Cybersecurity Uses Cases

Estimated Five Year Targets Of ABS Healthcare Company Ppt Summary Topics PDF
This slide shows the estimated future trends of ABS Healthcare Company for 5 years after the implementation of Strategies. These targets are related to number of Cybersecurity Cases, Client Satisfaction Rate, Company Revenue etc. Deliver and pitch your topic in the best possible manner with this estimated five year targets of ABS healthcare company ppt summary topics pdf. Use them to share invaluable insights on security measures to protect, cybersecurity cases are expected, 2021 to 2025 and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security Operations Application For IT Infrastructure Protection Template PDF
This slide highlight security operations SecOps use cases that could protect the business data. Some of the use cases include user-reported security incidents, infrastructure vulnerability response IVR, automation and orchestration, and SIR or VR reporting. Presenting Security Operations Application For IT Infrastructure Protection Template PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Infrastructure Vulnerability Response, Cyber Threat Intelligence, Fraud Reporting Automation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
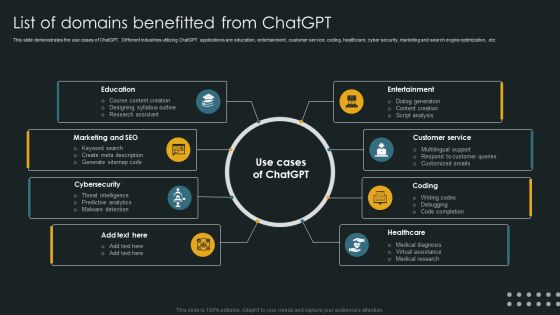
List Of Domains Benefitted From Chatgpt Slides PDF
This slide demonstrates the use cases of ChatGPT. Different industries utilizing ChatGPT applications are education, entertainment, customer service, coding, healthcare, cyber security, marketing and search engine optimization, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give List Of Domains Benefitted From Chatgpt Slides PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable List Of Domains Benefitted From Chatgpt Slides PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Cyber Safety Awareness Program Services Platform Ppt Show Information PDF
This slide covers platform for providing security awareness training services to clients. It includes elements such as platforms comprising of security awareness training content, phishing case studies, quarterly cyber awareness training, human based testing, monthly incident reporting, etc. Showcasing this set of slides titled Cyber Safety Awareness Program Services Platform Ppt Show Information PDF. The topics addressed in these templates are Platforms, Development, Core Self Managed. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Blockchain Security Solutions Deployment Overview Of Sybil Attack In Blockchain Summary PDF
This slide gives an overview of the sybil attack in the blockchain network. The purpose of this slide is to showcase the use case of a sybil attack, also known as eclipse attack, and how the sybil attack works to manipulate a blockchain network.. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Blockchain Security Solutions Deployment Overview Of Sybil Attack In Blockchain Summary PDF can be your best option for delivering a presentation. Represent everything in detail using Blockchain Security Solutions Deployment Overview Of Sybil Attack In Blockchain Summary PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Managed Cyber Security Solutions Service Threat Detection Process Ppt Portfolio Pictures PDF
The following slide highlights multistep process of managed security service to mitigate IT risks. It covers step such as operational readiness review, use cases, email notification, security analysis and event resolution. Presenting Managed Cyber Security Solutions Service Threat Detection Process Ppt Portfolio Pictures PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Event Resolution, Security Analysis, Use Cases, Operational Readiness Review. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Predictive Data Model Outliers Model For Predictive Analytics Introduction PDF
This slide talks about the outliers model used for predictive analytics, including its use cases, impact and algorithm used in it, such as the generalized linear model for two values. This model helps banking, finance, and cyber security organizations to detect fraud and cyber crimes. Make sure to capture your audiences attention in your business displays with our gratis customizable Predictive Data Model Outliers Model For Predictive Analytics Introduction PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Predictive Analytics Methods Outliers Model For Predictive Analytics Designs PDF
This slide talks about the outliers model used for predictive analytics, including its use cases, impact and algorithm used in it, such as the generalized linear model for two values. This model helps banking, finance, and cyber security organizations to detect fraud and cyber crimes. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Predictive Analytics Methods Outliers Model For Predictive Analytics Designs PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Cyber Risks And Incident Response Playbook KPI Dashboard To Track Department Wise Security Incidents Mockup PDF
Mentioned slide portrays KPI dashboard that can be used to monitor department wise security incidents. KPIs covered are new cases, total cases, resolved and pending cases. Presenting this PowerPoint presentation, titled Cyber Risks And Incident Response Playbook KPI Dashboard To Track Department Wise Security Incidents Mockup PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Cyber Risks And Incident Response Playbook KPI Dashboard To Track Department Wise Security Incidents Mockup PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Cyber Risks And Incident Response Playbook KPI Dashboard To Track Department Wise Security Incidents Mockup PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Outliers Model For Predictive Analytics Forward Looking Analysis IT Mockup PDF
This slide talks about the outliers model used for predictive analytics, including its use cases, impact and algorithm used in it, such as the generalized linear model for two values. This model helps banking, finance, and cyber security organizations to detect fraud and cyber crimes.Whether you have daily or monthly meetings, a brilliant presentation is necessary. Outliers Model For Predictive Analytics Forward Looking Analysis IT Mockup PDF can be your best option for delivering a presentation. Represent everything in detail using Outliers Model For Predictive Analytics Forward Looking Analysis IT Mockup PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Forecast Analysis Technique IT Outliers Model For Predictive Modeling Elements PDF
This slide talks about the outliers model used for predictive analytics, including its use cases, impact and algorithm used in it, such as the generalized linear model for two values. This model helps banking, finance, and cyber security organizations to detect fraud and cyber crimes. Slidegeeks is here to make your presentations a breeze with Forecast Analysis Technique IT Outliers Model For Predictive Modeling Elements PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Predictive Analytics In The Age Of Big Data Outliers Model For Predictive Analytics Demonstration PDF
This slide talks about the outliers model used for predictive analytics, including its use cases, impact and algorithm used in it, such as the generalized linear model for two values. This model helps banking, finance, and cyber security organizations to detect fraud and cyber crimes. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Predictive Analytics In The Age Of Big Data Outliers Model For Predictive Analytics Demonstration PDF can be your best option for delivering a presentation. Represent everything in detail using Predictive Analytics In The Age Of Big Data Outliers Model For Predictive Analytics Demonstration PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
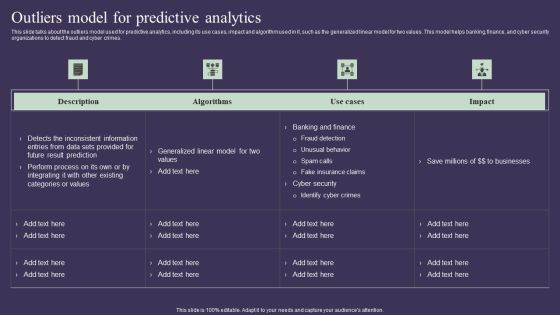
Projection Model Outliers Model For Predictive Analytics Topics PDF
This slide talks about the outliers model used for predictive analytics, including its use cases, impact and algorithm used in it, such as the generalized linear model for two values. This model helps banking, finance, and cyber security organizations to detect fraud and cyber crimes. Welcome to our selection of the Projection Model Outliers Model For Predictive Analytics Topics PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today

Difference Between ZTNA And Software Defined Perimeter Diagrams PDF
This slide outlines the comparison between zero trust network access and software-defined perimeter. The purpose of this slide is to highlight the key difference between the two security approaches based on definitional, key features, deployment, use cases, benefits and challenges. Make sure to capture your audiences attention in your business displays with our gratis customizable Difference Between ZTNA And Software Defined Perimeter Diagrams PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Comparison Between ZTNA And Secure Access Service Edge Professional PDF
This slide compares the two security models, such as zero trust network architecture and secure access service edge. The purpose of this slide is to highlight the difference between ZTNA and SASE based on definition, key features, deployment, use cases, benefits and challenges. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Comparison Between ZTNA And Secure Access Service Edge Professional PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

SDN Security Architecture Timeline For Software Defined Network Implementation Elements PDF
This slide talks about the timeline for software defined network implementation, including the steps to be performed, such as defining the use case, creating a cross functional team, testing, and reviewing. Want to ace your presentation in front of a live audience Our SDN Security Architecture Timeline For Software Defined Network Implementation Elements PDF can help you do that by engaging all the users towards you.. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Threat Modelling Procedure Of Cyber Security Program Elements PDF
This slide shows threat modelling process to identify gaps and improve efficiency of cyber security program. It contains five steps select digital asset, identify attack scenarios, evaluate existing controls, assess residual risks and construct business case.Presenting Threat Modelling Procedure Of Cyber Security Program Elements PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Digital Asset, Attack Scenarios, Evaluate Existing. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
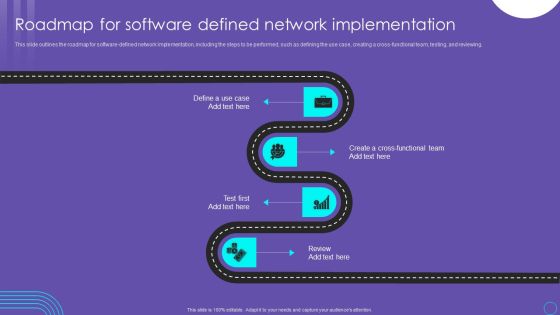
SDN Security Architecture Roadmap For Software Defined Network Implementation Slides PDF
This slide outlines the roadmap for software defined network implementation, including the steps to be performed, such as defining the use case, creating a cross functional team, testing, and reviewing. Find a pre designed and impeccable SDN Security Architecture Roadmap For Software Defined Network Implementation Slides PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Cyber Security Icon Dollar Sign Gear Wheel Ppt PowerPoint Presentation Complete Deck
This cyber security icon dollar sign gear wheel ppt powerpoint presentation complete deck acts as backup support for your ideas, vision, thoughts, etc. Use it to present a thorough understanding of the topic. This PPT slideshow can be utilized for both in-house and outside presentations depending upon your needs and business demands. Entailing twelve slides with a consistent design and theme, this template will make a solid use case. As it is intuitively designed, it suits every business vertical and industry. All you have to do is make a few tweaks in the content or any other component to design unique presentations. The biggest advantage of this complete deck is that it can be personalized multiple times once downloaded. The color, design, shapes, and other elements are free to modify to add personal touches. You can also insert your logo design in this PPT layout. Therefore a well-thought and crafted presentation can be delivered with ease and precision by downloading this cyber security icon dollar sign gear wheel ppt powerpoint presentation complete deck PPT slideshow.

Managing Cyber Security Incident Ppt PowerPoint Presentation Complete Deck With Slides
This Managing Cyber Security Incident Ppt PowerPoint Presentation Complete Deck With Slides acts as backup support for your ideas, vision, thoughts, etc. Use it to present a thorough understanding of the topic. This PPT slideshow can be utilized for both in-house and outside presentations depending upon your needs and business demands. Entailing twenty slides with a consistent design and theme, this template will make a solid use case. As it is intuitively designed, it suits every business vertical and industry. All you have to do is make a few tweaks in the content or any other component to design unique presentations. The biggest advantage of this complete deck is that it can be personalized multiple times once downloaded. The color, design, shapes, and other elements are free to modify to add personal touches. You can also insert your logo design in this PPT layout. Therefore a well-thought and crafted presentation can be delivered with ease and precision by downloading this Managing Cyber Security Incident Ppt PowerPoint Presentation Complete Deck With Slides PPT slideshow.
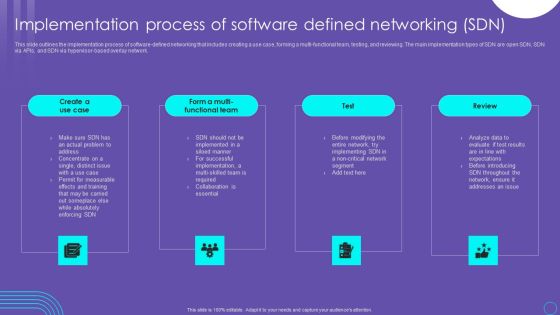
SDN Security Architecture Implementation Process Of Software Defined Networking SDN Diagrams PDF
This slide outlines the implementation process of software defined networking that includes creating a use case, forming a multi functional team, testing, and reviewing. The main implementation types of SDN are open SDN, SDN via APIs, and SDN via hypervisor based overlay network. The SDN Security Architecture Implementation Process Of Software Defined Networking SDN Diagrams PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

 Home
Home