Data Privacy

Cloud Security Assessment How Does Cloud Security Work Formats PDF
This slide depicts the process of legal compliance in cloud security, and it also represents that organizations are bound to keep customers data private across the cloud. Presenting Cloud Security Assessment How Does Cloud Security Work Formats PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Information Against, Transparency, Regulations. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Assessment Cloud Security Threats Malware Attacks Inspiration PDF
This slide represents the malware threat of cloud security and how it can affect data stored on the cloud, further leading to company loss.This is a Cloud Security Assessment Cloud Security Threats Malware Attacks Inspiration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Cloud Administrations, Information Exfiltration, Protection Frameworks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Assessment Cloud Security Threats Compliance Violations Mockup PDF
This slide depicts the value of compliance violations threat of cloud security in a business and how fast an organization can switch to a non compliance state.This is a Cloud Security Assessment Cloud Security Threats Compliance Violations Mockup PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Serious Repercussions, Data In The Business, Organizations Should You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Assessment Types Of Cloud Security Solutions Brochure PDF
This slide represents the cloud security solutions such as hybrid cloud security solutions, SMB cloud security solutions, and enterprise cloud security solutions.Presenting Cloud Security Assessment Types Of Cloud Security Solutions Brochure PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Categorization Of Services, Access Control, Data Compliance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Desktop Security Management Complete Computer Security Implementation Checklist Demonstration PDF
This slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. Presenting desktop security management complete computer security implementation checklist demonstration pdf to provide visual cues and insights. Share and navigate important information on twelve stages that need your due attention. This template can be used to pitch topics like technology, systems, organizations, information. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Assessment Pillars Of Cloud Security Identity Security Clipart PDF
This slide depicts the identity security pillar of cloud security. It also shows how it could be beneficial to protect data from loss.This is a Cloud Security Assessment Pillars Of Cloud Security Identity Security Clipart PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Devices To Accomplish, Service Permissions, Information Applications You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Tools Used In Cloud Security Cloud Computing Security IT Ppt Background Images PDF
This slide represents the list of tools utilized under cloud security systems to protect, manage, store and control data on the cloud. This is a tools used in cloud security cloud computing security it ppt background images pdf template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like silver sky, centrify, doc tracker, proofpoint, whitehat. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

What Is IT Security IT And How Does IT Work Ppt Slides Gridlines PDF
This slide defines the meaning of cyber security and how it helps to prevent data through different methods and techniques. This is a what is it security it and how does it work ppt slides gridlines pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like techniques, computer systems, networks, servers, mobile devices, cyber attacks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Datacenter Information Security Management Framework Professional PDF
This slide presents a framework showing elements of data center security governance. It includes key components such as security operation, application, server and endpoint security, perimeter and infrastructure, virtualized IT platform, etc. Pitch your topic with ease and precision using this Datacenter Information Security Management Framework Professional PDF. This layout presents information on Security Architecture, Security Functions, Governances. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
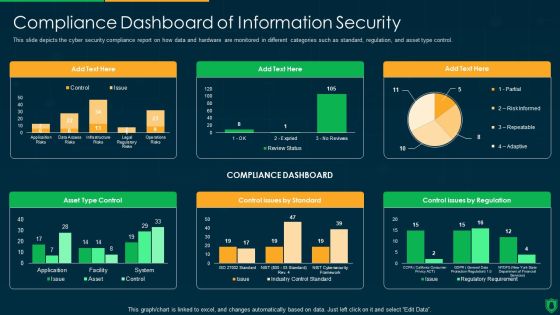
Info Security Compliance Dashboard Of Information Security Ppt PowerPoint Presentation File Graphics Download PDF
This slide depicts the cyber security compliance report on how data and hardware are monitored in different categories such as standard, regulation, and asset type control. Deliver an awe inspiring pitch with this creative info security compliance dashboard of information security ppt powerpoint presentation file graphics download pdf bundle. Topics like compliance dashboard, asset type control, control issues by standard, control issues by regulation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Info Security Requirement Of Information Security In Different Sectors Ppt PowerPoint Presentation File Grid PDF
This slide depicts the requirement of cyber security in different sectors and the percentage of attacks experienced in the medical, govt, military, and corporate sectors in the past 12 months. Deliver an awe inspiring pitch with this creative info security requirement of information security in different sectors ppt powerpoint presentation file grid pdf bundle. Topics like cyber attacks, past 12 months, organizations transfer, sensitive data over internet can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Security Threats Malware Attacks Sample PDF
This slide represents the malware threat of cloud security and how it can affect data stored on the cloud, further leading to company loss. This is a Cloud Security Threats Malware Attacks Sample PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Technology, Targets, Information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
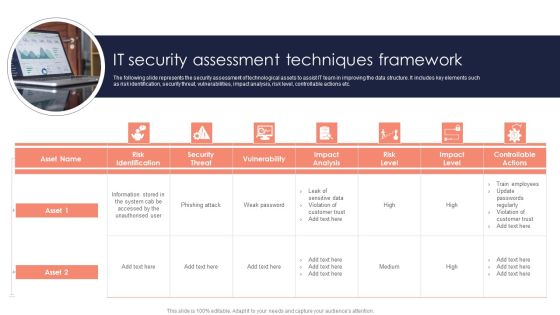
It Security Assessment Techniques Framework Introduction PDF
The following slide represents the security assessment of technological assets to assist IT team in improving the data structure. It includes key elements such as risk identification, security threat, vulnerabilities, impact analysis, risk level, controllable actions etc. Persuade your audience using this It Security Assessment Techniques Framework Introduction PDF. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including Impact Analysis, Risk Level, Information. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

IT Security Roadmap For Information Technology Security Training Ppt Layouts Vector PDF
This slide depicts the cyber security training roadmap. It also shows the plan and guidelines to conduct an effective training program. This is a it security roadmap for information technology security training ppt layouts vector pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like ensuring physical security, ensuring data security, mobile and remote computing best practices, safe and computing best practices. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
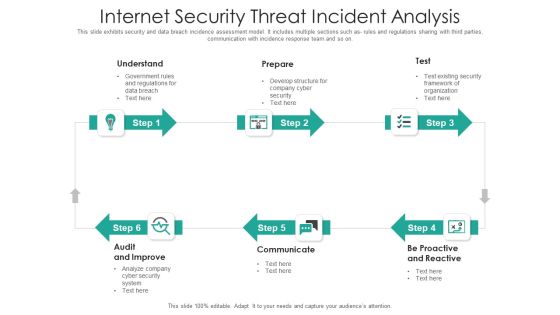
Internet Security Threat Incident Analysis Mockup PDF
This slide exhibits security and data breach incidence assessment model. It includes multiple sections such as- rules and regulations sharing with third parties, communication with incidence response team and so on. Presenting internet security threat incident analysis mockup pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including proactive and reactive, communicate, audit and improve. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cloud Security Checklist Access Control Rules PDF
This slide depicts the access control under the cloud security checklist and how it affects the organizations when data breaches happen due to poor access control management. Presenting Cloud Security Checklist Access Control Rules PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Security, Systems, Networks. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Security Risk Evaluation Information Security And Risk Management User Spending By Segment Demonstration PDF
This slide showcases expenses done by organization in different segments of information security and risk management. Key segments include application security, cloud security, data security, identify access management, infrastructure protection, integrated risk management, security services etc.This is a Information Security Risk Evaluation Information Security And Risk Management User Spending By Segment Demonstration PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Access Management, Infrastructure Protection, Security Equipment. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

RPA Discovery Procedure Security Steps Brochure PDF
Following slide exhibits steps for robotic process automation security. Purpose of this slide is to use business automation efficiently that prevents data leakage and fraud. It includes pointers such as bot actions accountability, avoid fraud, secure log integrity etc. Presenting RPA Discovery Procedure Security Steps Brochure PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Bot Actions Accountability, Avoid Errors And Fraud, Secure Log Integrity. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cloud Information Security Cloud Security Threats Malware Attacks Ppt File Ideas PDF
This slide represents the malware threat of cloud security and how it can affect data stored on the cloud, further leading to company loss. This is a Cloud Information Security Cloud Security Threats Malware Attacks Ppt File Ideas PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Cloud Administrations, Cyber Criminals, Deploy Malware. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Information Security Tools Used In Cloud Security Ppt Diagram Lists PDF
This slide represents the list of tools utilized under cloud security systems to protect, manage, store and control data on the cloud. This is a Cloud Information Security Tools Used In Cloud Security Ppt Diagram Lists PDF template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Cloud Solutions, Advanced Threats, Cipher Cloud. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security Hazards Management Program Pictures PDF
The below slide outlines the cyber security threats along with mitigation strategy which helps an organisation to tackle and prevent potential risks. Key components are threat, risk, priority, mitigation step, person responsible and deadline.Showcasing this set of slides titled Cyber Security Hazards Management Program Pictures PDF. The topics addressed in these templates are Sensitive Customer, Data Encryption Using. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cloud Information Security Cloud Security Checklist Logging And Monitoring Ppt Show Information PDF
This slide defines the importance of logging and monitoring activities on data in a network and how it could be beneficial in future analysis. Presenting Cloud Information Security Cloud Security Checklist Logging And Monitoring Ppt Show Information PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Future Evaluation, New Policies, Potential Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
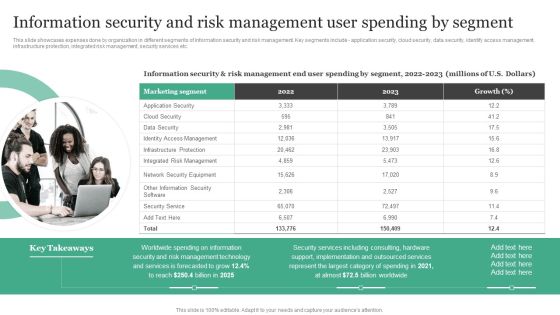
Information Security And Risk Management User Spending By Segment Information Security Risk Administration Slides PDF
This slide showcases expenses done by organization in different segments of information security and risk management. Key segments include - application security, cloud security, data security, identify access management, infrastructure protection, integrated risk management, security services etc.Make sure to capture your audiences attention in your business displays with our gratis customizable Information Security And Risk Management User Spending By Segment Information Security Risk Administration Slides PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
IT Security What Is Information Technology Security And How Does IT Work Ppt Icon Smartart
This slide defines the meaning of cyber security and how it helps to prevent data through different methods and techniques. Presenting it security what is information technology security and how does it work ppt icon smartart to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like techniques, servers, natural disasters. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Security Set Measures For Secure Communication Ppt Outline Slide Download PDF
This slide depicts secure communication within an organization and the technology to encrypt emails or data while sending or receiving them. This is a information security set measures for secure communication ppt outline slide download pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organization, technology. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Security Main Principle Of Information Security Ppt Outline Guidelines PDF
This slide represents the main principles of information security such as confidentiality, integrity, and availability and how it makes data confidential and consistent, and available to authorized users. This is a information security main principle of information security ppt outline guidelines pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like integrity, confidentiality, availability. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Security Risk Evaluation Current Information Security Issues Faced By Organization Clipart PDF
This slide showcases current capabilities of organization regarding information and data security. Its key component are risk management functions, required standard rating and actual standard rating,This is a Information Security Risk Evaluation Current Information Security Issues Faced By Organization Clipart PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Untrained Employees, Complex Risk, Management Policy . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Internet Security Threats Management Framework Icons PDF
This slide exhibits data breach risk management model. It includes major evaluation criteria such as- does the management has two unique credentials to perform administer activities, does the multifactor authentication is enabled for administrative access etc. Showcasing this set of slides titled internet security threats management framework icons pdf. The topics addressed in these templates are asset, control topic, evaluation questions, response, threat. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cloud Information Security How Does Cloud Security Work Governance Ppt Show Slide Portrait PDF
This slide depicts the governance policy under the cloud security system and how users, processes, and technology are monitored. This is a Cloud Information Security How Does Cloud Security Work Governance Ppt Show Slide Portrait PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Owner Ship, Accessibility Knowledge, Data Governance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Architecture Of Cloud Security Service Cloud Computing Security IT Ppt Professional Information PDF
This slide defines the architecture of the cloud security system and how data is kept, managed, and secured based on customer and service providers responsibilities. This is a architecture of cloud security service cloud computing security it ppt professional information pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cloud service provider responsibility, customer responsibility. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Information Security Topics That Fall Under The Umbrella Of Cloud Security Ppt Layouts Inspiration PDF
This slide shows the various topics that fall under the umbrella of cloud security, namely data center security, access control, threat prevention, threat detection, threat mitigation, redundancy, and legal compliance. This is a Cloud Information Security Topics That Fall Under The Umbrella Of Cloud Security Ppt Layouts Inspiration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Access Control, Threat Prevention, Threat Detection. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Risk Based Procedures To IT Security Checklist For Effectively Managing Asset Security Portrait PDF
Following slide displays system management checklist that company will use for effectively managing asset security. It also includes system management activities and frequency of performing them. This is a Risk Based Procedures To IT Security Checklist For Effectively Managing Asset Security Portrait PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like System Monitoring, Data Backup, Security Patches. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Risk Management Approach Introduction Checklist For Effectively Managing Asset Security Sample PDF
Following slide displays system management checklist that company will use for effectively managing asset security. It also includes system management activities and frequency of performing them. This is a IT Security Risk Management Approach Introduction Checklist For Effectively Managing Asset Security Sample PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like System Monitoring, Data Backup, Security Patches. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Automation Tools Integration Security Automation Architecture With Key Elements Mockup PDF
This slide showcases the architecture of security automation which includes security automation logs, security admin, policy server, active directory, reputation feeds and other data sources. Presenting IT Security Automation Tools Integration Security Automation Architecture With Key Elements Mockup PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Security Policy, Security Admin, Reputation Feeds. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security Main Principle Of Information Security Ppt Infographics Example Topics PDF
This slide represents the main principles of information security such as confidentiality, integrity, and availability and how it makes data confidential and consistent, and available to authorized users. This is a it security main principle of information security ppt infographics example topics pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like confidentiality, integrity, availability. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Information Security Cloud Security Threats Compliance Violations Ppt Slides Aids PDF
This slide depicts the value of compliance violations threat of cloud security in a business and how fast an organization can switch to a non-compliance state. This is a Cloud Information Security Cloud Security Threats Compliance Violations Ppt Slides Aids PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Risks Organizations, Data Business, Serious Repercussions. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Information Security Industries That Can Benefit From Cloud Security Ppt Summary Graphics PDF
This slide shows the industries categorized as automotive, education, financial, healthcare, insurance, and others that can take advantage of cloud security by storing data on clouds. This is a Cloud Information Security Industries That Can Benefit From Cloud Security Ppt Summary Graphics PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Automotive Education, Financial Healthcare, Insurance Production. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Information Security Precautions Need To Take In Cloud Security Ppt Ideas Gridlines PDF
This slide depicts the cloud security precautions that one organization should take while signing up for a cloud service. This is a Cloud Information Security Precautions Need To Take In Cloud Security Ppt Ideas Gridlines PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Data Storage, Service Provider, Quickly Retrieval. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Security Risk Evaluation Estimated Impact Of Information Security Risk Management Plan Microsoft PDF
This slide showcases capabilities of organization regarding information and data security after risk management plan. Its key components are risk management functions, required standard rating and actual standard rating.Deliver and pitch your topic in the best possible manner with this Information Security Risk Evaluation Estimated Impact Of Information Security Risk Management Plan Microsoft PDF. Use them to share invaluable insights on Identification Assess, Protecting Safeguarding, Detect Threat and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Checklist For Information Security Risk Management Information Security Risk Administration Portrait PDF
This slide showcases checklist that can help to ensure formulate and implementing data security risk management program in organization. Its key components are activity, assigned to and status.Take your projects to the next level with our ultimate collection of Checklist For Information Security Risk Management Information Security Risk Administration Portrait PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they all make your projects stand out from the rest.

Information Systems Security And Risk Management Plan Checklist For Information Security Risk Management Mockup PDF
This slide showcases checklist that can help to ensure formulate and implementing data security risk management program in organization. Its key components are activity, assigned to and status. Find a pre designed and impeccable Information Systems Security And Risk Management Plan Checklist For Information Security Risk Management Mockup PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Cloud Security Assessment Topics That Fall Under The Umbrella Of Cloud Security Microsoft PDF
This slide shows the various topics that fall under the umbrella of cloud security, namely data center security, access control, threat prevention, threat detection, threat mitigation, redundancy, and legal compliance.This is a Cloud Security Assessment Topics That Fall Under The Umbrella Of Cloud Security Microsoft PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Threat Prevention, Access Control, Centre Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Automation Systems Guide Security Automation Architecture With Key Elements Inspiration PDF
This slide showcases the architecture of security automation which includes security automation logs, security admin, policy server, active directory, reputation feeds and other data sources. Make sure to capture your audiences attention in your business displays with our gratis customizable IT Security Automation Systems Guide Security Automation Architecture With Key Elements Inspiration PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
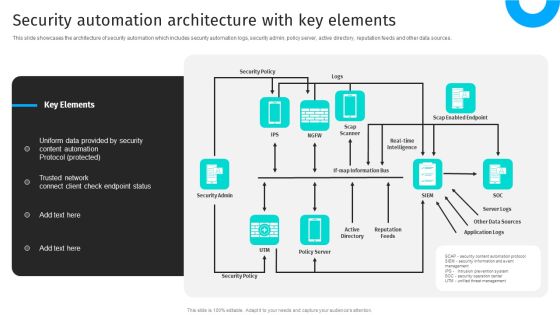
Security Automation To Analyze And Mitigate Cyberthreats Security Automation Architecture Topics PDF
This slide showcases the architecture of security automation which includes security automation logs, security admin, policy server, active directory, reputation feeds and other data sources.This modern and well-arranged Security Automation To Analyze And Mitigate Cyberthreats Security Automation Architecture Topics PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Information Security Best Practices For Cloud Security Ppt Ideas Deck PDF
This slide represents the best practices for cloud security, such as the shared responsibility model, operations management, building controls, and processes and data encryption. Presenting information security best practices for cloud security ppt ideas deck pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security, measures, planning, teams, network. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Assessment Cloud Security Checklist Logging And Monitoring Information PDF
This slide defines the importance of logging and monitoring activities on data in a network and how it could be beneficial in future analysis.Presenting Cloud Security Assessment Cloud Security Checklist Logging And Monitoring Information PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Security Breaches, Access Sensitive, System Activities In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Checklist Logging And Monitoring Cloud Computing Security IT Ppt Show Example PDF
This slide defines the importance of logging and monitoring activities on data in a network and how it could be beneficial in future analysis. This is a cloud security checklist logging and monitoring cloud computing security it ppt show example pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like evaluation, organization, policies, potential, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Information Security SMB Cloud Security Solutions Ppt Show Files PDF
This slide shows the small and midsized business cloud security solutions, including multi-tenant information division, access control, legitimate data compliance, and cautious scaling of cloud frameworks. Presenting Cloud Information Security SMB Cloud Security Solutions Ppt Show Files PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Multi Tenant, Access Control, Information Division. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Developing IT Security Strategy Estimated Impact Of Information Security Risk Clipart PDF
This slide showcases capabilities of organization regarding information and data security after risk management plan. Its key components are risk management functions, required standard rating and actual standard rating. Find a pre-designed and impeccable Developing IT Security Strategy Estimated Impact Of Information Security Risk Clipart PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Cloud Security Threats Malware Attacks Cloud Computing Security IT Ppt Show Diagrams PDF
This slide represents the malware threat of cloud security and how it can affect data stored on the cloud, further leading to company loss. Presenting cloud security threats malware attacks cloud computing security it ppt show diagrams pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like cloud administrations, cyber criminals, technology. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
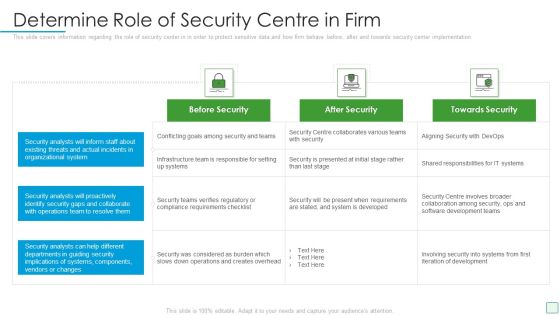
Developing Firm Security Strategy Plan Determine Role Of Security Centre In Firm Graphics PDF
This slide covers information regarding the role of security center in in order to protect sensitive data and how firm behave before, after and towards security center implementation. Deliver and pitch your topic in the best possible manner with this developing firm security strategy plan determine role of security centre in firm graphics pdf. Use them to share invaluable insights on before security, after security, towards security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
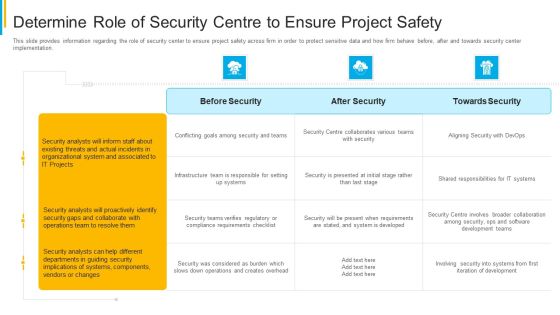
Project Security Administration IT Determine Role Of Security Centre To Ensure Project Safety Microsoft PDF
This slide provides information regarding the role of security center to ensure project safety across firm in order to protect sensitive data and how firm behave before, after and towards security center implementation. Deliver and pitch your topic in the best possible manner with this project security administration it determine role of security centre to ensure project safety microsoft pdf. Use them to share invaluable insights on before security, after security, towards security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
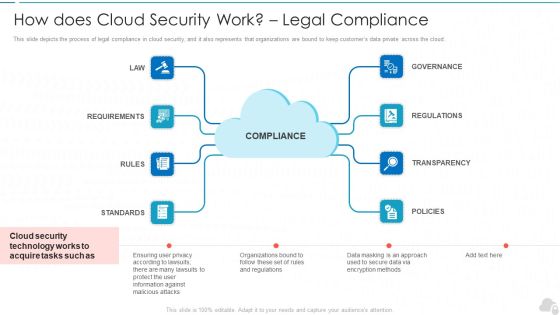
How Does Cloud Security Work Legal Compliance Cloud Computing Security IT Ppt Model Maker PDF
This slide depicts the process of legal compliance in cloud security, and it also represents that organizations are bound to keep customers data private across the cloud. This is a how does cloud security work legal compliance cloud computing security it ppt model maker pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like governance, regulations, transparency, policies, rules. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
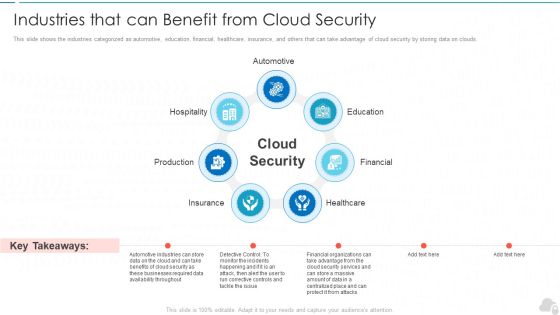
Industries That Can Benefit From Cloud Security Cloud Computing Security IT Ppt Professional PDF
This slide shows the industries categorized as automotive, education, financial, healthcare, insurance, and others that can take advantage of cloud security by storing data on clouds. This is a industries that can benefit from cloud security cloud computing security it ppt professional pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like production, hospitality, education, financial, healthcare. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Assessment Industries That Can Benefit From Cloud Security Topics PDF
This slide shows the industries categorized as automotive, education, financial, healthcare, insurance, and others that can take advantage of cloud security by storing data on clouds.This is a Cloud Security Assessment Industries That Can Benefit From Cloud Security Topics PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Automotive, Healthcare, Production You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Complete IT Security Implementation Checklist Ppt Layouts Graphics PDF
This slide depicts the network security checklist and measures an organization should take to protect data and company assets from network attacks or natural disasters. Presenting complete information technology security implementation checklist ppt file introduction pdf to provide visual cues and insights. Share and navigate important information on twelve stages that need your due attention. This template can be used to pitch topics like secure communications, device security, access control measures. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
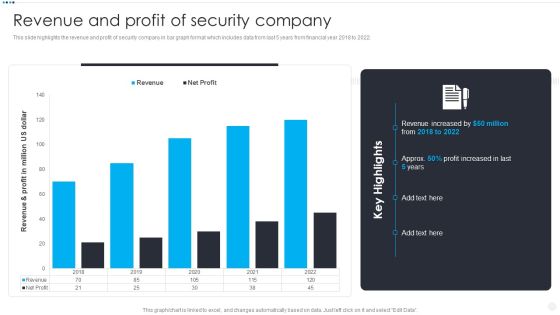
Smart Home Security Solutions Company Profile Revenue And Profit Of Security Company Elements PDF
This slide highlights the revenue and profit of security company in bar graph format which includes data from last 5 years from financial year 2018 to 2022. Deliver and pitch your topic in the best possible manner with this Smart Home Security Solutions Company Profile Revenue And Profit Of Security Company Elements PDF. Use them to share invaluable insights on Revenue And Profit, Million US Dollar, Revenue Increased Profit and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security And Surveillance Company Profile Revenue And Profit Of Security Company Microsoft PDF
This slide highlights the revenue and profit of security company in bar graph format which includes data from last 5 years from financial year 2018 to 2022.Deliver and pitch your topic in the best possible manner with this Security And Surveillance Company Profile Revenue And Profit Of Security Company Microsoft PDF. Use them to share invaluable insights on Revenue Increased, Increased In Last, Key Highlights and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
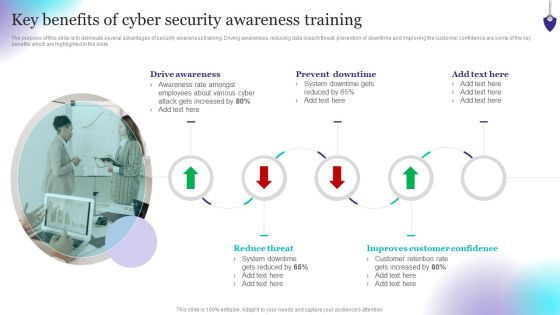
Organizing Security Awareness Key Benefits Of Cyber Security Awareness Training Rules PDF
The purpose of this slide is to delineate several advantages of security awareness training. Driving awareness, reducing data breach threat, prevention of downtime and improving the customer confidence are some of the key benefits which are highlighted in the slide. Make sure to capture your audiences attention in your business displays with our gratis customizable Organizing Security Awareness Key Benefits Of Cyber Security Awareness Training Rules PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
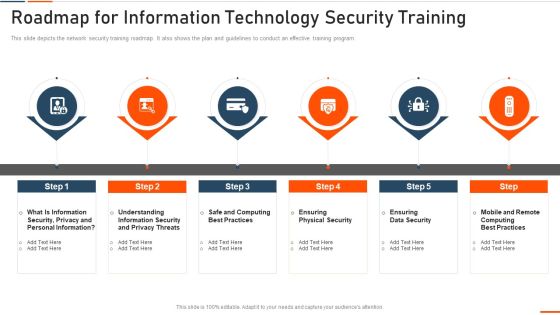
Roadmap For Information Technology Security Training Ppt Ideas Influencers PDF
This slide depicts the network security training roadmap. It also shows the plan and guidelines to conduct an effective training program. This is a roadmap for roadmap for information technology security training ppt ideas influencers pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like rmation security, computing best practices, physical security, data security . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

 Home
Home