Data Protection
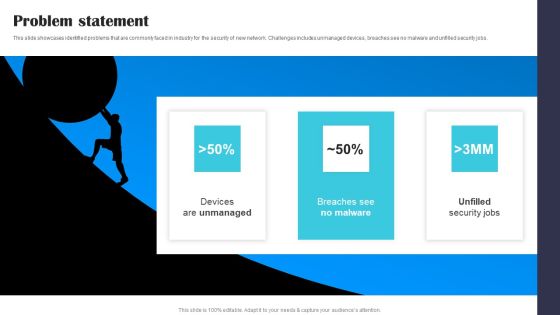
Security Software Company Investor Funding Pitch Deck Problem Statement Themes PDF
This slide showcases identified problems that are commonly faced in industry for the security of new network. Challenges includes unmanaged devices, breaches see no malware and unfilled security jobs. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Security Software Company Investor Funding Pitch Deck Problem Statement Themes PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

4 Step Arrow Cooperating Processes Business Action Plan PowerPoint Slides
We present our 4 step arrow cooperating processes business action plan PowerPoint Slides.Download and present our Arrows PowerPoint Templates because Our PowerPoint Templates and Slides are aesthetically designed to attract attention. We gaurantee that they will grab all the eyeballs you need. Download our Marketing PowerPoint Templates because You have gained great respect for your brilliant ideas. Use our PowerPoint Templates and Slides to strengthen and enhance your reputation. Download our Finance PowerPoint Templates because Our PowerPoint Templates and Slides are innately eco-friendly. Their high recall value negate the need for paper handouts. Download and present our Business PowerPoint Templates because You can Channelise the thoughts of your team with our PowerPoint Templates and Slides. Urge them to focus on the goals you have set. Present our Shapes PowerPoint Templates because You will get more than you ever bargained for. Use these PowerPoint slides for presentations relating to 3d, Abstract, Accounting, Arrow, Background, Bank, Bar, Benefit, Business, Calculation, Capital, Chart, Company, Connection, Corporate, Data, Design, Diagram, Directive, Earnings, Economy, Enterprise, Finance, Forecast, Graph, Growth, Illustration, Income, Increase, Information, Interest, Internet, Investment, Investor, Management, Market, Measure, Network, Office, Perspective, Plan, Price, Profit, Progress, Rise, Statistics, Technology, Vector, Wealth, World. The prominent colors used in the PowerPoint template are Yellow, Gray, Black. People tell us our 4 step arrow cooperating processes business action plan PowerPoint Slides provide great value for your money. Be assured of finding the best projection to highlight your words. Customers tell us our Benefit PowerPoint templates and PPT Slides are second to none. You can be sure our 4 step arrow cooperating processes business action plan PowerPoint Slides are designed to make your presentations professional. You can be sure our Bank PowerPoint templates and PPT Slides will generate and maintain the level of interest you desire. They will create the impression you want to imprint on your audience. Presenters tell us our 4 step arrow cooperating processes business action plan PowerPoint Slides will make you look like a winner. People tell us our Business PowerPoint templates and PPT Slides will impress their bosses and teams.

Table Of Contents For Information Systems Security And Risk Management Plan Brochure PDF
If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Table Of Contents For Information Systems Security And Risk Management Plan Brochure PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Cross Channel Marketing Plan Clients Estimated User Statistics After Using Mobile Applications And Social Networks Icons PDF
Presenting this set of slides with name cross channel marketing plan clients estimated user statistics after using mobile applications and social networks icons pdf. The topics discussed in these slide is estimated user statistics after using mobile applications and social networks. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cross Channel Marketing Plan For Clients User Statistics Before Using Mobile Applications And Social Networks Download PDF
Presenting this set of slides with name cross channel marketing plan for clients user statistics before using mobile applications and social networks download pdf. The topics discussed in these slide is user statistics before using mobile applications and social networks. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
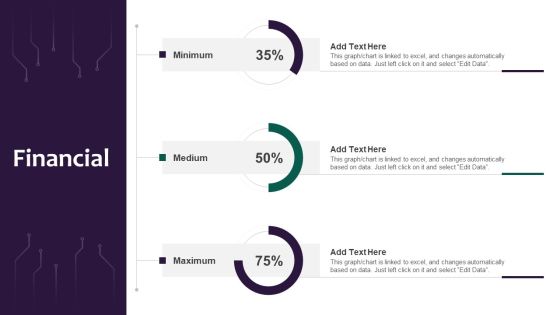
Information Systems Security And Risk Management Plan Financial Professional PDF
Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Information Systems Security And Risk Management Plan Financial Professional PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Information Systems Security And Risk Management Plan Financial Professional PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
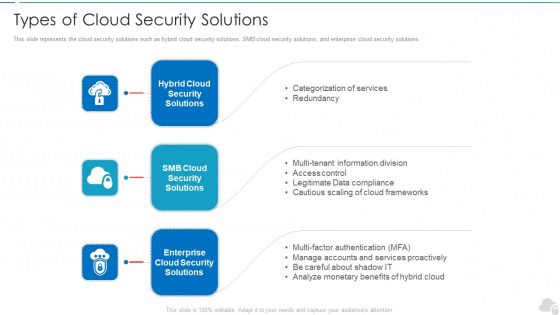
Types Of Cloud Security Solutions Cloud Computing Security IT Ppt Layouts Example PDF
This slide represents the cloud security solutions such as hybrid cloud security solutions, SMB cloud security solutions, and enterprise cloud security solutions. This is a types of cloud security solutions cloud computing security it ppt layouts example pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like hybrid cloud security solutions, smb cloud security solutions, enterprise cloud security solutions. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
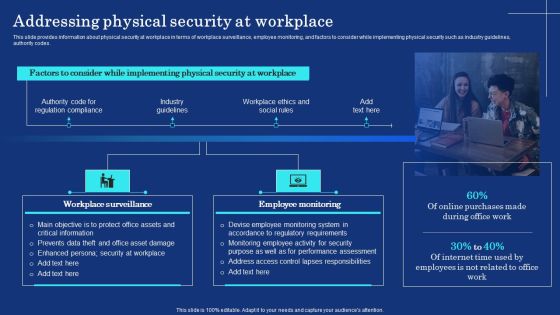
Organizational Assets Security Management Strategy Addressing Physical Security At Workplace Mockup PDF
This slide provides information about physical security at workplace in terms of workplace surveillance, employee monitoring, and factors to consider while implementing physical security such as industry guidelines, authority codes. Create an editable Organizational Assets Security Management Strategy Addressing Physical Security At Workplace Mockup PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Organizational Assets Security Management Strategy Addressing Physical Security At Workplace Mockup PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Role Of Technical Competence In Organizational Role Of Chief Information Security Officer Introduction PDF
This slide covers the role of chief information security officer which includes embed security information, stay informed, hire solid security staff, etc.This is a Role Of Technical Competence In Organizational Role Of Chief Information Security Officer Introduction PDF template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Become A Dependable, Identify C Level Team Members, Make Monthly Reports You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Systems Security And Risk Management Plan For Table Of Contents Mockup PDF
Welcome to our selection of the Information Systems Security And Risk Management Plan For Table Of Contents Mockup PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

Content Delivery Network Edge Server Reliability As Pillar Of CDN Design Information PDF
This slide depicts reliability as a pillar of CDN design which includes using the no single point of failure strategy most of the time. Deliver an awe inspiring pitch with this creative Content Delivery Network Edge Server Reliability As Pillar Of CDN Design Information PDF bundle. Topics like Systems, Redirect Traffic, Strategy can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Zero Trust Network Access System Use Cases Summary PDF
This slide outlines multiple use cases of zero-trust network access systems. The purpose of this slide is to showcase the main use cases of the ZTNA model, which are replacing VPN and MPLS connections, internal firewall replacement, securing remote access to private apps, limiting user access, and so on. Boost your pitch with our creative Zero Trust Network Access System Use Cases Summary PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Collection Of Information Technology Certifications Comptia A Certification Courses Details Icons PDF
This slide covers certification details about CompTIA A such as who should take these certifications, courses offered in this certification etc. This is a collection of information technology certifications comptia a certification courses details icons pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like systems administrator, network administrator, security administrator, designed. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
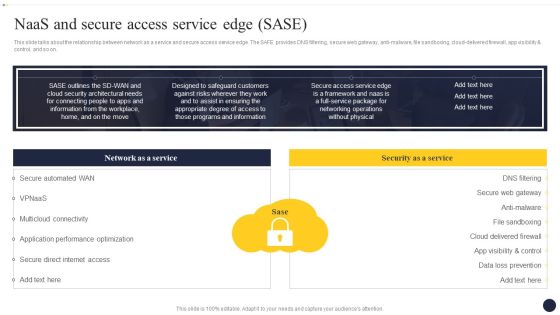
Integrating Naas Service Model To Enhance Naas And Secure Access Service Edge Sase Mockup PDF
This slide talks about the relationship between network as a service and secure access service edge. The SAFE provides DNS filtering, secure web gateway, anti-malware, file sandboxing, cloud-delivered firewall, app visibility and control, and so on. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Integrating Naas Service Model To Enhance Naas And Secure Access Service Edge Sase Mockup PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Integrating Naas Service Model To Enhance Naas And Secure Access Service Edge Sase Mockup PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Information Security Risk Evaluation Challenges And Solutions In Information Security Risk Management Template PDF
Deliver and pitch your topic in the best possible manner with this Information Security Risk Evaluation Challenges And Solutions In Information Security Risk Management Template PDF. Use them to share invaluable insights on Internal Vulnerabilities, Employee Awareness, Comprehensive Security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information And Technology Security Operations Ppt PowerPoint Presentation Complete Deck With Slides
This complete presentation has PPT slides on wide range of topics highlighting the core areas of your business needs. It has professionally designed templates with relevant visuals and subject driven content. This presentation deck has total of fifty nine slides. Get access to the customizable templates. Our designers have created editable templates for your convenience. You can edit the colour, text and font size as per your need. You can add or delete the content if required. You are just a click to away to have this ready made presentation. Click the download button now.
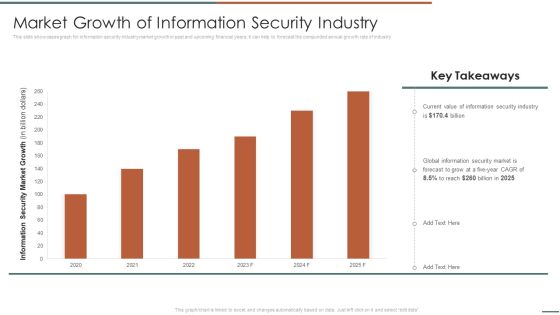
Information Security Risk Evaluation Market Growth Of Information Security Industry Infographics PDF
This slide showcases graph for information security industry market growth in past and upcoming financial years. It can help to forecast the compunded annual growth rate of industry .Deliver and pitch your topic in the best possible manner with this Information Security Risk Evaluation Market Growth Of Information Security Industry Infographics PDF. Use them to share invaluable insights on Information Security, Global Information, Security Market and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Content Delivery Network Edge Server Scattered Content Delivery Network Topology Formats PDF
This slide describes the scattered as a content delivery network topology its main focus is physical closeness and reducing the distance between PoPs. This is a Content Delivery Network Edge Server Scattered Content Delivery Network Topology Formats PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Geographic Regions, Content Delivery Network Topology. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Enhancing Information Technology With Strategic Information Security And Governance Icons PDF
This slide provides information regarding information security and governance management framework. The key elements include compliance, audit, response and recovery, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Enhancing Information Technology With Strategic Information Security And Governance Icons PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Defining Business Priorities To Ensure Information Security Ppt Pictures Gallery PDF
This slide illustrates the key business priorities of the organization such as efficient risk management, standardized incident management process to ensure information security. This is a defining business priorities to ensure information security ppt pictures gallery pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like reduce, risk, security, implement, communication. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Categories Of Online Certificate For Internet Authentication Ppt Portfolio Samples PDF
This slide showcases the different types of digital certificate for internet authentication. It includes types such as domain-validated SSL, organization and extended validation SSL and client certificates. Presenting Categories Of Online Certificate For Internet Authentication Ppt Portfolio Samples PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Domain Validated SSL, Organization Validated SSL, Extended Validation SSL. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Information Security Risk Evaluation Checklist For Information Security Risk Management Microsoft PDF
This slide showcases challenges involved in formulating risk management program for information security. It also shows solutions to tackle the challenges and impact of implementing them.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Checklist For Information Security Risk Management Microsoft PDF bundle. Topics like Identifying Potential, Defining Mitigation, Created Sales can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Security Risk Evaluation Financial Impact Of Information Security Attacks Background PDF
This slide showcases financial impact of different cyber security attacks on organizations. Its key elements are business disruption, information loss, revenue loss, equipment damage and total cost by attack type.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Financial Impact Of Information Security Attacks Background PDF bundle. Topics like Business Disruption, Cost By Consequence, Malware Attacks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Security Risk Evaluation Gap Assessment Of Organization Information Security Icons PDF
This slide showcases gap assessment of information security capabilities of organization. It also provides solutions to tackle the problems faced by company like, frequent malware attacks and lack of awareness among employees.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Gap Assessment Of Organization Information Security Icons PDF bundle. Topics like Frequent Malware, Phishing Attacks, Ransomware Attacks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information And Technology Security Operations Secops Dashboard To Track Vulnerabilities Information PDF
This slide provides information regarding the SecOps dashboard which is used to track and monitor various vulnerabilities identified. Deliver and pitch your topic in the best possible manner with this information and technology security operations secops dashboard to track vulnerabilities information pdf. Use them to share invaluable insights on assets, vulnerabilities, severity and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Comparative Analysis Of Technological Smart Homes Devices Information PDF
This side showcase the evaluation and evaluation of smart home devices for better automation, reduce human workload and increase home security. It include the devices such as router, system security, smart scale, smart vacuum and door locks. Showcasing this set of slides titled Comparative Analysis Of Technological Smart Homes Devices Information PDF. The topics addressed in these templates are Router, System Security, Smart Scale. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

IT Security Automation Systems Guide Domain Security Controls That Can Be Automated Sample PDF
This slide highlights the domain security controls that can be automated which includes security policy, asset management, human resources security, communications and operations management and access control domain. There are so many reasons you need a IT Security Automation Systems Guide Domain Security Controls That Can Be Automated Sample PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
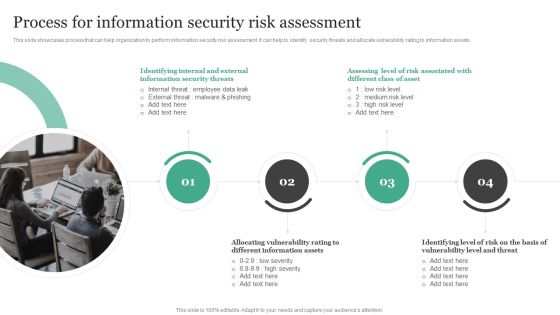
Process For Information Security Risk Assessment Information Security Risk Administration Demonstration PDF
This slide showcases process that can help organization to perform information security risk assessment. It can help to identify security threats and allocate vulnerability rating to information assets.Take your projects to the next level with our ultimate collection of Process For Information Security Risk Assessment Information Security Risk Administration Demonstration PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they all make your projects stand out from the rest.

Information Security Risk Evaluation Reporting Structure For Information Security Risk Management Guidelines PDF
This slide showcases plan that can help to communicate the major risks report on regular intervals. Its key components are risk, reported by, frequency, likelihood, criticality and impact.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Reporting Structure For Information Security Risk Management Guidelines PDF bundle. Topics like Phishing Attacks, Cross Attack, Security Vulnerabilities can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Secure Client Connection To Proxy And Secure Proxy Connection To Content Server Reverse Proxy For Load Balancing Rules PDF
This slide represents the secure client to proxy and secure proxy to the content server and how it can be used for the information that needs to be transmitted securely.Deliver and pitch your topic in the best possible manner with this Secure Client Connection To Proxy And Secure Proxy Connection To Content Server Reverse Proxy For Load Balancing Rules PDF. Use them to share invaluable insights on Server Outside, Between Server, Situation Works and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information Systems Security And Risk Management Plan Impact Of Information Security Loss On Organization Clipart PDF
There are so many reasons you need a Information Systems Security And Risk Management Plan Impact Of Information Security Loss On Organization Clipart PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Financial Impact Of Information Security Attacks Information Security Risk Administration Slides PDF
This slide showcases financial impact of different cyber security attacks on organizations. Its key elements are business disruption, information loss, revenue loss, equipment damage and total cost by attack type.Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Financial Impact Of Information Security Attacks Information Security Risk Administration Slides PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Financial Impact Of Information Security Attacks Information Security Risk Administration Slides PDF today and make your presentation stand out from the rest.
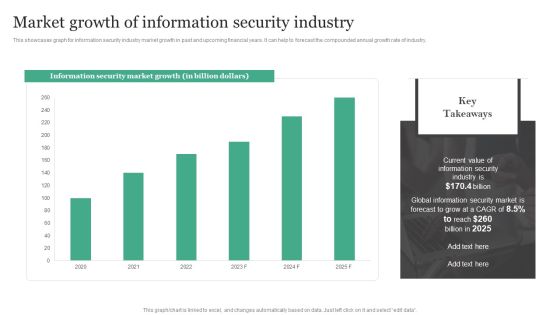
Market Growth Of Information Security Industry Information Security Risk Administration Rules PDF
This showcases graph for information security industry market growth in past and upcoming financial years. It can help to forecast the compounded annual growth rate of industry. This Market Growth Of Information Security Industry Information Security Risk Administration Rules PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Market Growth Of Information Security Industry Information Security Risk Administration Rules PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
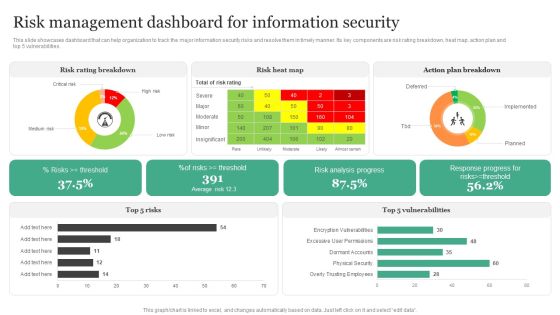
Risk Management Dashboard For Information Security Information Security Risk Administration Diagrams PDF
This slide showcases dashboard that can help organization to track the major information security risks and resolve them in timely manner. Its key components are risk rating breakdown, heat map, action plan and top 5 vulnerabilities.Create an editable Risk Management Dashboard For Information Security Information Security Risk Administration Diagrams PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Risk Management Dashboard For Information Security Information Security Risk Administration Diagrams PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Information Systems Security And Risk Management Plan Financial Impact Of Information Security Attacks Microsoft PDF
This slide showcases financial impact of different cyber security attacks on organizations. Its key elements are business disruption, information loss, revenue loss, equipment damage and total cost by attack type. Create an editable Information Systems Security And Risk Management Plan Financial Impact Of Information Security Attacks Microsoft PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Information Systems Security And Risk Management Plan Financial Impact Of Information Security Attacks Microsoft PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Cyber Security Risk Management Plan Information Security Risk Management Dashboard Sample PDF
Following slide covers information security risk management dashboard. It include KPIs such as risk analysis progress, percent risk, response progress for risks and number of risks encountered. Deliver an awe inspiring pitch with this creative cyber security risk management plan information security risk management dashboard sample pdf bundle. Topics like vulnerabilities, entities, action plan, risk analysis can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
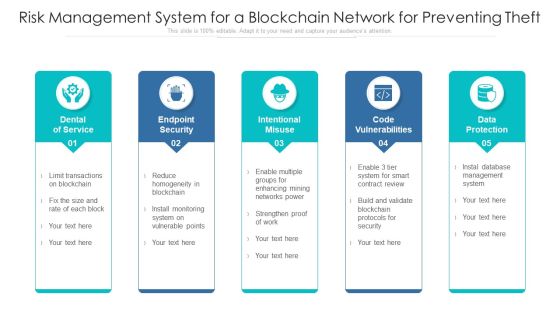
Risk Management System For A Blockchain Network For Preventing Theft Ppt PowerPoint Presentation Layouts Deck PDF
Presenting risk management system for a blockchain network for preventing theft ppt powerpoint presentation layouts deck pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including endpoint security, intentional misuse, code vulnerabilities. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Innovative Technology For Digital Network Connection Diagrams PDF
Showcasing this set of slides titled innovative technology for digital network connection diagrams pdf. The topics addressed in these templates are innovative technology for digital network connection. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Implementing Cyber Security Incident Management Table Of Contents Clipart PDF
Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Implementing Cyber Security Incident Management Table Of Contents Clipart PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Implementing Cyber Security Incident Management Table Of Contents Clipart PDF today and make your presentation stand out from the rest.

Cybersecurity Types Of Threats In Electronic Information Security Ppt Examples PDF
This slide depicts the main types of threats in cyber security, such as cybercrime, cyber terrorism, and cyberattacks to an organization and the purpose of each category threat. This is a cybersecurity types of threats in electronic information security ppt examples pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cyber crime, cyber terrorism, cyber crime. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Awareness Program Timeline Hacking Prevention Awareness Training For IT Security Professional PDF
This slide covers the security awareness implementation timeline for the organization cyber security training plan with conducting a simulated phishing exercise and system vendor risk assessment. This is a security awareness program timeline hacking prevention awareness training for it security professional pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like perform, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Developing 5G Wireless Cellular Network Discover Unique Features Heterogeneous Networks With 5G Information PDF
This slide provides details regarding unique features of 5G in terms of heterogeneous networks at premises, city and automobile through flexible framework to cater users coverage requirements. Deliver an awe inspiring pitch with this creative Developing 5G Wireless Cellular Network Discover Unique Features Heterogeneous Networks With 5G Information PDF bundle. Topics like Technologies, Networks Function Virtualization, Radio Access Network can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Security Risk Evaluation Framework For Information Security Risk Management Icons PDF
This slide showcases framework that can help organization to formulate plan for information security risk management. Its key elements are identify risks, analyze risks, evaluate and treat risks.Deliver and pitch your topic in the best possible manner with this Information Security Risk Evaluation Framework For Information Security Risk Management Icons PDF. Use them to share invaluable insights on Establish The Context, Identify Risks, Analyze Risks and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information Security Risk Evaluation Identifying Employees For Information Security Training Programme Background PDF
This slide showcases plan that can help organization to conduct training for employees for information security risk management. It will enable employees to monitor risks and resolve them in timely manner.Deliver and pitch your topic in the best possible manner with this Information Security Risk Evaluation Identifying Employees For Information Security Training Programme Background PDF. Use them to share invaluable insights on Threat Scanning, Malware Detection, Report Formulation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information Security Risk Evaluation Risk Management Dashboard For Information Security Summary PDF
This slide showcases dashboard that can help organization to track the major information security risks and resolve them in timely manner. Its key components are risk rating breakdown, heat map, action plan and top 5 vulnerabilities.Deliver and pitch your topic in the best possible manner with this Information Security Risk Evaluation Risk Management Dashboard For Information Security Summary PDF. Use them to share invaluable insights on Rating Breakdown, Vulnerabilities, Response Progress and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Identifying Employees For Information Security Training Programme Information Security Risk Administration Microsoft PDF
This slide showcases plan that can help organization to conduct training for employees for information security risk management. It will enable employees to monitor risks and resolve them in timely manner.If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Identifying Employees For Information Security Training Programme Information Security Risk Administration Microsoft PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Timeline For Information Security Risk Management Training Information Security Risk Administration Designs PDF
This slide showcases timeline that can help organization to conduct training for information security risk management programme. It also showcases weekly and step progress.From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Timeline For Information Security Risk Management Training Information Security Risk Administration Designs PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
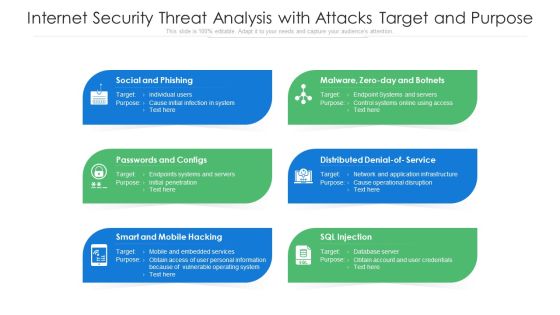
Internet Security Threat Analysis With Attacks Target And Purpose Ppt PowerPoint Presentation Pictures Structure PDF
Presenting internet security threat analysis with attacks target and purpose ppt powerpoint presentation pictures structure pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including social and phishing, passwords and configs, smart and mobile hacking. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Information Security Risk Evaluation Impact Of Information Security Loss On Organization Structure PDF
Presenting Information Security Risk Evaluation Impact Of Information Security Loss On Organization Structure PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Financial Organization, Loss Of Productivity, Reputational Loss. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Developing IT Security Strategy Kpis To Measure Information Security Risk Management Graphics PDF
This slide showcases KPIs that can help organization to measure the impact of cybersecurity risk management programme. It showcases estimated figures before and after implementation of plan. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Developing IT Security Strategy Kpis To Measure Information Security Risk Management Graphics PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Developing IT Security Strategy Kpis To Measure Information Security Risk Management Graphics PDF today and make your presentation stand out from the rest.

Information Systems Security And Risk Management Plan Process For Information Security Risk Assessment Formats PDF
This slide showcases process that can help organization to perform information security risk assessment. It can help identify security threats and allocate vulnerability rating to information assets. This modern and well arranged Information Systems Security And Risk Management Plan Process For Information Security Risk Assessment Formats PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
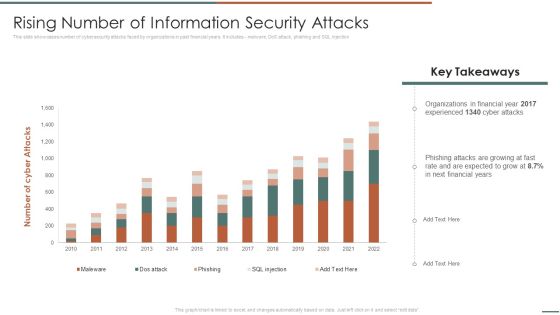
Information Security Risk Evaluation Rising Number Of Information Security Attacks Summary PDF
This slide showcases number of cybersecurity attacks faced by organizations in past financial years. It includes malware, DoS attack, phishing and SQL injection.Deliver and pitch your topic in the best possible manner with this Information Security Risk Evaluation Rising Number Of Information Security Attacks Summary PDF. Use them to share invaluable insights on Organizations In Financial, Experienced, Phishing Attacks and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Overview Of Cyber Security Awareness Course Ppt Ideas Styles PDF
The purpose of this slide is to provide a glimpse of the selected cyber security awareness course. It covers information about the instructor details, course content, attendees and learning outcome. Slidegeeks is here to make your presentations a breeze with Overview Of Cyber Security Awareness Course Ppt Ideas Styles PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Cyber Security Breache Response Strategy Table Of Contents Summary PDF
Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Cyber Security Breache Response Strategy Table Of Contents Summary PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Types Information Security Ppt PowerPoint Presentation Outline Clipart Cpb
Presenting this set of slides with name types information security ppt powerpoint presentation outline clipart cpb. This is an editable Powerpoint four stages graphic that deals with topics like types information security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Cloud Security Checklist Policies And Procedures Cloud Computing Security IT Ppt Layouts Show PDF
This slide depicts the policies and procedures of the cloud security checklist. It also represents how it is essential to create new and update the current policies in an organization. This is a cloud security checklist policies and procedures cloud computing security it ppt layouts show pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like implement policies, cloud security, organization, policy violation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
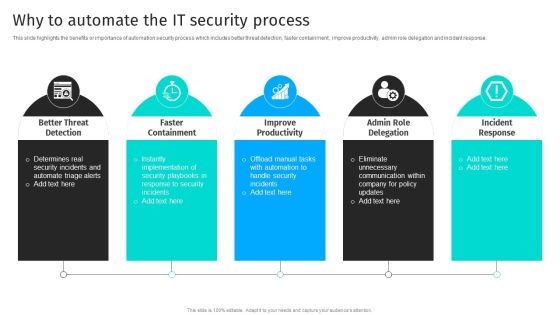
Security Automation To Analyze And Mitigate Cyberthreats Why To Automate The It Security Process Summary PDF
This slide highlights the benefits or importance of automation security process which includes better threat detection, faster containment, improve productivity, admin role delegation and incident response.Are you searching for a Security Automation To Analyze And Mitigate Cyberthreats Why To Automate The It Security Process Summary PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you ve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Security Automation To Analyze And Mitigate Cyberthreats Why To Automate The It Security Process Summary PDF from Slidegeeks today.

Agenda Of IT Security Risk Management Approach Introduction Infographics PDF
This is a Agenda Of IT Security Risk Management Approach Introduction Infographics PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Information Security, Business Agility, Risk Management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Security Risk Evaluation Vulnerability Rating For Risk Identification Guidelines PDF
This slide showcases table for allocating vulnerability rating to different class of information assets. It shows information about severity, vulnerability score and description.This is a Information Security Risk Evaluation Vulnerability Rating For Risk Identification Guidelines PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Drawback And Organization, Drawback Asset, Vulnerability Score. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Icon For Hotel Safety And Cyber Security Icon Professional PDF
Presenting Icon For Hotel Safety And Cyber Security Icon Professional PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Icon For Hotel, Safety Cyber, Security Icon This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

 Home
Home