Data Privacy

Risk Management Model For Data Security Defining Vulnerability Rating With Criteria Mockup PDF
Following slide defines the vulnerability ranking set by the firm. It includes information about vulnerability ranking, criteria and its description. Deliver and pitch your topic in the best possible manner with this Risk Management Model For Data Security Defining Vulnerability Rating With Criteria Mockup PDF. Use them to share invaluable insights on Vulnerability Ranking, High, LOW, MEDIUM, Attack Organization, Occurrence Attack and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Risk Management Model For Data Security Risk Reporting And Likelihood Infographics PDF
Mentioned slide shows encountered risk reporting and its likelihood. It includes information about risk encountered, frequency, reported by status, attack scenario, affected asset and likelihood. Deliver an awe inspiring pitch with this creative Risk Management Model For Data Security Risk Reporting And Likelihood Infographics PDF bundle. Topics like Risk Encountered, Frequency, Attack Scenario, Affected Asset can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
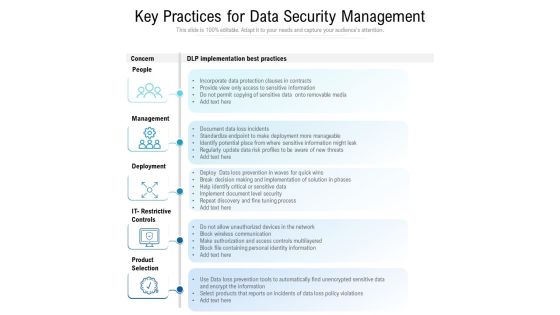
Key Practices For Data Security Management Ppt PowerPoint Presentation File Background Designs PDF
Persuade your audience using this key practices for data security management ppt powerpoint presentation file background designs pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including management, deployment, implementation. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cloud Computing Security Plan Five Years Roadmap For Data Protection Template
Introducing our cloud computing security plan five years roadmap for data protection template. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

Cloud Computing Security Plan Half Yearly Roadmap For Data Protection Formats
Presenting our innovatively structured cloud computing security plan half yearly roadmap for data protection formats Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

Data Breach Prevention Recognition Employee Security Awareness Training Budget Graphics PDF
This slide covers the training budget along with topics, provider, training date, duration, qualification, capability level and refresh or renewal status. Deliver an awe-inspiring pitch with this creative data breach prevention recognition employee security awareness training budget graphics pdf bundle. Topics like budget, capability level, renew, duration, qualification can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Data Breach Prevention Recognition Security Awareness New Strategies For Learning Download PDF
This slide covers effective ways to build cybersafe across an organization including key programs and approaches for the learning programs. Deliver an awe-inspiring pitch with this creative data breach prevention recognition security awareness new strategies for learning download pdf bundle. Topics like cybersafe across, organization, key programs, approaches, learning programs can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
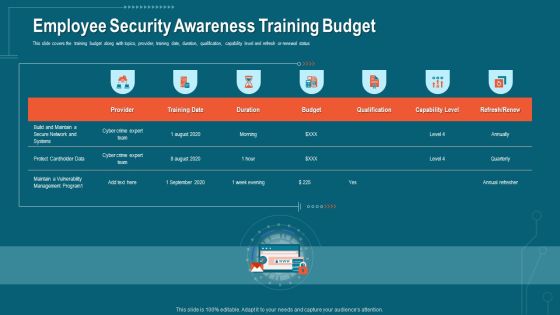
Companys Data Safety Recognition Employee Security Awareness Training Budget Formats PDF
This slide covers the training budget along with topics, provider, training date, duration, qualification, capability level and refresh or renewal status. Deliver an awe-inspiring pitch with this creative companys data safety recognition employee security awareness training budget formats pdf bundle. Topics like budget, capability level, training date, duration, qualification can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Companys Data Safety Recognition Security Awareness New Strategies For Learning Diagrams PDF
This slide covers effective ways to build cybersafe across an organization including key programs and approaches for the learning programs. Deliver and pitch your topic in the best possible manner with this companys data safety recognition security awareness new strategies for learning diagrams pdf. Use them to share invaluable insights on learning management, methodologies, risk profile and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
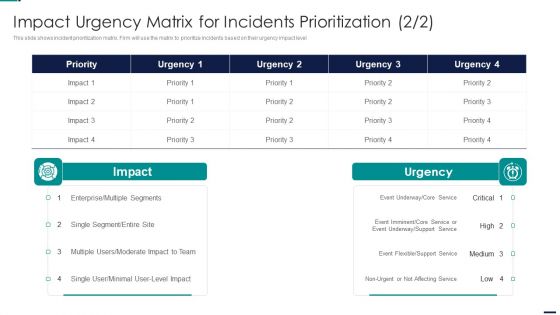
Impact Urgency Matrix For Incidents Risk Management Model For Data Security Pictures PDF
This slide shows incident prioritization matrix. Firm will use the matrix to prioritize incidents based on their urgency impact level. Deliver an awe inspiring pitch with this creative Impact Urgency Matrix For Incidents Risk Management Model For Data Security Pictures PDF bundle. Topics like Priority, Multiple Segments, Enterprise, Moderate Impact to Team can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Risk Management Model For Data Security Impact Urgency Matrix For Incidents Prioritization Ideas PDF
This slide shows incident prioritization matrix. Firm will use the matrix to prioritize incidents based on their urgency impact level. Deliver an awe inspiring pitch with this creative Risk Management Model For Data Security Impact Urgency Matrix For Incidents Prioritization Ideas PDF bundle. Topics like High System Wide, Medium Multiple Users, Low Single User, Inconvenient can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
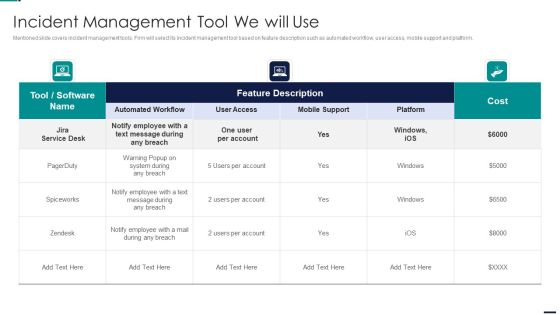
Risk Management Model For Data Security Incident Management Tool We Will Use Diagrams PDF
Mentioned slide covers incident management tools. Firm will select its incident management tool based on feature description such as automated workflow, user access, mobile support and platform. Deliver an awe inspiring pitch with this creative Risk Management Model For Data Security Incident Management Tool We Will Use Diagrams PDFbundle. Topics like Cost, Employee, Mobile Support, Automated Workflow, User Access can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Risk Management Model For Data Security Online And Onsite Training Schedule For Employee Rules PDF
This slide illustrates employee training schedule. It covers details about employee name, its position, software name, course type, training mode and duration. Deliver an awe inspiring pitch with this creative Risk Management Model For Data Security Online And Onsite Training Schedule For Employee Rules PDF bundle. Topics like Course Type, Training Mode, Training Duration, Employee can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
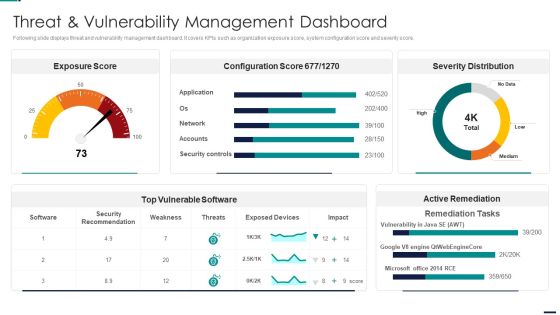
Risk Management Model For Data Security Threat And Vulnerability Management Dashboard Diagrams PDF
Following slide displays threat and vulnerability management dashboard. It covers KPIs such as organization exposure score, system configuration score and severity score. Deliver an awe inspiring pitch with this creative Risk Management Model For Data Security Threat And Vulnerability Management Dashboard Diagrams PDF bundle. Topics like Exposure Score, Configuration Score, Severity Distribution, Top Vulnerable Software, Active Remediation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Checklist For Work From Home Data Security Improving Cybersecurity With Incident Structure PDF
From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Checklist For Work From Home Data Security Improving Cybersecurity With Incident Structure PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Computer Data Storage Business Strategy PowerPoint Templates Ppt Backgrounds For Slides 0313
We present our Computer Data Storage Business Strategy PowerPoint Templates PPT Backgrounds For Slides 0313.Download our Technology PowerPoint Templates because It will let you Set new benchmarks with our PowerPoint Templates and Slides. They will keep your prospects well above par. Use our Communication PowerPoint Templates because You canTake a leap off the starting blocks with our PowerPoint Templates and Slides. They will put you ahead of the competition in quick time. Use our Success PowerPoint Templates because These PowerPoint Templates and Slides will give the updraft to your ideas. See them soar to great heights with ease. Use our Security PowerPoint Templates because Our PowerPoint Templates and Slides are topically designed to provide an attractive backdrop to any subject. Download our Business PowerPoint Templates because Our PowerPoint Templates and Slides are innately eco-friendly. Their high recall value negate the need for paper handouts.Use these PowerPoint slides for presentations relating to one computer server with a shape, concept of remote data storage, business, communication, technology, security, success. The prominent colors used in the PowerPoint template are Blue, White, Black.

Data Safety Risk Management Ppt PowerPoint Presentation Complete Deck With Slides
This data safety risk management ppt powerpoint presentation complete deck with slides acts as backup support for your ideas, vision, thoughts, etc. Use it to present a thorough understanding of the topic. This PPT slideshow can be utilized for both in-house and outside presentations depending upon your needs and business demands. Entailing sixteen slides with a consistent design and theme, this template will make a solid use case. As it is intuitively designed, it suits every business vertical and industry. All you have to do is make a few tweaks in the content or any other component to design unique presentations. The biggest advantage of this complete deck is that it can be personalized multiple times once downloaded. The color, design, shapes, and other elements are free to modify to add personal touches. You can also insert your logo design in this PPT layout. Therefore a well-thought and crafted presentation can be delivered with ease and precision by downloading this data safety risk management ppt powerpoint presentation complete deck with slides PPT slideshow.

Information Security Elements Of Data Security Application Security Ppt Slides Master Slide PDF
This slide defines application security and categories of application threats and tools to perform application security to prevent cyberattacks. This is a information security elements of data security application security ppt slides master slide pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like required, applications, information, customers, developers. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Professional Data Certification Program Global Information Assurance Certification GIAC Certification Roadmap Sample PDF
This slide covers cyber security certifications Roadmap in security administration, management, legal, audit, forensics and software security. Deliver and pitch your topic in the best possible manner with this IT Professional Data Certification Program Global Information Assurance Certification GIAC Certification Roadmap Sample PDF. Use them to share invaluable insights on Cloud Security, Management, Security Expert and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Semantic Data Searching Technique How Is The Semantic Web Different Than Other Technologies Elements PDF
This slide talks about the distinction between the semantic web with other technologies. It includes representing the meaning of data, use of natural language processing and semantic search that changes the way of storing, accessing, and conveying information. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Semantic Data Searching Technique How Is The Semantic Web Different Than Other Technologies Elements PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Information Security Latest Threats In Data Security Ppt Summary Slides PDF
This slide depicts the categories of recent threats that recently emerged in the United States, United Kingdom, and Australia in previous years. This is a information security latest threats in data security ppt summary slides pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like dridex malware, romance scams, emotet malware. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Risk Management Model For Data Security Defining Categories Of Information Security Threats Graphics PDF
This slide shows the categorization of information security threats. Categories covered are human error, natural disaster, software attacks and environmental control failures. Presenting Risk Management Model For Data Security Defining Categories Of Information Security Threats Graphics PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Human Error, Natural Disaster, Deliberate Software Attacks, Environmental Control Failures. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
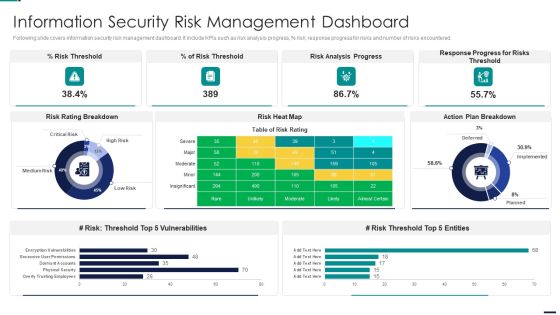
Risk Management Model For Data Security Information Security Risk Management Dashboard Pictures PDF
Following slide covers information security risk management dashboard. It include KPIs such as risk analysis progress, percent risk, response progress for risks and number of risks encountered. Deliver an awe inspiring pitch with this creative Risk Management Model For Data Security Information Security Risk Management Dashboard Pictures PDF bundle. Topics like Risk Threshold, Risk Analysis Progress, Response Progress For Risks Threshold, Action Plan Breakdown can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Table Of Contents For Data Breach Prevention Recognition Ppt Model Skills PDF
Presenting table of contents for data breach prevention recognition ppt model skills pdf to provide visual cues and insights. Share and navigate important information on fourteen stages that need your due attention. This template can be used to pitch topics like budget, communication plan, security awareness, security programs, cost. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
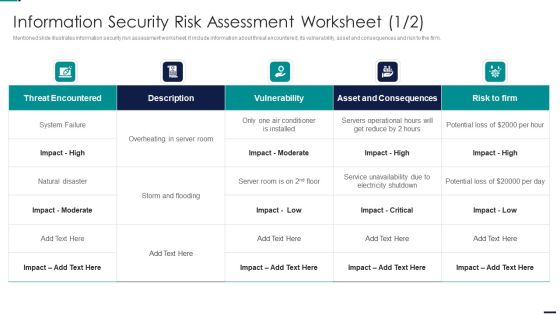
Information Security Risk Assessment Worksheet Risk Management Model For Data Security Designs PDF
Mentioned slide illustrates information security risk assessment worksheet. It include information about threat encountered, its vulnerability, asset and consequences and risk to the firm. Deliver and pitch your topic in the best possible manner with this Information Security Risk Assessment Worksheet Risk Management Model For Data Security Designs PDF. Use them to share invaluable insights on Threat Encountered, Vulnerability, Asset And Consequences, Risk To Firm and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Risk Management Model For Data Security Budget For Information Security Management Sample PDF
Mentioned slide shows budget for managing information security. It includes information such as functional area, software name, training duration, training cost, number of employees and total training cost. Deliver an awe inspiring pitch with this creative Risk Management Model For Data Security Budget For Information Security Management Sample PDF bundle. Topics like Functional Area, Training Duration, Risk Management, Incident Management, Asset Management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Security How Is Automation Used In Data Security Ppt Model Graphics Template PDF
This slide depicts the cyber protection of an organization through artificial intelligence and how it can be helpful in threat detection, threat response, and human augmentation. Presenting information security how is automation used in data security ppt model graphics template pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like threat detection, threat response, human augmentation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
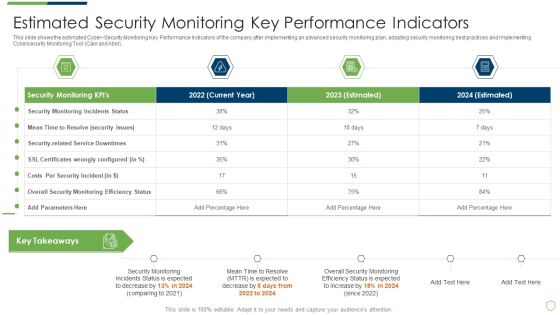
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Estimated Security Monitoring Guidelines PDF
This slide shows the estimated Cyber Security Monitoring Key Performance Indicators of the company after implementing an advanced security monitoring plan, adopting security monitoring best practices and implementing Cybersecurity Monitoring Tool Cain and Abel. Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach estimated security monitoring guidelines pdf. Use them to share invaluable insights on estimated security monitoring key performance indicators and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
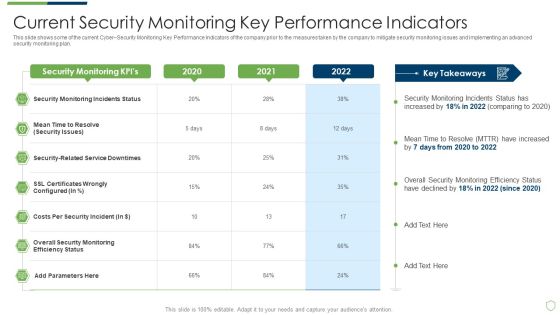
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Current Security Monitoring Pictures PDF
This slide shows some of the current Cyber Security Monitoring Key Performance Indicators of the company prior to the measures taken by the company to mitigate security monitoring issues and implementing an advanced security monitoring plan. Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach current security monitoring pictures pdf. Use them to share invaluable insights on current security monitoring key performance indicators and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
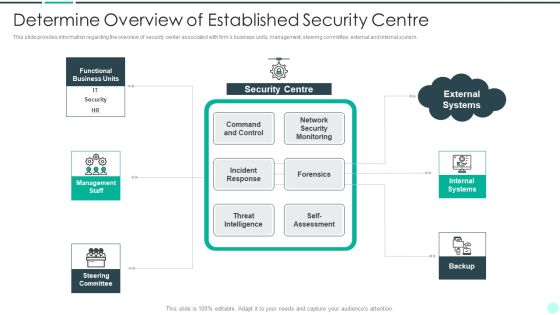
Executing Advance Data Analytics At Workspace Determine Overview Of Established Topics PDF
This slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. Deliver an awe inspiring pitch with this creative executing advance data analytics at workspace determine overview of established topics pdf bundle. Topics like determine overview of established security centre can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

1 Computer Behind A Firewall With Outgoing Data And Network Switch Ppt Slides
This image slide displays computer behind a firewall with outgoing data and network switch. This image slide has been crafted with graphic of computer, cloud, server and firewall icon. This image slide depicts cloud computing security. You may change size, color and orientation of any icon to your liking. Use this PowerPoint template, in your presentations to explain concepts like cloud computing, technology, networking and security. This image slide will enhance the quality of your presentations.

Risk Management Model For Data Security Present Security Management Capabilities Of The Firm Elements PDF
Following slide shows the current security management capabilities of the firm. It covers details about core functions, its description, key enablers, required and actual standard ratings. Deliver and pitch your topic in the best possible manner with this Risk Management Model For Data Security Present Security Management Capabilities Of The Firm Elements PDF. Use them to share invaluable insights on Core Functions, Key Enablers, Required Standard Rating, Actual Standard Rating and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

5 Steps To Improve Data Protection In Financial Institution Industry Guidelines PDF
This slide signifies the five stages to improve information protection in banking industry. It covers authentication, audit trails, secure infrastructure, processes and continuous communication. Presenting 5 Steps To Improve Data Protection In Financial Institution Industry Guidelines PDF to dispense important information. This template comprises Five stages. It also presents valuable insights into the topics including Authentication, Audit Trails, Secure Infrastructure. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Data Breach Prevention Recognition Highest Number Of Malware Attacks On Departments Pictures PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver and pitch your topic in the best possible manner with this data breach prevention recognition highest number of malware attacks on departments pictures pdf. Use them to share invaluable insights on sales department, accounts department, it department and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Companys Data Safety Recognition Highest Number Of Malware Attacks On Departments Sample PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver an awe-inspiring pitch with this creative companys data safety recognition highest number of malware attacks on departments sample pdf bundle. Topics like sales department, accounts department, it department can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Data Safety Initiatives Action Plan In Case Of Breaches Mockup PDF
Mentioned slide illustrates the mitigation plan of the company in case of any security breach. Sections covered are threat encountered, risk level, resources required and expected resolution time. Deliver an awe inspiring pitch with this creative data safety initiatives action plan in case of breaches mockup pdf bundle. Topics like threat encountered, security breach, system failure can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Table Of Contents For Companys Data Safety Recognition Ppt Professional Shapes PDF
This is a table of contents for companys data safety recognition ppt professional shapes pdf template with various stages. Focus and dispense information on fourteen stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like tracking, impact, budget, communication plan, security awareness. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Data Analysis Reporting Tools Ppt PowerPoint Presentation Professional Layout Cpb Pdf
Presenting this set of slides with name data analysis reporting tools ppt powerpoint presentation professional layout cpb pdf. This is an editable Powerpoint four stages graphic that deals with topics like cyber security detection response to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Data Center Infrastructure Management IT What Are Service Meshes Slides PDF
This slide depicts service meshes and how it works to enable speedy, reliable and secure communication among containerized and temporary application infrastructure services. Deliver and pitch your topic in the best possible manner with this data center infrastructure management it what are service meshes slides pdf. Use them to share invaluable insights on service, communication, infrastructure, capabilities and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Confidential Computing System Technology Technologies Used To Protect Data In Use Inspiration PDF
This slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Confidential Computing System Technology Technologies Used To Protect Data In Use Inspiration PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Confidential Computing System Technology Technologies Used To Protect Data In Use Inspiration PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

IT Professional Data Certification Program Cisco Certified Network Professional CCNP Training Courses Professional PDF
This slide covers Cisco Certified Network Professional CCNP training courses such CCNA, specialist, CNP and CCIE. Presenting IT Professional Data Certification Program Cisco Certified Network Professional CCNP Training Courses Professional PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Security, Enterprise, Service Provider. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Paying Loads Of Money To Manage Big Data Ppt PowerPoint Presentation File Files PDF
Presenting Paying Loads Of Money To Manage Big Data Ppt PowerPoint Presentation File Files PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Services, Extreme Security, Required Frameworks. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Executing Advance Data Analytics At Workspace Tracking Intelligence Infrastructure Elements PDF
This slide portrays information regarding tracking essential activities in intelligence infrastructure dashboard in terms of IT operations, security, business analytics, internet of things, etc. Deliver an awe inspiring pitch with this creative executing advance data analytics at workspace tracking intelligence infrastructure elements pdf bundle. Topics like leveraging potential technologies beneficial to firm can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Professional Data Certification Program Cisco Certified Internetwork Expert CCIE Certification Levels Slides PDF
This slide covers Cisco Certified Internetwork Expert CCIE Certification Levels such as entry, associate, professionals and experts along with technologies. Deliver and pitch your topic in the best possible manner with this IT Professional Data Certification Program Cisco Certified Internetwork Expert CCIE Certification Levels Slides PDF. Use them to share invaluable insights on Service Provider, Security, Network Programmability and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
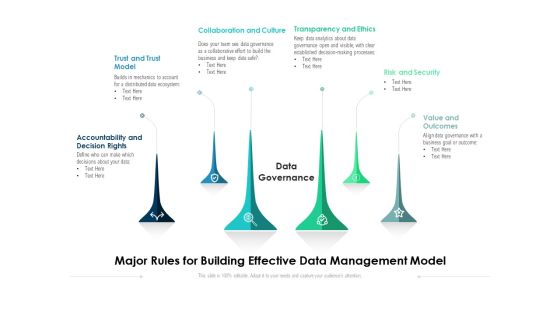
Major Rules For Building Effective Data Management Model Ppt PowerPoint Presentation File Design Inspiration PDF
Presenting major rules for building effective data management model ppt powerpoint presentation file design inspiration pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including risk and security, collaboration and culture, transparency and ethics. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
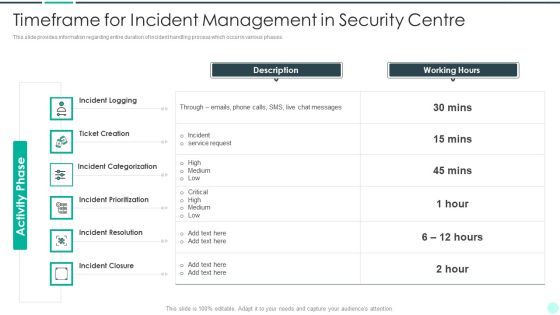
Executing Advance Data Analytics At Workspace Timeframe For Incident Management Download PDF
This slide provides information regarding entire duration of incident handling process which occur in various phases.Deliver and pitch your topic in the best possible manner with this executing advance data analytics at workspace timeframe for incident management download pdf. Use them to share invaluable insights on timeframe for incident management in security centre and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Executing Advance Data Analytics At Workspace Addressing Business Intelligence Background PDF
This slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations. Deliver an awe inspiring pitch with this creative executing advance data analytics at workspace addressing business intelligence background pdf bundle. Topics like contingency plan for threat handling in security centre can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
IT Data Services Certification Programs Comptia A Certification Courses Details Formats PDF
Presenting IT Data Services Certification Programs Comptia A Certification Courses Details Formats PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Security Certification Course, Network Administrator, Systems Administrator. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Professional Data Certification Program Comptia A Certification Salary And Job Details Elements PDF
This slide covers details CompTIA A Certification Salary expectations, Job Details and experience rating, expected demand, career path etc. Deliver an awe inspiring pitch with this creative IT Professional Data Certification Program Comptia A Certification Salary And Job Details Elements PDF bundle. Topics like Fundamentals, Information, Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Data Breach Prevention Recognition Communication Plan For Cybersecurity Events And Incidents Pictures PDF
This slide covers the communication delivery channels for cyber security awareness training for different departments target audience along with program topics. Deliver and pitch your topic in the best possible manner with this data breach prevention recognition communication plan for cybersecurity events and incidents pictures pdf. Use them to share invaluable insights on communication plan for cybersecurity events and incidents and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Companys Data Safety Recognition Communication Plan For Cybersecurity Events And Incidents Themes PDF
This slide covers the communication delivery channels for cyber security awareness training for different departments target audience along with program topics. Deliver an awe-inspiring pitch with this creative companys data safety recognition communication plan for cybersecurity events and incidents themes pdf bundle. Topics like department awareness training, resources training can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

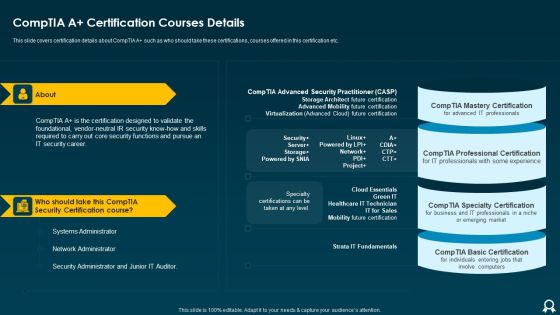
IT Professional Data Certification Program Comptia A Certification Courses Details Professional PDF
This slide covers certification details about CompTIA A such as who should take these certifications, courses offered in this certification etc. Deliver and pitch your topic in the best possible manner with this IT Professional Data Certification Program Comptia A Certification Courses Details Professional PDF. Use them to share invaluable insights on Network Administrator, Systems Administrator, Security Administrator and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Predictive Analytics In The Age Of Big Data Outliers Model For Predictive Analytics Demonstration PDF
This slide talks about the outliers model used for predictive analytics, including its use cases, impact and algorithm used in it, such as the generalized linear model for two values. This model helps banking, finance, and cyber security organizations to detect fraud and cyber crimes. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Predictive Analytics In The Age Of Big Data Outliers Model For Predictive Analytics Demonstration PDF can be your best option for delivering a presentation. Represent everything in detail using Predictive Analytics In The Age Of Big Data Outliers Model For Predictive Analytics Demonstration PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
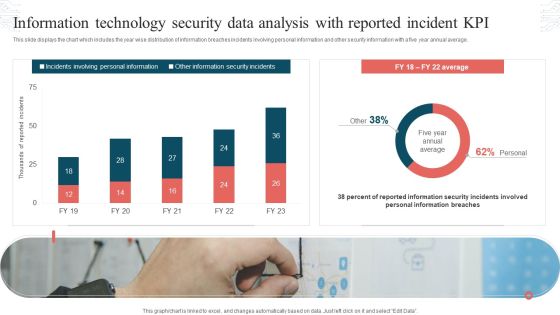
Information Technology Security Data Analysis With Reported Incident KPI Download PDF
This slide displays the chart which includes the year wise distribution of information breaches incidents involving personal information and other security information with a five year annual average. Showcasing this set of slides titled Information Technology Security Data Analysis With Reported Incident KPI Download PDF. The topics addressed in these templates are Incidents Involving, Personal Information, Other Information, Security Incidents. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Risk Management Model For Data Security Roles And Responsibilities For Managing Information Professional PDF
Following slide demonstrates various roles and responsibilities for information security management. Responsibilities covered are security policy development, asset classification and security framework development. This is a Risk Management Model For Data Security Roles And Responsibilities For Managing Information Professional PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Role, Position, Responsibility, Chief Information Officer, Information Management Manager. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Data Breach Prevention Recognition Where Is The Gap In Security Programs Summary PDF
This slide covers the problems in the organization regarding security awareness training along with the gap and solution to overcome those gaps. This is a data breach prevention recognition where is the gap in security programs summary pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like problems, solutions, gap. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Redis Cache Data Structure IT Harden The Server For Security Of Redis Cache Template PDF
This slide depicts the two components essential to harden the security of the Redis cache server, which includes adding the necessary security setting to both the Redis application as well as server. This is a redis cache data structure it harden the server for security of redis cache template pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like harden the server for security of redis cache. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Data Safety Initiatives Information Security Program Values To Business Background PDF
Following slide displays the major program values to companys business. Values here are divided in two areas namely detection and response and attack surface management. This is a data safety initiatives information security program values to business background pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like detection and response, attack surface management, current network. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Strategic Tips To Improve Physical Data Center Management Security Download PDF
This slide highlights tips to improve security of physical datacentre by having a thorough understanding of security measures and service level agreements. It covers secure location, physical access controls with building management security. Presenting Strategic Tips To Improve Physical Data Center Management Security Download PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Secure Location, Physical Access Controls, Secure Building Management Systems. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Redis Cache Data Structure IT Encrypted Password For Securing Redis Settings Formats PDF
This slide represents encrypted passwords for securing Redis settings, including using a minimum of 16 characters and avoiding words or phrases. This is a redis cache data structure it encrypted password for securing redis settings formats pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like encrypted password for securing redis settings. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
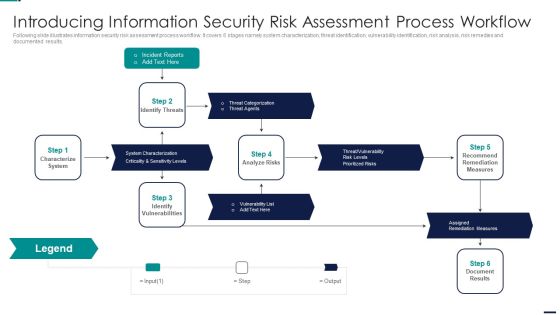
Risk Management Model For Data Introducing Information Security Risk Assessment Process Sample PDF
Following slide illustrates information security risk assessment process workflow. It covers 6 stages namely system characterization, threat identification, vulnerability identification, risk analysis, risk remedies and documented results. This is a Risk Management Model For Data Introducing Information Security Risk Assessment Process Sample PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Incident Reports, Characterize System, Identify Vulnerabilities, Assigned Remediation Measures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Data Safety Initiatives Defining Business Priorities To Ensure Information Security Slides PDF
This slide illustrates the key business priorities of the organization such as efficient risk management, standardized incident management process to ensure information security. This is a data safety initiatives defining business priorities to ensure information security slides pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like efficient risk management, transparent communication, standardized incident management process. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Companys Data Safety Recognition Security Awareness Tracking Kpis Culture Mockup PDF
This slide covers the key performance for security awareness training including compliance, security culture and incident reduction. This is a companys data safety recognition security awareness tracking kpis culture mockup pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like compliance, incident reduction, security culture. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Companys Data Safety Recognition Where Is The Gap In Security Programs Infographics PDF
This slide covers the problems in the organization regarding security awareness training along with the gap and solution to overcome those gaps. This is a companys data safety recognition where is the gap in security programs infographics pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like problems, gap, solutions. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Professional Data Certification Program Certified Information Systems Security Professional CISSP Details Portrait PDF
This slide covers CISSP certification details such as what is the CISSP, how to become certified, how to prepare for CISSP and why to get CISSP certifications. This is a IT Professional Data Certification Program Certified Information Systems Security Professional CISSP Details Portrait PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Organization, Customers, Access Management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Data Security Theft Or Loss Of Intellectual Property Microsoft PDF
This slide represents the loss of intellectual property threat and how organizations get affected by these types of risks. This is a Cloud Data Security Theft Or Loss Of Intellectual Property Microsoft PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Organizations, Businesses, Information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Data Services Certification Programs Certified Information Systems Security Professional CISSP Details Brochure PDF
This slide covers CISSP certification details such as what is the CISSP, how to become certified, how to prepare for CISSP and why to get CISSP certifications. Presenting IT Data Services Certification Programs Certified Information Systems Security Professional CISSP Details Brochure PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Software Engineering Technology, Network Security, Telecommunications. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Data Safety Initiatives Eliminating Manual Security Processes Through Automation Topics PDF
Mentioned slide displays the workflow process of how company will eliminate its existing manual security processes through automation tools. This is a data safety initiatives eliminating manual security processes through automation topics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like manual vulnerability, scanning and resolution, vulnerability scanning, team. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Data Breach Prevention Recognition Impact Of Security Awareness Training Sample PDF
This slide covers the good impact of security awareness program such as declining in the number of security threats which are phishing, network intrusion, inadvertent disclosure, stolen or lost devices or records and system misconfiguration. Deliver an awe-inspiring pitch with this creative data breach prevention recognition impact of security awareness training sample pdf bundle. Topics like security awareness program, security threats, network intrusion, inadvertent disclosure, system misconfiguration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Table Of Contents For Developing IT Security Strategy To Prevent Data Assets Pictures PDF
Slidegeeks has constructed Table Of Contents For Developing IT Security Strategy To Prevent Data Assets Pictures PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Table Of Contents For Developing IT Security Strategy To Prevent Data Assets Guidelines PDF
Do you know about Slidesgeeks Table Of Contents For Developing IT Security Strategy To Prevent Data Assets Guidelines PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
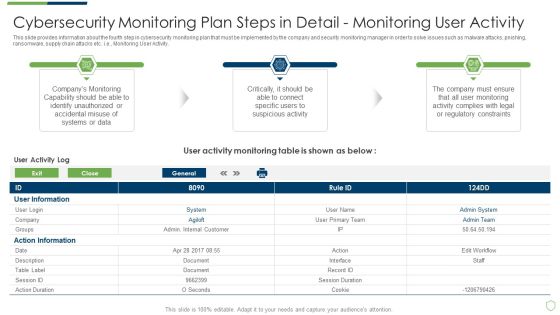
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Structure PDF
This slide provides information about some of the best security monitoring tools that are available with the security monitoring manager and what tool is selected by the security monitoring manager based on tool implementation costs, tool implementation time etc. Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring structure pdf. Use them to share invaluable insights on cybersecurity monitoring tools to be implemented and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Data Safety Initiatives For Effective IT Security Threats Administration Ppt PowerPoint Presentation Complete Deck With Slides
Pitch yourself both in house and outside by utilizing this complete deck. This data safety initiatives for effective it security threats administration ppt powerpoint presentation complete deck with slides focuses on key fundamentals of the topic, displayed using different slides. With a total of fifty six slides, this template is the best tool you can use to persuade your audience. It will not only help you create great presentations but also induce strategic thinking because of its well researched content and graphics. You can easily personalize any of the elements to suit your unique business setting. Additionally, it can be saved in PNG, JPG, and PDF formats to save your time and resources.

Developing IT Security Strategy To Prevent Data Assets Ppt PowerPoint Presentation Complete Deck With Slides
Use this Developing IT Security Strategy To Prevent Data Assets Ppt PowerPoint Presentation Complete Deck With Slides to ensure the business world gets to know you as a presentation expert with tremendous recall value. With its focus on providing the worlds best designs to highlight business ideas that have the potential to change the world, this PPT Template is sure to win you clients. The complete deck in seventy one slides is a compendium of information, structured in a manner that provides the best framework for a presentation. Use this completely editable and customizable presentation to make an impact and improve your order book. Download now.
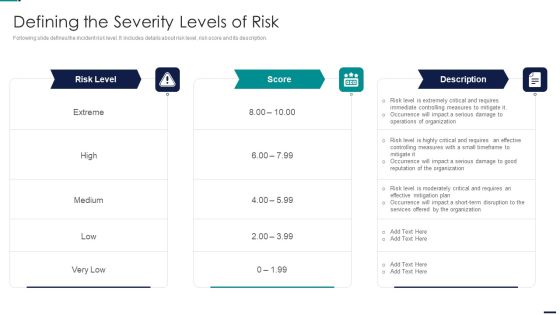
Risk Management Model For Data Security Defining The Severity Levels Of Risk Clipart PDF
Following slide defines the incident risk level. It includes details about risk level, risk score and its description. This is a Risk Management Model For Data Security Defining The Severity Levels Of Risk Clipart PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Risk Level, Score, High, Low, Medium, Operations, Organization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Companys Data Safety Recognition Impact Of Security Awareness Training Demonstration PDF
This slide covers the good impact of security awareness program such as declining in the number of security threats which are phishing, network intrusion, inadvertent disclosure, stolen or lost devices or records and system misconfiguration. Deliver an awe-inspiring pitch with this creative companys data safety recognition impact of security awareness training demonstration pdf bundle. Topics like system misconfiguration, inadvertent disclosure, network intrusion can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Emerging Cyber Security Incident And Data Breaches Amid Pandemic Ppt Ideas Skills PDF
The given slide reflects the upcoming cyber threats due to remote working amid of COVID -19. Some of them are pandemic associated attacks, cloud breaches and mobile security threats. Persuade your audience using this Emerging Cyber Security Incident And Data Breaches Amid Pandemic Ppt Ideas Skills PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Pandemic Associated Attacks, Cloud Breaches, Mobile Security Threats. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Data Safety Initiatives KPI Dashboard To Track Security Risk Events Portrait PDF
This slide displays KPI dashboard that company will use to track multiple risk events. Metrics covered in the dashboard are residual risks by period and risk category by total risk rating. Deliver and pitch your topic in the best possible manner with this data safety initiatives kpi dashboard to track security risk events portrait pdf. Use them to share invaluable insights on risk category, total risk rating, residual risk by period, technology risk and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Hurdles In Business Data Security In Trade Secret Ppt PowerPoint Presentation Pictures Master Slide PDF
Showcasing this set of slides titled hurdles in business data security in trade secret ppt powerpoint presentation pictures master slide pdf. The topics addressed in these templates are once trade secret is made public, it can be accessed by anyone, difficult to enforce than patent, level of protection granted to trade is generally considered weak and is different from country country. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Redis Cache Data Structure IT Implement Traffic Monitoring To Secure Redis Server Ideas PDF
This slide describes implementing traffic monitoring to check the usage patterns and raise flags to incase anything unusual happens. Presenting redis cache data structure it implement traffic monitoring to secure redis server ideas pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like management, system, location. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
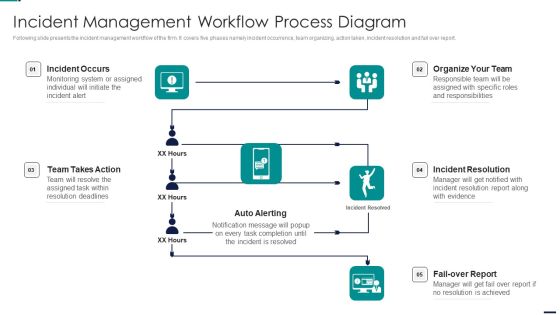
Risk Management Model For Data Security Incident Management Workflow Process Diagram Topics PDF
Following slide presents the incident management workflow of the firm. It covers five phases namely incident occurrence, team organizing, action taken, incident resolution and fail over report. Presenting Risk Management Model For Data Security Incident Management Workflow Process Diagram Topics PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Incident Occurs, Organize Team, Incident Resolution, Fail Over Report, Auto Alerting, Team Takes Action. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
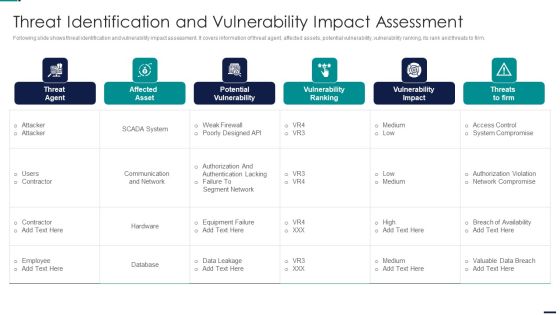
Risk Management Model For Data Security Threat Identification And Vulnerability Impact Slides PDF
Following slide shows threat identification and vulnerability impact assessment. It covers information of threat agent, affected assets, potential vulnerability, vulnerability ranking, its rank and threats to firm. Deliver and pitch your topic in the best possible manner with this Risk Management Model For Data Security Threat Identification And Vulnerability Impact Slides PDF. Use them to share invaluable insights on Threat Agent, Affected Asset, Potential Vulnerability, Vulnerability Ranking and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cloud Computing Security Plan Six Months Roadmap For Data Protection Themes
Presenting our jaw dropping cloud computing security plan six months roadmap for data protection themes. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.

Cloud Computing Security Plan Three Months Roadmap For Data Protection Structure
Presenting the cloud computing security plan three months roadmap for data protection structure. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
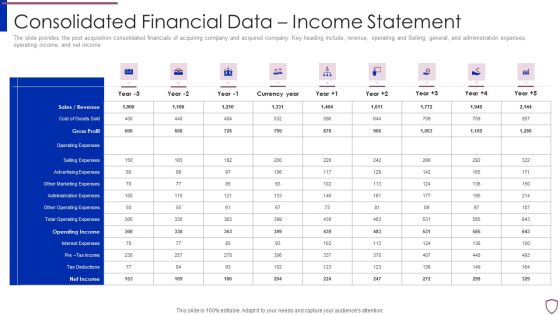
Financing Catalogue For Security Underwriting Agreement Consolidated Financial Data Income Statement Template PDF
The slide provides the post acquisition consolidated financials of acquiring company and acquired company. Key heading include, revenue, operating and Selling, general, and administration expenses, operating income, and net income. Deliver and pitch your topic in the best possible manner with this financing catalogue for security underwriting agreement consolidated financial data income statement template pdf. Use them to share invaluable insights on sales or revenue, cost of goods sold, gross profit, operating expenses, selling expenses and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Risk Management Model For Data Security Asset Criticality Of Identified System Components Topics PDF
Following slide demonstrates the asset criticality of identified system components. It covers details such as system name, component used, impact rating, criticality rating and failure cost. Deliver and pitch your topic in the best possible manner with this Risk Management Model For Data Security Asset Criticality Of Identified System Components Topics PDF. Use them to share invaluable insights on Impact Rating On Business, Criticality Rating, Failure Cost and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Risk Management Model For Data Security Mitigation Plan For Resolving Encountered Threat Icons PDF
Mentioned slide shows mitigation plan for resolving encountered threat. It covers details about encountered threat, its description, risk level, mitigation plan, resources required, responsible person, expected resolution time and communication mode. Deliver and pitch your topic in the best possible manner with this Risk Management Model For Data Security Mitigation Plan For Resolving Encountered Threat Icons PDF. Use them to share invaluable insights on Threat Encountered, Risk Level, Mitigation Plan, Resources Required and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
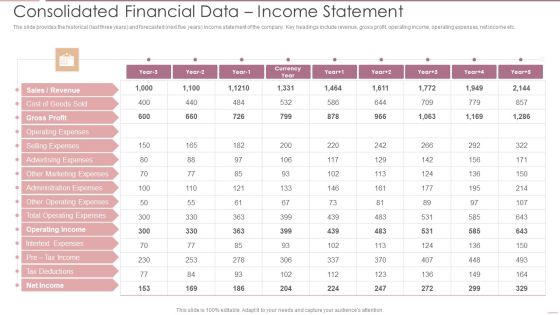
Investment Banking Security Underwriting Pitchbook Consolidated Financial Data Income Statement Diagrams PDF
The slide provides the historical last three years and forecasted next five years income statement of the company. Key headings include revenue, gross profit, operating income, operating expenses, net income etc.Deliver and pitch your topic in the best possible manner with this Investment Banking Security Underwriting Pitchbook Consolidated Financial Data Income Statement Diagrams PDF Use them to share invaluable insights on Gross Profit, Operating Expenses, Advertising Expenses and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Redis Cache Data Structure IT Block Unnecessary Traffic To Redis Server Pictures PDF
This slide represents block unnecessary traffic to Redis server by locking all traffic from server and creating loopback request exception. This is a redis cache data structure it block unnecessary traffic to redis server pictures pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like block unnecessary traffic to redis server. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Predictive Analytics In The Age Of Big Data Steps For Predictive Analytics Workflow Application Brochure PDF
This slide represents the steps for predictive analytics workflow application in industries, and it includes accessing and exploring information, pre-processing information, developing predictive models, and integrating analytics with systems. Boost your pitch with our creative Predictive Analytics In The Age Of Big Data Steps For Predictive Analytics Workflow Application Brochure PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Data Processing Services Delivery Areas Where ML Will Deliver Strong Outcomes Background PDF
This template covers the outcomes derived by the machine learning operations for the organization such as Fraud detection and prevention, Security detection and prevention, Optimization research etc. Presenting Data Processing Services Delivery Areas Where ML Will Deliver Strong Outcomes Background PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Cybersecurity, Mobile Security, IoT Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Data Breach Prevention Recognition Problem Faced By The Organization Elements PDF
This slide covers the problem faced by organization caused by employees due to lack of security awareness training programs. This is a data breach prevention recognition problem faced by the organization elements pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity, organization, problem, security awareness, training programs. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Companys Data Safety Recognition Cyber Attacks Experienced By The Company In Previous Financial Year Sample PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. This is a companys data safety recognition cyber attacks experienced by the company in previous financial year sample pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like system misconfiguration, inadvertent disclosure, network intrusion. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Data Science Learning Benefits In Financial Institution Ppt Icon Slide PDF
This slide contains the benefits that a finance company get from using AI, ML and DL to outsmart the competition and achieve desired business growth. It includes investment predictions, process automation, secure transactions, etc. Presenting Data Science Learning Benefits In Financial Institution Ppt Icon Slide PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Investment Predictions, Process Automation, Secure Transactions. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
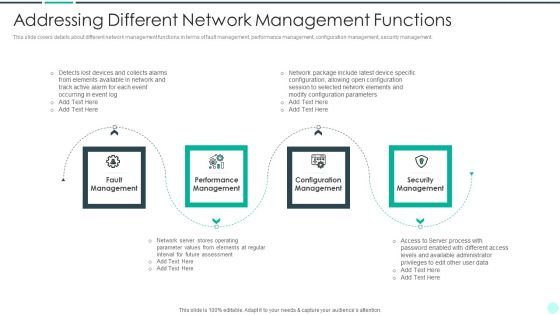
Executing Advance Data Analytics At Workspace Addressing Different Network Rules PDF
This slide covers details about different network management functions in terms of fault management, performance management, configuration management, security management. This is a executing advance data analytics at workspace addressing different network rules pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like management, performance, security, elements. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Executing Advance Data Analytics At Workspace Addressing Service Provider Vendor Formats PDF
This slide covers details about different network management functions in terms of fault management, performance management, configuration management, security management. This is a executing advance data analytics at workspace addressing service provider vendor formats pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like fault management, performance management, configuration management, security management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
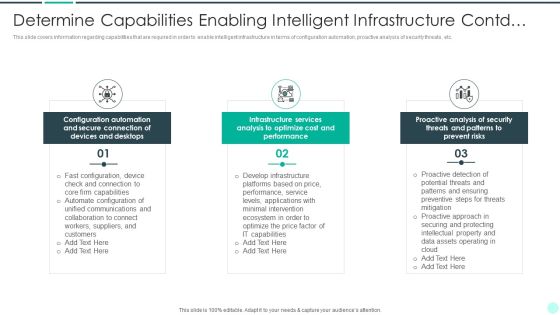
Executing Advance Data Analytics At Workspace Determine Capabilities Enabling Brochure PDF
This slide covers information regarding capabilities that are required in order to enable intelligent infrastructure in terms of configuration automation, proactive analysis of security threats, etc. Presenting executing advance data analytics at workspace determine capabilities enabling brochure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like secure, connection, devices, optimize. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Padlock On Keyboard Data Security PowerPoint Templates Ppt Backgrounds For Slides 0213
We present our Padlock On Keyboard Data Security PowerPoint Templates PPT Backgrounds For Slides 0213.Download and present our Computer PowerPoint Templates because It is Aesthetically crafted by artistic young minds. Our PowerPoint Templates and Slides are designed to display your dexterity. Download our Technology PowerPoint Templates because You aspire to touch the sky with glory. Let our PowerPoint Templates and Slides provide the fuel for your ascent. Present our Communication PowerPoint Templates because Our PowerPoint Templates and Slides will let your team Walk through your plans. See their energy levels rise as you show them the way. Download and present our Security PowerPoint Templates because Our PowerPoint Templates and Slides are the chords of your song. String them along and provide the lilt to your views. Download our Network Diagrams PowerPoint Templates because Our PowerPoint Templates and Slides will Activate the energies of your audience. Get their creative juices flowing with your words.Use these PowerPoint slides for presentations relating to A padlock on keyboard, computer, technology, security, network diagrams, communication. The prominent colors used in the PowerPoint template are Gray, Blue, Yellow.

Certified Data Professional Program Collection Of Information Technology Certifications Mockup PDF
This slide covers the CDP course details such as CDP Benefits, Who should become CDP, salary expectations, International Standards for CDP Program etc. This is a certified data professional program collection of information technology certifications mockup pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security requirements, information system, benefits, strategic, Risk assessment . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Data Services Certification Programs Career With Cisco Certified Network Associate CCNA Brochure PDF
This slide covers details about Cisco Certified Network Associate CCNA certification including career with CCNA, salary expectations, job responsibilities etc. This is a IT Data Services Certification Programs Career With Cisco Certified Network Associate CCNA Brochure PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Network Fundamentals, Automation And Programmability, Security Fundamentals. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Data Processing Services Delivery The Next Generation Operating Model After Implementing Ai Pictures PDF
This slide represents the next generation operating model after implementing AI in the organization and how it would increase the productivity and profit. This is a Data Processing Services Delivery The Next Generation Operating Model After Implementing Ai Pictures PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Organization, Sales Reports, Cyber Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Companys Data Safety Recognition Different Training Formats For Different Organization Levels Structure PDF
This slide covers the training format at different organization levels including strategy improves the actions of the customers and helps create a cybersafe atmosphere. This is a companys data safety recognition different training formats for different organization levels structure pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like interactive protection simulation, automated security awareness platform, cybersecurity. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Companys Data Safety Recognition Problem Faced By The Organization Portrait PDF
This slide covers the problem faced by organization caused by employees due to lack of security awareness training programs. This is a companys data safety recognition problem faced by the organization portrait pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity, financial impact, resource, social engineering, cost. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information And Cyber Data Safety Risk Management Maturity Levels Elements PDF
Mentioned slide showcase maturity stages of information security risk management, which will assist company to develop comprehensive cybersecurity strategy. The maturity stages could be Partial informed repetitive and adaptive. Presenting information and cyber data safety risk management maturity levels elements pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including partial, informed, repetitive, adaptive. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cybersecurity Online Risk Assessment Process To Enhance Data Protection Introduction PDF
The purpose of this slide is to represent a process for cybersecurity digital risk assessment to analyze business threats. It includes various stages such as classifying information assets, evaluating risks, examining risk, observing and reviewing effectiveness and implementing security controls. Presenting Cybersecurity Online Risk Assessment Process To Enhance Data Protection Introduction PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Classify Information Assets, Evaluate Risk, Examine Risk. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Data Wiper Spyware Attack Weaknesses Of Russian Cyber Cell Microsoft PDF
This slide represents the weaknesses of Russian cyber cells, which are expected as in other countries, such as lack of skilled professionals and corrupted officials.Presenting data wiper spyware attack weaknesses of russian cyber cell microsoft pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like lack of skilled professionals, corruption, security agencies In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Data Safety Initiatives Categorization Worksheet For Assets Owned By Organization Themes PDF
This slide illustrates asset categorization worksheet covering information about security system such as system name, its version, system location and other general information. This is a data safety initiatives categorization worksheet for assets owned by organization themes pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like asset tag, individual system, system accessibility, accessible to external entities. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
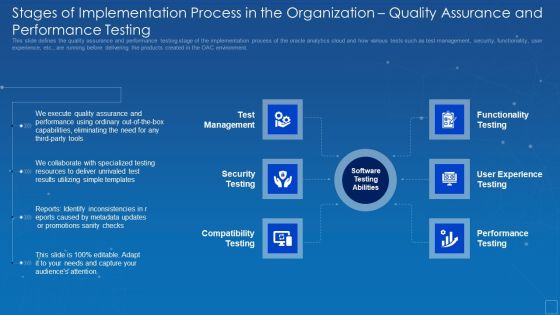
Oracle Cloud Data Analytics Administration IT Stages Implementation Organization Sample PDF
This slide defines the quality assurance and performance testing stage of the implementation process of the oracle analytics cloud and how various tests such as test management, security, functionality, user experience, etc., are running before delivering the products created in the OAC environment. This is a oracle cloud data analytics administration it stages implementation organization sample pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like eliminating, quality, assurance, performance, capabilities. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Data Wiper Spyware Attack Hacking Groups Launching Cyber Proxy War Against Russia Portrait PDF
This slide depicts the hacking groups such as the Anonymous hacker group, Conti ransomware gang, threat actors in Belarus launching cyber proxy war over Ukraine attacks by Russia.This is a data wiper spyware attack hacking groups launching cyber proxy war against russia portrait pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like infrastructure security, superpowers fought, conflicts through proxy You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
IT Data Services Certification Programs Cisco Certified Network Professional CCNP Training Courses Icons PDF
This slide covers Cisco Certified Network Professional CCNP training courses such CCNA, specialist, CNP and CCIE. This is a IT Data Services Certification Programs Cisco Certified Network Professional CCNP Training Courses Icons PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Enterprise Infrastructure, Service Provider, Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
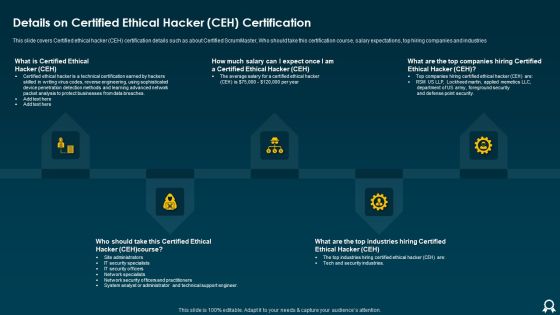
IT Data Services Certification Programs Details On Certified Ethical Hacker CEH Certification Brochure PDF
This slide covers Certified ethical hacker CEH certification details such as about Certified ScrumMaster, Who should take this certification course, salary expectations, top hiring companies and industries. This is a IT Data Services Certification Programs Details On Certified Ethical Hacker CEH Certification Brochure PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Average Salary, Point Security, Methods. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Professional Data Certification Program Comptia A Certification Examination Details Ideas PDF
This slide covers CompTIA A Certification Examination Details such as training and examination cost skills required to identify, topics and concepts etc. This is a IT Professional Data Certification Program Comptia A Certification Examination Details Ideas PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Networking Components, Security Components, Cost. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Professional Data Certification Program Cisco Certified Internetwork Expert CCIE Examination Details Infographics PDF
This slide covers CCIE examination details including certification, exam number, exam name duration and fees per attempt along with specialist courses. Presenting IT Professional Data Certification Program Cisco Certified Internetwork Expert CCIE Examination Details Infographics PDF to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like Network Security Engineer, Information Technology, Network Engineer. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Executing Advance Data Analytics At Workspace Determine Capabilities Enabling Sample PDF
This slide covers information regarding capabilities that are required in order to enable intelligent infrastructure in terms of configuration automation, proactive analysis of security threats, etc. Presenting executing advance data analytics at workspace determine capabilities enabling sample pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like capabilities, connection, communications, collaboration. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Executing Advance Data Analytics At Workspace How Firm Handle Variou Elements PDF
This slide provides information regarding how firm will handle insider threats through employee training, IT security and HR coordination, etc. Presenting executing advance data analytics at workspace how firm handle variou elements pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like employee training, coordination, implement, behavioral. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Executing Advance Data Analytics At Workspace Facilities Offered By Implementation Sample PDF
This slide portrays information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. Presenting executing advance data analytics at workspace facilities offered by implementation sample pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like investigation, prevention, organization, intelligence, collaborate . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Data Wiper Spyware Attack Cyber Officials Urge Agencies To Armor Download PDF
This slide represents that officials from the Department of Homeland Security have urged agencies to prepare for possible Russian cyberattacks, and CISA has amended its shields up guidelines.Presenting data wiper spyware attack cyber officials urge agencies to armor download pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like warning government, corporations to be cautious, russian cyberattacks In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Data Wiper Spyware Attack Should We Be Concerned About Russian Cyberattacks Professional PDF
This slide shows that US citizens should not be concerned about Russian cyberattacks as nothing has happened so far. However, the US Department of Homeland Security issued a warning to organizations to look for Russian cyberattacks.Presenting data wiper spyware attack should we be concerned about russian cyberattacks professional pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like already been targeted, methods america, russians could impose In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Professional Data Certification Program Details On Certified Ethical Hacker CEH Certification Portrait PDF
This slide covers Certified ethical hacker CEH certification details such as about Certified ScrumMaster, Who should take this certification course, salary expectations, top hiring companies and industries. Presenting IT Professional Data Certification Program Details On Certified Ethical Hacker CEH Certification Portrait PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Security Specialists, Network Specialists, Detection Methods. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Data Safety Initiatives Scorecard To Check Cybersecurity And Digital Risk Preparedness Rules PDF
Following slide illustrates a scorecard that company will use to check its preparedness against various cyber security and digital risk events. Sections covered here are fraud prevention considerations, score and notes. Deliver an awe inspiring pitch with this creative data safety initiatives scorecard to check cybersecurity and digital risk preparedness rules pdf bundle. Topics like risk prevention considerations, score, standard rating, top management displays can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

 Home
Home