Cybersecurity

Strategies For Every Phase Of The Cloud Journey To Remove Network Complexity Download PDF
This slide covers the strategies to overcome network complexities and increase reliability, Enhanced user experience, increasing efficiency and high security. Deliver an awe inspiring pitch with this creative Strategies For Every Phase Of The Cloud Journey To Remove Network Complexity Download PDF bundle. Topics like Productivity, Simplifying Security, Environment can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Training Program Frameworks Cont Ppt File Slideshow PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas.Deliver and pitch your topic in the best possible manner with this security training program frameworks cont ppt file slideshow pdf. Use them to share invaluable insights on implement strong access control measures, regularly monitor and test networks and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Managing IT Security IT 30 Days Plan Ppt Gallery Graphics Download PDF
This slide depicts how the cyber security model will work in the first 30 days and the tasks the organization should focus on. Deliver and pitch your topic in the best possible manner with this managing it security it 30 days plan ppt gallery graphics download pdf. Use them to share invaluable insights on phishing awareness, phishing reporting, phishing repeat offenders, facility physical security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Table Of Contents For Ukraine Cyberwarfare Cont Mockup Pdf
This is a table of contents for ukraine cyberwarfare cont mockup pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like reasons behind ukraine and russia cyber warfare, russian operations against ukraine, cyber attacks on ukraine. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Intelligence Architecture For Comprehensive Threat Evaluation Mockup PDF
This slide depicts an system architecture for complete threat evaluation using cyber intelligence to control the number of cyber-attacks. It includes testing methods, functions, categories, items and properties. Showcasing this set of slides titled Intelligence Architecture For Comprehensive Threat Evaluation Mockup PDF. The topics addressed in these templates are Performance, Timeliness, Customization. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Prevention Of Information Evaluating IT System Security Using Swot Analysis Download PDF
The purpose of this slide is to outline the strength, weakness, opportunities and threat SWOT evaluation of organization cyber security. Organization can detect the potential risks and opportunities in the cyber security using SWOT model. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Prevention Of Information Evaluating IT System Security Using Swot Analysis Download PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Prevention Of Information Evaluating IT System Security Using Swot Analysis Download PDF today and make your presentation stand out from the rest

Evaluating IT System Security Using Swot Analysis Ppt Pictures Clipart Images PDF
The purpose of this slide is to outline the strength, weakness, opportunities and threat SWOT evaluation of organization cyber security. Organization can detect the potential risks and opportunities in the cyber security using SWOT model. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Evaluating IT System Security Using Swot Analysis Ppt Pictures Clipart Images PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Evaluating IT System Security Using Swot Analysis Ppt Pictures Clipart Images PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today

Managing IT Security IT 60 Days Plan Ppt Ideas Graphics PDF
This slide represents the plan for 60 days after implementing the cyber security model in the organization. Deliver an awe inspiring pitch with this creative managing it security it 60 days plan ppt ideas graphics pdf bundle. Topics like policy violations, infected computers, data loss incidents, time to detect an incident can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
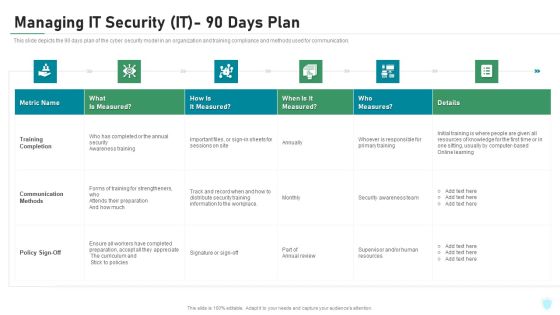
Managing IT Security IT 90 Days Plan Ppt Layouts Picture PDF
This slide depicts the 90 days plan of the cyber security model in an organization and training compliance and methods used for communication. Deliver and pitch your topic in the best possible manner with this managing it security it 90 days plan ppt layouts picture pdf. Use them to share invaluable insights on training completion, communication methods, policy sign off and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Table Of Contents For IT Security IT Cont Tracking Ppt Infographics Graphics Example PDF
Presenting table of contents for it security it cont tracking ppt infographics graphics example pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like cyber security, implementation, communication, administrative, training. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
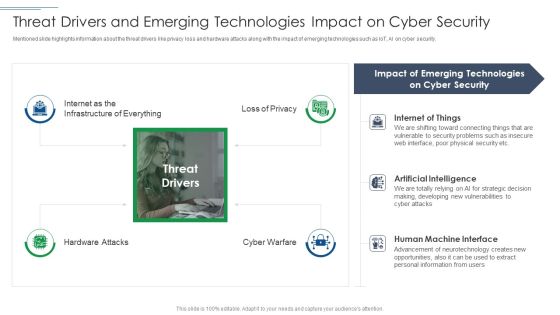
IT Security Risk Management Approach Introduction Threat Drivers And Emerging Technologies Download PDF
Presenting IT Security Risk Management Approach Introduction Threat Drivers And Emerging Technologies Download PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Cyber Security, Emerging Technologies, Artificial Intelligence. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
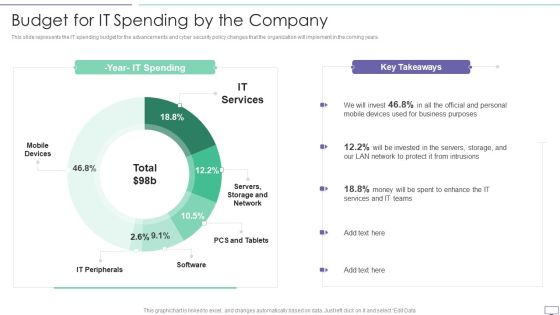
IT Security Hacker Budget For IT Spending By The Company Download PDF
This slide represents the IT spending budget for the advancements and cyber security policy changes that the organization will implement in the coming years.Deliver an awe inspiring pitch with this creative IT Security Hacker Budget For IT Spending By The Company Download PDF bundle. Topics like Business Purposes, Protect Intrusions, Services Teams can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Network Monitoring Tool Overview Introduction To Continuous Monitoring Ppt PowerPoint Presentation Model Slide Download PDF
Presenting this set of slides with name network monitoring tool overview introduction to continuous monitoring ppt powerpoint presentation model slide download pdf. This is a five stage process. The stages in this process are continuous monitoring, introduction, data security, support structure, risk management selections, knowledge security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
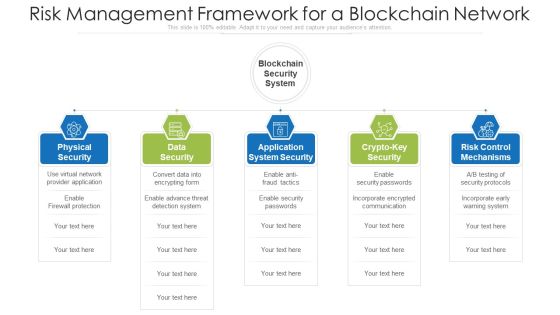
Risk Management Framework For A Blockchain Network Ppt PowerPoint Presentation Portfolio Format Ideas PDF
Persuade your audience using this risk management framework for a blockchain network ppt powerpoint presentation portfolio format ideas pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including application system security, risk control mechanisms, physical security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
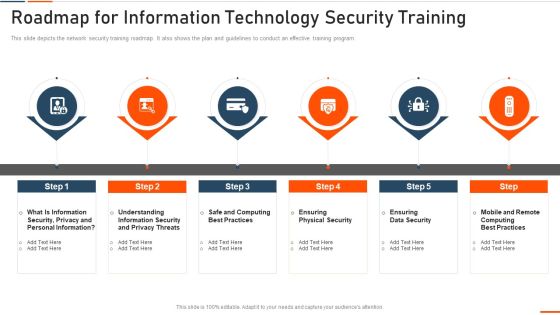
Roadmap For Information Technology Security Training Ppt Ideas Influencers PDF
This slide depicts the network security training roadmap. It also shows the plan and guidelines to conduct an effective training program. This is a roadmap for roadmap for information technology security training ppt ideas influencers pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like rmation security, computing best practices, physical security, data security . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Architecture In 5G Technology 5G Functional Architecture Topics PDF
This slide represents the security architecture in 5G technology, including the system-wide security tasks and 5G function element deployments or vertical security. The components include devices, global wireless solutions, access and network, applications and cloud infrastructure, and user ID administration.Deliver an awe inspiring pitch with this creative Security Architecture In 5G Technology 5G Functional Architecture Topics PDF bundle. Topics like Standardization Segment, Concentrated Security, Components Interfaces can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Corporate Security And Risk Management Determine Several Threat Actors Profile Clipart PDF
This slide provides details regarding several threat actors profile such as cyber criminal and hacktivists and addressing them on parameters such as motive, intent, capability, action, target victim, etc. Deliver an awe inspiring pitch with this creative corporate security and risk management determine several threat actors profile clipart pdf bundle. Topics like determine several threat actors profile can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Table Of Contents Data Safety Initiatives For Effective IT Security Threats Administration Summary PDF
Presenting table of contents data safety initiatives for effective it security threats administration summary pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like overcoming identified gaps, improved incident reporting, communication plan cyber breaches, ensuring effective risk governance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Impact Of Security Awareness Training Ppt Inspiration Design Templates PDF
This slide covers the good impact of security awareness program such as declining in the number of security threats which are phishing, network intrusion, inadvertent disclosure, stolen or lost devices or records and system misconfiguration. Deliver and pitch your topic in the best possible manner with this impact of security awareness training ppt inspiration design templates pdf. Use them to share invaluable insights on impact of security awareness training and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Computer System Security PowerPoint Templates And PowerPoint Themes 1012
Computer System Security PowerPoint Templates And PowerPoint Themes 1012-Deliver amazing Presentations with our above template consists of laptop and lifesaver. This image represents the concept of computer help or assistance. This template also depicts the concept of computer security. Use this template for web services, technical support etc. It signifies assistance, nteworking, rescue and save. It is a useful captivating tool conceived to enable you to define your message in your Business PPT presentations. Deliver amazing presentations to mesmerize your audience.-Computer System Security PowerPoint Templates And PowerPoint Themes 1012-This PowerPoint template can be used for presentations relating to-Computer network , marketing, finance, internet, computer, technology

Security Functioning Centre Analysing Different SOC Deployment Models Template PDF
This slide portrays information regarding the different security operations center deployment models from which firm can choose the suitable deployment model based on the characteristics associated to the Models. This is a security functioning centre analysing different soc deployment models template pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like distributed, network, security operations, operational technology, threat intelligence. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Blockchain Technology Framework IT Is Blockchain Technology Secure Demonstration PDF
This slide defines the security of blockchain technology and how hash codes are helpful to maintain data integrity and security in blockchain. This is a blockchain technology framework it is blockchain technology secure demonstration pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like expensive, systems, blockchain network, operations database. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
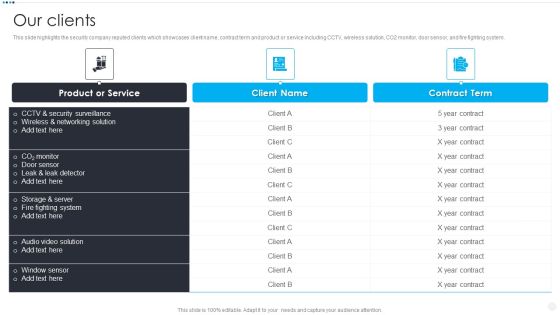
Smart Home Security Solutions Company Profile Our Clients Inspiration PDF
This slide highlights the security company reputed clients which showcases client name, contract term and product or service including CCTV, wireless solution, CO2 monitor, door sensor, and fire fighting system. Deliver and pitch your topic in the best possible manner with this Smart Home Security Solutions Company Profile Our Clients Inspiration PDF. Use them to share invaluable insights on Product Or Service, CCTV And Security, Wireless And Networking, Storage And Server and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
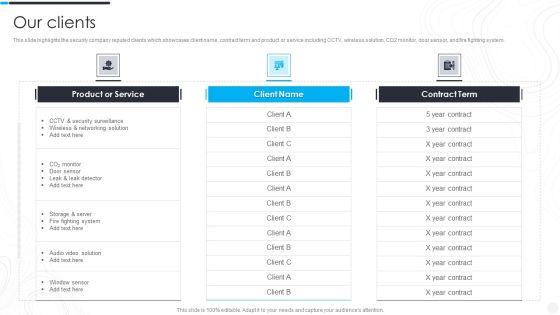
Security Camera System Company Profile Our Clients Rules PDF
This slide highlights the security company reputed clients which showcases client name, contract term and product or service including CCTV, wireless solution, CO2 monitor, door sensor, and fire fighting system. Deliver and pitch your topic in the best possible manner with this Security Camera System Company Profile Our Clients Rules PDF. Use them to share invaluable insights on Product Or Service, Security Surveillance, Wireless Networking and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Corporate System Security Quality Assurance Matrix Demonstration PDF
This slide covers quality assurance for corporate system security. It includes a matrix based on functional and customer requirements for security system such as no access to restricted sites, email tracking, confidential data protection, etc. Showcasing this set of slides titled Corporate System Security Quality Assurance Matrix Demonstration PDF. The topics addressed in these templates are Customer Requirements, Functional Requirements, Centralised Network. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Security Operations Essential Functions For Customer Satisfaction Inspiration PDF
This slide highlights key functions performed by SecOps team members in order to meet IT infrastructure network security objectives. It includes security monitoring, threat intelligence, triage and investigations, incident response, and root cause analysis. Persuade your audience using this Security Operations Essential Functions For Customer Satisfaction Inspiration PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Triage And Investigation, Incident Response, Root Course Analysis. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Information Security Process To Manage Firms Sensitive Data Mockup PDF
This slide provides information about information security process in order to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc. Boost your pitch with our creative Information Security Process To Manage Firms Sensitive Data Mockup PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Major Techniques For Project Safety IT Information Security Process To Manage Firms Sensitive Data Designs PDF
This slide provides information about information security process in order to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc. Deliver and pitch your topic in the best possible manner with this major techniques for project safety it information security process to manage firms sensitive data designs pdf. Use them to share invaluable insights on privileged password management, daily tasks performed by network administrator, network security audit checklist and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Upgrading Total Project Safety IT Information Security Process To Manage Firms Sensitive Data Structure PDF
This slide provides information about information security process in order to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc. Presenting upgrading total project safety it information security process to manage firms sensitive data structure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like privileged password management, daily tasks performed by network administrator, network security audit checklist. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Arrow 5 Stages Diverging Process Diagram Circular Network PowerPoint Templates
We present our arrow 5 stages diverging process diagram Circular Network PowerPoint templates.Present our Arrows PowerPoint Templates because you can present your opinions in this field using our impressive templates. Present our Business PowerPoint Templates because you have secured a name for yourself in the domestic market. Now the time is right to spread your reach to other countries. Download and present our Shapes PowerPoint Templates because they are Designed to attract the attention of your audience. Download our Process and Flows PowerPoint Templates because you are the star of your enlightened team. Use our Flow charts PowerPoint Templates because it helps to anticipate the doubts and questions in the minds of your colleagues and enlighten them with your inspired strategy to garner desired success.Use these PowerPoint slides for presentations relating to Arrow, green ,brochure, business, button, catalog, chart, circle, company, cross, design, diagram, direction, financial, glossy, goals,graph, green, junction, management, market, marketing, model, multicolored, multiple, navigation, network, options, orange, pie, plan, presentation, process, gray, sphere, statistics . The prominent colors used in the PowerPoint template are Green, Black, White. You can be sure our arrow 5 stages diverging process diagram Circular Network PowerPoint templates are Fantastic. Presenters tell us our catalog PowerPoint templates and PPT Slides are Gorgeous. We assure you our arrow 5 stages diverging process diagram Circular Network PowerPoint templates are Cheerful. Customers tell us our catalog PowerPoint templates and PPT Slides are Versatile. Presenters tell us our arrow 5 stages diverging process diagram Circular Network PowerPoint templates are designed by professionals You can be sure our catalog PowerPoint templates and PPT Slides are Graceful.

Security Training Program Frameworks Ppt Infographics Show PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas.This is a security training program frameworks ppt infographics show pdf. template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like build and maintain a secure network and systems, protect cardholder data. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Determine Focus Areas To Implement Security Operations Centre Diagrams PDF
This slide portrays information regarding the focus areas that are need to be addressed for effective implementation of security operations center. The focus areas are such as digital forensics and control, risk monitoring and management, etc. Deliver an awe inspiring pitch with this creative determine focus areas to implement security operations centre diagrams pdf bundle. Topics like digital forensics and control, risk monitoring and management, system and network administration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Security Program Values To Business Ppt File Smartart PDF
Following slide displays the major program values to companys business. Values here are divided in two areas namely detection and response and attack surface management. Presenting information security program values to business ppt file smartart pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like reduce, security, network, environment, management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Checklist Logging And Monitoring Download PDF
This slide defines the importance of logging and monitoring activities on data in a network and how it could be beneficial in future analysis. This is a Cloud Security Checklist Logging And Monitoring Download PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Potential, Observe Systems, Security Breaches. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Certified Information Systems Security Professional CISSP Examination Details Infographics PDF
This slide covers information about CISSP Examination such as weight of each domain in exams, prep courses details, qualification details etc. This is a Certified Information Systems Security Professional CISSP Examination Details Infographics PDF template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Requirements, Network Security, Risk Management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Integrated IOT Blockchain Platform Security Through Technology Background PDF
This slide covers steps for processing crypto currency transactions using block chain P2P technology. The purpose of this slide is to provide information on securing financial transactions. It includes steps from requesting transaction, transferring it on P2P network, validating transactions, creation of new data block, etc. Persuade your audience using this Integrated IOT Blockchain Platform Security Through Technology Background PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Transaction Requested Party, Requested Transaction, Crypto Currency. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
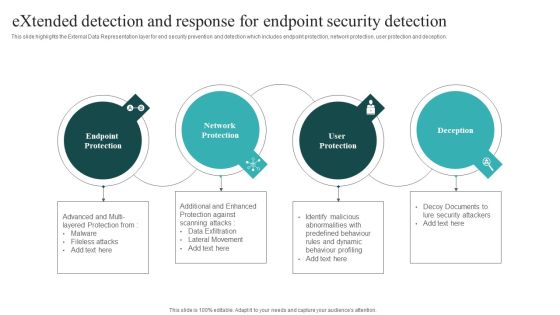
Extended Detection And Response For Endpoint Security Detection Themes PDF
This slide highlights the External Data Representation layer for end security prevention and detection which includes endpoint protection, network protection, user protection and deception. Boost your pitch with our creative Extended Detection And Response For Endpoint Security Detection Themes PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Business Governance Framework For Cryptographically Secured Services Structure PDF
This slide signifies the organisation governance model for cryptographically secured services. It includes steps like generic value network, analysis, canvas analysis and plan.Persuade your audience using this Business Governance Framework For Cryptographically Secured Services Structure PDF. This PPT design covers one stage, thus making it a great tool to use. It also caters to a variety of topics including Suggested Service, Provider Business, Business Model. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Scan Principle For Smart Phone Security Model Clipart PDF
This slide shows SCAN framework for securing phone against possible threats to prevent loss of business data. It include components such as system, configuration, application and network, etc. Persuade your audience using this Scan Principle For Smart Phone Security Model Clipart PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including System, Configuration, App. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Bring Your Own Device Security Policy Checklist Graphics PDF
This slide showcases checklist for bring your own device policy to map and understand of information network. It also includes check points related to back up, data security, companys protocol, etc. Presenting Bring Your Own Device Security Policy Checklist Graphics PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Check Points, Checklist, Device. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cloud Computing Security Architecture Training Program Guidelines PDF
The slide shows a training schedule overview for cloud security. It includes training of identify and assess management, compute and configuration management, data protection and automation, networking and logging, compliance, incident response and penetration testing and cloud wars. Showcasing this set of slides titled Cloud Computing Security Architecture Training Program Guidelines PDF. The topics addressed in these templates are Identify Access Management, Compute Configuration Management, Data Protection Automation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Business PowerPoint Templates Download Process Circular Flow Network Slides
We present our business powerpoint templates download process Circular Flow Network Slides.Download and present our Globe PowerPoint Templates because You can Be the puppeteer with our PowerPoint Templates and Slides as your strings. Lead your team through the steps of your script. Download and present our Ring Charts PowerPoint Templates because You can Inspire your team with our PowerPoint Templates and Slides. Let the force of your ideas flow into their minds. Download our Circle Charts PowerPoint Templates because this Layout can explain the relevance of the different layers and stages in getting down to your core competence, ability and desired result. Use our Arrows PowerPoint Templates because it shows various choices to be made. Use our Business PowerPoint Templates because you have secured a name for yourself in the domestic market. Now the time is right to spread your reach to other countries.Use these PowerPoint slides for presentations relating to Business, chart, circle,colors, concept, corporate, cycle, data,design, detail, development, diagram,engineering, graphic, ideas, illustration,image, implement, implementation, life,lifecycle, management, model, objects,organization, phase, plan, process,product, professional, project, quality,schema, shape. The prominent colors used in the PowerPoint template are Blue, Yellow, White. You can be sure our business powerpoint templates download process Circular Flow Network Slides will make you look like a winner. PowerPoint presentation experts tell us our circle PowerPoint templates and PPT Slides are designed by professionals Professionals tell us our business powerpoint templates download process Circular Flow Network Slides are Graceful. Presenters tell us our data PowerPoint templates and PPT Slides are the best it can get when it comes to presenting. Professionals tell us our business powerpoint templates download process Circular Flow Network Slides are Whimsical. Customers tell us our corporate PowerPoint templates and PPT Slides are Beautiful.
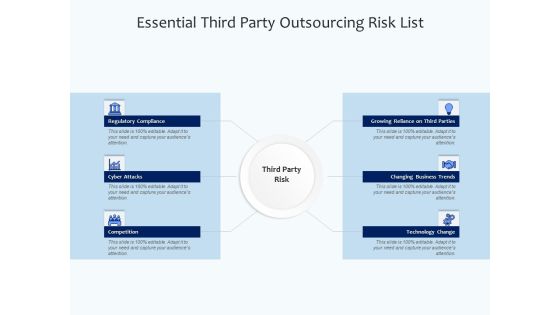
Essential Third Party Outsourcing Risk List Ppt PowerPoint Presentation File Sample PDF
Presenting essential third party outsourcing risk list ppt powerpoint presentation file sample pdf. to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including regulatory compliance, cyber attacks, competition, changing business trends, technology change. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
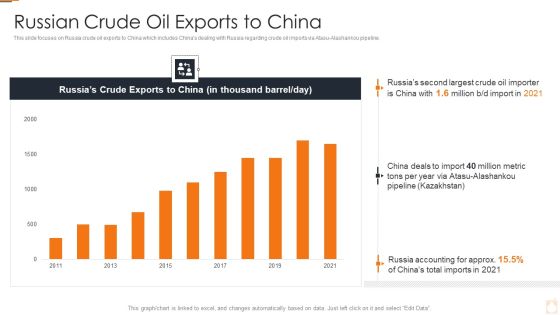
Ukraine Russia Conflict Effect On Petroleum Industry Russian Crude Oil Exports To China Information PDF
Deliver an awe inspiring pitch with this creative Ukraine Russia Conflict Effect On Petroleum Industry Russian Crude Oil Exports To China Information PDF bundle. Topics like Higher Energy Prices, Trade And Supply Chains, Increase In Cyber Attacks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Security Hacker Introduction To Ethical Hacking Graphics PDF
This slide depicts ethical hacking and how ethical hackers could be an asset to a company that can prevent malicious attacks on a computer system or network.This is a IT Security Hacker Introduction To Ethical Hacking Graphics PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Approved Effort, Data Is Referred, Ethical Hacking. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Blockchain Security Management Technology Working Flowchart Download PDF
This slide illustrates the working model of blockchain technology which is used to track and manage transaction in a business network. Process is divides into seven major steps. Persuade your audience using this Blockchain Security Management Technology Working Flowchart Download PDF. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including Transaction Completion, Cryptocurrency, Blockchain. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
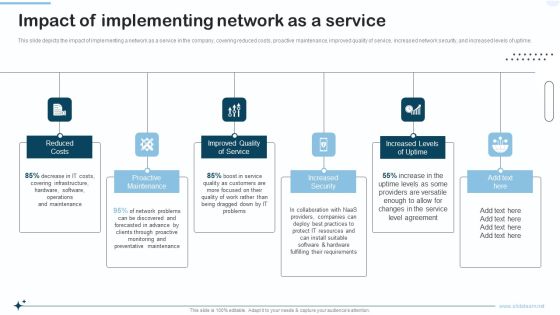
Naas Integrated Solution IT Impact Of Implementing Network As A Service Portrait PDF
This slide depicts the impact of implementing a network as a service in the company, covering reduced costs, proactive maintenance, improved quality of service, increased network security, and increased levels of uptime. Presenting Naas Integrated Solution IT Impact Of Implementing Network As A Service Portrait PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Improved Quality Of Service, Increased Security, Increased Levels Of Uptime. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
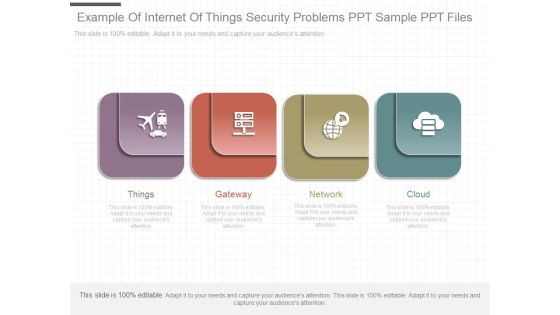
Example Of Internet Of Things Security Problems Ppt Sample Ppt Files
This is a example of internet of things security problems ppt sample ppt files. This is a four stage process. The stages in this process are things, gateway, network, cloud.
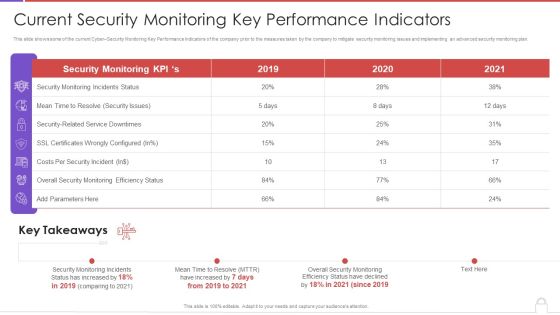
Methods To Develop Advanced Current Security Monitoring Key Performance Indicators Formats PDF
This slide shows some of the current Cyber Security Monitoring Key Performance Indicators of the company prior to the measures taken by the company to mitigate security monitoring issues and implementing an advanced security monitoring plan. Deliver an awe inspiring pitch with this creative methods to develop advanced current security monitoring key performance indicators formats pdf bundle. Topics like monitoring incidents status, security issues, costs per security incident, 2019 to 2020 can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
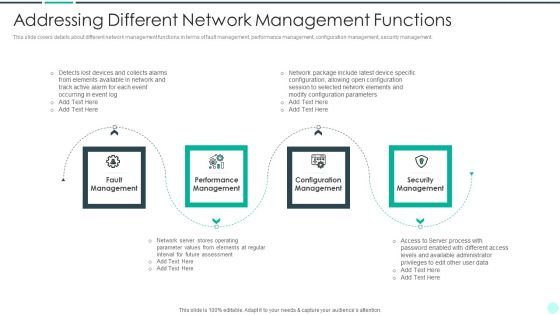
Executing Advance Data Analytics At Workspace Addressing Different Network Rules PDF
This slide covers details about different network management functions in terms of fault management, performance management, configuration management, security management. This is a executing advance data analytics at workspace addressing different network rules pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like management, performance, security, elements. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
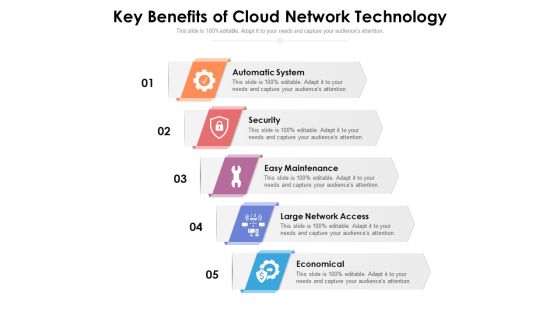
Key Benefits Of Cloud Network Technology Ppt PowerPoint Presentation Show Good PDF
Presenting this set of slides with name key benefits of cloud network technology ppt powerpoint presentation show good pdf. This is a five stage process. The stages in this process are automatic system, security, easy maintenance, large network access, economical. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Roadmap For IT Security IT Training Ppt Slides Format Ideas PDF
This slide depicts the cyber security training roadmap. It also shows the plan and guidelines to conduct an effective training program. Presenting roadmap for it security it training ppt slides format ideas pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security, privacy, safe and computing, ensuring physical security, mobile and remote. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
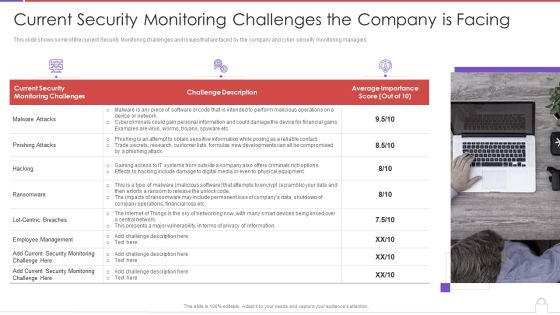
Methods To Develop Advanced Current Security Monitoring Challenges The Company Is Facing Professional PDF
This slide shows some of the current Security Monitoring challenges and issues that are faced by the company and cyber security monitoring managers. This is a methods to develop advanced current security monitoring challenges the company is facing professional pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like current security, monitoring challenges, challenge description, average importance score. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Roadmap Of Digital Risk Assessment Asset And Security Policy Development Sample PDF
The following slide highlights the roadmap of cyber security asset assessment and security policy development for organisation to draft system security policy which describes assessment, build, select, deployment, awareness and audit. Persuade your audience using this Roadmap Of Digital Risk Assessment Asset And Security Policy Development Sample PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Assessment, Build, Deployment, Select, Audit, Awareness. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Prevention Of Information Comparison Of Various Security Awareness Training Software Template PDF
The purpose of this slide is to drawn comparison of multiple software which can be used to provide cyber security training to the key stakeholders. Information covered in this slide is related to phishing simulations, security reporting, individualized security training plan etc. There are so many reasons you need a Prevention Of Information Comparison Of Various Security Awareness Training Software Template PDF. The first reason is you cant spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Our Services For Safety And Security System Services Proposal One Pager Sample Example Document
Purpose of the following slide is to show the key services that the organization offers , these services can be personal bodyguard services , cyber security services and security guard service. Presenting you an exemplary Our Services For Safety And Security System Services Proposal One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Our Services For Safety And Security System Services Proposal One Pager Sample Example Document brilliant piece now.

Our Services Proposal For Security Guard Services One Pager Sample Example Document
Purpose of the following slide is to show the key services that the organization offers , these services can be personal bodyguard services , cyber security services and security guard service. Presenting you an exemplary Our Services Proposal For Security Guard Services One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Our Services Proposal For Security Guard Services One Pager Sample Example Document brilliant piece now.

Security Operations Certifications And Training Courses For IT Professionals Topics PDF
This slide exhibits training courses for security operations administrators to enhance their cyber threat management skills. It includes elements such as course, course outline, rating, pricing, frequency, and mode of training. Showcasing this set of slides titled Security Operations Certifications And Training Courses For IT Professionals Topics PDF. The topics addressed in these templates are Security Operations, Fundamental, Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

5G Network Technology Assessing Contribution Of 5G To Global Economy Ppt Icon Slideshow PDF
This slide provides details regarding contribution of 5G to global economy with key enablers to digital economy such as infrastructure digital security and safety, regional specific content and services, etc. Deliver an awe inspiring pitch with this creative 5g network technology assessing contribution of 5g to global economy ppt icon slideshow pdf bundle. Topics like infrastructure, digital security and safety, regional specific content and services, enabling people to manage digitalization can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Various Types Of Payment Network Gateway Testing Ppt File Objects PDF
The following slide showcases types of gateway testing to ensure fast and errorless payment. Main test covered are functional, integration, performance, security and bank statement reconciliation. Persuade your audience using this Various Types Of Payment Network Gateway Testing Ppt File Objects PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Functional Testing, Integration Testing, Performance Testing, Security Testing . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Detail Impact Security Awareness Training Can Reduce The Risk Of A Data Breach Professional PDF
This slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen or lost devices or records and inadvertent disclosure. Deliver an awe-inspiring pitch with this creative detail impact security awareness training can reduce the risk of a data breach professional pdf bundle. Topics like phishing breakdown, network intrusion breakdown can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Detail Impact Security Awareness Training Can Reduce The Risk Of A Data Breach Information PDF
This slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen or lost devices or records and inadvertent disclosure. Deliver an awe-inspiring pitch with this creative detail impact security awareness training can reduce the risk of a data breach information pdf bundle. Topics like phishing breakdown, network intrusion breakdown, system misconfiguration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Detail Impact Security Awareness Training Can Reduce The Risk Of A Data Breach Icons PDF
This slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen or lost devices or records and inadvertent disclosure. Deliver an awe-inspiring pitch with this creative detail impact security awareness training can reduce the risk of a data breach icons pdf bundle. Topics like phishing breakdown, network intrusion breakdown can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Developing Firm Security Strategy Plan Contingency Plan For Threat Handling At Workplace Summary PDF
This slide portrays information contingency plan for handling threats at workplace with the help of technical equipment that assist contingency solution and considerations. Deliver an awe inspiring pitch with this creative developing firm security strategy plan contingency plan for threat handling at workplace summary pdf bundle. Topics like server, website, local area network, wide area network, mainframe systems, distributes systems can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
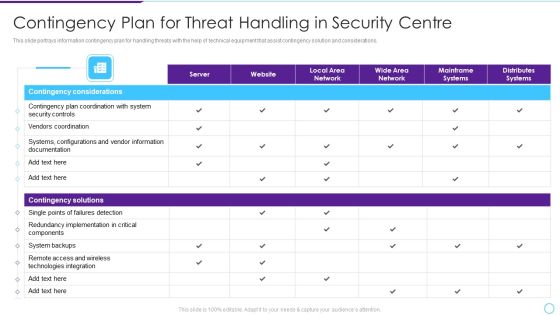
Intelligent Infrastructure Contingency Plan For Threat Handling In Security Centre Mockup PDF
This slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations. Deliver an awe inspiring pitch with this creative Intelligent Infrastructure Contingency Plan For Threat Handling In Security Centre Mockup PDF bundle. Topics like Contingency Considerations, Contingency Solutions, Server, Local Area Network, Local Area Network can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Hardware And Software Update In Company IT Security IT Ppt Model Infographics PDF
This slide depicts the hardware or software update measure under the cyber security model. It also tells the current status of the devices that need to update in the organization. Presenting hardware and software update in company it security it ppt model infographics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like technology, security, data across. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security Hardware And Software Update In Company Ppt Infographics Ideas PDF
This slide depicts the hardware or software update measure under the cyber security model. It also tells the current status of the devices that need to update in the organization. This is a it security hardware and software update in company ppt infographics ideas pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like technology, security, operating systems. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Info Security What Are The Benefits Of Informationsecurity Ppt PowerPoint Presentation Gallery Inspiration PDF
This slide depicts the different benefits of deploying a cyber security model in an organization and how it can minimize the risk and save a companys time, money, and efforts. Presenting info security what are the benefits of informationsecurity ppt powerpoint presentation gallery inspiration pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like data capture, threats online environment, security devices. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
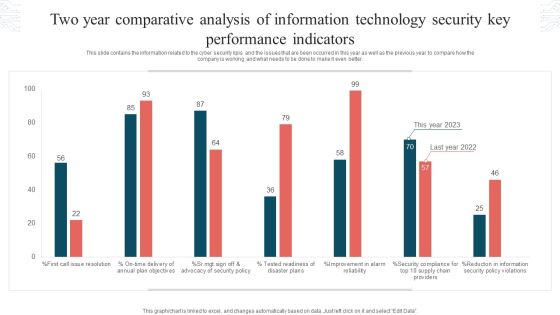
Two Year Comparative Analysis Of Information Technology Security Key Performance Indicators Graphics PDF
This slide contains the information related to the cyber security kpis and the issues that are been occurred in this year as well as the previous year to compare how the company is working and what needs to be done to make it even better. Showcasing this set of slides titled Two Year Comparative Analysis Of Information Technology Security Key Performance Indicators Graphics PDF. The topics addressed in these templates are Tested Readiness, Disaster Plans, Security Policy Violations. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Detail Impact Security Awareness Training Can Reduce The Risk Of A Data Breach Hacking Prevention Awareness Training For IT Security Professional PDF
This slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen or lost devices or records and inadvertent disclosure. Deliver and pitch your topic in the best possible manner with this detail impact security awareness training can reduce the risk of a data breach hacking prevention awareness training for it security professional pdf. Use them to share invaluable insights on system misconfiguration, network intrusion breakdown, phishing breakdown and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
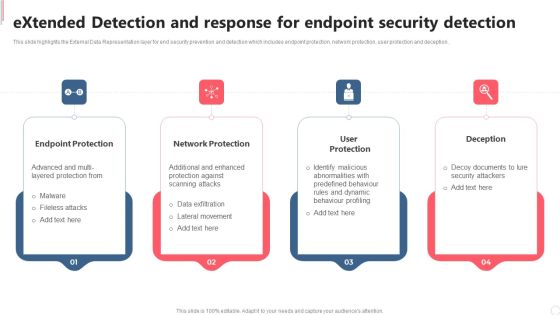
Extended Detection And Response For Endpoint Security Detection Clipart PDF
This slide highlights the External Data Representation layer for end security prevention and detection which includes endpoint protection, network protection, user protection and deception. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Extended Detection And Response For Endpoint Security Detection Clipart PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Extended Detection And Response For Endpoint Security Detection Clipart PDF today and make your presentation stand out from the rest.

Information Security Checklist For Data Privacy Implementation Elements PDF
This slide represents the checklist for data privacy implementation, which includes ensuring that every employee in the firm is aware of data privacy, monitoring the network for odd behavior. Presenting this PowerPoint presentation, titled Information Security Checklist For Data Privacy Implementation Elements PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Information Security Checklist For Data Privacy Implementation Elements PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Information Security Checklist For Data Privacy Implementation Elements PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
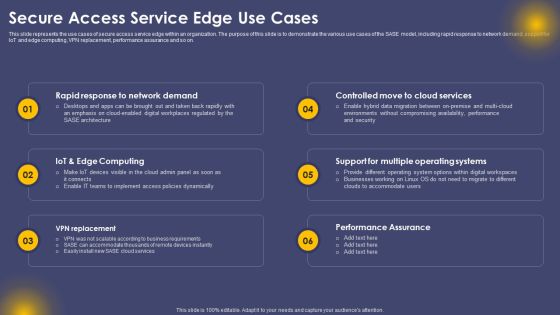
Secure Access Service Edge Use Cases Ppt Outline Images PDF
This slide represents the use cases of secure access service edge within an organization. The purpose of this slide is to demonstrate the various use cases of the SASE model, including rapid response to network demand, support for IoT and edge computing, VPN replacement, performance assurance and so on. Explore a selection of the finest Secure Access Service Edge Use Cases Ppt Outline Images PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Secure Access Service Edge Use Cases Ppt Outline Images PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Comparison Between ZTNA And Secure Access Service Edge Professional PDF
This slide compares the two security models, such as zero trust network architecture and secure access service edge. The purpose of this slide is to highlight the difference between ZTNA and SASE based on definition, key features, deployment, use cases, benefits and challenges. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Comparison Between ZTNA And Secure Access Service Edge Professional PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
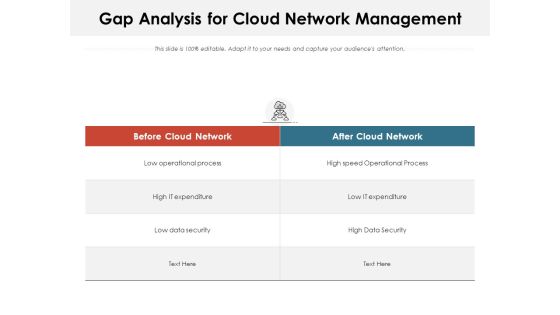
Gap Analysis For Cloud Network Management Ppt PowerPoint Presentation File Aids PDF
Presenting this set of slides with name gap analysis for cloud network management ppt powerpoint presentation file aids pdf. The topics discussed in these slides are process, data security, expenditure. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
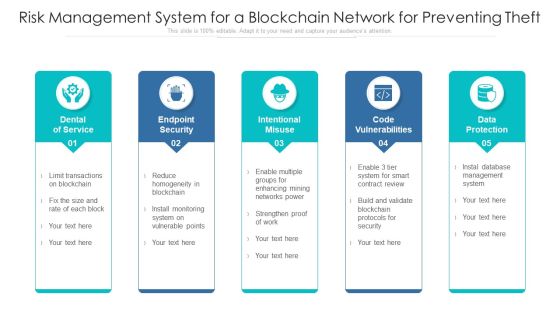
Risk Management System For A Blockchain Network For Preventing Theft Ppt PowerPoint Presentation Layouts Deck PDF
Presenting risk management system for a blockchain network for preventing theft ppt powerpoint presentation layouts deck pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including endpoint security, intentional misuse, code vulnerabilities. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Elements Of IT Security IT End User Education Ppt Model Deck PDF
This slide shows the end-user education within the cyber security model. It also represents various factors that effective training plans should involve. This is a elements of it security it end user education ppt model deck pdf template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like hire professional, train often, password protocols, microlearning opportunities, effective training. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Dashboard For Threat Tracking In IT Security IT Ppt Outline Examples PDF
This slide depicts the dashboard for threat tracking in cyber security by covering monthly threat status, current risk status, threat-based on the role, threats by owners, risk by threats, and threat report. Deliver an awe inspiring pitch with this creative dashboard for threat tracking in it security it ppt outline examples pdf bundle. Topics like monthly threat status, threats by owners, risk by threats, current risk status, threats based on role, threat report can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Info Security Hardware And Software Update In Company Ppt PowerPoint Presentation File Mockup PDF
This slide depicts the hardware or software update measure under the cyber security model. It also tells the current status of the devices that need to update in the organization. Presenting info security hardware and software update in company ppt powerpoint presentation file mockup pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like peripheral devices, technology, computers and servers. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

How To Overcome The Security Awareness Training Program Challenges Clipart PDF
The purpose of this is to highlight various solutions which can be used to overcome the cyber security awareness challenges. The key solutions covered in the slide are introducing dynamic courses, fully managed training program, convenient program etc. Deliver and pitch your topic in the best possible manner with this How To Overcome The Security Awareness Training Program Challenges Clipart PDF. Use them to share invaluable insights on Burden On Administrators, Employee Participation, Lose Interest and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Practices To Improve Security Awareness Level Amongst The Employees Contd Structure PDF
The purpose of this slide is to outline multiple ways which can be used by the organization to improve the cyber security awareness level of employees. The key practices mentioned in the slide are involving top level management, developing robust policies, and setting guidelines. Presenting Practices To Improve Security Awareness Level Amongst The Employees Contd Structure PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Management Involved, Develop Robust, Set Guidelines. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Organizations Risk Management And IT Security Integration Of Risk Management Into SDLC Inspiration PDF
This slide highlights the risk management integration with software development life cycle which includes SDLC phases Initiation, development, implementation and maintenance with risk management activities. The Organizations Risk Management And IT Security Prioritized Cyber Security Threats With Risk Mitigation Plan Demonstration PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
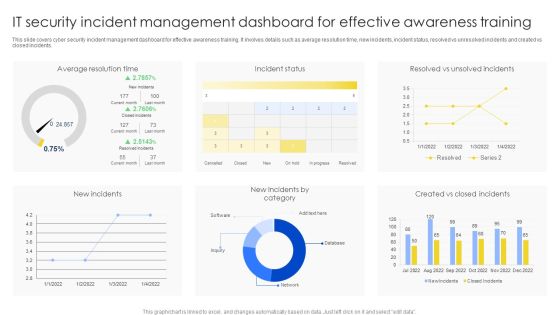
IT Security Incident Management Dashboard For Effective Awareness Training Pictures PDF
This slide covers cyber security incident management dashboard for effective awareness training. It involves details such as average resolution time, new incidents, incident status, resolved vs unresolved incidents and created vs closed incidents. Showcasing this set of slides titled IT Security Incident Management Dashboard For Effective Awareness Training Pictures PDF. The topics addressed in these templates are Average Resolution Time, Incident Status, New Incidents. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
IT Security Plan Best Practices To Defend Against Threats Icons PDF
This slide represents cyber security strategy best practices to defend against threats such a development of insider threat program, training employees, maintaining compliance etc. Persuade your audience using this IT Security Plan Best Practices To Defend Against Threats Icons PDF. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including Updating Systems And Software, Data Backup, Maintaining Compliance. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Prevention Of Information Comparative Assessment Of Security Awareness Online Courses Icons PDF
The purpose of this slide is to showcase comparison of various advance cyber security training courses. The comparison is drawn on the basis of course description, level, duration, no. of companies enrolled for this course etc. Want to ace your presentation in front of a live audience Our Prevention Of Information Comparative Assessment Of Security Awareness Online Courses Icons PDF can help you do that by engaging all the users towards you.. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

CPS Security And Privacy Life Cycle Ppt PowerPoint Presentation File Files PDF
This slide depicts the cyber physical systems security and privacy life cycle, including its phases from 1 to 6, along with the tasks performed in each phase. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate CPS Security And Privacy Life Cycle Ppt PowerPoint Presentation File Files PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Checklist To Ensure Secure Mobile Banking Ppt Inspiration Deck PDF
This slide shows checklist which can be used to adopt various security measure while using mobile banking. It includes tasks such as change passwords frequently, monitor transactions, avoid using public networks. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Checklist To Ensure Secure Mobile Banking Ppt Inspiration Deck PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Key Components Of Grid Computing Security Structure PDF
This slide talks about the security component of a grid computing network and how it protects the system by offering authentication and authorization processes. It also contains the OpenSSL deployment that permit users to execute operations within the grid. Welcome to our selection of the Key Components Of Grid Computing Security Structure PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
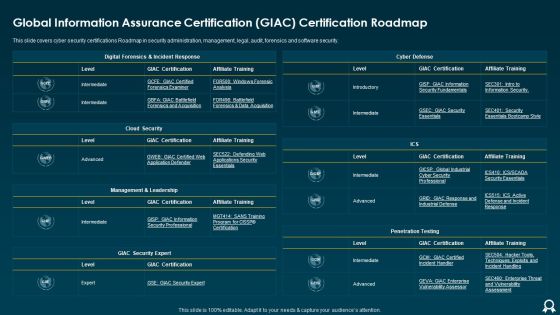
Global Information Assurance Certification GIAC Certification Roadmap Formats PDF
This slide covers cyber security certifications Roadmap in security administration, management, legal, audit, forensics and software security. Deliver an awe inspiring pitch with this creative Global Information Assurance Certification GIAC Certification Roadmap Formats PDF bundle. Topics like Cloud Security, Cyber Defense, Management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Project Security Administration IT Comparative Assessment Of Various Threat Agents Affecting Overall Project Safety Background PDF
This slide provides information regarding comparative assessment of different threat agents impacting IT project safety comparing on various parameters such as data loss impact, skills required to handle threat, etc. Deliver and pitch your topic in the best possible manner with this project security administration it comparative assessment of various threat agents affecting overall project safety background pdf. Use them to share invaluable insights on resource requirement, maintenance threats, cyber threats, social engineering and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Corporate Security And Risk Management Ensuring Collaboration Among Various Rules PDF
This slide provides details regarding ensuring collaboration among various functional areas in order to minimize insider cyber threats. Presenting corporate security and risk management ensuring collaboration among various rules pdf to provide visual cues and insights. Share and navigate important information on ten stages that need your due attention. This template can be used to pitch topics like finance, human resources, procurement, public relations, collaboration. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

SDN Security Architecture Infrastructure Layer And Apis Professional PDF
This slide represents the infrastructure layer and Application programming interfaces of SDN architecture. The layer contains the physical switches and other devices that help redirect the network traffic, and APIs are used to interact between the three layers of the SDN architecture. Slidegeeks has constructed SDN Security Architecture Infrastructure Layer And Apis Professional PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.
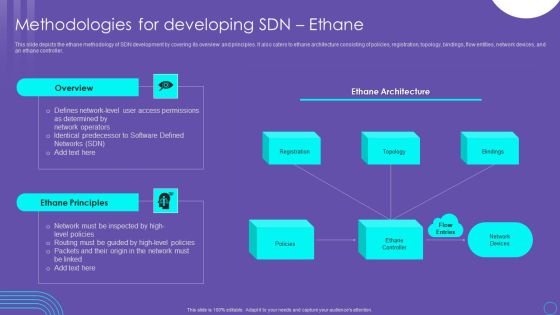
SDN Security Architecture Methodologies For Developing SDN Ethane Infographics PDF
This slide depicts the ethane methodology of SDN development by covering its overview and principles. It also caters to ethane architecture consisting of policies, registration, topology, bindings, flow entities, network devices, and an ethane controller. This SDN Security Architecture Methodologies For Developing SDN Ethane Infographics PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Application Protection Ppt Layout Presentation Design
This is a application protection ppt layout presentation design. This is a seven stage process. The stages in this process are content security, risk mitigation, risk assessment, application security, evaluation and assessment, endpoint security, network security.

Digitalization Of Operative Enterprises Breaking Up Of Network Into Zones Template PDF
This slide covers breaking of internal networks up into autonomous zones according to the risks faced by company. Deliver and pitch your topic in the best possible manner with this Digitalization Of Operative Enterprises Breaking Up Of Network Into Zones Template PDF. Use them to share invaluable insights on Virtualization Security, Network, System and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
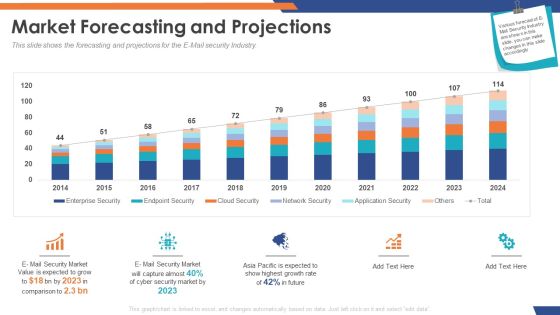
Email Security Market Research Report Market Forecasting And Projections Infographics PDF
Presenting this set of slides with name email security market research report market forecasting and projections infographics pdf. The topics discussed in these slides are network security, cloud security, endpoint security, enterprise security, application security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
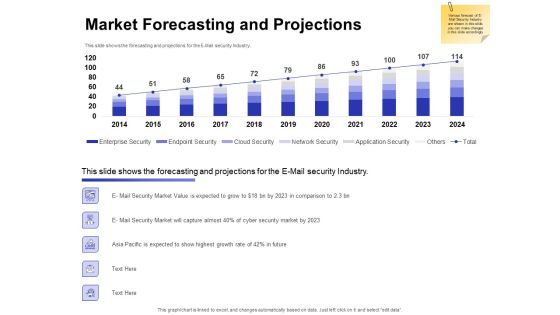
Global Cloud Based Email Security Market Market Forecasting And Projections Professional PDF
Presenting this set of slides with name global cloud based email security market market forecasting and projections professional pdf. The topics discussed in these slides are network security, cloud security, endpoint security, enterprise security, application security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Data Breach Prevention Recognition Impact Of Security Awareness Training Sample PDF
This slide covers the good impact of security awareness program such as declining in the number of security threats which are phishing, network intrusion, inadvertent disclosure, stolen or lost devices or records and system misconfiguration. Deliver an awe-inspiring pitch with this creative data breach prevention recognition impact of security awareness training sample pdf bundle. Topics like security awareness program, security threats, network intrusion, inadvertent disclosure, system misconfiguration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Public And Private Cloud Network Icon For Enterprise Data Management Ppt PowerPoint Presentation Portfolio Aids PDF
Persuade your audience using this public and private cloud network icon for enterprise data management ppt powerpoint presentation portfolio aids pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including public and private cloud network for securing data stored from various source icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
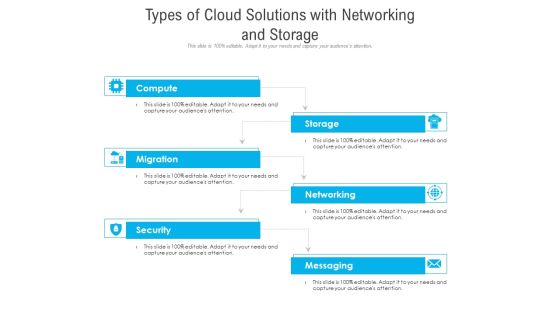
Types Of Cloud Solutions With Networking And Storage Ppt PowerPoint Presentation Outline Shapes PDF
Persuade your audience using this types of cloud solutions with networking and storage ppt powerpoint presentation outline shapes pdf. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including compute, migration, security, storage, networking, messaging. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
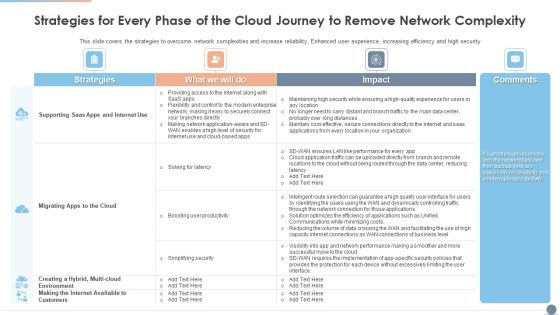
Strategies For Every Phase Of The Cloud Journey To Remove Network Complexity Graphics PDF
This slide covers the strategies to overcome network complexities and increase reliability, Enhanced user experience, increasing efficiency and high security Deliver and pitch your topic in the best possible manner with this Strategies For Every Phase Of The Cloud Journey To Remove Network Complexity Graphics PDF. Use them to share invaluable insights on Environment, Strategies, Productivity and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Professional Data Certification Program Cisco Certified Network Professional CCNP Training Courses Professional PDF
This slide covers Cisco Certified Network Professional CCNP training courses such CCNA, specialist, CNP and CCIE. Presenting IT Professional Data Certification Program Cisco Certified Network Professional CCNP Training Courses Professional PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Security, Enterprise, Service Provider. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Breaking Up Of Network Into Zones Managing Organizational Transformation Pictures PDF
This slide covers breaking of internal networks up into autonomous zones according to the risks faced by company. Deliver and pitch your topic in the best possible manner with this Breaking Up Of Network Into Zones Managing Organizational Transformation Pictures PDF. Use them to share invaluable insights on Antivirus Malware, Virtualization Security, Encryption and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Strategies For Every Phase Of The Cloud Journey To Remove Network Complexity Brochure PDF
This slide covers the strategies to overcome network complexities and increase reliability, Enhanced user experience, increasing efficiency and high security.Find a pre-designed and impeccable Strategies For Every Phase Of The Cloud Journey To Remove Network Complexity Brochure PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
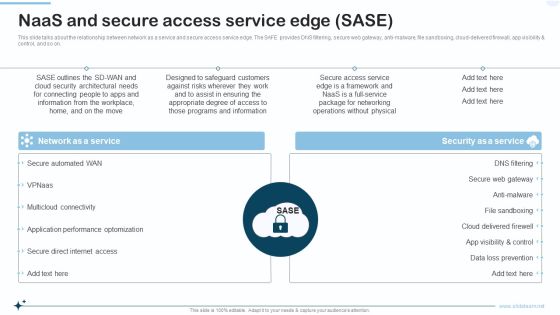
Naas Integrated Solution IT Naas And Secure Access Service Edge SASE Designs PDF
This slide talks about the relationship between network as a service and secure access service edge. The SAFE provides DNS filtering, secure web gateway, anti malware, file sandboxing, cloud delivered firewall, app visibility and control, and so on. Presenting Naas Integrated Solution IT Naas And Secure Access Service Edge SASE Designs PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Network As A Service, Security As A Service. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Deploying SDN System What Role Does SDN Play In Customer Security Structure PDF
This slide represents the role of software-defined networking in customer security. It allows clients to have separate settings for each type of network traffic and permits a low-security public-facing network for regular information. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Deploying SDN System What Role Does SDN Play In Customer Security Structure PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Deploying SDN System What Role Does SDN Play In Customer Security Structure PDF.

What Role Does SDN Play In Customer Security Ppt Outline Portrait PDF
This slide represents the role of software-defined networking in customer security. It allows clients to have separate settings for each type of network traffic and permits a low-security public-facing network for regular information. Do you know about Slidesgeeks What Role Does SDN Play In Customer Security Ppt Outline Portrait PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
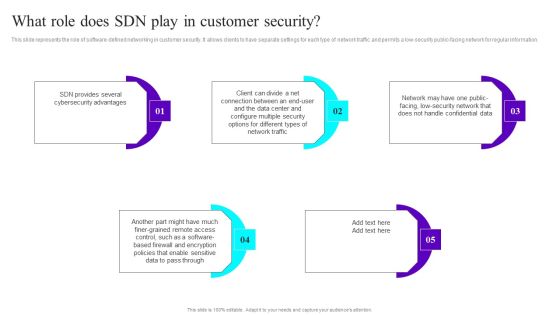
What Role Does SDN Play In Customer Security Ppt Infographic Template Slides PDF
This slide represents the role of software-defined networking in customer security. It allows clients to have separate settings for each type of network traffic and permits a low-security public-facing network for regular information. Do you know about Slidesgeeks What Role Does SDN Play In Customer Security Ppt Infographic Template Slides PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

Companys Data Safety Recognition Impact Of Security Awareness Training Demonstration PDF
This slide covers the good impact of security awareness program such as declining in the number of security threats which are phishing, network intrusion, inadvertent disclosure, stolen or lost devices or records and system misconfiguration. Deliver an awe-inspiring pitch with this creative companys data safety recognition impact of security awareness training demonstration pdf bundle. Topics like system misconfiguration, inadvertent disclosure, network intrusion can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Real Time Assessment Of Security Threats SIEM Logging Sources Infographics PDF
This slide covers the logging sources for SIEM which uses different devices such as security, network, servers, and applications. This is a real time assessment of security threats siem logging sources infographics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security devices, network devices, servers, applications. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Information And Event Management Strategies For Financial Audit And Compliance SIEM Logging Sources Mockup PDF
This slide covers the logging sources for SIEM which uses different devices such as security, network, servers, and applications. Presenting security information and event management strategies for financial audit and compliance siem logging sources mockup pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security devices, network devices, applications, servers. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Network Growth Plan With Identify Future Needs Ppt PowerPoint Presentation Gallery Format
Presenting this set of slides with name network growth plan with identify future needs ppt powerpoint presentation gallery format. This is a six stage process. The stages in this process are identify future needs, train support staff, have backout strategy, roll out strategy, notify end user, make secure upgradation process. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Network Upgrade Plan With Roll Out Strategy Ppt PowerPoint Presentation File Design Inspiration
Presenting this set of slides with name network upgrade plan with roll out strategy ppt powerpoint presentation file design inspiration. This is a six stage process. The stages in this process are identify future needs, train support staff, have backout strategy, roll out strategy, notify end user, make secure upgradation process. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cloud Network Safety Framework Ppt PowerPoint Presentation Gallery Layout Ideas PDF
This is a cloud network safety framework ppt powerpoint presentation gallery layout ideas pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security, accumulation, infrastructure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Network Safety Problems With Lock Icon Ppt PowerPoint Presentation Gallery Samples PDF
Presenting cloud network safety problems with lock icon ppt powerpoint presentation gallery samples pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like security, environments, vulnerabilities. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Block Chain Network With Distributed Ledgers Ppt PowerPoint Presentation File Layouts PDF
Persuade your audience using this block chain network with distributed ledgers ppt powerpoint presentation file layouts pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including security, decentralized, technology. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

5G Network Technology Determine Identity And Access Management With 5G Contd Ppt Outline Background PDF
This slide provides details regarding identity and access management with 5G in terms of 5G authentication. Deliver an awe inspiring pitch with this creative 5g network technology determine identity and access management with 5g contd ppt outline background pdf bundle. Topics like security, develop, infrastructure, protocol can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

5G Network Technology Determine Competitive Landscape Of 5G Ppt Summary Visual Aids PDF
This slide provides details regarding competitive landscape of 5G along with other technologies in terms of latency, mobility, coverage and bandwidth. Deliver and pitch your topic in the best possible manner with this 5g network technology determine competitive landscape of 5g ppt summary visual aids pdf. Use them to share invaluable insights on latency, mobility, coverage, bandwidth, security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
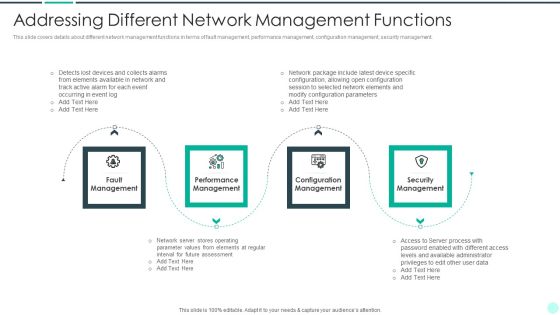
Executing Advance Data Analytics At Workspace Addressing Different Network Clipart PDF
This slide provides information regarding the various business intelligence solution by analyzing on various parameters such as hybrid cloud, data value maximization, secure infrastructure, etc. with cost. Deliver and pitch your topic in the best possible manner with this executing advance data analytics at workspace addressing different network clipart pdf. Use them to share invaluable insights on addressing business intelligence infrastructure solutions with cost and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Determine Competitive Landscape Of 5G 5G Network Architecture Instructions Information PDF
This slide provides details regarding competitive landscape of 5G along with other technologies in terms of latency, mobility, coverage and bandwidth. Deliver an awe inspiring pitch with this creative Determine Competitive Landscape Of 5G 5G Network Architecture Instructions Information PDF bundle. Topics like Bandwidth, Coverage, Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

 Home
Home