Cybersecurity

Data Wiper Spyware Attack For The First Time In History Anyone Can Join A War Clipart PDF
This slide represents the official announcement from Lotem Finkelstein, head of threat intelligence at Check Point Software, that anyone can join Ukraine and Russia cyber warfare.This is a data wiper spyware attack for the first time in history anyone can join a war clipart pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like global digital volunteers, connected to the ukraine russia, official from check You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Global Cyber Terrorism Incidents On The Rise IT Managing Cyber Terrorism 60 Days Plan Professional PDF
This slide depicts the plan for the next 60 days after the firm has implemented the cyber security model to tackle cyber terrorism. Deliver an awe inspiring pitch with this creative global cyber terrorism incidents on the rise it managing cyber terrorism 60 days plan professional pdf bundle. Topics like time to detect an incident, policy violations, data loss incidents, infected computers can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Physical System To Enhance Concept Map Of Cyber Physical Systems Topics PDF
This slide represents the concept map of the cyber-physical system that includes feedback systems, cyber security, improved design tools, design methodology, and its applications. Present like a pro with Cyber Physical System To Enhance Concept Map Of Cyber Physical Systems Topics PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether youre in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

4 Steps For Developing IT Security Plan Professional PDF
This slide represents 4 steps for developing cyber security strategy such as understanding cyber threats, assessing cyber security maturity, determining steps to improve cyber security program and documentation. Presenting 4 Steps For Developing IT Security Plan Professional PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Documenting Cyber Security Plan, Assessing Cyber Security Maturity, Organizations. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Information Security Security Of Employees Devices Ppt Model Infographics PDF
This slide depicts that the security of employees hardware or devices is also essential while applying the cyber security model. Presenting information security security of employees devices ppt model infographics pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security of employees devices. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Computing Cyber Threat Prevention Flowchart Slides PDF
The below slide provides a cloud security framework which encourages security companies to clarify the roles played by the various cloud security stakeholders within their organization and enhance overall security compliance. Major stages are visibility, governance, resolve violation, etc. Showcasing this set of slides titled Cloud Computing Cyber Threat Prevention Flowchart Slides PDF. The topics addressed in these templates are Visibility, Governance, Resolve Violations. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Physical System To Enhance Sensing Components Of Cyber Physical Systems Pictures PDF
This slide depicts the sensing components of cyber security systems, including sensors, aggregators, actuators, and their operations and position on the architecture. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Cyber Physical System To Enhance Sensing Components Of Cyber Physical Systems Pictures PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Key Elements Of IT Security Plan Background PDF
This slide represents key elements of cyber security strategy such as cyber risk management, security regulatory and compliance, cyber transformation, cyber strategy etc. Persuade your audience using this Key Elements Of IT Security Plan Background PDF. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Strategy, Executive Cyber Dashboard, Education Training Awareness. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Security Risk Management Plan Ppt PowerPoint Presentation Complete Deck With Slides
This complete deck acts as a great communication tool. It helps you in conveying your business message with personalized sets of graphics, icons etc. Comprising a set of fifty six slides, this complete deck can help you persuade your audience. It also induces strategic thinking as it has been thoroughly researched and put together by our experts. Not only is it easily downloadable but also editable. The color, graphics, theme any component can be altered to fit your individual needs. So grab it now.

Cyber Security Administration In Organization Ppt PowerPoint Presentation Complete Deck With Slides
This complete presentation has PPT slides on wide range of topics highlighting the core areas of your business needs. It has professionally designed templates with relevant visuals and subject driven content. This presentation deck has total of sixty eight slides. Get access to the customizable templates. Our designers have created editable templates for your convenience. You can edit the colour, text and font size as per your need. You can add or delete the content if required. You are just a click to away to have this ready made presentation. Click the download button now.

Developing Cyber Security Threat Awareness Staff Training Program Ppt PowerPoint Presentation Complete Deck With Slides
Induce strategic thinking by presenting this complete deck. Enthrall your audience by deploying this thought provoking PPT deck. It can be downloaded in both standard and widescreen aspect ratios, thus making it a complete package to use and deploy. Convey your thoughts and actions using the seventy eight slides presented in this complete deck. Additionally, feel free to alter its components like color, graphics, design, etc, to create a great first impression. Grab it now by clicking on the download button below.

Best Data Security Software Awards And Recognition For Company Online Database Security Proposal Clipart PDF
Presenting this set of slides with name best data security software awards and recognition for company online database security proposal clipart pdf. This is a three stage process. The stages in this process are awarded as best cyber security service provider, awarded as global leader in cyber security service, forbes named as americas best cyber security service firm. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Prevention Of Information In House Training Schedule We Will Implement Professional PDF
The purpose of this slide is to exhibit a comprehensive cyber security awareness training plan for the stakeholders. Information covered in this slide is related to malware, social engineering attack, business email compromise, ransomware, password attack, crypto-jacking and IoT-Based attack. Make sure to capture your audiences attention in your business displays with our gratis customizable Prevention Of Information In House Training Schedule We Will Implement Professional PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Blockchain Technology Applications For Cyber Threat Prevention Icons PDF
This slides represents various application of blockchain technology in enhancing cyber safety which helps to speed up data transfer procedures, offer secure transactions, and lower compliance expenses. Key components are IoT security, secure private messaging, etc. Presenting Blockchain Technology Applications For Cyber Threat Prevention Icons PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Prevention, Infrastructure, System . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Training Frequency For Cyber Safety Awareness Program Ppt Pictures Graphics PDF
This slide covers frequency of training to be provided as per prescribed format. It includes elements such as clicking suspicious links, use of simple passwords, workstation security management, public network management, etc. as per multiple time duration. Showcasing this set of slides titled Training Frequency For Cyber Safety Awareness Program Ppt Pictures Graphics PDF. The topics addressed in these templates are Training Included, Once Per Month, Frequency Training. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

1 Icon Of A Firewall To Separate The Internal Network From The External World Ppt Slides
This image slide displays icon of firewall. This image slide has been crafted with graphic of firewall icon to separate internal network from the external world. This image slide depicts security on network. You may change size, color and orientation of any icon to your liking. Use this PowerPoint template, in your presentations to explain concepts like networking and security. This image slide will enhance the quality of your presentations.
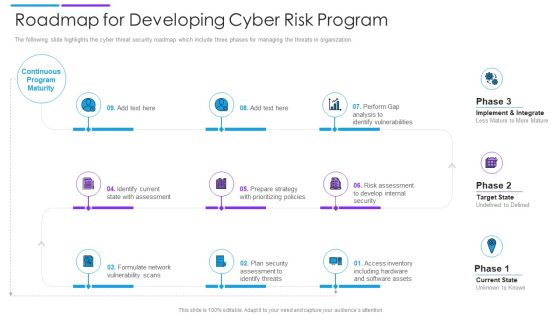
Roadmap For Developing Cyber Risk Program Download PDF
The following slide highlights the cyber threat security roadmap which include three phases for managing the threats in organization. Persuade your audience using this roadmap for developing cyber risk program download pdf. This PPT design covers nine stages, thus making it a great tool to use. It also caters to a variety of topics including internal security, software assets, identify threats. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Safety Awareness Program Plan Ppt Icon Smartart PDF
This slide covers plan related to cyber security awareness. It includes timeline pertaining to preparation, detection, analysis, eradication, recover and post incident of a security lapse. Presenting Cyber Safety Awareness Program Plan Ppt Icon Smartart PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Post Inside, Eradicate and Recover, Detection, Analysis. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Protection And Precaution Tracking Dashboard Designs PDF
This slide shows the dashboard of cyber safety and security of an organization. It includes risk level, compliance status, tracking and security budget. Showcasing this set of slides titled Cyber Protection And Precaution Tracking Dashboard Designs PDF. The topics addressed in these templates are Risk, Compliance Status, Risk Level. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

IT Cyber Threat Prevention Technology Market Topics PDF
This slide provides the statistical data for IT security software user market to help business and organizations enhance process efficiency. Major security technology are authentication, IoT, Zero trust, Cloud, application security, etc. Pitch your topic with ease and precision using this IT Cyber Threat Prevention Technology Market Topics PDF. This layout presents information on Key Insights, Progressive Rate, Technology. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Cyber Exploitation IT Budget For New Recruited Professionals Demonstration PDF
This slide represents the budget for newly recruited professionals, including new professionals, number of total posts, annual salaries, and total funding for salaries. Deliver and pitch your topic in the best possible manner with this cyber exploitation it budget for new recruited professionals demonstration pdf. Use them to share invaluable insights on it security analyst, certified ethical hacker, security consultant and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Agenda Of Enhancing Cyber Safety With Vulnerability Administratio Professional PDF
This is a agenda of enhancing cyber safety with vulnerability administratio professional pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security intelligence, log management and compliance, provides security services. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
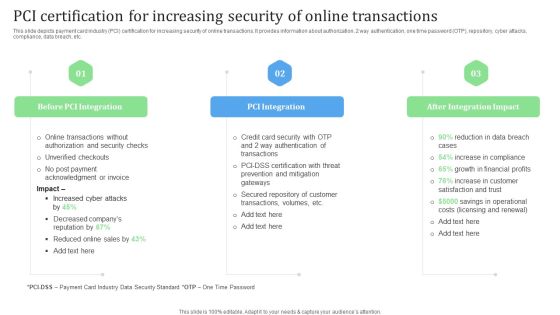
PCI Certification For Increasing Security Of Online Transactions Financial Management Strategies Ideas PDF
This slide depicts payment card industry PCI certification for increasing security of online transactions. It provides information about authorization, 2 way authentication, one time password OTP, repository, cyber attacks, compliance, data breach, etc. Slidegeeks has constructed PCI Certification For Increasing Security Of Online Transactions Financial Management Strategies Ideas PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Managing E Commerce Business Accounting Pci Certification For Increasing Security Of Online Transactions Download PDF
This slide depicts payment card industry PCI certification for increasing security of online transactions. It provides information about authorization, 2 way authentication, one time password OTP, repository, cyber attacks, compliance, data breach, etc. The Managing E Commerce Business Accounting Pci Certification For Increasing Security Of Online Transactions Download PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Aftereffects Of IT Security Threats On Business And Customers Ppt PowerPoint Presentation Layouts Background PDF
Persuade your audience using this aftereffects of it security threats on business and customers ppt powerpoint presentation layouts background pdf. This PPT design covers two stages, thus making it a great tool to use. It also caters to a variety of topics including violation of law, crucial information loss, loss of productivity, cyber espionage, risk of losing work in future, contract breach, trust among business people, ransom ware, online banking transactions are compromised, identity theft, credit card detail theft, spam mails or other attacks violates the law, fraud to customers by scare ware or other fraud tools. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Organizations Risk Management And IT Security Damage Control Assessment From IT Risk Management Demonstration PDF
This slide highlights the damage control form information technology risk management strategies which includes data breach, cyber threats, social engineering attacks, domain based threats and increase in business opportunities. This modern and well arranged Organizations Risk Management And IT Security Damage Control Assessment From IT Risk Management Demonstration PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Organizations Risk Management And IT Security Top IT Risks Reported At The Workplace Brochure PDF
This slide highlights the top IT risks reported at workplace which includes cyber threats, data loss, social engineering attacks, regulatory incidents, domain based threats and denial of service. Slidegeeks has constructed Organizations Risk Management And IT Security Top IT Risks Reported At The Workplace Brochure PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.
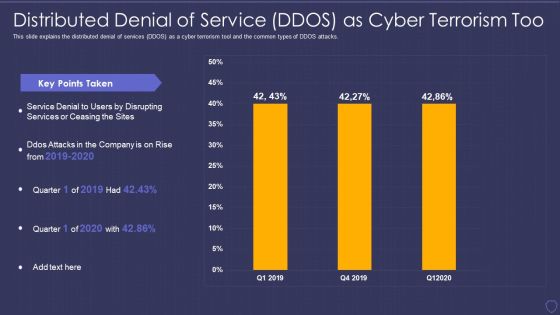
Global Cyber Terrorism Incidents On The Rise IT Distributed Denial Of Service Template PDF
This slide explains the distributed denial of services DDOS as a cyber terrorism tool and the common types of DDOS attacks. Deliver an awe inspiring pitch with this creative global cyber terrorism incidents on the rise it distributed denial of service template pdf bundle. Topics like distributed denial of service ddos as cyber terrorism too can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Three Layers Of Digital Risk Assessment Management Process Ppt Summary Visual Aids PDF
The following slide highlights the three layers of cyber security management process which are dependent on people, process and technology, it helps company to manage cyber risks such as phishing attacks, data loss and exposed vulnerabilities. Presenting Three Layers Of Digital Risk Assessment Management Process Ppt Summary Visual Aids PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including People, Process, Technology. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Technology Trends Impacting Digital Loans Ppt Summary Model PDF
This slide shows the impacts of technology trends on digital lending to enhance the customer service and simplify the process. It includes credit decision automation, personalized products, focus on cyber attacks, etc. Persuade your audience using this Technology Trends Impacting Digital Loans Ppt Summary Model PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Credit Decision Automation, Personalized Products, Focus Cyber Security . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Comprehensive Strategy To Improve Cyber Risk Prevention Graphics PDF
The slide showcases the steps for building efficient cyber resiliency across organization. It covers steps like secure remote working enablement, develop a comprehensive response plan, build a cyber security improvement roadmap, build detection and response capability and educating users on escalating threats. Pitch your topic with ease and precision using this Comprehensive Strategy To Improve Cyber Risk Prevention Graphics PDF. This layout presents information on Objective, Initiatives, Impact. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Desktop Security Management Security Of Employees Devices Microsoft PDF
This slide depicts that the security of employees hardware or devices is also essential while applying the cyber security model. Deliver an awe inspiring pitch with this creative desktop security management security of employees devices microsoft pdf bundle. Topics like security of employees devices can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Desktop Security Management Roadmap For Computer Security Training Graphics PDF
This slide depicts the cyber security training roadmap. It also shows the plan and guidelines to conduct an effective training program. Presenting desktop security management roadmap for computer security training graphics pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like information, security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Desktop Security Management Compliance Dashboard Of Computer Security Graphics PDF
This slide depicts the cyber security compliance report on how data and hardware are monitored in different categories such as standard, regulation, and asset type control. Deliver an awe inspiring pitch with this creative desktop security management compliance dashboard of computer security graphics pdf bundle. Topics like compliance dashboard of computer security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Safety Incident Management Statistics Associated To Workplace Threats Elements PDF
This slide provides details regarding statistics associated to workplace threats that firms face in terms of data records theft, workplace violence, financial phishing, etc. Deliver and pitch your topic in the best possible manner with this cyber safety incident management statistics associated to workplace threats elements pdf. Use them to share invaluable insights on cyber attacks costs, organizations, organizations have, organizations face, data records and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Terrorism Assault Average Loss To Firms In European Countries Slides PDF
This slide depicts the average loss to firms in European countries, representing Germany as the most affected country. Deliver and pitch your topic in the best possible manner with this cyber terrorism assault average loss to firms in european countries slides pdf Use them to share invaluable insights on German businesses, average loss , cyber terrorist attack and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information IT Security Communication Plan Guidelines PDF
This slide showcases an information cyber security communication plan to effectively communicate cyber incident and action plan. It includes cyber incidents such as virus, spyware, firewall hacking and phishing. Showcasing this set of slides titled Information IT Security Communication Plan Guidelines PDF. The topics addressed in these templates are Run Microsoft Defender Offline, Install Antivirus, Block Traffic Default. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
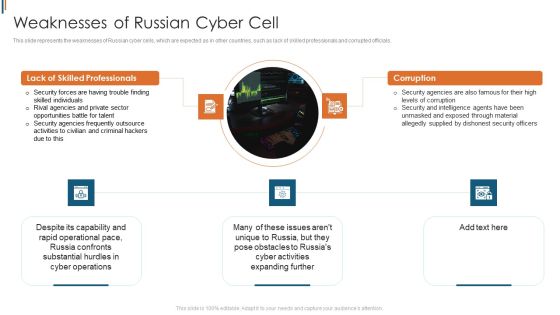
Ukraine Cyberwarfare Weaknesses Of Russian Cyber Cell Brochure Pdf
This slide represents the weaknesses of Russian cyber cells, which are expected as in other countries, such as lack of skilled professionals and corrupted officials. Presenting ukraine cyberwarfare weaknesses of russian cyber cell brochure pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like security forces are having trouble finding skilled individuals, rival agencies and private sector opportunities battle for talent, security agencies frequently outsource activities to civilian and criminal hackers due to this. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Safety Awareness Program Services Platform Ppt Show Information PDF
This slide covers platform for providing security awareness training services to clients. It includes elements such as platforms comprising of security awareness training content, phishing case studies, quarterly cyber awareness training, human based testing, monthly incident reporting, etc. Showcasing this set of slides titled Cyber Safety Awareness Program Services Platform Ppt Show Information PDF. The topics addressed in these templates are Platforms, Development, Core Self Managed. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
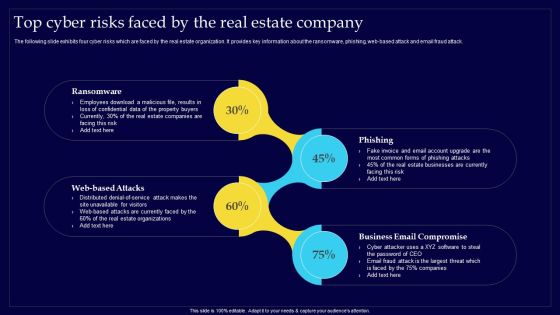
Executing Risk Mitigation Top Cyber Risks Faced By The Real Estate Company Structure PDF
The following slide exhibits four cyber risks which are faced by the real estate organization. It provides key information about the ransomware, phishing, web-based attack and email fraud attack. Retrieve professionally designed Executing Risk Mitigation Top Cyber Risks Faced By The Real Estate Company Structure PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Top Cyber Risks Faced By The Real Estate Company Enhancing Process Improvement By Regularly Information PDF
The following slide exhibits four cyber risks which are faced by the real estate organization. It provides key information about the ransomware, phishing, web-based attack and email fraud attack. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Top Cyber Risks Faced By The Real Estate Company Enhancing Process Improvement By Regularly Information PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Successful Risk Administration Top Cyber Risks Faced By The Real Estate Company Pictures PDF
The following slide exhibits four cyber risks which are faced by the real estate organization. It provides key information about the ransomware, phishing, web-based attack and email fraud attack. The Successful Risk Administration Top Cyber Risks Faced By The Real Estate Company Pictures PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Cyber Physical Systems In Water Distribution Systems Ppt PowerPoint Presentation File Backgrounds PDF
This slide represents the application of CPS in water distribution systems, including the tools such as the Attack Model and Toolbox to protect the system from attacks. Welcome to our selection of the Cyber Physical Systems In Water Distribution Systems Ppt PowerPoint Presentation File Backgrounds PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

Table Of Contents For Cyber Intelligent Computing System Infographics PDF
Deliver an awe inspiring pitch with this creative Table Of Contents For Cyber Intelligent Computing System Infographics PDF bundle. Topics like Systems Development, Systems Implementation, Security Strategy Plan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Distribution Network Features Of Content Delivery Network Elements PDF
This slide explains the features of content delivery networks such as protection against DDoS protection, HTTPS services, analytics, etc. Presenting Distribution Network Features Of Content Delivery Network Elements PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Service, Analytics, Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Ukraine Cyberwarfare International Cyber Aid To Ukraine Brochure Pdf
This slide describes the international cyber assistance to Ukraine by 6 European Union nations such as Lithuania, the Netherlands, Poland, Estonia, Romania, and Croatia. This is a ukraine cyberwarfare international cyber aid to ukraine brochure pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like ukraine is in grave danger, australia has also announced that it will teach ukrainian officials on cyber security, australia has also pledged to help the ukrainian government with cyber security through a bilateral cyber policy dialogue. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Telecommunications Technology Network Diagram Powerpoint Slides
This is a telecommunications technology network diagram powerpoint slides. This is a five stage process. The stages in this process are satellite, computer, provider, network security, wireless access.

Communication Plan For Cyber Breaches Ppt Layouts Ideas PDF
Mentioned slide portrays communication plan that company will use for effectively managing cyber breaches. Sections covered here are what to communicate, description, delivery method, frequency and responsible. Deliver an awe inspiring pitch with this creative communication plan for cyber breaches ppt layouts ideas pdf bundle. Topics like potential security, development process, method can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Exploitation IT Dashboard For Threat Tracking Topics PDF
This slide depicts the dashboard for threat tracking through cyber security measures and ethical hackers by covering monthly threat status, current risk status, threat-based on the role, threats by owners, risk by threats, and threat report. Deliver an awe inspiring pitch with this creative cyber exploitation it dashboard for threat tracking topics pdf bundle. Topics like dashboard for threat tracking can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Comparison Of Various Cyber Protection Software Portrait PDF
This slide shows comparative analysis of various cyber protection tools which can be used by organizations for IT safety. It includes features, compatibility, price and ratings. Pitch your topic with ease and precision using this Comparison Of Various Cyber Protection Software Portrait PDF. This layout presents information on Compatibility, Price, Security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Business Information Cyber Protection Program For Threat Prevention Background PDF
This slide covers business cyber security program for threat prevention which includes identify, protect, detect, respond and recover.Showcasing this set of slides titled Business Information Cyber Protection Program For Threat Prevention Background PDF. The topics addressed in these templates are Business Environment, Administrative Governance, Evaluating Risk. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Risk Mitigating Business Information Cyber Protection Strategies Themes PDF
This slide covers risk mitigating business cyber security strategies which are training employees, installing spyware, backup data and privileged access.Presenting Risk Mitigating Business Information Cyber Protection Strategies Themes PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Train Employees, Information Business, Related Activities. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cloud Security Assessment Key Cloud Security Use Cases Diagrams PDF
This slide represents the key use cases of cloud security namely privileged account access, data exfiltration, suspicious network connections, man-in-the-cloud attack, and unsecured storage containers.Deliver and pitch your topic in the best possible manner with this Cloud Security Assessment Key Cloud Security Use Cases Diagrams PDF Use them to share invaluable insights on Account Access, Data Exfiltration, Network Connections and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Security Architecture Ppt Infographic Template
This is a security architecture ppt infographic template. This is a five stage process. The stages in this process are networking segmentation, application classification, asset classification, asset inventory, security architecture.

Market Sizing Key Statistics Ppt Infographic Template Design Templates PDF
Presenting this set of slides with name market sizing key statistics ppt infographic template design templates pdf. This is a one stage process. The stages in this process are users dont protect their devices, of connected devices store personal information, of devices are vulnerable to security, of cyber attacks are unnoticed. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

TAM SAM And SOM Key Statistics Ppt Inspiration Maker PDF
Presenting tam sam and som key statistics ppt inspiration maker pdf to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like users dont protect their devices, of connected devices store personal information, of devices are vulnerable to security, of cyber attacks are unnoticed. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
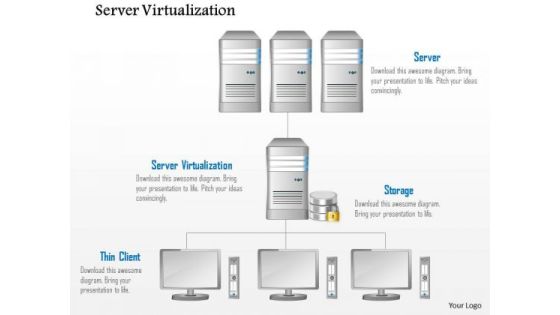
Business Diagram Server Virtulization Thin Client Storage And Database Ppt Slide
This image slide displays network of servers. This image slide has been designed with graphic of server workstation with concepts of server virtualization storage and thin client. This image slide will enhance the quality of your presentations.

Real Time Assessment Of Security Threats Security Intelligence Services Formats PDF
This slide covers the security intelligence services such as cyber threat intelligence, incident and response management, cyber analytics, vulnerability management, etc. Presenting real time assessment of security threats security intelligence services formats pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like incident response and management, cyber analytics, vulnerability management, infrastructure management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Strategies To Mitigate Cyber Security Risks Backup Maintenance Selecting Offsite Storage Facility Vendor Ppt Model Graphic Images PDF
Presenting this set of slides with name strategies to mitigate cyber security risks backup maintenance selecting offsite storage facility vendor ppt model graphic images pdf. This is a five stage process. The stages in this process are geographic location, accessibility, security, cost, operational fees, environment. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Milestone Roadmap Of A Cyber Security Company With Key Dates Ppt PowerPoint Presentation File Design Templates PDF
This slide signifies cyber security roadmap of an organization with seven millstone achieved within 4 year timeline. Persuade your audience using this Milestone Roadmap Of A Cyber Security Company With Key Dates Ppt PowerPoint Presentation File Design Templates PDF. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including Security Assessment Team, Identify Digital Assets, Provide Access Control. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
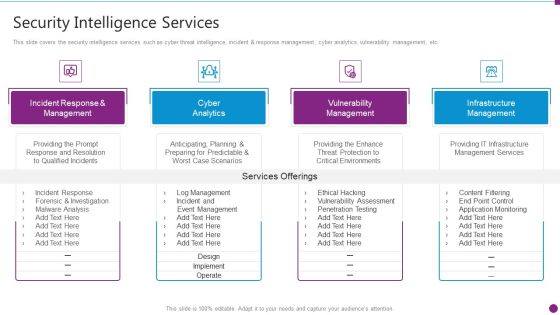
Security Information And Event Management Strategies For Financial Audit And Compliance Security Intelligence Services Graphics PDF
This slide covers the security intelligence services such as cyber threat intelligence, incident and response management, cyber analytics, vulnerability management, etc. This is a security information and event management strategies for financial audit and compliance siem architecture topics pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like incident response and management, cyber analytics, vulnerability management, infrastructure management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Customer Server Network Design Structure Model Ppt PowerPoint Presentation Gallery Graphics PDF
Presenting this set of slides with name customer server network design structure model ppt powerpoint presentation gallery graphics pdf. This is a one stage process. The stages in this process are central data base, data and information, internet, control switch, providing connection to server, common control switch, wireless access point server, providing internet medium, security firewall acting, threat and viruses. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Stock Photo Ball With Big Data Text For Data Protection Concept PowerPoint Slide
Graphic of ball with big data text has been used to craft this power point template. This image template contains the concept of data protection. Use this image for data security related topics in any presentation.

Cyber Strategies For KPMG For Client Data Protection Pictures PDF
This slide covers techniques to secure customers confidential data through several cyber security strategies. The purpose for this template is to provide an overview on important elements of top techniques deployed by the company . It includes strategies such as people, process, data and technology and regulatory. Boost your pitch with our creative Cyber Strategies For KPMG For Client Data Protection Pictures PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Cyber Exploitation IT Purpose Of Ethical Hacking Portrait PDF
This slide depicts the purpose of ethical hacking, including the tools and tactics they use and their responsibility to report the discovered vulnerabilities to the authorities. Deliver an awe inspiring pitch with this creative cyber exploitation it purpose of ethical hacking portrait pdf bundle. Topics like vulnerabilities, management, process, weaknesses, security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Exploitation IT Reputational Damage Due To Cyberattacks Professional PDF
This slide represents the reputational damage caused by continuous cyberattacks faced by the company in recent years and the fall of the company in the stock market. Deliver an awe inspiring pitch with this creative cyber exploitation it reputational damage due to cyberattacks professional pdf bundle. Topics like continuous, developed, security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Table Of Contents Cyber Safety Incident Management Formats PDF
Presenting table of contents cyber safety incident management formats pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like ensuring financial assets security, leveraging workforce, budget assessment, impact assessment, dashboard . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Safety Awareness Course Program List Ppt Infographics Shapes PDF
This slide covers list of programs available for increasing security awareness. It includes elements such as programs included for three levels covering essential, advanced and enterprise related services. Showcasing this set of slides titled Cyber Safety Awareness Course Program List Ppt Infographics Shapes PDF. The topics addressed in these templates are Programs, Essentials, Advanced. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Security Operations Application To Enhance Security Compliance Rules PDF
This slide shows a SecOps application that allows an organization to scale its security solution to meet its business needs and respond to the specific cyber threats they face. It includes security incident response, vulnerability response, configuration compliance, and threat intelligence. Persuade your audience using this Security Operations Application To Enhance Security Compliance Rules PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Configuration Compliance, Threat Intelligence, Vulnerability Response. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Workforce Security Realization Coaching Plan The ROI Of Security Awareness Training Pictures PDF
This slide covers the security awareness rate of interest calculations including typical cyber risk management factor for a trained, cyber-conscious workforce. Deliver and pitch your topic in the best possible manner with this workforce security realization coaching plan the roi of security awareness training pictures pdf. Use them to share invaluable insights on security awareness training and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
The Roi Of Security Awareness Training Hacking Prevention Awareness Training For IT Security Icons PDF
This slide covers the security awareness rate of interest calculations including typical cyber risk management factor for a trained, cyber-conscious workforce. Deliver and pitch your topic in the best possible manner with this the roi of security awareness training hacking prevention awareness training for it security icons pdf. Use them to share invaluable insights on organizations, training, security, costs and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Outliers Model For Predictive Analytics Forward Looking Analysis IT Mockup PDF
This slide talks about the outliers model used for predictive analytics, including its use cases, impact and algorithm used in it, such as the generalized linear model for two values. This model helps banking, finance, and cyber security organizations to detect fraud and cyber crimes.Whether you have daily or monthly meetings, a brilliant presentation is necessary. Outliers Model For Predictive Analytics Forward Looking Analysis IT Mockup PDF can be your best option for delivering a presentation. Represent everything in detail using Outliers Model For Predictive Analytics Forward Looking Analysis IT Mockup PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Forecast Analysis Technique IT Outliers Model For Predictive Modeling Elements PDF
This slide talks about the outliers model used for predictive analytics, including its use cases, impact and algorithm used in it, such as the generalized linear model for two values. This model helps banking, finance, and cyber security organizations to detect fraud and cyber crimes. Slidegeeks is here to make your presentations a breeze with Forecast Analysis Technique IT Outliers Model For Predictive Modeling Elements PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Predictive Analytics In The Age Of Big Data Outliers Model For Predictive Analytics Demonstration PDF
This slide talks about the outliers model used for predictive analytics, including its use cases, impact and algorithm used in it, such as the generalized linear model for two values. This model helps banking, finance, and cyber security organizations to detect fraud and cyber crimes. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Predictive Analytics In The Age Of Big Data Outliers Model For Predictive Analytics Demonstration PDF can be your best option for delivering a presentation. Represent everything in detail using Predictive Analytics In The Age Of Big Data Outliers Model For Predictive Analytics Demonstration PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
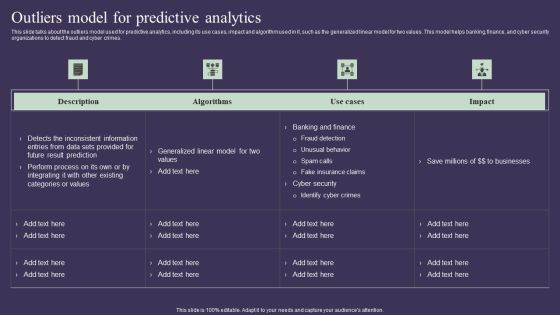
Projection Model Outliers Model For Predictive Analytics Topics PDF
This slide talks about the outliers model used for predictive analytics, including its use cases, impact and algorithm used in it, such as the generalized linear model for two values. This model helps banking, finance, and cyber security organizations to detect fraud and cyber crimes. Welcome to our selection of the Projection Model Outliers Model For Predictive Analytics Topics PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today

IT Threats Response Playbook Identifying The Origin And Type Of Cyber Incident Rules PDF
Following slide portrays information about the cyber incident source of origin, their description and type. Members can use this slide to effectively identify the source and type of any cyber attack.This is a IT Threats Response Playbook Identifying The Origin And Type Of Cyber Incident Rules PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like External Removable, Malicious Attachment, Loss Valuable. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Safety Breach Response Playbook Identifying The Origin And Type Of Cyber Incident Structure PDF
Following slide portrays information about the cyber incident source of origin, their description and type. Members can use this slide to effectively identify the source and type of any cyber attack. Want to ace your presentation in front of a live audience Our Safety Breach Response Playbook Identifying The Origin And Type Of Cyber Incident Structure PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

Desktop Security Management Elements Of Computer Security Operational Security Themes PDF
This slide defines the operational security element of cyber security. It also shows the best practices for operational security such as change management processes, deploys automation, etc. This is a desktop security management elements of computer security operational security themes pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like management, resources, require, security, plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
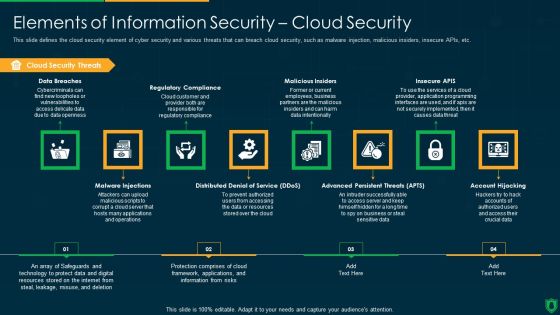
Info Security Elements Of Information Security Cloud Security Ppt PowerPoint Presentation Gallery Graphics Download PDF
This slide defines the cloud security element of cyber security and various threats that can breach cloud security, such as malware injection, malicious insiders, insecure APIs, etc. Presenting info security elements of information security cloud security ppt powerpoint presentation gallery graphics download pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like cloud security threats, regulatory compliance, malicious insiders, insecure apis. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Multiple Challenges Of Business Cyber Threat Prevention Sample PDF
The following slide represent the statistical data of various cyber safety challenges reported by business and organizations which helps to determine the most vulnerable one. Major areas are information security, business agility, automation, integration, etc. Showcasing this set of slides titled Multiple Challenges Of Business Cyber Threat Prevention Sample PDF. The topics addressed in these templates are Key Takeaways, Cyber Safety, Prevention. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
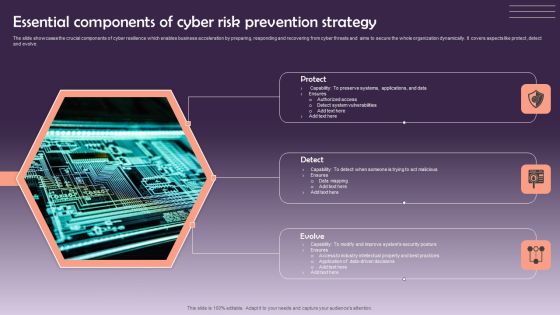
Essential Components Of Cyber Risk Prevention Strategy Information PDF
The slide showcases the crucial components of cyber resilience which enables business acceleration by preparing, responding and recovering from cyber threats and aims to secure the whole organization dynamically. It covers aspects like protect ,detect and evolve. Presenting Essential Components Of Cyber Risk Prevention Strategy Information PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Protect, Detect, Evolve. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cost Breakdown Multiple Points Incurred On Cyber Security System Of Failures Ppt PowerPoint Presentation Visual Aids Portfolio PDF
This slide depicts different points leading to failures to set up an effective security system. It includes the cost borne by company due to failures in log management, communication over unauthorized ports, asset inventory, failures of anti-malware software, etc.Showcasing this set of slides titled Cost Breakdown Multiple Points Incurred On Cyber Security System Of Failures Ppt PowerPoint Presentation Visual Aids Portfolio PDF. The topics addressed in these templates are Management Failures, Irregular Penetration, Expense Borne. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Cyber Security Cases Action Plan Risk Tracking Dashboard For Response Ppt PowerPoint Presentation File Graphics Example PDF
This slide highlights dashboard to identify and track security threats occurred in the company. The purpose of this template is to provide information to the management about severities of the incidents along with risk rating in form of heat map. Showcasing this set of slides titled Cyber Security Cases Action Plan Risk Tracking Dashboard For Response Ppt PowerPoint Presentation File Graphics Example PDF. The topics addressed in these templates are Risk Heat Map, Action Plan Breakdown, Risk Rating Breakdown. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

1 Network Diagram Showing Disaster Recovery To Remote Location Dr Ppt Slides
This image slide displays network diagram showing disaster recovery to remote locations. This image slide has been designed with graphic of cloud connected to various technology devices and database. This image slide depicts networking. You may change size, color and orientation of any icon to your liking. This image may be used to explain concepts of database recovery through cloud computing. Use this PowerPoint template to express views on cloud computing, networking and security in your presentations. This image slide will enhance the quality of your presentations.

Desktop Security Management Elements Of Computer Security Cloud Security Diagrams PDF
This slide defines the cloud security element of cyber security and various threats that can breach cloud security, such as malware injection, malicious insiders, insecure APIs, etc. This is a desktop security management elements of computer security cloud security diagrams pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like applications, service. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Elements Of Information Technology Security Cloud Security Ppt Outline Background Images PDF
This slide defines the cloud security element of cyber security and various threats that can breach cloud security, such as malware injection, malicious insiders, insecure APIs, etc. This is a it security elements of information technology security cloud security ppt outline background images pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like data breaches, malware injections, malicious insiders, account hijacking, distributed denial of service. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Elements Of Information Technology Security Operational Security Ppt Professional Format Ideas PDF
This slide defines the operational security element of cyber security. It also shows the best practices for operational security such as change management processes, deploys automation, etc. This is a it security elements of information technology security operational security ppt professional format ideas pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like change management processes, deploy automation, plan for disaster, restrict device access, implement dual control. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
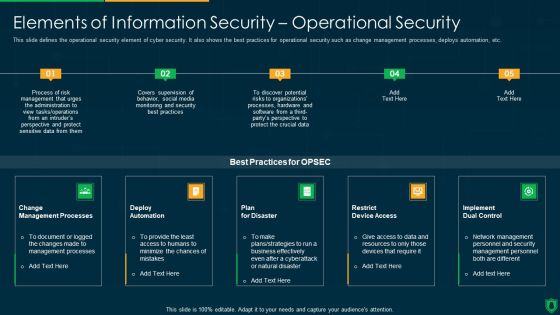
Info Security Elements Of Information Security Operational Security Ppt PowerPoint Presentation File Backgrounds PDF
This slide defines the operational security element of cyber security. It also shows the best practices for operational security such as change management processes, deploys automation, etc. This is a info security elements of information security operational security ppt powerpoint presentation file backgrounds pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like change management processes, deploy automation, plan for disaster, implement dual control. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Global Cyber Terrorism Incidents On The Rise IT Checklist To Deal With Cyber Terrorism Threats Key Template PDF
This slide represents the checklist to deal with cyber-terrorism threats which involve 24 7 monitoring, employee training, keeping software updated. Presenting global cyber terrorism incidents on the rise it checklist to deal with cyber terrorism threats key template pdf to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like employee training, monitoring, cyber security assessment, incident response plan, limited access privileges. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Global Cyber Terrorism Incidents On The Rise IT Checklist To Deal With Cyber Terrorism Threats Infographics PDF
This slide represents the checklist to deal with cyber-terrorism threats which involve 24 7 monitoring, employee training, keeping software updated. This is a global cyber terrorism incidents on the rise it checklist to deal with cyber terrorism threats infographics pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employee training, monitoring, cyber security assessment, incident response plan, limited access privileges. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Assessment Essential Pillars Of Cloud Security Clipart PDF
This slide shows the four essential pillars of cloud security, namely visibility and consistency, process based security, network security, and identity security.Presenting Cloud Security Assessment Essential Pillars Of Cloud Security Clipart PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Visibility And Consistency, Network Security, Identity Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information And Cyber Data Safety Risk Management Plan Summary PDF
Mentioned slide showcase information security risk management plan. The template provides information about various risks such as DDoS, crypto jacking, malware and password theft and with other details like degree of risk involved, impact, strategies to be deployed. Showcasing this set of slides titled information and cyber data safety risk management plan summary pdf. The topics addressed in these templates are information and cyber data safety risk management plan. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Intelligence Risk Assessment Dashboard With Heat Map Portrait PDF
This slide exhibits risk rating breakdown and heat map for analyzing current cyber security measures effectiveness. It covers top 5 vulnerabilities and clients under scrutiny. Pitch your topic with ease and precision using this Cyber Intelligence Risk Assessment Dashboard With Heat Map Portrait PDF This layout presents information on Risk Rating Breakdown, Action Plan Breakdown, Risk Possibility It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Cyber Safety Awareness Training Program Ppt Layouts Infographic Template PDF
This slide covers training program based on cyber security in an organization. It includes elements such as department, training topics, certifications involved and learning methods to be used and total training hours required. Showcasing this set of slides titled Cyber Safety Awareness Training Program Ppt Layouts Infographic Template PDF. The topics addressed in these templates are Department, Training, Certifications. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Five Step Procedure Of Cyber Threat Hunting Introduction PDF
This slide shows steps for effective and successful cyber security systems to prevent from threats.it contains steps hypothesis, process data, trigger, investigation and resolution. Persuade your audience using this Five Step Procedure Of Cyber Threat Hunting Introduction PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Prepare Detailed, Management Software, Management Software. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Information Security Risk Management Form Guidelines PDF
This slide shows information security risk acceptance form which contains accountable person details, risk acceptance summary, acceptance advantages, justification, advice, etc. This can benefit cyber security department in careful review prior to the acceptance of major risks involved. Pitch your topic with ease and precision using this Information Security Risk Management Form Guidelines PDF. This layout presents information on Risk Modification, Risk Acceptance, Cyber Security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Global Cyber Terrorism Incidents On The Rise IT Confidential Data Should Be Backup Structure PDF
This slide emphasizes the significance of backing up private data, which enables for data recovery in the event of an attack. Presenting global cyber terrorism incidents on the rise it confidential data should be backup structure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like confidential data should be backup. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Global Cyber Terrorism Incidents On The Rise IT Financial Loss Faced By The Business Designs PDF
This slide depicts the average financial loss faced by the business when projects of different scales are attacked. This is a global cyber terrorism incidents on the rise it financial loss faced by the business designs pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like targeted, revenue, financial. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Exploitation IT Regaining Reputation Of Our Company Demonstration PDF
This slide describes the regaining companys reputation through regaining customers trust by showcasing the companys new security policies and strategies. This is a cyber exploitation it regaining reputation of our company demonstration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like regaining reputation of our company. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Best Practices To Manage Cyber Protection Of Organization Microsoft PDF
This slide shows various practices which can be used to by organizations to manage information technology protection. These practices are monitor, risk plan, protection protocols and use technology. Persuade your audience using this Best Practices To Manage Cyber Protection Of Organization Microsoft PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Risk Plan, Security Protocols, Technology. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Three Types Of Computer Security Designs PDF
This slide shows the various types of information technology security. It includes network, end point and internet security. Presenting Three Types Of Computer Security Designs PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Network Security, Point Security, Internet Security This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Locked Laptop Computer Security Concept PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Locked Laptop Computer Security Concept PowerPoint Templates PPT Backgrounds For Slides 0113.Download and present our Computer PowerPoint Templates because It will get your audience in sync. Use our Technology PowerPoint Templates because You can Connect the dots. Fan expectations as the whole picture emerges. Present our Business PowerPoint Templates because You can Channelise the thoughts of your team with our PowerPoint Templates and Slides. Urge them to focus on the goals you have set. Present our Security PowerPoint Templates because It will Strengthen your hand with your thoughts. They have all the aces you need to win the day. Use our Services PowerPoint Templates because You will get more than you ever bargained for. Use these PowerPoint slides for presentations relating to Internet cyber laptop computer security lock, services, security, business, computer, technology. The prominent colors used in the PowerPoint template are Blue, Yellow, Gray. PowerPoint presentation experts tell us our Locked Laptop Computer Security Concept PowerPoint Templates PPT Backgrounds For Slides 0113 are second to none. People tell us our services PowerPoint templates and PPT Slides are aesthetically designed to attract attention. We guarantee that they will grab all the eyeballs you need. Presenters tell us our Locked Laptop Computer Security Concept PowerPoint Templates PPT Backgrounds For Slides 0113 will impress their bosses and teams. The feedback we get is that our laptop PowerPoint templates and PPT Slides will make the presenter look like a pro even if they are not computer savvy. Customers tell us our Locked Laptop Computer Security Concept PowerPoint Templates PPT Backgrounds For Slides 0113 are topically designed to provide an attractive backdrop to any subject. People tell us our security PowerPoint templates and PPT Slides effectively help you save your valuable time.
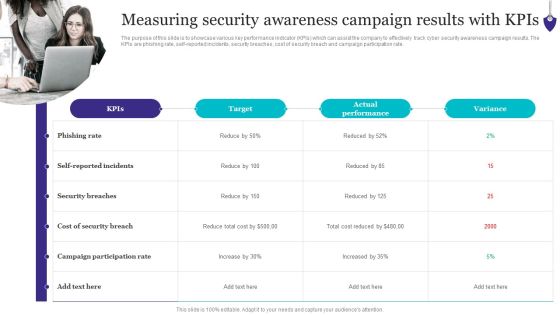
Organizing Security Awareness Measuring Security Awareness Campaign Results Download PDF
The purpose of this slide is to showcase various key performance indicator KPIs which can assist the company to effectively track cyber security awareness campaign results. The KPIs are phishing rate, self-reported incidents, security breaches, cost of security breach and campaign participation rate. Explore a selection of the finest Organizing Security Awareness Measuring Security Awareness Campaign Results Download PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Organizing Security Awareness Measuring Security Awareness Campaign Results Download PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
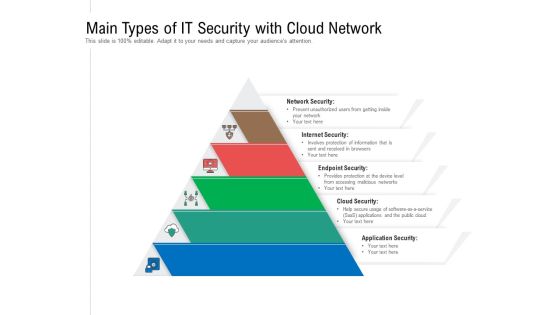
Main Types Of IT Security With Cloud Network Ppt PowerPoint Presentation Gallery Design Ideas PDF
Persuade your audience using this main types of it security with cloud network ppt powerpoint presentation gallery design ideas pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including network security, internet security, endpoint security, cloud security, application security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Our Strategies To Secure Network Load Balancer Ppt Outline Topics PDF
This slide represents the strategies to secure the network load balancer by protecting servers at the physical level, controlling network traffic, security app features, and more. Presenting our strategies to secure network load balancer ppt outline topics pdf to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like our strategies to secure network load balancer. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Organizing Security Awareness Comparative Assessment Of Security Awareness Clipart PDF
The purpose of this slide is to showcase comparison of various advance cyber security training courses. The comparison is drawn on the basis of course description, level, duration, no. of companies enrolled for this course etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Organizing Security Awareness Comparative Assessment Of Security Awareness Clipart PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Organizing Security Awareness Security Awareness Training Program Challenges Formats PDF
The purpose of this slide is to exhibit biggest cyber security awareness challenges which is faced by the organization. Outdated content, burden on administrators, low employee participation rate and employees losing interest are some of the key challenges which are highlighted in the slide. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Organizing Security Awareness Security Awareness Training Program Challenges Formats PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
Security For Network Protection From Unauthorized Access Vector Icon Ppt PowerPoint Presentation File Summary PDF
Presenting this set of slides with name security for network protection from unauthorized access vector icon ppt powerpoint presentation file summary pdf. This is a three stage process. The stages in this process are security for network protection from unauthorized access vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Importance Of Firewall Network Security In Business Vector Icon Ppt PowerPoint Presentation File Aids PDF
Presenting this set of slides with name importance of firewall network security in business vector icon ppt powerpoint presentation file aids pdf. This is a three stage process. The stages in this process are importance of firewall network security in business vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Threat Assessment For IT Network Security Ppt PowerPoint Presentation Gallery Example PDF
Presenting this set of slides with name threat assessment for it network security ppt powerpoint presentation gallery example pdf. This is a three stage process. The stages in this process are threat assessment for it network security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Data Transfer On Secured Network Vector Icon Ppt PowerPoint Presentation File Demonstration PDF
Presenting this set of slides with name data transfer on secured network vector icon ppt powerpoint presentation file demonstration pdf. This is a two stage process. The stages in this process are data transfer on secured network vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Corporate Data Management For Network Security Vector Icon Ppt PowerPoint Presentation Icon Portfolio PDF
Pitch your topic with ease and precision using this corporate data management for network security vector icon ppt powerpoint presentation icon portfolio pdf. This layout presents information on corporate data management for network security vector icon. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
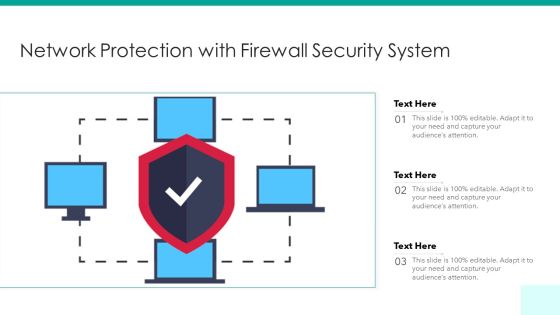
Network Protection With Firewall Security System Ppt PowerPoint Presentation File Pictures PDF
Presenting network protection with firewall security system ppt powerpoint presentation file pictures pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including network protection with firewall security system. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Query Slide Diagram For Designing A Secure Network Perimeter Diagrams PDF
Showcasing this set of slides titled query slide diagram for designing a secure network perimeter diagrams pdf. The topics addressed in these templates are query slide diagram for designing a secure network perimeter. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Icon Of Wireless Network Security System Camera Via Internet Diagrams PDF
Presenting icon of wireless network security system camera via internet diagrams pdf to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including icon of wireless network security system camera via internet. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Wireless Network Security System Camera Connected With Computer System Portrait PDF
Presenting wireless network security system camera connected with computer system portrait pdf to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including wireless network security system camera connected with computer system. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Icons Slide Safeguarding Network With SDN Security Ppt File Summary PDF
Help your business to create an attention-grabbing presentation using our Icons Slide Safeguarding Network With SDN Security Ppt File Summary PDF set of slides. The slide contains innovative icons that can be flexibly edited. Choose this Icons Slide Safeguarding Network With SDN Security Ppt File Summary PDF template to create a satisfactory experience for your customers. Go ahead and click the download button.
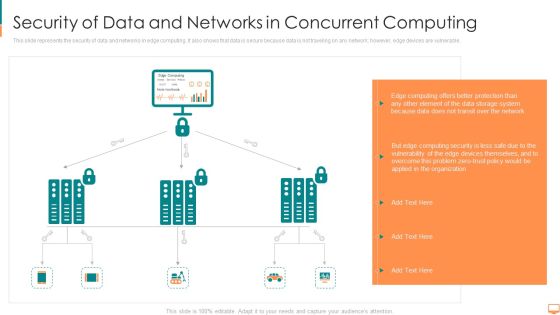
Security Of Data And Networks In Concurrent Computing Ppt File Themes PDF
This slide represents the security of data and networks in edge computing. It also shows that data is secure because data is not traveling on any network however, edge devices are vulnerable. This is a security of data and networks in concurrent computing ppt file themes pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like computing, transit, storage, system, protection, network. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Distributed Computing IT Security Of Data And Networks In Edge Computing Themes PDF
This slide represents the security of data and networks in edge computing. It also shows that data is secure because data is not traveling on any network however, edge devices are vulnerable. Presenting distributed computing it security of data and networks in edge computing themes pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like organization, data storage, computing security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

SDN Security Architecture Use Cases Of Software Defined Networking SDN Formats PDF
This slide represents the use cases of software defined networking, a developing technology that will eventually replace physical network designs with software controlled networking architecture. It shows its use in DevOps, campus networks, service provider networks, and data center security. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give SDN Security Architecture Use Cases Of Software Defined Networking SDN Formats PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable SDN Security Architecture Use Cases Of Software Defined Networking SDN Formats PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today

 Home
Home