Cyber Security Risk Assess

Cybersecurity Risk Administration Plan Impact Assessment Matrix Graphics PDF
Deliver and pitch your topic in the best possible manner with this Cybersecurity Risk Administration Plan Impact Assessment Matrix Graphics PDF Use them to share invaluable insights on Minor To No Infringement, Suspected Malicious Intent, Operational and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cybersecurity Risk Assessment And Administration Plan Template PDF
Find a pre-designed and impeccable Cybersecurity Risk Assessment And Administration Plan Template PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

SWOT Analysis Cybersecurity Risk Assessment And Administration Plan Summary PDF
Want to ace your presentation in front of a live audience Our SWOT Analysis Cybersecurity Risk Assessment And Administration Plan Summary PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.
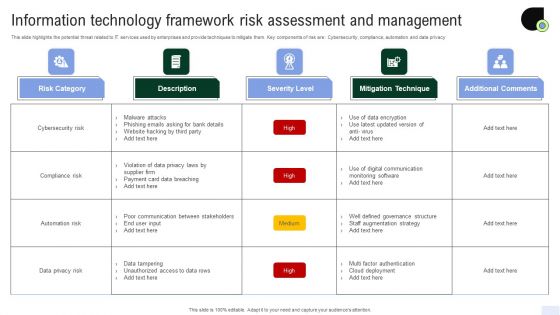
Information Technology Framework Risk Assessment And Management Diagrams PDF

Financial Cybersecurity Risk Assessment And Administration Plan Professional PDF
The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 parcent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Financial Cybersecurity Risk Assessment And Administration Plan Professional PDF from Slidegeeks and deliver a wonderful presentation.
Roadmap Cybersecurity Risk Assessment And Administration Plan Themes PDF
Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Roadmap Cybersecurity Risk Assessment And Administration Plan Themes PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Agenda For Cybersecurity Risk Assessment And Administration Plan Introduction PDF
Welcome to our selection of the Agenda For Cybersecurity Risk Assessment And Administration Plan Introduction PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 parcent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

Magnifier Cybersecurity Risk Assessment And Administration Plan Portrait PDF
Presenting this PowerPoint presentation, titled Magnifier Cybersecurity Risk Assessment And Administration Plan Portrait PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this ZZZZZZZZZZZZZZZZZZ. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable ZZZZZZZZZZZZZZZZZZ that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
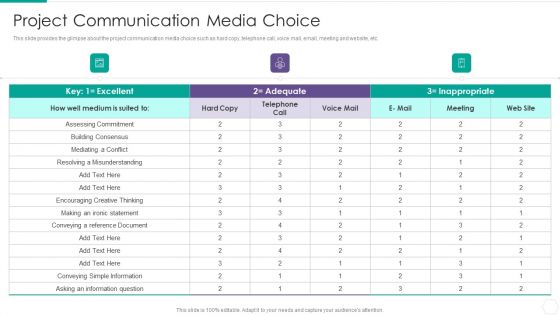
Quantitative Risk Assessment Project Communication Media Choice Inspiration PDF
This slide provides the glimpse about the project communication media choice such as hard copy, telephone call, voice mail, email, meeting and website, etc. Deliver an awe inspiring pitch with this creative Quantitative Risk Assessment Project Communication Media Choice Inspiration PDF bundle. Topics like Project Communication Media Choice can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
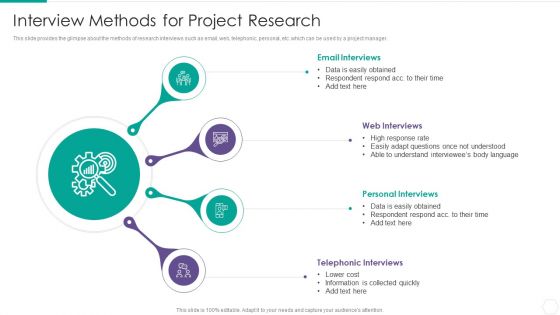
Quantitative Risk Assessment Interview Methods For Project Research Summary PDF
This slide provides the glimpse about the methods of research interviews such as email, web, telephonic, personal, etc. which can be used by a project manager. Presenting Quantitative Risk Assessment Interview Methods For Project Research Summary PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Email Interviews, Web Interviews, Personal Interviews, Telephonic Interviews. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Seven Steps Of Incident Response Digital Risk Assessment Cycle Ppt Portfolio Introduction PDF
The following slide highlights the sevens steps of incident cyber security cycle illustrating detection, communication channel, impact assessment, communication, escalation, delegation and resolution, Persuade your audience using this Seven Steps Of Incident Response Digital Risk Assessment Cycle Ppt Portfolio Introduction PDF. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including Resolution, Detection, Communication Channels, Impact Assessment. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Handling Cyber Threats Digital Era Employee Upskilling Training Program Ppt Professional Master Slide
Mentioned slide displays a five day employee upskilling training program that company will use to provide an in-dept details about information security program activities and deliverables. This is a handling cyber threats digital era employee upskilling training program ppt professional master slide template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like assess security requirements, perform a gap analysis, develop gap initiatives. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Analysis Brochure PDF
This slide provides information about the ninth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Review and Risk Analysis. Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring analysis brochure pdf bundle. Topics like cybersecurity monitoring plan steps in detail review and risk analysis can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
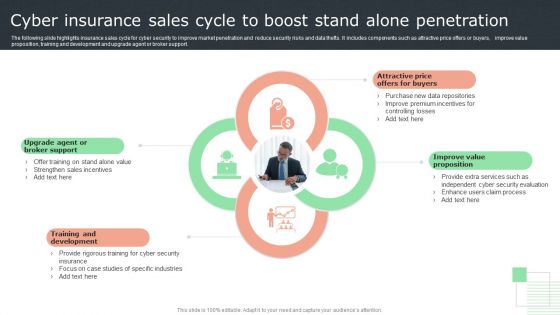
Cyber Insurance Sales Cycle To Boost Stand Alone Penetration Topics PDF
The following slide highlights insurance sales cycle for cyber security to improve market penetration and reduce security risks and data thefts. It includes components such as attractive price offers or buyers, improve value proposition, training and development and upgrade agent or broker support. Presenting Cyber Insurance Sales Cycle To Boost Stand Alone Penetration Topics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Broker Support, Development, Proposition. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

The Ultimate Guide To KPMG Other Cyber Strategies Of KPMG For Client Data Strategy SS V
This slide covers cyber strategies to protect KPMG customer data protection. The purpose of this template is to provide an overview on top techniques to be implemented to save clients data. It includes strategies such as developing comprehensive understanding of cyber threat landscape, implementing risk based approach, establishing robust security governance framework, etc. Take your projects to the next level with our ultimate collection of The Ultimate Guide To KPMG Other Cyber Strategies Of KPMG For Client Data Strategy SS V. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest

Table Of Contents For Info Security Wd Ppt PowerPoint Presentation Gallery Maker PDF
Presenting table of contents for info security wd ppt powerpoint presentation gallery maker pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like cyber risk assessment, steps for mitigation, cyber risk identification, key elements of information security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Measures And Ways To Mitigate Template PDF
This slide provides information about the ways and measures through which the company and security monitoring managers can overcome the problems and issues related to Security Monitoring. Deliver and pitch your topic in the best possible manner with this continuous development evaluation plan eliminate cyber attacks measures and ways to mitigate template pdf. Use them to share invaluable insights on malware attacks, pnishing attacks, ransomware and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
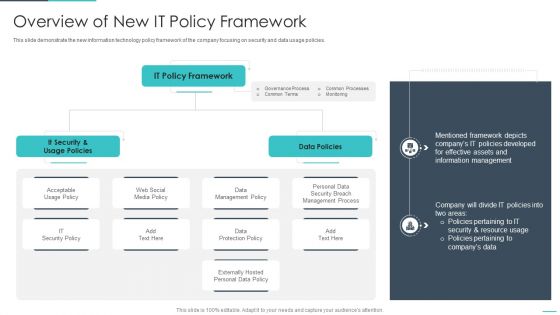
Handling Cyber Threats Digital Era Overview Of New IT Policy Framework Ppt Summary Guidelines PDF
This slide demonstrate the new information technology policy framework of the company focusing on security and data usage policies. Deliver and pitch your topic in the best possible manner with this handling cyber threats digital era overview of new it policy framework ppt summary guidelines pdf. Use them to share invaluable insights on overview of new it policy framework and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Digitalization Of Operative Enterprises Launch Of Cyber IT OT Strategy Themes PDF
This slide covers IT or OT cyber security strategy and approaches such as raining of an internal employee in cybersecurity, from the OT side, to keep the near job relation to OT teams etc. Presenting Digitalization Of Operative Enterprises Launch Of Cyber IT OT Strategy Themes PDF to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like Cybersecurity, Cyber Risk, Process Of Evaluating. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
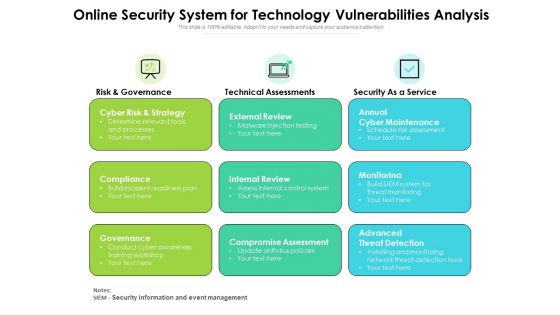
Online Security System For Technology Vulnerabilities Analysis Ppt PowerPoint Presentation Ideas Design Ideas PDF
Presenting this set of slides with name online security system for technology vulnerabilities analysis ppt powerpoint presentation ideas design ideas pdf. This is a three stage process. The stages in this process are cyber risk and strategy, compliance governance, external review, internal review, compromise assessment, annual cyber maintenance, monitorinag, advanced threat detection. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
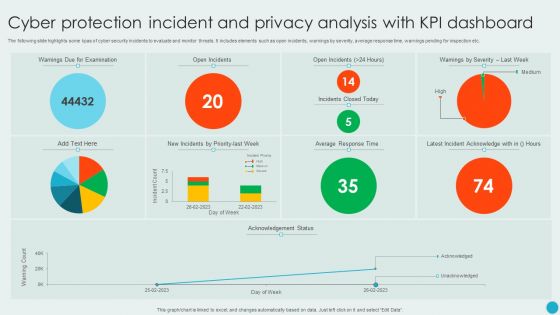
Cyber Protection Incident And Privacy Analysis With KPI Dashboard Ideas PDF
The following slide highlights some kpas of cyber security incidents to evaluate and monitor threats. It includes elements such as open incidents, warnings by severity, average response time, warnings pending for inspection etc. Showcasing this set of slides titled Cyber Protection Incident And Privacy Analysis With KPI Dashboard Ideas PDF. The topics addressed in these templates are Cyber Protection Incident, Privacy Analysis, KPI Dashboard. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
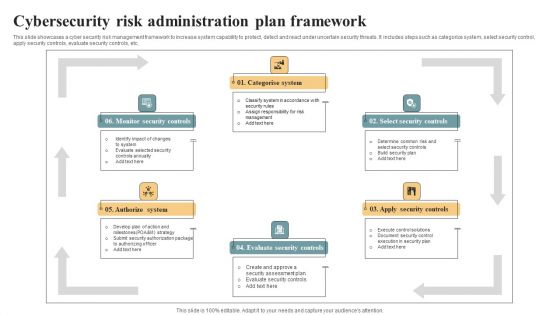
Cybersecurity Risk Administration Plan Framework Ideas PDF
This slide showcases a cyber security risk management framework to increase system capability to protect, detect and react under uncertain security threats. It includes steps such as categorize system, select security control, apply security controls, evaluate security controls, etc. Presenting Cybersecurity Risk Administration Plan Framework Ideas PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Categorise System, Select Security Controls, Apply Security Controls. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Business Threats Landscape Dashboard With Cyber Attacks Analysis Ppt Summary Brochure PDF
This slide illustrates risk landscape dashboard with cyber attacks analysis which contains malware attack frequency, country wise attacks, top 10 attacks, etc. It can assist IT managers in analyzing top threats so that they can be dealt with proper efficiency. Pitch your topic with ease and precision using this Business Threats Landscape Dashboard With Cyber Attacks Analysis Ppt Summary Brochure PDF. This layout presents information on Malware Attack Frequency, Every Minute, Every Second. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
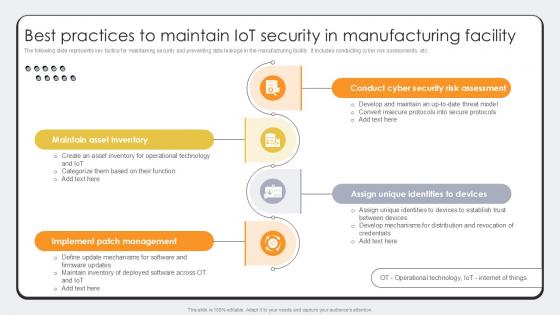
Best Practices To Maintain IoT Security Revolutionizing Production IoT Ppt Template
The following slide represents key tactics for maintaining security and preventing data leakage in the manufacturing facility. It includes conducting cyber risk assessments, etc. There are so many reasons you need a Best Practices To Maintain IoT Security Revolutionizing Production IoT Ppt Template. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Assessing Cost Of Information Breach In Different Countries Cybersecurity Risk Assessment Background PDF
Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Assessing Cost Of Information Breach In Different Countries Cybersecurity Risk Assessment Background PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
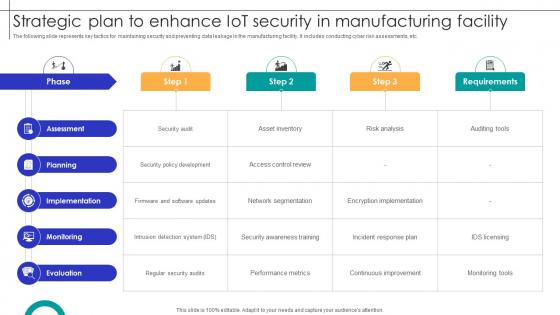
Strategic Plan To Enhance IOT Security In Manufacturing Facility Streamlining Production Ppt Sample
The following slide represents key tactics for maintaining security and preventing data leakage in the manufacturing facility. It includes conducting cyber risk assessments, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Strategic Plan To Enhance IOT Security In Manufacturing Facility Streamlining Production Ppt Sample for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Benefits Of Cloud Access Security Broker Ppt PowerPoint Presentation File Model PDF
This slide outlines the different advantages of cloud access security broker technology. This slide highlights the pros of CASB technology, including risk visibility, cyber threat prevention, granular cloud usage control, shadow IT assessment and management, DLP, managing privileged accounts and admin and controlled data sharing. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Benefits Of Cloud Access Security Broker Ppt PowerPoint Presentation File Model PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Benefits Of Cloud Access Security Broker Ppt PowerPoint Presentation File Model PDF.
Kpi Dashboard For Tracking Virtual Security Hazards Of Healthcare Organization Professional Pdf
This slide depicts dashboard for tracking cyber security risks faced by healthcare organizations to effectively manage the major threats and take action accordingly. The key performing indicators are percentage of risks exceeding threshold limit, breakdown of threat rating, action plan etc. Showcasing this set of slides titled Kpi Dashboard For Tracking Virtual Security Hazards Of Healthcare Organization Professional Pdf. The topics addressed in these templates are Analysis Progress, Resolution Progress, Threshold Limit. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Implementing Cybersecurity Awareness Program To Prevent Attacks Evaluating IT System Security Formats PDF
The purpose of this slide is to outline the strength, weakness, opportunities and threat SWOT evaluation of organization cyber security. Organization can detect the potential risks and opportunities in the cyber security using SWOT model. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Implementing Cybersecurity Awareness Program To Prevent Attacks Evaluating IT System Security Formats PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Implementing Cybersecurity Awareness Program To Prevent Attacks Evaluating IT System Security Formats PDF today and make your presentation stand out from the rest.

Prevention Of Information Evaluating IT System Security Using Swot Analysis Download PDF
The purpose of this slide is to outline the strength, weakness, opportunities and threat SWOT evaluation of organization cyber security. Organization can detect the potential risks and opportunities in the cyber security using SWOT model. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Prevention Of Information Evaluating IT System Security Using Swot Analysis Download PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Prevention Of Information Evaluating IT System Security Using Swot Analysis Download PDF today and make your presentation stand out from the rest
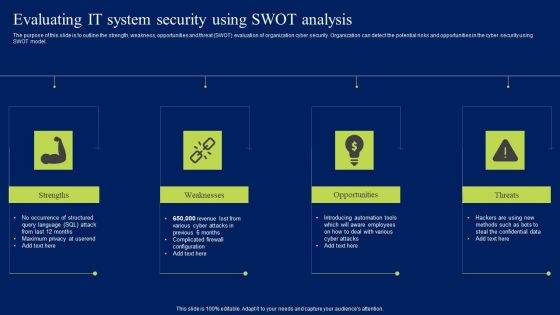
Evaluating IT System Security Using Swot Analysis Ppt Pictures Clipart Images PDF
The purpose of this slide is to outline the strength, weakness, opportunities and threat SWOT evaluation of organization cyber security. Organization can detect the potential risks and opportunities in the cyber security using SWOT model. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Evaluating IT System Security Using Swot Analysis Ppt Pictures Clipart Images PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Evaluating IT System Security Using Swot Analysis Ppt Pictures Clipart Images PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today
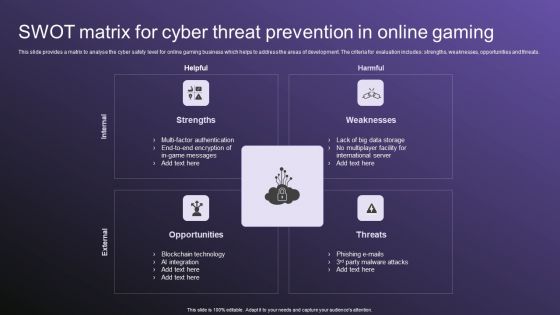
SWOT Matrix For Cyber Threat Prevention In Online Gaming Download PDF
This slide provides a matrix to analyse the cyber safety level for online gaming business which helps to address the areas of development. The criteria for evaluation includes strengths, weaknesses, opportunities and threats. Persuade your audience using this SWOT Matrix For Cyber Threat Prevention In Online Gaming Download PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Strengths, Weaknesses, Threats. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
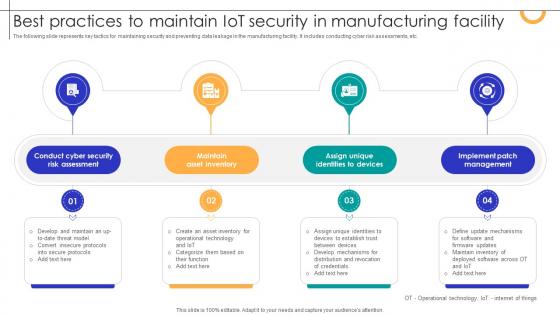
Best Practices To Maintain IOT Security In Manufacturing Facility Streamlining Production Ppt Template
The following slide represents key tactics for maintaining security and preventing data leakage in the manufacturing facility. It includes conducting cyber risk assessments, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Best Practices To Maintain IOT Security In Manufacturing Facility Streamlining Production Ppt Template With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Best Practices To Maintain IOT Security In Manufacturing Facility Streamlining Production Ppt Template today and make your presentation stand out from the rest

Aftereffects Of IT Security Threats On Business And Customers Ppt PowerPoint Presentation Layouts Background PDF
Persuade your audience using this aftereffects of it security threats on business and customers ppt powerpoint presentation layouts background pdf. This PPT design covers two stages, thus making it a great tool to use. It also caters to a variety of topics including violation of law, crucial information loss, loss of productivity, cyber espionage, risk of losing work in future, contract breach, trust among business people, ransom ware, online banking transactions are compromised, identity theft, credit card detail theft, spam mails or other attacks violates the law, fraud to customers by scare ware or other fraud tools. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Global Data Security Industry Report Growth Drivers Accelerating Cybersecurity Industry IR SS V
The purpose of the slide is to provide a comprehensive overview of the growth prospects in the cybersecurity market. It assists stakeholders to navigate the evolving landscape and make informed strategic decisions. It includes various growth factors such as increasing cyber threats, digital transformation, zero trust architecture, cyber insurance, IoT devices. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Global Data Security Industry Report Growth Drivers Accelerating Cybersecurity Industry IR SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Global Data Security Industry Report Growth Drivers Accelerating Cybersecurity Industry IR SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers

Information And Digital Risk Assessment Policy Development Ppt Portfolio Slideshow PDF
The following slide highlights the information and cyber security policy development by depicting purpose, audience, information security, access control, data segregation, data support, security awareness and responsibilities. Presenting Information And Digital Risk Assessment Policy Development Ppt Portfolio Slideshow PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Responsibilities, Security Awareness, Data Support, Data Segregation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Project Security Administration IT Various Ways To Manage Project Safety By Managing Threats Designs PDF
This slide provides information regarding various ways to handle threats to ensure project safety in terms of periodic risk assessment, end user informing, etc. Presenting project security administration it various ways to manage project safety by managing threats designs pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like track baseline behavior, networks and individuals, inform end user, periodic risk assessment, render least amount of privilege. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Steps Of Digital Risk Assessment In Organisation Ppt Infographics Templates PDF
The following slide highlights the steps of cyber security in organisation depicting network security, awareness, malware, external media, configuration, user privilege, incident management, monitoring and distant working. Presenting Steps Of Digital Risk Assessment In Organisation Ppt Infographics Templates PDF to dispense important information. This template comprises nine stages. It also presents valuable insights into the topics including Network Security, Awareness, Malware, External Media. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
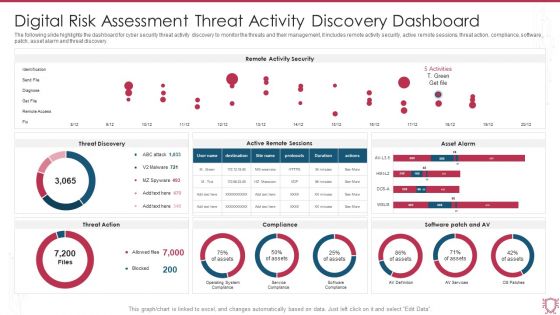
Digital Risk Assessment Threat Activity Discovery Dashboard Ppt Ideas Skills PDF
The following slide highlights the dashboard for cyber security threat activity discovery to monitor the threats and their management, it includes remote activity security, active remote sessions, threat action, compliance, software patch, asset alarm and threat discovery. Pitch your topic with ease and precision using this Digital Risk Assessment Threat Activity Discovery Dashboard Ppt Ideas Skills PDF. This layout presents information on Remote Activity Security, Threat Discovery, Asset Alarm. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Major Elements Of Internet Security Model Ppt PowerPoint Presentation Slides Mockup PDF
Pitch your topic with ease and precision using this major elements of internet security model ppt powerpoint presentation slides mockup pdf. This layout presents information on business strategy, enterprise risk and compliance, policy and procedures frameworks. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
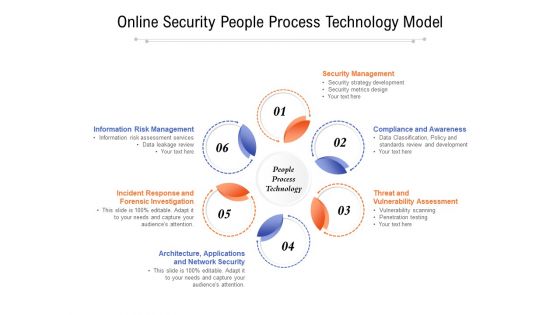
Online Security People Process Technology Model Ppt PowerPoint Presentation Slides Example Introduction PDF
Presenting online security people process technology model ppt powerpoint presentation slides example introduction pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including security management, compliance and awareness, threat and vulnerability assessment, architecture, applications, incident response and forensic investigation, information risk management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Integrating Chatgpt With Other Systems Security And Compliance Management Themes PDF
This slide provides information regarding the integration of ChatGPT with other systems for managing security and compliance in terms of fraud detection, handling cybersecurity, risk assessment and compliance monitoring. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Integrating Chatgpt With Other Systems Security And Compliance Management Themes PDF can be your best option for delivering a presentation. Represent everything in detail using Integrating Chatgpt With Other Systems Security And Compliance Management Themes PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Security Management Plan Steps In Detail Evaluating Information Processing Assets Template PDF
This slide provides information about the second step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Evaluating Information Processing Assets. Deliver an awe inspiring pitch with this creative security management plan steps in detail evaluating information processing assets template pdf bundle. Topics like information, network infrastructure, services, customer information can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
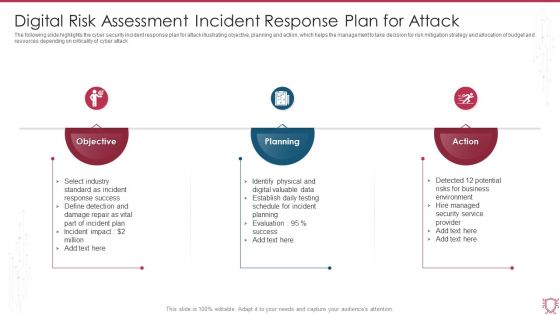
Digital Risk Assessment Incident Response Plan For Attack Ppt Backgrounds PDF
The following slide highlights the cyber security incident response plan for attack illustrating objective, planning and action, which helps the management to take decision for risk mitigation strategy and allocation of budget and resources depending on criticality of cyber attack. Persuade your audience using this Digital Risk Assessment Incident Response Plan For Attack Ppt Backgrounds PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Objective, Planning, Action. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Three Layers Of Digital Risk Assessment Management Process Ppt Summary Visual Aids PDF
The following slide highlights the three layers of cyber security management process which are dependent on people, process and technology, it helps company to manage cyber risks such as phishing attacks, data loss and exposed vulnerabilities. Presenting Three Layers Of Digital Risk Assessment Management Process Ppt Summary Visual Aids PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including People, Process, Technology. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Digital Risk Threat Assessment Checklist With Solution Ppt File Display PDF
The following slide highlights the cyber security threat assessment checklist with solution to assist management in decision making, id depicts threat, vulnerability, asset, consequences, risks and solution to control the risk. Showcasing this set of slides titled Digital Risk Threat Assessment Checklist With Solution Ppt File Display PDF. The topics addressed in these templates are System Threat, Data Threat, Cloud Security Threat. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
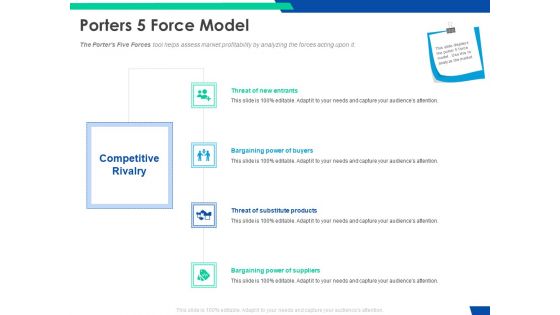
Cloud Based Email Security Market Report Porters 5 Force Model Ppt Inspiration Sample PDF
The Porters Five Forces tool helps assess market profitability by analyzing the forces acting upon it. This is a cloud based email security market report porters 5 force model ppt inspiration sample pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like threat of new entrants, bargaining power of buyers, threat of substitute products, bargaining power of suppliers. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Digital Risk Assessment Process For Cloud Services Ppt Pictures Topics PDF
The following slide highlights the cyber security process for cloud computing, cloud storage and cloud analytics storage. It depict identification, network security, data safety, application safety, monitoring and policy control to govern, protect and control the cloud services. Persuade your audience using this Digital Risk Assessment Process For Cloud Services Ppt Pictures Topics PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Identification, Data Safety, Monitoring, Policy Control. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Global Data Security Industry Report Key Considerations Assumptions Of Cybersecurity Industry Report IR SS V
The slide represents key considerations and limitations while building the cybersecurity industry report. The purpose of this slide is to provide framework and context for analysis and projections in addition to acknowledging uncertainties and potential risks in the future. Make sure to capture your audiences attention in your business displays with our gratis customizable Global Data Security Industry Report Key Considerations Assumptions Of Cybersecurity Industry Report IR SS V. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Phases Of Digital Risk Assessment Incident Response Cycle Ppt Gallery Format Ideas PDF
The following slide highlights the phase of cyber security incident response cycle depicting preparation phase, analysis phase, response phase, and post event phase. Persuade your audience using this Phases Of Digital Risk Assessment Incident Response Cycle Ppt Gallery Format Ideas PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Post Event Phase, Response Phase, Preparation Phase, Analysis Phase. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Conduct Third Party Risk Assessment Ppt PowerPoint Presentation File Ideas PDF
The following slide illustrates checklist to evaluate third party risk assessment to eliminate unnecessary threats. It includes elements such as cyber security policies, patch management process, physical security guidelines, information safety etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Conduct Third Party Risk Assessment Ppt PowerPoint Presentation File Ideas PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
Internet Security Threat Analysis Plan With Icons Ppt PowerPoint Presentation Ideas Influencers PDF
Pitch your topic with ease and precision using this internet security threat analysis plan with icons ppt powerpoint presentation ideas influencers pdf. This layout presents information on inspect, preliminary assessment, extended assessment. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Business Internet Security Threat Management And Compliance Framework Ppt PowerPoint Presentation Gallery Picture PDF
Presenting business internet security threat management and compliance framework ppt powerpoint presentation gallery picture pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including governance, risk, compliance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Global Data Security Industry Report Porters Framework Detailed Five Forces Analysis For Cybersecurity IR SS V
The slide highlights Porters framework and its implications in the cybersecurity industry. Evaluating the five forces can assist businesses in anticipating changes in the competition, influencing the evolution of industry structure, and finding more beneficial strategic positions. It covers the threat of new entrants and substitutes, competitive rivalry, and the bargaining power of suppliers and buyers. Welcome to our selection of the Global Data Security Industry Report Porters Framework Detailed Five Forces Analysis For Cybersecurity IR SS V. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

Upgrading Total Project Safety IT Determine Established Security Centre Overview Sample PDF
This slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. This is a upgrading total project safety it determine established security centre overview sample pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like incident response, forensics, threat intelligence, command and control, network security monitoring. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
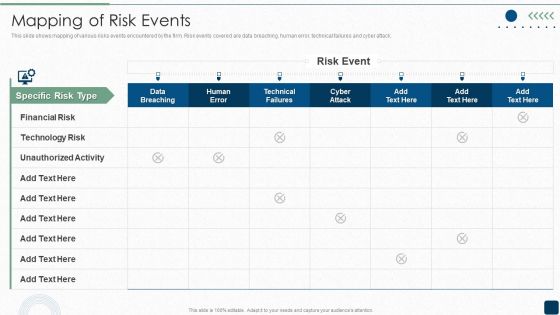
Mapping Of Risk Events Infographics PDF
This slide shows mapping of various risks events encountered by the firm. Risk events covered are data breaching, human error, technical failures and cyber attack.Deliver an awe inspiring pitch with this creative Mapping Of Risk Events Infographics PDF bundle. Topics like Financial Risk, Unauthorized Activity, Technology Risk can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Zero Trust Exchange Overview And Benefits Zero Trust Network Security Introduction Pdf
This slide provides an overview of zero trust exchange and its benefits. The purpose of this slide is to highlight the key advantages of zero trust exchange to businesses including enhancing user experience, reducing internet attacks and later threat movement, lowering costs and complexity, and so on. Want to ace your presentation in front of a live audience Our Zero Trust Exchange Overview And Benefits Zero Trust Network Security Introduction Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

About Traditional Firewalls Overview And Key Uses Network Security Brochure Pdf
This slide talks about the overview of firewall technology. The purpose of this slide is to illustrate the key uses of firewalls. These include protection against external and internal threats, conduct logging and auditing tasks, utilized by antivirus software, etc. Boost your pitch with our creative About Traditional Firewalls Overview And Key Uses Network Security Brochure Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
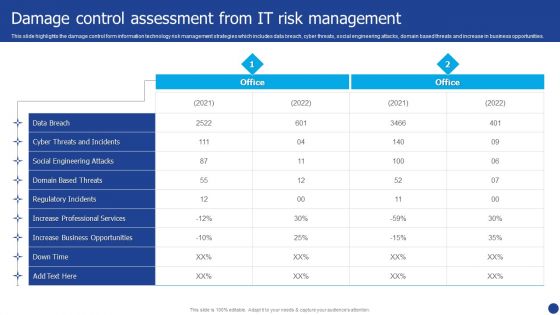
Information Technology Threat Mitigation Methods Damage Control Assessment From IT Risk Management Formats PDF
This slide highlights the damage control form information technology risk management strategies which includes data breach, cyber threats, social engineering attacks, domain based threats and increase in business opportunities. Deliver an awe inspiring pitch with this creative Information Technology Threat Mitigation Methods Damage Control Assessment From IT Risk Management Formats PDF bundle. Topics like Data Breach, Social Engineering Attacks, Cyber Threats can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Initiating Hazard Managing Structure Firm Operational Risk Assessment Worksheet Rules PDF
This slide illustrates operational risk assessment worksheet. Risk covered are monetary loss, reputation loss and loss of customer confidence. Deliver an awe-inspiring pitch with this creative initiating hazard managing structure firm operational risk assessment worksheet rules pdf bundle. Topics like business practices, cyber attack, internal fraud can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cybersecurity Online Risk Assessment Process To Enhance Data Protection Introduction PDF
The purpose of this slide is to represent a process for cybersecurity digital risk assessment to analyze business threats. It includes various stages such as classifying information assets, evaluating risks, examining risk, observing and reviewing effectiveness and implementing security controls. Presenting Cybersecurity Online Risk Assessment Process To Enhance Data Protection Introduction PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Classify Information Assets, Evaluate Risk, Examine Risk. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Risk Events Reporting And Likelihood Topics PDF
Mentioned slide shows encountered risk reporting and its likelihood. It includes information about risk encountered, frequency, reported by status, attack scenario, affected asset and likelihood. Deliver an awe inspiring pitch with this creative Risk Events Reporting And Likelihood Topics PDF bundle. Topics like Risk Encountered, Phishing Emails, Affected Asset can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Establishing Operational Risk Framework Banking Operational Risks Mapping Ppt File Icon PDF
This slide shows mapping of various operational risks under risk events. Risk events covered are internal fraud, external fraud, client and business practices and cyber attack. Deliver an awe-inspiring pitch with this creative establishing operational risk framework banking operational risks mapping ppt file icon pdf bundle. Topics like client and business practices, technology risk, transaction processing risk can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
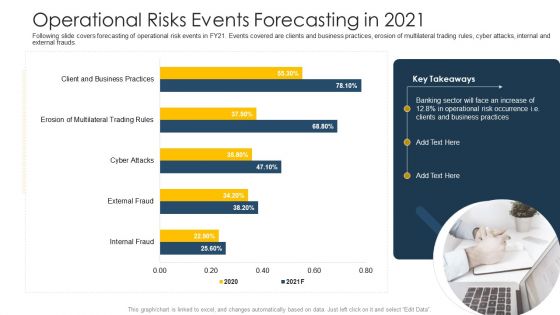
Establishing Operational Risk Framework Banking Operational Risks Events Forecasting In 2021 Portrait PDF
Following slide covers forecasting of operational risk events in FY21. Events covered are clients and business practices, erosion of multilateral trading rules, cyber attacks, internal and external frauds. Deliver and pitch your topic in the best possible manner with this establishing operational risk framework banking operational risks events forecasting in 2021 portrait pdf. Use them to share invaluable insights on business practices, operational risk and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Risk Assessment Software Dashboard For Cybersecurity Ppt PowerPoint Presentation Gallery Pictures PDF
This slide represents risk assessment software dashboard for cybersecurity. It includes risk percentage, number of risks, risk analysis progress, risk response progress, risk rating etc. Showcasing this set of slides titled Risk Assessment Software Dashboard For Cybersecurity Ppt PowerPoint Presentation Gallery Pictures PDF. The topics addressed in these templates are Risk Rating Breakdown, Action Plan Breakdown, Top 5 Entities Prone To Risk. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
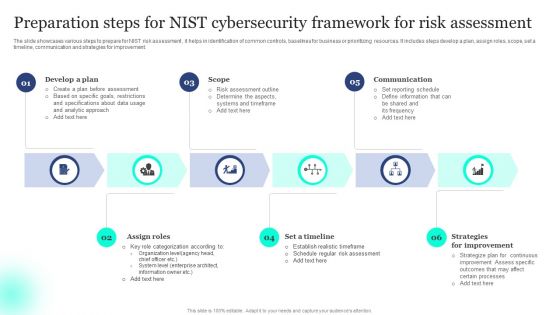
Preparation Steps For NIST Cybersecurity Framework For Risk Assessment Template PDF
The slide showcases various steps to prepare for NIST risk assessment , it helps in identification of common controls, baselines for business or prioritizing resources. It includes steps develop a plan, assign roles, scope, set a timeline, communication and strategies for improvement. Presenting Preparation Steps For NIST Cybersecurity Framework For Risk Assessment Template PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Scope, Communication, Improvement. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Thanks For Watching Cybersecurity Risk Assessment And Administration Plan Ideas PDF
Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Thanks For Watching Cybersecurity Risk Assessment And Administration Plan Ideas PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Thanks For Watching Cybersecurity Risk Assessment And Administration Plan Ideas PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Analysing The Impact On Assets Due To Information Breach Cybersecurity Risk Assessment Summary PDF
This slide showcases impact of information breach on different assets which can help organization in formulating risk monitoring policy. Its key components are criterion, criterion weight and information assets. Explore a selection of the finest Analysing The Impact On Assets Due To Information Breach Cybersecurity Risk Assessment Summary PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Analysing The Impact On Assets Due To Information Breach Cybersecurity Risk Assessment Summary PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
Icons Slide For Cybersecurity Risk Assessment And Administration Plan Brochure PDF
Download our innovative and attention grabbing Icons Slide For Cybersecurity Risk Assessment And Administration Plan Brochure PDF template. The set of slides exhibit completely customizable icons. These icons can be incorporated into any business presentation. So download it immediately to clearly communicate with your clientele.
Table Of Contents For Cybersecurity Risk Assessment And Administration Plan Microsoft PDF
There are so many reasons you need a Table Of Contents For Cybersecurity Risk Assessment And Administration Plan Microsoft PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
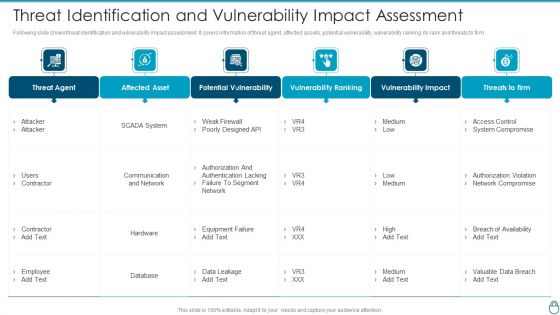
Cybersecurity Risk Administration Plan Threat Identification And Vulnerability Impact Assessment Slides PDF
Following slide shows threat identification and vulnerability impact assessment. It covers information of threat agent, affected assets, potential vulnerability, vulnerability ranking, its rank and threats to firm. Deliver an awe inspiring pitch with this creative Cybersecurity Risk Administration Plan Threat Identification And Vulnerability Impact Assessment Slides PDF bundle. Topics like Potential Vulnerability, Vulnerability Ranking, Vulnerability Impact can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
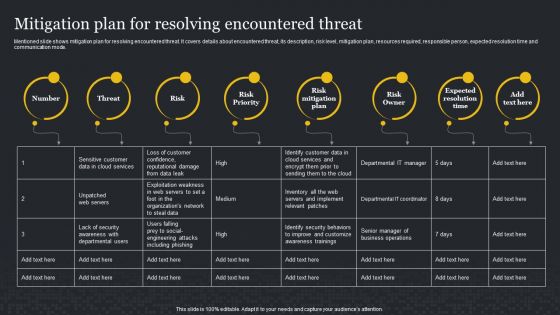
Mitigation Plan For Resolving Encountered Threat Cybersecurity Risk Assessment Demonstration PDF
Mentioned slide shows mitigation plan for resolving encountered threat. It covers details about encountered threat, its description, risk level, mitigation plan, resources required, responsible person, expected resolution time and communication mode. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Mitigation Plan For Resolving Encountered Threat Cybersecurity Risk Assessment Demonstration PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

30 60 90 Days Plan Cybersecurity Risk Assessment And Administration Plan Formats PDF
Make sure to capture your audiences attention in your business displays with our gratis customizable 30 60 90 Days Plan Cybersecurity Risk Assessment And Administration Plan Formats PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

G6 Table Of Contents For Cybersecurity Risk Assessment And Administration Plan Pictures PDF
Boost your pitch with our creative G6 Table Of Contents For Cybersecurity Risk Assessment And Administration Plan Pictures PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Post It Notes Cybersecurity Risk Assessment And Administration Plan Rules PDF
Create an editable Post It Notes Cybersecurity Risk Assessment And Administration Plan Rules PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. ZZZZZZZZZZZZZZZZZZ is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Information And Data Breach Impacting Customer Loyalty Cybersecurity Risk Assessment Infographics PDF
Retrieve professionally designed Information And Data Breach Impacting Customer Loyalty Cybersecurity Risk Assessment Infographics PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Assigning Criticality Rating To Information Assets Cybersecurity Risk Assessment Template PDF
This slide showcases criticality rating that can be allocation to assets for identifying critical assets. Its key elements are asst, failure cost, failure impact and criticality rating. Take your projects to the next level with our ultimate collection of Assigning Criticality Rating To Information Assets Cybersecurity Risk Assessment Template PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they well make your projects stand out from the rest.

Mitigation Strategies To Avoid Information Breach Cybersecurity Risk Assessment Professional PDF
This slide showcases strategies that can help organization to avoid information breach. Key strategies include implement antivirus software, monitor network traffic, incident response plan, patch management schedule and establish network access controls. Present like a pro with Mitigation Strategies To Avoid Information Breach Cybersecurity Risk Assessment Professional PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Cybersecurity Risk Assessment And Administration Plan Ppt PowerPoint Presentation Complete Deck With Slides
Take advantage of this well-researched and professionally-designed Cybersecurity Risk Assessment And Administration Plan Ppt PowerPoint Presentation Complete Deck With Slides to ace your next business meeting. Use this PPT complete deck to impress the management with your ideas for business growth and revenue increase. Use the seventy two slide Template Bundle to leave no stone unturned as you present each step of your process. Employ the visual tools within the slides such as graphs, charts, and tables to ensure that the audience can never look away from the presentation. With attractive visuals, easy to understand structure, and your knowledge, your presentation will have the attention it deserves. Download this PPT Template from the link below.

Cybersecurity Risk Administration Plan Multitiered Risk Management Framework Diagram Microsoft PDF
Presenting Cybersecurity Risk Administration Plan Multitiered Risk Management Framework Diagram Microsoft PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Organization, Mission Or Business Processes, Information Systems In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Business Units Risk Ratings And Analysis Software Dashboard Ideas PDF
This slide covers risk distribution among different business units. It also includes inherent risk ratings for anti-bribery, commodity markets, competition, cyber security along with residual risk distribution matrix. Pitch your topic with ease and precision using this Business Units Risk Ratings And Analysis Software Dashboard Ideas PDF. This layout presents information on Risk Dashboard, Inherent Risk Medium, Controls Rising Weak. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
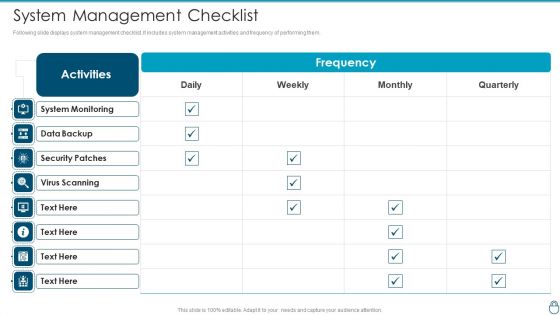
Cybersecurity Risk Administration Plan System Management Checklist Background PDF
Following slide displays system management checklist. It includes system management activities and frequency of performing them.Deliver and pitch your topic in the best possible manner with this Cybersecurity Risk Administration Plan System Management Checklist Background PDF Use them to share invaluable insights on System Monitoring, Security Patches, Virus Scanning and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
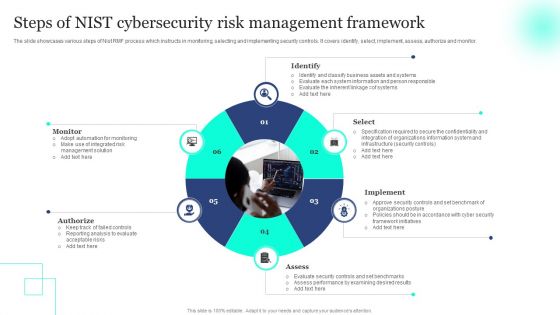
Steps Of NIST Cybersecurity Risk Management Framework Mockup PDF
The slide showcases various steps of Nist RMF process which instructs in monitoring, selecting and implementing security controls. It covers identify, select, implement, assess, authorize and monitor. Persuade your audience using this Steps Of NIST Cybersecurity Risk Management Framework Mockup PDF.zip. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Monitor, Authorize, Identify. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Mitigating Cybersecurity Threats And Vulnerabilities How Financial Risk Formats PDF
This slide provides details regarding various ways through financial risks can be controlled by handling liquidity risk, foreign exchange risk and credit exchange risk. Presenting mitigating cybersecurity threats and vulnerabilities how financial risk formats pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like liquidity risk, exchange risk, credit exchange risk. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
NIST Cybersecurity Framework For Risk Management Icon Formats PDF
Presenting NIST Cybersecurity Framework For Risk Management Icon Formats PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including NIST Cybersecurity, Framework, Risk Management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Treating The Risk Involved In Real Estate Project Diagrams PDF
The following slide exhibits various types of risks which can be treated and avoided based on their priority levels in the development of real estate project. The slide covers key information about the administrative risk, business email compromise, physical property damage, adapting to technology trends etc. Deliver and pitch your topic in the best possible manner with this Treating The Risk Involved In Real Estate Project Diagrams PDF. Use them to share invaluable insights on Risks To Treated, Management Stakeholders, Management Experience and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Treating The Risk Involved In Real Estate Project Guidelines PDF
The following slide exhibits various types of risks which can be treated and avoided based on their priority levels in the development of real estate project. The slide covers key information about the administrative risk, business email compromise, physical property damage, adapting to technology trends etc. This is a Treating The Risk Involved In Real Estate Project Guidelines PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Risks To Be Treated, Risk Management, Property Risk. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity Risk Administration Plan Incident Management Workflow Guidelines PDF
Following slide presents the incident management workflow of the firm. It covers five phases namely incident occurrence, team organizing, action taken, incident resolution and fail over report. Deliver an awe inspiring pitch with this creative Cybersecurity Risk Administration Plan Incident Management Workflow Guidelines PDF bundle. Topics like Organize Your Team, Incident Resolution, Team Takes Action can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
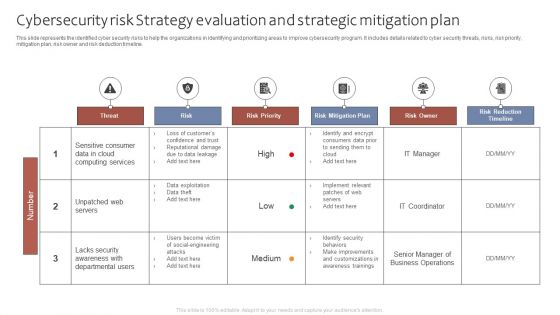
Cybersecurity Risk Strategy Evaluation And Strategic Mitigation Plan Ppt Portfolio Graphics Tutorials PDF
This slide represents the identified cyber security risks to help the organizations in identifying and prioritizing areas to improve cybersecurity program. It includes details related to cyber security threats, risks, risk priority, mitigation plan, risk owner and risk deduction timeline. Showcasing this set of slides titled Cybersecurity Risk Strategy Evaluation And Strategic Mitigation Plan Ppt Portfolio Graphics Tutorials PDF. The topics addressed in these templates are Threat, Risk, Risk Priority, Risk Mitigation Plan. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Evaluate Impact And Probability Of Risk Occurrence Ppt PowerPoint Presentation Diagram Images PDF
The following slide depicts the potential risk score of identified cyber risks to communicate and level threats. It includes key elements such as human and general errors, outdated security policy, selling companys confidential information, system failure etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Evaluate Impact And Probability Of Risk Occurrence Ppt PowerPoint Presentation Diagram Images PDF from Slidegeeks and deliver a wonderful presentation.

Evaluation Results Showing Bank Risk Ppt PowerPoint Presentation File Influencers PDF
Presenting evaluation results showing bank risk ppt powerpoint presentation file influencers pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including cyber security, perform, legal audit. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Risk Management For Organization Essential Assets Addressing Various Ways To Handle Insider Graphics PDF
This slide provides details regarding various ways to handle insider cyber threats in terms of periodic risk assessment, end user informing, etc. This is a risk management for organization essential assets addressing various ways to handle insider graphics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like periodic risk assessment, track baseline behavior networks and individuals, render least amount of privilege, inform end user. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Approaches To Overcome Cybersecurity Risk Faced By Real Estate Company Professional PDF
The following slide exhibits various approaches which can be used to prevent cybersecurity risk faced by the real estate enterprise. The key approaches highlighted in the slide are updating the security system, installing anti-phishing add-ons, using a customized web application firewall etc. Deliver an awe inspiring pitch with this creative Approaches To Overcome Cybersecurity Risk Faced By Real Estate Company Professional PDF bundle. Topics like Ransomware, Reduce Ransomware, Cybersecurity Awareness can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Methods To Develop Cybersecurity Monitoring Plan Steps In Detail Review And Risk Analysis Structure PDF
This slide provides information about the ninth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, punishing, ransomware, supply chain attacks etc. i.e., Review and Risk Analysis. Deliver an awe inspiring pitch with this creative methods to develop cybersecurity monitoring plan steps in detail review and risk analysis structure pdf bundle. Topics like potential consequence, low, medium, high can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Vendor Performance Analysis And Administration Supplier Performance Assessment Based On Procurement Risks Introduction PDF
This slide exhibits risk assessment of suppliers based on multiple procurement risks to identify supplier change requirements. It includes risks such as operational failures, administrations errors, late delivery, financial stability, legal compliance, frequency of price increases, product design improvements, cyber security, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Vendor Performance Analysis And Administration Supplier Performance Assessment Based On Procurement Risks Introduction PDF can be your best option for delivering a presentation. Represent everything in detail using Vendor Performance Analysis And Administration Supplier Performance Assessment Based On Procurement Risks Introduction PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Supplier Performance Assessment Based On Procurement Risks Ppt PowerPoint Presentation File Slides PDF
This slide exhibits risk assessment of suppliers based on multiple procurement risks to identify supplier change requirements. It includes risks such as operational failures, administrations errors, late delivery, financial stability, legal compliance, frequency of price increases, product design improvements, cyber security, etc. Present like a pro with Supplier Performance Assessment Based On Procurement Risks Ppt PowerPoint Presentation File Slides PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Risk Management Framework For A Blockchain Network Ppt PowerPoint Presentation Portfolio Format Ideas PDF
Persuade your audience using this risk management framework for a blockchain network ppt powerpoint presentation portfolio format ideas pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including application system security, risk control mechanisms, physical security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cybersecurity Monitoring Plan Steps In Detail Review And Risk Analysis Designs PDF
Deliver and pitch your topic in the best possible manner with this cybersecurity monitoring plan steps in detail review and risk analysis designs pdf. Use them to share invaluable insights on ensure that systems, monitoring capabilities, involved allowing analysts and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Marketers Guide To Data Analysis Optimization Tracking Spam Complaint Rate To Avoid Account Suspension Risk Template PDF
This slide covers an overview of the spam rate to identify the number of recipients who mark messages as spam in their inboxes. It also includes strategies to reduce spam, such as sending emails only to those who have opted to receive them, segmenting your email list, etc. Get a simple yet stunning designed Marketers Guide To Data Analysis Optimization Tracking Spam Complaint Rate To Avoid Account Suspension Risk Template PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Marketers Guide To Data Analysis Optimization Tracking Spam Complaint Rate To Avoid Account Suspension Risk Template PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
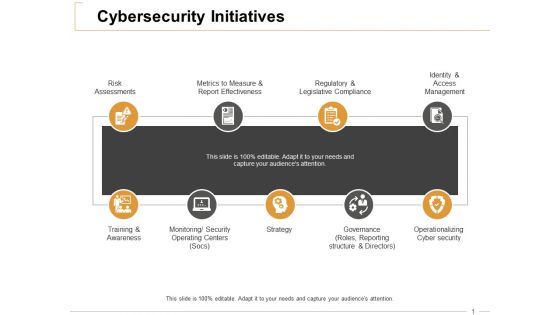
Cybersecurity Initiatives Ppt PowerPoint Presentation Outline Information
This is a cybersecurity initiatives ppt powerpoint presentation outline information. This is a nine stage process. The stages in this process are risk assessments, training and awareness, strategy, operationalizing cyber security, regulatory and legislative compliance.

Quarterly Cybersecurity Training Program And Assessment Schedule Sheet Elements PDF
This slide covers annual awareness training program schedule for employees. It includes training for network security, cyber security fundamentals, insider threats, malicious code, etc.Showcasing this set of slides titled Quarterly Cybersecurity Training Program And Assessment Schedule Sheet Elements PDF. The topics addressed in these templates are Insider Threats, Network Security, Risk Assessment. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cybersecurity Malware Assessment Use Cases Download PDF
This slide highlights cybersecurity analysis use cases which enable analysts to comprehend malwares functions, purposes and potential impact. The uses cases covered in this slide are threat hunting and alerts, malware detection, incident response, etc. Presenting Cybersecurity Malware Assessment Use Cases Download PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Threat Hunting, Malware Detection, Incident Response. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
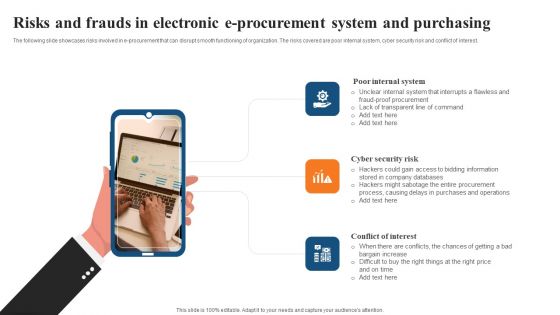
Risks And Frauds In Electronic E Procurement System And Purchasing Designs PDF
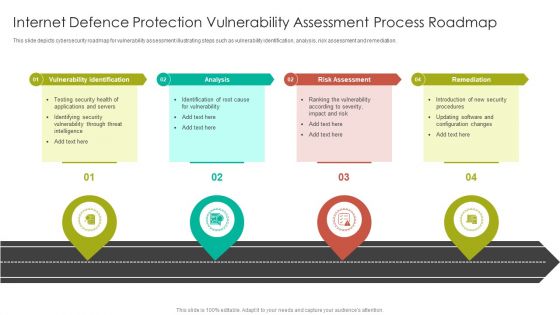
Internet Defence Protection Vulnerability Assessment Process Roadmap Graphics PDF
This slide depicts cybersecurity roadmap for vulnerability assessment illustrating steps such as vulnerability identification, analysis, risk assessment and remediation.Presenting Internet Defence Protection Vulnerability Assessment Process Roadmap Graphics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Vulnerability Identification, Risk Assessment, Remediation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Minimize Cloud Risks Medical Care Business Case Competition ABS Healthcare Company Overview Introduction PDF
This slide shows details about ABC Carbonated Drink Company such as company type, employees, headquarters, annual revenue, CEO, founding year etc. This is a minimize cloud risks medical care business case competition ABS healthcare company overview introduction pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like business overview, annual revenue, cyber security cases, manufactures, global advertising expenses. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
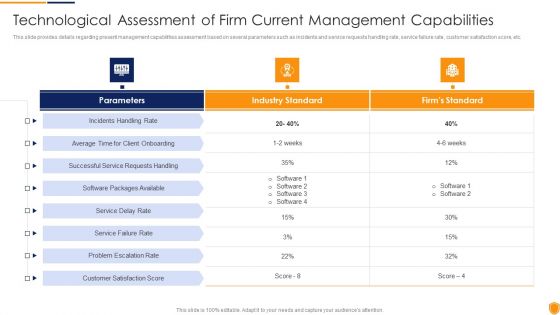
Mitigating Cybersecurity Threats And Vulnerabilities Technological Assessment Sample PDF
This slide provides details regarding present management capabilities assessment based on several parameters such as incidents and service requests handling rate, service failure rate, customer satisfaction score, etc. Deliver an awe inspiring pitch with this creative mitigating cybersecurity threats and vulnerabilities technological assessment sample pdf bundle. Topics like Industry Standard, Firms Standard, Client Onboarding, Service Failure Rate can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Best Practices For Secure Web Gateway Implementation Web Threat Protection System
This slide outlines various measures to be taken to maintain and enhance the functionality of Secure Web Gateway. The purpose of this slide is to demonstrate best practices for SWG. These are perform a risk assessment, deploy safe setups, monitor and analyse traffic, etc. There are so many reasons you need a Best Practices For Secure Web Gateway Implementation Web Threat Protection System. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
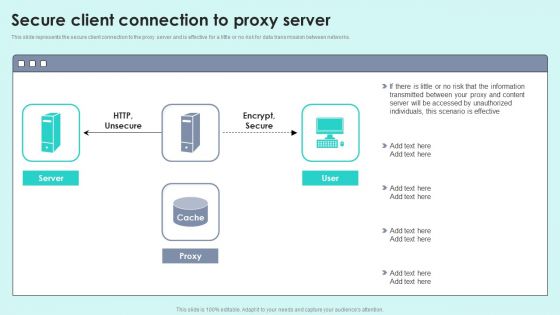
Secure Client Connection To Proxy Server Reverse Proxy For Load Balancing Portrait PDF
This slide represents the secure client connection to the proxy server and is effective for a little or no risk for data transmission between networks.Deliver an awe inspiring pitch with this creative Secure Client Connection To Proxy Server Reverse Proxy For Load Balancing Portrait PDF bundle. Topics like Transmitted Between, Accessed Unauthorized, Scenario Effective can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
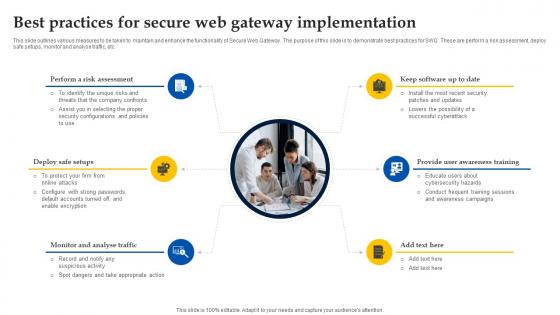
Web Access Control Solution Best Practices For Secure Web Gateway Implementation
This slide outlines various measures to be taken to maintain and enhance the functionality of Secure Web Gateway. The purpose of this slide is to demonstrate best practices for SWG. These are perform a risk assessment, deploy safe setups, monitor and analyse traffic, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Web Access Control Solution Best Practices For Secure Web Gateway Implementation can be your best option for delivering a presentation. Represent everything in detail using Web Access Control Solution Best Practices For Secure Web Gateway Implementation and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
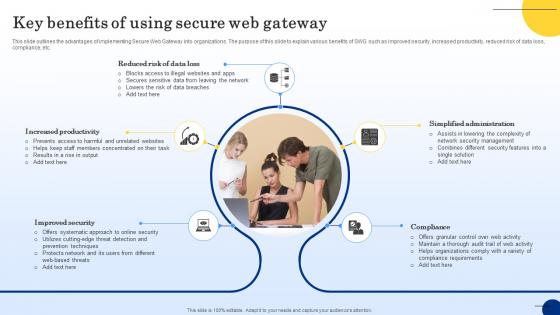
Key Benefits Of Using Secure Web Gateway Web Threat Protection System
This slide outlines the advantages of implementing Secure Web Gateway into organizations. The purpose of this slide to explain various benefits of SWG such as improved security, increased productivity, reduced risk of data loss, compliance, etc. Welcome to our selection of the Key Benefits Of Using Secure Web Gateway Web Threat Protection System. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
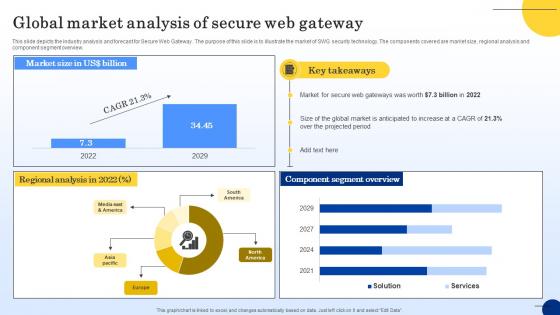
Global Market Analysis Of Secure Web Gateway Web Threat Protection System
This slide depicts the industry analysis and forecast for Secure Web Gateway. The purpose of this slide is to illustrate the market of SWG security technology. The components covered are market size, regional analysis and component segment overview. If you are looking for a format to display your unique thoughts, then the professionally designed Global Market Analysis Of Secure Web Gateway Web Threat Protection System is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Global Market Analysis Of Secure Web Gateway Web Threat Protection System and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Introduction To Next Generation Secure Web Gateway Web Threat Protection System
This slide demonstrates the concept of Next Generation Secure Web Gateway solution. The purpose of this slide is to provide an overview of next generation SGVs. This slide also talks about the need of this security technology for cloud applications. This modern and well-arranged Introduction To Next Generation Secure Web Gateway Web Threat Protection System provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Risks Analysis P2p Payment Startup Go To Market Strategy GTM SS V
The slide outlines potential risks and challenges in innovative fintech start-up business. It highlights components such as strategic, cybersecurity, fraud and operational.Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Risks Analysis P2p Payment Startup Go To Market Strategy GTM SS V was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Risks Analysis P2p Payment Startup Go To Market Strategy GTM SS V.

Strategies For Reducing Cybersecurity Risks In ABS Healthcare Company Ppt Professional Mockup PDF
This slide shows strategies that can be adopted by the company in order to minimize the cybersecurity risks and increasing malware attacks. Some strategies are data encryption, proper employee training, protection of physical devices, use df latest and updated softwares etc. This is a strategies for reducing cybersecurity risks in ABS healthcare company ppt professional mockup pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like data management, operating system maintenance, financial, protect devices that can be physically accessed. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Minimize Cloud Risks Medical Care Business Case Competition Table Of Contents Ideas PDF
Presenting minimize cloud risks medical care business case competition table of contents ideas pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like competitive analysis, cybersecurity, strategy implementation, key performance indicators, opportunity. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
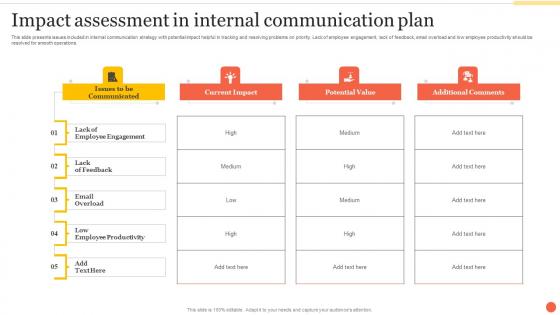
Impact Assessment In Internal Communication Plan Ppt Pictures File Formats Pdf
This slide presents issues included in internal communication strategy with potential impact helpful in tracking and resolving problems on priority. Lack of employee engagement, lack of feedback, email overload and low employee productivity should be resolved for smooth operations. Pitch your topic with ease and precision using this Impact Assessment In Internal Communication Plan Ppt Pictures File Formats Pdf. This layout presents information on Lack Feedback, Email Overload, Low Employee Productivity. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Mitigating Cybersecurity Threats And Vulnerabilities Comparative Assessment Of Various Background PDF
This slide provides details regarding comparative assessment of different threat agents on various parameters such as data loss impact, skills required to handle threat, etc. Deliver an awe inspiring pitch with this creative mitigating cybersecurity threats and vulnerabilities comparative assessment of various background pdf bundle. Topics like social engineering, insider threat, maintenance threats can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Minimize Cloud Risks Medical Care Business Case Competition SWOT Analysis Of ABS Healthcare Company Threats Ideas PDF
This slide shows some threats that may effect the company in future course of time and impact the company profits. Some potential threats are High Cybersecurity Risks , Intense Competition Level , Government Regulations and Currency Fluctuations etc. This is a minimize cloud risks medical care business case competition SWOT analysis of ABS healthcare company threats ideas pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity risks, intense competition, regulations and currency fluctuations, sales and revenue, marketing and technology. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Laptop And Credit Card Online Shopping PowerPoint Templates Ppt Backgrounds For Slides 0213
We present our Laptop And Credit Card Online Shopping PowerPoint Templates PPT Backgrounds For Slides 0213.Present our Computer PowerPoint Templates because Our PowerPoint Templates and Slides will let you Hit the target. Go the full distance with ease and elan. Present our Technology PowerPoint Templates because It can be used to Set your controls for the heart of the sun. Our PowerPoint Templates and Slides will be the propellant to get you there. Download our Communication PowerPoint Templates because It will mark the footprints of your journey. Illustrate how they will lead you to your desired destination. Present our Security PowerPoint Templates because Our PowerPoint Templates and Slides come in all colours, shades and hues. They help highlight every nuance of your views. Use our Finance PowerPoint Templates because You can Raise a toast with our PowerPoint Templates and Slides. Spread good cheer amongst your audience.Use these PowerPoint slides for presentations relating to Laptop and credit card E-commerce concept, security, computer, technology, communication, finance. The prominent colors used in the PowerPoint template are Blue, Black, Gray.

Table Of Contents Mitigating Cybersecurity Threats And Vulnerabilities Portrait PDF
Presenting table of contents mitigating cybersecurity threats and vulnerabilities portrait pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like current scenario assessment, secure digital assets, physical security, natural calamity threats. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

 Home
Home