Cyber Security Strategy
Information Security Define Access Control Measures For Employees Ppt Icon Pictures PDF
This slide represents how it is essential to minimize the rights or access of employees in an organization to keep data safe and prevent it from deletion, manipulation. This is a information security define access control measures for employees ppt icon pictures pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like networks, organization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

SDN Security Architecture Timeline For Software Defined Network Implementation Elements PDF
This slide talks about the timeline for software defined network implementation, including the steps to be performed, such as defining the use case, creating a cross functional team, testing, and reviewing. Want to ace your presentation in front of a live audience Our SDN Security Architecture Timeline For Software Defined Network Implementation Elements PDF can help you do that by engaging all the users towards you.. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.
Safeguarding Network With SDN Security Table Of Contents Ppt Visual Aids Files PDF
This slide represents the schematic elements of software-defined networking, such as the northbound interface, SDN controller, and southbound interface. These components transmit the information throughout the SDN architecture. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Safeguarding Network With SDN Security Table Of Contents Ppt Visual Aids Files PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Project Security Administration IT Contingency Plan For Managing Threats To Ensure It Project Safety Mockup PDF
This slide provides information regarding contingency plan for managing threats to ensure IT project safety with aid of technical equipment ensuring contingency plans. Deliver an awe inspiring pitch with this creative project security administration it contingency plan for managing threats to ensure it project safety mockup pdf bundle. Topics like distributes systems, mainframe systems, wide area network, local area network, website can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Table Of Contents For Building Security Awareness Among Workforce To Minimize Cybersecurity Threats Summary PDF
Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Table Of Contents For Building Security Awareness Among Workforce To Minimize Cybersecurity Threats Summary PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
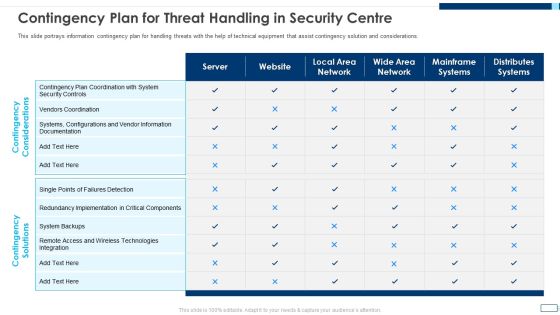
Evolving BI Infrastructure Contingency Plan For Threat Handling In Security Centre Pictures PDF
This slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations. Deliver and pitch your topic in the best possible manner with this evolving bi infrastructure contingency plan for threat handling in security centre pictures pdf. Use them to share invaluable insights on server, website, local area network, wide area network, mainframe systems, distributes systems and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
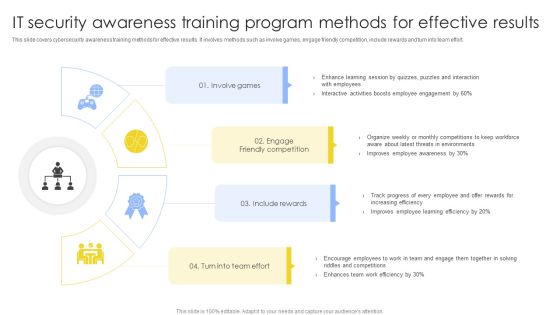
IT Security Awareness Training Program Methods For Effective Results Summary PDF
This slide covers cybersecurity awareness training methods for effective results. It involves methods such as involve games, engage friendly competition, include rewards and turn into team effort. Presenting IT Security Awareness Training Program Methods For Effective Results Summary PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Involve Games, Engage Friendly Competition, Include Rewards. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
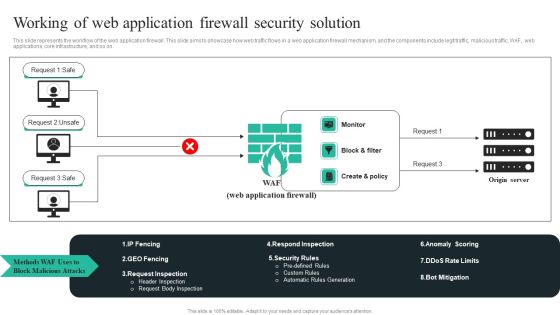
WAF Introduction Working Of Web Application Firewall Security Solution Microsoft PDF
This slide represents the workflow of the web application firewall. This slide aims to showcase how web traffic flows in a web application firewall mechanism, and the components include legit traffic, malicious traffic, WAF, web applications, core infrastructure, and so on. Take your projects to the next level with our ultimate collection ofWAF Introduction Working Of Web Application Firewall Security Solution Microsoft PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.

Desktop Security Management Define Access Control Measures For Employees Icons PDF
This slide represents how it is essential to minimize the rights or access of employees in an organization to keep data safe and prevent it from deletion, manipulation. This is a desktop security management define access control measures for employees icons pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organization, networks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Quarterly IT Security Awareness Training Program Plan Ppt Gallery Topics PDF
This slide covers quarterly cybersecurity awareness training program plan. It involves activities such as cybersecurity knowledge and survey, compliance training, phishing simulation etc. Pitch your topic with ease and precision using this Quarterly IT Security Awareness Training Program Plan Ppt Gallery Topics PDF. This layout presents information on Key Message, Core Awareness Activities, Responsible Person, Budget. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
How Is Automation Used In Information Technology Security Ppt File Icon PDF
This slide depicts the network protection of an organization through artificial intelligence and how it can be helpful in threat detection, threat response, and human augmentation. Presenting how is automation used in information technology security ppt file icon pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like threat detection, threat response, human detection. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Software Company Investor Funding Pitch Deck Our Solution Demonstration PDF
The following slide showcases solution offered by IT company for its customers which are see the new network, know current threats and protect with high ROI. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Security Software Company Investor Funding Pitch Deck Our Solution Demonstration PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.

SDN Security Architecture Working Of Software Defined Networking SDN Rules PDF
This slide describes the working of software defined networking, including its various components such as SDN applications, northbound and southbound interfaces, SDN controller, application plane, control plane and data plane. Slidegeeks is here to make your presentations a breeze with SDN Security Architecture Working Of Software Defined Networking SDN Rules PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first

Blockchain Security Solutions Deployment How Fraudsters Attack Blockchain Network Sample PDF
This slide describes the primary attacks that hackers can use to exploit blockchain technology networks. The purpose of this slide is to showcase some basic threats that hackers can use to manipulate a blockchain network, such as phishing attacks, routing attacks, sybil, and 51 percent. Present like a pro with Blockchain Security Solutions Deployment How Fraudsters Attack Blockchain Network Sample PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Employee Questionnaire To Assess IT Security Awareness Training Program Effectiveness Graphics PDF
This slide covers employee questionnaire to assess cybersecurity training program effectiveness. It involves questions to determine trainer effectiveness in teaching, knowledge and skills of trainer and details about training organization. Showcasing this set of slides titled Employee Questionnaire To Assess IT Security Awareness Training Program Effectiveness Graphics PDF. The topics addressed in these templates are Good Knowledge, Cyberattacks And Methods, Awareness Training. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

SDN Security Architecture Why Is An Software Defined Network Used Themes PDF
This slide depicts why the software defined network is used, including the increase in sales, excellent customer service, reduction in expenses, and less hardware is used, making room for more space and less power consumption. Present like a pro with SDN Security Architecture Why Is An Software Defined Network Used Themes PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Structured Networking Process Diagram 7 Stages Ppt Security Business Plan PowerPoint Slides
We present our structured networking process diagram 7 stages ppt security business plan PowerPoint Slides.Download our Business PowerPoint Templates because It will get your audience in sync. Use our Network Diagrams PowerPoint Templates because Our PowerPoint Templates and Slides will let you meet your Deadlines. Present our Shapes PowerPoint Templates because You can Hit a home run with our PowerPoint Templates and Slides. See your ideas sail into the minds of your audience. Download and present our Circle Charts PowerPoint Templates because Your ideas provide food for thought. Our PowerPoint Templates and Slides will help you create a dish to tickle the most discerning palate. Download our Curves and Lines PowerPoint Templates because Our PowerPoint Templates and Slides are topically designed to provide an attractive backdrop to any subject.Use these PowerPoint slides for presentations relating to art, business, button, chart, clip, communication, design, diagram, element, graph, graphic, green, icon, illustration, isolated, network, process, round, set, shape, shiny, symbol, teamwork, vector, web. The prominent colors used in the PowerPoint template are Gray, White, Black.
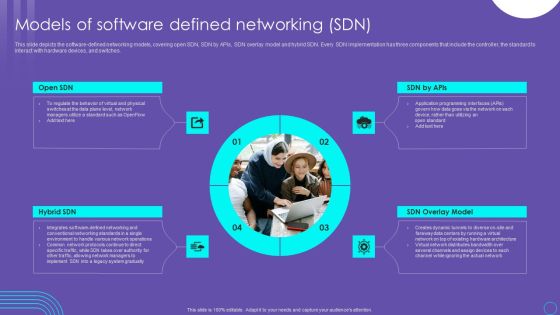
SDN Security Architecture Models Of Software Defined Networking SDN Slides PDF
This slide depicts the software defined networking models, covering open SDN, SDN by APIs, SDN overlay model and hybrid SDN. Every SDN implementation has three components that include the controller, the standard to interact with hardware devices, and switches. Do you know about Slidesgeeks SDN Security Architecture Models Of Software Defined Networking SDN Slides PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

SDN Security Architecture Role Of SDN In Edge Computing Iot And Remote Access Information PDF
This slide represents the role of software defined networking in edge computing, IoT, and remote locations to make them more accessible and less expensive. Smart SDN controllers detect network congestion and, in response, increase the bandwidth for remote and edge devices. Boost your pitch with our creative SDN Security Architecture Role Of SDN In Edge Computing Iot And Remote Access Information PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

SDN Security Architecture How SDN Can Have A Significant Impact On A Business Mockup PDF
This slide depicts the four critical areas where SDN can make a difference in an organization, such as network programmability, centralized intelligence and control, abstraction of the network, and openness. Welcome to our selection of the SDN Security Architecture How SDN Can Have A Significant Impact On A Business Mockup PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today

Keys Tied To Chain Security PowerPoint Templates Ppt Background For Slides 1112
We present our Keys Tied To Chain Security PowerPoint Templates PPT Background For Slides 1112.Use our Business PowerPoint Templates because, Spell out your advertising plans to increase market share. The feedback has been positive and productive Use our Success PowerPoint Templates because,This Slide offers an excellent background to build up the various stages of your business process. Use our Chains PowerPoint Templates because,Our PowerPoint templates designed for your ideas to sell. Use our Finance PowerPoint Templates because,Let this slide illustrates others piggyback on you to see well over the horizon Use our Marketing PowerPoint Templates because,Networking is an imperative in todays world. You need to access the views of others. Similarly you need to give access to them of your abilitiesUse these PowerPoint slides for presentations relating to Keys tied to chain, business, success, chains, finance, marketing. The prominent colors used in the PowerPoint template are Yellow, Brown, White

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Measures And Ways To Mitigate Rules PDF
This slide provides information about the ways and measures through which the company and security monitoring managers can overcome the problems and issues related to Security Monitoring. Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach measures and ways to mitigate rules pdf. Use them to share invaluable insights on measures and ways to mitigate security monitoring challenges and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

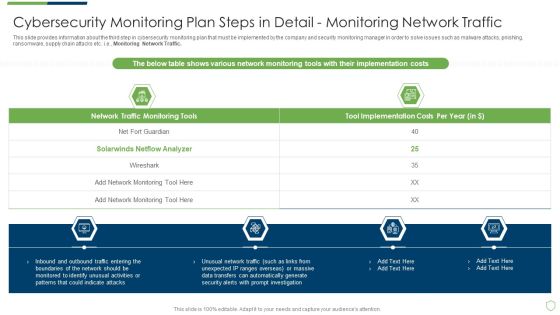
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps In Detail Fine Sample PDF
This slide provides information about the third step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Monitoring Network Traffic. Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps in detail fine sample pdf. Use them to share invaluable insights on cybersecurity monitoring plan steps in detail monitoring network traffic and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps In Detail Providing Sample PDF
This slide provides information about the second step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Monitoring All Systems. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps in detail providing sample pdf bundle. Topics like cybersecurity monitoring plan steps in detail monitoring all systems can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
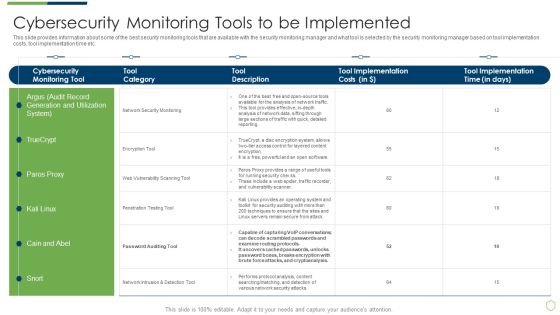
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Tools To Be Implemented Portrait PDF
This slide provides information about the fourth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Monitoring User Activity. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring tools to be implemented portrait pdf bundle. Topics like cybersecurity monitoring plan steps in detail monitoring user activity can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Detail Impact Information Security Plan Can Reduce The Risk Of Data Breach Ppt PowerPoint Presentation File Visual Aids PDF
This slide represents the current status of the cyber attacks in an organization after implementing the cyber security model. Deliver an awe inspiring pitch with this creative detail impact information security plan can reduce the risk of data breach ppt powerpoint presentation file visual aids pdf bundle. Topics like phishing breakdown, network intrusion breakdown, inadvertent desclosure can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Detail Impact IT Security IT Plan Can Reduce The Risk Of Data Breach In Organization Ppt Infographic Template Objects PDF
This slide represents the current status of the cyber attacks in an organization after implementing the cyber security model. Deliver and pitch your topic in the best possible manner with this detail impact it security it plan can reduce the risk of data breach in organization ppt infographic template objects pdf. Use them to share invaluable insights on detail impact it security it plan can reduce the risk of data breach in organization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps In Detail Structure PDF
This slide provides information about the sixth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Setting up a Centralized Collection and Analysis Capability. This is a modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps in detail structure pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail setting up a centralized collection and analysis capability. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Global Cyber Terrorism Incidents On The Rise IT How To Protect Company From Trojan Attacks Summary PDF
This slide explains how to protect the company from trojan attacks which include procedures such as installing advanced antivirus software. This is a global cyber terrorism incidents on the rise it how to protect company from trojan attacks summary pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like install a good antivirus programm, web application firewall waf, stick to reliable sources, avoid third party downloads. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
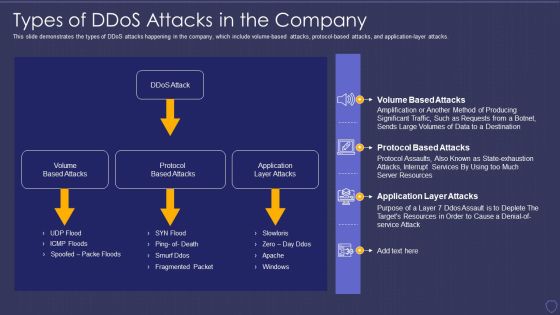
Global Cyber Terrorism Incidents On The Rise IT Types Of Ddos Attacks In The Company Elements PDF
This slide demonstrates the types of DDoS attacks happening in the company, which include volume-based attacks, protocol-based attacks, and application-layer attacks. Deliver and pitch your topic in the best possible manner with this global cyber terrorism incidents on the rise it types of ddos attacks in the company elements pdf. Use them to share invaluable insights on volume based attacks, protocol based attacks, application layer attacks and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

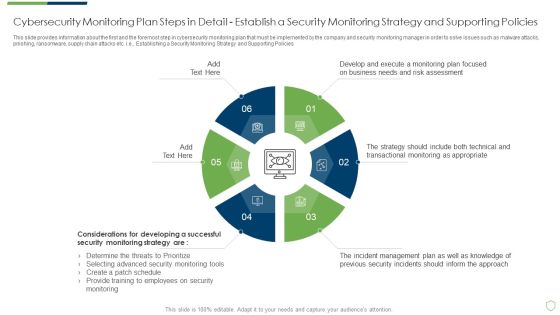
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps In Professional PDF
This slide provides information about the first and the foremost step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Establishing a Security Monitoring Strategy and Supporting Policies. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps in professional pdf bundle. Topics like cybersecurity monitoring plan steps in detail establish a security monitoring strategy and supporting policies can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
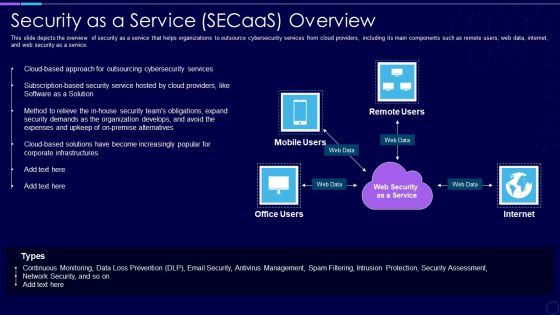
Everything As A Service Xaas For Cloud Computing IT Security As A Service Secaas Overview Portrait PDF
This slide depicts the overview of security as a service that helps organizations to outsource cybersecurity services from cloud providers, including its main components such as remote users, web data, internet, and web security as a service. Presenting everything as a service xaas for cloud computing it security as a service secaas overview portrait pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like expenses, security, organization, services, management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security As A Service Secaas Overview Xaas Cloud Computing Models Ppt PowerPoint Presentation Outline Slide Download PDF
This slide depicts the overview of security as a service that helps organizations to outsource cybersecurity services from cloud providers, including its main components such as remote users, web data, internet, and web security as a service.Deliver and pitch your topic in the best possible manner with this Security As A Service Secaas Overview Xaas Cloud Computing Models Ppt PowerPoint Presentation Outline Slide Download PDF. Use them to share invaluable insights on Outsourcing Cybersecurity, Software Solution, Expenses Upkeep and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
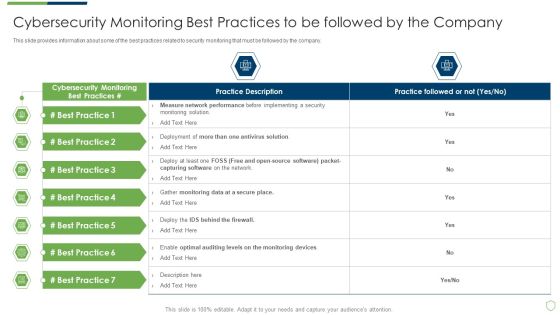
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Best Practices Introduction PDF
This slide provides information about some of the best practices related to security monitoring that must be followed by the company. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring best practices introduction pdf bundle. Topics like cybersecurity monitoring best practices to be followed by the company can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
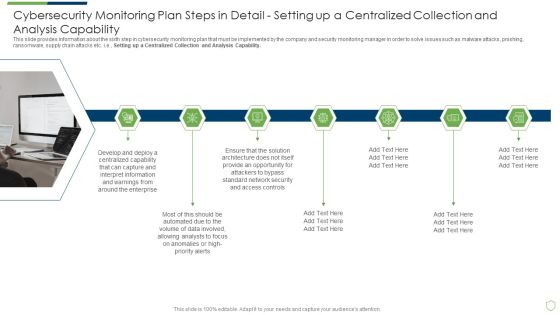
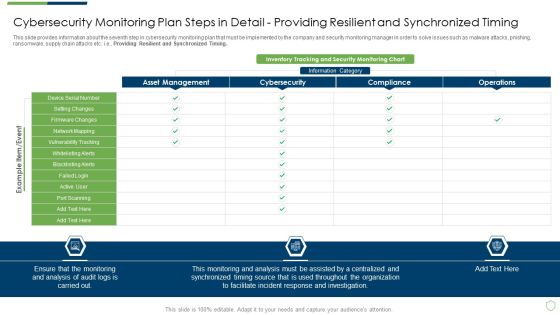
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps In Detail Setting Brochure PDF
This slide provides information about the seventh step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Providing Resilient and Synchronized Timing. Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps in detail setting brochure pdf. Use them to share invaluable insights on cybersecurity monitoring plan steps in detail providing resilient and synchronized timing and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps Elements PDF
This slide provides information about the ninth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Review and Risk Analysis. Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps elements pdf. Use them to share invaluable insights on cybersecurity monitoring plan steps in detail review and risk analysis and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Ppt PowerPoint Presentation Complete Deck With Slides
Pitch yourself both in house and outside by utilizing this complete deck. This modern security observation plan to eradicate cybersecurity risk and data breach ppt powerpoint presentation complete deck with slides focuses on key fundamentals of the topic, displayed using different slides. With a total of fourty six slides, this template is the best tool you can use to persuade your audience. It will not only help you create great presentations but also induce strategic thinking because of its well researched content and graphics. You can easily personalize any of the elements to suit your unique business setting. Additionally, it can be saved in PNG, JPG, and PDF formats to save your time and resources.
Marketing Strategy Ppt Powerpoint Presentation Styles Show
This is a marketing strategy ppt powerpoint presentation styles show. This is a seven stage process. The stages in this process are marketing strategy, social media, email marketing, paid advertising.

Marketing Strategy Ppt PowerPoint Presentation File Formats
This is a marketing strategy ppt powerpoint presentation file formats. This is a six stage process. The stages in this process are website design, blog, social media, paid advertising, email marketing.
Marketing Strategy Ppt PowerPoint Presentation Clipart
This is a marketing strategy ppt powerpoint presentation clipart. This is a six stage process. The stages in this process are social media marketing, search engine, blogging, email marketing, conversion analysis.

Marketing Strategy Ppt PowerPoint Presentation Portfolio Inspiration
This is a marketing strategy ppt powerpoint presentation portfolio inspiration. This is a seven stage process. The stages in this process are paid advertising, analytics and reporting, email marketing, social media blog, website design, search engine optimization.
Marketing Strategy Ppt PowerPoint Presentation Layouts Background
This is a marketing strategy ppt powerpoint presentation layouts background. This is a seven stage process. The stages in this process are social media, email marketing, analytics and reporting, paid advertising, search engine optimization, website design, blog.
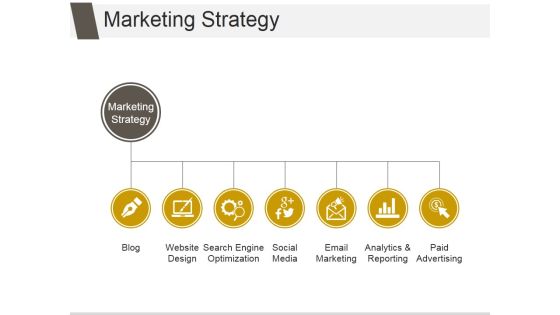
Marketing Strategy Ppt PowerPoint Presentation Summary
This is a marketing strategy ppt powerpoint presentation summary. This is a seven stage process. The stages in this process are blog, website design, search engine optimization, social media, email marketing, analytics and reporting, paid advertising.

Acquisition Marketing Strategy Powerpoint Slide Deck
This is a acquisition marketing strategy powerpoint slide deck. This is a six stage process. The stages in this process are seo, social news, social networks, blog, market research, analytics, clients visit web presence, leads, crm, email campaign, customer relationship management, call center.
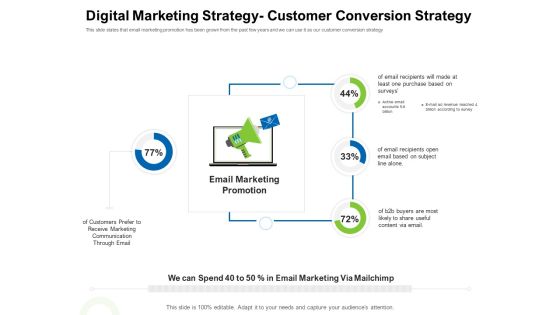
Strategies To Enter Physical Fitness Club Business Digital Marketing Strategy Customer Conversion Strategy Pictures PDF
This slide states that email marketing promotion has been grown from the past few years and we can use it as our customer conversion strategy Presenting strategies to enter physical fitness club business digital marketing strategy customer conversion strategy pictures pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like email, marketing, promotion, communication, buyers. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Email Strategy Analysis Diagram Powerpoint Guide
This is a email strategy analysis diagram powerpoint guide. This is a eight stage process. The stages in this process are evaluate results, implement, create creative solution, action findings, strategy, brief, research, identify need, develop strategy.

Customize Email Marketing Strategy Ppt Presentation
This is a customize email marketing strategy ppt presentation. This is a three stage process. The stages in this process are marketing plan and budget, marketing campaigns, website.

Email Marketing Strategy Diagram Ppt Presentation Examples
This is a email marketing strategy diagram ppt presentation examples. This is a six stage process. The stages in this process are segmentation, list creation and management, analysis and reporting, email marketing, marketing goals, design, deliverability.
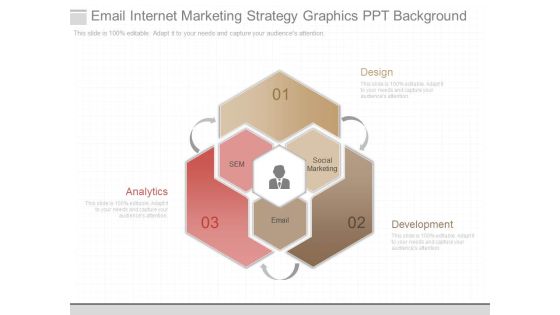
Email Internet Marketing Strategy Graphics Ppt Background
This is a email internet marketing strategy graphics ppt background. This is a three stage process. The stages in this process are design, analytics, development, sem, social marketing, email.

Consumer Email Strategy Diagram Ppt Example
This is a consumer email strategy diagram ppt example. This is a five stage process. The stages in this process are build and grow your list, create targeted segments, create personalize send, nurture your leads, measure impact.

Marketing With Email Strategy Ppt Sample
This is a marketing with email strategy ppt sample. This is a nine stage process. The stages in this process are campaign objectives, define kpls, professionally designed emails, professionally designed landing pages, contact management, list segmentation and targeted, website integration, crm integration, full metrics objectives.

Social Media Marketing Strategy Good Ppt Examples
This is a social media marketing strategy good ppt examples. This is a four stage process. The stages in this process are internet, email, you tube, twitter, social media marketing strategy.\n\n
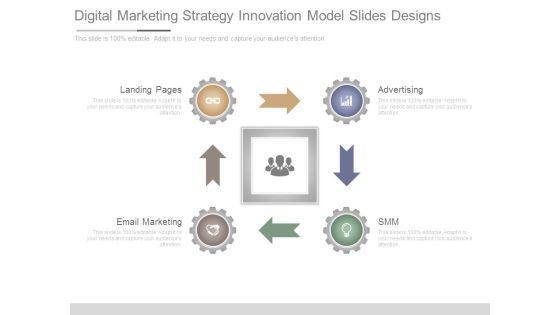
Digital Marketing Strategy Innovation Model Slides Designs
This is a digital marketing strategy innovation model slides designs. This is a four stage process. The stages in this process are landing pages, advertising, smm, email marketing.
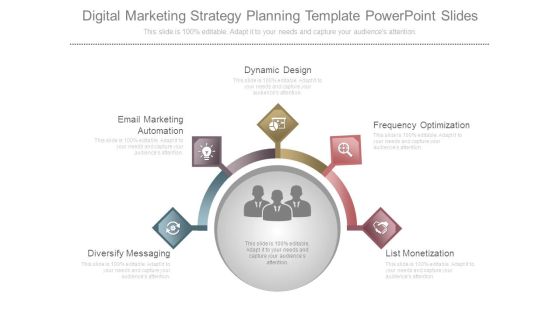
Digital Marketing Strategy Planning Template Powerpoint Slides
This is a digital marketing strategy planning template powerpoint slides. This is a five stage process. The stages in this process are dynamic design, frequency optimization, list monetization, diversify messaging, email marketing automation.
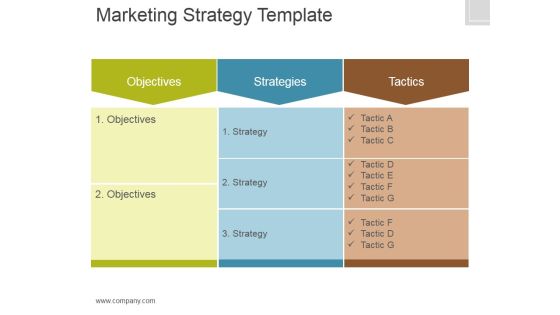
Marketing Strategy Template Ppt PowerPoint Presentation Model
This is a marketing strategy template ppt powerpoint presentation model. This is a seven stage process. The stages in this process are search engine optimization, website design, social media, blog, paid advertising, analytics and reporting, email marketing.

Rethinking Brand Strategy Toolkit Ppt Example
This is a rethinking brand strategy toolkit ppt example. This is a four stage process. The stages in this process are email marketing solution, contact list management, automatic follow up emails, campaign tracking and reporting.

360 Degree Of Marketing Strategy Ppt Diagram
This is a 360 degree of marketing strategy ppt diagram. This is a eight stage process. The stages in this process are corporate brochures collateral print, website, trade shows, email, social media, your audience, direct mail, mobile, direct sales.
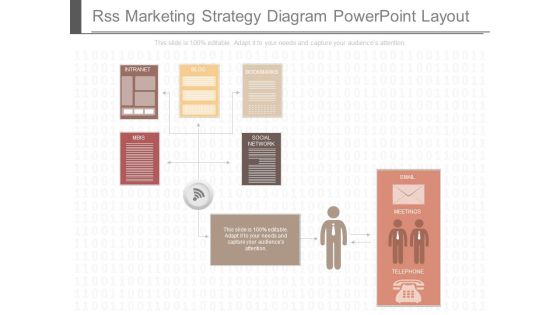
Rss Marketing Strategy Diagram Powerpoint Layout
This is a rss marketing strategy diagram powerpoint layout. This is a one stage process. The stages in this process are intranet, blog, bookmarks, mbis, social network, email, meetings, telephone.
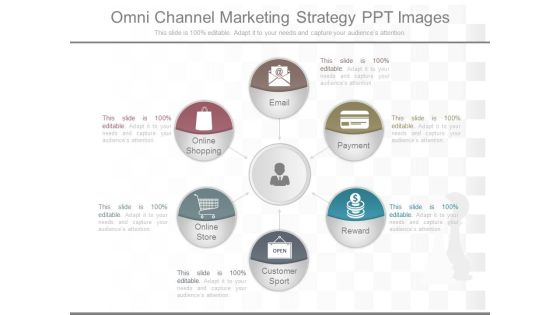
Omni Channel Marketing Strategy Ppt Images
This is a omni channel marketing strategy ppt images. This is a six stage process. The stages in this process are email, payment, reward, customer sport, online store, online shopping.

Factors Of Digital Marketing Strategy Ppt Sample
This is a factors of digital marketing strategy ppt sample. This is a eight stage process. The stages in this process are display, content marketing, content, mobile, social, paid search, website marketing, email marketing, mobile marketing.

 Home
Home