed by ISMS. Domains covered are security policy, asset management, physical and environmental security, cryptography and human resource security.This is a Security Domains That Will Be Addressed By ISMS Diagrams PDF template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Management Support, Resources Security, Prevention Of Unauthorized. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
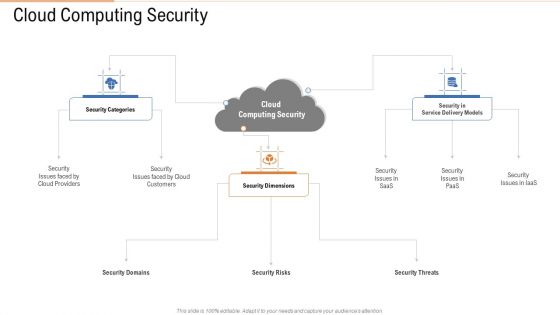
Cloud Computing Security Ppt Portfolio Background Images PDF
Presenting cloud computing security ppt portfolio background images pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like security dimensions, customers, security categories. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Functional Technology Icon For Security Threat Detection Structure PDF
Presenting functional technology icon for security threat detection structure pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including functional technology icon for security threat detection. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Cloud Deployment Security Management Technology Icon Topics PDF
Presenting Cloud Deployment Security Management Technology Icon Topics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Cloud Deployment Security, Management Technology Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Mobile Application Security Management Technology Icon Structure PDF
Presenting Mobile Application Security Management Technology Icon Structure PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Mobile Application Security, Management Technology Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Motion Smart Sensor Technology For Security Improvement Icon Mockup PDF
Presenting Motion Smart Sensor Technology For Security Improvement Icon Mockup PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Motion Smart, Sensor Technology, Security Improvement. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
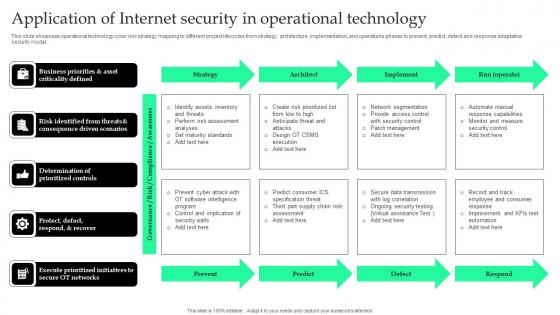
Application Of Internet Security In Operational Technology Pictures Pdf
This slide showcase operational technology cyber risk strategy mapping to different project lifecycles from strategy, architecture, implementation, and operations phases to prevent, predict, detect and response adaptative security model.Showcasing this set of slides titled Application Of Internet Security In Operational Technology Pictures Pdf The topics addressed in these templates are Consequence Driven Scenarios, Execute Prioritized, Risk Identified All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Security In 5G Technology Architecture 5G Functional Architecture Formats PDF
This slide depicts the security in 5G architecture, including the standards detailed by 3GPP 3rd Generation Partnership Project, such as SUPI, unified authentication, extensible authentication standards, and flexible security policies.This is a Security In 5G Technology Architecture 5G Functional Architecture Formats PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Previous Generations, Distinguish Authentication, Transactions Adaptable. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Table Of Contents For Cloud Security Assessment Cont Background PDF
This is a Table Of Contents For Cloud Security Assessment Cont Background PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Cloud Security, Security Responsibilities, Security Management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Types Information Security Ppt PowerPoint Presentation Outline Clipart Cpb
Presenting this set of slides with name types information security ppt powerpoint presentation outline clipart cpb. This is an editable Powerpoint four stages graphic that deals with topics like types information security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Elements Of NIST Cyber Security Framework Ideas PDF
The slide highlights the core elements or functions of Nist cyber security framework that enables to effectively outline your organizations cyber security goals and objectives. It includes identify, protect, detect, respond and recover. Persuade your audience using this Elements Of NIST Cyber Security Framework Ideas PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Incident Reoccurrences, Vulnerabilities, Framework. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

IT Security Defense Plan Maturity Evaluation Information PDF
This slide represents cyber security defense strategy maturity evaluation mode illustrating culture and organization, governance, visibility and controls, focused defense and intelligence operations. Persuade your audience using this IT Security Defense Plan Maturity Evaluation Information PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Organization, Focused Defense, Intelligence Operations. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Food Security Checklist To Fulfill Customer Standards Icons Pdf
Following slide shows the food safety check list to satisfy consumer requirements which will assist in measuring quality standards of food. It includes such as food preparation safety, contamination and frozen food. Showcasing this set of slides titled Food Security Checklist To Fulfill Customer Standards Icons Pdf. The topics addressed in these templates are Parameter, Inspected, Comments. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Voice Assistance Security Platform Investor Funding Presentation Complete Deck
This unique Voice Assistance Security Platform Investor Funding Presentation Complete Deck is a compendium of amazing information,actionable ideas on all business issues. The design of the presentation template ensures you have an ample opportunity to pick and choose areas you might want to emphasize. The thirty eight slides in the presentation template or all wonderfully colour coded to and ensure that you can get on with delivering your message with speed,and amazing effectiveness. Talk about management,leadership,change management,digital transformation etc with the unparalleled advantage of 100 percent customization of each and every elements of all our slides. Download now and see presentation take on a new dimension.

Checklist For Inspecting Office Security To Ensure Employees Portrait Pdf
Following slide shows checklist for office safety inspection to assure staff which will assist in reducing employee turnover because of work environment. It includes major parameters such as housekeeping, ergonomics, electricals, etc. Showcasing this set of slides titled Checklist For Inspecting Office Security To Ensure Employees Portrait Pdf. The topics addressed in these templates are Satisfactory, Unsatisfactory, Checklist Parameters. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
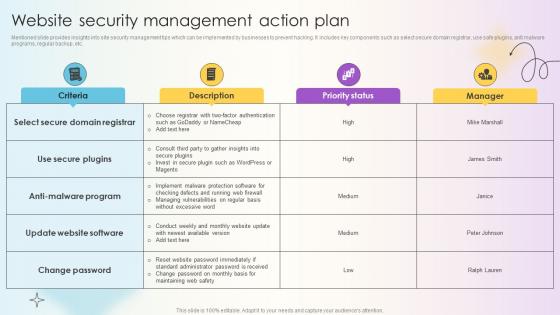
Managing Technical And Non Website Security Management Action Plan
Mentioned slide provides insights into site security management tips which can be implemented by businesses to prevent hacking. It includes key components such as select secure domain registrar, use safe plugins, anti malware programs, regular backup, etc. Welcome to our selection of the Managing Technical And Non Website Security Management Action Plan. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

Comprehensive Guide For Website Website Security Management Action Plan
Mentioned slide provides insights into site security management tips which can be implemented by businesses to prevent hacking. It includes key components such as select secure domain registrar, use safe plugins, anti malware programs, regular backup, etc. Welcome to our selection of the Comprehensive Guide For Website Website Security Management Action Plan. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

Current Security Management Plan Critical Success Factors Guidelines PDF
This slide shows some of the current IT Security Management Critical Success Factors of the company prior to the proactive measures taken by the company to mitigate security management problems and implementing an advanced Information Security Management System. Deliver and pitch your topic in the best possible manner with this current security management plan critical success factors guidelines pdf. Use them to share invaluable insights on security incidents level, security related service downtimes, intrusion attempts and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Current Security Management Plan Critical Success Factors Infographics PDF
This slide shows some of the current IT Security Management Critical Success Factors of the company prior to the proactive measures taken by the company to mitigate security management problems and implementing an advanced Information Security Management System.Deliver an awe inspiring pitch with this creative Current security management plan critical success factors infographics pdf bundle. Topics like security incidents level, security management, critical success factors can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Current Security Management Plan Critical Success Factors Topics PDF
This slide shows some of the current IT Security Management Critical Success Factors of the company prior to the proactive measures taken by the company to mitigate security management problems and implementing an advanced Information Security Management System.Deliver an awe inspiring pitch with this creative current security management plan critical success factors topics pdf bundle. Topics like security management, intrusion attempts, security implementation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
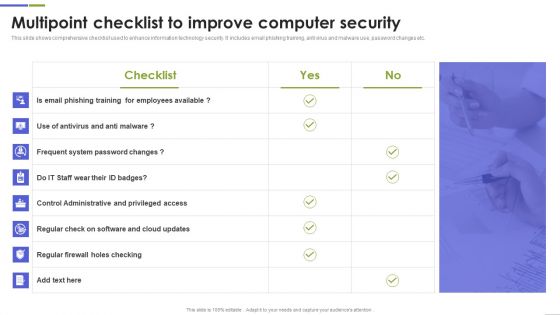
Multipoint Checklist To Improve Computer Security Guidelines PDF
This slide shows comprehensive checklist used to enhance information technology security. It includes email phishing training, anti virus and malware use, password changes etc. Showcasing this set of slides titled Multipoint Checklist To Improve Computer Security Guidelines PDF The topics addressed in these templates are Frequent System, Control Administrative, System Password All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Users Password IT Security Analysis Dashboard Elements PDF
This slide displays the analysis of the users password security in an organization to make sure that the users confidential details are safe. It includes security gains, password evaluation, active users data, activities of password, etc. Showcasing this set of slides titled Users Password IT Security Analysis Dashboard Elements PDF. The topics addressed in these templates are Password Evaluation Score, Security Gains. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
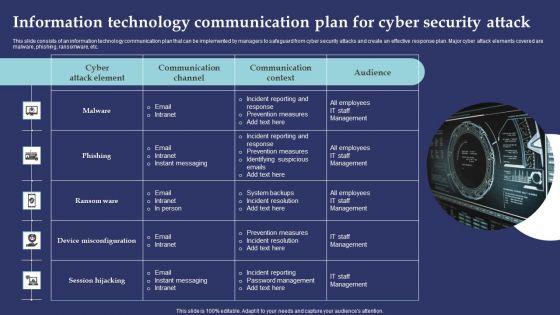
Information Technology Communication Plan For Cyber Security Attack Summary PDF
This slide consists of an information technology communication plan that can be implemented by managers to safeguard from cyber security attacks and create an effective response plan. Major cyber attack elements covered are malware, phishing, ransomware, etc. Presenting Information Technology Communication Plan For Cyber Security Attack Summary PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Incident Reporting Response, Prevention Measures, Incident Reporting. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Certified Information Systems Security Professional Cissp Examination Details Elements PDF
This slide covers information about CISSP Examination such as weight of each domain in exams, prep courses details, qualification details etc. Deliver an awe inspiring pitch with this creative certified information systems security professional cissp examination details elements pdf bundle. Topics like requirements, network security, security engineering, management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Technology Security Communication Channel Selection Plan Template PDF
Following slide consists of a matrix for selecting information technology security communication channels in order to ensure the seamless delivery of key messages to relevant stakeholders. Key content types are detailed messages, notifications, community feeds, documents, etc. Presenting Information Technology Security Communication Channel Selection Plan Template PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Detailed Message, Notifications, Community Feed. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Information Technology Security Crisis Communication Plan Checklist Professional PDF
Following slide presents an information technology security crisis communication plan checklist that can be used by information technology managers to ensure the effective preparation of a communication plan. Key elements covered in the checklist are identifying office protocol, creating a list of IT terms, etc. Presenting Information Technology Security Crisis Communication Plan Checklist Professional PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Communications Team, Internal Communication Plan, Dissemination Information. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
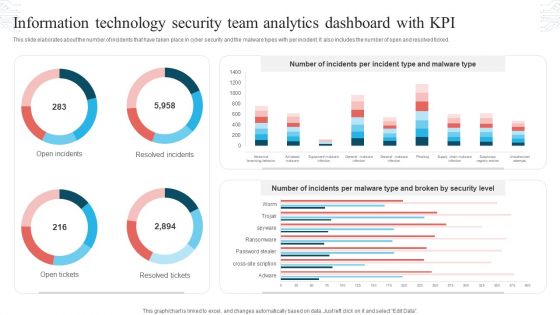
Information Technology Security Team Analytics Dashboard With KPI Themes PDF
This slide elaborates about the number of incidents that have taken place in cyber security and the malware types with per incident. It also includes the number of open and resolved ticked. Showcasing this set of slides titled Information Technology Security Team Analytics Dashboard With KPI Themes PDF. The topics addressed in these templates are Open Incidents, Resolved Incidents, Open Tickets, Resolved Tickets. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
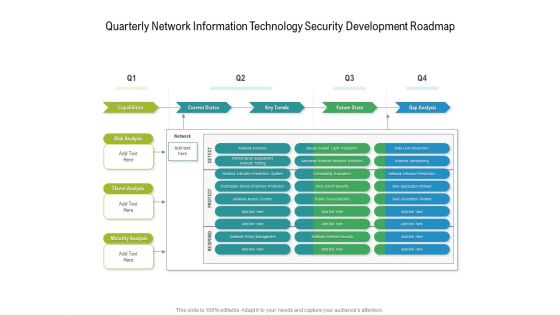
Quarterly Network Information Technology Security Development Roadmap Diagrams
Presenting our jaw dropping quarterly network information technology security development roadmap diagrams. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
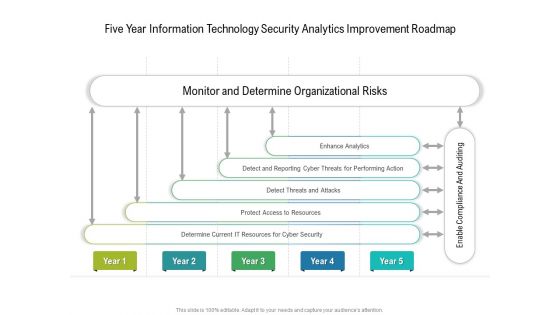
Five Year Information Technology Security Analytics Improvement Roadmap Infographics
We present our five year information technology security analytics improvement roadmap infographics. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched five year information technology security analytics improvement roadmap infographics in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Half Yearly Enterprise Information Technology Security Roadmap Through Identification Summary
We present our half yearly enterprise information technology security roadmap through identification summary. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched half yearly enterprise information technology security roadmap through identification summary in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Six Months Enterprise Information Technology Security Roadmap Through Identification Infographics
We present our six months enterprise information technology security roadmap through identification infographics. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched six months enterprise information technology security roadmap through identification infographics in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
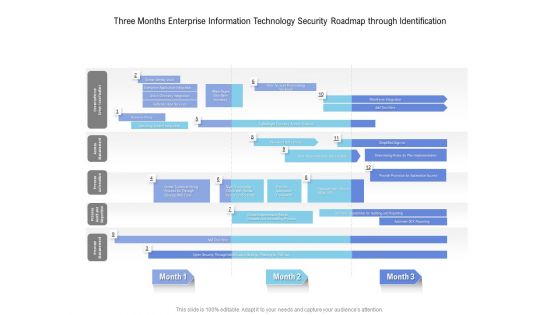
Three Months Enterprise Information Technology Security Roadmap Through Identification Introduction
We present our three months enterprise information technology security roadmap through identification introduction. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched three months enterprise information technology security roadmap through identification introduction in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
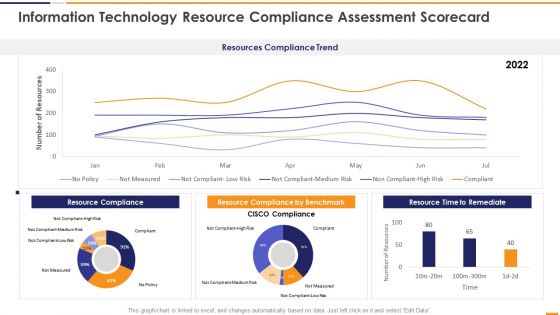
IT Security Evaluation Scorecard Information Technology Resource Compliance Background PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver and pitch your topic in the best possible manner with this IT Security Evaluation Scorecard Information Technology Resource Compliance Background PDF. Use them to share invaluable insights on Resources Compliance Trend, Resource Compliance 2022, Resource Compliance Benchmark, Resource Time Remediate and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
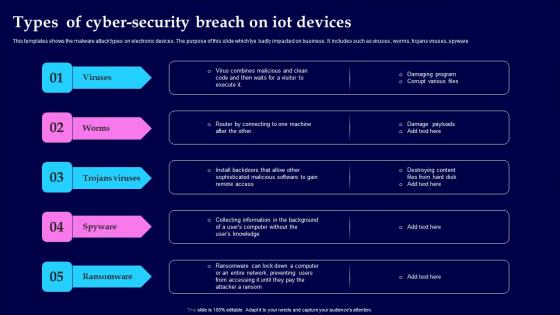
Types Of Cyber Security Breach On IOT Devices Themes Pdf
This templates shows the malware attack types on electronic devices. The purpose of this slide which tye badly impacted on business. It includes such as viruses, worms, trojans viruses, spyware Pitch your topic with ease and precision using this Types Of Cyber Security Breach On IOT Devices Themes Pdf This layout presents information on Viruses, Trojans Viruses, Spyware, Ransomware It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
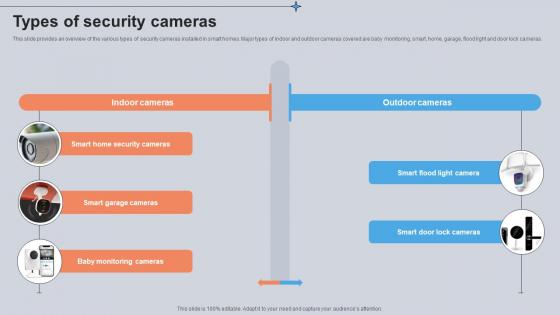
Types Of Security Cameras Utilizing Smart Appliances IoT SS V
This slide provides an overview of the various types of security cameras installed in smart homes. Major types of indoor and outdoor cameras covered are baby monitoring, smart, home, garage, flood light and door lock cameras. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Types Of Security Cameras Utilizing Smart Appliances IoT SS V. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Types Of Security Cameras Utilizing Smart Appliances IoT SS V today and make your presentation stand out from the rest

Information And Technology Security Operations Circular Inspiration PDF
This is a information and technology security operations circular inspiration pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like circular. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information And Technology Security Operations Timeline Slides PDF
This is a information and technology security operations timeline slides pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like timeline, 2017 to 2021. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
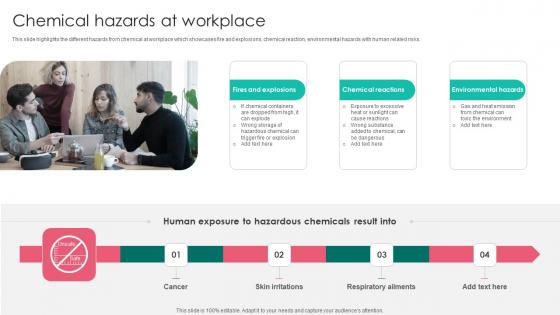
Chemical Hazards Workplace Safety Protocol And Security Practices Themes Pdf
This slide highlights the different hazards from chemical at workplace which showcases fire and explosions, chemical reaction, environmental hazards with human related risks. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Chemical Hazards Workplace Safety Protocol And Security Practices Themes Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Chemical Hazards Workplace Safety Protocol And Security Practices Themes Pdf today and make your presentation stand out from the rest

Security And Safety Checklist For Hotel Industry Summary PDF
This slide covers checklist for ensuring safety of visitors at hotels. The checklist includes security screening of bags, professional security team and screening of people at entrance.Showcasing this set of slides titled Security And Safety Checklist For Hotel Industry Summary PDF The topics addressed in these templates are Professional Security, Security Screening, Vehicles Screened All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Methods To Improve Online Banking Security Incorporating Banking Operational Growth
The purpose of the mentioned slide is to showcase the various ways to improve Internet banking security from hackers and fraudants. It includes methods such as industry-standard security protocol, avoiding public Wi-Fi, etc. Do you know about Slidesgeeks Methods To Improve Online Banking Security Incorporating Banking Operational Growth These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

Security Checklist Ppt Powerpoint Presentation Complete Deck With Slides
This Security Checklist Ppt Powerpoint Presentation Complete Deck With Slides acts as backup support for your ideas, vision, thoughts, etc. Use it to present a thorough understanding of the topic. This PPT slideshow can be utilized for both in-house and outside presentations depending upon your needs and business demands. Entailing thirteen slides with a consistent design and theme, this template will make a solid use case. As it is intuitively designed, it suits every business vertical and industry. All you have to do is make a few tweaks in the content or any other component to design unique presentations. The biggest advantage of this complete deck is that it can be personalized multiple times once downloaded. The color, design, shapes, and other elements are free to modify to add personal touches. You can also insert your logo design in this PPT layout. Therefore a well-thought and crafted presentation can be delivered with ease and precision by downloading this Security Checklist Ppt Powerpoint Presentation Complete Deck With Slides PPT slideshow.

Distributed Ledger Security Ppt Powerpoint Presentation Complete Deck With Slides
This Distributed Ledger Security Ppt Powerpoint Presentation Complete Deck With Slides acts as backup support for your ideas, vision, thoughts, etc. Use it to present a thorough understanding of the topic. This PPT slideshow can be utilized for both in-house and outside presentations depending upon your needs and business demands. Entailing twenty slides with a consistent design and theme, this template will make a solid use case. As it is intuitively designed, it suits every business vertical and industry. All you have to do is make a few tweaks in the content or any other component to design unique presentations. The biggest advantage of this complete deck is that it can be personalized multiple times once downloaded. The color, design, shapes, and other elements are free to modify to add personal touches. You can also insert your logo design in this PPT layout. Therefore a well-thought and crafted presentation can be delivered with ease and precision by downloading this Distributed Ledger Security Ppt Powerpoint Presentation Complete Deck With Slides PPT slideshow.

Digital Security Metrics Ppt Powerpoint Presentation Complete Deck With Slides
This Digital Security Metrics Ppt Powerpoint Presentation Complete Deck With Slides acts as backup support for your ideas, vision, thoughts, etc. Use it to present a thorough understanding of the topic. This PPT slideshow can be utilized for both in-house and outside presentations depending upon your needs and business demands. Entailing seventeen slides with a consistent design and theme, this template will make a solid use case. As it is intuitively designed, it suits every business vertical and industry. All you have to do is make a few tweaks in the content or any other component to design unique presentations. The biggest advantage of this complete deck is that it can be personalized multiple times once downloaded. The color, design, shapes, and other elements are free to modify to add personal touches. You can also insert your logo design in this PPT layout. Therefore a well-thought and crafted presentation can be delivered with ease and precision by downloading this Digital Security Metrics Ppt Powerpoint Presentation Complete Deck With Slides PPT slideshow.

Virtual Security Hazards Ppt PowerPoint Presentation Complete Deck With Slides
This Virtual Security Hazards Ppt PowerPoint Presentation Complete Deck With Slides acts as backup support for your ideas,vision,thoughts,etc. Use it to present a thorough understanding of the topic. This PPT slideshow can be utilized for both in house and outside presentations depending upon your needs and business demands. Entailing seventeen slides with a consistent design and theme,this template will make a solid use case. As it is intuitively designed,it suits every business vertical and industry. All you have to do is make a few tweaks in the content or any other component to design unique presentations. The biggest advantage of this complete deck is that it can be personalized multiple times once downloaded. The color,design,shapes,and other elements are free to modify to add personal touches. You can also insert your logo design in this PPT layout. Therefore a well thought and crafted presentation can be delivered with ease and precision by downloading this Virtual Security Hazards Ppt PowerPoint Presentation Complete Deck With Slides PPT slideshow.
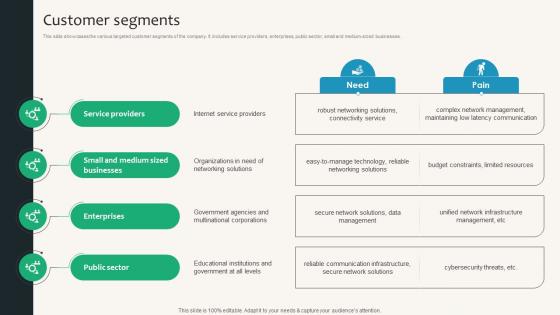
Customer Segments Security Service Provider Business Model BMC SS V
This slide showcases the various targeted customer segments of the company. It includes service providers, enterprises, public sector, small and medium-sized businesses. There are so many reasons you need a Customer Segments Security Service Provider Business Model BMC SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Devsecops Development Security And Operations Role Of Devsecops Ppt Template
This slide discusses the working process of development, security and operations in DevSecOps. The purpose of this slide is to highlight the process followed by DevSecOps for providing, monitoring and managing security at each level of the software system. Find highly impressive Devsecops Development Security And Operations Role Of Devsecops Ppt Template on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Devsecops Development Security And Operations Role Of Devsecops Ppt Template for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now
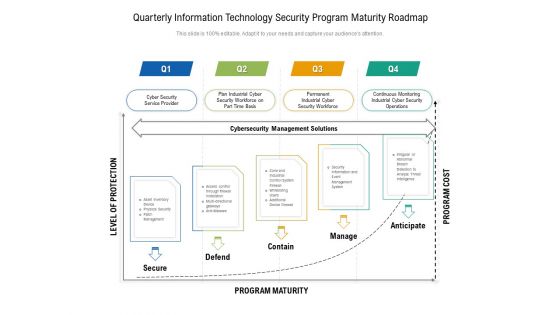
Quarterly Information Technology Security Program Maturity Roadmap Ideas
Introducing our quarterly information technology security program maturity roadmap ideas. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

Information And Technology Security Operations Quotes Diagrams PDF
Deliver an awe inspiring pitch with this creative information and technology security operations quotes diagrams pdf bundle. Topics like quotes can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Quarterly Information Technology Security Analytics Improvement Roadmap Template
Presenting our innovatively structured quarterly information technology security analytics improvement roadmap template Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
Local Security Policy In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Local Security Policy In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Local Security Policy that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design.
Cyber Security Milestones In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Cyber Security Milestones In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Cyber Security Milestones that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design.
Firewall Security Audit Checklist In Powerpoint And Google Slides Cpb
Presenting our innovatively-designed set of slides titled Firewall Security Audit Checklist In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Firewall Security Audit Checklist that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design.
System Security Diagram In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled System Security Diagram In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits System Security Diagram that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design.
Internet Security Threat Icon On Computer Elements PDF
Presenting internet security threat icon on computer elements pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including internet security threat icon on computer. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Table Of Contents For Information Security Law Summary PDF
Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Table Of Contents For Information Security Law Summary PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Table Of Contents For Information Security Law Summary PDF today and make your presentation stand out from the rest.

Six Practices For IT Security Management Program Microsoft PDF
This slide shows the best practices for security management program which includes essential tasks such as risk analysis and identification, manage risk, threat and issues, security consolidation procedure, etc. With assigned owner and frequency.Presenting Six Practices For IT Security Management Program Microsoft PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Analysis Prioritization, Consolidation Procedure, Strategic Initiatives This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
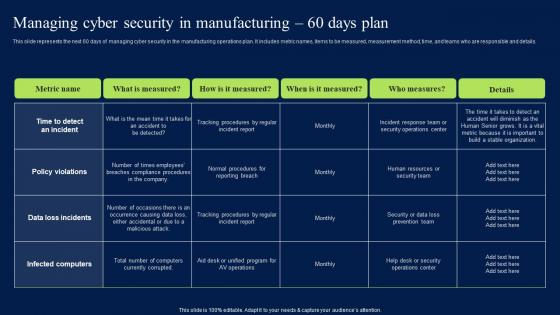
Managing Cyber Security In Manufacturing 60 Days Plan Mockup PDF
This slide represents the next 60 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Retrieve professionally designed Managing Cyber Security In Manufacturing 60 Days Plan Mockup PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Successful Security Token Offering Project Exploring Investment Opportunities Professional Pdf
The following slide showcases some insights about spice VC security token offerings STO project to boost crowdfunding. It includes elements such as overview, launched date, amount raised, features and percentage of return on investments ROI generated, etc. Take your projects to the next level with our ultimate collection of Successful Security Token Offering Project Exploring Investment Opportunities Professional Pdf. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest

Security Incident Report Template In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Security Incident Report Template In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Security Incident Report Template that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design.

 Home
Home