Data Breach

Solutions To Overcome Various It Protection Challenges Summary PDF
This slide shows solutions to various challenges faced by organizations to provide information technology protection. These challenges are data breaches, lack of expertise, insider threats and unsecured APIs. Persuade your audience using this Solutions To Overcome Various It Protection Challenges Summary PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Data Breaches, Cloud Security, Information. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Percent Of Risk Events Occurred Over Last Two Years Inspiration PDF
This slide portrays informational stats about risk events encountered by the firm over last two years. Risk events included in the slide are data breaching, cyber attacks, phishing emails, technical failures and human errors.Deliver and pitch your topic in the best possible manner with this Percent Of Risk Events Occurred Over Last Two Years Inspiration PDF. Use them to share invaluable insights on Data Breaching, Key Takeaways, Faced An Increase and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Legal And Law Assistance LLP Business Law Firm Corporate Case Study Slides PDF
This slide highlights the case study of law firm company which showcases challenge XYZ group files case for data breach, solution formed committee and proper investigation with IT experts. This is a Legal And Law Assistance LLP Business Law Firm Corporate Case Study Slides PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Challenge, Solution, Data Breach. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Online Security Threat And Risk Assessment Matrix Formats PDF
This slide showcases digital safety risk assessment matrix which helps analyze impact of threat on business processes. It provides information regarding hacking, data breaches, information misuse, malicious attacks and system failure. Showcasing this set of slides titled Online Security Threat And Risk Assessment Matrix Formats PDF. The topics addressed in these templates are Information Misuse, Data Breaches, Malicious Attacks. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Risk Assessment Tool For Corporate Resilience Mockup PDF
This slide highlights risk assessment tool for business resilience which covers multiple types of risk such as data breach, loss of building, loss of key rerecords, natural calamity and loss of general insurance claim. Showcasing this set of slides titled Risk Assessment Tool For Corporate Resilience Mockup PDF. The topics addressed in these templates are Data Breach, Loss Of Building, Natural Calamity. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting

Key Challenges To Medical Industry Cybersecurity Performance Background Pdf
This slide presents key challenges faced by cybersecurity in healthcare helpful for organizations to gain knowledge on main obstacles and solve them on priority basis. It includes data breaches, malware and ransomware, insider threats, distributed denial of service, cloud threats and lack of cyber awareness Showcasing this set of slides titled Key Challenges To Medical Industry Cybersecurity Performance Background Pdf. The topics addressed in these templates are Data Breaches, Service, Cloud Threats. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Four Key Security Threats Of Cloud Technology Ppt PowerPoint Presentation Gallery Introduction PDF
Presenting four key security threats of cloud technology ppt powerpoint presentation gallery introduction pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including data breaches by unethical hackers, permanent data freeze in trash box, possibility of regulatory noncompliance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

IT Security Elements Of Information Technology Security Cloud Security Ppt Outline Background Images PDF
This slide defines the cloud security element of cyber security and various threats that can breach cloud security, such as malware injection, malicious insiders, insecure APIs, etc. This is a it security elements of information technology security cloud security ppt outline background images pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like data breaches, malware injections, malicious insiders, account hijacking, distributed denial of service. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Information Security Cloud Security Checklist Access Control Ppt Inspiration Professional PDF
This slide depicts the access control under the cloud security checklist and how it affects the organizations when data breaches happen due to poor access control management. This is a Cloud Information Security Cloud Security Checklist Access Control Ppt Inspiration Professional PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Control Identity, Security Breaches, Data Servers. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Business Risk Mitigation System With Activity Planning Ppt PowerPoint Presentation File Outfit PDF
Pitch your topic with ease and precision using this business risk mitigation system with activity planning ppt powerpoint presentation file outfit pdf. This layout presents information on risks category, data breach, business strategy risks. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
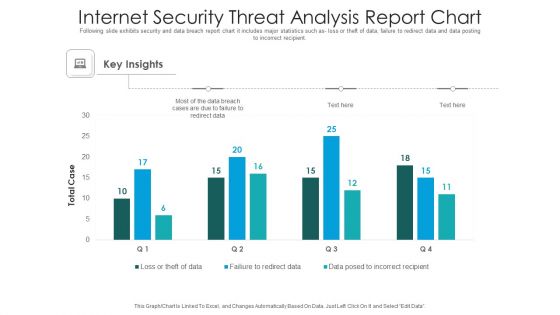
Internet Security Threat Analysis Report Chart Introduction PDF
Following slide exhibits security and data breach report chart it includes major statistics such as- loss or theft of data, failure to redirect data and data posting to incorrect recipient. Pitch your topic with ease and precision using this internet security threat analysis report chart introduction pdf. This layout presents information on internet security threat analysis report chart. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Current Market Trends Sample PDF
This slide provides information about the current market trends that are increasing the importance of security monitoring and motivating the company to implement a security monitoring plan in the company and follow monitoring strategies. Presenting continuous development evaluation plan eliminate cyber attacks current market trends sample pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like increasing digitization of sensitive data, general data protection laws, data breach notification laws. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Checklist Access Control Cloud Computing Security IT Ppt Show PDF
This slide depicts the access control under the cloud security checklist and how it affects the organizations when data breaches happen due to poor access control management. Deliver and pitch your topic in the best possible manner with this cloud security checklist access control cloud computing security it ppt show pdf. Use them to share invaluable insights on cloud services, security, privileged credentials, administrative and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Developing Firm Security Strategy Plan Current Potential Challenges Faced By Firm Designs PDF
This slide provides information about the various potential challenges faced by firm in terms of reported financial losses due to increase in security threats and increase in data breaches and record exposed. Deliver an awe inspiring pitch with this creative developing firm security strategy plan current potential challenges faced by firm designs pdf bundle. Topics like security, financial can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
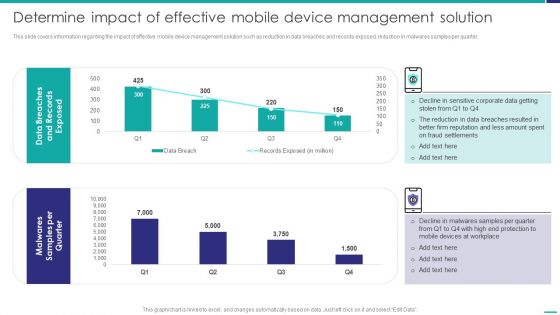
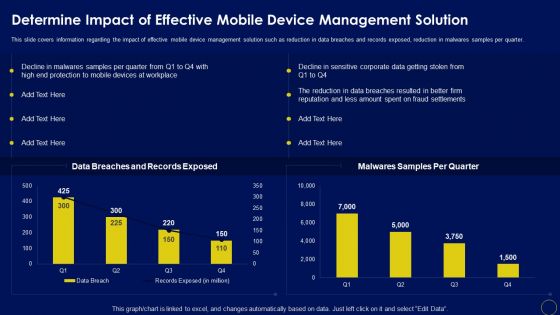
Determine Impact Of Effective Mobile Device Management Solution Mobile Device Security Management Graphics PDF
This slide covers information regarding the impact of effective mobile device management solution such as reduction in data breaches and records exposed, reduction in malwares samples per quarter. Deliver an awe inspiring pitch with this creative Determine Impact Of Effective Mobile Device Management Solution Mobile Device Security Management Graphics PDF bundle. Topics like Fraud Settlements, Devices Workplace, Malwares Samples can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
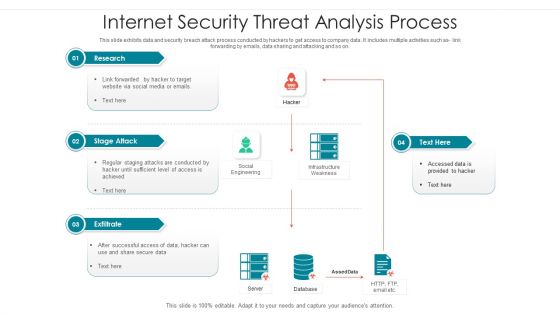
Internet Security Threat Analysis Process Brochure PDF
Following slide showcase how a data breach process is performed by hacker to collect and utilize company data. It includes following activities such as code integration with company software, so on. Showcasing this set of slides titled internet security threat analysis process brochure pdf. The topics addressed in these templates are supply chain attack, execution persistence, defense evasion, exfiltration, keyboard attack. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Asset Identification For Information Security Risk Management Topics PDF
This slide showcases identification of asset which can help organization to formulate risk monitoring plan. It can help to monitor the asset in real time for any data breach or cyber attack This is a Asset Identification For Information Security Risk Management Topics PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Customers Database, Products Database, Sales Database. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
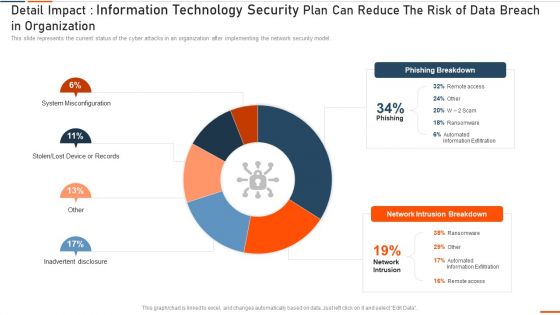
Detail Impact Information Technology Security Plan Can Reduce Ppt Show Slide Download PDF
This slide represents the current status of the cyber attacks in an organization after implementing the network security model. Deliver an awe inspiring pitch with this creative it security detail impact detail impact information technology security plan can reduce ppt show slide download pdf bundle. Topics like detail impact information technology security plan can reduce the risk of data breach in organization can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Key Benefits Of Cyber Security Awareness Training Background PDF
The purpose of this slide is to delineate several advantages of security awareness training. Driving awareness, reducing data breach threat, prevention of downtime and improving the customer confidence are some of the key benefits which are highlighted in the slide.This is a Key Benefits Of Cyber Security Awareness Training Background PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Drive Awareness, Reduce Threat, Amongst Employees. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Internet Security Threat Incident Analysis Mockup PDF
This slide exhibits security and data breach incidence assessment model. It includes multiple sections such as- rules and regulations sharing with third parties, communication with incidence response team and so on. Presenting internet security threat incident analysis mockup pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including proactive and reactive, communicate, audit and improve. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Asset Identification For Information Security Risk Management Cybersecurity Risk Assessment Inspiration PDF
This slide showcases identification of asset which can help organization to formulate risk monitoring plan. It can help form to monitor the asset in real time for any data breach or cyber attack. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 parcent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Asset Identification For Information Security Risk Management Cybersecurity Risk Assessment Inspiration PDF from Slidegeeks and deliver a wonderful presentation.
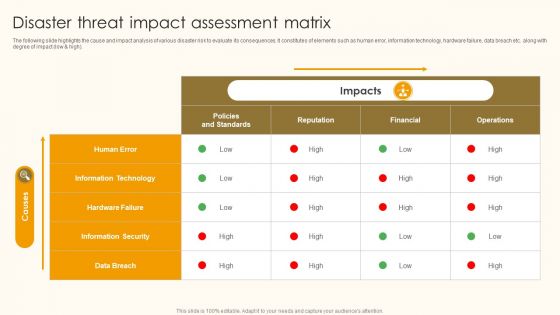
Disaster Threat Impact Assessment Matrix Ppt Ideas Design Templates PDF
The following slide highlights the cause and impact analysis of various disaster risk to evaluate its consequences. It constitutes of elements such as human error, information technology, hardware failure, data breach etc. along with degree of impact low and high. Showcasing this set of slides titled Disaster Threat Impact Assessment Matrix Ppt Ideas Design Templates PDF. The topics addressed in these templates are Human Error, Information Technology, Hardware Failure. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Contingency Plans To Minimize The Impact Of Risks Penetrating Markets With Financial Strategy SS V
This slide showcases Contingency plans to minimize the impact of risks. It includes plans such as data breach contingency plan, market downturn contingency plan and operational disruption contingency plan. Want to ace your presentation in front of a live audience Our Contingency Plans To Minimize The Impact Of Risks Penetrating Markets With Financial Strategy SS V can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.
Internet Security Threats Management Framework Icons PDF
This slide exhibits data breach risk management model. It includes major evaluation criteria such as- does the management has two unique credentials to perform administer activities, does the multifactor authentication is enabled for administrative access etc. Showcasing this set of slides titled internet security threats management framework icons pdf. The topics addressed in these templates are asset, control topic, evaluation questions, response, threat. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Security Cases Action Severity Level For Plan Ppt PowerPoint Presentation File Model PDF
This slide covers classification of cyber security events of financial organizations. The purpose of this classification is to identify events which needs immediate response. It includes elements such as severity level, cyber incidents, occurrence pattern, performance impact, data breach and financial costs Pitch your topic with ease and precision using this Cyber Security Cases Action Severity Level For Plan Ppt PowerPoint Presentation File Model PDF. This layout presents information on Severity Level, Cyber Incidents, Occurrence Pattern, Performance Impact. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
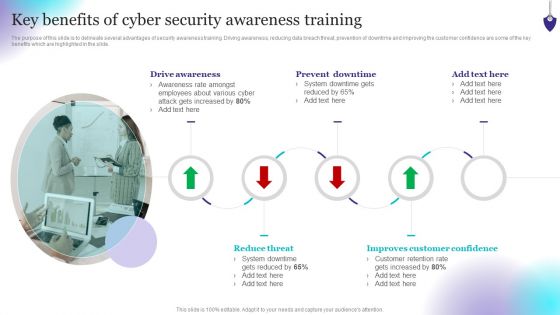
Organizing Security Awareness Key Benefits Of Cyber Security Awareness Training Rules PDF
The purpose of this slide is to delineate several advantages of security awareness training. Driving awareness, reducing data breach threat, prevention of downtime and improving the customer confidence are some of the key benefits which are highlighted in the slide. Make sure to capture your audiences attention in your business displays with our gratis customizable Organizing Security Awareness Key Benefits Of Cyber Security Awareness Training Rules PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
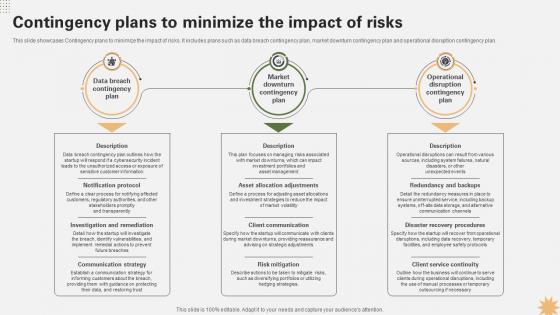
Contingency Plans To Minimize The Impact Strategy For Launching A Financial Strategy SS V
This slide showcases Contingency plans to minimize the impact of risks. It includes plans such as data breach contingency plan, market downturn contingency plan and operational disruption contingency plan. Want to ace your presentation in front of a live audience Our Contingency Plans To Minimize The Impact Strategy For Launching A Financial Strategy SS V can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.
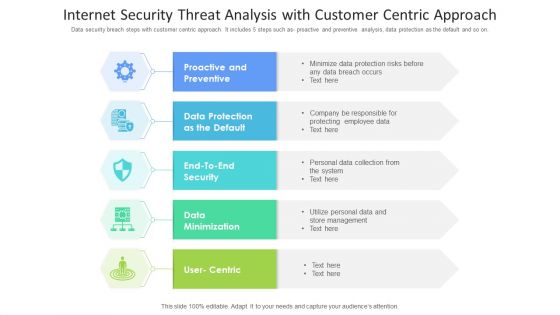
Internet Security Threat Analysis With Customer Centric Approach Mockup PDF
Data security breach steps with customer centric approach. It includes 5 steps such as- proactive and preventive analysis, data protection as the default and so on. Showcasing this set of slides titled internet security threat analysis with customer centric approach mockup pdf. The topics addressed in these templates are data minimization, data protection, proactive and preventive. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Developing Response Plan Managing Risks And Establishing Trust Through Efficient Infographics Pdf
This slide presents data breach response plan that sets out procedures and clear lines of authority. It includes steps such as identify the breach, contain the breach, assess risk and scope , notify management and stakeholders, notify affected individuals and determine affected individuals, notify law enforcement. Take your projects to the next level with our ultimate collection of Developing Response Plan Managing Risks And Establishing Trust Through Efficient Infographics Pdf. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest
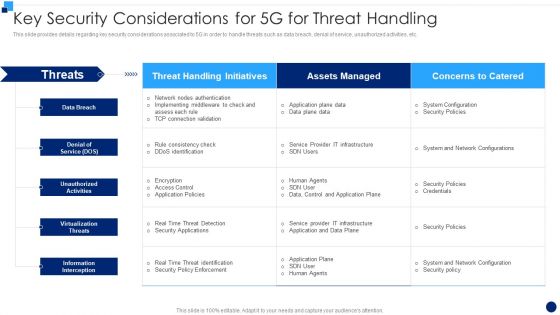
Key Security Considerations For 5G For Threat Handling Icons PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver and pitch your topic in the best possible manner with this Key Security Considerations For 5G For Threat Handling Icons PDF. Use them to share invaluable insights on Denial Of Service, Information Interception, Application Plane Data and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
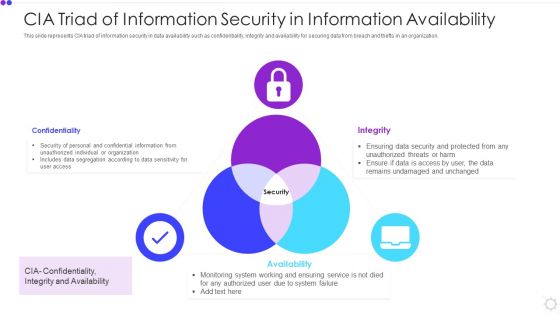
Cia Triad Of Information Security In Information Availability Microsoft PDF
This slide represents CIA triad of information security in data availability such as confidentiality, integrity and availability for securing data from breach and thefts in an organization. Presenting cia triad of information security in information availability microsoft pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including confidentiality, integrity, availability. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Health Analysis Dashboard For Multiple Risks Elements PDF
This slide shows data related to breach of health care analytics in different ways for misuse. It include three main sources of data breach-online leakage, internal staff, other reasons etc. Showcasing this set of slides titled Health Analysis Dashboard For Multiple Risks Elements PDF. The topics addressed in these templates are Health Analysis Dashboard, Multiple Risks. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Risk Evaluation Of Information Technology Systems Damage Control Assessment From IT Risk Management Download PDF
This slide highlights the damage control form information technology risk management strategies which includes data breach, cyber threats, social engineering attacks, domain based threats and increase in business opportunities. There are so many reasons you need a Risk Evaluation Of Information Technology Systems Damage Control Assessment From IT Risk Management Download PDF. The first reason is you cant spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
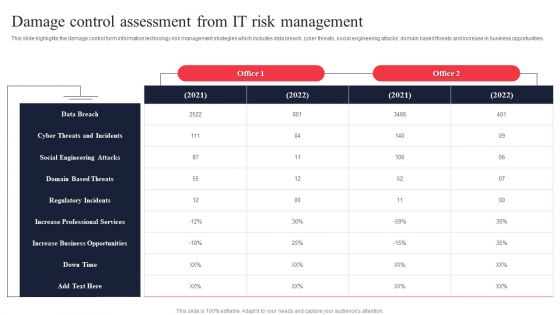
IT System Risk Management Guide Damage Control Assessment From IT Risk Management Information PDF
This slide highlights the damage control form information technology risk management strategies which includes data breach, cyber threats, social engineering attacks, domain based threats and increase in business opportunities. There are so many reasons you need a IT System Risk Management Guide Damage Control Assessment From IT Risk Management Information PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
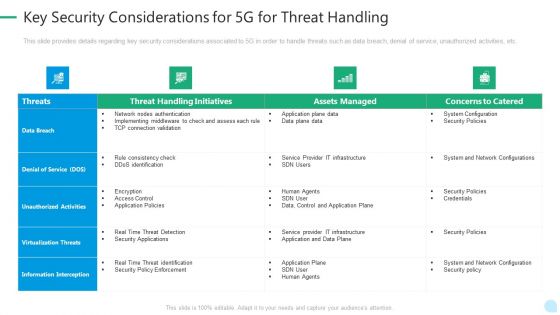
5G Network Technology Key Security Considerations For 5G For Threat Handling Ppt Gallery Gridlines PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver an awe inspiring pitch with this creative 5g network technology key security considerations for 5g for threat handling ppt gallery gridlines pdf bundle. Topics like virtualization threats, information interception, security policies, infrastructure can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
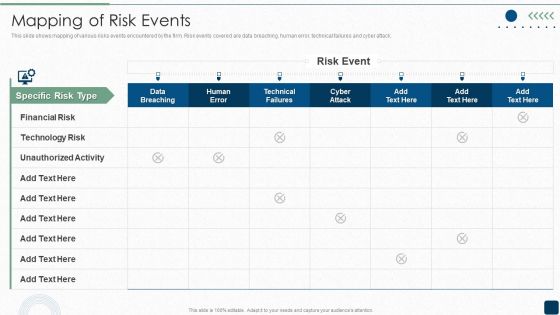
Mapping Of Risk Events Infographics PDF
This slide shows mapping of various risks events encountered by the firm. Risk events covered are data breaching, human error, technical failures and cyber attack.Deliver an awe inspiring pitch with this creative Mapping Of Risk Events Infographics PDF bundle. Topics like Financial Risk, Unauthorized Activity, Technology Risk can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Legal Advisory Company Description Law Firm Corporate Case Study Designs PDF
This slide highlights the case study of law firm company which showcases challenge XYZ group files case for data breach, solution formed committee and proper investigation with IT experts.Deliver an awe inspiring pitch with this creative Legal Advisory Company Description Law Firm Corporate Case Study Designs PDF bundle. Topics like Personal Information, Issues Investigation, Careful Examination can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
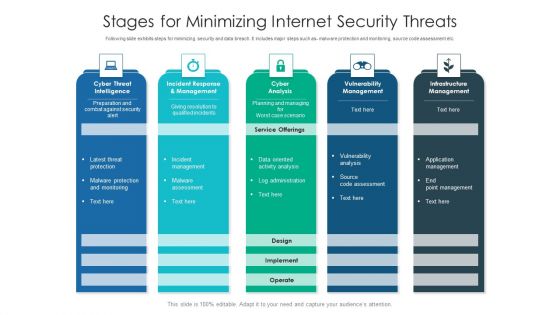
Stages For Minimizing Internet Security Threats Ideas PDF
Following slide exhibits steps for minimizing security and data breach. It includes major steps such as- malware protection and monitoring, source code assessment etc. Pitch your topic with ease and precision using this stages for minimizing internet security threats ideas pdf. This layout presents information on infrastructure management, cyber analysis, vulnerability management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
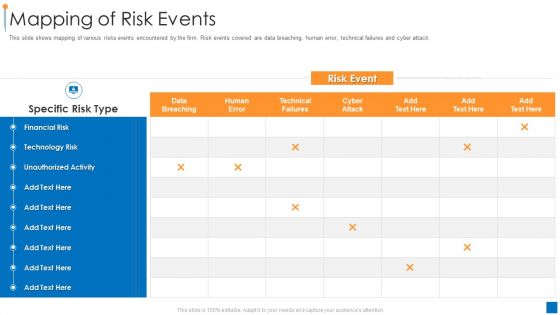
International Organization Standardization 270001 Mapping Of Risk Events Slides PDF
This slide shows mapping of various risks events encountered by the firm. Risk events covered are data breaching, human error, technical failures and cyber attack. Deliver an awe inspiring pitch with this creative international organization standardization 270001 mapping of risk events slides pdf bundle. Topics like financial risk, technology risk, unauthorized activity can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
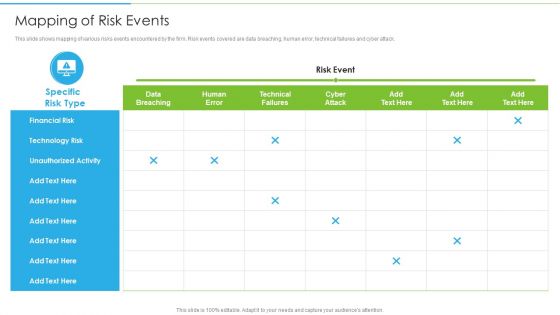
Ways To Accomplish ISO 27001 Accreditation Mapping Of Risk Events Summary PDF
This slide shows mapping of various risks events encountered by the firm. Risk events covered are data breaching, human error, technical failures and cyber attack. Deliver an awe inspiring pitch with this creative Ways To Accomplish ISO 27001 Accreditation Mapping Of Risk Events Summary PDF bundle. Topics like Financial Risk, Technology Risk, Unauthorized Activity can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

ISO 27001 Organizational Qualifying Procedure Mapping Of Risk Events Brochure PDF
This slide shows mapping of various risks events encountered by the firm. Risk events covered are data breaching, human error, technical failures and cyber attack.Deliver an awe inspiring pitch with this creative ISO 27001 Organizational Qualifying Procedure Mapping Of Risk Events Brochure PDF bundle. Topics like Unauthorized Activity, Technology Risk, Financial Risk can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
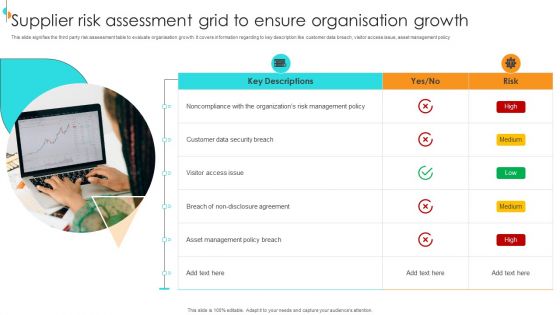
Supplier Risk Assessment Grid To Ensure Organisation Growth Summary PDF

Cyber Protection Improvement Plan Impact On Business Designs PDF
This slide shows difference between before and after implementing cyber protection improvement plan in business. It includes types phishing attacks, malware attacks, data breaches, etc. Showcasing this set of slides titled Cyber Protection Improvement Plan Impact On Business Designs PDF. The topics addressed in these templates are Cyber Protection Improvement, Plan Impact On Business. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Key Security Considerations For 5G For Threat Handling Elements PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver an awe inspiring pitch with this creative Key Security Considerations For 5G For Threat Handling Elements PDF bundle. Topics like System Configuration, Security Policies, Information Interception can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Developing 5G Wireless Cellular Network Key Security Considerations For 5G For Threat Handling Demonstration PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver an awe inspiring pitch with this creative Developing 5G Wireless Cellular Network Key Security Considerations For 5G For Threat Handling Demonstration PDF bundle. Topics like Information Interception, Virtualization Threats, Denial Of Service can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Pre And Post Process Results Of Cyber Security Process Changes Sample PDF
This slide shows reduction in threats percentage after adopting cyber security. It includes computer virus, data breach, DOS and phishing. Pitch your topic with ease and precision using this Pre And Post Process Results Of Cyber Security Process Changes Sample PDF. This layout presents information on Process Results, Process Changes, Key Insights. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Addressing Current Challenges In Managing Mobile Devices At Workplace Summary PDF
This slide covers information regarding the current challenges faced by firm in management of mobile devices at workplace with various risks associated to mobile devices such as corporate data protection, data breaches and records exposed, etc. Deliver an awe inspiring pitch with this creative Addressing Current Challenges In Managing Mobile Devices At Workplace Summary PDF bundle. Topics like Sensitive Corporate, Data Protection, Risks Associated can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
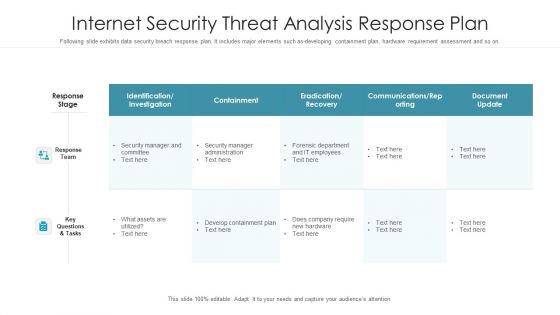
Internet Security Threat Analysis Response Plan Graphics PDF
Following slide exhibits data security breach response plan. It includes major elements such as-developing containment plan, hardware requirement assessment and so on. Pitch your topic with ease and precision using this internet security threat analysis response plan graphics pdf. This layout presents information on response team, response stage, key questions and tasks. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Determine Impact Of Effective Mobile Device Management Solution Business Mobile Device Security Guidelines PDF
This slide covers information regarding the impact of effective mobile device management solution such as reduction in data breaches and records exposed, reduction in malwares samples per quarter. The Determine Impact Of Effective Mobile Device Management Solution Business Mobile Device Security Guidelines PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
MDM Strategies At Office Addressing Current Challenges In Managing Mobile Devices At Workplace Icons PDF
This slide covers information regarding the current challenges faced by firm in management of mobile devices at workplace with various risks associated to mobile devices such as corporate data protection, data breaches and records exposed, etc. Deliver an awe inspiring pitch with this creative MDM Strategies At Office Addressing Current Challenges In Managing Mobile Devices At Workplace Icons PDF bundle. Topics like Risks Associated, Technical Support, Records Exposed can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Tips For Protecting Employee Electronic Footprint Clipart PDF
This slide lists down tips for protecting digital footprints for company employees to avoid data breach. It includes limiting data sharing, avoiding unsafe websites, not logging in with facebook and acting faster after a breach. Persuade your audience using this Tips For Protecting Employee Electronic Footprint Clipart PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Organizations, Confidential Information, Limit Data Sharing. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
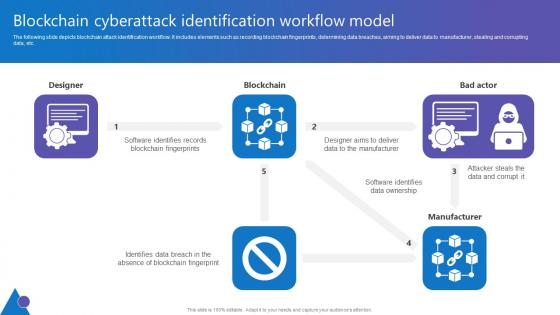
Blockchain Cyberattack Identification Comprehensive Guide To Blockchain Digital Security Microsoft Pdf
The following slide depicts blockchain attack identification workflow. It includes elements such as recording blockchain fingerprints, determining data breaches, aiming to deliver data to manufacturer, stealing and corrupting data, etc. Take your projects to the next level with our ultimate collection of Blockchain Cyberattack Identification Comprehensive Guide To Blockchain Digital Security Microsoft Pdf. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest
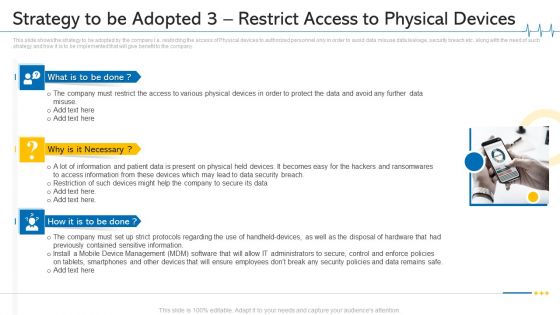
Minimize Cloud Risks Medical Care Business Case Competition Strategy To Be Adopted 3 Restrict Access To Physical Devices Ideas PDF
This slide shows the strategy to be adopted by the company i.e. restricting the access of Physical devices to authorized personnel only in order to avoid data misuse data leakage, security breach etc. along with the need of such strategy and how it is to be implemented that will give benefit to the company. This is a minimize cloud risks medical care business case competition strategy to be adopted 3 restrict access to physical devices ideas pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like mobile device management, data security breach, physical devices. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Checklist Access Control Rules PDF
This slide depicts the access control under the cloud security checklist and how it affects the organizations when data breaches happen due to poor access control management. Presenting Cloud Security Checklist Access Control Rules PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Security, Systems, Networks. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Assessment Cloud Security Checklist Access Control Sample PDF
This slide depicts the access control under the cloud security checklist and how it affects the organizations when data breaches happen due to poor access control management.This is a Cloud Security Assessment Cloud Security Checklist Access Control Sample PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Administrative Rights, Privileged Credentials, Legitimate Users You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Key Components Of People Centric Work Culture Security Ideas PDF
The following slide highlights the key elements of people centric security to prevent data breaches and IT damages. It includes activities such as personalized training, artificial intelligence AI and machine learning ML tools and prompt social engineering attacks etc. Persuade your audience using this Key Components Of People Centric Work Culture Security Ideas PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Personalized Training, Artificial Intelligence, Engineering Risk. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
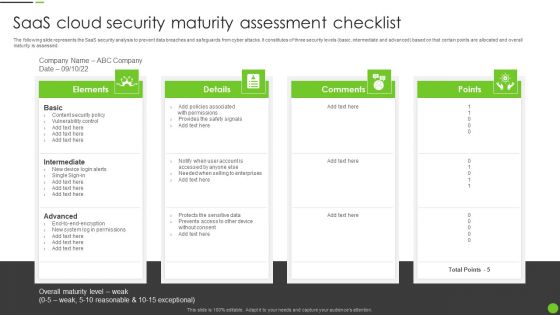
Saas Cloud Security Maturity Assessment Checklist Ppt PowerPoint Presentation File Portfolio PDF
The following slide represents the SaaS security analysis to prevent data breaches and safeguards from cyber attacks. It constitutes of three security levels basic, intermediate and advanced based on that certain points are allocated and overall maturity is assessed. Persuade your audience using this Saas Cloud Security Maturity Assessment Checklist Ppt PowerPoint Presentation File Portfolio PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Intermediate, Advanced, Content Security Policy. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
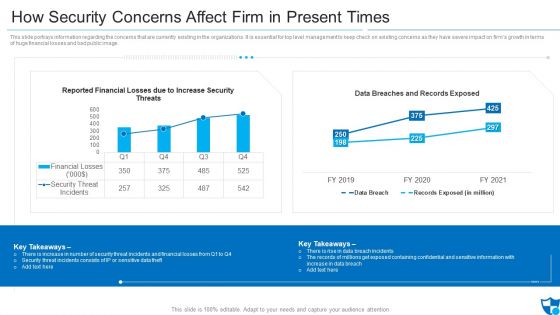
How Security Concerns Affect Firm In Present Times Pictures PDF
This slide portrays information regarding the concerns that are currently existing in the organizations. It is essential for top level management to keep check on existing concerns as they have severe impact on firms growth in terms of huge financial losses and bad public image. Deliver an awe inspiring pitch with this creative how security concerns affect firm in present times pictures pdf bundle. Topics like reported financial losses due to increase security threats, data breaches and records exposed, security threat incidents can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
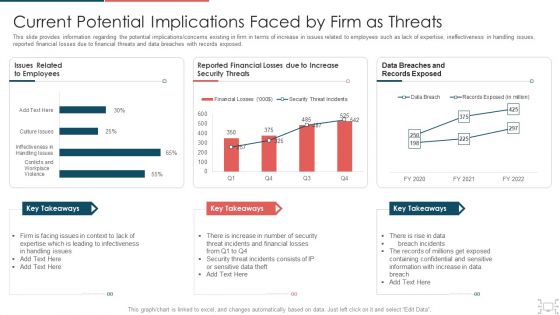
Cyber Security Administration In Organization Current Potential Implications Faced By Firm As Threats Clipart PDF
This slide provides information regarding the potential implications concerns existing in firm in terms of increase in issues related to employees such as lack of expertise, ineffectiveness in handling issues, reported financial losses due to financial threats and data breaches with records exposed. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization current potential implications faced by firm as threats clipart pdf. Use them to share invaluable insights on infectiveness, expertise, issues, security, increase and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Corporate Security And Risk Management Current Potential Implications Faced By Firm As Threats Inspiration PDF
This slide provides information regarding the potential implications or concerns existing in firm in terms of increase in issues related to employees such as lack of expertise, ineffectiveness in handling issues, reported financial losses due to financial threats and data breaches with records exposed. Deliver an awe inspiring pitch with this creative corporate security and risk management current potential implications faced by firm as threats inspiration pdf bundle. Topics like current potential implications faced by firm as threats can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

 Home
Home