Data Privacy

Users Password IT Security Analysis Dashboard Elements PDF
This slide displays the analysis of the users password security in an organization to make sure that the users confidential details are safe. It includes security gains, password evaluation, active users data, activities of password, etc. Showcasing this set of slides titled Users Password IT Security Analysis Dashboard Elements PDF. The topics addressed in these templates are Password Evaluation Score, Security Gains. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Modern Digital Smart Phone Device Security Methods Elements PDF
This slide shows major categories of mobile device security approaches. The purpose of this slide is to highlight effective approaches for protecting business data. It include methods such as endpoint protection and email security, etc. Persuade your audience using this Modern Digital Smart Phone Device Security Methods Elements PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Endpoint Protection, Secure Web Gateway, Email Security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Information Security Management System Auditing Methodology Download PDF
The following slide highlights the information security system audit framework illustrating key headings which includes act, plan, do and check which are used for update and improve isms, establish isms, implement policy and control and monitor and review performance Presenting Information Security Management System Auditing Methodology Download PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Analysis, Data, Risk. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Latest Trends For Mobile Smart Phone Security Icons PDF
This slide shows current trends for securing mobile phone against potential cyber attacks and loss of sensitive data. It include trends such as rise in security automation, increasing threat modelling and SAST-DAST integration etc qPresenting Latest Trends For Mobile Smart Phone Security Icons PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Increasing Security, SAST DAST Integration, Increasing Threat Modelling. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
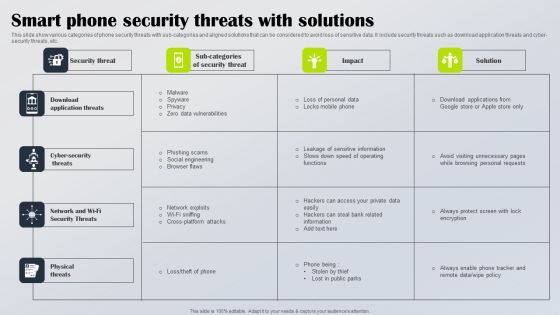
Smart Phone Security Threats With Solutions Diagrams PDF
This slide show various categories of phone security threats with sub categories and aligned solutions that can be considered to avoid loss of sensitive data. It include security threats such as download application threats and cyber security threats, etc. Showcasing this set of slides titled Smart Phone Security Threats With Solutions Diagrams PDF. The topics addressed in these templates are Download Application Threats, Cyber Security Threats, Network Wi Fi Security Threats. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Information Security Purpose Limitation Principle Of GDPR Law Graphics PDF
This slide depicts the purpose limitation principle, which states that you should be clear from the start about the reasons and intentions for collecting and processing data. Slidegeeks has constructed Information Security Purpose Limitation Principle Of GDPR Law Graphics PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

IT Risk Management Framework To Manage Security Threats Template PDF
This slide provides information regarding the implementation of IT risk management framework to monitor security threats. The initiatives include the implementation of an enterprise security program, deploy a control environment, etc. The IT Risk Management Framework To Manage Security Threats Template PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
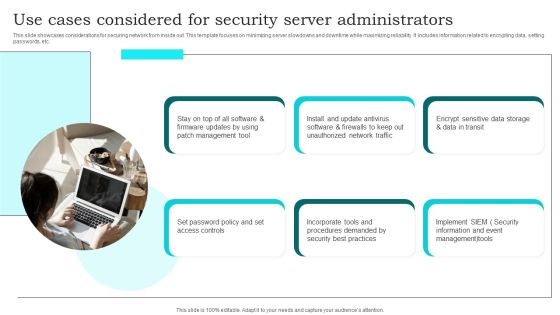
Use Cases Considered For Security Server Administrators Brochure PDF
This slide showcases considerations for securing network from inside out. This template focuses on minimizing server slowdowns and downtime while maximizing reliability. It includes information related to encrypting data, setting passwords, etc. Presenting Use Cases Considered For Security Server Administrators Brochure PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Management Tool, Set Password Policy, Unauthorized Network Traffic. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Security Training Program Frameworks Ppt Infographics Show PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas.This is a security training program frameworks ppt infographics show pdf. template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like build and maintain a secure network and systems, protect cardholder data. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Threats End User Control Themes PDF
This slide represents the end user threat in cloud security and how an organization needs to control user access and be aware of potential threats. This is a Cloud Security Threats End User Control Themes PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Centralized Data, Customer, Contact Information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Scan Principle For Smart Phone Security Model Clipart PDF
This slide shows SCAN framework for securing phone against possible threats to prevent loss of business data. It include components such as system, configuration, application and network, etc. Persuade your audience using this Scan Principle For Smart Phone Security Model Clipart PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including System, Configuration, App. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Generate Digitalization Roadmap For Business Consumer Insights Pictures PDF
This is a generate digitalization roadmap for business consumer insights pictures pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security of personal data, convenient, on the go access to health information, reliable information online for health issues. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Why Organizations Recruit Ethical Hackers Ppt Slides Smartart PDF
This is a why organizations recruit ethical hackers ppt slides smartart pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information systems, security, measures, data. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Benefits Of Blockchain Networks For Business Security Structure PDF
This slide defines the blockchain technology used to secure business data. The purpose of this template is to define blockchain technologies benefits, limitations and industry usage. It includes information related to public, private, hybrid and consortium technologies along with its advantages, disadvantages and industry usage. Pitch your topic with ease and precision using this Benefits Of Blockchain Networks For Business Security Structure PDF. This layout presents information on Public Permission Less, Private Permissioned, Hybrid Consortium. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Checklist To Implement Cloud Security In Business Microsoft PDF
This slide shows the checklist to implement cloud security in business, including policies and procedures, access control, networking, backup data, security patches, etc. Presenting Checklist To Implement Cloud Security In Business Microsoft PDF to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like Access Control, Networking, Security Patches And Updates. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

5 Layer IT Proactive Security Plan Topics PDF
This slide represents cyber proactive security strategy illustrating customer data, continuous learning, reaction to security threats, understanding security posture etc. Persuade your audience using this 5 Layer IT Proactive Security Plan Topics PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Organization Understanding, Organization Reaction, Organization Continuous Learning. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Critical Violations Security Dashboard With KPI Metrics Graphics PDF
This slide shows dashboard of security to mitigate violation by prioritizing KPIs. It includes application control, operating systems, restrict admin privileges, multi factor authentication and backup of important data. Showcasing this set of slides titled Critical Violations Security Dashboard With KPI Metrics Graphics PDF. The topics addressed in these templates are Risk Model, Application Components, Technologies Overview. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Security Operations Application For IT Infrastructure Protection Template PDF
This slide highlight security operations SecOps use cases that could protect the business data. Some of the use cases include user-reported security incidents, infrastructure vulnerability response IVR, automation and orchestration, and SIR or VR reporting. Presenting Security Operations Application For IT Infrastructure Protection Template PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Infrastructure Vulnerability Response, Cyber Threat Intelligence, Fraud Reporting Automation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

IT Security Risk Management Implementation Process Brochure PDF
The following slide explains implementation method for cybersecurity risk management for the organization to ensure protection of key business data. It includes steps such as categorize, security controls, implementation, assess, etc. Persuade your audience using this IT Security Risk Management Implementation Process Brochure PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Monitor, Authorize, Assess, Implementation, Security Controls, Categorize System. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Electronic Initiative For International Commerce Business Infographics PDF
This slide contains the initiatives for ecommerce business to expand globally. It includes ace, national trade platforms, skill framework, etc. Persuade your audience using this Electronic Initiative For International Commerce Business Infographics PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Secure Data, Productivity, Retail. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
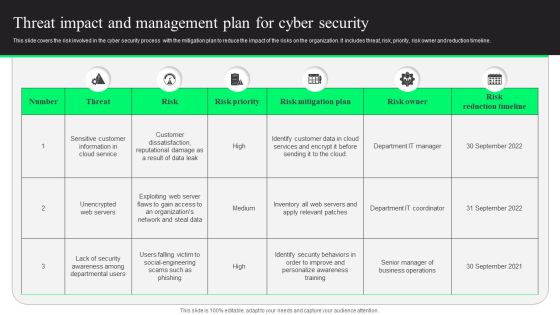
Threat Impact And Management Plan For Cyber Security Designs PDF
This slide covers the risk involved in the cyber security process with the mitigation plan to reduce the impact of the risks on the organization. It includes threat, risk, priority, risk owner and reduction timeline. Showcasing this set of slides titled Threat Impact And Management Plan For Cyber Security Designs PDF. The topics addressed in these templates are Risk Mitigation Plan, Risk Reduction Timeline, Customer Data. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cloud Network Security Training Programs Timeline Download PDF
The slide showcases training programs to improve individuals level of awareness about security measures designed to protect cloud based infrastructure and data. The elements are SANS, infosec, ISC, edX with their completion timeline and pricing package . Showcasing this set of slides titled Cloud Network Security Training Programs Timeline Download PDF. The topics addressed in these templates are Training Programs, Models Controls, Offense Defense Operations. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Role Of Management In Security Governance Across Firm Mockup PDF
This slide provides information regarding importance of management in to enable security governance across firm to ensure strategic alignment, risk management, integration, value delivery, resource management, etc. The Role Of Management In Security Governance Across Firm Mockup PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Organization Reinvention Need Of Cyber Security In Organization Graphics PDF
This slide covers the need of introducing cybersecurity in the business and how can organization integrate cybersecurity with digital transformation. Presenting Organization Reinvention Need Of Cyber Security In Organization Graphics PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Protection Against Malware, Protection Phishing Scams, Security Confidential Data. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cryptography Techniques For Framing Smart Phone Security Policy Portrait PDF
This slide shows cryptography techniques for phone oriented business data. The purpose of this slide is to highlight main techniques for building phone security policy. It include techniques such as simple codes, symmetric encryption and hashing, etc. Presenting Cryptography Techniques For Framing Smart Phone Security Policy Portrait PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Simple Codes, Symmetric Encryption, Asymmetric Encryption. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Enterprise Operational Framework For Shared Responsibility Framework Template PDF
This slide showcases operating model for shared responsibility which helps in maintaining cloud network security. It includes details about customer data, software, hardware infrastructure, etc. Showcasing this set of slides titled Enterprise Operational Framework For Shared Responsibility Framework Template PDF. The topics addressed in these templates are Customer, Organization, Responsibility Framework. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Most Effective Sales Enablement Strategies For B2B Marketers Determine B2B Purchase Decision Diagrams PDF
This slide provides information regarding B2B purchase decision maker assessment in terms of decision maker role, influence level, buy in, support quotient, etc. Deliver an awe inspiring pitch with this creative most effective sales enablement strategies for b2b marketers determine b2b purchase decision diagrams pdf bundle. Topics like encourage with data, exhibit marketing functionality, security features can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Sensing Components Of Cyber Physical Systems Ppt Ideas Graphics Example PDF
This slide depicts the sensing components of cyber security systems, including sensors, aggregators, actuators, and their operations and position on the architecture. Deliver an awe inspiring pitch with this creative Sensing Components Of Cyber Physical Systems Ppt Ideas Graphics Example PDF bundle. Topics like Processing Data, Information, Environment can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
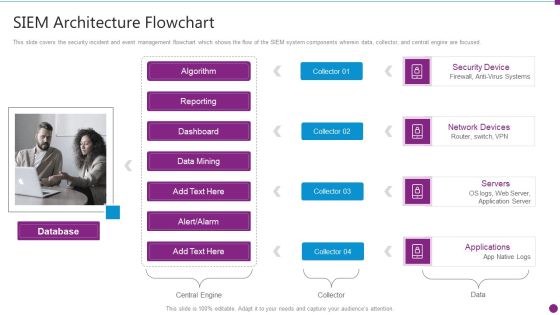
Security Information And Event Management Strategies For Financial Audit And Compliance SIEM Architecture Flowchart Microsoft PDF
This slide covers the security incident and event management flowchart which shows the flow of the SIEM system components wherein data, collector, and central engine are focused. This is a security information and event management strategies for financial audit and compliance siem architecture flowchart microsoft pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like database, security device, network devices, servers, applications. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Integration Of Digital Technology In Organization Need Of Cyber Security In Organization Information PDF
This slide covers the need of introducing cybersecurity in the business and how can organization integrate cybersecurity with digital transformation.Presenting Integration Of Digital Technology In Organization Need Of Cyber Security In Organization Information PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Confidential Data, Protection Phishing, Protection Against In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

30 60 90 Days Plan To Implement Cloud Security In Business Information PDF
This slide defines the 30,60 and 90 days plan to implement cloud security in the organization and what tasks would be performed on each 30 days interval. This is a 30 60 90 Days Plan To Implement Cloud Security In Business Information PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Analyze, Cloud Services Provided , Control Data. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
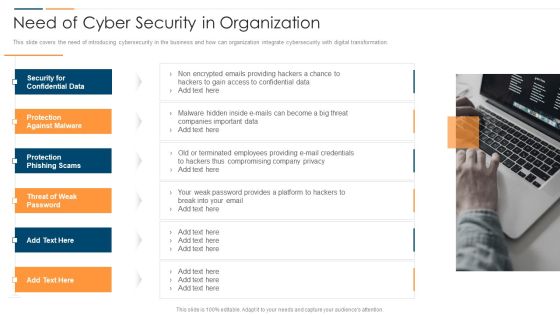
Revolution In Online Business Need Of Cyber Security In Organization Professional PDF
This slide covers the need of introducing cybersecurity in the business and how can organization integrate cybersecurity with digital transformation. This is a Revolution In Online Business Need Of Cyber Security In Organization Professional PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Confidential Data, Protection Against Malware, Protection Phishing Scams, Threat Weak Password. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Biometric Technology For Enhancing Mobile Banking Security Ppt Model Graphics PDF
This slide shows information which can be used by organizations to get insights about biometric technology growth in mobile banking. It includes details about process and types of biometric data. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Biometric Technology For Enhancing Mobile Banking Security Ppt Model Graphics PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
Various Strategies To Ensure Food Safety Food Security Excellence Ppt Icon Slide PDF
This slide provides information regarding various strategies used by firm in ensuring food safety in terms of streamlining global safety requirements, digitalization of food, food safety network. This is a various strategies to ensure food safety food security excellence ppt icon slide pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like streamlining global safety requirements, digitalization of food security or safety data, building food safety network. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT System Risk Management Guide Security Criteria And Control Measures For IT System Vulnerabilities Icons PDF
This slide highlights the security criteria for information technology system vulnerabilities with security area which includes management security, operational security and technical security. The IT System Risk Management Guide Security Criteria And Control Measures For IT System Vulnerabilities Icons PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Software Development Life Cycle Planning Security Criteria And Control Measures For IT System Vulnerabilities Brochure PDF
This slide highlights the security criteria for information technology system vulnerabilities with security area which includes management security, operational security and technical security. The Software Development Life Cycle Planning Security Criteria And Control Measures For IT System Vulnerabilities Brochure PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Saas Application Cloud Security Monthly Roadmap Ppt PowerPoint Presentation File Format PDF
The following slide represents six months software as a service security roadmap to protect asset and data. It includes activities such as assessing security requirement, planning safety services, developing security as code etc. Presenting Saas Application Cloud Security Monthly Roadmap Ppt PowerPoint Presentation File Format PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Determine Security, Develop Security, Modify Key Policies. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Security And Human Resource Services Business Profile Sales Revenue By Region Brochure PDF
This slide highlights the security company sales revenue by region and services. It showcases retail mall security, social event security, university hospital security, executive protection and building security. The Security And Human Resource Services Business Profile Sales Revenue By Region Brochure PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
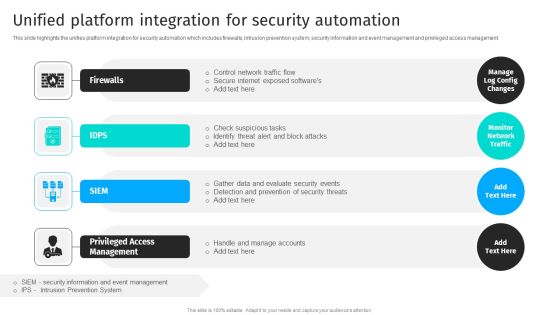
Security Automation To Analyze And Mitigate Cyberthreats Unified Platform Integration Themes PDF
This slide highlights the unifies platform integration for security automation which includes firewalls, intrusion prevention system, security information and event management and privileged access management.The Security Automation To Analyze And Mitigate Cyberthreats Unified Platform Integration Themes PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Mobile Device Management For Improving IT Operations Implementing Mobile Device Security Template PDF
This slide portrays information regarding optimization of current mobile device security framework. The IT department will require to fulfill crucial activities in specific timeframe. The Mobile Device Management For Improving IT Operations Implementing Mobile Device Security Template PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Reverse Proxy Web Server Reverse Proxy Web Server Application Side Technology Security Designs PDF
This slide represents the reverse proxy server-side technology, which is load balancing, and how reverse proxy side servers help high-traffic websites manage traffic. The Reverse Proxy Web Server Reverse Proxy Web Server Application Side Technology Security Designs PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

ERM Plan For Cyber Security Ppt PowerPoint Presentation File Ideas PDF
This slide displays the steps that helps to stay away from the threats of cyber security and makes clients feel safe from the cyber attacks. The steps includes Identifying digital assets, audit data, perform assessments, analyze risk level, establish committee ,etc. Persuade your audience using this ERM Plan For Cyber Security Ppt PowerPoint Presentation File Ideas PDF. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including Establish Risk Assessment Committee, Create Response Plan, Educate Employees On Policies. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Determine Various Mobile Devices Existing At Workplace Mobile Device Security Management Guidelines PDF
The employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. Deliver an awe inspiring pitch with this creative Determine Various Mobile Devices Existing At Workplace Mobile Device Security Management Guidelines PDF bundle. Topics like Corporate Data, Allowed Employees, Consumerization Technology can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
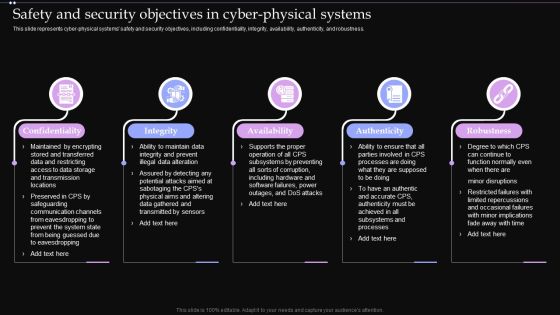
Safety And Security Objectives In Cyber Physical Systems Ppt PowerPoint Presentation File Example PDF
This slide represents cyber physical systems safety and security objectives, including confidentiality, integrity, availability, authenticity, and robustness. The Safety And Security Objectives In Cyber Physical Systems Ppt PowerPoint Presentation File Example PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Security Control Techniques For Real Estate Project Hazard Impact Analysis For Construction Site Icons PDF
The Security Control Techniques For Real Estate Project Hazard Impact Analysis For Construction Site Icons PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Real Time Assessment Of Security Threats Fully Managed Service Model Demonstration PDF
This slide covers the SIEM as a service model wherein all the steps are taken care by our company and the client just have to provide us the relevant data. Deliver an awe inspiring pitch with this creative real time assessment of security threats fully managed service model demonstration pdf bundle. Topics like threat and vulnerability management processes, reporting, retention, correlation, collection can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Retail Store Operations Strategies To Enhance Retail Store Security Pictures PDF
This slide provides information regarding the strategies to enhance retail store security such as integrate access control technology, deploy video surveillance, utilizes electronic article surveillance, install monitored alarms. The Retail Store Operations Strategies To Enhance Retail Store Security Pictures PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
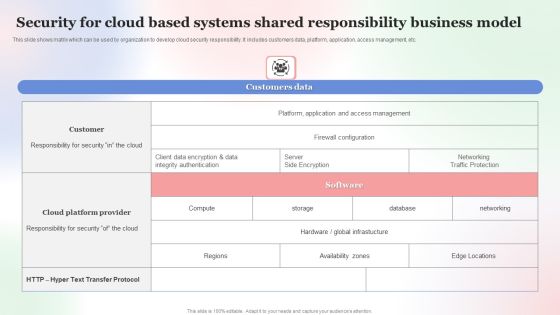
Security For Cloud Based Systems Shared Responsibility Business Model Professional PDF
This slide shows matrix which can be used by organization to develop cloud security responsibility. It includes customers data, platform, application, access management, etc. Showcasing this set of slides titled Security For Cloud Based Systems Shared Responsibility Business Model Professional PDF. The topics addressed in these templates are Security For Cloud Based, Systems Shared Responsibility, Business Model. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Deploying Corporate Aligned IT Strategy How Management Enables Effective Corporate Security Governance Topics PDF
This slide portrays information regarding the management role in effective corporate security governance by highlight management level, strategic alignment, risk management, etc. The Deploying Corporate Aligned IT Strategy How Management Enables Effective Corporate Security Governance Topics PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
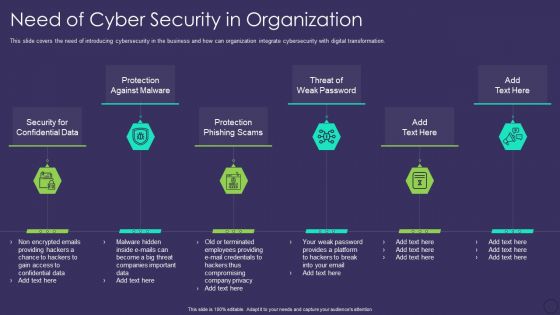
Comprehensive Business Digitization Deck Need Of Cyber Security In Organization Formats PDF
This slide covers the need of introducing cybersecurity in the business and how can organization integrate cybersecurity with digital transformation. Presenting comprehensive business digitization deck need of cyber security in organization formats pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security for confidential data, protection against malware, protection phishing scams, threat of weak password. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Net Banking Channel And Service Management Major Types Of E Banking Security Threats Inspiration PDF
This slide represents types of e banking security threats. It includes brute force, phishing, pharming, cross site scripting and trojan horse. The Net Banking Channel And Service Management Major Types Of E Banking Security Threats Inspiration PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Organizations Risk Management And IT Security Integration Of Risk Management Into SDLC Inspiration PDF
This slide highlights the risk management integration with software development life cycle which includes SDLC phases Initiation, development, implementation and maintenance with risk management activities. The Organizations Risk Management And IT Security Prioritized Cyber Security Threats With Risk Mitigation Plan Demonstration PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
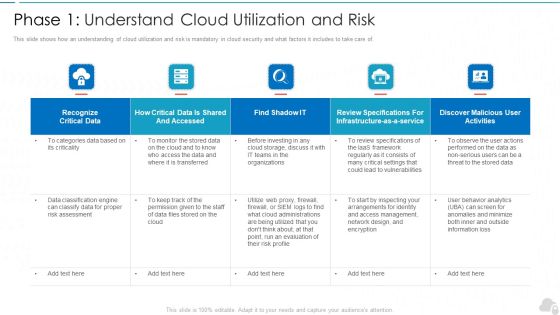
Phase 1 Understand Cloud Utilization And Risk Cloud Computing Security IT Ppt Summary Smartart PDF
This slide shows how an understanding of cloud utilization and risk is mandatory in cloud security and what factors it includes to take care of. Deliver and pitch your topic in the best possible manner with this phase 1 understand cloud utilization and risk cloud computing security it ppt summary smartart pdf. Use them to share invaluable insights on recognize critical data, infrastructure, evaluation, vulnerabilities, organizations and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Net Banking Channel And Service Management E Banking Security Measures And Features Designs PDF
This slide represents e banking security measures and features. It includes login details, encrypted data, account management and two factor authorization. This Net Banking Channel And Service Management E Banking Security Measures And Features Designs PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The product features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, dont wait, grab the presentation templates today.
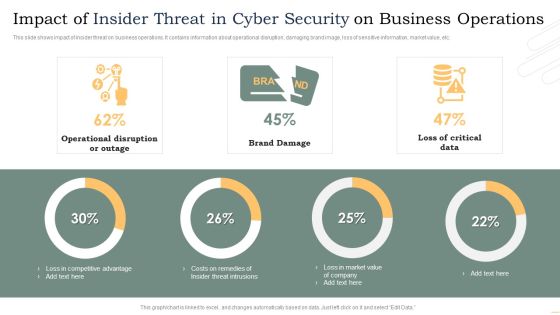
Impact Of Insider Threat In Cyber Security On Business Operations Microsoft PDF
This slide shows impact of insider threat on business operations. It contains information about operational disruption, damaging brand image, loss of sensitive information, market value, etc. Pitch your topic with ease and precision using this Impact Of Insider Threat In Cyber Security On Business Operations Microsoft PDF. This layout presents information on Operational Disruption Or Outage, Brand Damage, Loss Critical Data. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Insider Threat In Cyber Security Tracking Dashboard With User Details Portrait PDF
This slide shows user details tracked by insider threat dashboard. It provides information such as exposure events, file activity, archive, document, image, pdf, ppt, scripts, etc. Pitch your topic with ease and precision using this Insider Threat In Cyber Security Tracking Dashboard With User Details Portrait PDF. This layout presents information on Private Data, Exposure Events, User Activity, File Activity, Over Time. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Approaches To Improve Infra Cyber Security In AI Infrastructure Diagrams PDF
The following slide showcases various approaches to AI infrastructure which bodes well for future of organizations association. It presents information related to regulatory framework, expert consultations, etc. Presenting Approaches To Improve Infra Cyber Security In AI Infrastructure Diagrams PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Regulatory Framework, Protect AI Related Data, Involve Cybersecurity Experts. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Accelerate Online Journey Now Need Of Cyber Security In Organization Professional PDF
This slide covers the need of introducing cybersecurity in the business and how can organization integrate cybersecurity with digital transformation.Presenting Accelerate Online Journey Now Need Of Cyber Security In Organization Professional PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Confidential Data, Against Malware, Phishing Scams In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Organizing Security Awareness Most Common Cyber Attack Faced By Our Employees Mockup PDF
The Organizing Security Awareness Most Common Cyber Attack Faced By Our Employees Mockup PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

1G To 5G Wireless Communication System IT What Security Features Does 5G 5Th Generation Technology Include Professional PDF
This slide depicts the security features included in 5th generation technology, such as new cryptographic techniques for individual component protection, network slicing, encryption of IMSI to avoid eavesdropping spots, authentication confirmation, and secure network for sensitive data. Presenting 1G To 5G Wireless Communication System IT What Security Features Does 5G 5Th Generation Technology Include Professional PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Cryptographic Evidence, Domestic, Via Network Slicing. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
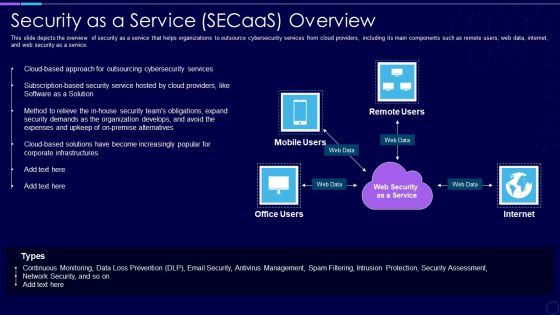
Everything As A Service Xaas For Cloud Computing IT Security As A Service Secaas Overview Portrait PDF
This slide depicts the overview of security as a service that helps organizations to outsource cybersecurity services from cloud providers, including its main components such as remote users, web data, internet, and web security as a service. Presenting everything as a service xaas for cloud computing it security as a service secaas overview portrait pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like expenses, security, organization, services, management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
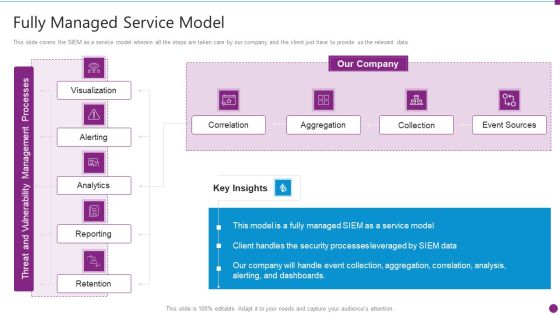
Security Information And Event Management Strategies For Financial Audit And Compliance Fully Managed Service Model Portrait PDF
This slide covers the SIEM as a service model wherein all the steps are taken care by our company and the client just have to provide us the relevant data. Deliver and pitch your topic in the best possible manner with this security information and event management strategies for financial audit and compliance fully managed service model portrait pdf. Use them to share invaluable insights on correlation, aggregation, collection, event sources and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security As A Service Secaas Overview Xaas Cloud Computing Models Ppt PowerPoint Presentation Outline Slide Download PDF
This slide depicts the overview of security as a service that helps organizations to outsource cybersecurity services from cloud providers, including its main components such as remote users, web data, internet, and web security as a service.Deliver and pitch your topic in the best possible manner with this Security As A Service Secaas Overview Xaas Cloud Computing Models Ppt PowerPoint Presentation Outline Slide Download PDF. Use them to share invaluable insights on Outsourcing Cybersecurity, Software Solution, Expenses Upkeep and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cloud Intelligence Framework For Application Consumption Financial Losses To The Organizations Due To Security Issues Mockup PDF
The slide provides total financial losses from the year 2017 to 2021 reported by the organizations in United states along with the key reasons behind those losses. Deliver an awe inspiring pitch with this creative cloud intelligence framework for application consumption financial losses to the organizations due to security issues mockup pdf bundle. Topics like security vulnerabilities, primary reasons for the growing, physical theft of a data-carrying device, 2016 to 2020 can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Series Of Cyber Security Attacks Against Ukraine 2022 Website Defacements Ddos Attacks And Website Clones Brochure PDF
This slide represents the other attacks carried out by russia on ukraine, such as website defacement, distributed denial-of-service attacks, and website clones. The Series Of Cyber Security Attacks Against Ukraine 2022 Website Defacements Ddos Attacks And Website Clones Brochure PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Lock Minded Security PowerPoint Templates And PowerPoint Backgrounds 0711
Microsoft PowerPoint Template and Background with security minded digital collage of human profile with key
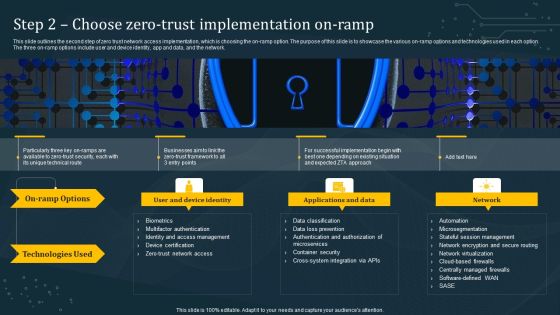
Step 2 Choose Zero Trust Implementation On Ramp Information PDF
This slide outlines the second step of zero trust network access implementation, which is choosing the on-ramp option. The purpose of this slide is to showcase the various on-ramp options and technologies used in each option. The three on-ramp options include user and device identity, app and data, and the network. Slidegeeks is here to make your presentations a breeze with Step 2 Choose Zero Trust Implementation On Ramp Information PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first

Cloud Access Security Broker And Secure Web Gateway Ppt PowerPoint Presentation Diagram Images PDF
This slide represents how CASB 2.0 not just discovers the shadow IT but helps to control it too. The purpose of this slide is to showcase how CASB 2.0 improves the SWG model by empowering it with rich cloud app data, getting dynamic control of shadow IT and simplifying deployment. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cloud Access Security Broker And Secure Web Gateway Ppt PowerPoint Presentation Diagram Images PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cloud Access Security Broker And Secure Web Gateway Ppt PowerPoint Presentation Diagram Images PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Implementing Cyber Security Incident Cyber Security Incidents Follow-Up Report Clipart PDF
This slide represents the follow-up report prepared by cyber security incident management team after successfully responding to cyber incidents experienced by the organization. It includes details related to date of incident, actions taken by responsible officer. The Implementing Cyber Security Incident Cyber Security Incidents Follow-Up Report Clipart PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

SIEM Architecture Flowchart Ppt Show Introduction PDF
This slide covers the security incident and event management flowchart which shows the flow of the SIEM system components wherein data, collector, and central engine are focused. This is a siem architecture flowchart ppt show introduction pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security device, network devices, servers, applications. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
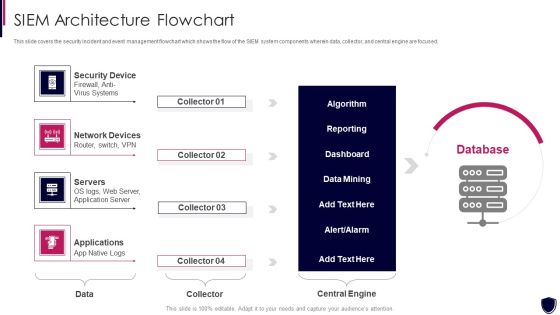
Enhancing Cyber Safety With Vulnerability Administration SIEM Architecture Flowchart Demonstration PDF
This slide covers the security incident and event management flowchart which shows the flow of the SIEM system components wherein data, collector, and central engine are focused. This is a enhancing cyber safety with vulnerability administration siem architecture flowchart demonstration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security device, network devices, servers, applications. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Operations Cyber Security Icon With Lock Clipart PDF
Persuade your audience using this Security Operations Cyber Security Icon With Lock Clipart PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Security Operations Cyber, Security Icon With Lock. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Global Medicare Digital Transformation Drivers Mockup PDF
This slide shows global healthcare forces for transforming medical sector to provide proper treatment in pandemic like situations. It include drivers such as empowering remote working model, creating patient first journey experience etc. Showcasing this set of slides titled Global Medicare Digital Transformation Drivers Mockup PDF. The topics addressed in these templates are Digitalize Patient Services, Security Programs, Securing Data. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Online Payment Service Digital Payment System Deployment Services Ppt Slides Brochure PDF
Listed Solutions provides centralized, secure storage of analytical assets, and advanced capabilities for management and control of predictive analytic processes. This is a online payment service digital payment system deployment services ppt slides brochure pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like automate processes, share analytical across, infrastructure, secure your data. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Computing Service Models IT Cloud Computing In Manufacturing Industry Inspiration PDF
This slide describes the usages of cloud computing in the manufacturing industry, including cyber security, cloud computing, big data, autonomous robots, augmented reality, simulation, etc. This is a cloud computing service models it cloud computing in manufacturing industry inspiration pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like simulation, cyber security, cloud computing, system integration, autonomous robots. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Apache Hadoop IT Disadvantages Of Hadoop Diagrams PDF
This slide represents the disadvantages of Hadoop on the basis of security, vulnerability by design, not suitable for small data, and potential stability concerns.This is a apache hadoop it disadvantages of hadoop diagrams pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security issues, vulnerable by design, potential stability concerns You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
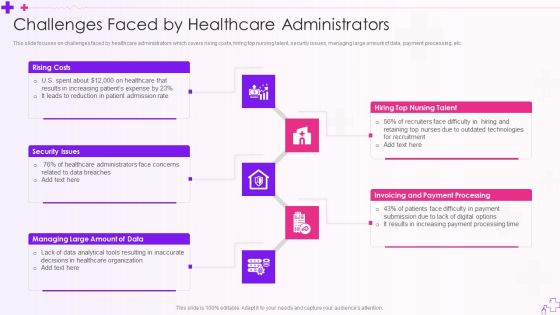
Integration Of Healthcare Center Administration System Challenges Faced By Healthcare Administrators Clipart PDF
This slide focuses on challenges faced by healthcare administrators which covers rising costs, hiring top nursing talent, security issues, managing large amount of data, payment processing, etc.This is a Integration Of Healthcare Center Administration System Challenges Faced By Healthcare Administrators Clipart PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Issues, Increasing Patients, Invoicing And Payment You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Advances In Healthcare Management System Challenges Faced By Healthcare Administrators Infographics PDF
This slide focuses on challenges faced by healthcare administrators which covers rising costs, hiring top nursing talent, security issues, managing large amount of data, payment processing, etc. This is a Advances In Healthcare Management System Challenges Faced By Healthcare Administrators Infographics PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Issues, Hiring Top Nursing Talent, Rising Costs. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Apache Hadoop Software Deployment Disadvantages Of Hadoop Structure PDF
This slide represents the disadvantages of Hadoop on the basis of security, vulnerability by design, not suitable for small data, and potential stability concerns.This is a Apache Hadoop Software Deployment Disadvantages Of Hadoop Structure PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Managing Complicated, Security Breaches, Potential Stability. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Distribution Service Models Cloud Computing In Manufacturing Industry Brochure PDF
This slide describes the usages of cloud computing in the manufacturing industry, including cyber security, cloud computing, big data, autonomous robots, augmented reality, simulation, etc. This is a Cloud Distribution Service Models Cloud Computing In Manufacturing Industry Brochure PDF template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Additive Manufacturing, Augmented Reality, Cyber Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Challenges Faced By Healthcare Administrators Sample PDF
This slide focuses on challenges faced by healthcare administrators which covers rising costs, hiring top nursing talent, security issues, managing large amount of data, payment processing, etc.Presenting Challenges Faced By Healthcare Administrators Sample PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Security Issues, Payment Processing, Managing Large In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Computing Services Cloud Computing In Manufacturing Industry Inspiration PDF
This slide describes the usages of cloud computing in the manufacturing industry, including cyber security, cloud computing, big data, autonomous robots, augmented reality, simulation, etc. Presenting Cloud Computing Services Cloud Computing In Manufacturing Industry Inspiration PDF to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like Cyber Security, Cloud Computing, System Integration. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Future Innovative Techniques For Global Digital Terrorism Background PDF
This slide show future upcoming techniques for tackling global cyber terrorism attacks and providing overall security to business data. It include techniques like permanent remote work security, regular automation and zero-trust principles etc. Persuade your audience using this Future Innovative Techniques For Global Digital Terrorism Background PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Improve Response Capability, Identify Supply Chain Risks, Automate Regularly. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Digital Trends In Customer Finance Market Template PDF
The slide highlights various digital and tech based trends in consumer financing and lending market. It includes key components like better customer experience, enhanced security, greater Omni channel capabilities, Non banking institutions market entry and AI tools. Persuade your audience using this Digital Trends In Customer Finance Market Template PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Evaluate Data, Ensure Security, Lending Services. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Information Technology Facilities Governance Client Standards Checklist Contd Icons PDF
In order to maximise service delivery efficiencies, customer satisfaction, the firm standardised certain environmental qualifications for type of hardwares, softwares, operating systems. This is a information technology facilities governance client standards checklist contd icons pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like protect servers, high speed internet access, secured encryption, wireless data. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Right Of Access To Private Land Ppt PowerPoint Presentation Pictures Ideas
This is a right of access to private land ppt powerpoint presentation pictures ideas. This is a three stage process. The stages in this process are access rights, access management, business.
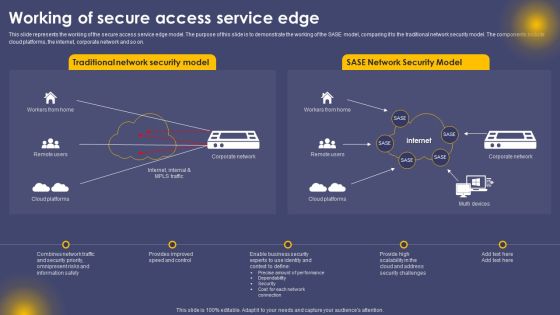
Working Of Secure Access Service Edge Ppt Summary Ideas PDF
This slide represents the working of the secure access service edge model. The purpose of this slide is to demonstrate the working of the SASE model, comparing it to the traditional network security model. The components include cloud platforms, the internet, corporate network and so on. The Working Of Secure Access Service Edge Ppt Summary Ideas PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Cybersecurity Operations Cybersecops Security Operations Threat Management Brochure PDF
This slide depicts the security operations threat management process. The purpose of this slide is to showcase the various stages and operations included in the security operations threat management process. The steps include discovery, preliminary investigation, triage, extended investigation, and contain and respond. The Cybersecurity Operations Cybersecops Security Operations Threat Management Brochure PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
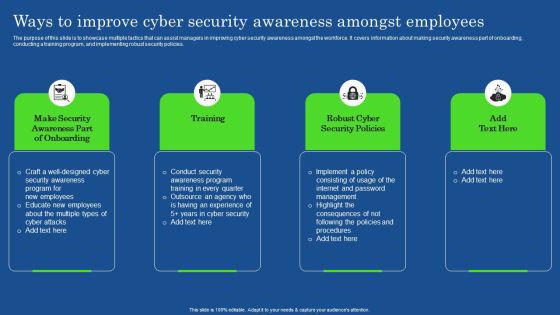
Ways To Improve Cyber Security Awareness Amongst Employees Elements PDF
The purpose of this slide is to showcase multiple tactics that can assist managers in improving cyber security awareness amongst the workforce. It covers information about making security awareness part of onboarding, conducting a training program, and implementing robust security policies. The Ways To Improve Cyber Security Awareness Amongst Employees Elements PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Cyber Security Incident Management Checklist During An Incident Inspiration PDF
This slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident management during the occurrence of the incident. The Cyber Security Incident Management Checklist During An Incident Inspiration PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Organizing Security Awareness General Outlook Of Ransomware Attack Structure PDF
The purpose of this slide is to outline an example of ransomware attack. The slide provides information about the working of ransomware attack work and how it can encrypts the victims data. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Organizing Security Awareness General Outlook Of Ransomware Attack Structure PDF can be your best option for delivering a presentation. Represent everything in detail using Organizing Security Awareness General Outlook Of Ransomware Attack Structure PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
Various Strategies To Ensure Food Safety Increased Superiority For Food Products Icons PDF
This slide provides information regarding various strategies used by firm in ensuring food safety in terms of streamlining global safety requirements, digitalization of food, food safety network. This is a various strategies to ensure food safety increased superiority for food products icons pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like streamlining global safety requirements, digitalization of food security or safety data, building food safety network. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
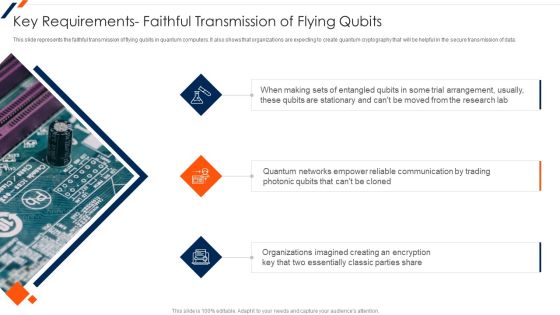
Quantum Computing Key Requirements Faithful Transmission Of Flying Qubits Designs PDF
This slide represents the faithful transmission of flying qubits in quantum computers. It also shows that organizations are expecting to create quantum cryptography that will be helpful in the secure transmission of data. This is a Quantum Computing Key Requirements Faithful Transmission Of Flying Qubits Designs PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Quantum Networks, Communication, Trial Arrangement. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Execution Of ICT Strategic Plan Role Of Technology In Effective Staff Management Download PDF
This slide represents role of technology in workforce management. It includes innovation, upgraded workspace, error-free work discourse, and security. The Execution Of ICT Strategic Plan Role Of Technology In Effective Staff Management Download PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Comparative Analysis Of Software Tools In Project Time Scheduling Summary PDF
This slide shows comparative analysis of software tools in project time management beneficial for project managers to complete work efficiently. This also includes details about tools, reviews, features, platforms, customizable and price per month Showcasing this set of slides titled comparative analysis of software tools in project time scheduling summary pdf. The topics addressed in these templates are security, data, application. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Naas Integrated Solution IT Virtual Private Network VPN Model Overview Designs PDF
This slide represents the overview of the virtual private network, including its benefits, such as protecting customer information from hackers, preventing internet service provider companies and websites from selling customer data, and so on. Deliver an awe inspiring pitch with this creative Naas Integrated Solution IT Virtual Private Network VPN Model Overview Designs PDF bundle. Topics like Secured Communication, Business, Information can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Software Comparative Assessment For Commodity Expansion Microsoft PDF
This slide signifies the comparative assessment for commodity expansion. It covers information related to features like capture real time data, end to end delivery tracking, automatic good detection form browser.Pitch your topic with ease and precision using this Software Comparative Assessment For Commodity Expansion Microsoft PDF. This layout presents information on Malware Removal, Security Protocol, Custom Analytics. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Online Settlement Revolution Digital Payment System Deployment Services Summary PDF
Listed Solutions provides centralized, secure storage of analytical assets, and advanced capabilities for management and control of predictive analytic processes. Presenting online settlement revolution digital payment system deployment services summary pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like automate process, analytics, infrastructure, data. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
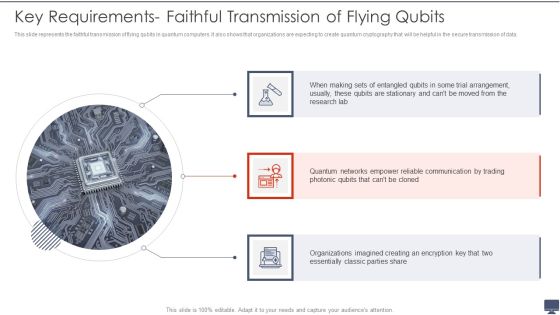
Quantum Computing Key Requirements Faithful Transmission Of Flying Qubits Ppt Portfolio Templates PDF
This slide represents the faithful transmission of flying qubits in quantum computers. It also shows that organizations are expecting to create quantum cryptography that will be helpful in the secure transmission of data. Presenting Quantum Computing Key Requirements Faithful Transmission Of Flying Qubits Ppt Portfolio Templates PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Organizations Imagined, Reliable Communication, Quantum Networks. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Comparison Between ITIL V2 And ITIL V3 IT Service Management Framework Structure PDF
This slide represents the difference between ITIL v2 and ITIL v3, based on focus, approach, security management, number of processes, and functions.The Comparison Between ITIL V2 And ITIL V3 IT Service Management Framework Structure PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
Various Strategies To Ensure Food Safety Application Of Quality Management For Food Processing Companies Icons PDF
This slide provides information regarding various strategies used by firm in ensuring food safety in terms of streamlining global safety requirements, digitalization of food, food safety network. This is a various strategies to ensure food safety application of quality management for food processing companies icons pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like streamlining global safety requirements, digitalization of food security or safety data, building food safety network. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
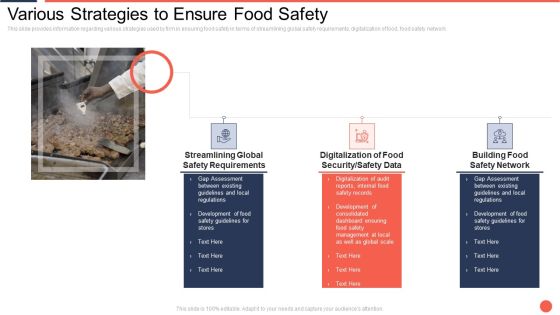
Various Strategies To Ensure Food Safety Assuring Food Quality And Hygiene Brochure PDF
This slide provides information regarding various strategies used by firm in ensuring food safety in terms of streamlining global safety requirements, digitalization of food, food safety network. This is a various strategies to ensure food safety assuring food quality and hygiene brochure pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like streamlining global safety requirements, digitalization of food security or safety data, building food safety network. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
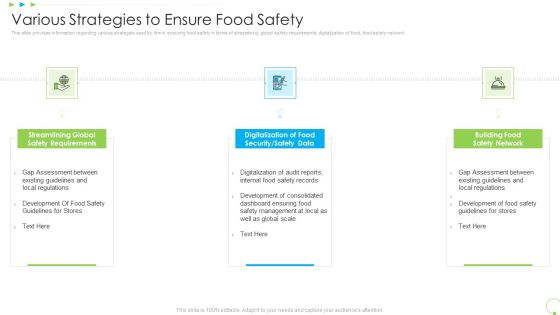
Various Strategies To Ensure Food Safety Uplift Food Production Company Quality Standards Structure PDF
This slide provides information regarding various strategies used by firm in ensuring food safety in terms of streamlining global safety requirements, digitalization of food, food safety network. This is a various strategies to ensure food safety uplift food production company quality standards structure pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like streamlining global safety requirements, digitalization of food security or safety data, building food safety network. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
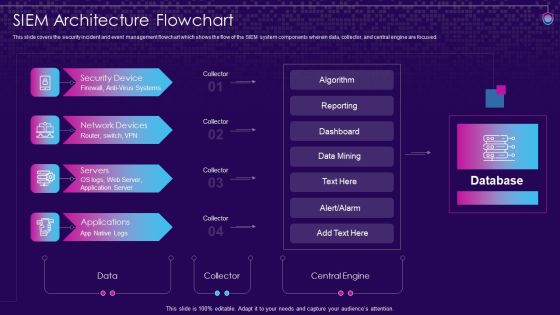
SIEM Architecture Flowchart SIEM Services Ppt Infographic Template Graphics Download PDF
This slide covers the security incident and event management flowchart which shows the flow of the SIEM system components wherein data, collector, and central engine are focused. This is a siem architecture flowchart siem services ppt infographic template graphics download pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like siem architecture flowchart. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
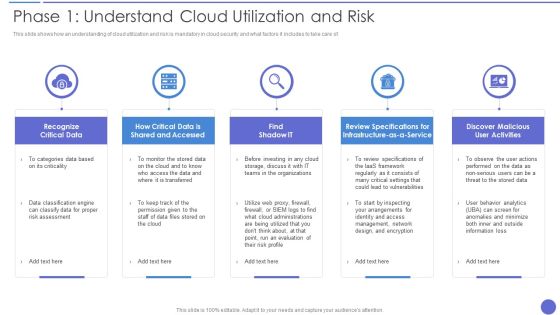
Phase 1 Understand Cloud Utilization And Risk Topics PDF
This slide shows how an understanding of cloud utilization and risk is mandatory in cloud security and what factors it includes to take care of. This is a Phase 1 Understand Cloud Utilization And Risk Topics PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Recognize Critical Data, Risk Assessment, Management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Quantum Key Distribution Key Requirements Faithful Transmission Of Flying Qubits Diagrams PDF
This slide represents the faithful transmission of flying qubits in quantum computers. It also shows that organizations are expecting to create quantum cryptography that will be helpful in the secure transmission of data. This is a Quantum Key Distribution Key Requirements Faithful Transmission Of Flying Qubits Diagrams PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Trial Arrangement, Quantum Networks, Reliable Communication You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Quantum Computing For Everyone IT Key Requirements Faithful Transmission Of Flying Qubits Icons PDF
This slide represents the faithful transmission of flying qubits in quantum computers. It also shows that organizations are expecting to create quantum cryptography that will be helpful in the secure transmission of data. Deliver and pitch your topic in the best possible manner with this quantum computing for everyone it key requirements faithful transmission of flying qubits icons pdf. Use them to share invaluable insights on organizations, communication, quantum networks and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Telehealth Venture Capitalist Funding Elevator Why Invest On Our Organization Ideas PDF
The following slide displays the key overview of the organization as it provides an overview of the industry verticals such as healthcare, life science, incubators etc. The following also displays the key capabilities of the industries. Deliver an awe inspiring pitch with this creative telehealth venture capitalist funding elevator why invest on our organization ideas pdf bundle. Topics like software, big data, cyber security, organization can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Devops Deployment And Transformation Services Advisory Solution For System Operations As A People Problem Professional PDF
This slide covers the solution of the problems faced by the clients such as monitoring, containers, metrics, analytics, logs, performance security etc. Elevate your presentations with our intuitive Devops Deployment And Transformation Services Advisory Solution For System Operations As A People Problem Professional PDF template. Whether youre delivering a pitch, sharing data, or presenting ideas, our visually-stunning single-slide PPT template is the perfect tool to captivate your audience. With 100 percenteditable features and a user-friendly interface, creating professional presentations has never been easier. Download now and leave a lasting impression.

Workplace Facility Management Services Company Hard And Soft Facility Management Services Mockup PDF
This slide highlights hard and soft facility management services which are offered by the company which includes cleaning services, support services, security services, catering services and technical services. The Workplace Facility Management Services Company Hard And Soft Facility Management Services Mockup PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Overcoming Challenges In Developing Mobile Commercial Banking Application Diagrams PDF
Following slide brings forth the ways to overcome challenges and offers solutions in developing application for mobile banking. The elements covered in this slide are challenges, solutions and outcomes. Showcasing this set of slides titled Overcoming Challenges In Developing Mobile Commercial Banking Application Diagrams PDF. The topics addressed in these templates are Regulatory Compliance Management, Securing Customer Data, Updating New Market Trends. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Workplace Portable Device Monitoring And Administration Mobile Device Management For Android Platform Slides PDF
This slide provides information regarding mobile device management for android platform with device settings policy, device security settings, etc. The Workplace Portable Device Monitoring And Administration Mobile Device Management For Android Platform Slides PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
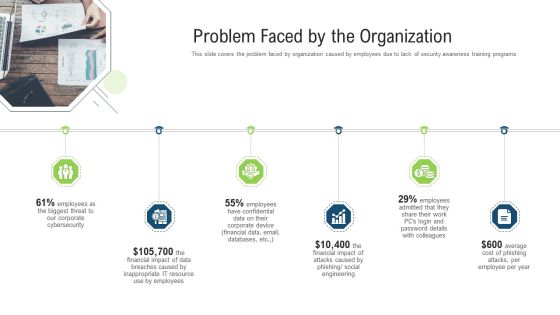
Problem Faced By The Organization Ppt Styles Layouts PDF
This slide covers the problem faced by organization caused by employees due to lack of security awareness training programs. Presenting problem faced by the organization ppt styles layouts pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like financial impact, email databases, financial data, average. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Distributed Computing IT How Edge Computing Can Benefit Business Template PDF
This slide depicts how edge computing can benefit businesses by reducing response time, providing better security, reduced costs, more excellent reliability, interoperability, and scalability. Presenting distributed computing it how edge computing can benefit business template pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like management costs, processing data, computers. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Enhancing Hospital Software System Challenges Faced By Healthcare Administrators Clipart PDF
This slide focuses on challenges faced by healthcare administrators which covers rising costs, hiring top nursing talent, security issues, managing large amount of data, payment processing, etc. Presenting enhancing hospital software system challenges faced by healthcare administrators clipart pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like challenges faced by healthcare administrators. In addition, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Based Service Models Cloud Computing In Manufacturing Industry Ideas PDF
This slide describes the usages of cloud computing in the manufacturing industry, including cyber security, cloud computing, big data, autonomous robots, augmented reality, simulation, etc.Presenting Cloud Based Service Models Cloud Computing In Manufacturing Industry Ideas PDF to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like Cloud Computing, Augmented Reality, Additive Manufacturing. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Consultancy Services Company Profile Client Reviews And Testimonials Ideas PDF
This slides focuses on client testimonials post using our products and services which helps to build credibility and reliability to business and helps in decision making process. Presenting IT Consultancy Services Company Profile Client Reviews And Testimonials Ideas PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Excellent Data, Security Services, Software Services. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Hard And Soft Facility Management Services Developing Tactical Fm Services Microsoft PDF
This slide highlights hard and soft facility management services which are offered by the company which includes cleaning services, support services, security services, catering services and technical services.The Hard And Soft Facility Management Services Developing Tactical Fm Services Microsoft PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
Standard Safety Equipment Required To Host Successful Event Activities For Successful Launch Event Graphics PDF
This slide provides an overview of safety equipments required at event premises. The equipments covered are temporary fencing, security personnel, first aid station and crowd control barriers. The Standard Safety Equipment Required To Host Successful Event Activities For Successful Launch Event Graphics PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Ways To Effectively Mitigate Contract Risk Assessment And Management Download PDF
The slide showcases various ways to mitigate contract risks. It suggests encryption to protect contract data, control assess with role based security, use clause and template libraries to increase compliance and use automated workflows to enforce business process. Presenting Ways To Effectively Mitigate Contract Risk Assessment And Management Download PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Encryption Protect, Control Assess Role, Use Clause Template Libraries. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

 Home
Home