Data Security And Protection
Security Operations Icon To Prevent Security Breaches Ideas PDF
Persuade your audience using this Security Operations Icon To Prevent Security Breaches Ideas PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Security Operations Icon, Prevent Security Breaches. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cloud Security Assessment Roadmap Of Cloud Security Implementation Information PDF
This slide defines the roadmap of cloud security implementation in an organization and what tasks would be performed in each months interval starting from January.Presenting Cloud Security Assessment Roadmap Of Cloud Security Implementation Information PDF to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like Configuration Management, Services Management, Security Measures. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Desktop Security Management Main Steps Of Operational Security Inspiration PDF
This slide depicts the main steps of operational security, such as describing sensitive information, identifying potential risks, and so on, by showing how these steps are operating. Presenting desktop security management main steps of operational security inspiration pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like financial, determine, analyze, systems, technologies. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
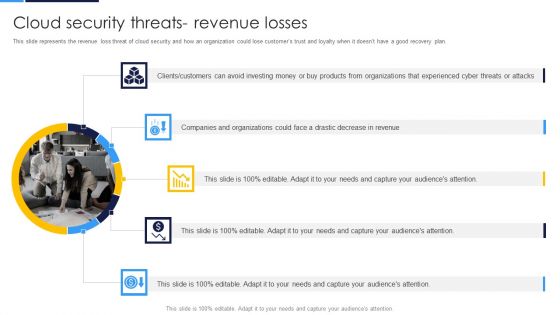
Cloud Security Assessment Cloud Security Threats Revenue Losses Introduction PDF
This slide represents the revenue loss threat of cloud security and how an organization could lose customers trust and loyalty when it doesnt have a good recovery plan.Presenting Cloud Security Assessment Cloud Security Threats Revenue Losses Introduction PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Clients Or Customers, Companies And Organizations, Organizations That Experienced. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
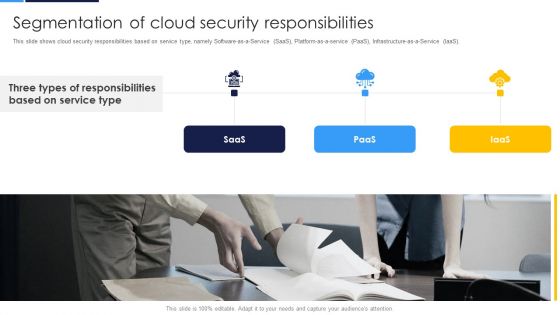
Cloud Security Assessment Segmentation Of Cloud Security Responsibilities Professional PDF
This slide shows cloud security responsibilities based on service type, namely Software as a Service SaaS, Platform-as-a-service PaaS, Infrastructure-as-a-Service IaaS.Deliver an awe inspiring pitch with this creative Cloud Security Assessment Segmentation Of Cloud Security Responsibilities Professional PDF bundle. Topics like Responsibilities, Based On Service, Three Types can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Security Assessment Hybrid Cloud Security Solutions Brochure PDF
This slide describes the hybrid cloud security solutions, which include categorization of services and redundancy.Presenting Cloud Security Assessment Hybrid Cloud Security Solutions Brochure PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Enable Organizations, Information Applications, Delicate Information In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
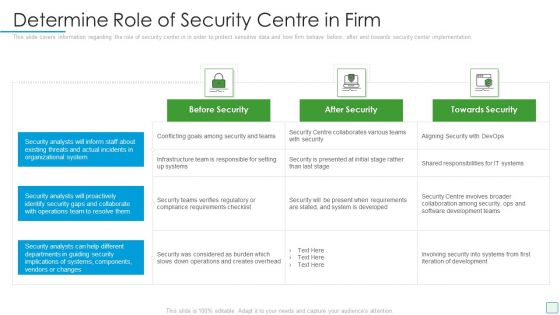
Developing Firm Security Strategy Plan Determine Role Of Security Centre In Firm Graphics PDF
This slide covers information regarding the role of security center in in order to protect sensitive data and how firm behave before, after and towards security center implementation. Deliver and pitch your topic in the best possible manner with this developing firm security strategy plan determine role of security centre in firm graphics pdf. Use them to share invaluable insights on before security, after security, towards security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
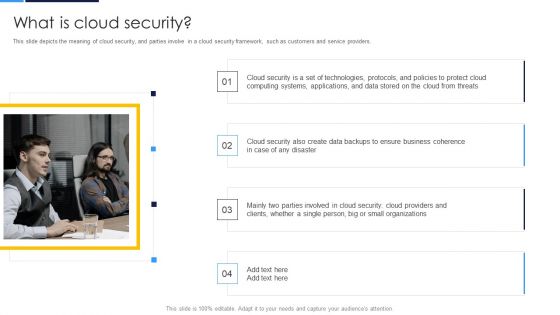
Cloud Security Assessment What Is Cloud Security Elements PDF
This slide depicts the meaning of cloud security, and parties involve in a cloud security framework, such as customers and service providers.Presenting Cloud Security Assessment What Is Cloud Security Elements PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Computing Systems, Business Coherence, Parties Involved. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Assessment Pillars Of Cloud Security Network Security Mockup PDF
This slide defines the network security pillar of cloud security and what precautions are taken to protect networks from attacks.Presenting Cloud Security Assessment Pillars Of Cloud Security Network Security Mockup PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Premises Conditions, Difficult For Attackers, Them Individually In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Assessment Enterprise Cloud Security Solutions Introduction PDF
This slide describes the enterprise cloud security solutions, including multi-factor authentication, managing accounts and service proactively, being careful about shadow IT, and analyzing the cost-benefits of hybrid cloud.Deliver and pitch your topic in the best possible manner with this Cloud Security Assessment Enterprise Cloud Security Solutions Introduction PDF. Use them to share invaluable insights on Manage Accounts, Services Proactively, Processes Fingerprints and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Uniformed Security Roadmap For Security Guard Services Proposal Diagrams PDF
Presenting uniformed security roadmap for security guard services proposal diagrams pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like roadmap. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Uniformed Security Timeline For Security Guard Services Proposal Structure PDF
Presenting uniformed security timeline for security guard services proposal structure pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like timeline, 2016 to 2020. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Security Incidents Tracking Dashboard Workplace Security Management Program Summary PDF
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Find highly impressive Security Incidents Tracking Dashboard Workplace Security Management Program Summary PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Security Incidents Tracking Dashboard Workplace Security Management Program Summary PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Organizing Security Awareness Measuring Security Awareness Campaign Results Download PDF
The purpose of this slide is to showcase various key performance indicator KPIs which can assist the company to effectively track cyber security awareness campaign results. The KPIs are phishing rate, self-reported incidents, security breaches, cost of security breach and campaign participation rate. Explore a selection of the finest Organizing Security Awareness Measuring Security Awareness Campaign Results Download PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Organizing Security Awareness Measuring Security Awareness Campaign Results Download PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
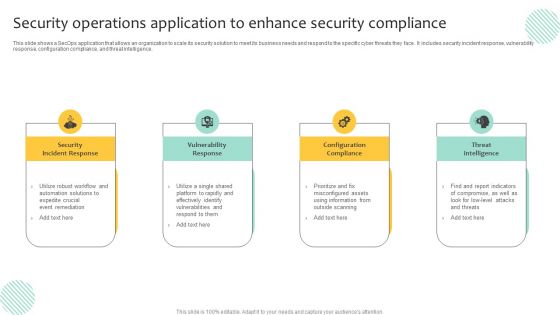
Security Operations Application To Enhance Security Compliance Rules PDF
This slide shows a SecOps application that allows an organization to scale its security solution to meet its business needs and respond to the specific cyber threats they face. It includes security incident response, vulnerability response, configuration compliance, and threat intelligence. Persuade your audience using this Security Operations Application To Enhance Security Compliance Rules PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Configuration Compliance, Threat Intelligence, Vulnerability Response. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cloud Security Assessment Key Challenges In Cloud Security Ideas PDF
This slide describes the critical challenges in the cloud security system, such as compliance violations, access control, Daniel of service, and unsecured APIs.Presenting Cloud Security Assessment Key Challenges In Cloud Security Ideas PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Compliance Violations, Access Control, Daniel Of Service In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Assessment Cloud Security Risks Or Threats Topics PDF
This slide represents the list of threats or risks that can impact the security of a cloud these risks include loss of intellectual property, compliance violations, malware attacks, and so on.Presenting Cloud Security Assessment Cloud Security Risks Or Threats Topics PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Revenue Losses, Shared Vulnerabilities, Compliance Violations In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Organizing Security Awareness Running Cyber Security Awareness Campaign Graphics PDF
The purpose of this slide is to provide an overview of cyber security awareness campaign which can be used to educate staff members. The campaign covers information about the objectives, security awareness topics to cover and various activities which will be covered. Boost your pitch with our creative Organizing Security Awareness Running Cyber Security Awareness Campaign Graphics PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you dont have to invest time in any additional work. Just grab the template now and use them.

Organizing Security Awareness Security Awareness Training Program Challenges Formats PDF
The purpose of this slide is to exhibit biggest cyber security awareness challenges which is faced by the organization. Outdated content, burden on administrators, low employee participation rate and employees losing interest are some of the key challenges which are highlighted in the slide. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Organizing Security Awareness Security Awareness Training Program Challenges Formats PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Desktop Security Management Latest Threats In Computer Security Inspiration PDF
This slide depicts the categories of recent threats that recently emerged in the United States, United Kingdom, and Australia in previous years. Presenting desktop security management latest threats in computer security inspiration pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like financial, information, systems. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Organizing Security Awareness Comparative Assessment Of Security Awareness Clipart PDF
The purpose of this slide is to showcase comparison of various advance cyber security training courses. The comparison is drawn on the basis of course description, level, duration, no. of companies enrolled for this course etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Organizing Security Awareness Comparative Assessment Of Security Awareness Clipart PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
Risk Security PowerPoint Ppt Templates Security Ppt Slides
Risk Security PowerPoint PPT templates Security PPT Slides-These high quality powerpoint pre-designed slides and powerpoint templates have been carefully created by our professional team to help you impress your audience. All slides have been created and are 100% editable in powerpoint. Each and every property of any graphic - color, size, orientation, shading, outline etc. can be modified to help you build an effective powerpoint presentation. Any text can be entered at any point in the powerpoint template or slide. Simply DOWNLOAD, TYPE and PRESENT!

Internet Security PowerPoint Template 0910
Blue Earth globe and padlock isolated over white background

Identity Security PowerPoint Template 1110
Blue Earth globe and padlock isolated over white background

Security Management Plan Steps In Detail Data Backup And Data Loss Recovery Plan Portrait PDF
Presenting security management plan steps in detail data backup and data loss recovery plan portrait pdf to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like outline business continuity, recovery infrastructure, inventory of the business. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
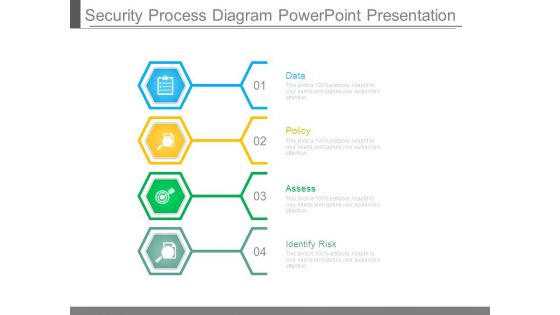
Security Process Diagram Powerpoint Presentation
This is a security process diagram powerpoint presentation. This is a four stage process. The stages in this process are data, policy, assess, identify risk.

Security Process Sample Powerpoint Presentation
This is a security process sample powerpoint presentation. This is a four stage process. The stages in this process are data, policy, assess, identify risk.

Major Types Of Data Security Breaches Data Breach Prevention Microsoft Pdf
This slide discusses the significant categories of information loss. The purpose of this slide is to describe several types of data security breaches. These include human error, device loss, cyberattacks, internal breaches, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Major Types Of Data Security Breaches Data Breach Prevention Microsoft Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Major Types Of Data Security Breaches Data Breach Prevention Microsoft Pdf.

Stock Photo Business Model Strategy Protect Your Savings Stock Images
Our Sales Concepts Go Back To School Bus Business Images And Graphics Powerpoint Templates Abhor Doodling. They Never Let The Interest Flag.

Internet Protocol Security PPT Example
This Internet Protocol Security PPT Example is a primer on how to capitalize on business opportunities through planning, innovation, and market intelligence. The content-ready format of the complete deck will make your job as a decision-maker a lot easier. Use this ready-made PowerPoint Template to help you outline an extensive and legible plan to capture markets and grow your company on the right path, at an exponential pace. What is even more amazing is that this presentation is completely editable and 100 percent customizable. This eighty nine slide complete deck helps you impress a roomful of people with your expertise in business and even presentation. Craft such a professional and appealing presentation for that amazing recall value. Download now.
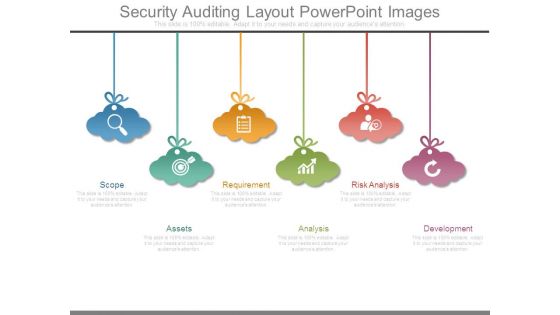
Security Auditing Layout Powerpoint Images
This is a security auditing layout powerpoint images. This is a six stage process. The stages in this process are scope, assets, requirement, analysis, risk analysis, development.
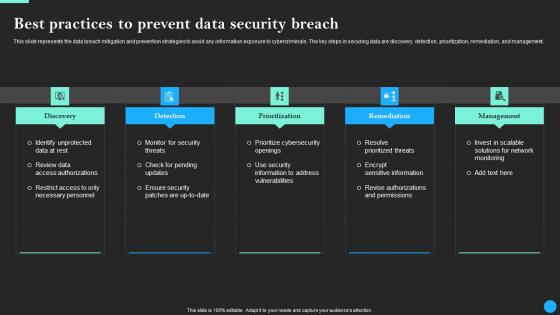
Best Practices To Prevent Data Security Breach Data Breach Prevention Information Pdf
This slide represents the data breach mitigation and prevention strategies to avoid any information exposure to cybercriminals. The key steps in securing data are discovery, detection, prioritization, remediation, and management. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Best Practices To Prevent Data Security Breach Data Breach Prevention Information Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Best Practices To Prevent Data Security Breach Data Breach Prevention Information Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today

Best Practices To Prevent Data Security Breach Data Fortification Strengthening Defenses
This slide represents the data breach mitigation and prevention strategies to avoid any information exposure to cybercriminals. The key steps in securing data are discovery, detection, prioritization, remediation, and management. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Best Practices To Prevent Data Security Breach Data Fortification Strengthening Defenses a try. Our experts have put a lot of knowledge and effort into creating this impeccable Best Practices To Prevent Data Security Breach Data Fortification Strengthening Defenses. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today

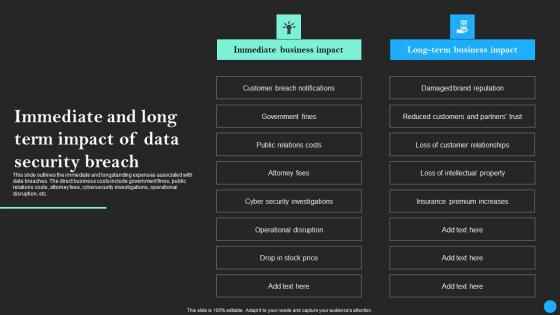
Immediate And Long Term Impact Of Data Security Breach Data Fortification Strengthening Defenses
This slide outlines the immediate and longstanding expenses associated with data breaches. The direct business costs include government fines, public relations costs, attorney fees, cybersecurity investigations, operational disruption, etc. Are you searching for a Immediate And Long Term Impact Of Data Security Breach Data Fortification Strengthening Defenses that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Immediate And Long Term Impact Of Data Security Breach Data Fortification Strengthening Defenses from Slidegeeks today.
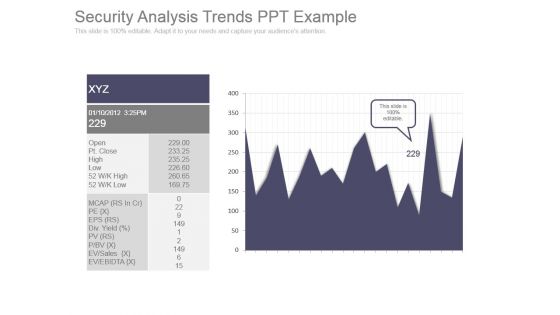
Security Analysis Trends Ppt Example
This is a security analysis trends ppt example. This is a one stage process. The stages in this process are open, pt close, high, low, mcap, pe, eps, div, pv, p bv, ev sales, ev ebidta.
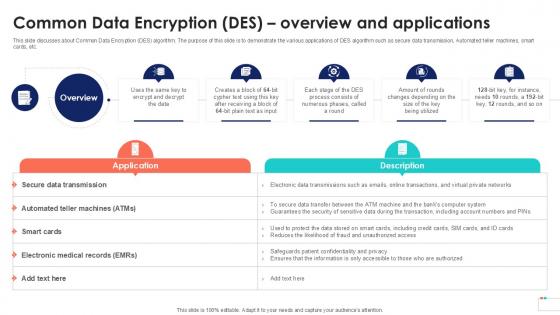
Common Data Encryption Des Overview Data Security In Cloud Computing Ppt Sample
This slide discusses about Common Data Encryption DES algorithm. The purpose of this slide is to demonstrate the various applications of DES algorithm such as secure data transmission, Automated teller machines, smart cards, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Common Data Encryption Des Overview Data Security In Cloud Computing Ppt Sample template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Common Data Encryption Des Overview Data Security In Cloud Computing Ppt Sample that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers

Common Data Encryption Des Cloud Data Security Using Cryptography Slides Pdf
This slide discusses about Common Data Encryption DES algorithm. The purpose of this slide is to demonstrate the various applications of DES algorithm such as secure data transmission, Automated teller machines, smart cards, etc. Welcome to our selection of the Common Data Encryption Des Cloud Data Security Using Cryptography Slides Pdf. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today

Data Center Infrastructure Management IT Data Center Security Standards We Used Professional PDF
This slide shows the data center security standards that we used to prevent data, and it includes layered security measures, access lists, video surveillance, source access points, and 24 7 security. Deliver and pitch your topic in the best possible manner with this data center infrastructure management it data center security standards we used professional pdf. Use them to share invaluable insights on layered security measures, access lists, video surveillance, secure access points, security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Big Data Architect Security Of Information In Big Data Graphics PDF
This slide represents the securing information in big data challenge of big data and solutions to this challenge, such as encryption data, separation of data, security monitoring in real-time, and so on.Deliver an awe inspiring pitch with this creative Big Data Architect Security Of Information In Big Data Graphics PDF bundle. Topics like Most Challenging, Securing Massive, Data Collections can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Tools Used In Cloud Security Cloud Computing Security IT Ppt Background Images PDF
This slide represents the list of tools utilized under cloud security systems to protect, manage, store and control data on the cloud. This is a tools used in cloud security cloud computing security it ppt background images pdf template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like silver sky, centrify, doc tracker, proofpoint, whitehat. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Elements Of Information Technology Security Cloud Security Ppt Outline Background Images PDF
This slide defines the cloud security element of cyber security and various threats that can breach cloud security, such as malware injection, malicious insiders, insecure APIs, etc. This is a it security elements of information technology security cloud security ppt outline background images pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like data breaches, malware injections, malicious insiders, account hijacking, distributed denial of service. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Data Analytics Management Security Of Information In Big Data Summary PDF
This slide represents the securing information in big data challenge of big data and solutions to this challenge, such as encryption data, separation of data, security monitoring in real-time, and so on.Deliver an awe inspiring pitch with this creative Data Analytics Management Security Of Information In Big Data Summary PDF bundle. Topics like Securing Massive, Companies Frequently, Comprehending Preserving can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

CCTV Security Services PPT Template
Drive the power of innovation with our revolutionary CCTV Security Services PPT Template. This dynamic tool empowers you to create visually-stunning presentations that leave a lasting impression. With its user-friendly interface and 100 percent editable features, you can effortlessly customize every aspect of your slides, ensuring they align perfectly with your message. No design skills No problem. Our expertly crafted template provides a solid foundation for your ideas, allowing you to focus on what matters most delivering a compelling presentation. Do not settle for mediocrity, choose excellence with our template today.
Immediate And Long Term Impact Of Data Security Breach Data Breach Prevention Topics Pdf
This slide outlines the immediate and longstanding expenses associated with data breaches. The direct business costs include government fines, public relations costs, attorney fees, cybersecurity investigations, operational disruption, etc. Retrieve professionally designed Immediate And Long Term Impact Of Data Security Breach Data Breach Prevention Topics Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Data Center Infrastructure Management IT Data Center Security And Safety Demonstration PDF
This slide represents the data center security and safety that includes physical security, climate control system, data backup system, data backup system, and backup power generator. Deliver an awe inspiring pitch with this creative data center infrastructure management it data center security and safety demonstration pdf bundle. Topics like client privacy, physical security, waterless sprinklers, data backup system, virus prevention system can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Working Of Common Data Encryption Data Security In Cloud Computing Ppt Example
This slide represents the working flow of Common Data Encryption DES algorithm. The purpose of this slide is to outline the algorithm steps. This slide also explains the DES modes of operation, which include Digital Codebook, Cipher Block Chaining, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Working Of Common Data Encryption Data Security In Cloud Computing Ppt Example and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Working Of Common Data Encryption Cloud Data Security Using Cryptography Demonstration Pdf
This slide represents the working flow of Common Data Encryption DES algorithm. The purpose of this slide is to outline the algorithm steps. This slide also explains the DES modes of operation, which include Digital Codebook, Cipher Block Chaining, etc. Boost your pitch with our creativeWorking Of Common Data Encryption Cloud Data Security Using Cryptography Demonstration Pdf. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Security Management Plan Steps In Detail Data Backup And Data Loss Recovery Plan Demonstration PDF
This slide provides information about the eighth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Data Backup and Data Loss Recovery Plan. Presenting Security management plan steps in detail data backup and data loss recovery plan demonstration pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like security management plan steps in detail - data backup and data loss recovery plan. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
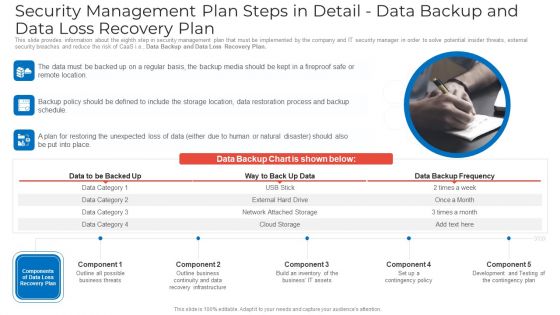
Security Management Plan Steps In Detail Data Backup And Data Loss Recovery Plan Ideas PDF
This slide provides information about the eighth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Data Backup and Data Loss Recovery Plan. This is a security management plan steps in detail data backup and data loss recovery plan ideas pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security management plan steps in detail data backup and data loss recovery plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Data Center Infrastructure Management IT Checklist We Follow For Data Center Security Formats PDF
This slide depicts the best practices for data center security based including identity and control data, classify sensitive data, map data flows, define groups, periodic audits, and reviews and integrate devsecops. Deliver an awe inspiring pitch with this creative data center infrastructure management it checklist we follow for data center security formats pdf bundle. Topics like identity and control data, classify sensitive data, map data flows, define groups, periodic audits and reviews, integrate devsecops can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Data Privacy Data Security Ppt PowerPoint Presentation Ideas Sample Cpb Pdf
Presenting this set of slides with name data privacy data security ppt powerpoint presentation ideas sample cpb pdf. This is an editable Powerpoint four stages graphic that deals with topics like data privacy data security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Security Management Plan Steps In Detail Data Backup And Data Loss Recovery Plan Professional PDF
This is a security management plan steps in detail data backup and data loss recovery plan professional pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like application security tools, categories of application, data backup frequency. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Executing Advance Data Analytics At Workspace Enabling Data Security Risk Demonstration PDF
The data security risk management action plan will help in keeping the track of potential risks that are existing and what are their level, what are the resources required to handle them. Deliver and pitch your topic in the best possible manner with this executing advance data analytics at workspace enabling data security risk demonstration pdf. Use them to share invaluable insights on enabling data security risk management action plan and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Executing Advance Data Analytics At Workspace Enabling Data Security Risk Icons PDF
The data security risk management action plan will help in keeping the track of potential risks that are existing and what are their level, what are the resources required to handle them. Deliver and pitch your topic in the best possible manner with this executing advance data analytics at workspace enabling data security risk icons pdf. Use them to share invaluable insights on enabling data security risk management action plan and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Security Elements Of Information Technology Security Network Security Ppt Pictures Graphics PDF
This slide represents the network security element of cyber security and different network security methods such as firewalls, email security, web security, and antivirus software. Presenting it security elements of information technology security network security ppt pictures graphics pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like web security, end point security, virtual private network, email security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
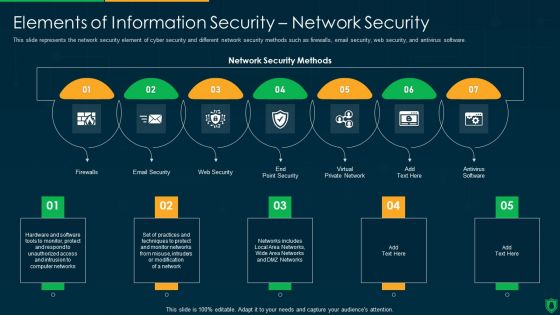
Info Security Elements Of Information Security Network Security Ppt PowerPoint Presentation File Vector PDF
This slide represents the network security element of cyber security and different network security methods such as firewalls, email security, web security, and antivirus software. Presenting info security elements of information security network security ppt powerpoint presentation file vector pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like email security, web security, virtual private network, firewalls. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

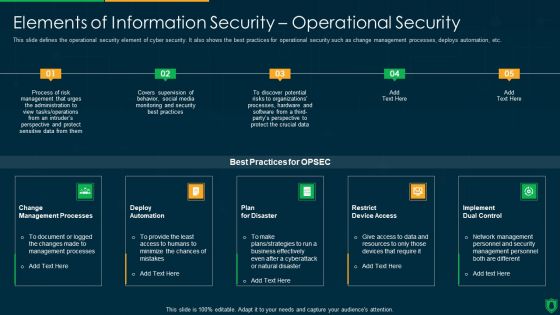
IT Security Elements Of Information Technology Security Operational Security Ppt Professional Format Ideas PDF
This slide defines the operational security element of cyber security. It also shows the best practices for operational security such as change management processes, deploys automation, etc. This is a it security elements of information technology security operational security ppt professional format ideas pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like change management processes, deploy automation, plan for disaster, restrict device access, implement dual control. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Information Security Cloud Security Checklist Security Patches And Updates Ppt Show Background Designs PDF
This slide depicts the importance of security patches and timely updates of security technologies. It also shows how it is crucial to scan systems, servers, and frameworks regularly. This is a Cloud Information Security Cloud Security Checklist Security Patches And Updates Ppt Show Background Designs PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Measures, New Technologies, Security Tool. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
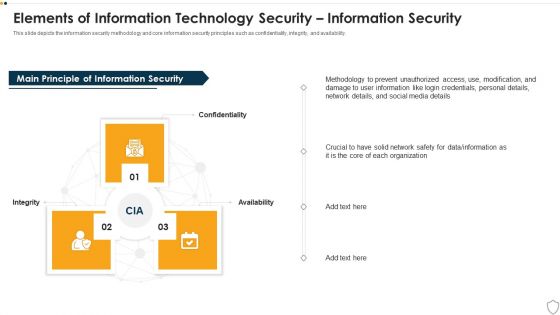
IT Security Elements Of Information Technology Security Information Security Ppt Gallery Grid PDF
This slide depicts the information security methodology and core information security principles such as confidentiality, integrity, and availability. This is a it security elements of information technology security information security ppt gallery grid pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like integrity, confidentiality, availability. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
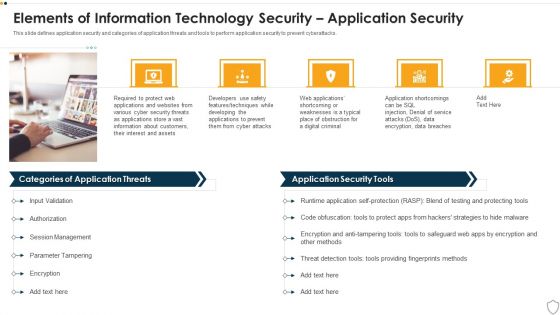
IT Security Elements Of Information Technology Security Application Security Ppt Slide Download PDF
This slide defines application security and categories of application threats and tools to perform application security to prevent cyberattacks. Presenting it security elements of information technology security application security ppt slide download pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like developing, techniques, service, management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Info Security Elements Of Information Security Application Security Ppt PowerPoint Presentation File Graphics Download PDF
This slide defines application security and categories of application threats and tools to perform application security to prevent cyberattacks. Deliver and pitch your topic in the best possible manner with this info security elements of information security application security ppt powerpoint presentation file graphics download pdf. Use them to share invaluable insights on application security tools, parameter tampering, encryption and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Desktop Security Management Elements Of Computer Security Operational Security Themes PDF
This slide defines the operational security element of cyber security. It also shows the best practices for operational security such as change management processes, deploys automation, etc. This is a desktop security management elements of computer security operational security themes pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like management, resources, require, security, plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
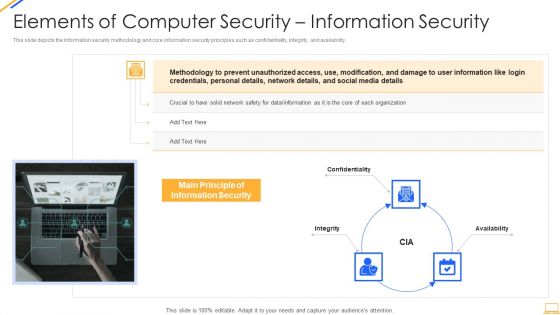
Desktop Security Management Elements Of Computer Security Information Security Portrait PDF
This slide depicts the information security methodology and core information security principles such as confidentiality, integrity, and availability. Presenting desktop security management elements of computer security information security portrait pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like social media, information security, organization, network. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Extended Detection And Response For Endpoint Security Detection Information PDF
This slide highlights the External Data Representation layer for end security prevention and detection which includes endpoint protection, network protection, user protection and deception.There are so many reasons you need a Extended Detection And Response For Endpoint Security Detection Information PDF. The first reason is you can notspend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Info Security Elements Of Information Security Information Security Ppt PowerPoint Presentation Gallery Smartart PDF
This slide depicts the information security methodology and core information security principles such as confidentiality, integrity, and availability. This is a info security elements of information security information security ppt powerpoint presentation gallery smartart pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like confidentiality, availability, integrity, information security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Desktop Security Management Elements Of Computer Security Application Security Download PDF
This is a desktop security management elements of computer security application security download pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like applications, information, security, customers, required. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Info Security Elements Of Information Security Operational Security Ppt PowerPoint Presentation File Backgrounds PDF
This slide defines the operational security element of cyber security. It also shows the best practices for operational security such as change management processes, deploys automation, etc. This is a info security elements of information security operational security ppt powerpoint presentation file backgrounds pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like change management processes, deploy automation, plan for disaster, implement dual control. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Cloud Security Assessment Cloud Security Checklist Security Patches And Updates Icons PDF
This slide depicts the importance of security patches and timely updates of security technologies. It also shows how it is crucial to scan systems, servers, and frameworks regularly.This is a Cloud Security Assessment Cloud Security Checklist Security Patches And Updates Icons PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Measures, Latest Or Advanced, Patches On Developed You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
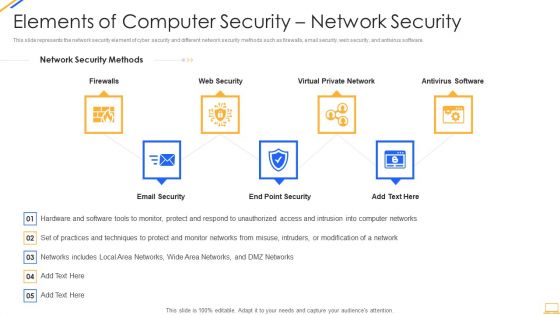
Desktop Security Management Elements Of Computer Security Network Security Infographics PDF
This slide represents the network security element of cyber security and different network security methods such as firewalls, email security, web security, and antivirus software. Presenting desktop security management elements of computer security network security infographics pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like network, security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Cloud Security Checklist Security Patches And Updates Cloud Computing Security IT Ppt File Icon PDF
This slide depicts the importance of security patches and timely updates of security technologies. It also shows how it is crucial to scan systems, servers, and frameworks regularly. Presenting cloud security checklist security patches and updates cloud computing security it ppt file icon pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like organization, measures, technologies, developed. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information And Technology Security Operations Role Of Security Operations Centre In Security Operations Brochure PDF
This slide portrays information regarding the role of security operations center in SecOps and how firm behave before, after and towards SecOps implementation. Presenting information and technology security operations role of security operations centre in security operations brochure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like organizational, collaborate, security, analysts. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
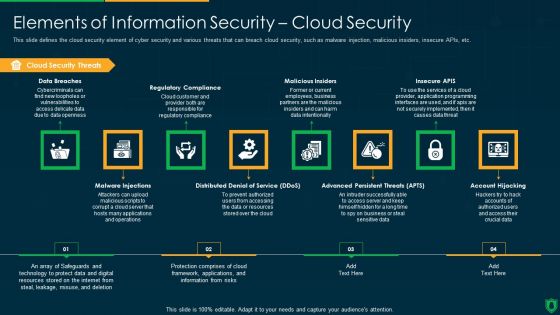
Info Security Elements Of Information Security Cloud Security Ppt PowerPoint Presentation Gallery Graphics Download PDF
This slide defines the cloud security element of cyber security and various threats that can breach cloud security, such as malware injection, malicious insiders, insecure APIs, etc. Presenting info security elements of information security cloud security ppt powerpoint presentation gallery graphics download pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like cloud security threats, regulatory compliance, malicious insiders, insecure apis. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Pillars Of Cloud Security Process Based Security Cloud Computing Security IT Ppt Slides Skills PDF
This slide represents the process-based security pillar of cloud security. It also shows how it works and what precautions does it take. This is a pillars of cloud security process based security cloud computing security it ppt slides skills pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like movement, cloud security, vulnerabilities, lifecycle. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Desktop Security Management Elements Of Computer Security Cloud Security Diagrams PDF
This slide defines the cloud security element of cyber security and various threats that can breach cloud security, such as malware injection, malicious insiders, insecure APIs, etc. This is a desktop security management elements of computer security cloud security diagrams pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like applications, service. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Assessment Pillars Of Cloud Security Process Based Security Mockup PDF
This slide represents the process-based security pillar of cloud security. It also shows how it works and what precautions does it take.This is a Cloud Security Assessment Pillars Of Cloud Security Process Based Security Mockup PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Vulnerability Management, Recognizes Vulnerabilities, Operational Security You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
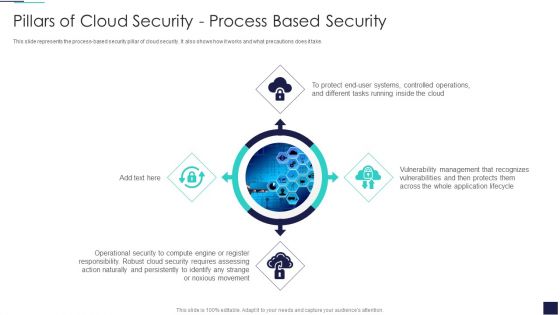
Cloud Information Security Pillars Of Cloud Security Process Based Security Ppt Slides Topics PDF
This slide represents the process-based security pillar of cloud security. It also shows how it works and what precautions does it take. This is a Cloud Information Security Pillars Of Cloud Security Process Based Security Ppt Slides Topics PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Controlled Operations, Vulnerability Management, Application Lifecycle. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Essential Elements Of Security Monitoring Plan Sample PDF
This slide provides information about some of the essential elements that must be a part of security monitoring plan in order to protect sensitive information. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach essential elements of security monitoring plan sample pdf bundle. Topics like critical infrastructure, cloud security, application security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
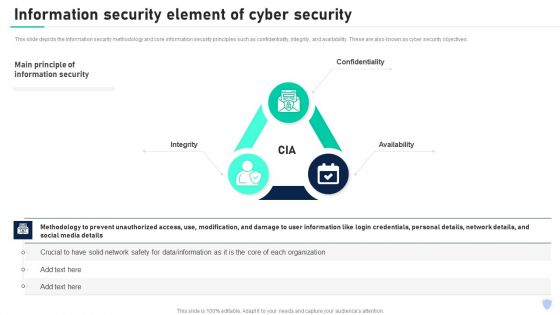
Cyber Security Components To Enhance Processes Information Security Element Of Cyber Security Mockup PDF
This slide depicts the information security methodology and core information security principles such as confidentiality, integrity, and availability. These are also known as cyber security objectives. Want to ace your presentation in front of a live audience Our Cyber Security Components To Enhance Processes Information Security Element Of Cyber Security Mockup PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Cloud Information Security Tools Used In Cloud Security Ppt Diagram Lists PDF
This slide represents the list of tools utilized under cloud security systems to protect, manage, store and control data on the cloud. This is a Cloud Information Security Tools Used In Cloud Security Ppt Diagram Lists PDF template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Cloud Solutions, Advanced Threats, Cipher Cloud. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security Components To Enhance Processes Cloud Security Element Of Cyber Security Brochure PDF
This slide defines the cloud security element of cyber security and various threats that can breach cloud security, such as malware injection, malicious insiders, insecure APIs, etc. It also caters to best practices and the security framework of the cloud. Create an editable Cyber Security Components To Enhance Processes Cloud Security Element Of Cyber Security Brochure PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Cyber Security Components To Enhance Processes Cloud Security Element Of Cyber Security Brochure PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Cyber Security Components To Enhance Processes Operational Security Element Of Cyber Security Graphics PDF
This slide defines the operational security element of cyber security. It also shows the best practices for operational security, such as changing management processes, deploying automation, planning for disasters, restricting device access, and implementing dual control. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Cyber Security Components To Enhance Processes Operational Security Element Of Cyber Security Graphics PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Cyber Security Components To Enhance Processes Operational Security Element Of Cyber Security Graphics PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

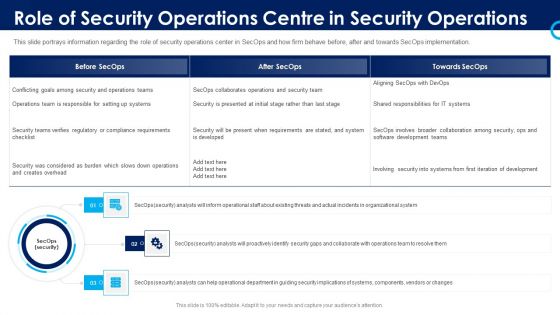
Security And Process Integration Role Of Security Operations Centre In Security Operations Inspiration PDF
This slide portrays information regarding the role of security operations center in SecOps and how firm behave before, after and towards SecOps implementation. Presenting security and process integration role of security operations centre in security operations inspiration pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like organizational, collaborate, security, analysts. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Organizational Security Solutions Role Of Security Operations Centre In Security Operations Graphics PDF
This slide portrays information regarding the role of security operations center in SecOps and how firm behave before, after and towards SecOps implementation. Presenting organizational security solutions role of security operations centre in security operations graphics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like organizational, collaborate, security, analysts. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Functioning Centre Role Of Security Operations Centre In Security Operations Sample PDF
This slide portrays information regarding the role of security operations center in SecOps and how firm behave before, after and towards SecOps implementation. Presenting security functioning centre role of security operations centre in security operations sample pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like organizational system, security, operations team. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
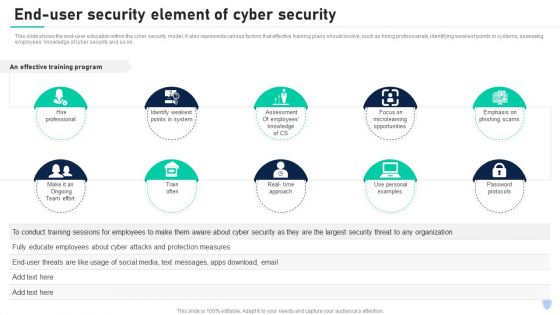
Cyber Security Components To Enhance Processes End User Security Element Of Cyber Security Formats PDF
This slide shows the end user education within the cyber security model. It also represents various factors that effective training plans should involve, such as hiring professionals, identifying weakest points in systems, assessing employees knowledge of cyber security and so on. Find a pre designed and impeccable Cyber Security Components To Enhance Processes End User Security Element Of Cyber Security Formats PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Cyber Security Components To Enhance Processes End User Security Element Of Cyber Security Brochure PDF
This slide shows the end-user education within the cyber security model. It also represents various factors that effective training plans should involve, such as hiring professionals, identifying weakest points in systems, assessing employees knowledge of cyber security and so on. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Cyber Security Components To Enhance Processes End User Security Element Of Cyber Security Brochure PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
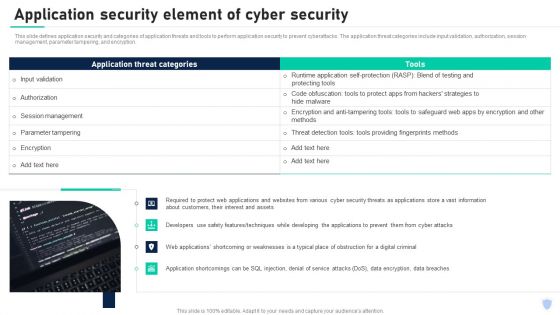
Cyber Security Components To Enhance Processes Application Security Element Of Cyber Security Infographics PDF
This slide defines application security and categories of application threats and tools to perform application security to prevent cyberattacks. The application threat categories include input validation, authorization, session management, parameter tampering, and encryption. Boost your pitch with our creative Cyber Security Components To Enhance Processes Career Opportunities In Cybersecurity Profession Sample PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Building Trust With IoT Security Overview Of Encryption Security Attacks In IoT Environment IoT SS V
This slide presents an overview and types of encryption security threats, helpful in protecting data during transmission and storage. It includes various threats such as side channel, cryptanalysis, and man in middle attack. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Building Trust With IoT Security Overview Of Encryption Security Attacks In IoT Environment IoT SS V for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Secure Files Security PowerPoint Presentation Slides Cc
Microsoft PowerPoint Slides and Backgrounds with illustration of a lock place dinfront of and open file folder

Secure Files Security PowerPoint Presentation Slides S
Microsoft PowerPoint Slides and Backgrounds with illustration of a lock place dinfront of and open file folder

Secure Files Security PowerPoint Presentation Slides C
Microsoft PowerPoint Slides and Backgrounds with illustration of a lock place dinfront of and open file folder

Secure Files Security PowerPoint Presentation Slides F
Microsoft PowerPoint Slides and Backgrounds with illustration of a lock place dinfront of and open file folder

Secure Files Security PowerPoint Presentation Slides R
Microsoft PowerPoint Slides and Backgrounds with illustration of a lock place dinfront of and open file folder
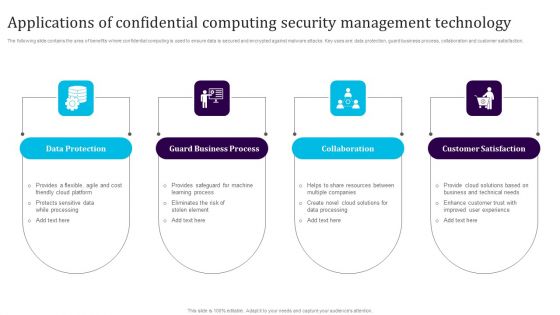
Applications Of Confidential Computing Security Management Technology Sample PDF
The following slide contains the area of benefits where confidential computing is used to ensure data is secured and encrypted against malware attacks. Key uses are data protection, guard business process, collaboration and customer satisfaction. Presenting Applications Of Confidential Computing Security Management Technology Sample PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Data Protection, Guard Business Process, Collaboration, Customer Satisfaction. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Current Security Monitoring Challenges Slides PDF
This slide shows some of the current Security Monitoring challenges and issues that are faced by the company and cyber security monitoring managers. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach current security monitoring challenges slides pdf bundle. Topics like current security monitoring challenges the company is facing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Security Monitoring Dashboard With Malicious Icons PDF
Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach security monitoring dashboard with malicious icons pdf bundle. Topics like security monitoring dashboard with malicious requests and average latency rate can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Best Data Security Software 30 60 90 Days Plan For Company Online Database Security Proposal Sample PDF
Presenting this set of slides with name best data security software 30 60 90 days plan for company online database security proposal sample pdf. This is a three stage process. The stages in this process are 30 60 90 days plan, company, online database security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
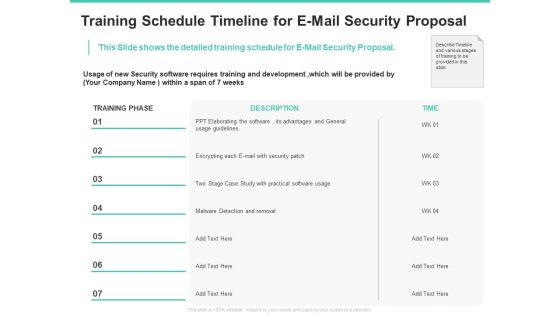
Email Security Encryption And Data Loss Prevention Training Schedule Timeline For E Mail Security Proposal Diagrams PDF
This Slide shows the detailed training schedule for E-Mail Security Proposal. Deliver an awe-inspiring pitch with this creative email security encryption and data loss prevention training schedule timeline for e mail security proposal diagrams pdf bundle. Topics like case study, security, development, timeline can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Security Monitoring Dashboard With Application Slides PDF
Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach security monitoring dashboard with application slides pdf. Use them to share invaluable insights on security monitoring dashboard with application control and operating system statistics and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information Systems Security And Risk Management Plan Current Information And Data Security Capabilities Of Firm Diagrams PDF
This slide showcases current capabilities of organization regarding information and data security. Its key component are risk management functions, required standard rating and actual standard rating. Boost your pitch with our creative Information Systems Security And Risk Management Plan Current Information And Data Security Capabilities Of Firm Diagrams PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

How Does Cloud Security Work Data Retention And Business Continuity Planning Cloud Computing Security IT Ppt Slides Demonstration PDF
This slide represents the data recovery and business continuity plan in cloud security and what to consider while making a business continuity plan. This is a how does cloud security work data retention and business continuity planning cloud computing security it ppt slides demonstration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like impact analysis, testing and maintenance, plan development, recovery strategies. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
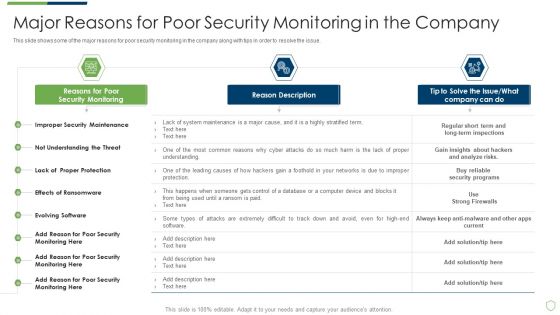
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Major Reasons For Poor Security Elements PDF
This slide shows some of the major reasons for poor security monitoring in the company along with tips in order to resolve the issue. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach major reasons for poor security elements pdf bundle. Topics like major reasons for poor security monitoring in the company can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Way To Overcome Security Introduction PDF
This slide provides information about the way that the company and security monitoring manager must choose in order to solve the challenge problem related to Malware Attacks and other potential security monitoring challenges. The solution is to set up an advanced Cybersecurity Monitoring Plan in place with the help of a set series of steps mentioned in the slide. This is a modern security observation plan to eradicate cybersecurity risk and data breach way to overcome security introduction pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like way to overcome security monitoring challenges setting up an advanced cybersecurity monitoring plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Best Data Security Software Statement Of Work And Contract For Company Online Database Security Proposal Themes PDF
Presenting this set of slides with name best data security software statement of work and contract for company online database security proposal themes pdf. This is a six stage process. The stages in this process are services rendered, mutual cooperation, terms of payment, plans cancellation, confidentiality, terms and termination. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
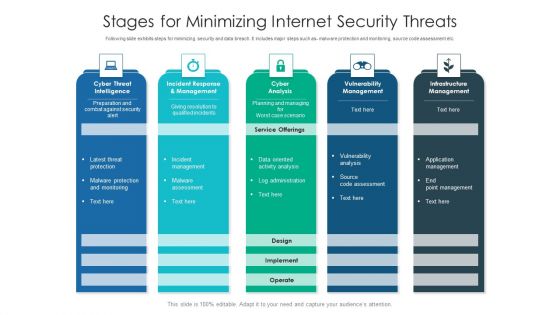
Stages For Minimizing Internet Security Threats Ideas PDF
Following slide exhibits steps for minimizing security and data breach. It includes major steps such as- malware protection and monitoring, source code assessment etc. Pitch your topic with ease and precision using this stages for minimizing internet security threats ideas pdf. This layout presents information on infrastructure management, cyber analysis, vulnerability management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
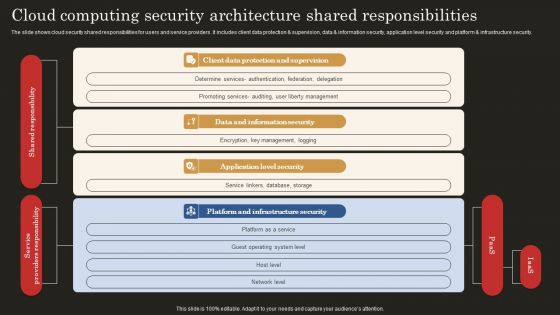
Cloud Computing Security Architecture Shared Responsibilities Brochure PDF
The slide shows cloud security shared responsibilities for users and service providers. It includes client data protection and supervision, data and information security, application level security and platform and infrastructure security. Showcasing this set of slides titled Cloud Computing Security Architecture Shared Responsibilities Brochure PDF. The topics addressed in these templates are Client Data Protection, Data Information Security, Application Level Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
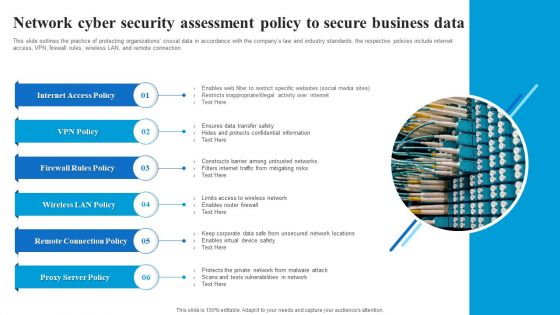
Network Cyber Security Assessment Policy To Secure Business Data Microsoft PDF
This slide outlines the practice of protecting organizations crucial data in accordance with the companys law and industry standards. the respective policies include internet access, VPN, firewall rules, wireless LAN, and remote connection. Showcasing this set of slides titled Network Cyber Security Assessment Policy To Secure Business Data Microsoft PDF. The topics addressed in these templates are Internet Access Policy, Firewall Rules Policy, Wireless LAN Policy, Remote Connection Policy. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Protecting PC Security From Hacker Vector Icon Ppt PowerPoint Presentation File Infographics PDF
Presenting protecting pc security from hacker vector icon ppt powerpoint presentation file infographics pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including protecting pc security from hacker vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Password Protected Security Control System Ppt PowerPoint Presentation Styles Ideas PDF
Persuade your audience using this password protected security control system ppt powerpoint presentation styles ideas pdf. This PPT design covers two stages, thus making it a great tool to use. It also caters to a variety of topics including password protected security control system. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

CASB 2 0 IT Cloud Access Security Broker Use Cases
This slide represents the use cases of cloud access security broker. The purpose of this slide is to showcase the multiple use cases of cloud access security broker, covering protection against threats, governing usage, securing data, and enforcing data loss and compliance policies. Presenting this PowerPoint presentation, titled CASB 2 0 IT Cloud Access Security Broker Use Cases, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this CASB 2 0 IT Cloud Access Security Broker Use Cases. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable CASB 2 0 IT Cloud Access Security Broker Use Cases that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
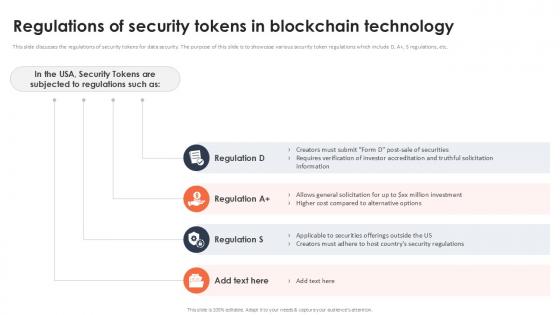
Regulations Of Security Tokens In Blockchain Technology Securing Your Data Ppt Slide
This slide discusses the regulations of security tokens for data security. The purpose of this slide is to showcase various security token regulations which include D, A, S regulations, etc. Find a pre-designed and impeccable Regulations Of Security Tokens In Blockchain Technology Securing Your Data Ppt Slide The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Extended Detection And Response For Endpoint Security Detection Themes PDF
This slide highlights the External Data Representation layer for end security prevention and detection which includes endpoint protection, network protection, user protection and deception. Boost your pitch with our creative Extended Detection And Response For Endpoint Security Detection Themes PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Comparative Analysis Of Security And Utility Token Securing Your Data Ppt Template
This slide highlights the differences between security and utility tokens. The purpose of this slide is to compare security and utility tokens on various aspects such as purpose, expectations, scam potential, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Comparative Analysis Of Security And Utility Token Securing Your Data Ppt Template can be your best option for delivering a presentation. Represent everything in detail using Comparative Analysis Of Security And Utility Token Securing Your Data Ppt Template and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Comparative Analysis Of Standard And Distributed Ledger Security Mockup Pdf
This slide analyses comparison of standard and blockchain security aimed at assessing respective security considerations to prevent attacks against both paradigms. The basis of challenges are denial of service, endpoint security, intentional misuse, code vulnerabilities and data protection Pitch your topic with ease and precision using this Comparative Analysis Of Standard And Distributed Ledger Security Mockup Pdf This layout presents information on Denial Of Service, Endpoint Security, Code Vulnerabilities It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Protected World Environment Security PowerPoint Templates Ppt Backgrounds For Slides 0313
We present our Protected World Environment Security PowerPoint Templates PPT Backgrounds For Slides 0313.Present our Environment PowerPoint Templates because Our PowerPoint Templates and Slides provide you with a vast range of viable options. Select the appropriate ones and just fill in your text. Download our Umbrellas PowerPoint Templates because Our PowerPoint Templates and Slides will provide you the cutting edge. Slice through the doubts in the minds of your listeners. Download our Security PowerPoint Templates because Your audience will believe you are the cats whiskers. Download and present our Future PowerPoint Templates because Our PowerPoint Templates and Slides are a sure bet. Gauranteed to win against all odds. Present our Success PowerPoint Templates because Your audience will believe you are the cats whiskers.Use these PowerPoint slides for presentations relating to Protection of an environment, security, environment, umbrellas, success, future. The prominent colors used in the PowerPoint template are Green, Gray, White.

Working Of Security Tokenization In Financial Assets Securing Your Data Ppt Powerpoint
This slide highlights the phases of security tokenization. The purpose of this slide is to showcase the working of security tokenization along with its phases which include creation, dividend distribution, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Working Of Security Tokenization In Financial Assets Securing Your Data Ppt Powerpoint These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Building Trust With IoT Security Edge Computing Role In Securing IoT Data IoT SS V
This slide showcases the significant role of edge computing in enhancing IoT data security and privacy. It include role such as data filtering and processing, localised threat identification, and reduce attack surface. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Building Trust With IoT Security Edge Computing Role In Securing IoT Data IoT SS V and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Bank Protected With Padlock And Chain Security PowerPoint Templates Ppt Backgrounds For Slides 0213
We present our Bank Protected With Padlock And Chain Security PowerPoint Templates PPT Backgrounds For Slides 0213.Use our Business PowerPoint Templates because Our PowerPoint Templates and Slides team portray an attitude of elegance. Personify this quality by using them regularly. Download and present our Security PowerPoint Templates because You can Stir your ideas in the cauldron of our PowerPoint Templates and Slides. Cast a magic spell on your audience. Use our Services PowerPoint Templates because Our PowerPoint Templates and Slides are focused like a searchlight beam. They highlight your ideas for your target audience. Download and present our Future PowerPoint Templates because You can Zap them with our PowerPoint Templates and Slides. See them reel under the impact. Present our Chains PowerPoint Templates because Your success is our commitment. Our PowerPoint Templates and Slides will ensure you reach your goal.Use these PowerPoint slides for presentations relating to Piggy bank secured with padlock and chain, business, security, services, future, chains. The prominent colors used in the PowerPoint template are Pink, Black, White.
Wireless Network Security System Icon Of Cloud Servers To Secure Data Clipart PDF
Persuade your audience using this wireless network security system icon of cloud servers to secure data clipart pdf. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including wireless network security system icon of cloud servers to secure data. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
What Are The Benefits Of A Cloud Security System Cloud Computing Security IT Ppt Icon Clipart Images PDF
This slide represents the benefits of a cloud security system, such as efficient recovery, openness, no hardware requirement, DDOS protection, and data security. Deliver an awe inspiring pitch with this creative what are the benefits of a cloud security system cloud computing security it ppt icon clipart images pdf bundle. Topics like efficient recovery, openness, no hardware required, ddos protection, efficient data security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Information Security What Are The Benefits Of A Cloud Security System Ppt Gallery Infographic Template PDF
This slide represents the benefits of a cloud security system, such as efficient recovery, openness, no hardware requirement, DDOS protection, and data security. This is a Cloud Information Security What Are The Benefits Of A Cloud Security System Ppt Gallery Infographic Template PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Efficient Recovery, DDOS Protection, Efficient Data. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Protected By A Risk Security PowerPoint Templates And PowerPoint Backgrounds 0211
Microsoft PowerPoint Template and Background with a pair of silver handcuffs attached to satisfaction guaranteed symbol
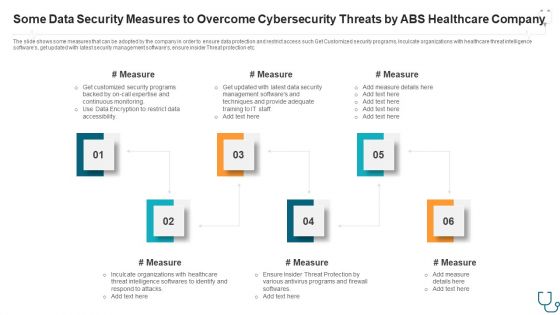
Some Data Security Measures To Overcome Cybersecurity Threats By Abs Healthcare Company Ppt Styles Slide Portrait PDF
The slide shows some measures that can be adopted by the company in order to ensure data protection and restrict access such Get Customized security programs, Inculcate organizations with healthcare threat intelligence softwares, get updated with latest security management softwares, ensure insider Threat protection etc. This is a some data security measures to overcome cybersecurity threats by abs healthcare company ppt styles slide portrait pdf. template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like some data security measures to overcome cybersecurity threats by abs healthcare company. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
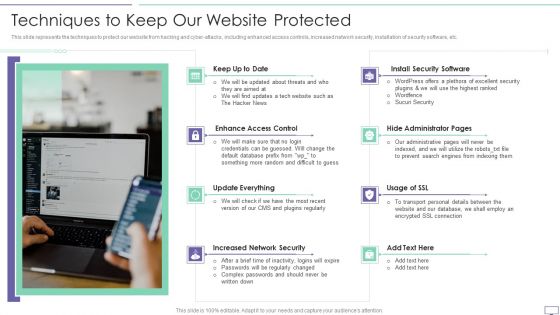
IT Security Hacker Techniques To Keep Our Website Protected Guidelines PDF
This slide represents the techniques to protect our website from hacking and cyber attacks, including enhanced access controls, increased network security, installation of security software, etc.This is a IT Security Hacker Techniques To Keep Our Website Protected Guidelines PDF template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Software, Enhance Access, Update Everything. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IAC Security For Protecting Cloud IAC Tools For Performance Analysis PPT Slide
This slide showcases the security of Infrastructure as Code for protecting cloud infrastructure. The purpose of this slide is to highlight the importance of IaC security such as consistency and predictability, early detection and prevention, reduced human error, etc. Retrieve professionally designed IAC Security For Protecting Cloud IAC Tools For Performance Analysis PPT Slide to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
Computer Protected With Security System From Online Threat Ppt PowerPoint Presentation File Example Topics PDF
Presenting computer protected with security system from online threat ppt powerpoint presentation file example topics pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including computer protected with security system from online threat. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Client Side Encryption To Protect Client Side Encryption PPT Example
This slide discusses client-side encryption to protect the data after storing it in the cloud network. This slide also highlights the importance of client-side encryption in different scenarios, such as secure collaboration, protection against cloud provider vulnerabilities, etc. There are so many reasons you need a Client Side Encryption To Protect Client Side Encryption PPT Example. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
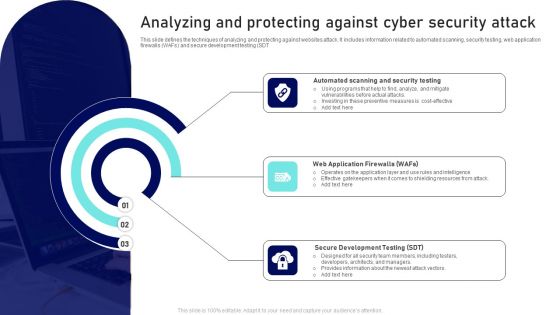
Analyzing And Protecting Against Cyber Security Attack Ppt Pictures Background Designs PDF
This slide defines the techniques of analyzing and protecting against websites attack. It includes information related to automated scanning, security testing, web application firewalls WAFs and secure development testing SDT. Presenting Analyzing And Protecting Against Cyber Security Attack Ppt Pictures Background Designs PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Web Application Firewalls, Secure Development Testing, Automated Scanning, Security Testing. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Smart Phone Application Protected With IT Security Software Ppt PowerPoint Presentation File Graphic Images PDF
Persuade your audience using this smart phone application protected with it security software ppt powerpoint presentation file graphic images pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including smart phone application protected with it security software. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Security Control Techniques For Real Estate Project Personal Protective Equipment For Construction Themes PDF
Get a simple yet stunning designed Security Control Techniques For Real Estate Project Personal Protective Equipment For Construction Themes PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Security Control Techniques For Real Estate Project Personal Protective Equipment For Construction Themes PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for. Grab this template today.
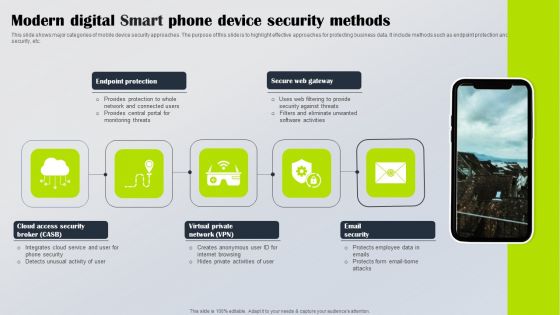
Modern Digital Smart Phone Device Security Methods Elements PDF
This slide shows major categories of mobile device security approaches. The purpose of this slide is to highlight effective approaches for protecting business data. It include methods such as endpoint protection and email security, etc. Persuade your audience using this Modern Digital Smart Phone Device Security Methods Elements PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Endpoint Protection, Secure Web Gateway, Email Security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
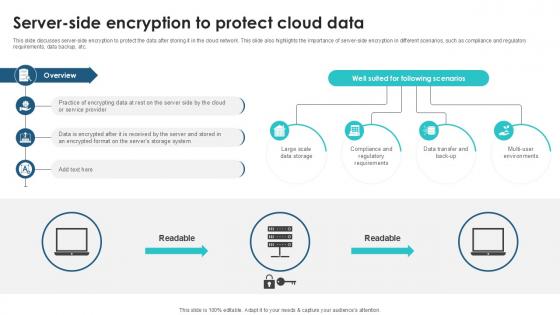
Server Side Encryption To Protect Client Side Encryption PPT Presentation
This slide discusses server-side encryption to protect the data after storing it in the cloud network. This slide also highlights the importance of server-side encryption in different scenarios, such as compliance and regulatory requirements, data backup, etc. Are you searching for a Server Side Encryption To Protect Client Side Encryption PPT Presentation that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Server Side Encryption To Protect Client Side Encryption PPT Presentation from Slidegeeks today.

Strategy To Protect Iot Integrated Devices Designs PDF
This slide showcases strategy to protect internet of things IoT integrated devices. It includes information about virtual containers, user access, identification, communication, data center, virtual conditions, etc. This is a Strategy To Protect Iot Integrated Devices Designs PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Segregate Networks, Connect New Iot Device, Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Strategy To Protect Iot Integrated Devices Sample PDF
This slide showcases strategy to protect internet of things IoT integrated devices. It includes information about virtual containers, user access, identification, communication, data center, virtual conditions, etc. Presenting Strategy To Protect Iot Integrated Devices Sample PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Security, Network, Applications. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
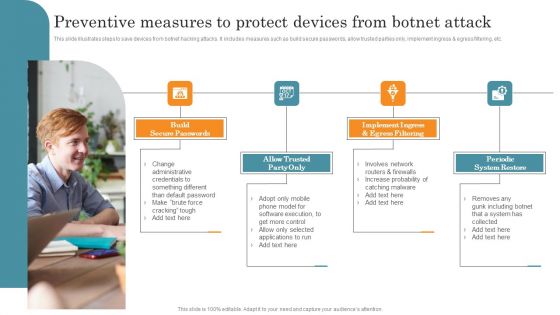
Preventive Measures To Protect Devices From Botnet Attack Demonstration PDF
This slide illustrates steps to save devices from botnet hacking attacks. It includes measures such as build secure passwords, allow trusted parties only, implement ingress and egress filtering, etc. Presenting Preventive Measures To Protect Devices From Botnet Attack Demonstration PDF to dispense important information. This template comprises Four stages. It also presents valuable insights into the topics including Build Secure Passwords, Allow Trusted Party Only, Implement Ingress. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Security And Identity Platform Ppt Background
This is a security and identity platform ppt background. This is a eight stage process. The stages in this process are big data platform, database platform, data warehouse platform, e commerce platforms, bpm platform, security and identity platform, development platform, integration platforms.
Simple Ways To Protect Oneself From Identity Fraud Diagrams PDF
This slide showcases approaches for protecting identity theft. This template focuses on applying different strategies which eliminate or reduce any chances of fraud occurrence. It includes information related to securing hard copies, setting strong passwords, etc. Presenting Simple Ways To Protect Oneself From Identity Fraud Diagrams PDF to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including Choose Strong Passwords, Beware Doubtful, Examine Financial Statements. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Various Practices To Protect Functional Technology System Information PDF
Showcasing this set of slides titled various practices to protect functional technology system information pdf. The topics addressed in these templates are inventory software, awareness training, security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Best Way Protect Passwords In Powerpoint And Google Slides Cpb
Introducing our well designed Best Way Protect Passwords In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Best Way Protect Passwords. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience.

Password Protect In Powerpoint And Google Slides Cpb
Introducing our well-designed Password Protect In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Password Protect. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience.

Datacenter Services Network Security Ppt Sample
This is a datacenter services network security ppt sample. This is a five stage process. The stages in this process are arrow, business, marketing.
Password Protect Gmail Attachment In Powerpoint And Google Slides Cpb
Introducing our well-designed Password Protect Gmail Attachment In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Password Manager Android Windows. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience.

Protect Earth Globe Nature PowerPoint Templates And PowerPoint Themes 1012
Protect Earth Globe Nature PowerPoint Templates And PowerPoint Themes 1012-Visually support your Microsoft office PPT Presentation with our above template illustrating a 3d word protect with globe. This image represents the concept of environment protection. It portrays the concept of conservation, earth, energy, environment, global, nature, planet, pollution, power, protect, protection, recycle, reduce, save, sphere and warming. Our unique image makes your presentations professional showing that you care about even the smallest details.-Protect Earth Globe Nature PowerPoint Templates And PowerPoint Themes 1012-This PowerPoint template can be used for presentations relating to-Project world globe, environment, nature, earth, global, technology
Ways To Secure And Protect Business Website Ppt PowerPoint Presentation Gallery Layout PDF
Persuade your audience using this ways to secure and protect business website ppt powerpoint presentation gallery layout pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including ways to secure and protect business website. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
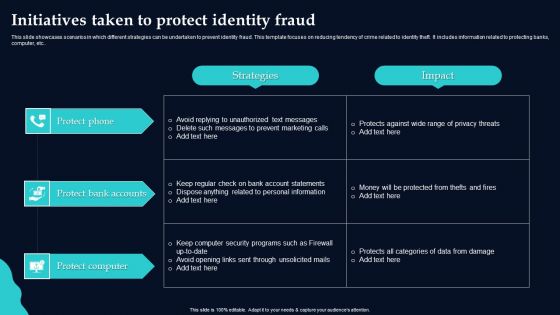
Initiatives Taken To Protect Identity Fraud Professional PDF
This slide showcases scenarios in which different strategies can be undertaken to prevent identity fraud. This template focuses on reducing tendency of crime related to identity theft. It includes information related to protecting banks, computer, etc. Showcasing this set of slides titled Initiatives Taken To Protect Identity Fraud Professional PDF. The topics addressed in these templates are Protect Phone, Protect Bank Accounts, Protect Computer. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Security Training Program Frameworks Ppt Infographics Show PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas.This is a security training program frameworks ppt infographics show pdf. template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like build and maintain a secure network and systems, protect cardholder data. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Stock Photo Business Strategy Implementation Protect Your Financial Condition Photos
Brace Yourself, Arm Your Thoughts. Prepare For The Hustle With Our stock photo business strategy implementation protect your financial condition stock photo photos Powerpoint Templates. Generate Ecstasy With Our money Powerpoint Templates. Your Thoughts Will Delight Your Audience.

Best Practices To Protect Technology Systems Contd Elements PDF
This slide provides information regarding best practices to protect technology systems in terms of compliance with legal regulations on student privacy, internet and content filtering. Presenting Best Practices To Protect Technology Systems Contd Elements PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Student Privacy, Content Filtering, Understanding District. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Guidelines Under Environmental Policy To Protect Environment Sample PDF
The slide provides the major guidelines and rules under environmental policy to protect environment. Major rules and guidelines include green completion rule, underground injection control program, the bureau of land management BLM rule etc.Presenting guidelines under environmental policy to protect environment sample pdf. to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like green completion rule, management software, power and cooling. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Protect Globe Environment PowerPoint Templates And PowerPoint Themes 1012
The above template displays a diagram of 3D word protect with globe. This image represents the concept of environment. It is a useful captivating tool concieved to enable you to define your message in your global PPT presentations. Go ahead and add personality to your presentations with our stunning template. Deliver amazing presentations to mesmerize your audience.

Guidelines Under Environmental Policy To Protect Environment Inspiration PDF
Presenting guidelines under environmental policy to protect environment inspiration pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like green completion rule, underground injection control program, the bureau of land management blm rule. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Kids Health Protect Insurance Ppt PowerPoint Presentation Complete Deck
Improve your presentation delivery using this kids health protect insurance ppt powerpoint presentation complete deck. Support your business vision and objectives using this well-structured PPT deck. This template offers a great starting point for delivering beautifully designed presentations on the topic of your choice. Comprising twelve slides this professionally designed template is all you need to host discussion and meetings with collaborators. Each slide is self-explanatory and equipped with high-quality graphics that can be adjusted to your needs. Therefore, you will face no difficulty in portraying your desired content using this PPT slideshow. This PowerPoint slideshow contains every important element that you need for a great pitch. It is not only editable but also available for immediate download and utilization. The color, font size, background, shapes everything can be modified to create your unique presentation layout. Therefore, download it now.
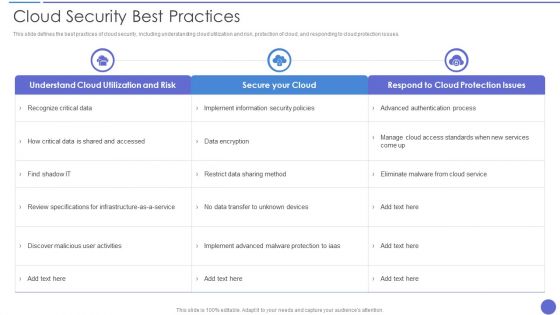
Cloud Security Best Practices Themes PDF
This slide defines the best practices of cloud security, including understanding cloud utilization and risk, protection of cloud, and responding to cloud protection issues. Deliver and pitch your topic in the best possible manner with this Cloud Security Best Practices Themes PDF. Use them to share invaluable insights on Secure Your Cloud, Data Encryption, Recognize Critical Data and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Cloud Based Email Security Market Report Issues Faced By Companies Data Ppt Icon Templates PDF
Various issues faced by the end user in E Mail marketing Industry are shown in this slide. Presenting cloud based email security market report issues faced by companies data ppt icon templates pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security for confidential data, protection against malware, protection phishing scams, threat of weak password. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Building Trust With IoT Security Essential Data Privacy Regulations For Ensuring Connected Devices IoT SS V
This slide exhibits personal data handling regulations for organisations across various regions. It includes data regulations such as general data protection regulation, the California consumer privacy act, and personal data protection act in Singapore. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Building Trust With IoT Security Essential Data Privacy Regulations For Ensuring Connected Devices IoT SS V was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Building Trust With IoT Security Essential Data Privacy Regulations For Ensuring Connected Devices IoT SS V.

Extended Detection And Response For Endpoint Security Detection Clipart PDF
This slide highlights the External Data Representation layer for end security prevention and detection which includes endpoint protection, network protection, user protection and deception. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Extended Detection And Response For Endpoint Security Detection Clipart PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Extended Detection And Response For Endpoint Security Detection Clipart PDF today and make your presentation stand out from the rest.

CASB 2 0 IT Cloud Access Security Broker Pillar Overview
This slide represents the four major pillars of cloud access security broker. The purpose of this slide is to showcase the main pillars of implementing a cloud access security broker. The pillars include compliance, visibility, threat protection, and data security. Are you searching for a CASB 2 0 IT Cloud Access Security Broker Pillar Overview that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download CASB 2 0 IT Cloud Access Security Broker Pillar Overview from Slidegeeks today.
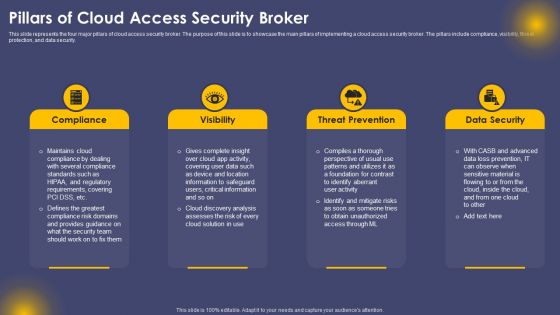
Pillars Of Cloud Access Security Broker Ppt Show Background PDF
This slide represents the four major pillars of cloud access security broker. The purpose of this slide is to showcase the main pillars of implementing a cloud access security broker. The pillars include compliance, visibility, threat protection, and data security. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Pillars Of Cloud Access Security Broker Ppt Show Background PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Pillars Of Cloud Access Security Broker Ppt Show Background PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Current Market Trends Inspiration PDF
This slide provides information about the current market trends that are increasing the importance of security monitoring and motivating the company to implement a security monitoring plan in the company and follow monitoring strategies. This is a modern security observation plan to eradicate cybersecurity risk and data breach current market trends inspiration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like increasing digitization of sensitive data, outsourcing, general data protection laws. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Security 30 60 90 Days Plan For Data Privacy Ppt PowerPoint Presentation File Gallery PDF
This slide represents the 30 60 90 days plan for data privacy, including hiring DPO Data Protection Officer, understanding the data and requirements, analyzing the risks. Create an editable Information Security 30 60 90 Days Plan For Data Privacy Ppt PowerPoint Presentation File Gallery PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Information Security 30 60 90 Days Pl is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Hurdles In Business Data Security In Trade Secret Ppt PowerPoint Presentation Pictures Master Slide PDF
Showcasing this set of slides titled hurdles in business data security in trade secret ppt powerpoint presentation pictures master slide pdf. The topics addressed in these templates are once trade secret is made public, it can be accessed by anyone, difficult to enforce than patent, level of protection granted to trade is generally considered weak and is different from country country. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
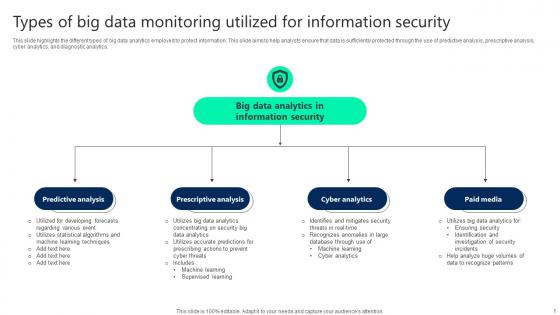
Types Of Big Data Monitoring Utilized For Information Security Elements pdf
This slide highlights the different types of big data analytics employed to protect information. This slide aims to help analysts ensure that data is sufficiently protected through the use of predictive analysis, prescriptive analysis, cyber analytics, and diagnostic analytics. Pitch your topic with ease and precision using this Types Of Big Data Monitoring Utilized For Information Security Elements pdf. This layout presents information on Predictive Analysis, Prescriptive Analysis, Cyber Analytics. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Cloud Network Security Training Programs Timeline Download PDF
The slide showcases training programs to improve individuals level of awareness about security measures designed to protect cloud based infrastructure and data. The elements are SANS, infosec, ISC, edX with their completion timeline and pricing package . Showcasing this set of slides titled Cloud Network Security Training Programs Timeline Download PDF. The topics addressed in these templates are Training Programs, Models Controls, Offense Defense Operations. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Dashboard For Data Security Risk Management Cybersecurity Risk Assessment Template PDF
This slide showcases dashboard that can help organization in managing the data security risks. Its key elements are enterprise risk, risk by objectives, data protection finding and overdue actions by status. Welcome to our selection of the Dashboard For Data Security Risk Management Cybersecurity Risk Assessment Template PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 parcent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
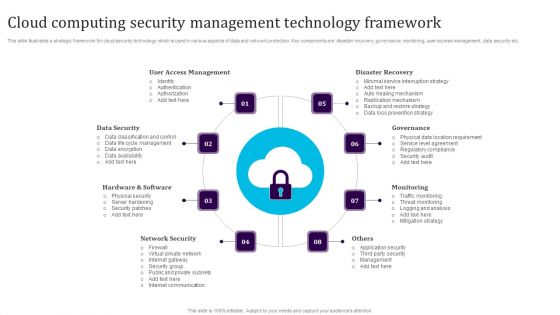
Cloud Computing Security Management Technology Framework Elements PDF
This slide illustrates a strategic framework for cloud security technology which is used in various aspects of data and network protection. Key components are disaster recovery, governance, monitoring, user access management, data security etc. Persuade your audience using this Cloud Computing Security Management Technology Framework Elements PDF. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including User Access Management, Data Security, Hardware And Software, Network Security, Monitoring, Governance. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
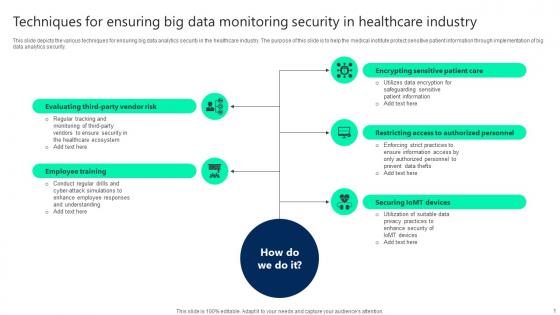
Techniques For Ensuring Big Data Monitoring Security In Healthcare Industry Infographics pdf
This slide depicts the various techniques for ensuring big data analytics security in the healthcare industry. The purpose of this slide is to help the medical institute protect sensitive patient information through implementation of big data analytics security. Pitch your topic with ease and precision using this Techniques For Ensuring Big Data Monitoring Security In Healthcare Industry Infographics pdf. This layout presents information on Employee Training, Securing Iomt Devices, Restricting Access. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Info Security Dispose Data And Equipment Properly Ppt PowerPoint Presentation File Model PDF
This is a info security dispose data and equipment properly ppt powerpoint presentation file model pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like data and hardware, protect it, organization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Applications Of Data Masking Internet Of Things Security Technology Topics Pdf
This slide represents the various applications of data masking technology that helps to protect sensitive data by providing a functional alternative for networks. The various categories include encryption, scrambling, nulling out, substitution, shuffling, etc. Showcasing this set of slides titled Applications Of Data Masking Internet Of Things Security Technology Topics Pdf The topics addressed in these templates are Encryption, Scrambling, Substitution, Shuffling All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Info Security Employee Awareness Training Budget For FY2022 Ppt PowerPoint Presentation File Graphics Download PDF
This slide represents the organizations staff training budget through a graph covering trainer name, date, and capability levels. Deliver an awe inspiring pitch with this creative info security employee awareness training budget for fy2022 ppt powerpoint presentation file graphics download pdf bundle. Topics like build and maintain, secure network and system, protect cardholder data, maintain a vulnerability, management program can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
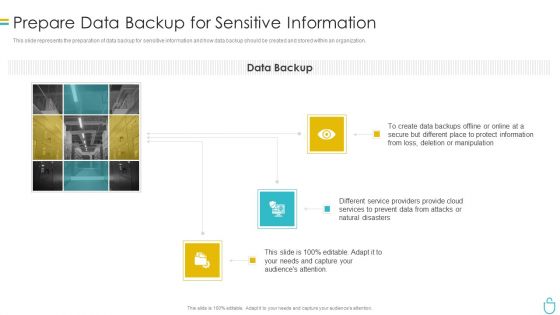
Information Security Prepare Data Backup For Sensitive Information Ppt Introduction PDF
This slide represents the preparation of data backup for sensitive information and how data backup should be created and stored within an organization. This is a information security prepare data backup for sensitive information ppt introduction pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like protect information, manipulation, services, natural disasters, secure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
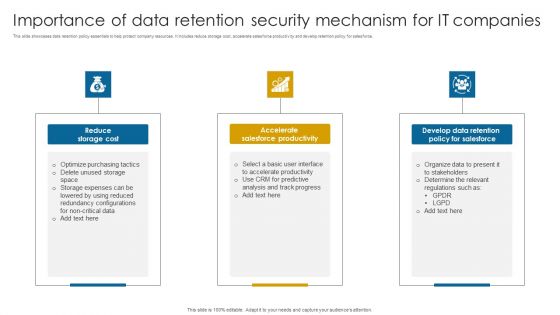
Importance Of Data Retention Security Mechanism For It Companies Professional PDF
This slide showcases data retention policy essentials to help protect company resources. It includes reduce storage cost, accelerate salesforce productivity and develop retention policy for salesforce.Presenting Importance Of Data Retention Security Mechanism For It Companies Professional PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Salesforce Productivity, Develop Data Retention, Determine Relevant. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cloud Security Checklist Networking Elements PDF
This slide defines the importance of network security under cloud security. It also shows how data should transfer over a network to protect it from malicious attacks. Presenting Cloud Security Checklist Networking Elements PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Network, Encrypt Critical Data. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Stock Photo 3d Blue Folder With Lock For Data Security PowerPoint Slide
This power point image template has been crafted with graphic of 3d blue folder and lock. This image contains the concept of data security. Use this image PPT for your technology and security related presentations.
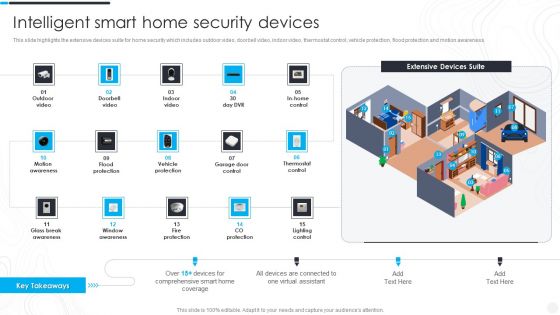
Security Camera System Company Profile Intelligent Smart Home Security Devices Portrait PDF
This slide highlights the extensive devices suite for home security which includes outdoor video, doorbell video, indoor video, thermostat control, vehicle protection, flood protection and motion awareness. Deliver an awe inspiring pitch with this creative Security Camera System Company Profile Intelligent Smart Home Security Devices Portrait PDF bundle. Topics like Flood Protection, Motion Awareness, Vehicle Protection can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
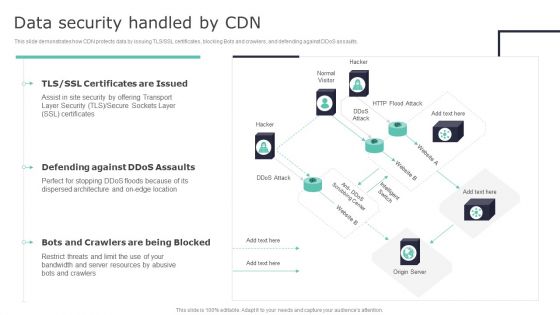
Deploying Content Distribution Network System Data Security Handled By CDN Sample PDF
This slide demonstrates how CDN protects data by issuing TLS or SSL certificates, blocking Bots and crawlers, and defending against DDoS assaults. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Deploying Content Distribution Network System Data Security Handled By CDN Sample PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates
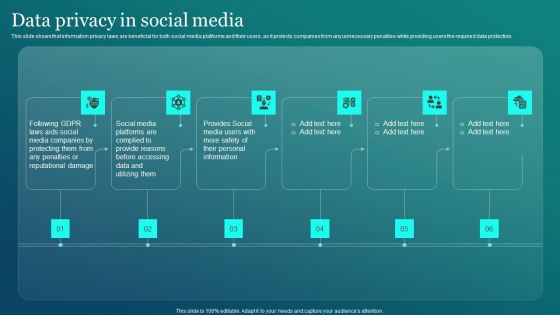
Information Security Data Privacy In Social Media Ppt PowerPoint Presentation File Portfolio PDF
This slide shows that information privacy laws are beneficial for both social media platforms and their users, as it protects companies from any unnecessary penalties while providing users the required data protection. Get a simple yet stunning designed Information Security Data Privacy In Social Media Ppt PowerPoint Presentation File Portfolio PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Information Security Data Privacy In Social Media Ppt PowerPoint Presentation File Portfolio PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
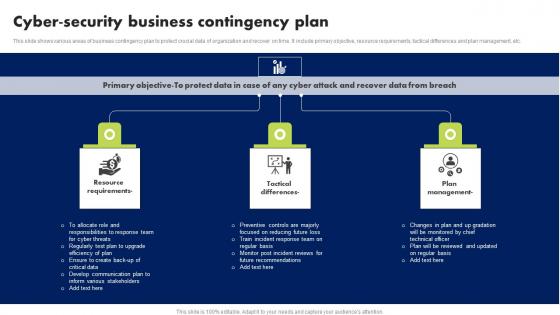
Cyber Security Business Contingency Plan Brochure Pdf
This slide shows various areas of business contingency plan to protect crucial data of organization and recover on time. It include primary objective, resource requirements, tactical differences and plan management, etc. Showcasing this set of slides titled Cyber Security Business Contingency Plan Brochure Pdf. The topics addressed in these templates are Resource Requirements, Tactical Differences, Plan Management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Data Security And Privacy With Biometric Ppt PowerPoint Presentation Gallery Slides PDF
Presenting data security and privacy with biometric ppt powerpoint presentation gallery slides pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including data security and privacy with biometric. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Security Symbol For Data Risk Vector Icon Ppt PowerPoint Presentation Pictures Guide PDF
Presenting security symbol for data risk vector icon ppt powerpoint presentation pictures guide pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including security symbol for data risk vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Cloud Data Security Vector Icon Ppt PowerPoint Presentation Diagram Templates PDF
Presenting cloud data security vector icon ppt powerpoint presentation diagram templates pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including cloud data security vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

 Home
Home