Cyber Security Training
Network Security Protection Ensuring Safety From Online Threat Ppt PowerPoint Presentation Portfolio Influencers PDF
Persuade your audience using this network security protection ensuring safety from online threat ppt powerpoint presentation portfolio influencers pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including network security protection ensuring safety from online threat. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Web App Security Practices Ppt PowerPoint Presentation Show Portfolio Cpb Pdf
Presenting this set of slides with name web app security practices ppt powerpoint presentation show portfolio cpb pdf. This is an editable Powerpoint five stages graphic that deals with topics like web app security practices to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Icon Of Wireless Network Security System For WIFI Networks With Smart Lock Sample PDF
Persuade your audience using this icon of wireless network security system for wifi networks with smart lock sample pdf. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including icon of wireless network security system for wifi networks with smart lock. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
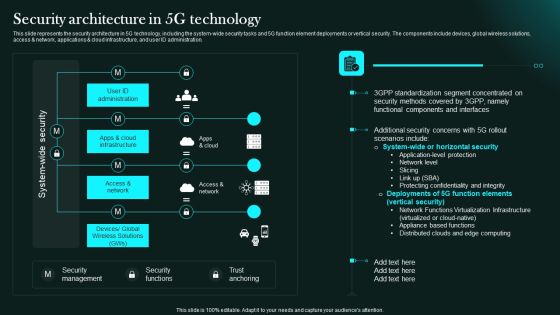
Security Architecture In 5G Technology 5G Network Functional Architecture Clipart PDF
This slide represents the security architecture in 5G technology, including the system-wide security tasks and 5G function element deployments or vertical security. The components include devices, global wireless solutions, access network, applications cloud infrastructure, and user ID administration.Retrieve professionally designed Security Architecture In 5G Technology 5G Network Functional Architecture Clipart PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You Do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
Security Software Deployed To Countermeasure Internet Threats Ppt PowerPoint Presentation Gallery Icon PDF
Persuade your audience using this security software deployed to countermeasure internet threats ppt powerpoint presentation gallery icon pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including security software deployed to countermeasure internet threats. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Coder Checking Business Internet Security Threats Ppt PowerPoint Presentation Gallery Model PDF
Persuade your audience using this coder checking business internet security threats ppt powerpoint presentation gallery model pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including coder checking business internet security threats. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Icon Of Wireless Network Security System With WIFI Lock Elements PDF
Persuade your audience using this icon of wireless network security system with wifi lock elements pdf. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including icon of wireless network security system with wifi lock. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Smart Phone With Wireless Network Security Alarm Icon Ppt Pictures Graphics Tutorials PDF
Persuade your audience using this smart phone with wireless network security alarm icon ppt pictures graphics tutorials pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including smart phone with wireless network security alarm icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

IT Security Hacker Altered Business Practices Due To Hacking Structure PDF
This slide represents that hackers forced the company to alter business practices followed by years and shut down online shopping stores in some regions.Deliver an awe inspiring pitch with this creative IT Security Hacker Altered Business Practices Due To Hacking Structure PDF bundle. Topics like Stored Information, Personal Information, Social Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Hacker Icon For Online Security Ppt PowerPoint Presentation Styles Example PDF
Persuade your audience using this hacker icon for online security ppt powerpoint presentation styles example pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including hacker icon for online security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cloud Online Certificate Icon For Information Security Ppt Styles Example Introduction PDF
Persuade your audience using this Cloud Online Certificate Icon For Information Security Ppt Styles Example Introduction PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Cloud Online, Certificate Icon, Information Security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Industrial Online Security Coaching System Of Business Ppt PowerPoint Presentation Ideas Designs Download PDF
Presenting this set of slides with name industrial online security coaching system of business ppt powerpoint presentation ideas designs download pdf. This is a three stage process. The stages in this process are essentials, design and build, specialist, key activities. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cybersecurity Operations Cybersecops Skills Required For Security Operations Teams Sample PDF
This slide talks about the skills required for security operation teams. The purpose of this slide is to showcase the various skills that can help SecOps to secure an organization completely. The primary skills include no-code automation, communicating modern threats from first principles, peer influence, and so on. Are you searching for a Cybersecurity Operations Cybersecops Skills Required For Security Operations Teams Sample PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Cybersecurity Operations Cybersecops Skills Required For Security Operations Teams Sample PDF from Slidegeeks today.

Best Work From Home Data Security Practices Improving Cybersecurity With Incident Inspiration PDF
Purpose of this slide is to provide information about the best data security practices that can be followed by employees who are working from home. Practices covered are configure WIFI encryption, avoid external devices, system update etc.Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Best Work From Home Data Security Practices Improving Cybersecurity With Incident Inspiration PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Best Work From Home Data Security Practices Improving Cybersecurity With Incident Inspiration PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
Steps To Enhance Bring Your Own Device Security Policy In Devices Icons PDF
This slide showcases steps to enhance bring your own device security to protect devices. It also includes steps such as cloud networks, password protection, routine back ups, data access, etc. Persuade your audience using this Steps To Enhance Bring Your Own Device Security Policy In Devices Icons PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Password Protection, Data Access, Antivirus Software. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
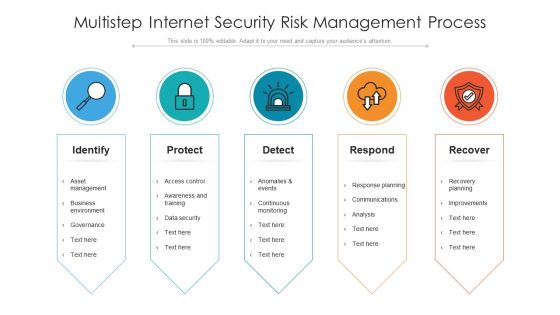
Multistep Internet Security Risk Management Process Ppt PowerPoint Presentation File Graphics PDF
Persuade your audience using this multistep internet security risk management process ppt powerpoint presentation file graphics pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including identify, protect, detect. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
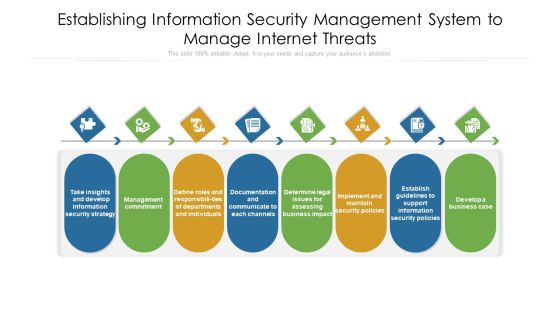
Establishing Information Security Management System To Manage Internet Threats Ppt PowerPoint Presentation File Visuals PDF
Persuade your audience using this establishing information security management system to manage internet threats ppt powerpoint presentation file visuals pdf. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including documentation, departments, management. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
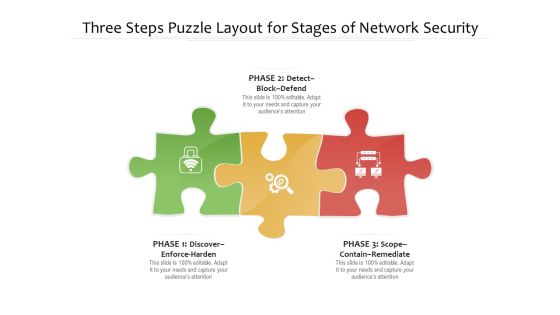
Three Steps Puzzle Layout For Stages Of Network Security Ppt PowerPoint Presentation File Vector PDF
Persuade your audience using this three steps puzzle layout for stages of network security ppt powerpoint presentation file vector pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including detect block defend, discover enforce harden, scope contain remediate. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
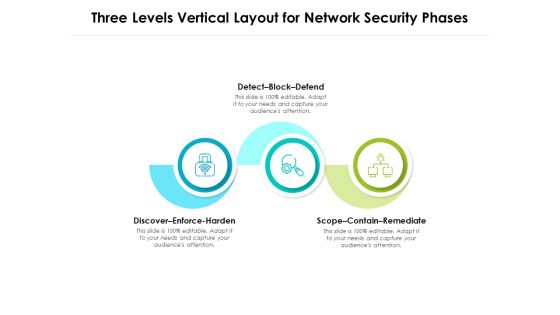
Three Levels Vertical Layout For Network Security Phases Ppt PowerPoint Presentation Portfolio Background Designs PDF
Persuade your audience using this three levels vertical layout for network security phases ppt powerpoint presentation portfolio background designs pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including detect block defend, discover enforce harden, scope contain remediate. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
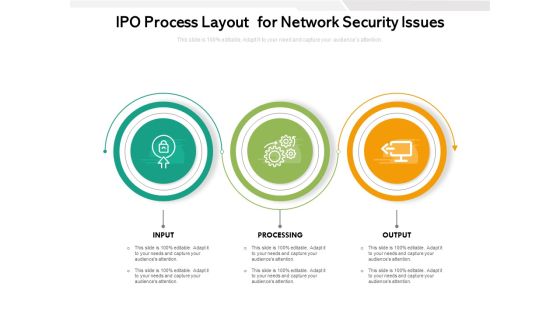
IPO Process Layout For Network Security Issues Ppt PowerPoint Presentation Outline Graphics Template PDF
Persuade your audience using this ipo process layout for network security issues ppt powerpoint presentation outline graphics template pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including processing, output, input. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Different Types Of Threats In IT Security Ppt PowerPoint Presentation Portfolio Model PDF
Persuade your audience using this different types of threats in it security ppt powerpoint presentation portfolio model pdf. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including malware, botnets, virus, trojan, spam, phishing, malicious codes, web based attack. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cashless Payment Strategies To Enhance Business Performance Best Practices To Maintain Digital Wallet Security Brochure PDF
Mentioned slide exhibits various best practices which can be implemented by followed by businesses to secure e-wallets. It includes best practices such as enable passwords, secure network connections, install reliable applications, secure login credentials, and keep personal data private. Retrieve professionally designed Cashless Payment Strategies To Enhance Business Performance Best Practices To Maintain Digital Wallet Security Brochure PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Bring Your Own Device Security Policy Trust Model Architecture Three Stage Process Rules PDF
This slide showcases BYOD trust model architecture three stage process, it concentrates on securing resource access independent of network location, subject, or asset. It also includes phases such as authentication, record keeping. evidence collection , etc. Persuade your audience using this Bring Your Own Device Security Policy Trust Model Architecture Three Stage Process Rules PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Record Keeping, Evidence Collection, Authentication . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Blockchain And Internet Of Things Security Technology For Healthcare Industry Mockup PDF
This slide highlights the importance of blockchain technology in healthcare industry which is used to preserve data and promote workflow authenticity. Key components are supply chain, electronic health records, safety access and staff verification. Persuade your audience using this Blockchain And Internet Of Things Security Technology For Healthcare Industry Mockup PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Supply Chain, Electronic Health Records, Safety Access, Staff Verification. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Skills Required To Become An Ethical Hacker Security Ppt Layouts Guide PDF
This slide depicts the skills required to become an ethical hacker, such as programming knowledge, scripting languages, networking skills, and understanding databases and servers. Presenting skills required to become an ethical hacker security ppt layouts guide pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like networking, technologies, management, database. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Digital Risk Assessment Key Metrics Monitoring Dashboard Ppt Ideas Diagrams PDF
The following slide highlights the cyber security key metrics monitoring dashboard illustrating critical applications, mission critical, other regulations, SOX, key metrics, controls, audits and cyber security training compliance. Showcasing this set of slides titled Digital Risk Assessment Key Metrics Monitoring Dashboard Ppt Ideas Diagrams PDF. The topics addressed in these templates are Critical Applications, Mission Critical, Other Regulation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cybersecurity Impact On Organization After Implementing Ppt Summary Influencers PDF
This slide depicts the impact of cyber security training on an organization. It also shows how trained employees can reduce cyber attacks in the organization. Presenting cybersecurity impact on organization after implementing ppt summary influencers pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like network intrusion, inadvertent disclosure, system misconfiguration. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
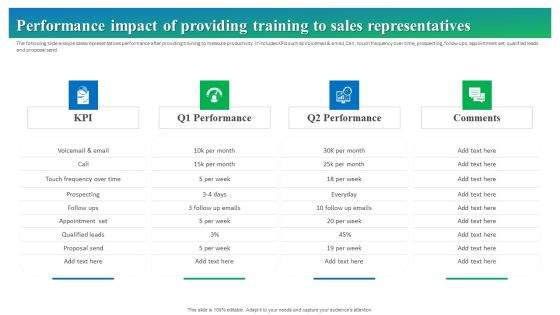
Process Enhancement Plan To Boost Sales Performance Performance Impact Of Providing Training To Sales Representatives Ideas PDF
The following slide analyze sales representatives performance after providing training to measure productivity. It includes KPIs such as Voicemail and email, Call , touch frequency over time, prospecting, follow ups, appointment set, qualified leads and proposal send. Want to ace your presentation in front of a live audience Our Process Enhancement Plan To Boost Sales Performance Performance Impact Of Providing Training To Sales Representatives Ideas PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.
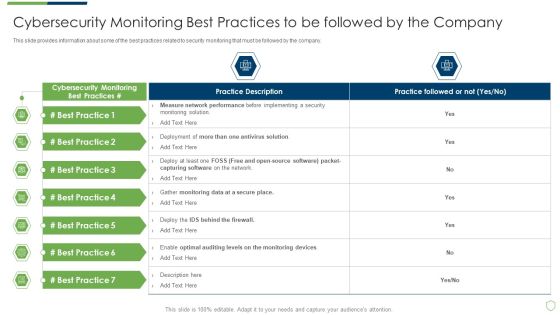
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Best Practices Introduction PDF
This slide provides information about some of the best practices related to security monitoring that must be followed by the company. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring best practices introduction pdf bundle. Topics like cybersecurity monitoring best practices to be followed by the company can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Companys Data Safety Recognition Communication Plan For Cybersecurity Events And Incidents Themes PDF
This slide covers the communication delivery channels for cyber security awareness training for different departments target audience along with program topics. Deliver an awe-inspiring pitch with this creative companys data safety recognition communication plan for cybersecurity events and incidents themes pdf bundle. Topics like department awareness training, resources training can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Communication Plan For Cybersecurity Events And Incidents Ppt Icon Good PDF
This slide covers the communication delivery channels for cyber security awareness training for different departments target audience along with program topics. Deliver and pitch your topic in the best possible manner with this communication plan for cybersecurity events and incidents ppt icon good pdf. Use them to share invaluable insights on resources training, awareness training, cybersecurity and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Communication Plan For Cybersecurity Events And Incidents Ppt Ideas Introduction PDF
This slide covers the communication delivery channels for cyber security awareness training for different departments target audience along with program topics Deliver an awe-inspiring pitch with this creative communication plan for cybersecurity events and incidents ppt ideas introduction pdf. bundle. Topics like approved communication topics, department awareness training can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Implementing Cybersecurity Awareness Program To Prevent Attacks Comparison Of Various Ideas PDF
The purpose of this slide is to drawn comparison of multiple software which can be used to provide cyber security training to the key stakeholders. Information covered in this slide is related to phishing simulations, security reporting, individualized security training plan etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Implementing Cybersecurity Awareness Program To Prevent Attacks Comparison Of Various Ideas PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Implementing Cybersecurity Awareness Program To Prevent Attacks Comparison Of Various Ideas PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Data Breach Prevention Recognition Communication Plan For Cybersecurity Events And Incidents Pictures PDF
This slide covers the communication delivery channels for cyber security awareness training for different departments target audience along with program topics. Deliver and pitch your topic in the best possible manner with this data breach prevention recognition communication plan for cybersecurity events and incidents pictures pdf. Use them to share invaluable insights on communication plan for cybersecurity events and incidents and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Communication Plan For Cybersecurity Events And Incidents Ppt Inspiration Graphic Images PDF
This slide covers the communication delivery channels for cyber security awareness training for different departments target audience along with program topics. Deliver and pitch your topic in the best possible manner with this communication plan for cybersecurity events and incidents ppt inspiration graphic images pdf. Use them to share invaluable insights on communication plan for cybersecurity events and incidents and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Implementing Cybersecurity Awareness Program To Prevent Attacks Assessment Test To Measure Brochure PDF
The purpose of this slide is to outline a comprehensive assessment test which can be used by the trainer to evaluate the effectiveness of cyber security training plan. The questions covered in the slide is related to spam, ways to protect from cyberbullying etc. Want to ace your presentation in front of a live audience Our Implementing Cybersecurity Awareness Program To Prevent Attacks Assessment Test To Measure Brochure PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.
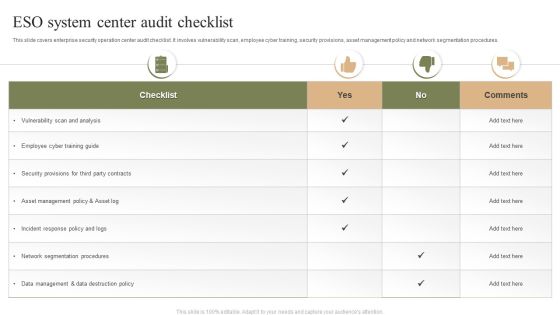
ESO System Center Audit Checklist Ppt PowerPoint Presentation Gallery Clipart Images PDF
This slide covers enterprise security operation center audit checklist. It involves vulnerability scan, employee cyber training, security provisions, asset management policy and network segmentation procedures. Showcasing this set of slides titled ESO System Center Audit Checklist Ppt PowerPoint Presentation Gallery Clipart Images PDF. The topics addressed in these templates are Checklist, Employee Cyber, Training Guide. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Five Steps Risk Management Process Of Insurance Process Mockup PDF
This slide show the risk management process which can be used by banking insurance company. It includes information security program, security codes, cyber security and training. Pitch your topic with ease and precision using this Five Steps Risk Management Process Of Insurance Process Mockup PDF. This layout presents information on Information Security Program, Security Codes, Cyber Security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Five Steps Insurance Risk Management Procedure Professional PDF
This slide show the risk management process of an insurance company. It includes information security program, security codes, cyber security and training. Persuade your audience using this Five Steps Insurance Risk Management Procedure Professional PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Security Codes, Cyber Security, Stay Informed. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cybersecurity Initiatives Ppt PowerPoint Presentation Outline Information
This is a cybersecurity initiatives ppt powerpoint presentation outline information. This is a nine stage process. The stages in this process are risk assessments, training and awareness, strategy, operationalizing cyber security, regulatory and legislative compliance.

IT OT Organizational Structure Based On Target And Culture Convergence Strategy Mockup PDF
This slide covers IT or OT cyber security organizational structure useful to train OT teams in IT cybersecurity to speak the same language and, conversely, train IT cybersecurity teams in OT to know the problems that need to be addressed. Presenting IT OT Organizational Structure Based On Target And Culture Convergence Strategy Mockup PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Architecture Boards, Security Architecture, Awareness and Training. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Smart Venture Digitial Transformation IT OT Organizational Structure Based On Target Download PDF
This slide covers IT or OT cyber security organizational structure useful to train OT teams in IT cybersecurity to speak the same language and, conversely, train IT cybersecurity teams in OT to know the problems that need to be addressed. This is a Smart Venture Digitial Transformation IT OT Organizational Structure Based On Target Download PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Enterprise CIO, Product Heads, Crisis Management, IT Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Digitalization Of Operative Enterprises IT OT Organizational Structure Based On Target And Culture Sharing Sample PDF
This slide covers IT or OT cyber security organizational structure useful to train OT teams in IT cybersecurity to speak the same language and, conversely, train IT cybersecurity teams in OT to know the problems that need to be addressed. Deliver an awe inspiring pitch with this creative Digitalization Of Operative Enterprises IT OT Organizational Structure Based On Target And Culture Sharing Sample PDF bundle. Topics like Business Continuity, Crisis Management, Design can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT OT Organizational Structure Based On Managing Organizational Transformation Designs PDF
This slide covers IT OT cyber security organizational structure useful to train OT teams in IT cybersecurity to speak the same language and, conversely, train IT cybersecurity teams in OT to know the problems that need to be addressed. Deliver and pitch your topic in the best possible manner with this IT OT Organizational Structure Based On Managing Organizational Transformation Designs PDF. Use them to share invaluable insights on Organizational Structure, Target, Culture Sharing and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT OT Organizational Structure Based On Target And Culture Sharing Rules PDF
This slide covers IT OT cyber security organizational structure useful to train OT teams in IT cybersecurity to speak the same language and, conversely, train IT cybersecurity teams in OT to know the problems that need to be addressed. Make sure to capture your audiences attention in your business displays with our gratis customizable IT OT Organizational Structure Based On Target And Culture Sharing Rules PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

IT Risk Control Strategies Risk Management Framework Mockup PDF
This slide shows the framework for information technology risk management which includes cyber security governance, IT and security risk assessment, training and awareness, security operation centre, independent audit and gap analysis. Persuade your audience using this IT Risk Control Strategies Risk Management Framework Mockup PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Security Governance, IT Risk Assessment, Security Assessment. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Secure Online Banking For Money Transfer Background PDF
Persuade your audience using this secure online banking for money transfer background pdf. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including secure online banking for money transfer. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Practices For Secure Online Transactions Processing Ppt Icon Themes PDF
This slide mentions practices for online transactions processing to ensure secure checkout process. It includes matching IP and billing address, Encrypt data and use payment tokenization method. Persuade your audience using this Practices For Secure Online Transactions Processing Ppt Icon Themes PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Encrypt Data, Use Payment Tokenization, IP And Billing. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Business Governance Framework For Cryptographically Secured Services Structure PDF
This slide signifies the organisation governance model for cryptographically secured services. It includes steps like generic value network, analysis, canvas analysis and plan.Persuade your audience using this Business Governance Framework For Cryptographically Secured Services Structure PDF. This PPT design covers one stage, thus making it a great tool to use. It also caters to a variety of topics including Suggested Service, Provider Business, Business Model. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Secured Laptop Global Business PowerPoint Templates Ppt Backgrounds For Slides 0213
We present our Secured Laptop Global Business PowerPoint Templates PPT Backgrounds For Slides 0213.Download our Security PowerPoint Templates because You can Create a matrix with our PowerPoint Templates and Slides. Feel the strength of your ideas click into place. Download our Success PowerPoint Templates because Our PowerPoint Templates and Slides are focused like a searchlight beam. They highlight your ideas for your target audience. Present our Business PowerPoint Templates because It will get your audience in sync. Use our Technology PowerPoint Templates because Our PowerPoint Templates and Slides will weave a web of your great ideas. They are gauranteed to attract even the most critical of your colleagues. Use our Computer PowerPoint Templates because You can Be the star of the show with our PowerPoint Templates and Slides. Rock the stage with your ideas.Use these PowerPoint slides for presentations relating to Key on laptop, security, success, business, technology, computer. The prominent colors used in the PowerPoint template are Black, Yellow, Blue.

Step By Step Procedure For Using Chatgpt Chat Generative Pre Trained Transformer Designs PDF
This slide illustrates the procedure of using ChatGPT. The purpose of this slide is to provide a guided tour to the user to start their experience with ChatGPT. The process start by opening the official website and login with email address. There are so many reasons you need a Step By Step Procedure For Using Chatgpt Chat Generative Pre Trained Transformer Designs PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Best Practices To Secure Internet Of Things Network Gateway Ppt Outline Elements PDF
The following slide showcases best practices to secure IOT gateway that are device establishment, establishing strong identity and provide identity to ecosystem. Presenting Best Practices To Secure Internet Of Things Network Gateway Ppt Outline Elements PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Performance Metrics For Project Management Office, Requirement Gathering. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Network Protection Icon For Securing Customer Information Ppt PowerPoint Presentation Icon Pictures PDF
Persuade your audience using this network protection icon for securing customer information ppt powerpoint presentation icon pictures pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including network protection icon for securing customer information. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Secured Public Cloud Network On Premises Vector Icon Ppt PowerPoint Presentation Gallery Slideshow PDF
Persuade your audience using this secured public cloud network on premises vector icon ppt powerpoint presentation gallery slideshow pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including secured public cloud network on premises vector icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Four Stage Approach Graphic For Online File Storage Secure Ppt PowerPoint Presentation File Show PDF
Persuade your audience using this four stage approach graphic for online file storage secure ppt powerpoint presentation file show pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including four stage approach graphic for online file storage secure. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Transform Management Instruction Schedule Technological Change Management Designs PDF
This slide represents the strategic plan developed to facilitate training to employees related to introducing new technological advancements in the enterprise. It includes details related to training topics such as cloud computing, cyber security, data storage etc. Find highly impressive Transform Management Instruction Schedule Technological Change Management Designs PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Transform Management Instruction Schedule Technological Change Management Designs PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
Public And Private Cloud Network Icon With Secure User Information Ppt PowerPoint Presentation Infographic Template Skills PDF
Presenting public and private cloud network icon with secure user information ppt powerpoint presentation infographic template skills pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including public and private cloud network icon with secure user information. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Yellow Computer Folder With-key Internet PowerPoint Templates And PowerPoint Themes 1112
We present our Yellow Computer Folder With-Key Internet PowerPoint Templates And PowerPoint Themes 1112.Use our Computer PowerPoint Templates because, Different people with differing ideas and priorities perform together to score. Use our Internet PowerPoint Templates because, Our template will help pinpoint their viability. Use our Communication PowerPoint Templates because, Use our creative template to lay down your views. Use our Security PowerPoint Templates because, Gears Interconnected:- The Gear Train is a basic element of living and daily business. Use our Symbol PowerPoint Templates because,Use our templates for your colleagues knowledge to feed.Use these PowerPoint slides for presentations relating to Yellow computer folder with key Internet Security Computer Symbol Communication. The prominent colors used in the PowerPoint template are Yellow, White, Brown
Network And Information Threat Safety Vector Icon Ppt PowerPoint Presentation File Example PDF
Persuade your audience using this network and information threat safety vector icon ppt powerpoint presentation file example pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including network and information threat safety vector icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Files Folder And Lifebuoy Computer PowerPoint Templates Ppt Backgrounds For Slides 1212
We present our Files Folder And Lifebuoy Computer PowerPoint Templates PPT Backgrounds For Slides 1212.Present our Computer PowerPoint Templates because the graphic is a symbol of growth and success. Download our Security PowerPoint Templates because you can see In any endeavour people matter most. Present our Inetrnet PowerPoint Templates because you can Signpost your preferred roadmap to your eager co- travellers and demonstrate clearly how you intend to navigate them towards the desired corporate goal. Download our Success PowerPoint Templates because the success of your venture depends on the performance of every team member. Download our Teamwork PowerPoint Templates because the Gear train is a basic element of living and daily business.Use these PowerPoint slides for presentations relating to Computer folders on a lifebuoy, internet, computer, security, success, teamwork. The prominent colors used in the PowerPoint template are Yellow, Red, White. Professionals tell us our Files Folder And Lifebuoy Computer PowerPoint Templates PPT Backgrounds For Slides 1212 are Stunning. Use our on PowerPoint templates and PPT Slides are Zippy. We assure you our Files Folder And Lifebuoy Computer PowerPoint Templates PPT Backgrounds For Slides 1212 are Charming. We assure you our computer PowerPoint templates and PPT Slides are Functional. Presenters tell us our Files Folder And Lifebuoy Computer PowerPoint Templates PPT Backgrounds For Slides 1212 are Ultra. PowerPoint presentation experts tell us our computer PowerPoint templates and PPT Slides are Graceful.

 Home
Home