Data Protection
Integrating Data Privacy System Roadmap For Data Privacy Implementation Ppt Ideas Graphic Images
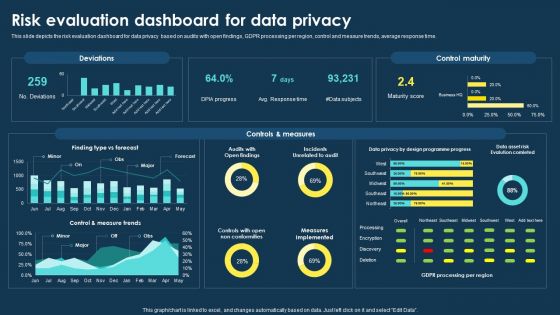
This slide depicts the purpose limitation principle, which states that you should be clear from the start about the reasons and intentions for collecting and processing data. Explore a selection of the finest Integrating Data Privacy System Risk Evaluation Dashboard For Data Privacy Ppt File Slides PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Integrating Data Privacy System Risk Evaluation Dashboard For Data Privacy Ppt File Slides PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Integrating Data Privacy System Introduction To Data Privacy Ppt Ideas Outline PDF
This slide provides a quick overview of data privacy, which refers to a persons capacity to control how much of their personal information is shared. This Integrating Data Privacy System Introduction To Data Privacy Ppt Ideas Outline PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Integrating Data Privacy System Introduction To Data Privacy Ppt Ideas Outline PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, dont wait, grab the presentation templates today.
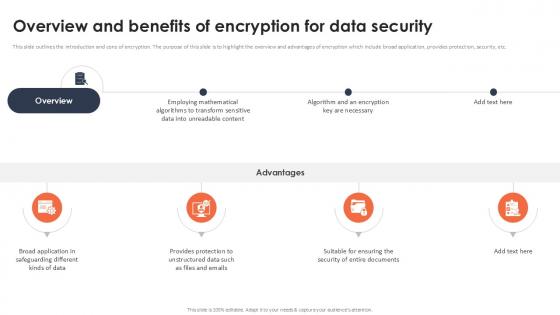
Overview And Benefits Of Encryption For Data Security Securing Your Data Ppt Powerpoint
This slide outlines the introduction and cons of encryption. The purpose of this slide is to highlight the overview and advantages of encryption which include broad application, provides protection, security, etc. Retrieve professionally designed Overview And Benefits Of Encryption For Data Security Securing Your Data Ppt Powerpoint to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
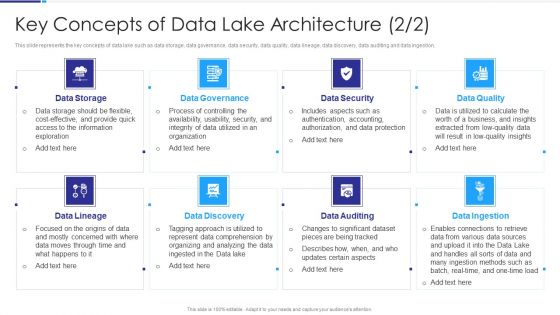
Data Lake Architecture Key Concepts Of Data Lake Architecture Infographics PDF
This slide represents the key concepts of data lake such as data storage, data governance, data security, data quality, data lineage, data discovery, data auditing and data ingestion. Presenting Data Lake Architecture Key Concepts Of Data Lake Architecture Infographics PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Data Storage, Data Governance, Data Security, Data Quality, Data Lineage, Data Discovery, Data Auditing, Data Ingestion. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Plan Useful Data Backup Schedule Ppt PowerPoint Presentation File Pictures PDF
The following slide showcases the monthly calendar for data backup to advance cybersecurity protection and loss of information. It mainly includes techniques such as fully and incremental data backup etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Plan Useful Data Backup Schedule Ppt PowerPoint Presentation File Pictures PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
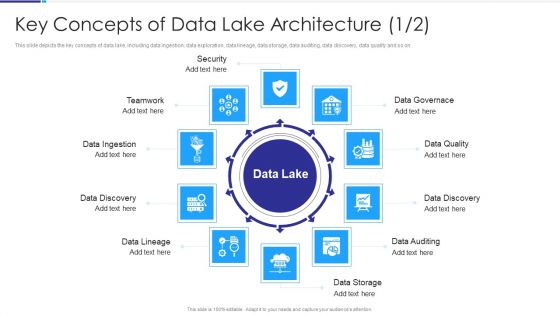
Key Concepts Of Data Lake Architecture Data Lake Architecture Ppt Pictures Shapes PDF
This slide depicts the key concepts of data lake, including data ingestion, data exploration, data lineage, data storage, data auditing, data discovery, data quality and so on. Presenting Key Concepts Of Data Lake Architecture Data Lake Architecture Ppt Pictures Shapes PDF to provide visual cues and insights. Share and navigate important information on ten stages that need your due attention. This template can be used to pitch topics like Security, Data Governace, Data Quality, Data Discovery, Data Auditing, Data Storage, Data Lineage, Data Discovery. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Major Types Of Data Security Breaches Data Breach Prevention Microsoft Pdf
This slide discusses the significant categories of information loss. The purpose of this slide is to describe several types of data security breaches. These include human error, device loss, cyberattacks, internal breaches, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Major Types Of Data Security Breaches Data Breach Prevention Microsoft Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Major Types Of Data Security Breaches Data Breach Prevention Microsoft Pdf.
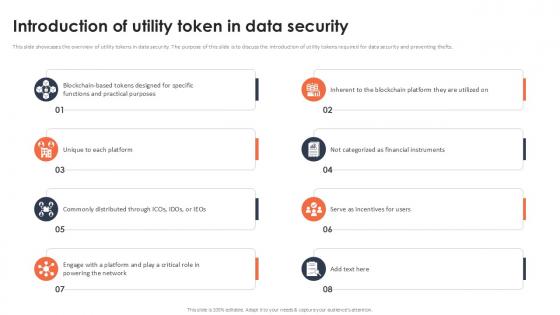
Introduction Of Utility Token In Data Security Securing Your Data Ppt Presentation
This slide showcases the overview of utility tokens in data security. The purpose of this slide is to discuss the introduction of utility tokens required for data security and preventing thefts. Explore a selection of the finest Introduction Of Utility Token In Data Security Securing Your Data Ppt Presentation here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Introduction Of Utility Token In Data Security Securing Your Data Ppt Presentation to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
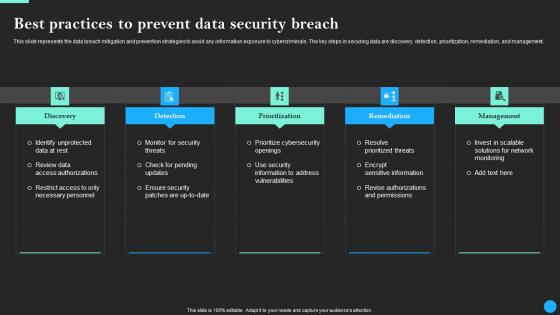
Best Practices To Prevent Data Security Breach Data Breach Prevention Information Pdf
This slide represents the data breach mitigation and prevention strategies to avoid any information exposure to cybercriminals. The key steps in securing data are discovery, detection, prioritization, remediation, and management. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Best Practices To Prevent Data Security Breach Data Breach Prevention Information Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Best Practices To Prevent Data Security Breach Data Breach Prevention Information Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today

Best Practices For Tokenization In Data Security Securing Your Data Ppt Example
The purpose of this slide is to highlight the best approaches for tokenization. The practices include broadening data tokenization scope, regularly revise policies, effective cyber security, etc. There are so many reasons you need a Best Practices For Tokenization In Data Security Securing Your Data Ppt Example The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Best Practices To Prevent Data Security Breach Data Fortification Strengthening Defenses
This slide represents the data breach mitigation and prevention strategies to avoid any information exposure to cybercriminals. The key steps in securing data are discovery, detection, prioritization, remediation, and management. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Best Practices To Prevent Data Security Breach Data Fortification Strengthening Defenses a try. Our experts have put a lot of knowledge and effort into creating this impeccable Best Practices To Prevent Data Security Breach Data Fortification Strengthening Defenses. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today
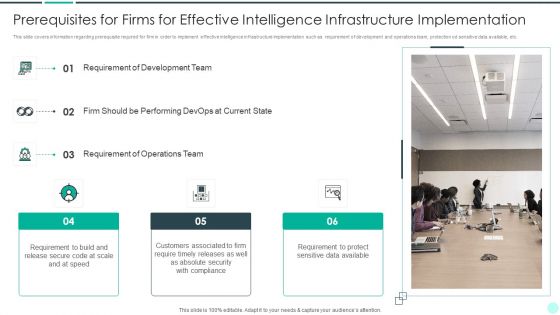
Executing Advance Data Analytics At Workspace Prerequisites For Firms Clipart PDF
This slide covers information regarding prerequisite required for firm in order to implement effective intelligence infrastructure implementation such as requirement of development and operations team, protection od sensitive data available, etc. This is a executing advance data analytics at workspace prerequisites for firms clipart pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like requirement, development, team, performing, operations. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Roadmap To Implement Tokenization For Data Security Securing Your Data Ppt Sample
This slide outlines the deployment for tokenization. The purpose of this slide is to highlight the steps that an organization should take while implementing tokenization including, generating tokens, identifying sensitive data, etc. Boost your pitch with our creative Roadmap To Implement Tokenization For Data Security Securing Your Data Ppt Sample Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
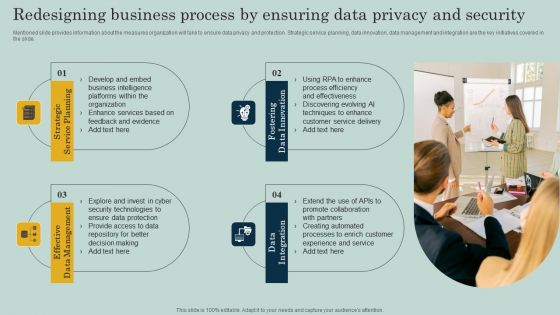
Redesigning Business Process By Ensuring Data Privacy And Security Ppt Infographics Objects PDF
Mentioned slide provides information about the measures organization will take to ensure data privacy and protection. Strategic service planning, data innovation, data management and integration are the key initiatives covered in the slide. Create an editable Redesigning Business Process By Ensuring Data Privacy And Security Ppt Infographics Objects PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Redesigning Business Process By Ensuring Data Privacy And Security Ppt Infographics Objects PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Tokenization Working Process For Data Security Securing Your Data Ppt Presentation
This slide represents the workflow of tokenization. The purpose of this slide is to highlight the process of tokenization which includes downloading a mobile payment application, generating tokens, etc. Find highly impressive Tokenization Working Process For Data Security Securing Your Data Ppt Presentation on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Tokenization Working Process For Data Security Securing Your Data Ppt Presentation for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now

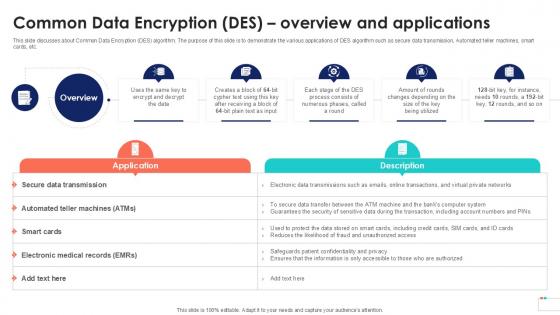
Common Data Encryption Des Cloud Data Security Using Cryptography Slides Pdf
This slide discusses about Common Data Encryption DES algorithm. The purpose of this slide is to demonstrate the various applications of DES algorithm such as secure data transmission, Automated teller machines, smart cards, etc. Welcome to our selection of the Common Data Encryption Des Cloud Data Security Using Cryptography Slides Pdf. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today

Overview Of Platform Tokenization In Data Security Securing Your Data Ppt Presentation
This slide discusses the introduction of first type tokenization in data security. The purpose of this slide is to highlight the overview of platform tokenization and how they gain security, transactional capacity, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Overview Of Platform Tokenization In Data Security Securing Your Data Ppt Presentation to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Overview Of Platform Tokenization In Data Security Securing Your Data Ppt Presentation

Immediate And Long Term Impact Of Data Security Breach Data Fortification Strengthening Defenses
This slide outlines the immediate and longstanding expenses associated with data breaches. The direct business costs include government fines, public relations costs, attorney fees, cybersecurity investigations, operational disruption, etc. Are you searching for a Immediate And Long Term Impact Of Data Security Breach Data Fortification Strengthening Defenses that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Immediate And Long Term Impact Of Data Security Breach Data Fortification Strengthening Defenses from Slidegeeks today.

Redesigning Business Process By Ensuring Data Privacy And Security Ppt Portfolio Elements PDF
Mentioned slide provides information about the measures organization will take to ensure data privacy and protection. Strategic service planning, data innovation, data management and integration are the key initiatives covered in the slide. Slidegeeks is here to make your presentations a breeze with Redesigning Business Process By Ensuring Data Privacy And Security Ppt Portfolio Elements PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
Common Data Encryption Des Overview Data Security In Cloud Computing Ppt Sample
This slide discusses about Common Data Encryption DES algorithm. The purpose of this slide is to demonstrate the various applications of DES algorithm such as secure data transmission, Automated teller machines, smart cards, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Common Data Encryption Des Overview Data Security In Cloud Computing Ppt Sample template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Common Data Encryption Des Overview Data Security In Cloud Computing Ppt Sample that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers

Characteristics Of Utility Tokenization In Data Security Securing Your Data Ppt Slide
This slide discusses the features of utility tokenization in data security. The purpose of this slide is to showcase the characteristics of utility tokenization which include service provided to user, purpose, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Characteristics Of Utility Tokenization In Data Security Securing Your Data Ppt Slide will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Salient Features Of Tokenization In Data Security Securing Your Data Ppt Sample
This slide outlines the key characteristics of tokenization in data security. The purpose of this slide is to highlight the properties of tokenization that include underlying representation, transferability, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Salient Features Of Tokenization In Data Security Securing Your Data Ppt Sample for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
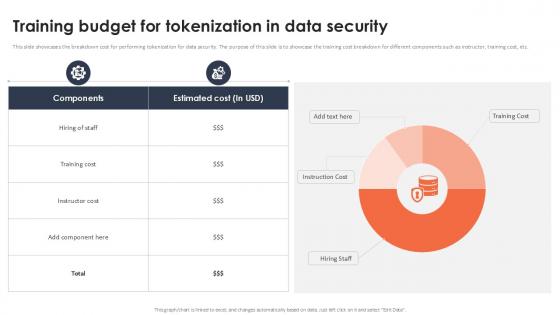
Training Budget For Tokenization In Data Security Securing Your Data Ppt Slide
This slide showcases the breakdown cost for performing tokenization for data security. The purpose of this slide is to showcase the training cost breakdown for different components such as instructor, training cost, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Training Budget For Tokenization In Data Security Securing Your Data Ppt Slide and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Data Breach Response Plan Secure Operations Data Breach Prevention Themes Pdf
This slide represents actions to be taken, the responsible team, the deadline, and tasks for securing operations after a data breach. The action items include secure physical areas, assemble expert team, consult with legal counsel, secure website and contact search engines, etc. Welcome to our selection of the Data Breach Response Plan Secure Operations Data Breach Prevention Themes Pdf. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today

Business Process Data Lineage Data Lineage Based On Persona Specific Use Cases Infographics Pdf
This slide describes the type of data lineage based on persona specific use cases and includes business, technical and design data lineage. The business data lineage encourages data exploration, validating datas authenticity and consistency, and so on. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Business Process Data Lineage Data Lineage Based On Persona Specific Use Cases Infographics Pdf can be your best option for delivering a presentation. Represent everything in detail using Business Process Data Lineage Data Lineage Based On Persona Specific Use Cases Infographics Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
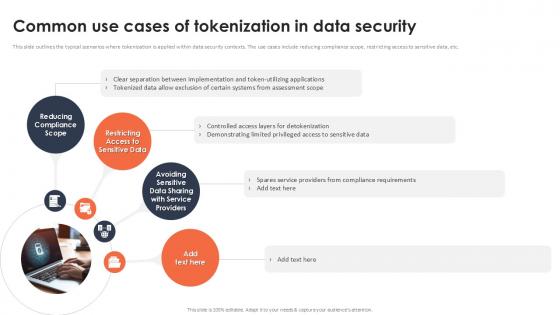
Common Use Cases Of Tokenization In Data Security Securing Your Data Ppt Sample
This slide outlines the typical scenarios where tokenization is applied within data security contexts. The use cases include reducing compliance scope, restricting access to sensitive data, etc. Slidegeeks is here to make your presentations a breeze with Common Use Cases Of Tokenization In Data Security Securing Your Data Ppt Sample With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first

Timeline To Implementation Tokenization In Data Security Securing Your Data Ppt Sample
This slide outlines the timeline for executing tokenization. The purpose of this slide is to showcase the different steps performed while implementing tokenization, including key management, monitoring, etc. Get a simple yet stunning designed Timeline To Implementation Tokenization In Data Security Securing Your Data Ppt Sample It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Timeline To Implementation Tokenization In Data Security Securing Your Data Ppt Sample can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
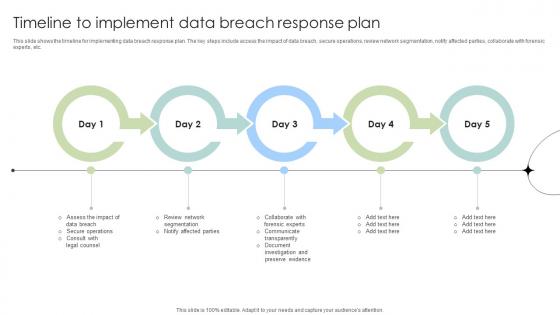
Timeline To Implement Data Breach Response Plan Data Fortification Strengthening Defenses
This slide shows the timeline for implementing data breach response plan. The key steps include access the impact of data breach, secure operations, review network segmentation, notify affected parties, collaborate with forensic experts, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Timeline To Implement Data Breach Response Plan Data Fortification Strengthening Defenses will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Data Breach Prevention Implementation Budget For Organization Data Fortification Strengthening Defenses
This slide represents the estimated and actual cost of implementing data breach prevention measures in an organization. The cost categories are security software and tools, employee training, security consultants, data encryption, and network security.If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Data Breach Prevention Implementation Budget For Organization Data Fortification Strengthening Defenses and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Big Data Architect Security Of Information In Big Data Graphics PDF
This slide represents the securing information in big data challenge of big data and solutions to this challenge, such as encryption data, separation of data, security monitoring in real-time, and so on.Deliver an awe inspiring pitch with this creative Big Data Architect Security Of Information In Big Data Graphics PDF bundle. Topics like Most Challenging, Securing Massive, Data Collections can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
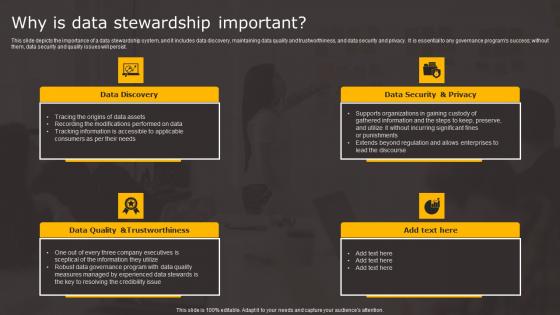
Data Stewardship In Business Processes Why Is Data Stewardship Important Download Pdf
This slide depicts the importance of a data stewardship system, and it includes data discovery, maintaining data quality and trustworthiness, and data security and privacy. It is essential to any governance programs success without them, data security and quality issues will persist. The Data Stewardship In Business Processes Why Is Data Stewardship Important Download Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
Data Stewardship In Business Processes Uses Of Data Stewardship Program Icons Pdf
This slide represents the uses of a data stewardship program that includes resolving any data or data related challenges, decreasing risks by security measures, improving data documentation, developing and using quality measures, and so on. Explore a selection of the finest Data Stewardship In Business Processes Uses Of Data Stewardship Program Icons Pdf here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Data Stewardship In Business Processes Uses Of Data Stewardship Program Icons Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Problems With Dark Data Accumulation Importance Of Unstructured Data Ppt Sample
This slide track the problems that are caused by dark data. The purpose of this slide is to explain how dark data can cause storage issues, hide valuable information, security issues, etc.Presenting this PowerPoint presentation, titled Problems With Dark Data Accumulation Importance Of Unstructured Data Ppt Sample, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Problems With Dark Data Accumulation Importance Of Unstructured Data Ppt Sample. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Problems With Dark Data Accumulation Importance Of Unstructured Data Ppt Sample that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Data Stewardship In Business Processes Responsibilities Data Steward Stewardship Introduction Pdf
This slide represents a data stewards responsibilities, including data cataloging, monitoring, data workflows, advocacy, and security. They are also responsible for maintaining appropriate data lineage that will help them and stakeholders. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Data Stewardship In Business Processes Responsibilities Data Steward Stewardship Introduction Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Data Stewardship In Business Processes Responsibilities Data Steward Stewardship Introduction Pdf today and make your presentation stand out from the rest

Data Integration Implementation Challenges And Solutions Data Integration Strategies For Business
This slide highlights various limitations of data integration. The purpose of this slide is to discuss the solutions to different challenges associated with data integration. These include security risks, delays in data delivery, resource-constrained, and their solutions. If you are looking for a format to display your unique thoughts, then the professionally designed Data Integration Implementation Challenges And Solutions Data Integration Strategies For Business is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Data Integration Implementation Challenges And Solutions Data Integration Strategies For Business and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
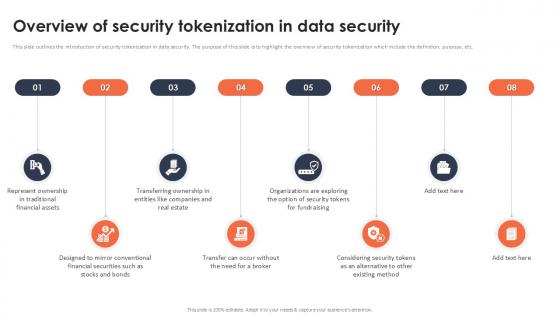
Overview Of Security Tokenization In Data Security Securing Your Data Ppt Sample
This slide outlines the introduction of security tokenization in data security. The purpose of this slide is to highlight the overview of security tokenization which include the definition, purpose, etc. This Overview Of Security Tokenization In Data Security Securing Your Data Ppt Sample from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Data Lake Development With Azure Cloud Software Key Concepts Of Data Lake Architecture Clipart PDF
This slide depicts the key concepts of data lake, including data ingestion, data exploration, data lineage, data storage, data auditing, data discovery, data quality and so on. This is a Data Lake Development With Azure Cloud Software Key Concepts Of Data Lake Architecture Clipart PDF template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security, Teamwork, Data Ingestion. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Tokenization In Payment Card Industry For Data Security Securing Your Data Ppt Example
This slide outlines the introduction of tokenization in payment card industry. The purpose of this slide is to showcase the process of tokenization in payment card industry to secure non sharable details of client. Slidegeeks is here to make your presentations a breeze with Tokenization In Payment Card Industry For Data Security Securing Your Data Ppt Example With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first

Checklist To Conduct Tokenization In Data Security Securing Your Data Ppt Example
This slide showcases the checklist for performing tokenization. The purpose of this slide is to highlight the actions performed while conducting regression testing, person responsible, status and comments for the same. Present like a pro with Checklist To Conduct Tokenization In Data Security Securing Your Data Ppt Example Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Overview And Process Of Tokenization In Data Security Securing Your Data Ppt Presentation
This slide highlights the introduction and phases of tokenization in data security. The purpose of this slide is to showcase the overview and process such as various assets, verification of ownership, transfer to blockchain, etc. Slidegeeks has constructed Overview And Process Of Tokenization In Data Security Securing Your Data Ppt Presentation after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Reasons For Conducting Tokenization In Data Security Securing Your Data Ppt Presentation
This slide outlines the rationale for implementing tokenization n data security. The reasons include minimizing risks, build customer trust, advancement in payment methods, etc. Do you know about Slidesgeeks Reasons For Conducting Tokenization In Data Security Securing Your Data Ppt Presentation These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
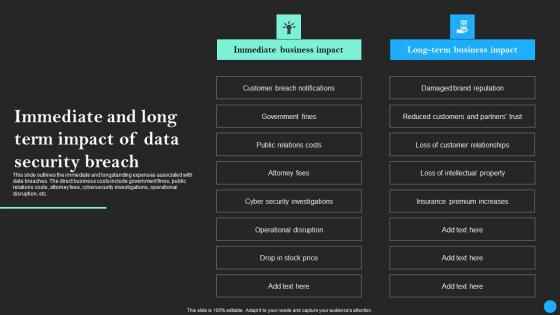
Immediate And Long Term Impact Of Data Security Breach Data Breach Prevention Topics Pdf
This slide outlines the immediate and longstanding expenses associated with data breaches. The direct business costs include government fines, public relations costs, attorney fees, cybersecurity investigations, operational disruption, etc. Retrieve professionally designed Immediate And Long Term Impact Of Data Security Breach Data Breach Prevention Topics Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
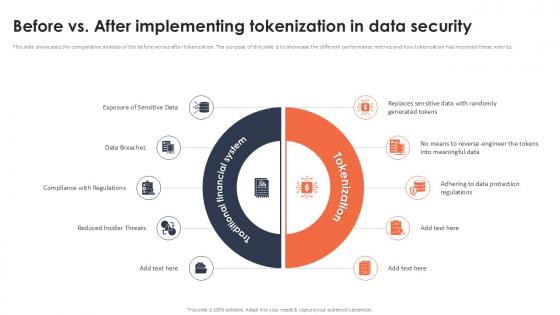
Before Vs After Implementing Tokenization In Data Security Securing Your Data Ppt Example
This slide showcases the comparative analysis of the before versus after tokenization. The purpose of this slide is to showcase the different performance metrics and how tokenization has improved these metrics. Want to ace your presentation in front of a live audience Our Before Vs After Implementing Tokenization In Data Security Securing Your Data Ppt Example can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

Data Security Benefits Of Adopting Tokenization Securing Your Data Ppt Presentation
This slide discusses the cons of tokenization. The purpose of this slide is to showcase the advantages of tokenization such as utilizing less resources, decreases risk, stimulates innovation, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Data Security Benefits Of Adopting Tokenization Securing Your Data Ppt Presentation and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Types Of Information Leaked In Data Breach Data Fortification Strengthening Defenses
This slide outlines the different forms of information loss in a data security breach. The major types of data leaked are financial data, medical or personal health information, Personally Identifiable Information, vulnerable and sensitive data, etc. Present like a pro with Types Of Information Leaked In Data Breach Data Fortification Strengthening Defenses. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Data Center Infrastructure Management IT Checklist We Follow For Data Center Security Formats PDF
This slide depicts the best practices for data center security based including identity and control data, classify sensitive data, map data flows, define groups, periodic audits, and reviews and integrate devsecops. Deliver an awe inspiring pitch with this creative data center infrastructure management it checklist we follow for data center security formats pdf bundle. Topics like identity and control data, classify sensitive data, map data flows, define groups, periodic audits and reviews, integrate devsecops can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
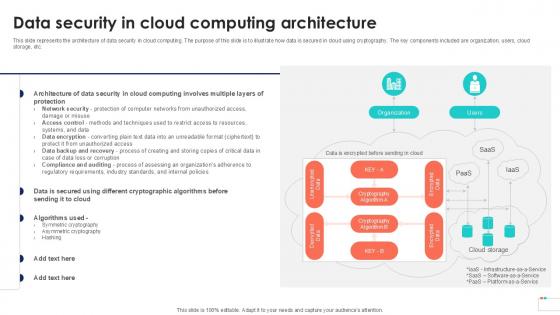
Data Security In Cloud Computing Data Security In Cloud Computing Ppt Example
This slide represents the architecture of data security in cloud computing. The purpose of this slide is to illustrate how data is secured in cloud using cryptography. The key components included are organization, users, cloud storage, etc. This modern and well-arranged Data Security In Cloud Computing Data Security In Cloud Computing Ppt Example provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Data Security In Cloud Computing Cloud Data Security Using Cryptography Formats Pdf
This slide talks about the key components of working of a cloud cryptography system. The purpose of this slide is to explain the main steps involved in functioning of cloud cryptography. The techniques explained are data in transit, data at rest and legal and regulatory issues. Retrieve professionally designed Data Security In Cloud Computing Cloud Data Security Using Cryptography Formats Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Data Lake Architecture What Are The Challenges Of Cloud Data Lake Ppt Outline Format PDF
This slide depicts the cloud data lake challenges such as data security, data swamp, on-premise data warehouse, and data governance. This is a Data Lake Architecture What Are The Challenges Of Cloud Data Lake Ppt Outline Format PDF template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Due To Security Concerns, Storing Structured Data, Data Governance, Data Lake. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
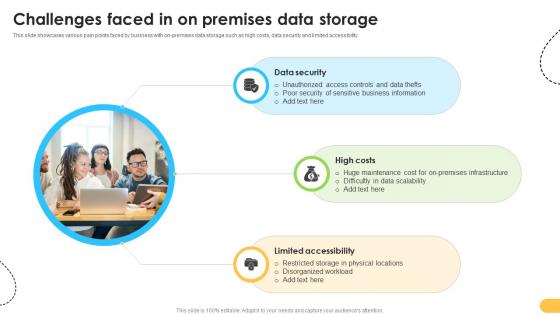
Challenges Faced In On Premises Data Storage Data Migration From On Premises
This slide showcases various pain points faced by business with on-premises data storage such as high costs, data security and limited accessibility. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Challenges Faced In On Premises Data Storage Data Migration From On Premises a try. Our experts have put a lot of knowledge and effort into creating this impeccable Challenges Faced In On Premises Data Storage Data Migration From On Premises. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today

Data Analytics Management Security Of Information In Big Data Summary PDF
This slide represents the securing information in big data challenge of big data and solutions to this challenge, such as encryption data, separation of data, security monitoring in real-time, and so on.Deliver an awe inspiring pitch with this creative Data Analytics Management Security Of Information In Big Data Summary PDF bundle. Topics like Securing Massive, Companies Frequently, Comprehending Preserving can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Data Breach Prevention Strategies For Enterprises Data Breach Prevention Slides Pdf
The purpose of this slide is to outline the data breach mitigation strategies for businesses. These include access control, encryption, web security solutions, network security, up-to-date software and hardware, preparation, training employees and users, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Data Breach Prevention Strategies For Enterprises Data Breach Prevention Slides Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Data Breach Prevention Strategies For Enterprises Data Breach Prevention Slides Pdf

Checklist For Responding To A Data Breach Attack Data Breach Prevention Microsoft Pdf
This slide represents the checklist for implementing a data breach response plan. The fundamental approaches are identify and isolate impacted systems or networks, perform a formal risk assessment, restore systems and address security flaws, notify affected parties, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Checklist For Responding To A Data Breach Attack Data Breach Prevention Microsoft Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
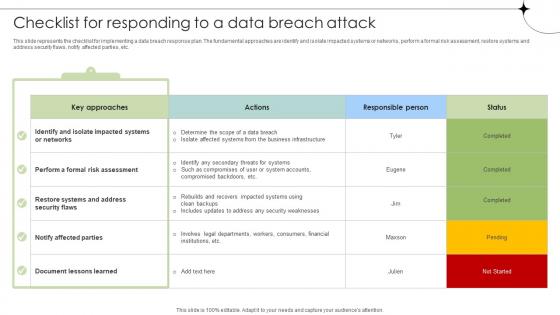
Checklist For Responding To A Data Breach Attack Data Fortification Strengthening Defenses
This slide represents the checklist for implementing a data breach response plan. The fundamental approaches are identify and isolate impacted systems or networks, perform a formal risk assessment, restore systems and address security flaws, notify affected parties, etc.From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Checklist For Responding To A Data Breach Attack Data Fortification Strengthening Defenses will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
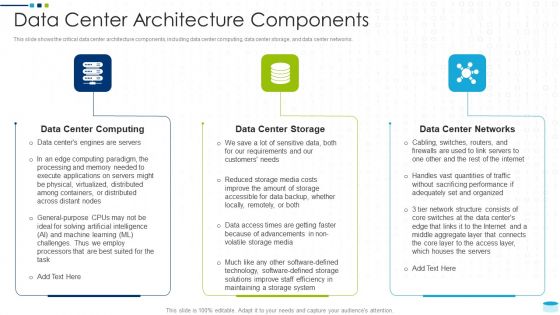
Data Center Infrastructure Management IT Data Center Architecture Components Professional PDF
This slide shows the critical data center architecture components, including data center computing, data center storage, and data center networks. This is a data center infrastructure management it data center architecture components professional pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like data center computing, data center storage, data center networksf. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
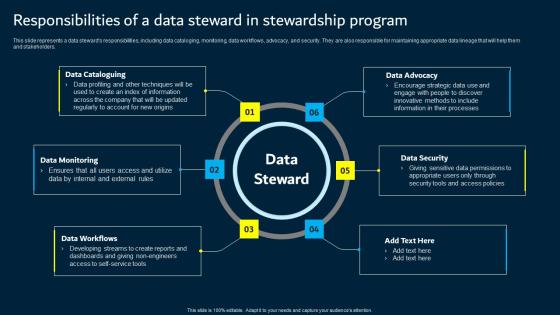
Responsibilities Of A Data Steward In Stewardship Program Data Custodianship Topics Pdf
This slide represents a data steward s responsibilities, including data cataloging, monitoring, data workflows, advocacy, and security. They are also responsible for maintaining appropriate data lineage that will help them and stakeholders. This modern and well arranged Responsibilities Of A Data Steward In Stewardship Program Data Custodianship Topics Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
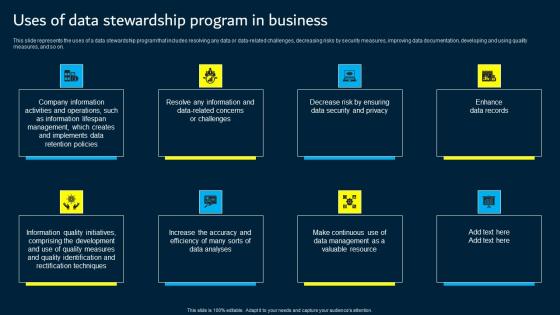
Uses Of Data Stewardship Program In Business Data Custodianship Structure Pdf
This slide represents the uses of a data stewardship program that includes resolving any data or data related challenges, decreasing risks by security measures, improving data documentation, developing and using quality measures, and so on. Do you know about Slidesgeeks Uses Of Data Stewardship Program In Business Data Custodianship Structure Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

Working Of Common Data Encryption Data Security In Cloud Computing Ppt Example
This slide represents the working flow of Common Data Encryption DES algorithm. The purpose of this slide is to outline the algorithm steps. This slide also explains the DES modes of operation, which include Digital Codebook, Cipher Block Chaining, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Working Of Common Data Encryption Data Security In Cloud Computing Ppt Example and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Working Of Common Data Encryption Cloud Data Security Using Cryptography Demonstration Pdf
This slide represents the working flow of Common Data Encryption DES algorithm. The purpose of this slide is to outline the algorithm steps. This slide also explains the DES modes of operation, which include Digital Codebook, Cipher Block Chaining, etc. Boost your pitch with our creativeWorking Of Common Data Encryption Cloud Data Security Using Cryptography Demonstration Pdf. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Data Stewardship In Business Processes Role Of Data Steward In A Company Background Pdf
This slide represents the role of a data steward in a company, including overseeing the information resources, maintaining data quality, addressing security and privacy related risks, and developing and keeping policies up to date. Make sure to capture your audiences attention in your business displays with our gratis customizable Data Stewardship In Business Processes Role Of Data Steward In A Company Background Pdf. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

 Home
Home