Data Breach

Security Management Plan Steps In Detail Training And Building Role Competencies Portrait PDF
This slide provides information about the seventh step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Training and Building Role Competencies. This is a security management plan steps in detail training and building role competencies portrait pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like management system, information security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Management Plan Steps In Detail System Maintenance And Monitoring Portrait PDF
This slide provides information about the ninth and the last step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. System Maintenance and Monitoring. This is a security management plan steps in detail system maintenance and monitoring portrait pdf template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security management plan steps in detail system maintenance and monitoring. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

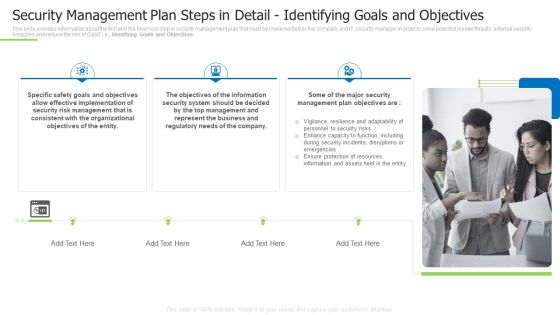
Security Management Plan Steps In Detail Identifying Goals And Objectives Graphics PDF
This slide provides information about the first and the foremost step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Identifying Goals and Objectives. This is a security management plan steps in detail identifying goals and objectives graphics pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security management plan steps in detail identifying goals and objectives. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Techniques And Strategies To Reduce Security Management Risks Security Detail System Maintenance And Monitoring Mockup PDF
This slide provides information about the ninth and the last step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., System Maintenance and Monitoring. This is a techniques and strategies to reduce security management risks security detail system maintenance and monitoring mockup pdf template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like perfective maintenance, corrective maintenance, perfective maintenance You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Techniques And Strategies To Reduce Security Management Risks Security Management Plan Steps Portrait PDF
This slide provides information about the fifth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Adopting Access Controls. This is a techniques and strategies to reduce security management risks security management plan steps portrait pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like suggested coverage, security risk management, estimated security management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Techniques And Strategies To Reduce Security Management Risks Security Management Plan Steps In Detail Inspiration PDF
This slide provides information about the first and the foremost step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Identifying Goals and Objectives. This is a techniques and strategies to reduce security management risks security management plan steps in detail inspiration pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like effective implementation, consistent with the organizational, represent the business You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
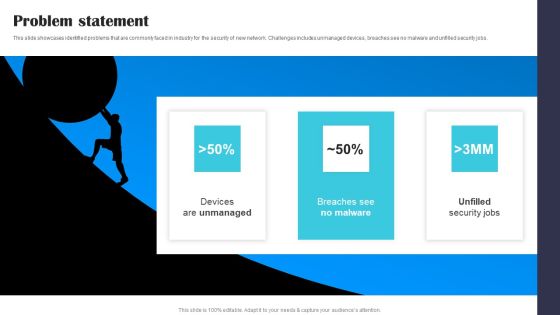
Security Software Company Investor Funding Pitch Deck Problem Statement Themes PDF
This slide showcases identified problems that are commonly faced in industry for the security of new network. Challenges includes unmanaged devices, breaches see no malware and unfilled security jobs. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Security Software Company Investor Funding Pitch Deck Problem Statement Themes PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Security Management Plan Steps In Detail System Maintenance And Monitoring Summary PDF
This slide provides information about the ninth and the last step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., System Maintenance and Monitoring. Presenting security management plan steps in detail system maintenance and monitoring summary pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like types of system maintenance, installation costs, types of system monitoring. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Management Plan Steps In Detail Training And Building Role Competencies Topics PDF
This slide provides information about the seventh step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Training and Building Role Competencies. Presenting security management plan steps in detail training and building role competencies topics pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like security management roles, training required, role description. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Management Plan Steps In Detail Training And Building Role Competencies Clipart PDF
This slide provides information about the seventh step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Training and Building Role Competencies. Presenting security management plan steps in detail training and building role competencies clipart pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like security management roles, training required, competencies required. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Management Plan Steps In Detail Training And Building Role Competencies Slides PDF
This slide provides information about the seventh step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Training and Building Role Competencies. Presenting security management plan steps in detail training and building role competencies slides pdf to provide visual cues and insights. Share and navigate important information on five tages that need your due attention. This template can be used to pitch topics like security management roles, training required, role description In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Department Cases Action Plan Response Report Ppt PowerPoint Presentation File Layout PDF
This slide highlights tracking sheet of security incidents occurred in several departments in an organization. The purpose of this template is to provide information to the management about security breaches in the company. It includes elements such as number of incidents, cost per incident, team responsiveness rates, status of action taken, etc. Pitch your topic with ease and precision using this Cyber Security Department Cases Action Plan Response Report Ppt PowerPoint Presentation File Layout PDF. This layout presents information on Key Components, Cost Per Incident, Team Responsiveness. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Cloud Security Checklist Logging And Monitoring Download PDF
This slide defines the importance of logging and monitoring activities on data in a network and how it could be beneficial in future analysis. This is a Cloud Security Checklist Logging And Monitoring Download PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Potential, Observe Systems, Security Breaches. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Assessment Cloud Security Checklist Logging And Monitoring Information PDF
This slide defines the importance of logging and monitoring activities on data in a network and how it could be beneficial in future analysis.Presenting Cloud Security Assessment Cloud Security Checklist Logging And Monitoring Information PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Security Breaches, Access Sensitive, System Activities In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Application Of Cloud Service Xaas In Disaster Recovery Demonstration PDF
Following slide presents a strategic application of everything as a service XaaS in disaster recovery of enterprise data warehouses. Major elements covered are on-premise infrastructure, cloud failure, benefits, etc. Showcasing this set of slides titled Application Of Cloud Service Xaas In Disaster Recovery Demonstration PDF. The topics addressed in these templates are Benefits, Reduced Security Breaches, Quick Recovery IT Disasters . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Business Operations Strategic Tactical Planning Cyber Threat Intelligence Summary PDF
This slide exhibits strategic tactical and operational levels of cyber threat intelligence to ensure data and software protection from threats. It includes identify reason, assist extent of breach, alert and identify prevention system and ensure safety in advance. Persuade your audience using this Business Operations Strategic Tactical Planning Cyber Threat Intelligence Summary PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Strategic Cyber Threat Intelligence, Tactical Cyber Threat Intelligence, Operational Cyber Threat Intelligence. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Overview Of New IT Policy Framework Ppt Summary Format Ideas PDF
This slide demonstrate the new information technology policy framework of the company focusing on security and data usage policies. Presenting overview of new it policy framework ppt summary format ideas pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like management policy, security breach, information, resource. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Computing Project Administration Challenges And Solutions Ppt Visual Aids Slides PDF
Following slide outlines various types of cloud project management challenges such as data vulnerability, inefficient employees working in cloud computing, and using multi-cloud server. It also covers detail information about the solutions that can be used by managers to overcome cloud based problems and ensuring successful completion of project. Persuade your audience using this Cloud Computing Project Administration Challenges And Solutions Ppt Visual Aids Slides PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Solutions, Challenges, Security Breaches. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Global Statistics Highlighting Vendor Management Scenario Download PDF
The following slide showcases global scenario of vendor management. It provides information about security breaches,Presenting Global Statistics Highlighting Vendor Management Scenario Download PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Risk Management, Security Breaches, Vendor Invoice. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Project Risk And Procurement Management System Rules PDF
This slide covers project risk and procurement management system. It involves risks such as security breach, damaged goods, supplier unwillingness and confidentiality breach. Showcasing this set of slides titled Project Risk And Procurement Management System Rules PDF. The topics addressed in these templates are Responsible Person, Risk Category. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

SLA KPL Dashboard Indicating Top Week Performers Ppt Infographics Examples PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Showcasing this set of slides titled SLA KPL Dashboard Indicating Top Week Performers Ppt Infographics Examples PDF. The topics addressed in these templates are Active Slas Risk, Active Slas Breached, Active Slas. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Statistics Indicating Changing Landscape Of Business Threats Ppt Model Design Templates PDF
This slide showcases statistics indicating changing landscape of business risk which can be referred by executives and managers to make decisions regarding their upcoming strategies and opportunities for risks. It includes information about cybersecurity breaches, business interruption, new technologies, climatic change, Persuade your audience using this Statistics Indicating Changing Landscape Of Business Threats Ppt Model Design Templates PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Security Breaches, Business Interruption, New Technologies. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Vendor Management To Handle Purchase Global Statistics Highlighting Vendor Management Scenario Elements PDF
The following slide showcases global scenario of vendor management. It provides information about security breaches, vendor risk management, invoice issues, vendor access, poor quality, supplier identification, etc.Presenting Vendor Management To Handle Purchase Global Statistics Highlighting Vendor Management Scenario Elements PDF to provide visual cues and insights. Share and navigate important information on five stage that need your due attention. This template can be used to pitch topics like Management Initiatives, Vendor Invoice, Security Breaches. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
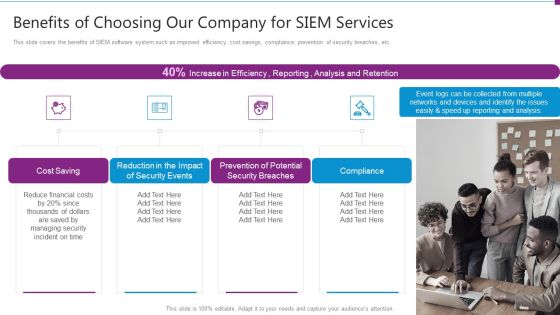
Security Information And Event Management Strategies For Financial Audit And Compliance Benefits Of Choosing Our Company Topics PDF
This slide covers the benefits of SIEM software system such as improved efficiency, cost savings, compliance, prevention of security breaches, etc. This is a security information and event management strategies for financial audit and compliance benefits of choosing our company topics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cost saving, security events, security breaches, compliance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Financial Services Enterprise Transformation Problems Cultural Shift Towards Technology Guidelines PDF
This slide shows the problems related to the cultural shifts in the technological trends in the banking companies which includes high expectation of the customers, security breaches, customer retention, etc.This is a Financial Services Enterprise Transformation Problems Cultural Shift Towards Technology Guidelines PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Breaches, Customer Retention, Cultural Shift You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Digital Transformation Of Consumer Problems Cultural Shift Towards Technology In Banking Company Template PDF
This slide shows the problems related to the cultural shifts in the technological trends in the banking companies which includes high expectation of the customers, security breaches, customer retention, etc. This is a Digital Transformation Of Consumer Problems Cultural Shift Towards Technology In Banking Company Template PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Cultural Shift, High Expectations, Security Breaches. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
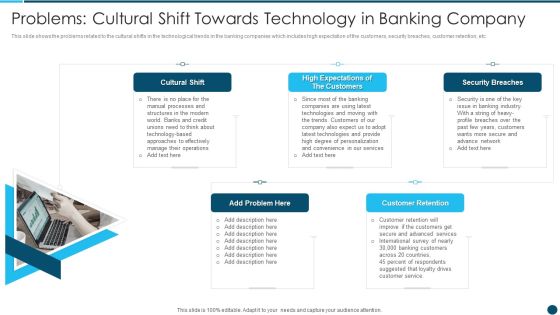
Digital Technology Adoption In Banking Industry Problems Cultural Shift Towards Technology Designs PDF
This slide shows the problems related to the cultural shifts in the technological trends in the banking companies which includes high expectation of the customers, security breaches, customer retention, etc.Presenting Digital Technology Adoption In Banking Industry Problems Cultural Shift Towards Technology Designs PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like High Expectations Of The Customers, Security Breaches, Customer Retention In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Exploitation IT Purpose Of Hackers Infographics PDF
This slide describes the common types of cybercrime such as identity theft, computer fraud, privacy breach, electronic money laundering, electronic funds transfer, and so on. This is a cyber exploitation it purpose of hackers infographics pdf template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like computer fraud, privacy breach, electronic money laundering, electronic funds transfer, denial of service attacks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
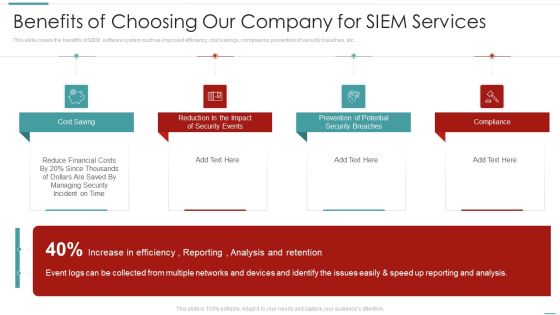
Risk Recognition Automation Benefits Of Choosing Our Company For Siem Services Ppt Gallery Design Inspiration PDF
This slide covers the benefits of SIEM software system such as improved efficiency, cost savings, compliance, prevention of security breaches, etc. This is a risk recognition automation benefits of choosing our company for siem services ppt gallery design inspiration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cost saving, prevention of potential security breaches, compliance, reduction in the impact of security events. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Hacker Purpose Of Hackers Mockup PDF
This slide describes the common types of cybercrime such as identity theft, computer fraud, privacy breach, electronic money laundering, electronic funds transfer, and so on. This is a IT Security Hacker Purpose Of Hackers Mockup PDF template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Identity Theft, Computer Fraud, Privacy Breach. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Enhancing Cyber Safety With Vulnerability Administration Benefits Of Choosing Our Company Inspiration PDF
This slide covers the benefits of SIEM software system such as improved efficiency, cost savings, compliance, prevention of security breaches, etc. Presenting enhancing cyber safety with vulnerability administration benefits of choosing our company inspiration pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like cost saving, reduction in the impact of security events, prevention of potential security breaches, compliance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
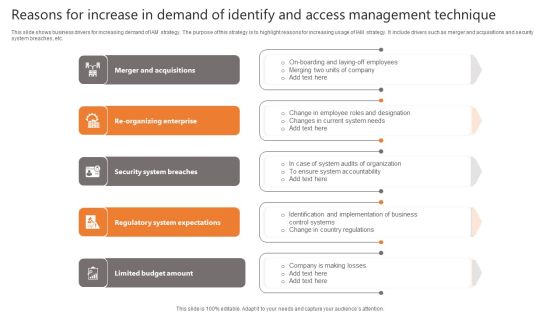
Reasons For Increase In Demand Of Identify And Access Management Technique Sample PDF
This slide shows business drivers for increasing demand of IAM strategy. The purpose of this strategy is to highlight reasons for increasing usage of IAM strategy. It include drivers such as merger and acquisitions and security system breaches, etc. Presenting Reasons For Increase In Demand Of Identify And Access Management Technique Sample PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Security System Breaches, Regulatory System Expectations, Limited Budget Amount. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Effects Of Inadequate Report For Quality Management System Clipart PDF
This slide showcases the adverse effects of poor document control on the organizations quality management system. The purpose is to take action on time. It includes fines, efficiency, storage space, security breaches, and violation of regulations. Persuade your audience using this Effects Of Inadequate Report For Quality Management System Clipart PDF. This PPT design covers Five stages, thus making it a great tool to use. It also caters to a variety of topics including Storage Space, Security Breaches, Violation Of Regulations. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

SIEM Benefits Of Choosing Our Company For SIEM Services Ppt File Outfit PDF
This slide covers the benefits of SIEM software system such as improved efficiency, cost savings, compliance, prevention of security breaches, etc. Presenting siem benefits of choosing our company for siem services ppt file outfit pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like cost saving, reduction in the impact of security events, prevention of potential security breaches, compliance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Major Risks Involved In Business Process Outsourcing Service Industry Designs PDF
This slide highlights some of the major risks faced by businesses that are engaged in outsourcing the activities to a foreign company. The key risks are security breaches, cost of service, communication issues and overdependence on service providers. Presenting Major Risks Involved In Business Process Outsourcing Service Industry Designs PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Security Breaches, Cost Services, Communicationi Ssues. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

IT Protection Cyber Security Cyber Threat Ppt PowerPoint Presentation Complete Deck
Presenting this set of slides with name it protection cyber security cyber threat ppt powerpoint presentation complete deck. The topics discussed in these slides are network protection, cyber security, cyber threat, laptop protected, security breach. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Apache Hadoop Software Deployment Disadvantages Of Hadoop Structure PDF
This slide represents the disadvantages of Hadoop on the basis of security, vulnerability by design, not suitable for small data, and potential stability concerns.This is a Apache Hadoop Software Deployment Disadvantages Of Hadoop Structure PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Managing Complicated, Security Breaches, Potential Stability. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
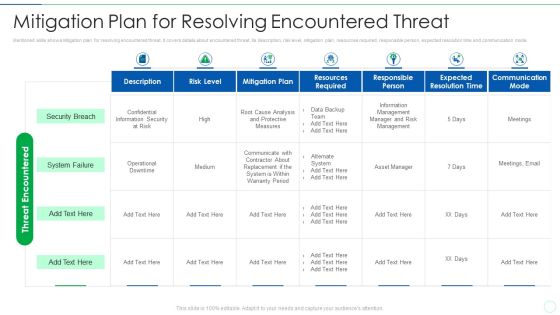
Effective IT Risk Management Process Mitigation Plan For Resolving Infographics PDF
Mentioned slide shows mitigation plan for resolving encountered threat. It covers details about encountered threat, its description, risk level, mitigation plan, resources required, responsible person, expected resolution time and communication mode. Deliver an awe inspiring pitch with this creative effective it risk management process mitigation plan for resolving infographics pdf bundle. Topics like security breach, system failure, communicate, analysis can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
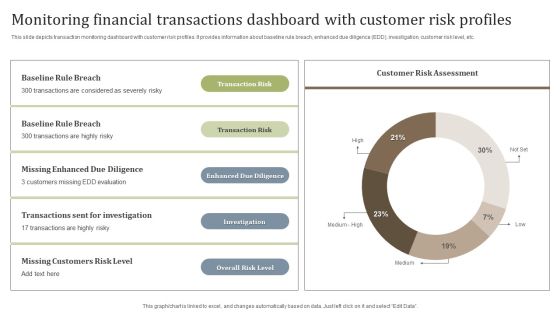
Monitoring Financial Transactions Dashboard With Customer Risk Profiles Diagrams PDF
This slide depicts transaction monitoring dashboard with customer risk profiles. It provides information about baseline rule breach, enhanced due diligence EDD, investigation, customer risk level, etc. Showcasing this set of slides titled Monitoring Financial Transactions Dashboard With Customer Risk Profiles Diagrams PDF. The topics addressed in these templates are Overall Risk Level, Investigation, Enhanced Due Diligence. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Vendor Risk Management And Audit Checklist Vendor Management Strategies Topics PDF
The following slide showcases vendor risk management and audit checklist. It provides information about contract breach, lawsuits, termination, vendor relation, intellectual property, criminal check, background check, etc. Deliver an awe inspiring pitch with this creative Vendor Risk Management And Audit Checklist Vendor Management Strategies Topics PDF bundle. Topics like Company Provided, Information Compromise, Architecture Expertise can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Customer Service Enterprise Workforce Dashboard Designs PDF
This slide ILLUSTRATES consumer support extended team dashboard. It provides information about average resolution time, cases transferred open cases, service level agreements SLAs, etc. Pitch your topic with ease and precision using this Customer Service Enterprise Workforce Dashboard Designs PDF. This layout presents information on Average Resolution Time, Active SLAs Breached, Average Customer. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
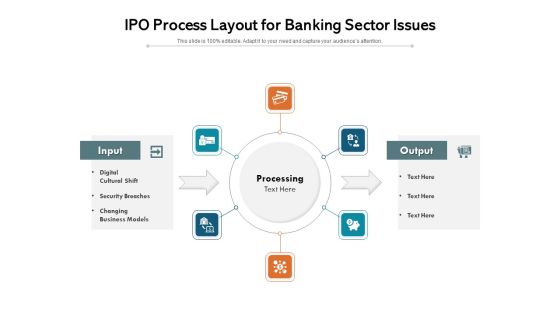
IPO Process Layout For Banking Sector Issues Ppt PowerPoint Presentation Show Design Templates PDF
Presenting ipo process layout for banking sector issues ppt powerpoint presentation show design templates pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including processing, output, input, digital cultural shift, security breaches, changing business models. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Current Security Management Challenges The Company Is Facing Download PDF
Presenting current security management challenges the company is facing download pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like potential insider threats, external security breaches, rise of caas. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Measures And Ways To Mitigate Security Management Challenges Background PDF
This slide provides information about the ways and measures through which the company and IT security managers can overcome the problems and issues related to Security Management. Deliver an awe inspiring pitch with this creative measures and ways to mitigate security management challenges background pdf bundle. Topics like potential insider threats, external security breaches, weak links in the supply chain can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Anti Scam Playbook Addressing The Compliance Risks And Their Impact On Business Structure PDF
The goal of this slide is to provide information about compliance risks as well as the consequences of a breach. Sections covered here are impact scale, legal, financial, operational and reputation. Deliver an awe inspiring pitch with this creative Anti Scam Playbook Addressing The Compliance Risks And Their Impact On Business Structure PDF bundle. Topics like Financial, Operational, Reputation, Potential can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Various Strategies To Prevent Business Addressing The Compliance Risks And Their Impact Introduction PDF
The goal of this slide is to provide information about compliance risks as well as the consequences of a breach. Sections covered here are impact scale, legal, financial, operational and reputation. Deliver an awe inspiring pitch with this creative Various Strategies To Prevent Business Addressing The Compliance Risks And Their Impact Introduction PDF bundle. Topics like Impact Scale, Financial, Operational can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Global Statistics Highlighting Vendor Management Scenario Vendor Management Strategies Slides PDF
The following slide showcases global scenario of vendor management. It provides information about security breaches, vendor risk management, invoice issues, vendor access, poor quality, supplier identification, etc.Presenting Global Statistics Highlighting Vendor Management Scenario Vendor Management Strategies Slides PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Vendor Management, Vendor Invoice, Initiated Supplier. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
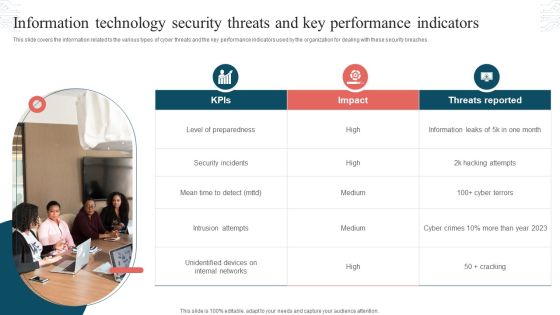
Information Technology Security Threats And Key Performance Indicators Formats PDF
This slide covers the information related to the various types of cyber threats and the key performance indicators used by the organization for dealing with these security breaches. Presenting Information Technology Security Threats And Key Performance Indicators Formats PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Threats Reported, Security Incidents, Intrusion Attempts. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Biochip Technology Disadvantages Of Biochip Ppt PowerPoint Presentation File Inspiration PDF
This slide showcases the disadvantages of biochips, such as it is very expensive the privacy of an individual is breached, and many such limitations. Want to ace your presentation in front of a live audience Our Biochip Technology Disadvantages Of Biochip Ppt PowerPoint Presentation File Inspiration PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.
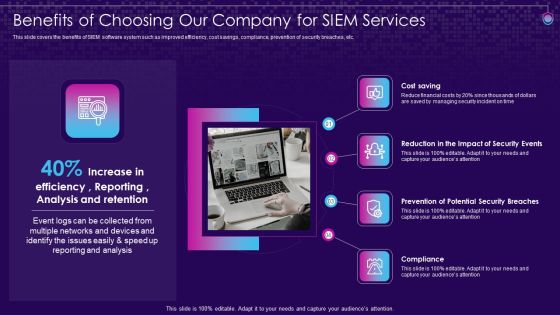
SIEM Services Benefits Of Choosing Our Company For SIEM Services Ppt Layouts Slide Download PDF
This slide covers the benefits of SIEM software system such as improved efficiency, cost savings, compliance, prevention of security breaches, etc. This is a siem services benefits of choosing our company for siem services ppt layouts slide download pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cost saving, reduction, prevention of potential security, compliance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Automation Tools Integration Right Time To Add Automation In Security Summary PDF
This slide depicts that what is the right time to invest in security automation it showcases failed human insights high time for resolution, high security breaches, no additional budget to hire security team. This is a IT Security Automation Tools Integration Right Time To Add Automation In Security Summary PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Failed Human Insights, Right Time Automation, High Time. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Effective Communication Plan To Address Fraud Event Appropriately Fraud Threat Administration Guide Template PDF
Following slide portrays communication plan that company is using for effectively managing cyber breaches. Sections covered here are type of fraud, description, delivery method, frequency and responsible.This is a Effective Communication Plan To Address Fraud Event Appropriately Fraud Threat Administration Guide Template PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Phishing Technique, Obtain Passwords, Communicate Through. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Terms And Conditions For Home Financing Business Proposal Ppt Layouts Aids PDF
This slide represents terms and conditions for private money lending proposal including collateral, default, severability, exclusive jurisdiction for suit in case of breach, borrower, lender, principal loan amount, etc. Unleash your creativity with our Terms And Conditions For Home Financing Business Proposal Ppt Layouts Aids PDF single-slide PPT template. Whether you are a seasoned presenter or a newbie, our editable and visually-stunning template will make your presentations shine. This template is versatile and easy to use. Make your presentations unforgettable with our premium template and leave a lasting impression on your audience.

Comparative Analysis Of Virtual Monitoring And Management Software Pictures PDF
This slide outlines comparative assessment of various remote monitoring and management software to assist organizations in accessing cybersecurity technical controls for any potential breaches. This slide focuses on components such as software, reviews, features, price and target audience. Showcasing this set of slides titled Comparative Analysis Of Virtual Monitoring And Management Software Pictures PDF. The topics addressed in these templates are Software, Reviews, Features, Price, Target Audience. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Addressing The Compliance Risks And Their Impact On Business Themes PDF
The goal of this slide is to provide information about compliance risks as well as the consequences of a breach. Sections covered here are impact scale, legal, financial, operational and reputation. Boost your pitch with our creative Addressing The Compliance Risks And Their Impact On Business Themes PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Integrating AML And Transaction Why Is Transaction Monitoring Essential Elements PDF
This slide showcases reasons why transaction monitoring is essential. It provides information about maintaining compliance, regulatory breaches, spotting financial crimes, risk based approach, better customer understanding, behavioral analytics, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Integrating AML And Transaction Why Is Transaction Monitoring Essential Elements PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Measures And Ways To Mitigate Security Management Challenges Structure PDF
This slide provides information about the ways and measures through which the company and IT security managers can overcome the problems and issues related to Security Management.This is a Measures and ways to mitigate security management challenges structure pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like potential insider threats, external security breaches, weak links in the supply chain. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Anti Scam Playbook Effective Communication Plan To Address Fraud Event Appropriately Sample PDF
Following slide portrays communication plan that company is using for effectively managing cyber breaches. Sections covered here are type of fraud, description, delivery method, frequency and responsible. This is a Anti Scam Playbook Effective Communication Plan To Address Fraud Event Appropriately Sample PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Management, Information, System, Risk. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Current Security Management Challenges The Company Is Facing Elements PDF
This slide shows some of the current Security Management challenges and issues that are faced by the company and IT security managers.This is a Current security management challenges the company is facing elements pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like potential insider threats, external security breaches, employee management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Real Time Assessment Of Security Threats Benefits Of Choosing Our Company For SIEM Services Introduction PDF
This slide covers the benefits of SIEM software system such as improved efficiency, cost savings, compliance, prevention of security breaches, etc. This is a real time assessment of security threats benefits of choosing our company for siem services introduction pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cost saving, security events, compliance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security Automation Framework Right Time To Add Automation In Security Microsoft PDF
This slide depicts that what is the right time to invest in security automation it showcases failed human insights high time for resolution, high security breaches, no additional budget to hire security team. Want to ace your presentation in front of a live audience Our Cyber Security Automation Framework Right Time To Add Automation In Security Microsoft PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Terms And Conditions For Customized Lending Business Proposal Formats PDF
This slide represents terms and conditions for private money lending proposal including collateral, default, severability, exclusive jurisdiction for suit in case of breach, borrower, lender, principal loan amount, etc. Unleash your creativity with our Terms And Conditions For Customized Lending Business Proposal Formats PDF single-slide PPT template. Whether you are a seasoned presenter or a newbie, our editable and visually-stunning template will make your presentations shine. This template is versatile and easy to use. Make your presentations unforgettable with our premium template and leave a lasting impression on your audience.

Solutions To Overcome Various Personal Banking Relationship Challenges Structure PDF
This slide signifies the solutions to overcome various banking relationship challenges. It covers information about challenges like security breach, regulatory compliance and changing business model with implemented strategies to overcome.Presenting Solutions To Overcome Various Personal Banking Relationship Challenges Structure PDF to dispense important information. This template comprises one stage. It also presents valuable insights into the topics including Regulatory Compliance, Changing Business, Authentication System. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Four Strategies For Tech Ethical Investing Icons PDF
This slide shows the strategies to make ethical investments in tech companies. It includes four strategies for ethical tech investments such as monitor funds, stay updated on ethical breaches, consider employee ratings and assess environmental, social and corporate governance score. Presenting Four Strategies For Tech Ethical Investing Icons PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Monitor Funds, Consider Employees Ratings, Assess Environmental. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Terms And Conditions For Commercial Loan Financing Proposal Infographics PDF
This slide represents terms and conditions for private money lending proposal including collateral, default, severability, exclusive jurisdiction for suit in case of breach, borrower, lender, principal loan amount, etc. Unleash your creativity with our Terms And Conditions For Commercial Loan Financing Proposal Infographics PDF single-slide PPT template. Whether you are a seasoned presenter or a newbie, our editable and visually stunning template will make your presentations shine. This template is versatile and easy to use. Make your presentations unforgettable with our premium template and leave a lasting impression on your audience.

Common Types Of Cyber Crime Ppt Model Background Image PDF
This slide describes the common types of cybercrime such as identity theft, computer fraud, privacy breach, electronic money laundering, electronic funds transfer, and so on. Presenting common types of cyber crime ppt model background image pdf to provide visual cues and insights. Share and navigate important information on ten stages that need your due attention. This template can be used to pitch topics like information, networks, social media, technology. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Terms And Conditions For Private Mortgage Broker For Property Purchase Proposal Ideas PDF
This slide represents terms and conditions for private money lending proposal including collateral, default, severability, exclusive jurisdiction for suit in case of breach, borrower, lender, principal loan amount, etc. Take your presentations to the next level with our Terms And Conditions For Private Mortgage Broker For Property Purchase Proposal Ideas PDF template. With its sleek design and seamless editing features, this single-slide PPT template is a game-changer for professionals who want to make an impact. Impress your audience with stunning visuals and engaging content that will capture their attention from start to finish. Get your hands on our template and elevate your presentations to new heights.

New Era In Identity Verification And Fraud Formats PDF
This slide showcases multiple factors creating new identity proofing requirements needed to successfully capture revenue and reduce friction. It covers aspects such as massive breaches, collaborative fraud networks, real-time changes, etc. Showcasing this set of slides titled New Era In Identity Verification And Fraud Formats PDF. The topics addressed in these templates are Collaborative Fraud Network, Identity Features, Location Characteristics. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Benefits Of ISO 27001 Certification Summary PDF
This slide displays various organizational benefits after getting ISO 27001 certification. Benefits included are information confidentiality, low operational cost, increase in the trust of valuable partners and customers and competitive advantage.Presenting Benefits Of ISO 27001 Certification Summary PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Security Breaches, Competitive Advantage, Recognized Standard. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Fraud Avoidance Playbook Effective Communication Plan To Address Fraud Event Appropriately Clipart PDF
Following slide portrays communication plan that company is using for effectively managing cyber breaches. Sections covered here are type of fraud, description, delivery method, frequency and responsible. Presenting Fraud Avoidance Playbook Effective Communication Plan To Address Fraud Event Appropriately Clipart PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Delivery Method, Finance Department, Management Information. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Ways To Accomplish ISO 27001 Accreditation Mitigation Plan To Resolve Encountered Icons PDF
Mentioned slide portrays mitigation plan to resolve the encountered risk events. It includes information of risk encountered, its description, threat level, mitigation plan, resources required, responsibility, resolution time and communication channel. Deliver and pitch your topic in the best possible manner with this Ways To Accomplish ISO 27001 Accreditation Mitigation Plan To Resolve Encountered Icons PDF. Use them to share invaluable insights on Security Breach, System Failure, Mitigation Plan and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
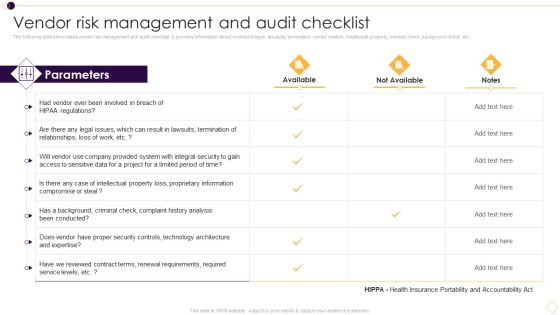
Supplier Management For Enhanced SCM And Procurement Vendor Risk Management And Audit Checklist Structure PDF
The following slide showcases vendor risk management and audit checklist. It provides information about contract breach, lawsuits, termination, vendor relation, intellectual property, criminal check, background check, etc. Deliver and pitch your topic in the best possible manner with this Supplier Management For Enhanced SCM And Procurement Vendor Risk Management And Audit Checklist Structure PDF. Use them to share invaluable insights on Intellectual Property, Does Vendor, Reviewed Contract and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Micro Chip Disadvantages Of Biochip Ppt PowerPoint Presentation File Example Introduction PDF
This slide showcases the disadvantages of biochips, such as it is very expensive, the privacy of an individual is breached, and many such limitations. Presenting Micro Chip Disadvantages Of Biochip Ppt PowerPoint Presentation File Example Introduction PDF to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like Biochips Costly, Individual Privacy, Human Liberty. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Addressing The Compliance Risks And Their Impact On Business Fraud Threat Administration Guide Topics PDF
The goal of this slide is to provide information about compliance risks as well as the consequences of a breach. Sections covered here are impact scale, legal, financial, operational and reputation.Deliver an awe inspiring pitch with this creative Addressing The Compliance Risks And Their Impact On Business Fraud Threat Administration Guide Topics PDF bundle. Topics like Potential Disruption, Criminal Prosecution, Press Exposure can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Fraud Avoidance Playbook Addressing The Compliance Risks And Their Impact On Business Clipart PDF
The goal of this slide is to provide information about compliance risks as well as the consequences of a breach. Sections covered here are impact scale, legal, financial, operational and reputation. Deliver an awe inspiring pitch with this creative Fraud Avoidance Playbook Addressing The Compliance Risks And Their Impact On Business Clipart PDF bundle. Topics like Financial Fraud, Potential Disruption, Business can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Vendor Risk Management And Audit Checklist Vendor Management System Deployment Graphics PDF
The following slide showcases vendor risk management and audit checklist. It provides information about contract breach, lawsuits, termination, vendor relation, intellectual property, criminal check, background check, etc. Get a simple yet stunning designed Vendor Risk Management And Audit Checklist Vendor Management System Deployment Graphics PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit ZZZZZZZZZZZZZZZ can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Creating Transaction Monitoring Why Is Transaction Monitoring Essential Infographics PDF
This slide showcases reasons why transaction monitoring is essential. It provides information about maintaining compliance, regulatory breaches, spotting financial crimes, risk based approach, better customer understanding, behavioral analytics, etc. Get a simple yet stunning designed Creating Transaction Monitoring Why Is Transaction Monitoring Essential Infographics PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Creating Transaction Monitoring Why Is Transaction Monitoring Essential Infographics PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Anti Fraud Guide Addressing The Compliance Risks One Pager Sample Example Document
The goal of this slide is to provide information about compliance risks as well as the consequences of a breach. Sections covered here are impact scale, legal, financial, operational and reputation. Presenting you an exemplary Anti Fraud Guide Addressing The Compliance Risks One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Anti Fraud Guide Addressing The Compliance Risks One Pager Sample Example Document brilliant piece now.

Quarterly Key Account Action Strategy Download PDF
The following slide showcases strategic account action plan on quarter basis for breaking annual planning in small parts and achieve goals effectively. It involves account objectives and strategies to review the outcomes of last quarter and improve it. Presenting Quarterly Key Account Action Strategy Download PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Senior Level Management, Assess Service, Security Breaches. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
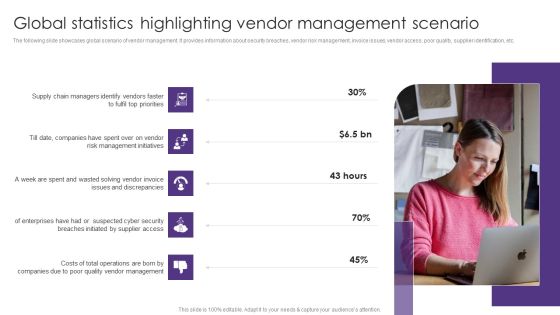
Global Statistics Highlighting Vendor Management Scenario Vendor Management System Deployment Background PDF
The following slide showcases global scenario of vendor management. It provides information about security breaches, vendor risk management, invoice issues, vendor access, poor quality, supplier identification, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Global Statistics Highlighting Vendor Management Scenario Vendor Management System Deployment Background PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Global Statistics Highlighting Vendor Management Scenario Vendor Management System Deployment Background PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today

Deploying Banking Transaction Why Is Transaction Monitoring Essential Information PDF
This slide showcases reasons why transaction monitoring is essential. It provides information about maintaining compliance, regulatory breaches, spotting financial crimes, risk based approach, better customer understanding, behavioral analytics, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Deploying Banking Transaction Why Is Transaction Monitoring Essential Information PDF can be your best option for delivering a presentation. Represent everything in detail using Deploying Banking Transaction Why Is Transaction Monitoring Essential Information PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
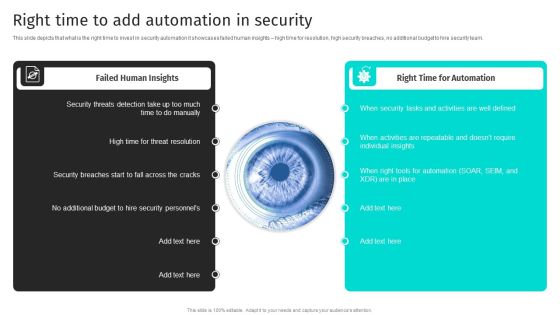
Security Automation To Analyze And Mitigate Cyberthreats Right Time To Add Automation In Security Inspiration PDF
This slide depicts that what is the right time to invest in security automation it showcases failed human insights high time for resolution, high security breaches, no additional budget to hire security team.Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Security Automation To Analyze And Mitigate Cyberthreats Right Time To Add Automation In Security Inspiration PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Actual Time Transaction Monitoring Software And Strategies Why Is Transaction Monitoring Essential Portrait PDF
This slide showcases reasons why transaction monitoring is essential. It provides information about maintaining compliance, regulatory breaches, spotting financial crimes, risk based approach, better customer understanding, behavioral analytics, etc. Slidegeeks is here to make your presentations a breeze with Actual Time Transaction Monitoring Software And Strategies Why Is Transaction Monitoring Essential Portrait PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
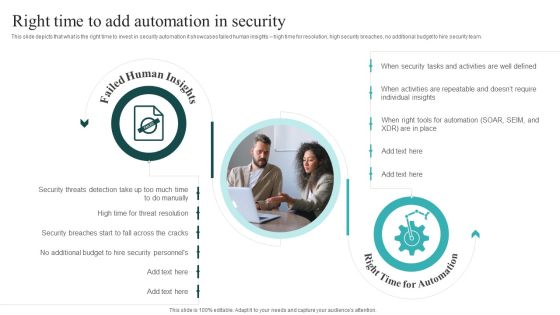
IT Security Automation Systems Guide Right Time To Add Automation In Security Professional PDF
This slide depicts that what is the right time to invest in security automation it showcases failed human insights high time for resolution, high security breaches, no additional budget to hire security team. Present like a pro with IT Security Automation Systems Guide Right Time To Add Automation In Security Professional PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

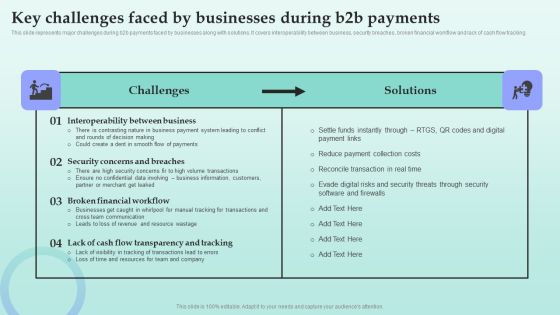
Key Challenges Faced By Businesses During B2b Payments Comprehensive Guide For Developing Rules PDF
This slide represents major challenges during b2b payments faced by businesses along with solutions. It covers interoperability between business, security breaches, broken financial workflow and lack of cash flow tracking.This Key Challenges Faced By Businesses During B2b Payments Comprehensive Guide For Developing Rules PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Key Challenges Faced By Businesses During B2b Payments Comprehensive Guide For Developing Rules PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
Strategies For Successful Customer Base Development In B2b M Commerce Key Challenges Faced By Businesses During B2b Background PDF
This slide represents major challenges during b2b payments faced by businesses along with solutions. It covers interoperability between business, security breaches, broken financial workflow and lack of cash flow tracking. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Strategies For Successful Customer Base Development In B2b M Commerce Key Challenges Faced By Businesses During B2b Background PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Strategies For Successful Customer Base Development In B2b M Commerce Key Challenges Faced By Businesses During B2b Background PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.

Key Challenges Faced By Businesses During B2B Payments Structure PDF
This slide represents major challenges during b2b payments faced by businesses along with solutions. It covers interoperability between business, security breaches, broken financial workflow and lack of cash flow tracking. Slidegeeks is here to make your presentations a breeze with Key Challenges Faced By Businesses During B2B Payments Structure PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

KYC Transaction Monitoring System Business Security Why Is Transaction Monitoring Essential Designs PDF
This slide showcases reasons why transaction monitoring is essential. It provides information about maintaining compliance, regulatory breaches, spotting financial crimes, risk based approach, better customer understanding, behavioral analytics, etc. Present like a pro with KYC Transaction Monitoring System Business Security Why Is Transaction Monitoring Essential Designs PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Introduction To B2B Online Shopping Payment Options Key Challenges Faced By Businesses Formats PDF
This slide represents major challenges during b2b payments faced by businesses along with solutions. It covers interoperability between business, security breaches, broken financial workflow and lack of cash flow tracking. This modern and well arranged Introduction To B2B Online Shopping Payment Options Key Challenges Faced By Businesses Formats PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Vendor Risk Management And Audit Checklist Effective Vendor Management For Enhancing Rules PDF
The following slide showcases vendor risk management and audit checklist. It provides information about contract breach, lawsuits, termination, vendor relation, intellectual property, criminal check, background check, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Vendor Risk Management And Audit Checklist Effective Vendor Management For Enhancing Rules PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Deploying AML Transaction Monitoring Why Is Transaction Monitoring Essential Structure PDF
This slide showcases reasons why transaction monitoring is essential. It provides information about maintaining compliance, regulatory breaches, spotting financial crimes, risk based approach, better customer understanding, behavioral analytics, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Deploying AML Transaction Monitoring Why Is Transaction Monitoring Essential Structure PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Deploying AML Transaction Monitoring Why Is Transaction Monitoring Essential Structure PDF.

Effective Communication Plan To Address Fraud Event Appropriately Slides PDF
Following slide portrays communication plan that company is using for effectively managing cyber breaches. Sections covered here are type of fraud, description, delivery method, frequency and responsible. If you are looking for a format to display your unique thoughts, then the professionally designed Effective Communication Plan To Address Fraud Event Appropriately Slides PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Effective Communication Plan To Address Fraud Event Appropriately Slides PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Aftereffects Of IT Security Threats On Business And Customers Ppt PowerPoint Presentation Layouts Background PDF
Persuade your audience using this aftereffects of it security threats on business and customers ppt powerpoint presentation layouts background pdf. This PPT design covers two stages, thus making it a great tool to use. It also caters to a variety of topics including violation of law, crucial information loss, loss of productivity, cyber espionage, risk of losing work in future, contract breach, trust among business people, ransom ware, online banking transactions are compromised, identity theft, credit card detail theft, spam mails or other attacks violates the law, fraud to customers by scare ware or other fraud tools. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Techniques To Monitor Transactions Why Is Transaction Monitoring Essential Infographics PDF
This slide showcases reasons why transaction monitoring is essential. It provides information about maintaining compliance, regulatory breaches, spotting financial crimes, risk based approach, better customer understanding, behavioral analytics, etc. Slidegeeks is here to make your presentations a breeze with Techniques To Monitor Transactions Why Is Transaction Monitoring Essential Infographics PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, youre sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether youre giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Formulating Money Laundering Why Is Transaction Monitoring Essential Pictures PDF
This slide showcases reasons why transaction monitoring is essential. It provides information about maintaining compliance, regulatory breaches, spotting financial crimes, risk based approach, better customer understanding, behavioral analytics, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Deploying Banking Transaction Using Behavioral Analytics For Multiple Transactions Structure PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Deploying Banking Transaction Using Behavioral Analytics For Multiple Transactions Structure PDF today and make your presentation stand out from the rest.

 Home
Home