Cyber Security Strategy

IT Security Incident Response Communication Plan Development Background PDF
This slide illustrates steps to develop a cyber security incident response communication plan to minimize impact level. It includes steps such as formulate team activation process, designate person, create criteria for law involvement etc. Presenting IT Security Incident Response Communication Plan Development Background PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Formulate Team Activation, Designate Person, Formulate Communication Template. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Data Integration Architecture To Manage Cyber Risk Pictures PDF
This slide showcases the structure to manage cybersecurity threats and risk of any organization. It includes steps such as identifying user with data access, protecting data accessibility, secure networks, install and updating antivirus, developing plan for managing disasters etc. Presenting Identify, Protect, Detect to dispense important information. This template comprises Five stages. It also presents valuable insights into the topics including Data Integration Architecture To Manage Cyber Risk Pictures PDF. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Current Security Monitoring Challenges Slides PDF
This slide shows some of the current Security Monitoring challenges and issues that are faced by the company and cyber security monitoring managers. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach current security monitoring challenges slides pdf bundle. Topics like current security monitoring challenges the company is facing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Communication Plan For Cyber Breaches Ppt Layouts Ideas PDF
Mentioned slide portrays communication plan that company will use for effectively managing cyber breaches. Sections covered here are what to communicate, description, delivery method, frequency and responsible. Deliver an awe inspiring pitch with this creative communication plan for cyber breaches ppt layouts ideas pdf bundle. Topics like potential security, development process, method can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Comparison Of Various Security Awareness Training Software Demonstration PDF
The purpose of this slide is to drawn comparison of multiple software which can be used to provide cyber security training to the key stakeholders. Information covered in this slide is related to phishing simulations, security reporting, individualized security training plan etc. If you are looking for a format to display your unique thoughts, then the professionally designed Comparison Of Various Security Awareness Training Software Demonstration PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Comparison Of Various Security Awareness Training Software Demonstration PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

PCI Certification For Increasing Security Of Online Transactions Designs PDF
This slide depicts payment card industry PCI certification for increasing security of online transactions. It provides information about authorization, 2 way authentication, one time password OTP, repository, cyber attacks, compliance, data breach, etc. Presenting this PowerPoint presentation, titled PCI Certification For Increasing Security Of Online Transactions Designs PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this PCI Certification For Increasing Security Of Online Transactions Designs PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable PCI Certification For Increasing Security Of Online Transactions Designs PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Cyber Protection Improvement Plan Impact On Business Designs PDF
This slide shows difference between before and after implementing cyber protection improvement plan in business. It includes types phishing attacks, malware attacks, data breaches, etc. Showcasing this set of slides titled Cyber Protection Improvement Plan Impact On Business Designs PDF. The topics addressed in these templates are Cyber Protection Improvement, Plan Impact On Business. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Pricing Plan Of Security Awareness Packages Slides PDF
The purpose of this slide is to showcase the pricing plan of cyber security awareness package. It covers information about the total number of employees along with different packages such as silver, gold, platinum and diamond. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Pricing Plan Of Security Awareness Packages Slides PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Business Operations Strategic Tactical Planning Cyber Threat Intelligence Summary PDF
This slide exhibits strategic tactical and operational levels of cyber threat intelligence to ensure data and software protection from threats. It includes identify reason, assist extent of breach, alert and identify prevention system and ensure safety in advance. Persuade your audience using this Business Operations Strategic Tactical Planning Cyber Threat Intelligence Summary PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Strategic Cyber Threat Intelligence, Tactical Cyber Threat Intelligence, Operational Cyber Threat Intelligence. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Botnet Attack Cyber Criminal Activity Icon Ideas PDF
Showcasing this set of slides titled Botnet Attack Cyber Criminal Activity Icon Ideas PDF. The topics addressed in these templates are Botnet Attack Cyber, Criminal Activity Icon. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Risk Icon Indicating Malware Attack Elements PDF
Presenting cyber risk icon indicating malware attack elements pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including cyber risk icon indicating malware attack. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
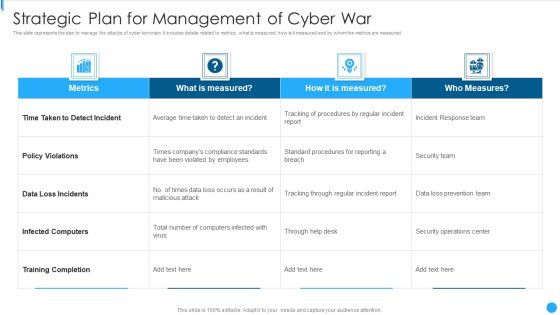
Strategic Plan For Management Of Cyber War Portrait PDF
This slide represents the plan to manage the attacks of cyber terrorism. It includes details related to metrics, what is measured, how is it measured and by whom the metrics are measured.Showcasing this set of slides titled Strategic Plan For Management Of Cyber War Portrait PDF The topics addressed in these templates are Loss Incidents, Infected Computers, Training Completion All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Data Safety Initiatives Communication Plan For Cyber Breaches Topics PDF
Mentioned slide portrays communication plan that company will use for effectively managing cyber breaches. Sections covered here are what to communicate, description, delivery method, frequency and responsible. Presenting data safety initiatives communication plan for cyber breaches topics pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like communicate, delivery method, frequency, responsible, product report. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Agenda For Russian Cyber Attacks On Ukraine Summary PDF
This is a agenda for russian cyber attacks on ukraine summary pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like technical, analysis, websites, globally. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Conceptual Framework Of Cyber War With Impact Demonstration PDF
This slide covers the framework for cyberterrorism whose main objective is to destroy target organization, industry or economy. It represents the target, motivation, tools of attack, domain, method of action and impact of the cyber terrorism in a country.Presenting Conceptual Framework Of Cyber War With Impact Demonstration PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including National Information, Infrastructure System, Civilian Population This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Five Year Cyber Information Safety Career Growth Roadmap Background
We present our five year cyber information safety career growth roadmap background. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched five year cyber information safety career growth roadmap background in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
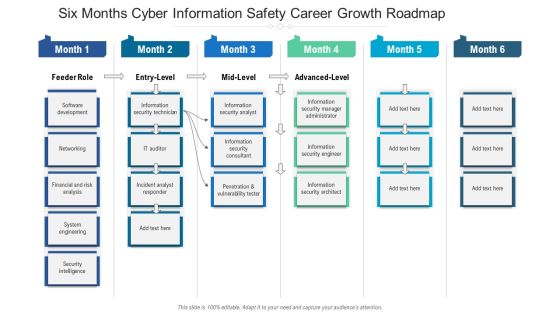
Six Months Cyber Information Safety Career Growth Roadmap Portrait
We present our six months cyber information safety career growth roadmap portrait. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched six months cyber information safety career growth roadmap portrait in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Three Months Cyber Information Safety Career Growth Roadmap Sample
We present our three months cyber information safety career growth roadmap sample. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched three months cyber information safety career growth roadmap sample in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Cyber Safety Incident Management Determine Threat Scenario Analysis Background PDF
This slide provides details regarding threat scenario assessment by understanding various phases of threat actor attack on victim. Presenting cyber safety incident management determine threat scenario analysis background pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like determine threat scenario analysis. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Safety Incident Management Workplace Incident Summary Report Background PDF
This slide can be utilized to report any workplace incident. After filling this form it will be forwarded to Business unit safety director and HR representative. Deliver an awe inspiring pitch with this creative cyber safety incident management workplace incident summary report background pdf bundle. Topics like workplace incident summary report can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Elements Of Botnet Hacking And Cyber Criminal Attacks Brochure PDF
This slide illustrates key elements of botnet attacks. It includes elements such as compromised devices, command and control servers, botnet use, quiet threat, etc. Persuade your audience using this Elements Of Botnet Hacking And Cyber Criminal Attacks Brochure PDF. This PPT design covers Four stages, thus making it a great tool to use. It also caters to a variety of topics including Compromised Devices, Command Control Servers, Botnet Use, Quiet Threat. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Safety Incident Management Threat Management Action Plan Sample PDF
The threat management action plan will help in keeping the track of various potential threats that are existing in the firm. The person responsible in handling the threats will keep track of the duration in which threat is resolved. Presenting cyber safety incident management threat management action plan sample pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like threat identification, threat treatment. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
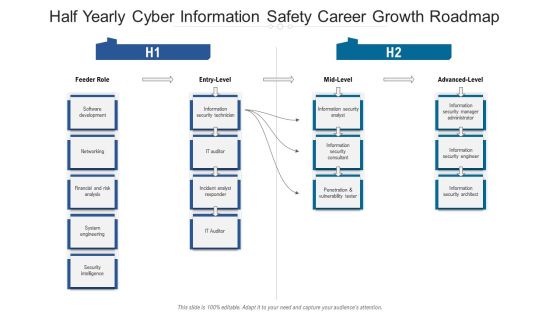
Half Yearly Cyber Information Safety Career Growth Roadmap Designs
Presenting the half yearly cyber information safety career growth roadmap designs. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Quarterly Cyber Information Safety Career Growth Roadmap Elements
Presenting the quarterly cyber information safety career growth roadmap elements. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Digital Risk Assessment Transformation Strategy With Implementation Slides PDF
The following slide highlights the cyber security transformation strategy with implementation illustrating benchmark, analysis, vision, roadmap, mobilization, and implementation which assists in transforming cyber security of organisation. Presenting Digital Risk Assessment Transformation Strategy With Implementation Slides PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Implementation, Benchmark, Analysis, Vision. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Information Systems Security And Risk Management Plan Selecting Suitable Software For Information Security Risk Management Diagrams PDF
This slide showcases software that can help organization to monitor and information security risk. It provides information about Cyber Risk Quantification, vulnerability management, Centralized repository for assets etc. Get a simple yet stunning designed Information Systems Security And Risk Management Plan Selecting Suitable Software For Information Security Risk Management Diagrams PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Information Systems Security And Risk Management Plan Selecting Suitable Software For Information Security Risk Management Diagrams PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
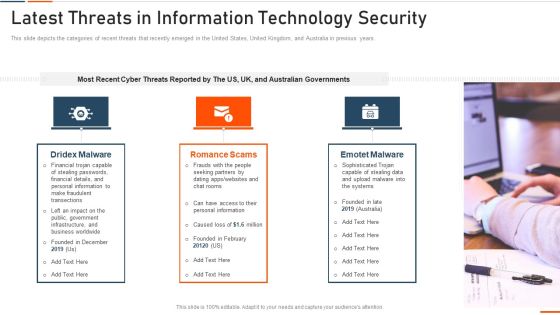
Latest Threats In Information Technology Security Ppt Pictures Designs PDF
This slide represents the different elements of Network security such as application security, network security, information security, etc. This is a latest threats in information technology security ppt pictures designs pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like network security, cloud security, application security, operational security, information security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Mitigation Tactics To Prevent Internet Security Threats Formats PDF
This side exhibits mitigation strategies to prevent security breach incidents. It includes multiple actions such as keeping track of all personal assets, analyzing logging process security and so on. Presenting mitigation tactics to prevent internet security threats formats pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including communication management, monitoring and alerting, logging, visibility. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Online Security Requirements For Iot Devices And Systems Graphics PDF
This slide showcases digital security requirements for IOT devices which help analyze security security threats and vulnerabilities. It provides information regarding email encryption, data integrity, security policy and monitoring and user authentication. Pitch your topic with ease and precision using this Online Security Requirements For Iot Devices And Systems Graphics PDF. This layout presents information on Device Management, Security Policy, Security Monitoring. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Information Security Program Framework Key Components Ppt Inspiration Ideas PDF
Mentioned slide portrays the key components of companys information security framework. Components covered are context and leadership, evaluation and direction, prevention, detection etc. Deliver and pitch your topic in the best possible manner with this information security program framework key components ppt inspiration ideas pdf. Use them to share invaluable insights on network security, application security, vendor management, data security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information Security Operations Training Department Program Chart Infographics PDF
This slide covers employees training in organizations based on different security operations. It includes training based on security policy, incident management, security audit, cybersecurity, malware analysis, etc. Showcasing this set of slides titled Information Security Operations Training Department Program Chart Infographics PDF. The topics addressed in these templates are Induction Complete, Company Security Policy, Incident Management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Electronic Voting System Voting System Standards Security Template PDF
This slide represents the security standard of the voting system that ensures the security of voting machines to prevent them from being tempered or manipulated through physical security, auditability, and internet connection.Presenting Electronic Voting System Voting System Standards Security Template PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Manipulated Tampered, Ensuring Security, Security Include. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Sample Network Security Diagram Ppt Example Of Ppt
This is a sample network security diagram ppt example of ppt. This is a six stage process. The stages in this process are network security, analyse, plan, design, implement, operate, optimize.

Security Architecture In 5G Technology 5G Functional Architecture Topics PDF
This slide represents the security architecture in 5G technology, including the system-wide security tasks and 5G function element deployments or vertical security. The components include devices, global wireless solutions, access and network, applications and cloud infrastructure, and user ID administration.Deliver an awe inspiring pitch with this creative Security Architecture In 5G Technology 5G Functional Architecture Topics PDF bundle. Topics like Standardization Segment, Concentrated Security, Components Interfaces can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

6 Step Process To Implement Information Availability Security Icons PDF
This slide represents 6 step process to implement data availability security illustrating simplified recording, on site maintenance and online security, training, record disposal and plan. Presenting 6 step process to implement information availability security icons pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including required, develop, security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Organizational Network Staff Learning Security Awareness Training Roadmap Sample PDF
This slide covers the roadmap for training concepts and guidelines on security awareness to advise and plan the company for a comprehensive training program. Presenting organizational network staff learning security awareness training roadmap sample pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like ensuring data security, information security and privacy threats, ensuring physical security. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

Organizational Network Staff Learning Security Awareness Program Checklist Background PDF
This slide covers the Checklist that will help organizations prepare and implement their safety awareness training. The details listed below can be used to promote preparation and education planning in the area of security awareness. Presenting organizational network staff learning security awareness program checklist background pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security awareness program, implementing security awareness, sustaining security awareness. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

5G Network Operations Security Architecture In 5G Technology Inspiration PDF
This slide represents the security architecture in 5G technology, including the system-wide security tasks and 5G function element deployments or vertical security. The components include devices, global wireless solutions, access and network, applications cloud infrastructure, and user ID administration. Presenting this PowerPoint presentation, titled 5G Network Operations Security Architecture In 5G Technology Inspiration PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this 5G Network Operations Security Architecture In 5G Technology Inspiration PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable 5G Network Operations Security Architecture In 5G Technology Inspiration PDFthat is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
Icon Showcasing Effective Online Security Policy Topics PDF
Persuade your audience using this Icon Showcasing Effective Online Security Policy Topics PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Icon Showcasing Effective, Online Security Policy. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Roadmap For Information Technology Security Training Ppt Ideas Influencers PDF
This slide depicts the network security training roadmap. It also shows the plan and guidelines to conduct an effective training program. This is a roadmap for roadmap for information technology security training ppt ideas influencers pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like rmation security, computing best practices, physical security, data security . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Determine Established Security Centre Overview Ppt Show Visual Aids PDF
This slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. Deliver an awe inspiring pitch with this creative determine established security centre overview ppt show visual aids pdf bundle. Topics like security, network, systems, management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Computing Data Protection Security Architecture Solution Professional PDF
The slide shows a overall architecture of cloud data security system to provide data protection solution in controllable cloud security environment. It includes web application firewall, risk detection, physical and hardware security, digitalization and data encryption and back up. Showcasing this set of slides titled Cloud Computing Data Protection Security Architecture Solution Professional PDF. The topics addressed in these templates are Web Application Firewall, Data Detection, Data Awareness. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Security For Cloud Based Systems Architectural Solution Model Background PDF
This slide shows architecture solution which can be used by organizations in cloud data security. It includes web application firewall, risk detection, data detection, etc. Showcasing this set of slides titled Security For Cloud Based Systems Architectural Solution Model Background PDF. The topics addressed in these templates are Security For Cloud Based, Systems Architectural Solution Model. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Checklist To Implement Cloud Security In Business Microsoft PDF
This slide shows the checklist to implement cloud security in business, including policies and procedures, access control, networking, backup data, security patches, etc. Presenting Checklist To Implement Cloud Security In Business Microsoft PDF to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like Access Control, Networking, Security Patches And Updates. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Architecture In 5G Technology 5G Network Structure Background PDF
This slide represents the security architecture in 5G technology, including the system-wide security tasks and 5G function element deployments or vertical security. The components include devices, global wireless solutions, access network, applications cloud infrastructure, and user ID administration.Are you searching for a Security Architecture In 5G Technology 5G Network Structure Background PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Security Architecture In 5G Technology 5G Network Structure Background PDF from Slidegeeks today.

Software Defined Networking And Security Ppt Styles Slides PDF
This slide describes the security in software-defined networking, including the security features of SDN architecture such as threat defense, SDN telemetry, segmentation, and ddos. It also includes security components for SDN such as infrastructure, controller, API, and application security. Slidegeeks is here to make your presentations a breeze with Software Defined Networking And Security Ppt Styles Slides PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
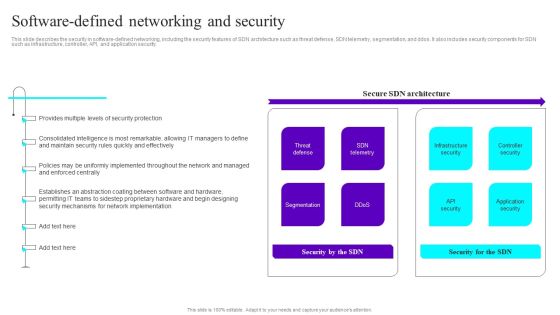
Software Defined Networking And Security Ppt Slides File Formats PDF
This slide describes the security in software-defined networking, including the security features of SDN architecture such as threat defense, SDN telemetry, segmentation, and ddos. It also includes security components for SDN such as infrastructure, controller, API, and application security. Slidegeeks is here to make your presentations a breeze with Software Defined Networking And Security Ppt Slides File Formats PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Ways To Improve Digital Banking Security Elements PDF
This slide mentions the ways to improve online banking security for seamless customer experience. It includes industry standard security protocol, skipping public Wi-Fi, changing password regularly and asking for text alerts. Presenting Ways To Improve Digital Banking Security Elements PDF to dispense important information. This template comprises Four stages. It also presents valuable insights into the topics including Industry Standard Security Protocol, Skip Public Wifi, Change Passwords Regularly. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Internet Security Threat Icon On Computer Elements PDF
Presenting internet security threat icon on computer elements pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including internet security threat icon on computer. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Icon For Implementation Of Complete Digital Security Network Professional PDF
Presenting Icon For Implementation Of Complete Digital Security Network Professional PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Icon For Implementation, Complete Digital Security Network. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cybersecurity Training Workshop On Security Breach Trends Icon Designs PDF
Presenting Cybersecurity Training Workshop On Security Breach Trends Icon Designs PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Cybersecurity Training, Workshop On Security, Breach Trends Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Multipoint Checklist To Improve Computer Security Guidelines PDF
This slide shows comprehensive checklist used to enhance information technology security. It includes email phishing training, anti virus and malware use, password changes etc. Showcasing this set of slides titled Multipoint Checklist To Improve Computer Security Guidelines PDF The topics addressed in these templates are Frequent System, Control Administrative, System Password All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cybersecurity Operations Cybersecops Security Operations Model And Incidents Diagrams PDF
This slide represents the security operations model, covering the incidents managed by the security operations center. The model includes three teams such as hunters, investigators, and triage. The incidents include multi-stage incidents, known campaign tracking, and high-volume incidents. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Cybersecurity Operations Cybersecops Security Operations Model And Incidents Diagrams PDF from Slidegeeks and deliver a wonderful presentation.

Internet Security Threat Analysis Plan With Event Handling Summary PDF
Following slide exhibits security breach plan with incident topology. It includes major steps such as- provide incidence guidance to employees, guidance for categorization and actions etc. Presenting internet security threat analysis plan with event handling summary pdf to dispense important information. This template comprises one stage. It also presents valuable insights into the topics including internet security threat analysis plan with event handling. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Computer Security Incident Handling Cybersecurity Maintenance Checklist Background PDF
Presenting this set of slides with name computer security incident handling cybersecurity maintenance checklist background pdf. The topics discussed in these slides are system monitoring real time, backup monitoring, preventive maintenance, virus scanning, security patches, executive reporting, review and planning meeting. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Distribution Network Data Security Handled By CDN Topics PDF
This slide demonstrates how CDN protects data by issuing TLS or SSL certificates, blocking Bots and crawlers, and defending against DDoS assaults. Deliver an awe inspiring pitch with this creative Distribution Network Data Security Handled By CDN Topics PDF bundle. Topics like Security, Resources, Location can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Network Security Architecture And Boundaries Graphics PDF
The slide presents an architecture describing technologies and hardware to protect data and systems within cloud platforms . The slide includes security boundaries and key takeaways. Showcasing this set of slides titled Cloud Network Security Architecture And Boundaries Graphics PDF. The topics addressed in these templates are Presentation Mobility, Presentation Platform, Applications. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Internet Security Threat Analysis Process By Backdoor Graphics PDF
This slide exhibits data and security breach attack process conducted by hackers to get access to company data. It includes multiple activities such as link forwarding by emails, data sharing and attacking and so on. Showcasing this set of slides titled internet security threat analysis process by backdoor graphics pdf. The topics addressed in these templates are exfiltrate, stage attack, research. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cybersecurity Best Practices For Cloud Security Ppt Ideas Images PDF
This slide represents the best practices for cloud security, such as the shared responsibility model, operations management, building controls, and processes and data encryption. Presenting cybersecurity best practices for cloud security ppt ideas images pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like measures, security, planning, network, systems. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security Hacker Cybersecurity Awareness Training For Staff Guidelines PDF
This slide represents the cybersecurity awareness training program for staff, including the name of the participants and what modules would be covered under training daily. Deliver and pitch your topic in the best possible manner with this IT Security Hacker Cybersecurity Awareness Training For Staff Guidelines PDF. Use them to share invaluable insights on Project Managers, Senior Executives, Security Introduction and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

 Home
Home