Data Security And Protection
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps In Detail Setting Brochure PDF
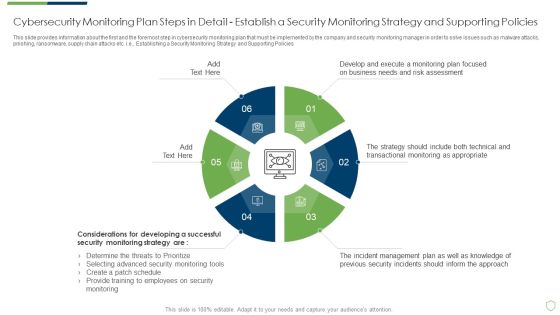
This slide provides information about the seventh step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Providing Resilient and Synchronized Timing. Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps in detail setting brochure pdf. Use them to share invaluable insights on cybersecurity monitoring plan steps in detail providing resilient and synchronized timing and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Executing Security Management Program To Mitigate Threats And Safeguard Confidential Organizational Data Poste It Notes Clipart PDF
This is a Executing security management program to mitigate threats and safeguard confidential organizational data poste it notes clipart pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like poste it notes. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Detail Impact Security Awareness Training Can Reduce The Risk Of A Data Breach Ppt Outline Gridlines PDF
This slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen or lost devices or records and inadvertent disclosure. Deliver and pitch your topic in the best possible manner with this detail impact security awareness training can reduce the risk of a data breach ppt outline gridlines pdf. Use them to share invaluable insights on phishing breakdown, network intrusion breakdown and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Executing Security Management Program To Mitigate Threats And Safeguard Confidential Organizational Data 30 60 90 Days Plan Brochure PDF
Presenting Executing security management program to mitigate threats and safeguard confidential organizational data 30 60 90 days plan brochure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like 30 60 90 days plan. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Terrorism Assault Techniques To Protect SCADA Systems From Cyber Attacks Demonstration PDF
This slide depicts the techniques to protect SCADA from cyber-attacks which include security training of employees, strict firewalls.Presenting cyber terrorism assault techniques to protect scada systems from cyber attacks demonstration pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like access controls, strict firewalls, network security procedures In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
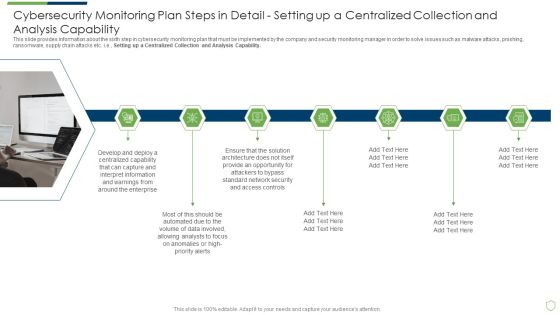
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps In Detail Structure PDF
This slide provides information about the sixth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Setting up a Centralized Collection and Analysis Capability. This is a modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps in detail structure pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail setting up a centralized collection and analysis capability. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Steps To Ensure Robotic Process Automated Security Ideas PDF
This slide defines steps to ensure the security of robotic process automation, and it covers guarantee accountability for bot activities, protection from abuse, frauds, logs and bot development. This is a Steps To Ensure Robotic Process Automated Security Ideas PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Guarantee Accountability, Protect Log Respectability, Empower Secure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Ppt PowerPoint Presentation Complete Deck With Slides
Pitch yourself both in house and outside by utilizing this complete deck. This modern security observation plan to eradicate cybersecurity risk and data breach ppt powerpoint presentation complete deck with slides focuses on key fundamentals of the topic, displayed using different slides. With a total of fourty six slides, this template is the best tool you can use to persuade your audience. It will not only help you create great presentations but also induce strategic thinking because of its well researched content and graphics. You can easily personalize any of the elements to suit your unique business setting. Additionally, it can be saved in PNG, JPG, and PDF formats to save your time and resources.

Executing Security Management Program To Mitigate Threats And Safeguard Confidential Organizational Data Ppt PowerPoint Presentation Complete Deck
This complete deck acts as a great communication tool. It helps you in conveying your business message with personalized sets of graphics, icons etc. Comprising a set of fourtytwo slides, this complete deck can help you persuade your audience. It also induces strategic thinking as it has been thoroughly researched and put together by our experts. Not only is it easily downloadable but also editable. The color, graphics, theme any component can be altered to fit your individual needs. So grab it now.

Organization Reinvention Need Of Cyber Security In Organization Graphics PDF
This slide covers the need of introducing cybersecurity in the business and how can organization integrate cybersecurity with digital transformation. Presenting Organization Reinvention Need Of Cyber Security In Organization Graphics PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Protection Against Malware, Protection Phishing Scams, Security Confidential Data. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Person Protecting Data By Using Network Access Control Ppt PowerPoint Presentation Gallery Infographics PDF
Persuade your audience using this person protecting data by using network access control ppt powerpoint presentation gallery infographics pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including person protecting data by using network access control. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
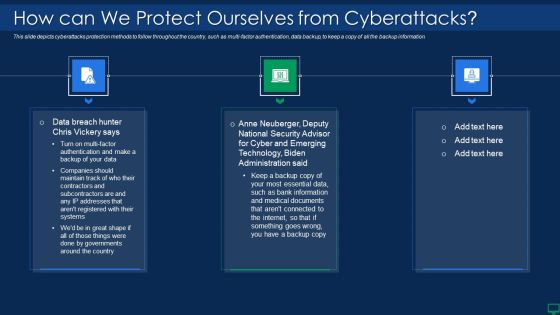
Russian Cyber Attacks On Ukraine IT How Can We Protect Ourselves Rules PDF
This slide depicts cyberattacks protection methods to follow throughout the country, such as multi factor authentication, data backup, to keep a copy of all the backup information. This is a russian cyber attacks on ukraine it how can we protect ourselves rules pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like internet, documents, information, data. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Performance Indicators To Measure Information Security Controls Brochure PDF
Following slide illustrates performance indicators for measuring information security controls. It includes controls details, performance indicator formula, target and periodicity.Deliver an awe inspiring pitch with this creative Performance Indicators To Measure Information Security Controls Brochure PDF bundle. Topics like Information Security, Security Training, Malware Protection can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Five Elements Of Cloud Services Security Brochure PDF
This slide includes elements of cloud computing security to assure network protection and efficient management. It contains five elements architecture, security, due diligence, authentication, monitor and visibility.Presenting Five Elements Of Cloud Services Security Brochure PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Security Coverage, Intrusion Detection, Computing Regulations. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Business Cyber Security Risk Assessment Process Inspiration PDF
The slide shows cyber threat detection and protection measures in order to eliminate the potential risks to the business. The steps include identifying, detecting, responding, protecting, and recovering. Persuade your audience using this Business Cyber Security Risk Assessment Process Inspiration PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Identify, Detect, Respond, Protect, Recover. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
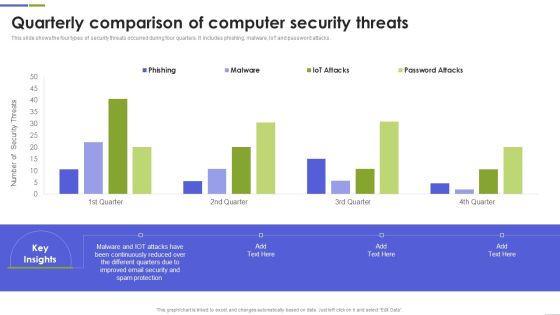
Quarterly Comparison Of Computer Security Threats Mockup PDF
This slide shows the four types of security threats occurred during four quarters. It includes phishing, malware, IoT and password attacks. Pitch your topic with ease and precision using this Quarterly Comparison Of Computer Security Threats Mockup PDF This layout presents information on Continuously Reduced, Different Quarters, Spam Protection It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Supply Chain Management Strategy To Protect Iot Integrated Devices Infographics PDF
This slide showcases strategy to protect internet of things IoT integrated devices. It includes information about virtual containers, user access, identification, communication, data center, virtual conditions, etc. Deliver an awe inspiring pitch with this creative Supply Chain Management Strategy To Protect Iot Integrated Devices Infographics PDF bundle. Topics like Place Devices, Virtual Containers, Segregate Networks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Steps To Deploy People Centric Work Culture Security Background PDF
The following slide showcases steps to enforce human centric security system to empower employees in handling useful information. It includes elements such as establishing environment for people centric security PCS, promoting culture of cyber security, etc. Presenting Steps To Deploy People Centric Work Culture Security Background PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Converting Cybersecurity, Punishment System, Protection Practices. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Technological Smart Homes Security Steps To Eliminate Threat Themes PDF
This side showcase the steps to reduce the threats of smart home by creating solid defense for burglary and provides cybersecurity. It includes key elements such as door security, window reinforcement, save energy, garage protection and cybersecurity. Presenting Technological Smart Homes Security Steps To Eliminate Threat Themes PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Door Security, Window Reinforcement, Efficient Utilization Energy. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Manpower Corporate Security Business Profile Awards And Accolades Download PDF
This slide highlights the security company additional security services which includes safety escort service, executive protection and special event security. Presenting Manpower Corporate Security Business Profile Awards And Accolades Download PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Asis International, Gptw Institute, Sia Awards. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security Risk Management Implementation Process Brochure PDF
The following slide explains implementation method for cybersecurity risk management for the organization to ensure protection of key business data. It includes steps such as categorize, security controls, implementation, assess, etc. Persuade your audience using this IT Security Risk Management Implementation Process Brochure PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Monitor, Authorize, Assess, Implementation, Security Controls, Categorize System. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Crime And War Security Strategic Vision Designs PDF
This slide represents the cyber crime and security strategies formulated by the United Kingdom. It includes details related to strategic vision and four objectives of the UK cyber terrorism security team.Persuade your audience using this Cyber Crime And War Security Strategic Vision Designs PDF This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Security Strategy, Protection Promotion, Secured Cyberspace Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Complete IT Security IT Implementation Checklist Ppt Diagrams PDF
This slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. Deliver an awe inspiring pitch with this creative complete it security it implementation checklist ppt diagrams pdf bundle. Topics like training, antivirus software, secure communications, access control measures, device security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Network Code Security PowerPoint Templates And PowerPoint Backgrounds 0511
Microsoft PowerPoint Template and Background with cyber security network data monitor as abstract

Cloud Network Security Architecture And Boundaries Graphics PDF
The slide presents an architecture describing technologies and hardware to protect data and systems within cloud platforms . The slide includes security boundaries and key takeaways. Showcasing this set of slides titled Cloud Network Security Architecture And Boundaries Graphics PDF. The topics addressed in these templates are Presentation Mobility, Presentation Platform, Applications. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

IT Security Analysis To Prevent Insider Threats Infographics PDF
This slide covers the data on the security by using the technologies to protect the data from the insider threats. It includes the analysis with risk model, CWE, OWASP, SQL injection, misconfiguration, etc. Presenting IT Security Analysis To Prevent Insider Threats Infographics PDF to dispense important information. This template comprises nine stages. It also presents valuable insights into the topics including Security Project, Application, Risk Model. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Three Stages To Protect The Environment Ppt PowerPoint Presentation Gallery Introduction PDF
Presenting three stages to protect the environment ppt powerpoint presentation gallery introduction pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including three stages to protect the environment. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Save Earth And Protect Global Environment Icon Ppt PowerPoint Presentation File Example File PDF
Presenting save earth and protect global environment icon ppt powerpoint presentation file example file pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including save earth and protect global environment icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
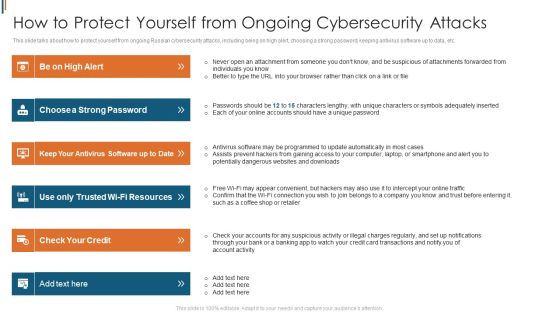
Ukraine Cyberwarfare How To Protect Yourself From Ongoing Cybersecurity Attacks Themes Pdf
This slide talks about how to protect yourself from ongoing Russian cybersecurity attacks, including being on high alert, choosing a strong password, keeping antivirus software up to data, etc. This is a ukraine cyberwarfare how to protect yourself from ongoing cybersecurity attacks themes pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like choose a strong password, keep your antivirus software up to date, use only trusted wi fi resources. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
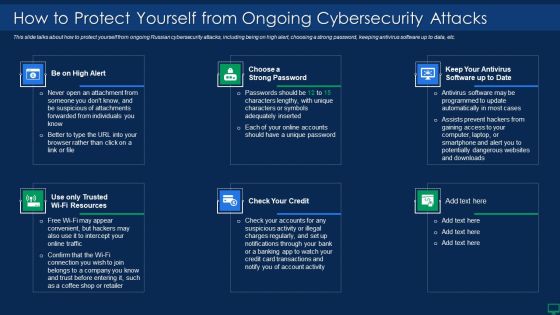
Russian Cyber Attacks On Ukraine IT How To Protect Yourself Summary PDF
This slide talks about how to protect yourself from ongoing Russian cybersecurity attacks, including being on high alert, choosing a strong password, keeping antivirus software up to data, etc. Presenting russian cyber attacks on ukraine it how to protect yourself summary pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like resources, account, potentially. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Electronic Learning Playbook Best Practices To Protect Technology Systems Cont Introduction PDF
This slide provides information regarding best practices to protect technology systems in terms of compliance with legal regulations on student privacy, internet and content filtering. Deliver an awe inspiring pitch with this creative electronic learning playbook best practices to protect technology systems cont introduction pdf bundle. Topics like deploy internet content, approve applications websites, suitable school devices can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Key Safety Audits To Protect All Hardware Devices Ppt PowerPoint Presentation File Graphics Pictures PDF
Persuade your audience using this key safety audits to protect all hardware devices ppt powerpoint presentation file graphics pictures pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including key safety audits to protect all hardware devices. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
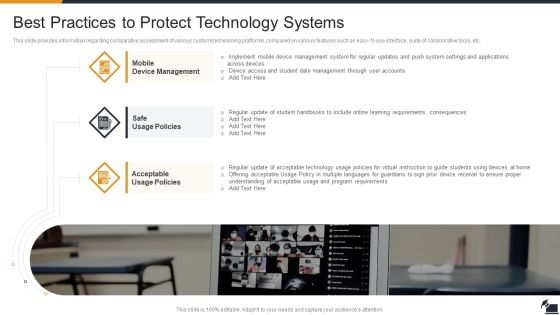
Electronic Learning Playbook Best Practices To Protect Technology Systems Formats PDF
This slide provides information regarding comparative assessment of various customized learning platforms, compared on various features such as easy to use interface, suite of collaborative tools, etc. Deliver and pitch your topic in the best possible manner with this electronic learning playbook best practices to protect technology systems formats pdf Use them to share invaluable insights on best practices to protect technology systems and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cloud Management And Monitoring Configure Govern And Protect Ppt Powerpoint Presentation Layouts Graphic Images
This is a cloud management and monitoring configure govern and protect ppt powerpoint presentation layouts graphic images. This is a five stage process. The stages in this process are cloud computing, cloud management, cloud governance.

Distance Coaching Playbook Best Practices To Protect Technology Systems Summary PDF
This slide provides information regarding best practices to protect technology systems in terms of mobile device management, safe usage policies and acceptable usage policies. Deliver an awe inspiring pitch with this creative Distance Coaching Playbook Best Practices To Protect Technology Systems Summary PDF bundle. Topics like Mobile Device Management, Safe Usage Policies, Acceptable Usage Policies can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Web Development What Is The Cyber Security Designs PDF
This slide represents how data security keeps in mind while developing websites, and security measures are already added to designed websites to protect them from malicious attacks.Presenting Web Development What Is The Cyber Security Designs PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Categories Of Cyber, Operational Security, Includes Network Security In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Protect Business From Financial Crisis PowerPoint Templates Ppt Backgrounds For Slides 0513
Plan your storyboard with our Protect Business From Financial Crisis PowerPoint Templates Umbrellas Backgrounds For Slide. Give an outline to the solutions you have. Give power to your elbow with our Protect Business From Financial Crisis PowerPoint Templates Ppt Backgrounds For Slides 0513 PowerPoint Templates. Get that extra information you need. Drum up support with our Arrows PowerPoint Templates. They will come in droves to stand by you.

Unconventional Monetary Policy How Did Those Who Bought Cdos Protect Themselves Clipart PDF
Presenting unconventional monetary policy how did those who bought cdos protect themselves clipart pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like traditional, protected, instruments, crisis. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

US Economic Crisis How Did Those Who Bought Cdos Protect Themselves Ppt Model Background Images PDF
Presenting us economic crisis how did those who bought cdos protect themselves ppt model background images pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like traditional, protected, instruments, crisis. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Global Financial Catastrophe 2008 How Did Those Who Bought CDO Protect Themselves Ppt Icon Examples PDF
Presenting global financial catastrophe 2008 how did those who bought cdo protect themselves ppt icon examples pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like traditional, protected, instruments, crisis. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Multinational Financial Crisis How Did Those Who Bought CDO Protect Themselves Ppt Summary Graphics Pictures PDF
Presenting multinational financial crisis how did those who bought cdo protect themselves ppt summary graphics pictures pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like traditional, protected, instruments, crisis. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Key Initiatives To Protect The Fitness Industry From Outbreak Brochure PDF
This slide covers information about the major steps taken by the authorities and gym owners to protect the fitness industry from outbreak.Deliver and pitch your topic in the best possible manner with this key initiatives to protect the fitness industry from outbreak brochure pdf. Use them to share invaluable insights on memberships starting, outreach and awareness raising, promoting positive social attitudes and behavior and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Curved Roadmap Graphics To Protect Personal Assets From Business Ppt PowerPoint Presentation File Gallery PDF
Presenting curved roadmap graphics to protect personal assets from business ppt powerpoint presentation file gallery pdf to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including curved roadmap graphics to protect personal assets from business. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
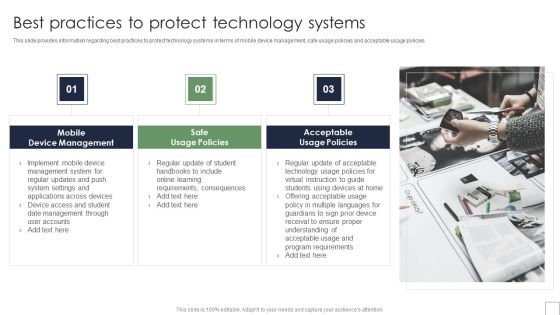
Remote Learning Playbook Best Practices To Protect Technology Systems Structure PDF
This slide provides information regarding best practices to protect technology systems in terms of mobile device management, safe usage policies and acceptable usage policies. This is a Remote Learning Playbook Best Practices To Protect Technology Systems Structure PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Mobile Device Management, Safe Usage Policies, Acceptable Usage Policies. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
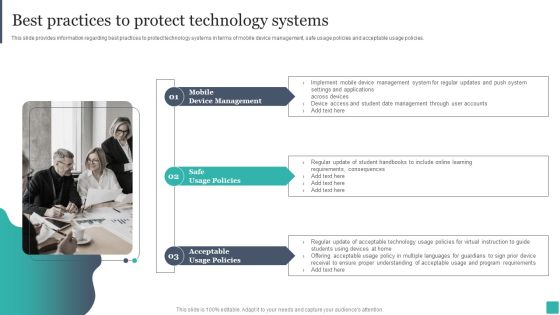
Technology Mediated Learning Playbook Best Practices To Protect Technology Systems Microsoft PDF
This slide provides information regarding best practices to protect technology systems in terms of mobile device management, safe usage policies and acceptable usage policies. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Technology Mediated Learning Playbook Best Practices To Protect Technology Systems Microsoft PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

WAF Introduction How WAF Will Protect Client Company From Cyberattacks Microsoft PDF
This slide depicts what the will WAF mechanism will do to protect information from cyberattacks. It includes session block, IP address block, request block, user block, generating admin alerts, and creating history logs. This WAF Introduction How WAF Will Protect Client Company From Cyberattacks Microsoft PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The WAF Introduction How WAF Will Protect Client Company From Cyberattacks Microsoft PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
E Learning Playbook Best Practices To Protect Technology Systems Icons PDF
This slide provides information regarding best practices to protect technology systems in terms of mobile device management, safe usage policies and acceptable usage policies. Presenting E Learning Playbook Best Practices To Protect Technology Systems Icons PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Acceptable Usage Policies, Safe Usage Policies, Mobile Device Management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

How WAF Will Protect Client Company From Cyberattacks WAF Platform Infographics PDF
This slide depicts what the will WAF mechanism will do to protect information from cyberattacks. It includes session block, IP address block, request block, user block, generating admin alerts, and creating history logs. This is a How WAF Will Protect Client Company From Cyberattacks WAF Platform Infographics PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like System, Risk, Information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Addressing The Practices To Protect Business Against Fraud Fraud Threat Administration Guide Sample PDF
Purpose of this slide is to portray the existing ways of protecting business from fraud events such as WIFI hacking, business email compromise scams, and ransomware.This is a Addressing The Practices To Protect Business Against Fraud Fraud Threat Administration Guide Sample PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Compromise Scams, Ransomware, Confidential Information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
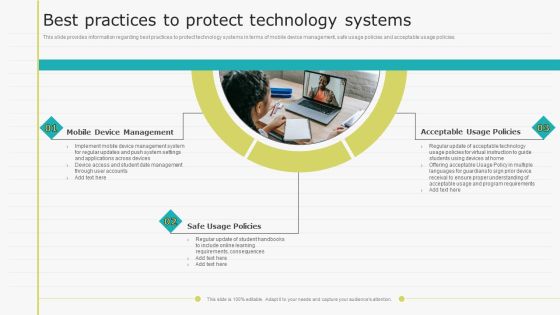
Virtual Learning Playbook Best Practices To Protect Technology Systems Slides PDF
This slide provides information regarding best practices to protect technology systems in terms of mobile device management, safe usage policies and acceptable usage policies. Presenting Virtual Learning Playbook Best Practices To Protect Technology Systems Slides PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Mobile Device Management, Safe Usage Policies, Acceptable Usage Policies. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Digital Coaching And Learning Playbook Best Practices To Protect Technology Systems Designs PDF
This slide provides information regarding best practices to protect technology systems in terms of mobile device management, safe usage policies and acceptable usage policies. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Digital Coaching And Learning Playbook Best Practices To Protect Technology Systems Designs PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Case Competition Petroleum Sector Issues Guidelines Under Environmental Policy To Protect Environment Diagrams PDF
The slide provides the major guidelines and rules under environmental policy to protect environment. Major rules and guidelines include green completion rule, underground injection control program, the bureau of land management BLM rule etc. This is a case competition petroleum sector issues guidelines under environmental policy to protect environment diagrams pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like control program, management, national environmental policy act, impact statements, environmental assessments. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Terrorism Assault How To Protect Company From Trojan Attacks Demonstration PDF
This slide explains how to protect the company from trojan attacks which include procedures such as installing advanced antivirus software. This is a cyber terrorism assault how to protect company from trojan attacks demonstration pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like device conventional, next generation antivirus, prevent trojan infection You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Fraud Avoidance Playbook Addressing The Practices To Protect Business Against Fraud Infographics PDF
Purpose of this slide is to portray the existing ways of protecting business from fraud events such as WIFI hacking, business email compromise scams, and ransomware. This is a Fraud Avoidance Playbook Addressing The Practices To Protect Business Against Fraud Infographics PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like The Wi Fi Crack, Business Email Compromise Scams, Ransomware. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Web App Firewall Services IT How WAF Will Protect Client Company From Cyberattacks Elements PDF
This slide depicts what the will WAF mechanism will do to protect information from cyberattacks. It includes session block, IP address block, request block, user block, generating admin alerts, and creating history logs. Presenting web app firewall services it how waf will protect client company from cyberattacks elements pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like information, systems, networks, method. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Anti Scam Playbook Addressing The Practices To Protect Business Against Fraud Formats PDF
Purpose of this slide is to portray the existing ways of protecting business from fraud events such as WIFI hacking, business email compromise scams, and ransomware. Presenting Anti Scam Playbook Addressing The Practices To Protect Business Against Fraud Formats PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Information, Financial, System. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
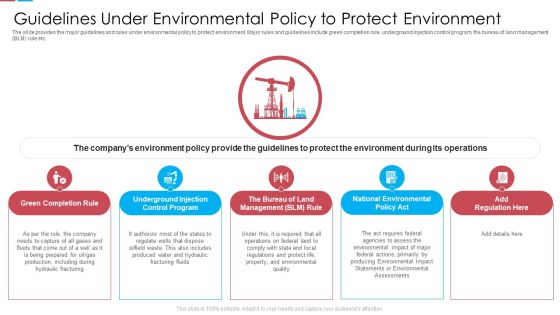
Guidelines Under Environmental Policy To Protect Environment Ppt Slides Template PDF
The slide provides the major guidelines and rules under environmental policy to protect environment. Major rules and guidelines include green completion rule, underground injection control program, the bureau of land management BLM rule etc. Presenting guidelines under environmental policy to protect environment ppt slides template pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like green completion rule, underground injection control program, bureau of land management blm rule. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Various Strategies To Prevent Business Addressing The Practices To Protect Business Against Fraud Graphics PDF
Purpose of this slide is to portray the existing ways of protecting business from fraud events such as WIFI hacking, business email compromise scams, and ransomware. Presenting Various Strategies To Prevent Business Addressing The Practices To Protect Business Against Fraud Graphics PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Business Email, Compromise Scams, Ransomware. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Protect The Business From Market Risks PowerPoint Templates Ppt Backgrounds For Slides 0513
Document the process on our Protect The Business From Market Risks PowerPoint Templates PPT Backgrounds For Slides. Make a record of every detail. Satiate desires with our umbrellas PowerPoint Templates. Give them all they want and more. Be the doer with our business PowerPoint Templates. Put your thoughts into practice.

Protect Your Home And Family PowerPoint Templates Ppt Backgrounds For Slides 0713
Give power to your elbow with our Protect Your Home And Family PowerPoint Templates PPT Backgrounds For Slides. Get that extra information you need. Put them on the same page with our children PowerPoint Templates. Your team will sing from the same sheet. Push the envelop with our people PowerPoint Templates. Let your thoughts rise above the norm.

 Home
Home