Data Privacy

Optimizing Online Stores Challenges In Selecting Effective Order Management Graphics PDF
This slide represents the hurdles and business challenges faced by marketing manager of abc ecommerce firm in the current scenario. it includes business challenges such as customers exploding expectations, agility, data security, customer retention and omni-channel experience. there are so many reasons you need a optimizing online stores challenges faced by ecommerce marketing manager demonstration pdf. the first reason is you cant spend time making everything from scratch, thus, slidegeeks has made presentation templates for you too. you can easily download these templates from our website easily.

Challenges Faced By Ecommerce Marketing Manager Deploying Ecommerce Order Management Introduction PDF
This slide represents the hurdles and business challenges faced by marketing manager of ABC ecommerce firm in the current scenario. It includes business challenges such as customers exploding expectations, agility, data security, customer retention and omni-channel experience.Want to ace your presentation in front of a live audience Our Challenges Faced By Ecommerce Marketing Manager Deploying Ecommerce Order Management Introduction PDF can help you do that by engaging all the users towards you.. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

Decentralized Applications Benefits Of Tron Blockchain Infographics PDF
This slide highlights the advantages of Tron blockchain, including equivalent profits, data ownership, strong security confirmation, scalability, and high effectiveness. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Decentralized Applications Benefits Of Tron Blockchain Infographics PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Decentralized Applications Benefits Of Tron Blockchain Infographics PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Integrating CRM Solution To Acquire Potential Customers Important Considerations For Implementing Mobile CRM Brochure PDF
This slide represents the key factors to be kept in mid at the time of deploying mobile CRM in the organization. It includes details related to key considerations for CRM implementation such as data security, device compatibility and features. There are so many reasons you need a Integrating CRM Solution To Acquire Potential Customers Important Considerations For Implementing Mobile CRM Brochure PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
Impact Of Cybersecurity Incidents On Organization Microsoft PDF
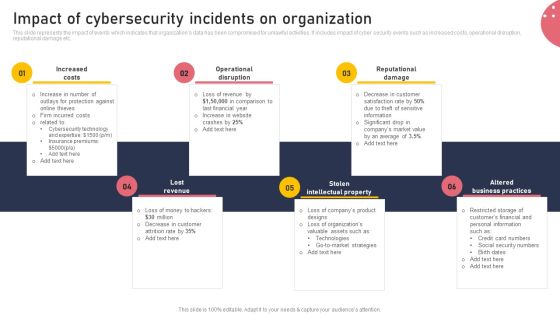
This slide represents the impact of events which indicates that organizations data has been compromised for unlawful activities. It includes impact of cyber security events such as increased costs, operational disruption, reputational damage etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Impact Of Cybersecurity Incidents On Organization Microsoft PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Pre And Post Results Of Cloud Computing Process Changes Graphics PDF
This slide showcases ways in which cloud computing benefits a companys working to achieve desired goal on time. It includes data security and cost efficiency. Persuade your audience using this Pre And Post Results Of Cloud Computing Process Changes Graphics PDF. This PPT design covers two stages, thus making it a great tool to use. It also caters to a variety of topics including Cloud Computing, Expensive Equipment, Includes Purchasing. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cybersecurity Operations Cybersecops Secops Software Tools Based On Threats Introduction PDF
This slide talks about categorizing primary SecOps software tools based on threats. The purpose of this slide is to showcase the top software solutions for SecOps, including DNS security, network detection and response, anti-phishing, data discovery, and packet-level visibility. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Cybersecurity Operations Cybersecops Secops Software Tools Based On Threats Introduction PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

CASB Deployment With Standard Components Pricing Ppt PowerPoint Presentation File Example File PDF
This slide represents the cost of CASB deployment with standard components. This slide aims to showcase the pricing of classic elements for CASB deployment in an organization. The components include visibility, compliance, threat protection, and data security with Salesforce, Box, and Office 365 environments. There are so many reasons you need a CASB Deployment With Standard Components Pricing Ppt PowerPoint Presentation File Example File PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Electronic Learning Playbook Best Practices To Protect Technology Systems Cont Introduction PDF
This slide provides information regarding best practices to protect technology systems in terms of compliance with legal regulations on student privacy, internet and content filtering. Deliver an awe inspiring pitch with this creative electronic learning playbook best practices to protect technology systems cont introduction pdf bundle. Topics like deploy internet content, approve applications websites, suitable school devices can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Blockchain Security Solutions Deployment Advantages Of Blockchain Technology Brochure PDF
This slide represents the various advantages of blockchain technology based on information security, digital freedom, privacy, and lower transaction fees. Find a pre-designed and impeccable Blockchain Security Solutions Deployment Advantages Of Blockchain Technology Brochure PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Wellness Management Healthcare Industry Key Challenges Ppt Professional Portfolio PDF
This is a wellness management healthcare industry key challenges ppt professional portfolio pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like patient expectations, ageing us demographics, security, privacy, compliance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Chart Showing Technology Threats Methods And Technology For Cyber Security Ppt PowerPoint Presentation Ideas Slideshow PDF
Presenting chart showing technology threats methods and technology for cyber security ppt powerpoint presentation ideas slideshow pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including computer security attributes, attack methods, technology for internet security, confidentiality, integrity, privacy, availability. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Technology Guide For Serverless Computing Cloud Computing Challenges Infographics PDF
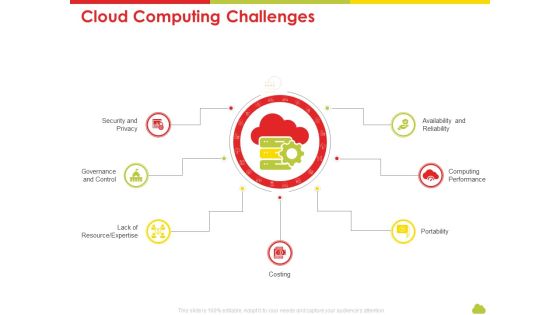
Presenting technology guide for serverless computing cloud computing challenges infographics pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like security and privacy, governance and control, portability, costing, computing performance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Mesh Computing Technology Hybrid Private Public Iaas Paas Saas Workplan Cloud Computing Challenges Download PDF
Presenting mesh computing technology hybrid private public iaas paas saas workplan cloud computing challenges download pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like portability, costing, resource, security and privacy, availability and reliability. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Machine To Machine Communication Outline Iot Security Challenges Ppt File Background Designs PDF
The slide highlights key Challenges in IoT security. Presenting machine to machine communication outline iot security challenges ppt file background designs pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like authentication, access control, privacy, policy enforcement, trust, mobile security, secure middleware, confidentiality. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
Matrix For Competitors Website Landscape Comparative Themes PDF
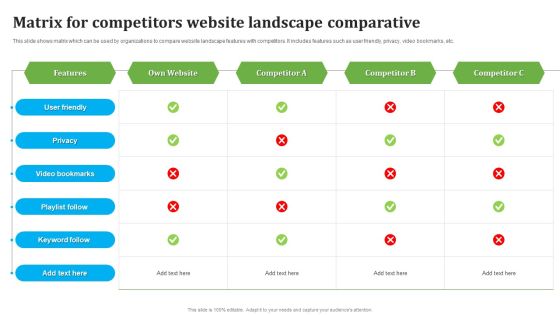
This slide shows matrix which can be used by organizations to compare website landscape features with competitors. It includes features such as user friendly, privacy, video bookmarks, etc. Pitch your topic with ease and precision using this Matrix For Competitors Website Landscape Comparative Themes PDF. This layout presents information onMatrix Competitors, Website Landscape Comparative . It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Dollars With Lock And Chain Money Investment PowerPoint Templates And PowerPoint Themes 1012
Dollars With Lock And Chain Money Investment PowerPoint Templates And PowerPoint Themes 1012-Create dynamic Microsoft office PPT Presentations with our professional templates containing a graphic of dollars with lock and chain. This image signifies the concept of data security and money investment. This image has been conceived to enable you to emphatically communicate your ideas in your Business and Financial PPT presentations on finance, protection and banking. Our PPT images are so perfectly designed that it reveals the very basis of our PPT template to make your clients understand.-Dollars With Lock And Chain Money Investment PowerPoint Templates And PowerPoint Themes 1012-This PowerPoint template can be used for presentations relating to-Dollars chained and locked, business, security, finance, money, chains

Stock Photo Internet Symbol With Lock PowerPoint Slide
This image slide displays internet symbol with lock. This conceptual image slide has been designed with graphic of blue color at the rate symbol and lock. This image slide depicts online security. Use this PowerPoint template, in your presentations to express views on e-mail, internet, security, safeguard, password and privacy. This image may also be used to exhibit technology protection. This wonderful image is sure to help you achieve your goal of making professional presentations.

Future Of Cloud Access Security Broker CASB 2 0 Ppt PowerPoint Presentation File Outline PDF
This slide outlines the overview of cloud access security broker 2.0. The purpose of this slide is to showcase the various limitations of CASB version 1.0 and the emerging need for CASB 2.0. The components of CASB 2.0 include user authentication, web security, data loss prevention, advanced malware protection, etc. Explore a selection of the finest Future Of Cloud Access Security Broker CASB 2 0 Ppt PowerPoint Presentation File Outline PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Future Of Cloud Access Security Broker CASB 2 0 Ppt PowerPoint Presentation File Outline PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Benefits Of Secure Access Service Edge SASE Ppt Pictures Demonstration PDF
This slide outlines the key benefits of secure access service edge. The purpose of this slide is to showcase the advantages of the SASE model, such as flexibility, cost savings, reduced complexity, increased performance, threat and data protection and increased network performance. This Benefits Of Secure Access Service Edge SASE Ppt Pictures Demonstration PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Challenges Of Business Software Applications And Benefits Offered By Playbook Mockup PDF
This template covers challenges of software applications development and deployment within the company. It also includes solutions and processes that benefit CIOs, business owners, and developers.Deliver an awe inspiring pitch with this creative Challenges Of Business Software Applications And Benefits Offered By Playbook Mockup PDF bundle. Topics like Company Mission, Security And Privacy, Limited Technical can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

COVID 19 Mitigating Impact On High Tech Industry The Impact Of COVID 19 On Internet Of Things Brochure PDF
Presenting this set of slides with name covid 19 mitigating impact on high tech industry the impact of covid 19 on internet of things brochure pdf. The topics discussed in these slides are positive impact, iot vendors, negative impact iot vendors, impact not clear, enterprise technology needs, technology general, iot technology, specific iot applications, iot security and privacy, people and relationship. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Core Components Of Online Certificate System Ppt Pictures Outline PDF
This slide showcase the advantages and effects of digital certificate. It includes benefits such as privacy, flexibility, excellent to use and cost effective. Showcasing this set of slides titled Core Components Of Online Certificate System Ppt Pictures Outline PDF. The topics addressed in these templates are Extension Fields, Certificate, Validity Duration. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Information Security And Risk Management User Spending By Segment Cybersecurity Risk Assessment Rules PDF
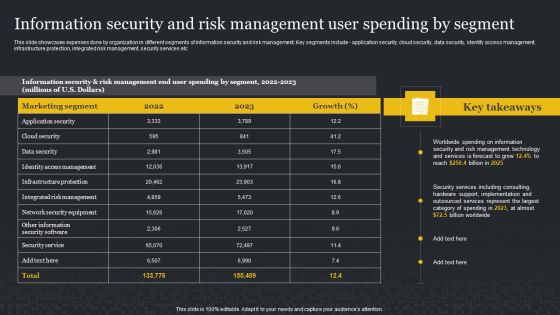
This slide showcases expenses done by organization in different segments of information security and risk management. Key segments include application security, cloud security, data security, identify access management, infrastructure protection, integrated risk management, security services etc. This Information Security And Risk Management User Spending By Segment Cybersecurity Risk Assessment Rules PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Cyber Security Automation Framework Impacts Of Ineffective Information Technology Security Demonstration PDF
This slide highlights the impacts of ineffective information technology security at organization level which includes average cost of security, average time to identify data breach and total legitimate risks. Create an editable Cyber Security Automation Framework Impacts Of Ineffective Information Technology Security Demonstration PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Cyber Security Automation Framework Impacts Of Ineffective Information Technology Security Demonstration PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

IT Security Automation Systems Guide Impacts Of Ineffective Information Technology Security Infographics PDF
This slide highlights the impacts of ineffective information technology security at organization level which includes average cost of security, average time to identify data breach and total legitimate risks. Get a simple yet stunning designed IT Security Automation Systems Guide Impacts Of Ineffective Information Technology Security Infographics PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit IT Security Automation Systems Guide Impacts Of Ineffective Information Technology Security Infographics PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Budget For Information Security Risk Management Information Security Risk Administration Guidelines PDF
This slide showcases budget that can should be allocated for different information security risk management activities. It provides information about employees training, software implementation, risk monitoring and data backup.Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Budget For Information Security Risk Management Information Security Risk Administration Guidelines PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Budget For Information Security Risk Management Information Security Risk Administration Guidelines PDF.

Zero Trust Network Access User Flow Overview Mockup PDF
This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. Create an editable Zero Trust Network Access User Flow Overview Mockup PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Zero Trust Network Access User Flow Overview Mockup PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Developing IT Security Strategy Budget For Information Security Risk Management Information PDF
This slide showcases budget that can should be allocated for different information security risk management activities. It provides information about employees training, software implementation, risk monitoring and data backup. This Developing IT Security Strategy Budget For Information Security Risk Management Information PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Developing IT Security Strategy Budget For Information Security Risk Management Information PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Organizing Security Awareness Need For Cyber Security Awareness Training Rules PDF
The purpose of this slide is to highlight the importance of conducting cyber security awareness training. It provides information about the prevention from cyber attack and data breach, build a culture of cyber security, to robust technological defenses etc. Are you searching for a Organizing Security Awareness Need For Cyber Security Awareness Training Rules PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort youve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Organizing Security Awareness Need For Cyber Security Awareness Training Rules PDF from Slidegeeks today.

Developing IT Security Strategy Information Security And Risk Management User Spending Structure PDF
This slide showcases expenses done by organization in different segments of information security and risk management. Key segments include - application security, cloud security, data security, identify access management, infrastructure protection, integrated risk management, security services etc. Present like a pro with Developing IT Security Strategy Information Security And Risk Management User Spending Structure PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Asset Identification For Information Security Risk Management Information Security Risk Administration Information PDF
This slide showcases identification of asset which can help organization to formulate risk monitoring plan. It can help to monitor the asset in real time for any data breach or cyber attack. Slidegeeks has constructed Asset Identification For Information Security Risk Management Information Security Risk Administration Information PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Key Characteristics Of Modern ZTNA Solution Portrait PDF
This slide outlines the top features that a modern ZTNA model should include. This slide highlights the characteristics of modern ZTNA solutions, including data loss prevention, scalable performance, granular visibility and reporting, BYOD deployment options, advanced threat protection, and SASE offering. Are you searching for a Key Characteristics Of Modern ZTNA Solution Portrait PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Key Characteristics Of Modern ZTNA Solution Portrait PDF from Slidegeeks today.

Developing IT Security Strategy Checklist For Information Security Risk Management Pictures PDF
This slide showcases checklist that can help to ensure formulate and implementing data security risk management program in organization. Its key components are activity, assigned to and status. Explore a selection of the finest Developing IT Security Strategy Checklist For Information Security Risk Management Pictures PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Developing IT Security Strategy Checklist For Information Security Risk Management Pictures PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Cyber Security Automation Framework Security Automation Architecture With Key Elements Rules PDF
This slide showcases the architecture of security automation which includes security automation logs, security admin, policy server, active directory, reputation feeds and other data sources. This modern and well arranged Cyber Security Automation Framework Security Automation Architecture With Key Elements Rules PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Information Systems Security And Risk Management Plan Asset Identification For Information Security Risk Management Background PDF
This slide showcases identification of asset which can help organization to formulate risk monitoring plan. It can help form to monitor the asset in real time for any data breach or cyber attack. Take your projects to the next level with our ultimate collection of Information Systems Security And Risk Management Plan Asset Identification For Information Security Risk Management Background PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.

Developing IT Security Strategy Asset Identification For Information Security Risk Professional PDF
This slide showcases identification of asset which can help organization to formulate risk monitoring plan. It can help to monitor the asset in real time for any data breach or cyber attack. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Developing IT Security Strategy Asset Identification For Information Security Risk Professional PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Organizing Security Awareness Operational Outlook Of Security Awareness Training Ideas PDF
The purpose of this slide is to showcase the general outlook of cyber security awareness training software. The slide covers information about opened simulations, links clicked, reported, attachments opened, data entered etc. Retrieve professionally designed Organizing Security Awareness Operational Outlook Of Security Awareness Training Ideas PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Secure Access Service Edge Cloud Security Model Ppt PowerPoint Presentation Complete Deck With Slides
With well-researched insights and carefully-constructed design, this Secure Access Service Edge Cloud Security Model Ppt PowerPoint Presentation Complete Deck With Slides is all that you need for your next business meeting with clients and win them over. Add your data to graphs, charts, and tables that are already ready to display it with stunning visuals and help your audience recall your work. With this PPT Complete Deck, you will be able to display your knowledge of the subject as well as your skills as a communicator. Share your ideas and make an impact on the audience with this PowerPoint Layout and ensure that you are known as a presentation professional. Download this PPT Template Bundle to create the most interesting presentation anyone has ever seen.

Information Security Adhere To Strict Compliance Requirements Diagrams PDF
This slide shows that you can use a data classification engine to locate and categorize regulated and sensitive material also, compliance standards serve as a foundation. If you are looking for a format to display your unique thoughts, then the professionally designed Information Security Adhere To Strict Compliance Requirements Diagrams PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Information Security Adhere To Strict Compliance Requirements Diagrams PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Information Systems Security And Risk Management Plan Estimated Impact Of Information Security Risk Management Plan Ideas PDF
This slide showcases capabilities of organization regarding information and data security after risk management plan. Its key component are risk management functions, required standard rating and actual standard rating. This Information Systems Security And Risk Management Plan Estimated Impact Of Information Security Risk Management Plan Ideas PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The product features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Challenges With Traditional Network Security Approaches Ppt Gallery Icon PDF
This slide describes the challenges with traditional network security approaches. The purpose of this slide is to demonstrate the various challenges caused by conventional network security methods while backhauling traffic to data centers, including disjoint management, workload, slower cloud adoption, and so on. Present like a pro with Challenges With Traditional Network Security Approaches Ppt Gallery Icon PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Prevention Of Information Operational Outlook Of Security Awareness Structure PDF
The purpose of this slide is to showcase the general outlook of cyber security awareness training software. The slide covers information about opened simulations, links clicked, reported, attachments opened, data entered. Slidegeeks has constructed Prevention Of Information Operational Outlook Of Security Awareness Structure PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Need For Cyber Security Awareness Training Ppt Gallery Template PDF
The purpose of this slide is to highlight the importance of conducting cyber security awareness training. It provides information about the prevention from cyber attack and data breach, build a culture of cyber security, to robust technological defenses etc. Welcome to our selection of the Need For Cyber Security Awareness Training Ppt Gallery Template PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today
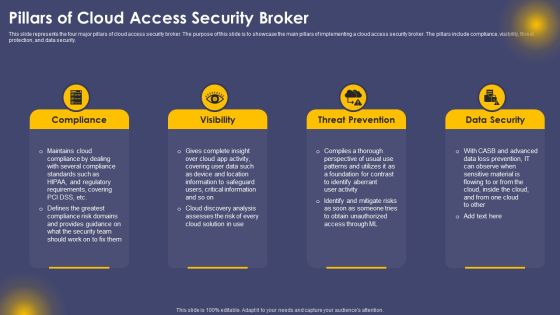
Pillars Of Cloud Access Security Broker Ppt Show Background PDF
This slide represents the four major pillars of cloud access security broker. The purpose of this slide is to showcase the main pillars of implementing a cloud access security broker. The pillars include compliance, visibility, threat protection, and data security. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Pillars Of Cloud Access Security Broker Ppt Show Background PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Pillars Of Cloud Access Security Broker Ppt Show Background PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

PCI Certification For Increasing Security Of Online Transactions Designs PDF
This slide depicts payment card industry PCI certification for increasing security of online transactions. It provides information about authorization, 2 way authentication, one time password OTP, repository, cyber attacks, compliance, data breach, etc. Presenting this PowerPoint presentation, titled PCI Certification For Increasing Security Of Online Transactions Designs PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this PCI Certification For Increasing Security Of Online Transactions Designs PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable PCI Certification For Increasing Security Of Online Transactions Designs PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Determine Role Of Security Centre In Firm Designs PDF
This slide covers information regarding the role of security center in in order to protect sensitive data and how firm behave before, after and towards security center implementation. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Determine Role Of Security Centre In Firm Designs PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Determine Role Of Security Centre In Firm Designs PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

PCI Certification For Increasing Security Of Online Transactions Background PDF
This slide depicts payment card industry PCI certification for increasing security of online transactions. It provides information about authorization, 2 way authentication, one time password OTP, repository, cyber attacks, compliance, data breach, etc. Explore a selection of the finest PCI Certification For Increasing Security Of Online Transactions Background PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our PCI Certification For Increasing Security Of Online Transactions Background PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
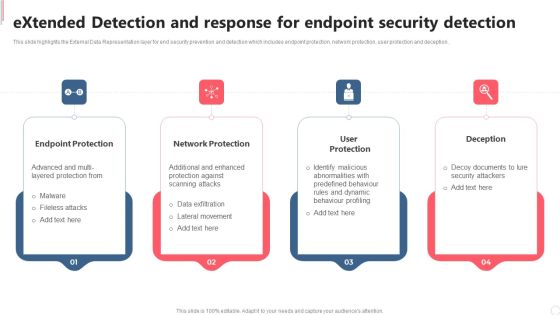
Extended Detection And Response For Endpoint Security Detection Clipart PDF
This slide highlights the External Data Representation layer for end security prevention and detection which includes endpoint protection, network protection, user protection and deception. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Extended Detection And Response For Endpoint Security Detection Clipart PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Extended Detection And Response For Endpoint Security Detection Clipart PDF today and make your presentation stand out from the rest.

Cyber Security Awareness Facts And Statistics Ppt PowerPoint Presentation File Background Images PDF
The following slide showcases some facts and figures to generate awareness about cyber-crimes. It includes elements such as hike in ransomware attacks, more employees are expected to be target of malware attacks, increasing cost of data breaches etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cyber Security Awareness Facts And Statistics Ppt PowerPoint Presentation File Background Images PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cyber Security Awareness Facts And Statistics Ppt PowerPoint Presentation File Background Images PDF

Information Security And Risk Management User Spending By Segment Portrait PDF
This slide showcases expenses done by organization in different segments of information security and risk management. Key segments include - application security, cloud security, data security, identify access management, infrastructure protection, integrated risk management, security services etc. Presenting this PowerPoint presentation, titled Information Security And Risk Management User Spending By Segment Portrait PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Information Security And Risk Management User Spending By Segment Portrait PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Information Security And Risk Management User Spending By Segment Portrait PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
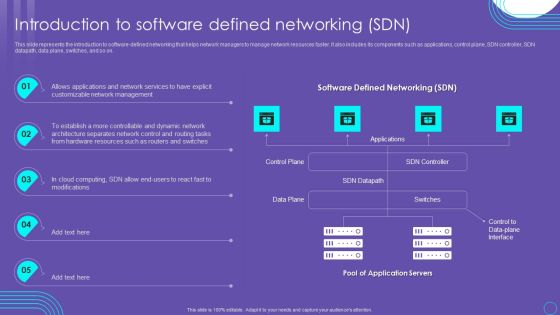
SDN Security Architecture Introduction To Software Defined Networking SDN Information PDF
This slide represents the introduction to software defined networking that helps network managers to manage network resources faster. It also includes its components such as applications, control plane, SDN controller, SDN datapath, data plane, switches, and so on. Presenting this PowerPoint presentation, titled SDN Security Architecture Introduction To Software Defined Networking SDN Information PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this SDN Security Architecture Introduction To Software Defined Networking SDN Information PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable SDN Security Architecture Introduction To Software Defined Networking SDN Information PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Security Automation To Analyze And Mitigate Cyberthreats Impacts Of Ineffective Information Designs PDF
This slide highlights the impacts of ineffective information technology security at organization level which includes average cost of security, average time to identify data breach and total legitimate risks.If you are looking for a format to display your unique thoughts, then the professionally designed Security Automation To Analyze And Mitigate Cyberthreats Impacts Of Ineffective Information Designs PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Security Automation To Analyze And Mitigate Cyberthreats Impacts Of Ineffective Information Designs PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Information Security Seven Principles Of GDPR Law Ppt PowerPoint Presentation File Inspiration PDF
This slide represents the seven principles of GDPR law, including lawfulness and transparency, purpose limitation, data minimization, accuracy, storage limitation, integrity and confidentiality, accountability. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Information Security Seven Principles Of GDPR Law Ppt PowerPoint Presentation File Inspiration PDF can be your best option for delivering a presentation. Represent everything in detail using Information Security Seven Principles Of GDPR Law Ppt PowerPoint Presentation File Inspiration PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Execution Of ICT Strategic Plan Most Commonly Types Of ICT Securities Used By Businesses Microsoft PDF
This slide represents various types of information and communication technology ICT securities used by businesses. It covers network security, endpoint security, access security, and data encryption. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Execution Of ICT Strategic Plan Most Commonly Types Of ICT Securities Used By Businesses Microsoft PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Execution Of ICT Strategic Plan Most Commonly Types Of ICT Securities Used By Businesses Microsoft PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

5G Technology Development For Digital Transformation Key Security Considerations For 5G For Threat Handling Themes PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download 5G Technology Development For Digital Transformation Key Security Considerations For 5G For Threat Handling Themes PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the 5G Technology Development For Digital Transformation Key Security Considerations For 5G For Threat Handling Themes PDF.

Prevention Of Information Need For Cyber Security Awareness Training Graphics PDF
The purpose of this slide is to highlight the importance of conducting cyber security awareness training. It provides information about the prevention from cyber attack and data breach, build a culture of cyber security, to robust technological defenses etc. Retrieve professionally designed Prevention Of Information Need For Cyber Security Awareness Training Graphics PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Prevention Of Information Key Benefits Of Cyber Security Awareness Training Inspiration PDF
The purpose of this slide is to delineate several advantages of security awareness training. Driving awareness, reducing data breach threat, prevention of downtime and improving the customer confidence are some of the key benefits which are highlighted in the slide. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Prevention Of Information Key Benefits Of Cyber Security Awareness Training Inspiration PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Prevention Of Information Key Benefits Of Cyber Security Awareness Training Inspiration PDF

Estimated Impact Of Information Security Risk Management Plan Cybersecurity Risk Assessment Rules PDF
This slide showcases capabilities of organization regarding information and data security after risk management plan. Its key component are risk management functions, required standard rating and actual standard rating. Explore a selection of the finest Estimated Impact Of Information Security Risk Management Plan Cybersecurity Risk Assessment Rules PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Estimated Impact Of Information Security Risk Management Plan Cybersecurity Risk Assessment Rules PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Cyber Security Awareness Training Program Improving Cybersecurity With Incident Microsoft PDF
This slide portrays statistical information about cyber threats. Information covered is related data breach, ransomware attacks, cyberthreat complaints and phishing attack.Purpose of this slide is to provide information about the cyber security awareness training program to be conducted for in-house team. It also provides the details about training types, content types and audience.Whether you have daily or monthly meetings, a brilliant presentation is necessary. Cyber Security Awareness Training Program Improving Cybersecurity With Incident Microsoft PDF can be your best option for delivering a presentation. Represent everything in detail using Cyber Security Awareness Training Program Improving Cybersecurity With Incident Microsoft PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
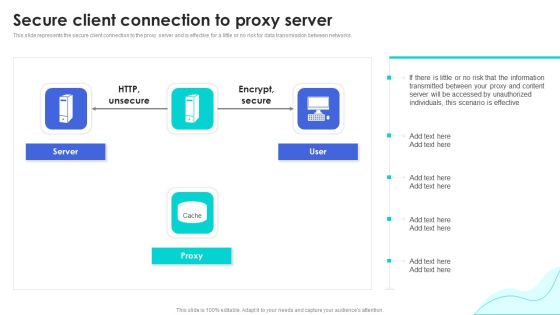
Reverse Proxy Web Server Secure Client Connection To Proxy Server Themes PDF
This slide represents the secure client connection to the proxy server and is effective for a little or no risk for data transmission between networks. Presenting this PowerPoint presentation, titled Reverse Proxy Web Server Secure Client Connection To Proxy Server Themes PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Reverse Proxy Web Server Secure Client Connection To Proxy Server Themes PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Reverse Proxy Web Server Secure Client Connection To Proxy Server Themes PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Impact Of Cyber Security Policies And Practices Ppt PowerPoint Presentation Diagram Graph Charts PDF
The following slide focuses on drafting cyber security policies to manage data control and breach. It mainly includes elements such as impact of existing cyber safety policies, mitigation actions, Presenting this PowerPoint presentation, titled Impact Of Cyber Security Policies And Practices Ppt PowerPoint Presentation Diagram Graph Charts PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Impact Of Cyber Security Policies And Practices Ppt PowerPoint Presentation Diagram Graph Charts PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Impact Of Cyber Security Policies And Practices Ppt PowerPoint Presentation Diagram Graph Charts PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Cloud Access Security Broker CASB Introduction Ppt PowerPoint Presentation File Portfolio PDF
This slide outlines the overview and benefits of cloud access security broker. The purpose of this slide is to demonstrate the benefits of CASB, such as risk visibility, threat prevention, granular cloud usage control, shadow IT assessment and management, and data loss prevention. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Cloud Access Security Broker CASB Introduction Ppt PowerPoint Presentation File Portfolio PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Cloud Access Security Broker CASB Introduction Ppt PowerPoint Presentation File Portfolio PDF.

Information Security Accountability Principle Of GDPR Law Ppt PowerPoint Presentation File Backgrounds PDF
This slide shows the accountability principle, which implies that the data controller or organization is responsible for adhering to all the standards of GDPR and showing compliance if required. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Information Security Accountability Principle Of GDPR Law Ppt PowerPoint Presentation File Backgrounds PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
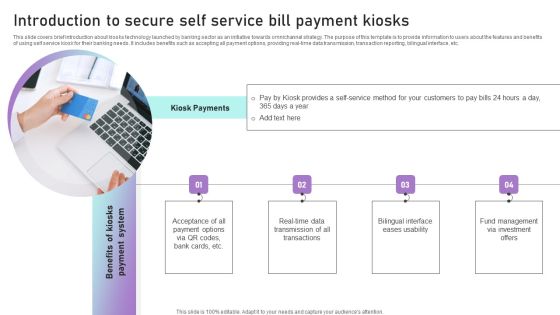
Introduction To Secure Self Service Bill Payment Kiosks Ppt Outline Grid PDF
This slide covers brief introduction about kiosks technology launched by banking sector as an initiative towards omnichannel strategy. The purpose of this template is to provide information to users about the features and benefits of using self service kiosk for their banking needs. It includes benefits such as accepting all payment options, providing real-time data transmission, transaction reporting, bilingual interface, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Introduction To Secure Self Service Bill Payment Kiosks Ppt Outline Grid PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Determine Cyber Security Risks And Threats Ppt PowerPoint Presentation Diagram Lists PDF
The following slide highlights cyber security risks and threats identified within the company to analyze and protect from potential loss. It includes elements such as objectives, issue identifier, malware, phishing, ransomware, weak credentials, data breach etc. This Determine Cyber Security Risks And Threats Ppt PowerPoint Presentation Diagram Lists PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Determine Cyber Security Risks And Threats Ppt PowerPoint Presentation Diagram Lists PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

CYBER Security Breache Response Strategy Cyber Attacks Faced By The Company In Previous Year Information PDF
This slide represents the attacks faced by the organization which led to theft of confidential data and sensitive information of the organization. It represents the increase in ransomware and phishing attacks experienced by the enterprise within 5 years. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give CYBER Security Breache Response Strategy Cyber Attacks Faced By The Company In Previous Year Information PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable CYBER Security Breache Response Strategy Cyber Attacks Faced By The Company In Previous Year Information PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Cashless Payment Strategies To Enhance Business Performance Best Practices To Maintain Digital Wallet Security Brochure PDF
Mentioned slide exhibits various best practices which can be implemented by followed by businesses to secure e-wallets. It includes best practices such as enable passwords, secure network connections, install reliable applications, secure login credentials, and keep personal data private. Retrieve professionally designed Cashless Payment Strategies To Enhance Business Performance Best Practices To Maintain Digital Wallet Security Brochure PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Checklist For Information Security Risk Management Cybersecurity Risk Assessment Summary PDF
This slide showcases checklist that can help to ensure formulate and implementing data security risk management program in organization. Its key components are activity, assigned to and status. Do you know about Slidesgeeks Checklist For Information Security Risk Management Cybersecurity Risk Assessment Summary PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

Omnichannel Banking Services Platform Introduction To Secure Self Service Bill Payment Kiosks Icons PDF
This slide covers brief introduction about kiosks technology launched by banking sector as an initiative towards omnichannel strategy. The purpose of this template is to provide information to users about the features and benefits of using self service kiosk for their banking needs. It includes benefits such as accepting all payment options, providing real-time data transmission, transaction reporting, bilingual interface, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Omnichannel Banking Services Platform Introduction To Secure Self Service Bill Payment Kiosks Icons PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Omnichannel Banking Services Platform Introduction To Secure Self Service Bill Payment Kiosks Icons PDF today and make your presentation stand out from the rest.

Omnichannel Strategy Implementation For Banking Solutions Introduction To Secure Self Service Bill Payment Formats PDF
This slide covers brief introduction about kiosks technology launched by banking sector as an initiative towards omnichannel strategy. The purpose of this template is to provide information to users about the features and benefits of using self service kiosk for their banking needs. It includes benefits such as accepting all payment options, providing real-time data transmission, transaction reporting, bilingual interface, etc. Present like a pro with Omnichannel Strategy Implementation For Banking Solutions Introduction To Secure Self Service Bill Payment Formats PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
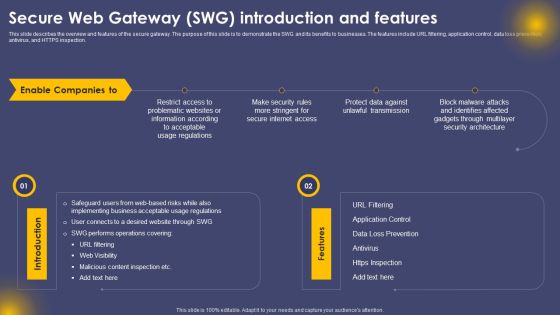
Secure Web Gateway SWG Introduction And Features Ppt Portfolio Master Slide PDF
This slide describes the overview and features of the secure gateway. The purpose of this slide is to demonstrate the SWG and its benefits to businesses. The features include URL filtering, application control, data loss prevention, antivirus, and HTTPS inspection. Present like a pro with Secure Web Gateway SWG Introduction And Features Ppt Portfolio Master Slide PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
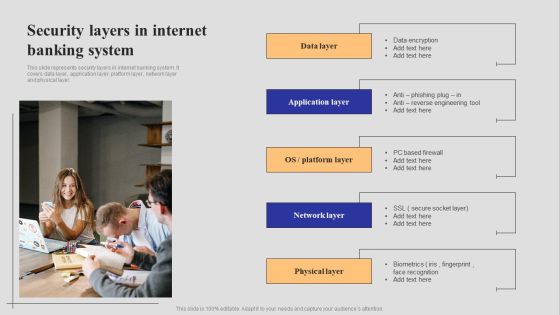
Introduction To Digital Banking Services Security Layers In Internet Banking System Guidelines PDF
This slide represents security layers in internet banking system. It covers data layer, application layer, platform layer, network layer and physical layer. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Introduction To Digital Banking Services Security Layers In Internet Banking System Guidelines PDF can be your best option for delivering a presentation. Represent everything in detail using Introduction To Digital Banking Services Security Layers In Internet Banking System Guidelines PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Deployment Of Omnichannel Banking Solutions Introduction To Secure Self Service Bill Payment Kiosks Portrait PDF
This slide covers brief introduction about kiosks technology launched by banking sector as an initiative towards omnichannel strategy. The purpose of this template is to provide information to users about the features and benefits of using self service kiosk for their banking needs. It includes benefits such as accepting all payment options, providing real-time data transmission, transaction reporting, bilingual interface, etc. Slidegeeks has constructed Deployment Of Omnichannel Banking Solutions Introduction To Secure Self Service Bill Payment Kiosks Portrait PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

Benefits Of Cloud Access Security Broker Ppt PowerPoint Presentation File Model PDF
This slide outlines the different advantages of cloud access security broker technology. This slide highlights the pros of CASB technology, including risk visibility, cyber threat prevention, granular cloud usage control, shadow IT assessment and management, DLP, managing privileged accounts and admin and controlled data sharing. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Benefits Of Cloud Access Security Broker Ppt PowerPoint Presentation File Model PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Benefits Of Cloud Access Security Broker Ppt PowerPoint Presentation File Model PDF.
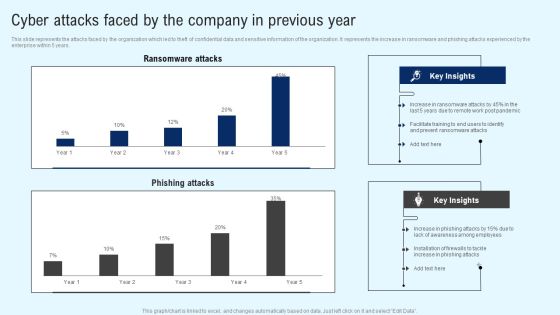
Implementing Cyber Security Incident Cyber Attacks Faced By The Company In Previous Year Information PDF
This slide represents the attacks faced by the organization which led to theft of confidential data and sensitive information of the organization. It represents the increase in ransomware and phishing attacks experienced by the enterprise within 5 years. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Implementing Cyber Security Incident Cyber Attacks Faced By The Company In Previous Year Information PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

SDN Security Architecture Working Of Software Defined Networking SDN Rules PDF
This slide describes the working of software defined networking, including its various components such as SDN applications, northbound and southbound interfaces, SDN controller, application plane, control plane and data plane. Slidegeeks is here to make your presentations a breeze with SDN Security Architecture Working Of Software Defined Networking SDN Rules PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first

Cloud Access Security Broker Pillar Overview Ppt PowerPoint Presentation File Infographics PDF
This slide represents the four major pillars of cloud access security broker. The purpose of this slide is to showcase the main pillars of implementing a cloud access security broker. The pillars include compliance, visibility, threat protection, and data security. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Cloud Access Security Broker Pillar Overview Ppt PowerPoint Presentation File Infographics PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Cloud Access Security Broker Pillar Overview Ppt PowerPoint Presentation File Infographics PDF today and make your presentation stand out from the rest.

Implementing Cybersecurity Awareness Program To Prevent Attacks Need For Cyber Security Awareness Training Background PDF
The purpose of this slide is to highlight the importance of conducting cyber security awareness training. It provides information about the prevention from cyber attack and data breach, build a culture of cyber security, to robust technological defenses etc. Retrieve professionally designed Implementing Cybersecurity Awareness Program To Prevent Attacks Need For Cyber Security Awareness Training Background PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Execution Of ICT Strategic Plan Key ICT Security Measures Used By Businesses Ideas PDF
This slide represents essential information and communication technology ICT security measures businesses use. It covers strong password authentication, data backup, network access control, etc. Create an editable Execution Of ICT Strategic Plan Key ICT Security Measures Used By Businesses Ideas PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Execution Of ICT Strategic Plan Key ICT Security Measures Used By Businesses Ideas PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Omnichannel Services Solution In Financial Sector Introduction To Secure Self Service Bill Payment Kiosks Mockup PDF
This slide covers brief introduction about kiosks technology launched by banking sector as an initiative towards omnichannel strategy. The purpose of this template is to provide information to users about the features and benefits of using self service kiosk for their banking needs. It includes benefits such as accepting all payment options, providing real-time data transmission, transaction reporting, bilingual interface, etc. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Omnichannel Services Solution In Financial Sector Introduction To Secure Self Service Bill Payment Kiosks Mockup PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.

Comprehensive Guide For Ensuring IT Infrastructure Security Ppt PowerPoint Presentation Complete Deck With Slides
With well-researched insights and carefully-constructed design, this Comprehensive Guide For Ensuring IT Infrastructure Security Ppt PowerPoint Presentation Complete Deck With Slides is all that you need for your next business meeting with clients and win them over. Add your data to graphs, charts, and tables that are already ready to display it with stunning visuals and help your audience recall your work. With this PPT Complete Deck, you will be able to display your knowledge of the subject as well as your skills as a communicator. Share your ideas and make an impact on the audience with this PowerPoint Layout and ensure that you are known as a presentation professional. Download this PPT Template Bundle to create the most interesting presentation anyone has ever seen.

Enhancing Cloud Security With CASB Ppt PowerPoint Presentation Complete Deck With Slides
With well-researched insights and carefully-constructed design, this Enhancing Cloud Security With CASB Ppt PowerPoint Presentation Complete Deck With Slides is all that you need for your next business meeting with clients and win them over. Add your data to graphs, charts, and tables that are already ready to display it with stunning visuals and help your audience recall your work. With this PPT Complete Deck, you will be able to display your knowledge of the subject as well as your skills as a communicator. Share your ideas and make an impact on the audience with this PowerPoint Layout and ensure that you are known as a presentation professional. Download this PPT Template Bundle to create the most interesting presentation anyone has ever seen.

Cloud Access Security Broker Pillar Compliance Ppt PowerPoint Presentation File Layouts PDF
This slide gives an overview of the compliance pillar of cloud access security broker. The purpose of this slide is to showcase how compliance is a vital factor for an organization migrating its data and systems to the cloud. Compliance can help industries such as healthcare, retail, and financial services. Present like a pro with Cloud Access Security Broker Pillar Compliance Ppt PowerPoint Presentation File Layouts PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Damage Security Insurance Proposal Gantt Chart Ppt Gallery Graphic Tips PDF
Your complex projects can be managed and organized simultaneously using this detailed damage security insurance proposal gantt chart ppt gallery graphic tips pdf template. Track the milestones, tasks, phases, activities, and subtasks to get an updated visual of your project. Share your planning horizon and release plan with this well crafted presentation template. This exemplary template can be used to plot various dependencies to distinguish the tasks in the pipeline and their impact on the schedules and deadlines of the project. Apart from this, you can also share this visual presentation with your team members and stakeholders. It a resourceful tool that can be incorporated into your business structure. Therefore, download and edit it conveniently to add the data and statistics as per your requirement.

SDN Security Architecture Use Cases Of Software Defined Networking SDN Formats PDF
This slide represents the use cases of software defined networking, a developing technology that will eventually replace physical network designs with software controlled networking architecture. It shows its use in DevOps, campus networks, service provider networks, and data center security. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give SDN Security Architecture Use Cases Of Software Defined Networking SDN Formats PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable SDN Security Architecture Use Cases Of Software Defined Networking SDN Formats PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today

CYBER Security Breache Response Strategy Impact Of Cybersecurity Incidents On Organization Template PDF
This slide represents the impact of events which indicates that organizations data has been compromised for unlawful activities. It includes impact of cyber security events such as increased costs, operational disruption, reputational damage etc. Presenting this PowerPoint presentation, titled CYBER Security Breache Response Strategy Impact Of Cybersecurity Incidents On Organization Template PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this CYBER Security Breache Response Strategy Impact Of Cybersecurity Incidents On Organization Template PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable CYBER Security Breache Response Strategy Impact Of Cybersecurity Incidents On Organization Template PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Organizations Risk Management And IT Security Impact Of IT Risks On Organization Structure PDF
This slide highlights the impacts of information technology risks on organization which includes graph for overspend project budget and data breach for 2021 year. Explore a selection of the finest Organizations Risk Management And IT Security Impact Of IT Risks On Organization Structure PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Organizations Risk Management And IT Security Impact Of IT Risks On Organization Structure PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
Operational Outlook Of Security Awareness Training Software Ppt Icon Slideshow PDF
The purpose of this slide is to showcase the general outlook of cyber security awareness training software. The slide covers information about opened simulations, links clicked, reported, attachments opened, data entered etc. Explore a selection of the finest Operational Outlook Of Security Awareness Training Software Ppt Icon Slideshow PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Operational Outlook Of Security Awareness Training Software Ppt Icon Slideshow PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Implementing Cybersecurity Awareness Program To Prevent Attacks Key Benefits Of Cyber Security Awareness Clipart PDF
The purpose of this slide is to delineate several advantages of security awareness training. Driving awareness, reducing data breach threat, prevention of downtime and improving the customer confidence are some of the key benefits which are highlighted in the slide. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Implementing Cybersecurity Awareness Program To Prevent Attacks Key Benefits Of Cyber Security Awareness Clipart PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Implementing Cybersecurity Awareness Program To Prevent Attacks Key Benefits Of Cyber Security Awareness Clipart PDF
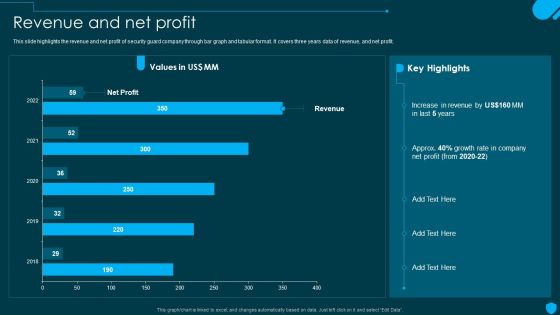
Security And Human Resource Services Business Profile Revenue And Net Profit Designs PDF
This slide highlights the revenue and net profit of security guard company through bar graph and tabular format. It covers three years data of revenue, and net profit. Explore a selection of the finest Security And Human Resource Services Business Profile Revenue And Net Profit Designs PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Security And Human Resource Services Business Profile Revenue And Net Profit Designs PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
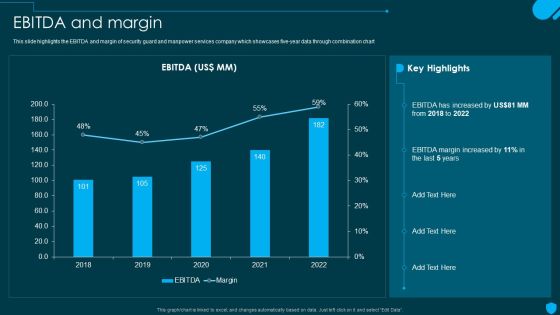
Security And Human Resource Services Business Profile EBITDA And Margin Ideas PDF
This slide highlights the EBITDA and margin of security guard and manpower services company which showcases five-year data through combination chart. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Security And Human Resource Services Business Profile EBITDA And Margin Ideas PDF can be your best option for delivering a presentation. Represent everything in detail using Security And Human Resource Services Business Profile EBITDA And Margin Ideas PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Deploying Cyber Security Incident Response Administration Impact Of Cybersecurity Incidents On Organization Microsoft PDF
This slide represents the impact of events which indicates that organizations data has been compromised for unlawful activities. It includes impact of cyber security events such as increased costs, operational disruption, reputational damage etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Deploying Cyber Security Incident Response Administration Impact Of Cybersecurity Incidents On Organization Microsoft PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Deploying Cyber Security Incident Response Administration Impact Of Cybersecurity Incidents On Organization Microsoft PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Key Benefits Of Cyber Security Awareness Training Ppt Model Mockup PDF
The purpose of this slide is to delineate several advantages of security awareness training. Driving awareness, reducing data breach threat, prevention of downtime and improving the customer confidence are some of the key benefits which are highlighted in the slide. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Key Benefits Of Cyber Security Awareness Training Ppt Model Mockup PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Key Benefits Of Cyber Security Awareness Training Ppt Model Mockup PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers

Cloud Access Security Broker Casb Overview Ppt Professional Design Inspiration PDF
This slide outlines the overview and benefits of cloud access security broker. The purpose of this slide is to demonstrate the benefits of CASB, such as risk visibility, threat prevention, granular cloud usage control, shadow IT assessment and management, and data loss prevention. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Cloud Access Security Broker Casb Overview Ppt Professional Design Inspiration PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Cloud Access Security Broker Casb Overview Ppt Professional Design Inspiration PDF today and make your presentation stand out from the rest.

Implementing Cyber Security Incident Impact Of Cybersecurity Incidents On Organization Graphics PDF
This slide represents the impact of events which indicates that organizations data has been compromised for unlawful activities. It includes impact of cyber security events such as increased costs, operational disruption, reputational damage etc. Get a simple yet stunning designed Implementing Cyber Security Incident Impact Of Cybersecurity Incidents On Organization Graphics PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Implementing Cyber Security Incident Impact Of Cybersecurity Incidents On Organization Graphics PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
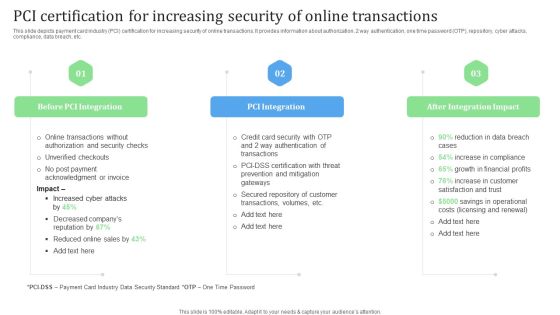
PCI Certification For Increasing Security Of Online Transactions Financial Management Strategies Ideas PDF
This slide depicts payment card industry PCI certification for increasing security of online transactions. It provides information about authorization, 2 way authentication, one time password OTP, repository, cyber attacks, compliance, data breach, etc. Slidegeeks has constructed PCI Certification For Increasing Security Of Online Transactions Financial Management Strategies Ideas PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

KYC Transaction Monitoring System Business Security Analyzing Impact On Key Operations Ideas PDF
This slide showcases assessing impact on major operations and workflows. It provides information about customer understanding, knowledge, data management, financial risk management, customer relationship management, client onboarding, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download KYC Transaction Monitoring System Business Security Analyzing Impact On Key Operations Ideas PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the KYC Transaction Monitoring System Business Security Analyzing Impact On Key Operations Ideas PDF.

Implementing Cybersecurity Awareness Program To Prevent Attacks Operational Outlook Of Security Awareness Elements PDF
The purpose of this slide is to showcase the general outlook of cyber security awareness training software. The slide covers information about opened simulations, links clicked, reported, attachments opened, data entered etc. Slidegeeks has constructed Implementing Cybersecurity Awareness Program To Prevent Attacks Operational Outlook Of Security Awareness Elements PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

KYC Transaction Monitoring System Business Security Determining Residual Risks Topics PDF
This slide showcases assessment matrix to determine residual risks. It provides information about inherent risks, control assessment, satisfaction, visibility, risk management controls, data analytics, etc. Explore a selection of the finest KYC Transaction Monitoring System Business Security Determining Residual Risks Topics PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our KYC Transaction Monitoring System Business Security Determining Residual Risks Topics PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Impact Of Cyber Safety Security Measures Ppt PowerPoint Presentation File Layouts PDF
The following slide depicts the projected consequences of implementing cyber security preventive measures. It includes data about number of cyber attracts pre and post adopting latest strategies. Slidegeeks has constructed Impact Of Cyber Safety Security Measures Ppt PowerPoint Presentation File Layouts PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

Security Software Company Investor Funding Pitch Deck Org Structure Guidelines PDF
This slide showcases the organization structure of an IT company which includes CEO, chief architect, VP marketing, VP sales, chief data scientist, chief scientist, VP product, VP engineering, founding BOD, former board member, founder, former CEO. Find highly impressive Security Software Company Investor Funding Pitch Deck Org Structure Guidelines PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Security Software Company Investor Funding Pitch Deck Org Structure Guidelines PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

CYBER Security Breache Response Strategy Best Practices For Cybersecurity Incident Management Ideas PDF
This slide represents the impact of events which indicates that organizations data has been compromised for unlawful activities. It includes impact of cyber security events such as increased costs, operational disruption, reputational damage etc. Boost your pitch with our creative CYBER Security Breache Response Strategy Best Practices For Cybersecurity Incident Management Ideas PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Deploying Cyber Security Incident Response Administration Cyber Attacks Faced By The Company Sample PDF
This slide represents the attacks faced by the organization which led to theft of confidential data and sensitive information of the organization. It represents the increase in ransomware and phishing attacks experienced by the enterprise within 5 years. Get a simple yet stunning designed Deploying Cyber Security Incident Response Administration Cyber Attacks Faced By The Company Sample PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Deploying Cyber Security Incident Response Administration Cyber Attacks Faced By The Company Sample PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

KYC Transaction Monitoring System Business Security Timeline Implementing Transaction Summary PDF
This slide showcases timeline to introduce transaction monitoring system. It provides information about scenario planning, threshold setting, deployment, project management office PMO, project planning, scenario identification, data source identification, etc. Get a simple yet stunning designed KYC Transaction Monitoring System Business Security Timeline Implementing Transaction Summary PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit KYC Transaction Monitoring System Business Security Timeline Implementing Transaction Summary PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Organizations Risk Management And IT Security Damage Control Assessment From IT Risk Management Demonstration PDF
This slide highlights the damage control form information technology risk management strategies which includes data breach, cyber threats, social engineering attacks, domain based threats and increase in business opportunities. This modern and well arranged Organizations Risk Management And IT Security Damage Control Assessment From IT Risk Management Demonstration PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
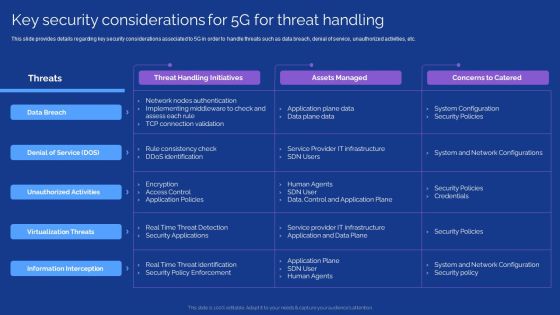
Development Guide For 5G World Key Security Considerations For 5G For Threat Handling Slides PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. This modern and well arranged Development Guide For 5G World Key Security Considerations For 5G For Threat Handling Slides PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Secure Web Gateways SWG Setup And Working Ppt Show Tips PDF
This slide depicts the methods to setup the secure web gateways and their working. The purpose of this slide is to demonstrate the various ways in which organizations can install the SWGs. It also caters to the working and functions performed by SWGs to protect data and safe browsing on the internet. Slidegeeks is here to make your presentations a breeze with Secure Web Gateways SWG Setup And Working Ppt Show Tips PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Workplace Security Management Program Ppt PowerPoint Presentation Complete Deck With Slides
Using this ready-made PowerPoint slide, you can incorporate your own data to make an impact with your business innovation and clarity of goals. Use this brilliantly designed Workplace Security Management Program Ppt PowerPoint Presentation Complete Deck With Slides to showcase how ultimately all business concepts are related. This presentation template can also be used to record resource allocation in a visual form. The twenty one Slide Workplace Security Management Program Ppt PowerPoint Presentation Complete Deck With Slides is suitable for all your business needs, where you need to make sure that all bases are covered. Download this PPT template now to start a journey on your chosen business, with customer satisfaction the key aim.

Security Software Company Investor Funding Pitch Deck Core Team Guidelines PDF
The following slide showcases key personnel of executive team of IT company which are CEO, chief architect, VP marketing, sales, product, engineering, chief data scientist, chief scientist, etc. Get a simple yet stunning designed Security Software Company Investor Funding Pitch Deck Core Team Guidelines PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Security Software Company Investor Funding Pitch Deck Core Team Guidelines PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Cybersecurity Operations Cybersecops Challenges And Solutions Of Security Operations Graphics PDF
This slide outlines the key challenges and solutions of security operations centers. The purpose of this slide is to highlight the problems faced by SOC teams and methods to overcome those problems. The main challenges include talent gaps, sophisticated attackers, increased data and network traffic, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Cybersecurity Operations Cybersecops Challenges And Solutions Of Security Operations Graphics PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Organizations Risk Management And IT Security Ppt PowerPoint Presentation Complete With Slides
This presentation deck enables you to communicate the message, idea, and proposal to your audience in a clear and effective manner. The slides of this PowerPoint Bundle are professional and visually appealing, engaging your audience and gaining their heartful interest in your content. In addition to its spectacular design, this PPT deck is easy to use and altered to fit the specific needs of the user. All fifty one slides in this set are compatible with multiple data handling and presentation platforms like Google Slides, MS Excel, Tableau, etc., so you can present your information hassle free. Begin your journey to tremendous success using our Organizations Risk Management And IT Security Ppt PowerPoint Presentation Complete With Slides in many settings, including meetings, pitches, and conference presentations In fact, customer testimonials.

Organizations Risk Management And IT Security Top IT Risks Reported At The Workplace Brochure PDF
This slide highlights the top IT risks reported at workplace which includes cyber threats, data loss, social engineering attacks, regulatory incidents, domain based threats and denial of service. Slidegeeks has constructed Organizations Risk Management And IT Security Top IT Risks Reported At The Workplace Brochure PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.
SDN Security Architecture Importance Of Virtualization In Software Defined Networking Icons PDF
This slide represents the importance of virtualization in software defined networking and how they complement one another. It also includes how SDN helps simplify the process of controlling data packet routing via a central server. Retrieve professionally designed SDN Security Architecture Importance Of Virtualization In Software Defined Networking Icons PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
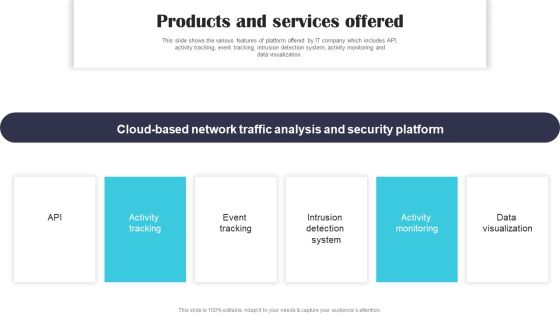
Security Software Company Investor Funding Pitch Deck Products And Services Offered Clipart PDF
This slide shows the various features of platform offered by IT company which includes API, activity tracking, event tracking, intrusion detection system, activity monitoring and data visualization. This modern and well arranged Security Software Company Investor Funding Pitch Deck Products And Services Offered Clipart PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Series Of Cyber Security Attacks Against Ukraine 2022 How Can We Protect Ourselves From Cyberattacks Slides PDF
This slide depicts cyberattacks protection methods to follow throughout the country, such as multi-factor authentication, data backup, to keep a copy of all the backup information. Create an editable Series Of Cyber Security Attacks Against Ukraine 2022 How Can We Protect Ourselves From Cyberattacks Slides PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Series Of Cyber Security Attacks Against Ukraine 2022 How Can We Protect Ourselves From Cyberattacks Slides PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Blockchain Business Methodology Impact On Business Operations Information PDF
This slide covers the details related to the advantages of blockchain technology for business. The purpose of this template is to defines blockchain as it helps to increase trust, security, transparency and bring other benefits to businesses. It includes details related to innovation, reduced cost, etc. Pitch your topic with ease and precision using this Blockchain Business Methodology Impact On Business Operations Information PDF. This layout presents information on Innovation, Security And Privacy, Tokenization, Cost. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Case Study Life Science And Healthcare Solutions Company Profile Ideas PDF
The slide showcases the challenge faced by healthcare business to develop digital capabilities. The company leveraged technology partner to develop and deploy customized cloud-based patient management platform for easy data access with added security. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Case Study Life Science And Healthcare Solutions Company Profile Ideas PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Integrating Naas Service Model To Enhance Challenges And Solutions Of Network Information PDF
This slide depicts the challenges and solutions of the network as a service. It includes compatibility issues related to hardware and infrastructure, vendor lock-in repercussions, and storing information in traditional on-site data centers. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Integrating Naas Service Model To Enhance Challenges And Solutions Of Network Information PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Integrating Naas Service Model To Enhance Challenges And Solutions Of Network Information PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
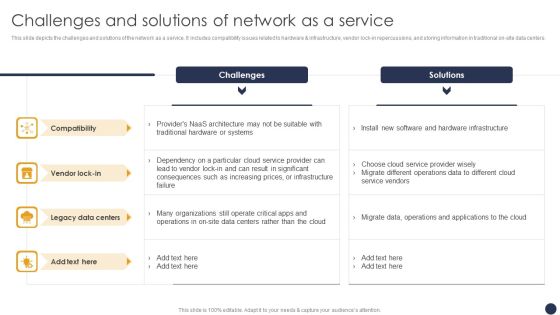
Integrating Naas Service Model Challenges And Solutions Of Network As A Service Ppt Professional Rules PDF
This slide depicts the challenges and solutions of the network as a service. It includes compatibility issues related to hardware and infrastructure, vendor lock-in repercussions, and storing information in traditional on-site data centers. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Integrating Naas Service Model Challenges And Solutions Of Network As A Service Ppt Professional Rules PDF can be your best option for delivering a presentation. Represent everything in detail using Integrating Naas Service Model Challenges And Solutions Of Network As A Service Ppt Professional Rules PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Statistics Showing Rising Demand Of Green Marketing Professional PDF
The following slide depicts some statistical data to access latest market information and launch innovative products. It includes elements such as brand trust, loyal customers, environmental benefits, eco-friendly goods, more productivity etc. Explore a selection of the finest Statistics Showing Rising Demand Of Green Marketing Professional PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Statistics Showing Rising Demand Of Green Marketing Professional PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Financial Analytics Solution Investor Funding Elevator Pitch Deck Revenue Streams Elements PDF
This slide represents various revenue generation sources of global analytics marketplace. It includes revenue sources such as subscription plans, API access, Data licensing, and custom analytics. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Financial Analytics Solution Investor Funding Elevator Pitch Deck Revenue Streams Elements PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Datafy Process To Datafy Your Business Operations Formats PDF
This slide depicts the process of effective datafication implementation in businesses. It includes having the right technology, an appropriate platform and a centralized repository to store data and make it accessible to everyone in the organization. Slidegeeks has constructed Datafy Process To Datafy Your Business Operations Formats PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Supply Chain Planning To Enhance Logistics Process Challenges In Supply Planning With Mitigation Strategies Designs PDF
This slide highlights the key challenges which includes multiple channels, speed and quality, increased costs, inconsistent data access with mitigation strategies for smooth functioning. This Supply Chain Planning To Enhance Logistics Process Challenges In Supply Planning With Mitigation Strategies Designs PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Guidebook For Executing Business Market Intelligence Market Intelligence Software Tool Comparison Topics PDF
This slide showcases comparison and assessment matrix of market intelligence software solution tools. It includes key elements such as advanced search, new leads identification, load time or data access, web browser extension, ideal customer targeting, Salesforce integration, prospect tracking or following, etc. This Guidebook For Executing Business Market Intelligence Market Intelligence Software Tool Comparison Topics PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Strategies To Select Best Order Management System Deploying Ecommerce Order Management Software Download PDF
This slide represents the techniques to help organization in choosing the right OMS which well integrates with the existing ecommerce site of the organization. It includes strategies for selection of OMS such as assess current business needs, consider functionalities, plan integration of systems and data etc.Retrieve professionally designed Strategies To Select Best Order Management System Deploying Ecommerce Order Management Software Download PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You Do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Incident Response Techniques Deployement Impact Of Cybersecurity Incidents On Organization Clipart PDF
This slide represents the impact of events which indicates that organizations data has been compromised for unlawful activities. It includes impact of cyber security events such as increased costs, operational disruption, reputational damage etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Incident Response Techniques Deployement Cyber Security Incident Management Team Structure Diagrams PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Incident Response Techniques Deployement Cyber Security Incident Management Team Structure Diagrams PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Reverse Proxy Web Server Reverse Proxy Web Server Application Side Technology Ideas PDF
This slide explains the reverse proxy server-side technology, that is security, and how data is transmitted securely in the presence of a proxy server that hides the actual servers identity. Are you searching for a Reverse Proxy Web Server Reverse Proxy Web Server Application Side Technology Ideas PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort youve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Reverse Proxy Web Server Reverse Proxy Web Server Application Side Technology Ideas PDF from Slidegeeks today.

Strategy To Be Adopted 2 Educate And Increase Employee Awareness Inspiration PDF
This slide shows the strategy to be adopted by the company i.e. Educate and provide proper data security training to the employees, make them familiar with latest security techniques etc. along with the need of such strategy and how it is to be implemented that will give benefit to the company. Presenting strategy to be adopted 2 educate and increase employee awareness inspiration pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like strategy to be adopted 2 educate and increase employee awareness. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Strategy To Be Adopted 2 Educate And Increase Employee Awareness Infographics PDF
This slide shows the strategy to be adopted by the company i.e. Educate and provide proper data security training to the employees, make them familiar with latest security techniques etc. along with the need of such strategy and how it is to be implemented that will give benefit to the company. Presenting strategy to be adopted 2 educate and increase employee awareness infographics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like strategy to be adopted 2 educate and increase employee awareness. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
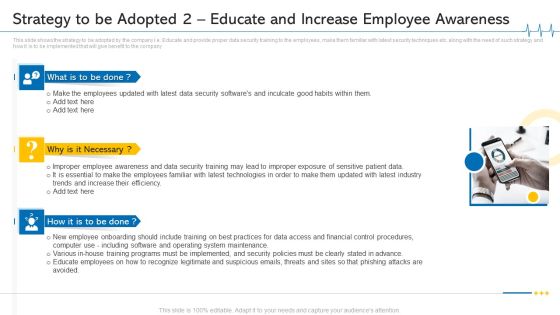
Strategy To Be Adopted 2 Educate And Increase Employee Awareness Ppt Pictures File Formats PDF
This slide shows the strategy to be adopted by the company i.e. Educate and provide proper data security training to the employees, make them familiar with latest security techniques etc. along with the need of such strategy and how it is to be implemented that will give benefit to the company. Presenting strategy to be adopted 2 educate and increase employee awareness ppt pictures file formats pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like technologies, financial control procedures, operating system maintenance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cybersecurity Operations Cybersecops Limitations Of SOC As A Service Model Template PDF
This slide depicts the challenges of adopting SOC as a service. The purpose of this slide is to highlight the main limitations of SOC as a service, including the onboarding process, enterprising data security, cost of log delivery, regulatory considerations, no dedicated IT security team, and limited customized options. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Cybersecurity Operations Cybersecops Limitations Of SOC As A Service Model Template PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Information Technology Due Diligence Checklist Guide For Successful Merger And Acquisition Pictures PDF
Mentioned slide showcases due diligence checklist to measure IT infrastructure health of the target company. Here the health is monitored based on infrastructure availability, telecom system, data analytics, security and compliance.Slidegeeks has constructed Information Technology Due Diligence Checklist Guide For Successful Merger And Acquisition Pictures PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
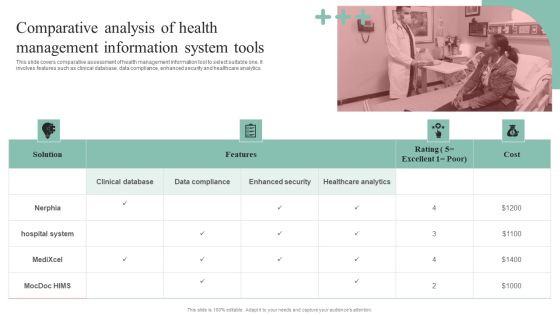
Incorporating HIS To Enhance Healthcare Services Comparative Analysis Of Health Management Information System Tools Summary PDF
This slide covers comparative assessment of health management information tool to select suitable one. It involves features such as clinical database, data compliance, enhanced security and healthcare analytics. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Incorporating HIS To Enhance Healthcare Services Comparative Analysis Of Health Management Information System Tools Summary PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Incorporating HIS To Enhance Healthcare Services Comparative Analysis Of Health Management Information System Tools Summary PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Global Survey Insights On Digital Transformation Ppt Visual Aids Files PDF
Following slide displays key statistics supporting success of digital transformation. It includes survey insights related to performance improvement, business opportunities, data security, evolving technologies, technology investments and procurement. This Global Survey Insights On Digital Transformation Ppt Visual Aids Files PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Global Survey Insights On Digital Transformation Ppt Visual Aids Files PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Zero Trust Network Access Architectural Models Diagrams PDF
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. Are you searching for a Zero Trust Network Access Architectural Models Diagrams PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Zero Trust Network Access Architectural Models Diagrams PDF from Slidegeeks today.

DLT Technology Blockchain Technology In Government Sector Ppt Model Vector PDF
This slide represents the use case of blockchain in the government sector how it would benefit voting, data security, budgeting and corruption. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give DLT Technology Blockchain Technology In Government Sector Ppt Model Vector PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable DLT Technology Blockchain Technology In Government Sector Ppt Model Vector PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Emerging Technology Trends For Business Growth Diagrams PDF
The following slide showcases various emerging trends of technology that plays crucial role in business growth and success. It showcases trends such as cloud computing, data analytics, artificial intelligence, internet of things and cyber security. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Emerging Technology Trends For Business Growth Diagrams PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Emerging Technology Trends For Business Growth Diagrams PDF.

Comparing Tools Required For Implementing Technology Transformation Template PDF
This slide shows the comparison of technology transformation tools on the basis of features such as team progress tracking, real time communication functionality, data security and task automation.Find highly impressive Comparing Tools Required For Implementing Technology Transformation Template PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Comparing Tools Required For Implementing Technology Transformation Template PDF for your upcoming presentation. All the presentation templates are 100precent editable and you can change the color and personalize the content accordingly. Download now.

Transform Management Instruction Schedule Technological Change Management Designs PDF
This slide represents the strategic plan developed to facilitate training to employees related to introducing new technological advancements in the enterprise. It includes details related to training topics such as cloud computing, cyber security, data storage etc. Find highly impressive Transform Management Instruction Schedule Technological Change Management Designs PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Transform Management Instruction Schedule Technological Change Management Designs PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Confidential Computing System Technology Introduction To Confidential Computing Microsoft PDF
This slide represents the introduction to confidential computing, including its overview and objectives. Confidential computing is a cloud computing method to secure data while processing and gives business confidence to migrate their information and valuable assets to the cloud. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Confidential Computing System Technology Introduction To Confidential Computing Microsoft PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
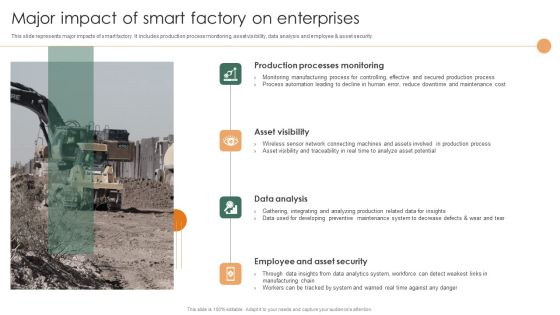
Smart Manufacturing Deployment Improve Production Procedures Major Impact Of Smart Factory On Enterprises Designs PDF
This slide represents major impacts of smart factory. It includes production process monitoring, asset visibility, data analysis and employee asset security.Are you searching for a Smart Manufacturing Deployment Improve Production Procedures Major Impact Of Smart Factory On Enterprises Designs PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you ve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Smart Manufacturing Deployment Improve Production Procedures Major Impact Of Smart Factory On Enterprises Designs PDF from Slidegeeks today.
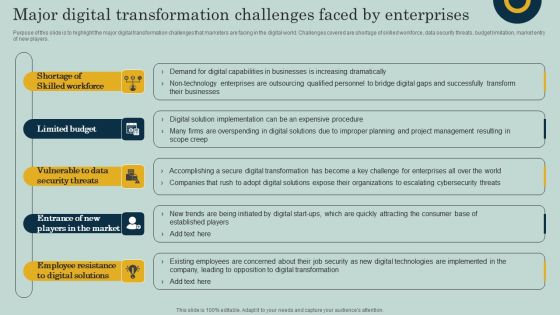
Major Digital Transformation Challenges Faced By Enterprises Ppt Inspiration Examples PDF
Purpose of this slide is to highlight the major digital transformation challenges that marketers are facing in the digital world. Challenges covered are shortage of skilled workforce, data security threats, budget limitation, market entry of new players. Are you searching for a Major Digital Transformation Challenges Faced By Enterprises Ppt Inspiration Examples PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Major Digital Transformation Challenges Faced By Enterprises Ppt Inspiration Examples PDF from Slidegeeks today.

Training Program For Implementing Technological Change Management Training Plan Introduction PDF
This slide represents the strategic plan developed to facilitate training to employees related to introducing new technological advancements in the enterprise. It includes details related to training topics such as cloud computing, cyber security, data storage etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Training Program For Implementing Technological Change Management Training Plan Introduction PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

CASB Reverse Proxy Deployment Use Cases Ppt PowerPoint Presentation Diagram Lists PDF
This slide illustrates the use cases of reverse proxy server deployment of the cloud access security broker model. The purpose of this slide is to highlight the main use cases of reverse proxy deployment, including using user behavior to enforce access constraints, keeping data from certain programs from being lost, and so on. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give CASB Reverse Proxy Deployment Use Cases Ppt PowerPoint Presentation Diagram Lists PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable CASB Reverse Proxy Deployment Use Cases Ppt PowerPoint Presentation Diagram Lists PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Implementing Smart Manufacturing Technology To Increase Productivity Major Impact Of Smart Factory On Enterprises Elements PDF
This slide represents major impacts of smart factory. It includes production process monitoring, asset visibility, data analysis and employee and asset security. Welcome to our selection of the Implementing Smart Manufacturing Technology To Increase Productivity Major Impact Of Smart Factory On Enterprises Elements PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

Evolution Of Wireless Technologies Key Features And Disadvantages Of 5Th Generation Structure PDF
This slide represents the critical features and disadvantages of 5th generation technology. Features include faster internet speeds, low millisecond latency, improved network security and dependability, data reduction in total costs, use of small cells and beam technologies, and so on. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Evolution Of Wireless Technologies Key Features And Disadvantages Of 5Th Generation Structure PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
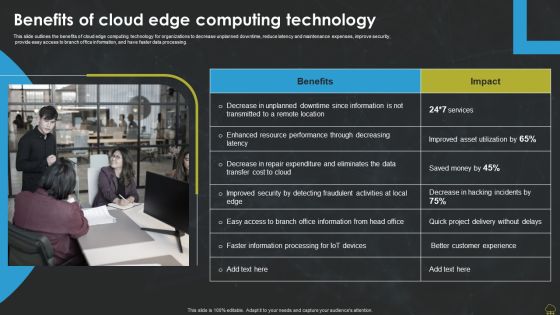
Integrating Edge Computing To Enhance Operational Efficiency Benefits Of Cloud Edge Computing Technology Designs PDF
This slide outlines the benefits of cloud edge computing technology for organizations to decrease unplanned downtime, reduce latency and maintenance expenses, improve security, provide easy access to branch office information, and have faster data processing. Want to ace your presentation in front of a live audience Our Integrating Edge Computing To Enhance Operational Efficiency Benefits Of Cloud Edge Computing Technology Designs PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Implementing Digital Transformation Global Survey Insights On Digital Transformation Background PDF
Following slide displays key statistics supporting success of digital transformation. It includes survey insights related to performance improvement, business opportunities, data security, evolving technologies, technology investments and procurement. This Implementing Digital Transformation Global Survey Insights On Digital Transformation Background PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Implementing Digital Transformation Global Survey Insights On Digital Transformation Background PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, dont wait, grab the presentation templates today.

Global Survey Insights On Digital Transformation Ppt Icon Topics PDF
Following slide displays key statistics supporting success of digital transformation. It includes survey insights related to performance improvement, business opportunities, data security, evolving technologies, technology investments and procurement. Welcome to our selection of the Global Survey Insights On Digital Transformation Ppt Icon Topics PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

Mobile Phone Generations 1G To 5G Key Features And Disadvantages Of 5Th Generation Technology Rules PDF
This slide represents the critical features and disadvantages of 5th generation technology. Features include faster internet speeds, low millisecond latency, improved network security and dependability, data reduction in total costs, use of small cells and beam technologies, and so on. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Mobile Phone Generations 1G To 5G Key Features And Disadvantages Of 5Th Generation Technology Rules PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Mobile Phone Generations 1G To 5G Key Features And Disadvantages Of 5Th Generation Technology Rules PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today

Change Management Strategy Comparing Tools Required For Implementing Technology Structure PDF
This slide shows the comparison of technology transformation tools on the basis of features such as team progress tracking, real time communication functionality, data security and task automation. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Change Management Strategy Comparing Tools Required For Implementing Technology Structure PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Change Management Strategy Comparing Tools Required For Implementing Technology Structure PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Transition Plan For Business Management Comparing Tools Required For Implementing Technology Brochure PDF
This slide shows the comparison of technology transformation tools on the basis of features such as team progress tracking, real time communication functionality, data security and task automation. Get a simple yet stunning designed Transition Plan For Business Management Comparing Tools Required For Implementing Technology Brochure PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Transition Plan For Business Management Comparing Tools Required For Implementing Technology Brochure PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Change Management Process Comparing Tools Required For Implementing Technology Mockup PDF
This slide shows the comparison of technology transformation tools on the basis of features such as team progress tracking, real time communication functionality, data security and task automation. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Change Management Process Comparing Tools Required For Implementing Technology Mockup PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Change Management Process Comparing Tools Required For Implementing Technology Mockup PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Designing Strategies For Company Growth And Success Emerging Technology Trends For Business Growth Introduction PDF
The following slide showcases various emerging trends of technology that plays crucial role in business growth and success. It showcases trends such as cloud computing, data analytics, artificial intelligence, internet of things and cyber security. This Designing Strategies For Company Growth And Success Emerging Technology Trends For Business Growth Introduction PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Designing Strategies For Company Growth And Success Emerging Technology Trends For Business Growth Introduction PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Confidential Computing System Technology Need For Confidential Computing In Cloud Guidelines PDF
This slide depicts the need for confidential computing in a cloud environment and by showcasing the security concerns with early data processing system and confidential computing solutions to overcome those problems. Get a simple yet stunning designed Confidential Computing System Technology Need For Confidential Computing In Cloud Guidelines PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Confidential Computing System Technology Need For Confidential Computing In Cloud Guidelines PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
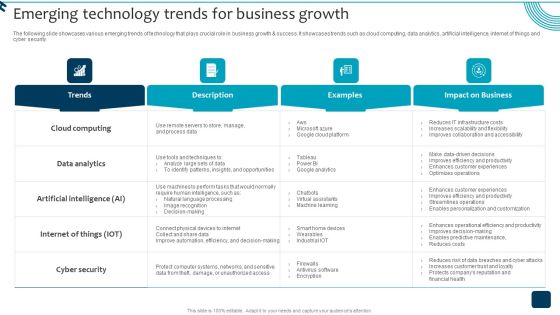
Strategic Brand Growth Plan For Market Leadership Emerging Technology Trends For Business Background PDF
The following slide showcases various emerging trends of technology that plays crucial role in business growth and success. It showcases trends such as cloud computing, data analytics, artificial intelligence, internet of things and cyber security. Do you know about Slidesgeeks Strategic Brand Growth Plan For Market Leadership Emerging Technology Trends For Business Background PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

Key Features And Disadvantages Of 3Rd Generation System Wireless Technology Transformation Introduction PDF
This slide shows the key features and disadvantages of the 3G communication systems. The features include increased data rate, video calling, enhanced security and coverage, increased user numbers, mobile application support, navigation systems, improved web surfing, television streaming, and 3D games. Welcome to our selection of the Key Features And Disadvantages Of 3Rd Generation System Wireless Technology Transformation Introduction PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

Key Trends In Bitcoin Industry Decentralized Fund Investment Playbook Information PDF
The following slide displays key trends that will impact the Bitcoin industry, these trends can boost the market towards growth and help an investor to understand the overall shape of the market. These trends can be transparency and data security, adoption of crypto by financial institution etc.Want to ace your presentation in front of a live audience Our Key Trends In Bitcoin Industry Decentralized Fund Investment Playbook Information PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

Cloud Capability Model For Strategy Architecture And Governance Cloud Computing Complexities Template PDF
This slide covers the cloud capability model including strategy, architecture, governance, identity and security with data centre, platform, infrastructure and software as services. Explore a selection of the finest Cloud Capability Model For Strategy Architecture And Governance Cloud Computing Complexities Template PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Cloud Capability Model For Strategy Architecture And Governance Cloud Computing Complexities Template PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Cloud Capability Model For Strategy Architecture And Governance Clipart PDF
This slide covers the cloud capability model including strategy, architecture, governance, identity and security with data centre, platform, infrastructure and software as services.Are you searching for a Cloud Capability Model For Strategy Architecture And Governance Clipart PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you ve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Cloud Capability Model For Strategy Architecture And Governance Clipart PDF from Slidegeeks today.
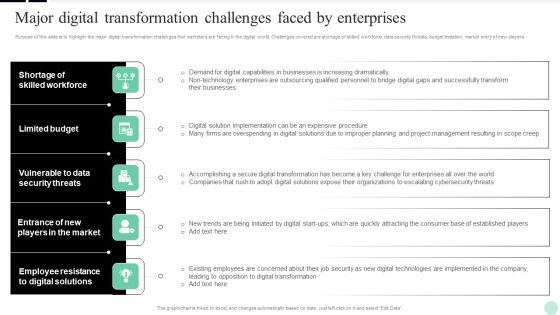
Implementing Digital Transformation Major Digital Transformation Challenges Faced By Enterprises Professional PDF
Purpose of this slide is to highlight the major digital transformation challenges that marketers are facing in the digital world. Challenges covered are shortage of skilled workforce, data security threats, budget limitation, market entry of new players. Are you searching for a Implementing Digital Transformation Major Digital Transformation Challenges Faced By Enterprises Professional PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort youve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Implementing Digital Transformation Major Digital Transformation Challenges Faced By Enterprises Professional PDF from Slidegeeks today.

Recruitment Marketing Strategies For NPO Business Employee Reviews And Ratings For NPO Culture Elements PDF
This slide showcases statistical data outlining overall employee satisfaction at non profit business to assess workplace culture and environment. It highlights elements such as job security, promotions appraisal, work satisfaction, work life balance, salary and benefits, skill development and company culture. This Recruitment Marketing Strategies For NPO Business Employee Reviews And Ratings For NPO Culture Elements PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Recruitment Marketing Strategies For NPO Business Employee Reviews And Ratings For NPO Culture Elements PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
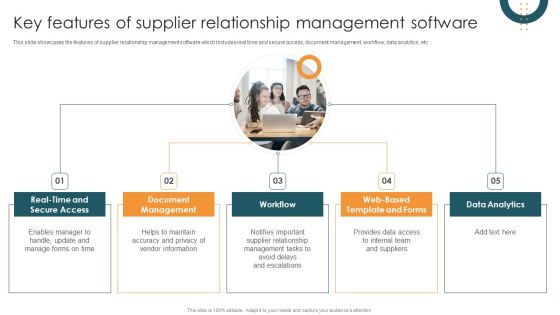
Vendor Relation Management Techniques Key Features Of Supplier Relationship Management Software Download PDF
This slide showcases the features of supplier relationship management software which includes real time and secure access, document management, workflow, data analytics, etc. Do you know about Slidesgeeks Vendor Relation Management Techniques Key Features Of Supplier Relationship Management Software Download PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

Analyzing And Deploying Effective CMS Challenges Faced By Ecommerce Marketing Manager Introduction PDF
This slide represents the hurdles and business challenges faced by marketing manager of ABC ecommerce firm in the current scenario. It includes business challenges such as customers exploding expectations, agility, data security, customer retention and omni channel experience. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Analyzing And Deploying Effective CMS Challenges Faced By Ecommerce Marketing Manager Introduction PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
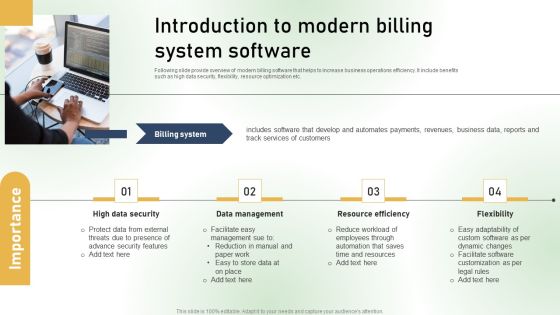
Introduction To Modern Billing System Software Ppt PowerPoint Presentation File Ideas PDF
Following slide provide overview of modern billing software that helps to increase business operations efficiency. It include benefits such as high data security, flexibility, resource optimization etc.Retrieve professionally designed Introduction To Modern Billing System Software Ppt PowerPoint Presentation File Ideas PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Airtable Capital Funding Pitch Deck Problem Statement Sample PDF
This slide covers problem associated with building application for creating and sharing relational databases. It involves major challenges such as data security, lack of flexibility and scalability, user interface experience and cross platform compatibility. If you are looking for a format to display your unique thoughts, then the professionally designed Airtable Capital Funding Pitch Deck Problem Statement Sample PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Airtable Capital Funding Pitch Deck Problem Statement Sample PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
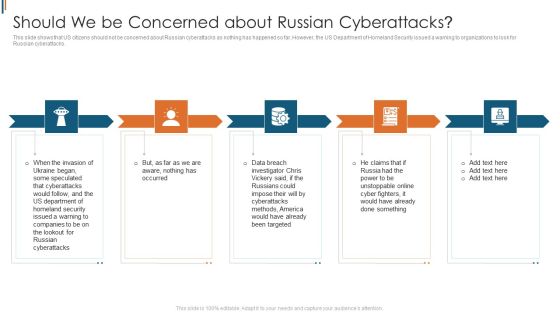
Ukraine Cyberwarfare Should We Be Concerned About Russian Cyberattacks Sample Pdf
This slide shows that US citizens should not be concerned about Russian cyberattacks as nothing has happened so far. However, the US Department of Homeland Security issued a warning to organizations to look for Russian cyberattacks. This is a ukraine cyberwarfare should we be concerned about russian cyberattacks sample pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like but, as far as we are aware, nothing has occurred, he claims that if russia had the power to be unstoppable online cyber fighters, data breach investigator chris vickery said, if the russians could impose their will by cyberattacks methods. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
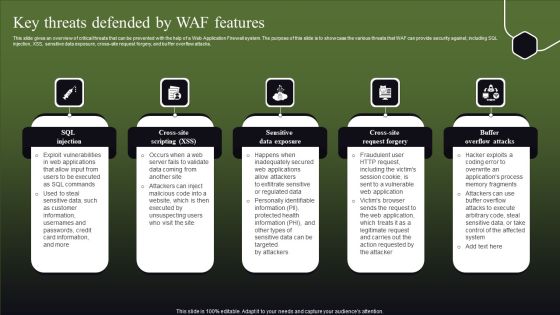
Key Threats Defended By WAF Features Ppt Pictures Elements PDF
This slide gives an overview of critical threats that can be prevented with the help of a Web Application Firewall system. The purpose of this slide is to showcase the various threats that WAF can provide security against, including SQL injection, XSS, sensitive data exposure, cross-site request forgery, and buffer overflow attacks. Explore a selection of the finest Key Threats Defended By WAF Features Ppt Pictures Elements PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Key Threats Defended By WAF Features Ppt Pictures Elements PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Cashless Payment Strategies To Enhance Business Performance Impact Assessment Of Mobile Wallet Application Professional PDF
Mentioned slide provides information about mobile wallet payment implementation impact on business activities. It includes impacts such as easy customer data analytics, offer reward and loyalty points, smooth workflow, and improved security. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cashless Payment Strategies To Enhance Business Performance Impact Assessment Of Mobile Wallet Application Professional PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cashless Payment Strategies To Enhance Business Performance Impact Assessment Of Mobile Wallet Application Professional PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers

Implementing An Effective Ecommerce Management Framework Challenges Faced By Ecommerce Marketing Manager Graphics PDF
This slide represents the hurdles and business challenges faced by marketing manager of ABC ecommerce firm in the current scenario. It includes business challenges such as customers exploding expectations, agility, data security, customer retention and omni-channel experience. Create an editable Implementing An Effective Ecommerce Management Framework Challenges Faced By Ecommerce Marketing Manager Graphics PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre-designed presentation templates help save time. Implementing An Effective Ecommerce Management Framework Challenges Faced By Ecommerce Marketing Manager Graphics PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Implementing Management System To Enhance Ecommerce Processes Challenges Faced By Ecommerce Marketing Manager Rules PDF
This slide represents the hurdles and business challenges faced by marketing manager of ABC ecommerce firm in the current scenario. It includes business challenges such as customers exploding expectations, agility, data security, customer retention and omni-channel experience. Create an editable Implementing Management System To Enhance Ecommerce Processes Challenges Faced By Ecommerce Marketing Manager Rules PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Implementing Management System To Enhance Ecommerce Processes Challenges Faced By Ecommerce Marketing Manager Rules PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Deploying SDN System Use Cases Of Software Defined Networking SDN Ideas PDF
This slide represents the use cases of software-defined networking, a developing technology that will eventually replace physical network designs with software-controlled networking architecture. It shows its use in DevOps, campus networks, service provider networks, and data center security. Slidegeeks has constructed Deploying SDN System Use Cases Of Software Defined Networking SDN Ideas PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
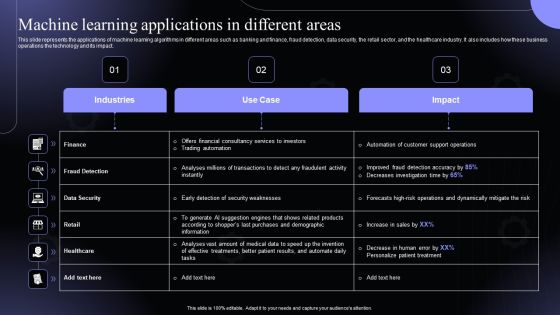
Machine Learning Applications In Different Areas Hyperautomation Software Solutions IT Designs PDF
This slide represents the applications of machine learning algorithms in different areas such as banking and finance, fraud detection, data security, the retail sector, and the healthcare industry. It also includes how these business operations the technology and its impact.Slidegeeks has constructed Machine Learning Applications In Different Areas Hyperautomation Software Solutions IT Designs PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Characteristics Impact Of Blockchain On Modern Systems Introduction PDF
This slide represents the critical features of hybrid blockchain technology. The purpose of this slide is to showcase the characteristics of hybrid blockchains over private and public blockchains. These include data security, low transaction costs, a closed ecosystem, new rules, and so on. Boost your pitch with our creative Characteristics Impact Of Blockchain On Modern Systems Introduction PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Positive Impact Of Effective Existing Products And Service Offerings Of Firm Formats PDF
This slide showcases products and services of information technology company. The offerings covered are file servers, virtual desktops, office phones, network equipment, help desk, data backup, web designing, network security and cloud services. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Positive Impact Of Effective Existing Products And Service Offerings Of Firm Formats PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Existing Products And Service Offerings Of Firm Stakeholder Engagement Plan For Launch Event Ideas PDF
This slide showcases products and services of information technology company. The offerings covered are file servers, virtual desktops, office phones, network equipment, help desk, data backup, web designing, network security and cloud services. Take your projects to the next level with our ultimate collection of Existing Products And Service Offerings Of Firm Stakeholder Engagement Plan For Launch Event Ideas PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they well make your projects stand out from the rest.

Use Cases Of Software Defined Networking SDN Ppt Slides Show PDF
This slide represents the use cases of software-defined networking, a developing technology that will eventually replace physical network designs with software-controlled networking architecture. It shows its use in devops, campus networks, service provider networks, and data center security. This Use Cases Of Software Defined Networking SDN Ppt Slides Show PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
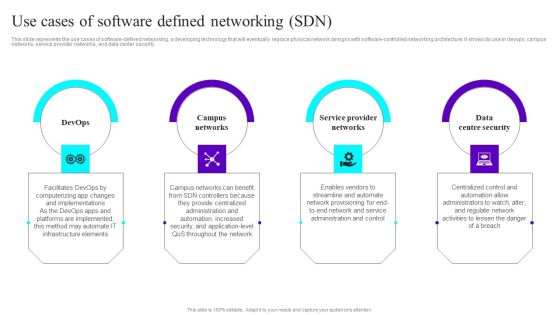
Use Cases Of Software Defined Networking SDN Ppt Styles Aids PDF
This slide represents the use cases of software-defined networking, a developing technology that will eventually replace physical network designs with software-controlled networking architecture. It shows its use in devops, campus networks, service provider networks, and data center security. This Use Cases Of Software Defined Networking SDN Ppt Styles Aids PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Empowering Network Agility Through SDN Use Cases Of Software Defined Networking SDN Elements PDF
This slide represents the use cases of software defined networking, a developing technology that will eventually replace physical network designs with software controlled networking architecture. It shows its use in devops, campus networks, service provider networks, and data center security. Presenting this PowerPoint presentation, titled Empowering Network Agility Through SDN Use Cases Of Software Defined Networking SDN Elements PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Empowering Network Agility Through SDN Use Cases Of Software Defined Networking SDN Elements PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Empowering Network Agility Through SDN Use Cases Of Software Defined Networking SDN Elements PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

 Home
Home