Data Privacy

Corporate Security And Risk Management Addressing Various Ways To Handle Insider Cyber Threats Contd Guidelines PDF
This slide provides details regarding various ways to handle insider cyber threats in terms of active remediation implementation, deactivating orphaned user accounts, etc. Presenting corporate security and risk management addressing various ways to handle insider cyber threats contd guidelines pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like develop strict access management policies, deactivate orphaned user accounts, implement active remediation, investigate remote access policies. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Corporate Security And Risk Management Determine Staff Training Schedule For Skills Enhancement Inspiration PDF
The employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. Presenting corporate security and risk management determine staff training schedule for skills enhancement inspiration pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like advanced software training, advanced skills training. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Corporate Security And Risk Management Different Kinds Of Insider Digital Threats Themes PDF
This slide provides details regarding various kinds of insider digital threats such as malicious insider, negligent insider, third party insider, etc. Presenting corporate security and risk management different kinds of insider digital threats themes pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like malicious insider, negligent or careless insider, third party insider . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Corporate Security And Risk Management Threat Management Action Plan Risk Portrait PDF
The threat management action plan will help in keeping the track of various potential threats that are existing in the firm. The person responsible in handling the threats will keep track of the duration in which threat is resolved. Presenting corporate security and risk management threat management action plan risk portrait pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like threat identification, threat treatment . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Corporate Security And Risk Management Workplace Incident Summary Report Background PDF
This slide can be utilized to report any workplace incident. After filling this form it will be forwarded to Business unit safety director and HR representative. Presenting corporate security and risk management workplace incident summary report background pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like workplace incident summary report. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
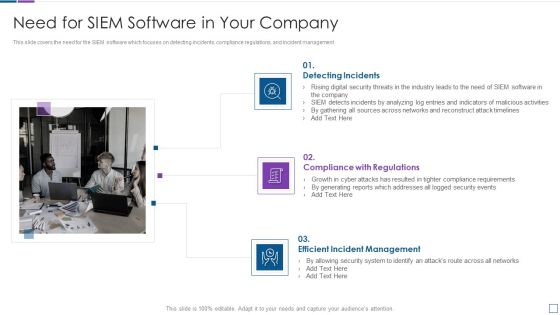
Real Time Assessment Of Security Threats Need For SIEM Software In Your Company Template PDF
This slide covers the need for the SIEM software which focuses on detecting incidents, compliance regulations, and incident management. Presenting real time assessment of security threats need for siem software in your company template pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like detecting incidents, compliance with regulations, efficient incident management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Phishing Scams And Attacks Assessment And Cyber Security Training Inspiration PDF
Mentioned slide showcases phishing awareness training program used to prevent cyber attacks. It provides detailed information about deploying phishing program within the organization, analyzing and preparing reports, developing training and education etc. Persuade your audience using this phishing scams and attacks assessment and cyber security training inspiration pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including analyze, develop, measure. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Risk Based Procedures To IT Security Communication Plan For Cyber Breaches Structure PDF
Mentioned slide portrays communication plan that company will use for effectively managing cyber breaches. Sections covered here are what to communicate, description, delivery method, frequency and responsible. Presenting Risk Based Procedures To IT Security Communication Plan For Cyber Breaches Structure PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Sprint Report, Delivery Method, Frequency Responsible. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security Hacker Hacking Of Our Social Media Accounts Formats PDF
This slide represents the hacking of a companys social media accounts such as Facebook and Instagram by hackers in 2019 and the amount of money by running scam ads.Presenting IT Security Hacker Hacking Of Our Social Media Accounts Formats PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Scammers Gained, Business Manager, Altered The Password. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security Hacker Preventing Measures For Social Media Accounts Diagrams PDF
This slide represents the preventing measures for social media accounts, including setting up login notifications, updating social media login credentials, using anti-malware software, and reviewing company policies.Presenting IT Security Hacker Preventing Measures For Social Media Accounts Diagrams PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Login Notifications, Malware Software, Policies Regularly. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
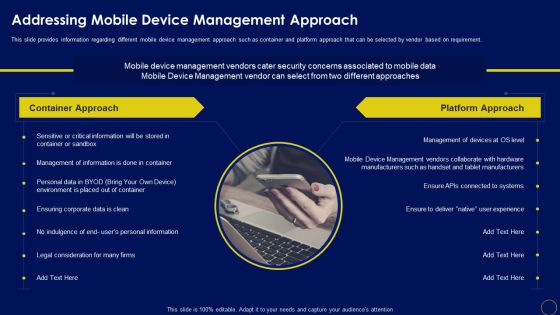
Addressing Mobile Device Management Business Mobile Device Security Management Download PDF
This slide provides information regarding different mobile device management approach such as container and platform approach that can be selected by vendor based on requirement. This modern and well-arranged Addressing Mobile Device Management Business Mobile Device Security Management Download PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

KYC Transaction Monitoring System Business Security Real Time Atm Fraud And Crime Detection Themes PDF
This slide illustrates real time crime and fraud detection process flow for ATMS. It provides information about repeated transactions, counterfeit cards, hacked ATMS, skimmer, terminal, point of sale, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give KYC Transaction Monitoring System Business Security Real Time Atm Fraud And Crime Detection Themes PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable KYC Transaction Monitoring System Business Security Real Time Atm Fraud And Crime Detection Themes PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Ensuring Mobile Device Compliance And Policy Enforcement Business Mobile Device Security Formats PDF
This slide provides information regarding mobile device compliance and policy enforcement with automated device setup, dynamic workflows and policies, etc.Want to ace your presentation in front of a live audience Our Ensuring Mobile Device Compliance And Policy Enforcement Business Mobile Device Security Formats PDF can help you do that by engaging all the users towards you.. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

KYC Transaction Monitoring System Business Security Analyzing Impact Of Money Laundering Guidelines PDF
This slide analyzing impact of money laundering on economy. It provides information about placement, layering, integration, global GDP, income distribution, tax revenues, growth rate, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable KYC Transaction Monitoring System Business Security Analyzing Impact Of Money Laundering Guidelines PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

CRM Implementation Strategy Implementation Add Roles And Enable Security Rules PDF
This slide highlights the setting roles of new users and assigning roles, also highlights the enable security with field level and integration of lead generation with emails for contact management.Deliver an awe inspiring pitch with this creative CRM Implementation Strategy Implementation Add Roles And Enable Security Rules PDF bundle. Topics like Enable Security, Double Authentication, Prevent Unauthorized can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Manpower Corporate Security Business Profile Employees Rules And Regulations Formats PDF
This slide highlights the security guard company rules and regulations which showcases In and out time, note visitor name, and wear uniform at working hours. Deliver an awe inspiring pitch with this creative Manpower Corporate Security Business Profile Employees Rules And Regulations Formats PDF bundle. Topics like Security, Employees Rules And Regulations can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Roadmap Of Digital Risk Assessment Asset And Security Policy Development Sample PDF
The following slide highlights the roadmap of cyber security asset assessment and security policy development for organisation to draft system security policy which describes assessment, build, select, deployment, awareness and audit. Persuade your audience using this Roadmap Of Digital Risk Assessment Asset And Security Policy Development Sample PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Assessment, Build, Deployment, Select, Audit, Awareness. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Grid Computing Applications Introduction To Grid Computing Security Model Rules PDF
This slide represents the introduction to the grid computing security model, including the security components such as authentication and delegation. The security model consists of intrusion detection, anti-virus management, policy management, user management, key management, and so on. Make sure to capture your audiences attention in your business displays with our gratis customizable Grid Computing Applications Introduction To Grid Computing Security Model Rules PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
Grid Computing For High Performance Solutions Introduction To Grid Computing Security Model Icons PDF
This slide represents the introduction to the grid computing security model, including the security components such as authentication and delegation. The security model consists of intrusion detection, anti-virus management, policy management, user management, key management, and so on. There are so many reasons you need a Grid Computing For High Performance Solutions Introduction To Grid Computing Security Model Icons PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Strategies We Will Implement To Make Security Awareness Training Interactive Brochure PDF
The purpose of this slide is to exhibit variety of strategies which can be used to engage employees in the security awareness training plan. The strategies highlighted in the slide are gamification, personalization, high-quality content and variety. This is a Strategies We Will Implement To Make Security Awareness Training Interactive Brochure PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Gamification, Personalization, High Quality. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
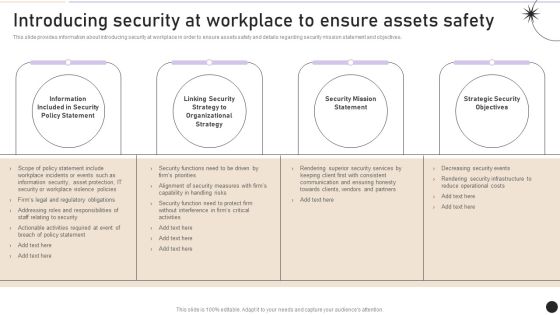
Introducing Security At Workplace To Ensure Assets Safety Graphics PDF
This slide provides information about introducing security at workplace in order to ensure assets safety and details regarding security mission statement and objectives. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Introducing Security At Workplace To Ensure Assets Safety Graphics PDF can be your best option for delivering a presentation. Represent everything in detail using Introducing Security At Workplace To Ensure Assets Safety Graphics PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Deploying Cyber Security Incident Response Administration Comparative Analysis Of Web Application Graphics PDF
This slide represents the comparison between various web application firewall products based on multiple parameters to help organization select the best web application firewall for their organization. It includes comparison between WAF products based on features such as cookie tampering etc. This Deploying Cyber Security Incident Response Administration Comparative Analysis Of Web Application Graphics PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Deploying Cyber Security Incident Response Administration Comparative Analysis Of Web Application Graphics PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today.

Strategies To Mitigate Cyber Security Risks Cybersecurity Contingency Plan Business Impact Analysis Brochure PDF
Presenting this set of slides with name strategies to mitigate cyber security risks cybersecurity contingency plan business impact analysis brochure pdf. This is a three stage process. The stages in this process are determining vital it resources, determining issues impacts and acceptable outage time, assign recovery priorities, settlement agreements, litigation files, department file cabinets. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
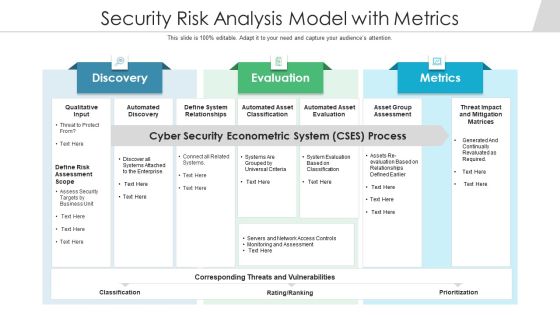
Security Risk Analysis Model With Metrics Ppt PowerPoint Presentation Outline Designs PDF
Persuade your audience using this security risk analysis model with metrics ppt powerpoint presentation outline designs pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including automated discovery, define system relationships, automated asset classification. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Annual Premium Comparison Worksheet Of Homeowners Security Diagrams PDF
This slide shows worksheet representing comparison of insurance premium of different firms for insured or customer to help in making decision . it includes various facilities provided by insurance firms. Showcasing this set of slides titled Annual Premium Comparison Worksheet Of Homeowners Security Diagrams PDF. The topics addressed in these templates are Purchase Price, Insurance, Medical Payments. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
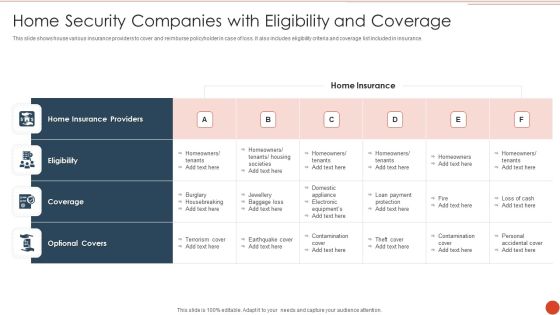
Home Security Companies With Eligibility And Coverage Infographics PDF
This slide shows house various insurance providers to cover and reimburse policyholder in case of loss. It also includes eligibility criteria and coverage list included in insurance. Showcasing this set of slides titled Home Security Companies With Eligibility And Coverage Infographics PDF. The topics addressed in these templates are Home Insurance Providers, Home Insurance, Loan Payment Protection. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

HR Security Training And Wellbeing KPI Dashboard Professional PDF
This slide showcases dashboard for HR safety training and wellbeing. This template aims to improve employee working efficiency and enhance working conditions to foster their working efficiency. It provides details regarding incidents reported, training programs implemented to reduce number of incidents, cost of providing training and level of employee satisfaction with training. Showcasing this set of slides titled HR Security Training And Wellbeing KPI Dashboard Professional PDF. The topics addressed in these templates are Severity, Injury Consequence, Employee Satisfaction Training. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Need Of Implementing HR Security Programs At Workplace Pictures PDF
This slide highlights the need of importance of workplace safety in an organization. This template aims to provide details regarding workplace safety to increase productivity, reduce turnover rates, safe working conditions, reduction in risk factors, avoid loss of resources, reduction in expenses, foster employee wellbeing and follow legal guidelines, etc. Showcasing this set of slides titled Need Of Implementing HR Security Programs At Workplace Pictures PDF. The topics addressed in these templates are Productivity, Working Environment, Absenteeism. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Workplace Risk Mitigation Strategies For HR Security Portrait PDF
This slide highlights techniques for minimizing risk factors in the workplace. the purpose of this template is to employ effective strategies for ensuring workforce safety eventually enhancing overall productivity and efficiency. It also provides details regarding the status of performance along with insights. Showcasing this set of slides titled Workplace Risk Mitigation Strategies For HR Security Portrait PDF. The topics addressed in these templates are Risk Assessment Management, Safety Training And Education, Compliance Regulations. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Threat Security Before And After Artificial Intelligence Formats PDF
This slide describes the four main cyber risks that currently threaten our digital world, as well as the difference between traditional methods and newer, AI based methods. It includes cyber threats such as malware, DDoS, IOT and endpoints and social engineering. Showcasing this set of slides titled Threat Security Before And After Artificial Intelligence Formats PDF. The topics addressed in these templates are Malware, Distributed Denial Service, Social Engineering. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Various Practices To Protect Functional Technology System Information PDF
Showcasing this set of slides titled various practices to protect functional technology system information pdf. The topics addressed in these templates are inventory software, awareness training, security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Security Functioning Centre Facilities Offered By Successful Implementation Infographics PDF
This slide portrays information regarding the various facilities that are offered by successful implementation of SecOps in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. Presenting security functioning centre facilities offered by successful implementation infographics pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like risk mitigation, investigations, employees. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Determine New Roles Pivotal For Successful Devops Security Designs PDF
This slide provides information regarding the new roles considered as pivotal for successful DevOps in terms of DevOps evangelist, release manager, automation architect integration specialist. Presenting determine new roles pivotal for successful devops security designs pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like manager, management, coordination. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Addressing Mobile Device Management Mobile Device Security Management Slides PDF
This slide provides information regarding different mobile device management approach such as container and platform approach that can be selected by vendor based on requirement. Presenting Addressing Mobile Device Management Mobile Device Security Management Slides PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Corporate Owned, Personally Enabled, Equipment Personal. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Resolving Integrate IOT Security Challenges With Blockchain Platform Structure PDF
This slide covers various challenges and issues faced while using IoT applications. The purpose of this slide is to provide information about various challenges and proposed solutions. It includes challenges such as RPL routing attack, cost and capacity constraints, cloud server downtime along with description and blockchain solutions. Pitch your topic with ease and precision using this Resolving Integrate IOT Security Challenges With Blockchain Platform Structure PDF. This layout presents information on Iot Challenges, Blockchain Solutions, Cloud Server Downtime. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Comparative Assessment Of Online Security Management Software Summary PDF
This slide showcases comparative assessment of various digital safety management software used to boost performance across organization. It provides information regarding software, features, price, free trail and user ratings. Pitch your topic with ease and precision using this Comparative Assessment Of Online Security Management Software Summary PDF. This layout presents information on Price, Absence Management System, Softwares. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Automated Security Awareness Platform And Cost Graphics PDF
This slide covers the Automated training programs for security awareness that will help educate workers to act appropriately, even when introduced to entirely new risks.Presenting automated security awareness platform and cost graphics pdf. to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like automated learning management, actionable reporting, available anytime. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Determine Focus Areas To Implement Security Operations Centre Diagrams PDF
This slide portrays information regarding the focus areas that are need to be addressed for effective implementation of security operations center. The focus areas are such as digital forensics and control, risk monitoring and management, etc. Deliver an awe inspiring pitch with this creative determine focus areas to implement security operations centre diagrams pdf bundle. Topics like digital forensics and control, risk monitoring and management, system and network administration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
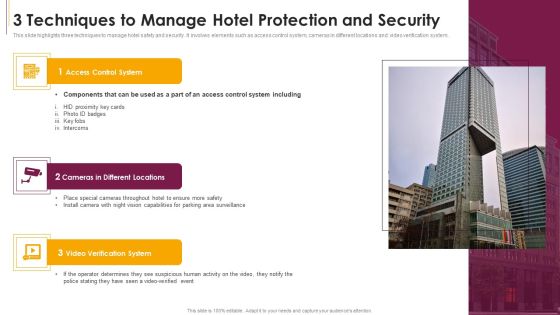
3 Techniques To Manage Hotel Protection And Security Sample PDF
This slide highlights three techniques to manage hotel safety and security. It involves elements such as access control system, cameras in different locations and video verification system.Presenting 3 Techniques To Manage Hotel Protection And Security Sample PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Access Control System, Cameras In Different Locations, Verification System This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
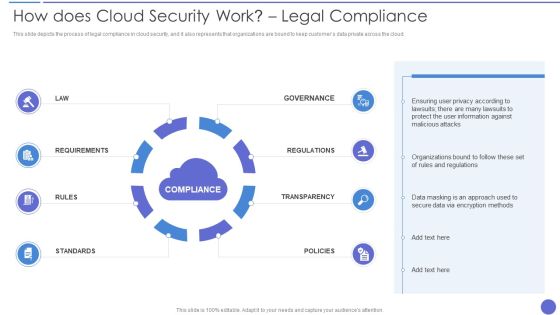
How Does Cloud Security Work Legal Compliance Background PDF
This slide represents the identity and access management in a cloud security system that is based on authentication, authorization, access control, and central user repository. Presenting How Does Cloud Security Work Legal Compliance Background PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Authorization, Authentication, Access Management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security And Surveillance Company Profile Business Development Strategy Icons PDF
This slide highlights the security company channel expansion strategy which showcases strategies for retail, multifamily and professional channels including instore lead generation and robust product offerings.Presenting Security And Surveillance Company Profile Business Development Strategy Icons PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Professional Channels, National Operations, Remove Insurance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
IT Security Hacker Dashboard For Threat Tracking Rules PDF
This slide depicts the dashboard for threat tracking through cyber security measures and ethical hackers by covering monthly threat status, current risk status, threat-based on the role, threats by owners, risk by threats, and threat report.Deliver an awe inspiring pitch with this creative IT Security Hacker Dashboard For Threat Tracking Rules PDF bundle. Topics like Threat Dashboard, Loss Of Information, Regulations And Contracts can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Impact Of Cyber Security Breach Lost Revenue Portrait PDF
The purpose of this slide is to showcase the consequences of cyber security breach on the company revenue. It provides information about the revenue lost over different months caused by different cyber attack such as malware, social engineering attack, business email compromise etc. Deliver an awe inspiring pitch with this creative Impact Of Cyber Security Breach Lost Revenue Portrait PDF bundle. Topics like Social Engineering, Password Attack, Ransomware can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
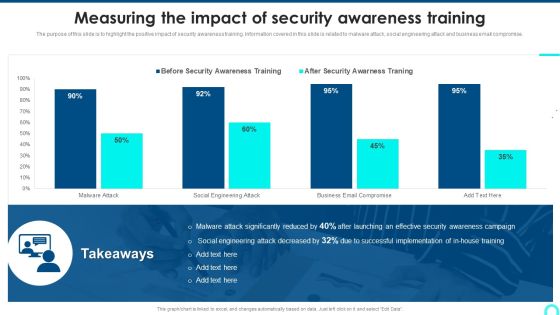
Measuring The Impact Of Security Awareness Training Structure PDF
The purpose of this slide is to highlight the positive impact of security awareness training. Information covered in this slide is related to malware attack, social engineering attack and business email compromise. Deliver and pitch your topic in the best possible manner with this Measuring The Impact Of Security Awareness Training Structure PDF. Use them to share invaluable insights on Attack Significantly, Awareness Campaign, Social Engineering and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security Agency Business Profile Case Study Elements PDF
This slide highlights the case study of security guard company which includes key problems robberies and theft, with integrated solution and key benefits. Presenting Security Agency Business Profile Case Study Elements PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like The Problem, Solution, Benefits. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Agency Business Profile Our Global Presence Themes PDF
This slide highlights the security guard and manpower services company global presence through world map. It includes the presence in developed and emerging markets. Presenting Security Agency Business Profile Our Global Presence Themes PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Developed Markets, Customers, Employees. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Manpower Corporate Security Business Profile Our Business Approach Introduction PDF
This slide highlights the business approach of security company which includes strategic planning, human resource management, participatory management and productivity management. Presenting Manpower Corporate Security Business Profile Our Business Approach Introduction PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Hr Management, Participatory Management, Productivity Management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Crisis Communication Process Framework Icons PDF
This slide showcases a model of crisis communication process for cyber security. It includes identify issues, set goals, and objectives, community and constraints, stakeholder assessment, communication and engagement tools, implement strategy and evaluate and follow up. Presenting Cyber Security Crisis Communication Process Framework Icons PDF to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including Implement Strategy, Identify Community, Set Goals And Objectives. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Workflow For Managing Cyber Security Incident Response Team Brochure PDF
This slide covers workflow for cyber security incident response team. It involves team members such as incident handler, forensic analyst, network analyst, incident coordinator and analyst. Presenting Workflow For Managing Cyber Security Incident Response Team Brochure PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Incident Handler, Forensic Analyst, Network Analyst, Incident Coordinator. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Security Attack Incident Response Flowchart Ppt Summary Show PDF
This slide defines the flowchart for web attack incident response. It includes information related to the steps taken to resolve the web attack incident taken place using the cybersecurity. Persuade your audience using this Cyber Security Attack Incident Response Flowchart Ppt Summary Show PDF. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including Prioritizing Security Response, Investigating, Preparing Report Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills

Strategic Initiatives And Cyber Security Programs Ppt Summary Picture PDF
This slide defines the global initiatives and cyber security program. it includes information related to the product development, leadership, outreach and awareness, policy advocacy, capacity building and collaboration. Persuade your audience using this Strategic Initiatives And Cyber Security Programs Ppt Summary Picture PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Product Development, Thought Leadership, Policy Advocacy. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
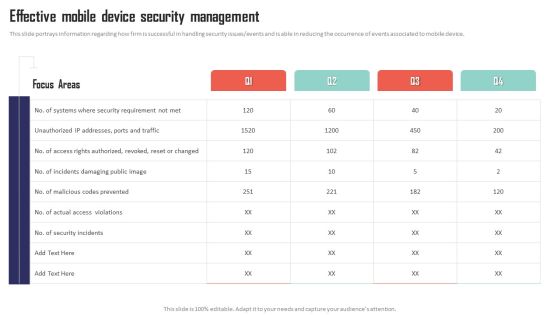
Mobile Device Management Effective Mobile Device Security Management Formats PDF
This slide portrays information regarding how firm is successful in handling security issues or events and is able in reducing the occurrence of events associated to mobile device. Want to ace your presentation in front of a live audience Our Mobile Device Management Effective Mobile Device Security Management Formats PDF can help you do that by engaging all the users towards you.. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

Scope For Security Camera Services One Pager Sample Example Document
This slide depicts the project scope providing information about the multiple activities to be performed by the bidding company for the client. Presenting you an exemplary Scope For Security Camera Services One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Scope For Security Camera Services One Pager Sample Example Document brilliant piece now.

How Management Enables Effective Corporate Security Governance Graphics PDF
This slide portrays information regarding the management role in effective corporate security governance by highlight management level, strategic alignment, risk management, etc. This modern and well-arranged How Management Enables Effective Corporate Security Governance Graphics PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

IT Security Incident Response Communication Plan Development Background PDF
This slide illustrates steps to develop a cyber security incident response communication plan to minimize impact level. It includes steps such as formulate team activation process, designate person, create criteria for law involvement etc. Presenting IT Security Incident Response Communication Plan Development Background PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Formulate Team Activation, Designate Person, Formulate Communication Template. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Crime Threat To Security Ppt PowerPoint Presentation Visual Aids Files
Presenting this set of slides with name cyber crime threat to security ppt powerpoint presentation visual aids files. This is a one stage process. The stage in this process is cyber crime threat to security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Threat Detection Online Security Computer Program Ppt PowerPoint Presentation Professional Icon PDF
Presenting this set of slides with name threat detection online security computer program ppt powerpoint presentation professional icon pdf. This is a three stage process. The stages in this process are threat detection online security computer program. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Threat Assessment For IT Network Security Ppt PowerPoint Presentation Gallery Example PDF
Presenting this set of slides with name threat assessment for it network security ppt powerpoint presentation gallery example pdf. This is a three stage process. The stages in this process are threat assessment for it network security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Threat Scanning For IT Security Ppt PowerPoint Presentation Gallery Smartart PDF
Presenting this set of slides with name threat scanning for it security ppt powerpoint presentation gallery smartart pdf. This is a three stage process. The stages in this process are threat scanning for it security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
IT Professional Showing Online Security System Model Ppt PowerPoint Presentation Model Graphic Tips PDF
Presenting this set of slides with name it professional showing online security system model ppt powerpoint presentation model graphic tips pdf. This is a one stage process. The stage in this process is it professional showing online security system model. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
 Home
Home