Data Privacy

Information Technology Security Risk Assessment Grid Information PDF
The following slide depicts the analysis of IT security to prevent loss of confidentiality and integrity. The matrix constitutes of elements such as risk, likelihood, its impact and overall threat level. Persuade your audience using this Information Technology Security Risk Assessment Grid Information PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Loss Of Privacy, System Integrity, Loss Of Data. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
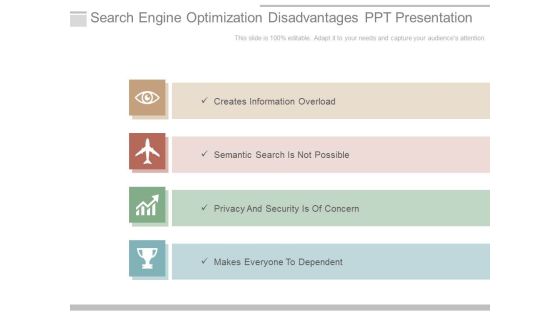
Search Engine Optimization Disadvantages Ppt Presentation
This is a search engine optimization disadvantages ppt presentation. This is a four stage process. The stages in this process are creates information overload, semantic search is not possible, privacy and security is of concern, makes everyone to dependent.

Naas Architectural Framework Naas As An Enabler For Cloud Transformation Brochure PDF
This slide talks about how NaaS works as a key driver for cloud transformation by providing secure and protected connectivity between businesses and their customers, internet of things devices with corporate applications, and so on. This modern and well-arranged Naas Architectural Framework Naas As An Enabler For Cloud Transformation Brochure PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Permission Based Email Marketing Status Checklist Guidelines PDF
This slide represents status of company implementing permission based email marketing to promote business. It include steps such as customer consent, customer privacy statement, provide unsubscribe option etc. with completion status. Showcasing this set of slides titled Permission Based Email Marketing Status Checklist Guidelines PDF. The topics addressed in these templates are Consumer Privacy, Security, Requirement. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
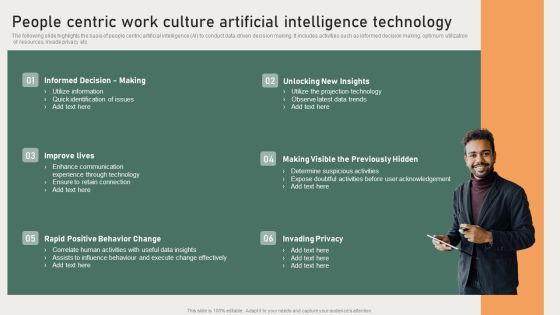
People Centric Work Culture Artificial Intelligence Technology Template PDF
The following slide highlights the basis of people centric artificial intelligence AI to conduct data driven decision making. It includes activities such as informed decision making, optimum utilization of resources, invade privacy etc. Persuade your audience using this People Centric Work Culture Artificial Intelligence Technology Template PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Improve Lives, Invading Privacy, Unlocking New Insights. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
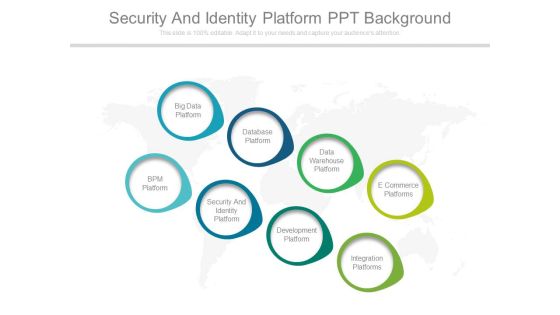
Security And Identity Platform Ppt Background
This is a security and identity platform ppt background. This is a eight stage process. The stages in this process are big data platform, database platform, data warehouse platform, e commerce platforms, bpm platform, security and identity platform, development platform, integration platforms.

Business Diagram 3d Lock With Pie Chart And Text Boxes For Business PowerPoint Slide
This Power Point diagram has been crafted with pie chart in shape of lock. It contains diagram of lock pie chart to compare and present data in an effective manner. Use this diagram to build professional presentations for your viewers.

Business Diagram 3d Lock With Pie Graph For Result Representation PowerPoint Slide
This Power Point diagram has been crafted with pie chart in shape of lock. It contains diagram of lock pie chart to compare and present data in an effective manner. Use this diagram to build professional presentations for your viewers.

Security Administration Powerpoint Shapes
This is a security administration powerpoint shapes. This is a three stage process. The stages in this process are storage management, directory service administration, security administration.

Datacenter Services Network Security Ppt Sample
This is a datacenter services network security ppt sample. This is a five stage process. The stages in this process are arrow, business, marketing.

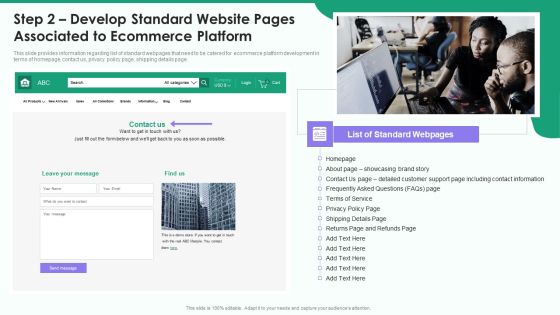
Retail Trading Platform Step 2 Develop Standard Website Pages Associated To Ecommerce Platform Demonstration PDF
This slide provides information regarding list of standard webpages that need to be catered for ecommerce platform development in terms of homepage, contact us, privacy policy page, shipping details page. This is a retail trading platform step 2 develop standard website pages associated to ecommerce platform demonstration pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like privacy policy page, shipping details page, contact information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Hacker Purpose Of Hackers Mockup PDF
This slide describes the common types of cybercrime such as identity theft, computer fraud, privacy breach, electronic money laundering, electronic funds transfer, and so on. This is a IT Security Hacker Purpose Of Hackers Mockup PDF template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Identity Theft, Computer Fraud, Privacy Breach. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Online Business Strategy Playbook Step 2 Develop Standard Website Pages Associated To Ecommerce Platform Themes PDF
This slide provides information regarding list of standard webpages that need to be catered for ecommerce platform development in terms of homepage, contact us, privacy policy page, shipping details page. This is a online business strategy playbook step 2 develop standard website pages associated to ecommerce platform themes pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like policy, privacy, shipping, details, refunds. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Reverse Proxy Server IT Why To Use Reverse Proxy Server Ppt Gallery Good PDF
This slide depicts why to use reverse proxy servers, including control over cyber loafing, bandwidth saving, privacy benefits, security, and access to blocked resources. Presenting reverse proxy server it why to use reverse proxy server ppt gallery good pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like employees, privacy benefits, advanced security, access to blocked, resources and websites. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Exploitation IT Purpose Of Hackers Infographics PDF
This slide describes the common types of cybercrime such as identity theft, computer fraud, privacy breach, electronic money laundering, electronic funds transfer, and so on. This is a cyber exploitation it purpose of hackers infographics pdf template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like computer fraud, privacy breach, electronic money laundering, electronic funds transfer, denial of service attacks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Terrorism Assault Three Major Forms Of Cyber Terrorism Brochure PDF
This slide describes the three major forms of cyber terrorism attacks such as privacy violation, networks damage, and disruptions, and distribution denial of service attack.This is a cyber terrorism assault three major forms of cyber terrorism brochure pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like privacy violation, networks damage and disruptions, distributed denial You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Minimum Cloud Security Standards For Saas And Paas Ppt PowerPoint Presentation Gallery Skills PDF
The following slide depicts the minimum security standards to protect software and platform as a service SaaS and PaaS. It includes elements such as encryption, authentication, security and privacy etc. along with high, medium and low risk level. Pitch your topic with ease and precision using this Minimum Cloud Security Standards For Saas And Paas Ppt PowerPoint Presentation Gallery Skills PDF. This layout presents information on Required Actions, Encryption, Security And Privacy. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Business Software Playbook Software Concept Phase TO DO Checklist Template PDF
This template covers checklist for software or application concept definition phase. It includes tasks such as meeting with privacy team, gain access for tools, design UI or UX interface, develop use case etc.Presenting Business Software Playbook Software Concept Phase TO DO Checklist Template PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Security Team, Privacy Team, Systems Architecture. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
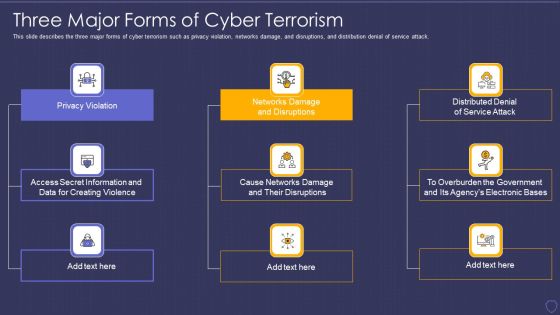
Global Cyber Terrorism Incidents On The Rise IT Three Major Forms Of Cyber Terrorism Topics PDF
This slide describes the three major forms of cyber terrorism such as privacy violation, networks damage, and disruptions, and distribution denial of service attack. Presenting global cyber terrorism incidents on the rise it three major forms of cyber terrorism topics pdf to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like privacy violation, networks damage and disruptions, distributed denial of service attack. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Micro Chip Disadvantages Of Biochip Ppt PowerPoint Presentation File Example Introduction PDF
This slide showcases the disadvantages of biochips, such as it is very expensive, the privacy of an individual is breached, and many such limitations. Presenting Micro Chip Disadvantages Of Biochip Ppt PowerPoint Presentation File Example Introduction PDF to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like Biochips Costly, Individual Privacy, Human Liberty. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Challenges And Solutions For Effective Medical Administration Brochure PDF
The following slide illustrates some major challenges and solutions in managing medical facilities to improve operating efficiencies. Some of the problems identified are as increasing cost, privacy issues, rising cybersecurity threats, fluctuating equipment cost etc. Persuade your audience using this Challenges And Solutions For Effective Medical Administration Brochure PDF. This PPT design covers one stage, thus making it a great tool to use. It also caters to a variety of topics including Increasing Cost, Privacy Issues, Rising Cybersecurity. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
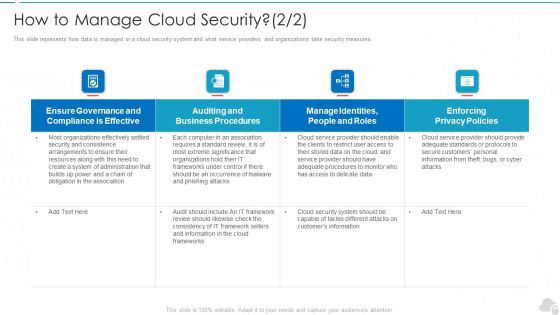
How To Manage Cloud Security Cloud Computing Security IT Ppt Infographic Template Inspiration PDF
This slide represents how data is managed in a cloud security system and what service providers and organizations take security measures. Deliver an awe inspiring pitch with this creative how to manage cloud security cloud computing security it ppt infographic template inspiration pdf bundle. Topics like effective, privacy policies, business procedures, frameworks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Smartphone Health Checkup App Comparison Portrait PDF
Pitch your topic with ease and precision using this Smartphone Health Checkup App Comparison Portrait PDF. This layout presents information on Store, Privacy Risk Index, Confidence Rating. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Terms Of Agreement Tutoring Service Proposal Ppt Summary Professional PDF
Deliver and pitch your topic in the best possible manner with this terms of agreement tutoring service proposal ppt summary professional pdf. Use them to share invaluable insights on definitions, privacy policy, payments, termination of service, user content and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Pros Cons Of IT Solutions Ppt PowerPoint Presentation Professional Rules
Presenting this set of slides with name pros cons of it solutions ppt powerpoint presentation professional rules. The topics discussed in these slides are implementation problems, technological fragmentation, privacy concerns, security concerns. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Business Analytics Execution Challenges And Solutions Ppt PowerPoint Presentation Ideas Sample PDF
Showcasing this set of slides titled business analytics execution challenges and solutions ppt powerpoint presentation ideas sample pdf. The topics addressed in these templates are getting funding for the transition, safeguarding privacy and security, solution. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Terms Of Agreement For Online Tutoring Services Ppt PowerPoint Presentation Slides Aids PDF
Presenting this set of slides with name terms of agreement for online tutoring services ppt powerpoint presentation slides aids pdf. The topics discussed in these slides are definitions, scope service, privacy policy, payments, user content, modifications service, termination service. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cloud Information Security What Are The Downsides Of A Cloud Security Ppt Infographics Files PDF
This slide describes the downsides of the cloud security system, including loss of control over data, data loss, insider theft, and data breaches. Presenting Cloud Information Security What Are The Downsides Of A Cloud Security Ppt Infographics Files PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Data Loss, Loss Control, Insider Theft, Data Breaches. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Major Indicators Of Cybersecurity Insider Threat In Cyber Security Microsoft PDF
This slide shows major indicators of cybersecurity insider threat along with mitigation strategies. It contains information about behavioral, information technology IT sabotage and data theft. Presenting Major Indicators Of Cybersecurity Insider Threat In Cyber Security Microsoft PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Behavioral, IT Sabotage, Data Theft. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cloud Information Security How Does Cloud Security Work Ppt Inspiration Graphics PDF
This slide describes how a cloud security system works and what controls or measures are implemented to secure the data over the cloud. This is a Cloud Information Security How Does Cloud Security Work Ppt Inspiration Graphics PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Data Security, Access Management, Legal Compliance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Information Security Why Cloud Security Is Important Ppt Diagrams PDF
This slide defines why cloud security is essential based on data centralization, cost, diminished control, and data reliability. This is a Cloud Information Security Why Cloud Security Is Important Ppt Diagrams PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Cost Effective, Diminished Administration, Centralized Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Integration Of Paas Whats Included In A Platform As A Service Paas Icons PDF
This slide describes the working of the platform as a service framework and it includes components such as users, applications, software, operating system, integrated development environment, network access, database, data security, data backup, application hosting, and hardware.. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Integration Of Paas Whats Included In A Platform As A Service Paas Icons PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Best Safety Practices For Saas Cloud Security Ppt PowerPoint Presentation Gallery Sample PDF
The following slide illustrates some best practices to ensure and maintain SaaS security. It includes activities such as creating security review checklist, training employees, hiring security service providers, establishing secure infrastructure, protecting data by monitoring etc. Presenting Best Safety Practices For Saas Cloud Security Ppt PowerPoint Presentation Gallery Sample PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Create Security Review Checklist, Train Employees, Establish Secure Infrastructure. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Architecture Of Cloud Security Cloud Information Security Ppt Inspiration Samples PDF
This slide defines the architecture of the cloud security system and how data is kept, managed, and secured based on customer and service providers responsibilities. This is a Architecture Of Cloud Security Cloud Information Security Ppt Inspiration Samples PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Customer Responsibility, Cloud Service, Provider Responsibility. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Information Security How Does Cloud Security Work Legal Compliance Ppt Layouts Templates PDF
This slide depicts the process of legal compliance in cloud security, and it also represents that organizations are bound to keep customers data private across the cloud. Presenting Cloud Information Security How Does Cloud Security Work Legal Compliance Ppt Layouts Templates PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Regulations Transparency, Standards Policies, Requirements Governance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Reverse Proxy Server IT Reverse Proxy Server Side Technology Security Ppt Professional Backgrounds PDF
This slide explains the reverse proxy server-side technology, that is security, and how data is transmitted securely in the presence of a proxy server that hides the actual servers identity. This is a reverse proxy server it reverse proxy server side technology security ppt professional backgrounds pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security proxy session, security proxy, host. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Optimizing Digital Marketing Strategy Discover What The Future Looks Like Infographics PDF
This template covers the process of using privacy sandbox to protect users online privacy. it includes steps such as matching conversion on an advertisers website with clicked ads, reporting without revealing the identity of users, aggregating the data, and limiting the amount of information shared. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Optimizing Digital Marketing Strategy Discover What The Future Looks Like Infographics PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Optimizing Digital Marketing Strategy Discover What The Future Looks Like Infographics PDF today and make your presentation stand out from the rest.

Apples Strategy To Achieve Top Brand Value Position How Advertisers Can Improve Business Through Revamped Infographics PDF
This slide provides information regarding transformed privacy landscape enabled by Apple and how advertisers can improve their business through such revamping by deploying privacy preservation methodologies, enable transition across advertising models, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Apples Strategy To Achieve Top Brand Value Position How Advertisers Can Improve Business Through Revamped Infographics PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

5G Network Applications And Features 5G Radio Access Network Architecture Overview Background PDF
This slide represents the overview of the 5G radio access network architecture and its components, including distributed unit, central unit, radio hardware unit, and so on. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created 5G Network Applications And Features 5G Radio Access Network Architecture Overview Background PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Key Monitoring Strategies To Counter Insider Threat In Cyber Security Demonstration PDF
This slide shows vital monitoring strategies for countering insider threat. It provides information about monitoring, protecting sensitive data, ascertaining user access, implementing least privilege model, applying security analytics and training employees. Persuade your audience using this Key Monitoring Strategies To Counter Insider Threat In Cyber Security Demonstration PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Monitoring User Data, Protecting Sensitive Data, Protecting Sensitive Data. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Business Information Application Protection Testing Flow Chart Themes PDF
This slide covers business application security testing flow chart which includes secure application model, security standard recognition and privacy testing.Pitch your topic with ease and precision using this Business Information Application Protection Testing Flow Chart Themes PDF. This layout presents information on Security Consistency, Target Weighting, Target Recognition. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Icon Of Security Computer System Interface For Securing Information Ppt Professional Background PDF
Persuade your audience using this Icon Of Security Computer System Interface For Securing Information Ppt Professional Background PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Icon Security Computer, System Interface Securing, Information. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Security Officer Service Company Profile Educational Institute And Hospital Security Services Ideas PDF
This slide highlights the security company services for educational institutes, hospitals, and health care centers. Major services include safe entry and exit of vehicles, safe environment to students and patients, check visitors etc. This is a Security Officer Service Company Profile Educational Institute And Hospital Security Services Ideas PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Provide Safe Environment, Safeguard Environment, Campus Patrolling. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Officer Service Company Profile Corporate And Industrial Security Services Demonstration PDF
This slide highlights the industrial and corporate security services by manpower security company which includes administer electronic access control, respond to alarms, visitor pass management and patrol inside the factory. Presenting Security Officer Service Company Profile Corporate And Industrial Security Services Demonstration PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Corporate Security, Industrial Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Organizing Security Awareness How Much Employees Are Aware Of Cyber Security Summary PDF
The purpose of this slide is to showcase the cyber security assessment test result. It covers information about the pass or fail rate of employees who received the security awareness training and fail rate by age. Find highly impressive Organizing Security Awareness How Much Employees Are Aware Of Cyber Security Summary PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Organizing Security Awareness How Much Employees Are Aware Of Cyber Security Summary PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Security Officer Service Company Profile Employees Rules And Regulations Inspiration PDF
This slide highlights the security guard company rules and regulations which showcases In and out time, note visitor name, and wear uniform at working hours. This is a Security Officer Service Company Profile Employees Rules And Regulations Inspiration PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Officer, Employees, Security Officer. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Officer Service Company Profile Staff Recruiting Criteria And Training Centre Microsoft PDF
This is a Security Officer Service Company Profile Staff Recruiting Criteria And Training Centre Microsoft PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Selection Criteria, Authorized Training Centre. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Officer Service Company Profile Employee And Staff Welfare Download PDF
This slide highlights the staff and employee welfare services which includes social security, insurance, medical, accommodation, pick and drop services. Presenting Security Officer Service Company Profile Employee And Staff Welfare Download PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Social Security, Insurance, Medical, Accommodation, Pick And Drop. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Saas Application Cloud Security Infrastructure Icon Ppt PowerPoint Presentation Gallery Introduction PDF
Persuade your audience using this Saas Application Cloud Security Infrastructure Icon Ppt PowerPoint Presentation Gallery Introduction PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Saas Application, Cloud Security, Infrastructure Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

IT Managing Cyber Security Incident Response Icon Ppt Portfolio Model PDF
Persuade your audience using this IT Managing Cyber Security Incident Response Icon Ppt Portfolio Model PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including IT Managing, Cyber Security, Incident Response, Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Security Officer Service Company Profile Mission Vision And Core Values Sample PDF
This slide highlights the security company long term and short term objectives which includes trust, collaboration, service, and innovation as base of core values. Presenting Security Officer Service Company Profile Mission Vision And Core Values Sample PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Core Values, Integrity, Commitment, Passion, Team work. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Strategies To Build Managing Cyber Security Incident Response Plan Demonstration PDF
This slide covers strategies to build cyber incident response plan. It involves strategies such as establish IR team, conduct threat analysis, develop procedures and train employees. Persuade your audience using this Strategies To Build Managing Cyber Security Incident Response Plan Demonstration PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Establish IR Team, Conduct Threat Analysis, Develop Procedures. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Seven Steps Of Incident Response Digital Risk Assessment Cycle Ppt Portfolio Introduction PDF
The following slide highlights the sevens steps of incident cyber security cycle illustrating detection, communication channel, impact assessment, communication, escalation, delegation and resolution, Persuade your audience using this Seven Steps Of Incident Response Digital Risk Assessment Cycle Ppt Portfolio Introduction PDF. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including Resolution, Detection, Communication Channels, Impact Assessment. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Our Market Selection Process Series A Capital Funding Elevator Pitch Deck For Real Estate Professional PDF
This slide highlights the companys process of selecting a suitable market based on various factors such as crime rates, disposable income, job specific location areas and millennial preferences. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Our Market Selection Process Series A Capital Funding Elevator Pitch Deck For Real Estate Professional PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Our Market Selection Process Series A Capital Funding Elevator Pitch Deck For Real Estate Professional PDF.
ESO System Icon Ppt PowerPoint Presentation Gallery Slides PDF
Persuade your audience using this ESO System Icon Ppt PowerPoint Presentation Gallery Slides PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including ESO System, Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Reverse Proxy Server IT Secure Client Connection To Proxy And Secure Proxy Connection Ppt Infographic Template Design Inspiration PDF
This slide represents the secure client to proxy and secure proxy to the content server and how it can be used for the information that needs to be transmitted securely. This is a reverse proxy server it secure client connection to proxy and secure proxy connection ppt infographic template design inspiration pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like server outside firewall, encrypted, secure, proxy, client. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
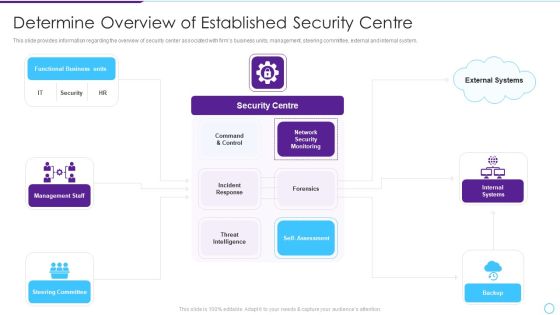
Intelligent Infrastructure Determine Overview Of Established Security Centre Introduction PDF
This slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. This is a Intelligent Infrastructure Determine Overview Of Established Security Centre Introduction PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Functional Business Units, Security Centre, Internal Systems, Self Assessment, Steering Committee. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Factors For Cloud Computing Security Assessment Ppt Gallery Deck PDF
Presenting Factors For Cloud Computing Security Assessment Ppt Gallery Deck PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Factors For, Cloud Computing, Security Assessment. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

IT Security Awareness Training Program Icons Ppt Layouts Structure PDF
Persuade your audience using this IT Security Awareness Training Program Icons Ppt Layouts Structure PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including IT Security Awareness, Training Program, Icons. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cloud Online Certificate Icon For Information Security Ppt Styles Example Introduction PDF
Persuade your audience using this Cloud Online Certificate Icon For Information Security Ppt Styles Example Introduction PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Cloud Online, Certificate Icon, Information Security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

 Home
Home