Cyber Security Operations
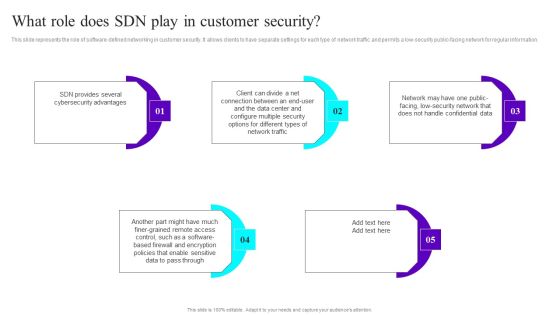
What Role Does SDN Play In Customer Security Ppt Infographic Template Slides PDF
This slide represents the role of software-defined networking in customer security. It allows clients to have separate settings for each type of network traffic and permits a low-security public-facing network for regular information. Do you know about Slidesgeeks What Role Does SDN Play In Customer Security Ppt Infographic Template Slides PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

Security Software Company Investor Funding Pitch Deck Market Potential Brochure PDF
The following slide showcases growth opportunity lying in market for an IT company. It outlines opportunity areas and CAGR in sectors information security and network detection and response. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Security Software Company Investor Funding Pitch Deck Market Potential Brochure PDF can be your best option for delivering a presentation. Represent everything in detail using Security Software Company Investor Funding Pitch Deck Market Potential Brochure PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Phase 3 Respond To Cloud Protection Issues Cloud Computing Security IT Ppt Gallery Rules PDF
This slide represents phase 3 of cloud security, such as respond to cloud protection issues. It includes an advanced authentication process, manages cloud access standards when new services come up, and eliminates malware from cloud services. Deliver and pitch your topic in the best possible manner with this phase 3 respond to cloud protection issues cloud computing security it ppt gallery rules pdf. Use them to share invaluable insights on authentication process, service, web policies and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Leading Cloud Access Security Broker Platforms Ppt PowerPoint Presentation File Styles PDF
This slide outlines the Leading cloud access security broker platforms. The purpose of this slide is to highlight the leading CASB platforms, including G-suite, office 365, and Amazon Web Services, and it also represents the benefits and features of these cloud platforms. Are you searching for a Leading Cloud Access Security Broker Platforms Ppt PowerPoint Presentation File Styles PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Leading Cloud Access Security Broker Platforms Ppt PowerPoint Presentation File Styles PDF from Slidegeeks today.

O RAN Architecture Role Of Security In Open RAN Standards Ppt Infographics Topics PDF
This slide represents the role of security in open RAN, which is built on the zero trust model. It means not to trust anybody and all the authorized and unauthorized devices, personnel, or networks have to go through some security checks. Retrieve professionally designed O RAN Architecture Role Of Security In Open RAN Standards Ppt Infographics Topics PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Info Security Employee Awareness Training Budget For FY2022 Ppt PowerPoint Presentation File Graphics Download PDF
This slide represents the organizations staff training budget through a graph covering trainer name, date, and capability levels. Deliver an awe inspiring pitch with this creative info security employee awareness training budget for fy2022 ppt powerpoint presentation file graphics download pdf bundle. Topics like build and maintain, secure network and system, protect cardholder data, maintain a vulnerability, management program can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Integrating Chatgpt With Other Systems Security And Compliance Management Themes PDF
This slide provides information regarding the integration of ChatGPT with other systems for managing security and compliance in terms of fraud detection, handling cybersecurity, risk assessment and compliance monitoring. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Integrating Chatgpt With Other Systems Security And Compliance Management Themes PDF can be your best option for delivering a presentation. Represent everything in detail using Integrating Chatgpt With Other Systems Security And Compliance Management Themes PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Problem Faced By The Organization Hacking Prevention Awareness Training For IT Security Rules PDF
This slide covers the problem faced by organization caused by employees due to lack of security awareness training programs. This is a problem faced by the organization hacking prevention awareness training for it security rules pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like corporate, cybersecurity, financial. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Hacker Roles And Responsibilities Of Ethical Hackers Pictures PDF
This slide represents the types of ethical hacking such as web application hacking, system hacking, web server hacking, hacking wireless networks, and social engineering.Presenting IT Security Hacker Roles And Responsibilities Of Ethical Hackers Pictures PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Application Hacking, System Hacking, Wireless Networks. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Folder And Alarm Clock Security PowerPoint Templates Ppt Backgrounds For Slides 1212
We present our Folder And Alarm Clock Security PowerPoint Templates PPT Backgrounds For Slides 1212.Download and present our Time Planning PowerPoint Templates because the vision of being the market leader is clear to you. Download our Internet PowerPoint Templates because there are a bucketful of brilliant ideas swirling around within your group. Download our Computer PowerPoint Templates because you can Transmit your thoughts via our slides and proud your team to action. Download and present our Success PowerPoint Templates because the success of your venture depends on the performance of every team member. Present our Business PowerPoint Templates because everybody knows The world over it is a priority for many. Along with it there are so many oppurtunities waiting to be utilised.Use these PowerPoint slides for presentations relating to Alarm clock and folder, business, time planning, internet, computer, success. The prominent colors used in the PowerPoint template are Red, Yellow, White. Professionals tell us our Folder And Alarm Clock Security PowerPoint Templates PPT Backgrounds For Slides 1212 are Stylish. Use our folder PowerPoint templates and PPT Slides are Fantastic. We assure you our Folder And Alarm Clock Security PowerPoint Templates PPT Backgrounds For Slides 1212 are Efficient. We assure you our time PowerPoint templates and PPT Slides will make the presenter look like a pro even if they are not computer savvy. Presenters tell us our Folder And Alarm Clock Security PowerPoint Templates PPT Backgrounds For Slides 1212 are Reminiscent. PowerPoint presentation experts tell us our business PowerPoint templates and PPT Slides are Cheerful.

Organizational Network Staff Learning Employee Security Awareness Training Budget Information PDF
This slide covers the training budget along with topics, provider, training date, duration, qualification, capability level and refresh or renewal status. Deliver and pitch your topic in the best possible manner with this organizational network staff learning employee security awareness training budget information pdf. Use them to share invaluable insights on capability level, budget, duration and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
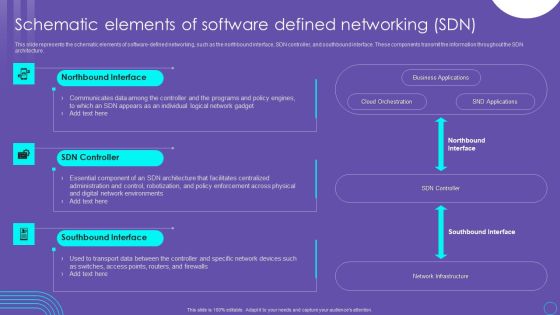
SDN Security Architecture Schematic Elements Of Software Defined Networking SDN Pictures PDF
This slide represents the schematic elements of software defined networking, such as the northbound interface, SDN controller, and southbound interface. These components transmit the information throughout the SDN architecture. Create an editable SDN Security Architecture Schematic Elements Of Software Defined Networking SDN Pictures PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. SDN Security Architecture Schematic Elements Of Software Defined Networking SDN Pictures PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

IT Security Assessment Matrix Of IT Risks Ppt Slides Visual Aids PDF
This slide depicts the cyberattacks surface based on different property types. It also covers the attacks based on web mobile applications, online payments, employee devices. Deliver an awe inspiring pitch with this creative information technology security assessment matrix of it risks ppt outline objects pdf bundle. Topics like assessment matrix of it risks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Risk Management Model For Data Security Online And Onsite Training Schedule For Employee Rules PDF
This slide illustrates employee training schedule. It covers details about employee name, its position, software name, course type, training mode and duration. Deliver an awe inspiring pitch with this creative Risk Management Model For Data Security Online And Onsite Training Schedule For Employee Rules PDF bundle. Topics like Course Type, Training Mode, Training Duration, Employee can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
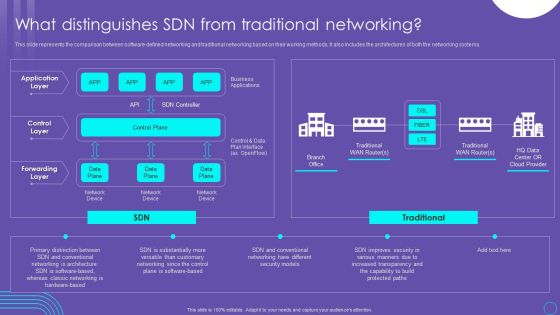
SDN Security Architecture What Distinguishes SDN From Traditional Networking Microsoft PDF
This slide represents the comparison between software defined networking and traditional networking based on their working methods. It also includes the architectures of both the networking systems. Get a simple yet stunning designed SDN Security Architecture What Distinguishes SDN From Traditional Networking Microsoft PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit SDN Security Architecture What Distinguishes SDN From Traditional Networking Microsoft PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Reporting Structure For Information Security Risk Management Cybersecurity Risk Assessment Formats PDF
This slide showcases plan that can help to communicate the major risks report on regular intervals. Its key components are risk, reported by, frequency, likelihood, criticality and impact. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Reporting Structure For Information Security Risk Management Cybersecurity Risk Assessment Formats PDF can be your best option for delivering a presentation. Represent everything in detail using Reporting Structure For Information Security Risk Management Cybersecurity Risk Assessment Formats PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
IT Security Risk Management Approach Introduction Threat Vulnerability Asset Matrix Icons PDF
Mentioned slide displays the threat vulnerability asset matrix covering sections namely ranked threat agent and details about critical resources ranked from most critical to least. Deliver and pitch your topic in the best possible manner with this IT Security Risk Management Approach Introduction Threat Vulnerability Asset Matrix Icons PDF. Use them to share invaluable insights on Social Engineering, Server Systems, Internet and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
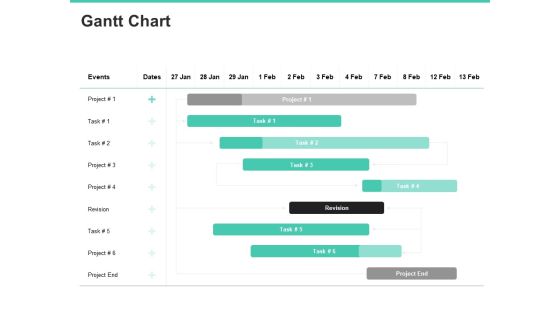
Email Security Encryption And Data Loss Prevention Gantt Chart Information PDF
Your complex projects can be managed and organized simultaneously using this detailed email security encryption and data loss prevention gantt chart information pdf template. Track the milestones, tasks, phases, activities, and subtasks to get an updated visual of your project. Share your planning horizon and release plan with this well-crafted presentation template. This exemplary template can be used to plot various dependencies to distinguish the tasks in the pipeline and their impact on the schedules and deadlines of the project. Apart from this, you can also share this visual presentation with your team members and stakeholders. It a resourceful tool that can be incorporated into your business structure. Therefore, download and edit it conveniently to add the data and statistics as per your requirement.

Employee Awareness Training Budget For FY2020 IT Security IT Ppt Show Slides PDF
This slide represents the organizations staff training budget through a graph covering trainer name, date, and capability levels. This is a employee awareness training budget for fy2020 it security it ppt show slides pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like maintain, vulnerability, management, secure, network. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Skills Required To Become An Ethical Hacker Security Ppt Layouts Guide PDF
This slide depicts the skills required to become an ethical hacker, such as programming knowledge, scripting languages, networking skills, and understanding databases and servers. Presenting skills required to become an ethical hacker security ppt layouts guide pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like networking, technologies, management, database. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Blockchain Security Solutions Deployment Overview Of Sybil Attack In Blockchain Summary PDF
This slide gives an overview of the sybil attack in the blockchain network. The purpose of this slide is to showcase the use case of a sybil attack, also known as eclipse attack, and how the sybil attack works to manipulate a blockchain network.. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Blockchain Security Solutions Deployment Overview Of Sybil Attack In Blockchain Summary PDF can be your best option for delivering a presentation. Represent everything in detail using Blockchain Security Solutions Deployment Overview Of Sybil Attack In Blockchain Summary PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
IT Security IT Prepare And Deploy Strong IT Policies Ppt Icon Design Ideas PDF
This slide represents the value of having strong IT policies within an organization regarding software, hardware, passwords, and data transfer. Deliver an awe inspiring pitch with this creative it security it prepare and deploy strong it policies ppt icon design ideas pdf bundle. Topics like it policies, management, access, policies, network can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Security Prepare And Deploy Strong IT Policies Ppt Gallery Images PDF
This slide represents the value of having strong IT policies within an organization regarding software, hardware, passwords, and data transfer. Deliver an awe inspiring pitch with this creative information security prepare and deploy strong it policies ppt gallery images pdf bundle. Topics like management, network, device, data can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Desktop Security Management Prepare And Deploy Strong It Policies Template PDF
This slide represents the value of having strong IT policies within an organization regarding software, hardware, passwords, and data transfer. Deliver and pitch your topic in the best possible manner with this desktop security management prepare and deploy strong it policies template pdf. Use them to share invaluable insights on management, data, network and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
IT Security Prepare And Deploy Strong IT Policies Ppt Icon Graphics Example PDF
This slide represents the value of having strong IT policies within an organization regarding software, hardware, passwords, and data transfer. Deliver an awe inspiring pitch with this creative it security prepare and deploy strong it policies ppt icon graphics example pdf bundle. Topics like management, it policies, network access can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

SDN Security Architecture Training Program For Software Defined Networking SDN Mockup PDF
This slide represents the training program for software defined networking. It caters to participant teams, modules to be covered in training, training schedule, and mode of training such as online and offline. There are so many reasons you need a SDN Security Architecture Training Program For Software Defined Networking SDN Mockup PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

IT Security IT Awareness Training For Staff Ppt Gallery Example Introduction PDF
This slide represents the cybersecurity awareness training program for staff, including the name of the participants and what modules would be covered under training daily. Deliver and pitch your topic in the best possible manner with this it security it awareness training for staff ppt gallery example introduction pdf. Use them to share invaluable insights on developers, organizations, senior executives, planning, strategies and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Reverse Proxy Web Server Reverse Proxy Web Server Application Side Technology Security Designs PDF
This slide represents the reverse proxy server-side technology, which is load balancing, and how reverse proxy side servers help high-traffic websites manage traffic. The Reverse Proxy Web Server Reverse Proxy Web Server Application Side Technology Security Designs PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Kpis To Measure Information Security Risk Management Cybersecurity Risk Assessment Infographics PDF
This slide showcases KPIs that can help organization to measure the impact of cybersecurity risk management programme. It showcases estimated figures before and after implementation of plan. Slidegeeks has constructed Kpis To Measure Information Security Risk Management Cybersecurity Risk Assessment Infographics PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
Information Security Define Access Control Measures For Employees Ppt Icon Pictures PDF
This slide represents how it is essential to minimize the rights or access of employees in an organization to keep data safe and prevent it from deletion, manipulation. This is a information security define access control measures for employees ppt icon pictures pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like networks, organization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Desktop Security Management Define Access Control Measures For Employees Icons PDF
This slide represents how it is essential to minimize the rights or access of employees in an organization to keep data safe and prevent it from deletion, manipulation. This is a desktop security management define access control measures for employees icons pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organization, networks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Safeguarding Network With SDN Security Table Of Contents Ppt Visual Aids Files PDF
This slide represents the schematic elements of software-defined networking, such as the northbound interface, SDN controller, and southbound interface. These components transmit the information throughout the SDN architecture. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Safeguarding Network With SDN Security Table Of Contents Ppt Visual Aids Files PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Define Access Control Measures For Employees IT Security IT Ppt Professional Icon PDF
This slide represents how it is essential to minimize the rights or access of employees in an organization to keep data safe and prevent it from deletion, manipulation. This is a define access control measures for employees it security it ppt professional icon pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organization, access data, networks, responsibilities. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Blockchain Security Solutions Deployment How Ddos Attack Works In Blockchain Network Diagrams PDF
This slide represents the overview of distributed denial-of-service DDOS attacks in blockchain technology. This slide aims to showcase how distributed denial-of-service DDOS works to exploit a blockchain network by generating multiple requests from a single source. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Blockchain Security Solutions Deployment How Ddos Attack Works In Blockchain Network Diagrams PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
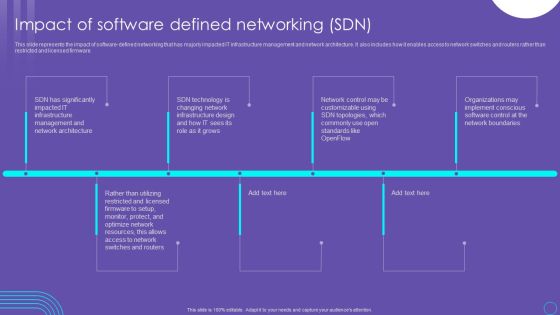
SDN Security Architecture Impact Of Software Defined Networking SDN Guidelines PDF
This slide represents the impact of software defined networking that has majorly impacted IT infrastructure management and network architecture. It also includes how it enables access to network switches and routers rather than restricted and licensed firmware. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download SDN Security Architecture Impact Of Software Defined Networking SDN Guidelines PDF from Slidegeeks and deliver a wonderful presentation.

Information Security Attacks Faced By Organization Cybersecurity Risk Assessment Brochure PDF
This slide showcases most common information attacks faced by organization. It includes malware, phishing, man in the middle attack, SQL injection, zero day exploit and DNS attack. Take your projects to the next level with our ultimate collection of Information Security Attacks Faced By Organization Cybersecurity Risk Assessment Brochure PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they well make your projects stand out from the rest.

Cloud Information Security Zero Trust Policy And Why You Should Embrace IT Ppt File Outfit PDF
This slide represents the zero-trust policy and why organizations should embrace it, and how user access control is managed under the zero-trust policy. This is a Cloud Information Security Zero Trust Policy And Why You Should Embrace IT Ppt File Outfit PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Authentication Device, Validation Network, Restrict Access. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Awareness Training Program To Enhance Effectiveness Of Employees Structure PDF
This slide covers cybersecurity awareness training to enhance effectiveness of employees. It involves document management, passwords and authentication and social engineering and phishing. Persuade your audience using this IT Security Awareness Training Program To Enhance Effectiveness Of Employees Structure PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Document Management, Passwords And Authentication, Social, Engineering And Phishing. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Employee Questionnaire To Assess IT Security Awareness Training Program Effectiveness Graphics PDF
This slide covers employee questionnaire to assess cybersecurity training program effectiveness. It involves questions to determine trainer effectiveness in teaching, knowledge and skills of trainer and details about training organization. Showcasing this set of slides titled Employee Questionnaire To Assess IT Security Awareness Training Program Effectiveness Graphics PDF. The topics addressed in these templates are Good Knowledge, Cyberattacks And Methods, Awareness Training. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Why IT Security Awareness Training Program Is Essential For Employees Background PDF
This slide covers need of cybersecurity awareness training withing organization. It involves reasons such as increases employee awareness, assures educated staff, enhances organizational reputation and boosts confidence. Presenting Why IT Security Awareness Training Program Is Essential For Employees Background PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Increases Awareness, Assures Educated Staff, Enhances Organizational Reputation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Blockchain Security Solutions Deployment How Fraudsters Attack Blockchain Network Sample PDF
This slide describes the primary attacks that hackers can use to exploit blockchain technology networks. The purpose of this slide is to showcase some basic threats that hackers can use to manipulate a blockchain network, such as phishing attacks, routing attacks, sybil, and 51 percent. Present like a pro with Blockchain Security Solutions Deployment How Fraudsters Attack Blockchain Network Sample PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
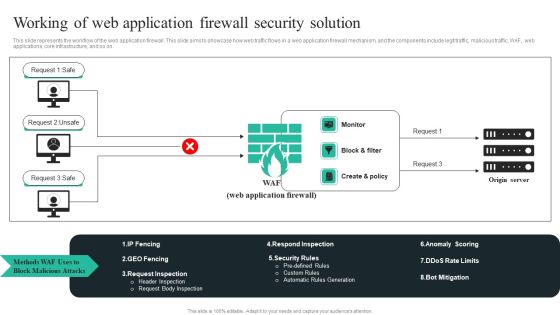
WAF Introduction Working Of Web Application Firewall Security Solution Microsoft PDF
This slide represents the workflow of the web application firewall. This slide aims to showcase how web traffic flows in a web application firewall mechanism, and the components include legit traffic, malicious traffic, WAF, web applications, core infrastructure, and so on. Take your projects to the next level with our ultimate collection ofWAF Introduction Working Of Web Application Firewall Security Solution Microsoft PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.
SDN Security Architecture Importance Of Virtualization In Software Defined Networking Icons PDF
This slide represents the importance of virtualization in software defined networking and how they complement one another. It also includes how SDN helps simplify the process of controlling data packet routing via a central server. Retrieve professionally designed SDN Security Architecture Importance Of Virtualization In Software Defined Networking Icons PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

SDN Security Architecture How SDN Can Have A Significant Impact On A Business Mockup PDF
This slide depicts the four critical areas where SDN can make a difference in an organization, such as network programmability, centralized intelligence and control, abstraction of the network, and openness. Welcome to our selection of the SDN Security Architecture How SDN Can Have A Significant Impact On A Business Mockup PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today

SDN Security Architecture Role Of SDN In Edge Computing Iot And Remote Access Information PDF
This slide represents the role of software defined networking in edge computing, IoT, and remote locations to make them more accessible and less expensive. Smart SDN controllers detect network congestion and, in response, increase the bandwidth for remote and edge devices. Boost your pitch with our creative SDN Security Architecture Role Of SDN In Edge Computing Iot And Remote Access Information PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Developing New Sales And Marketing Strategic Approach Marketing Operations Strategy Ppt PowerPoint Presentation Layouts Graphics Example PDF
Presenting this set of slides with name developing new sales and marketing strategic approach marketing operations strategy ppt powerpoint presentation layouts graphics example pdf. The topics discussed in these slides are marketing initiatives, content, email, targeted content. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Detail Impact Information Security Plan Can Reduce The Risk Of Data Breach Ppt PowerPoint Presentation File Visual Aids PDF
This slide represents the current status of the cyber attacks in an organization after implementing the cyber security model. Deliver an awe inspiring pitch with this creative detail impact information security plan can reduce the risk of data breach ppt powerpoint presentation file visual aids pdf bundle. Topics like phishing breakdown, network intrusion breakdown, inadvertent desclosure can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Detail Impact IT Security IT Plan Can Reduce The Risk Of Data Breach In Organization Ppt Infographic Template Objects PDF
This slide represents the current status of the cyber attacks in an organization after implementing the cyber security model. Deliver and pitch your topic in the best possible manner with this detail impact it security it plan can reduce the risk of data breach in organization ppt infographic template objects pdf. Use them to share invaluable insights on detail impact it security it plan can reduce the risk of data breach in organization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Global Cyber Terrorism Incidents On The Rise IT How To Prevent Ddos Attacks In The Company Designs PDF
This slide represents the ways to prevent DDoS attacks in the company, which include network monitoring, updating security elements, etc. Presenting global cyber terrorism incidents on the rise it how to prevent ddos attacks in the company designs pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like mitigation technologies, service, traffic irregularities, network monitoring. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
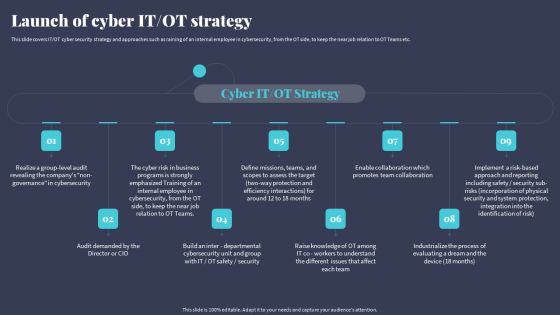
Tactics For Incorporating OT And IT With The Latest PI System Launch Of Cyber IT OT Strategy Brochure PDF
This slide covers IT OT cyber security strategy and approaches such as raining of an internal employee in cybersecurity, from the OT side, to keep the near job relation to OT Teams etc. Explore a selection of the finest Tactics For Incorporating OT And IT With The Latest PI System Launch Of Cyber IT OT Strategy Brochure PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Tactics For Incorporating OT And IT With The Latest PI System Launch Of Cyber IT OT Strategy Brochure PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
Reverse Proxy Server IT Cyber Attacks On The Main Server Of Company Ppt Icon Graphics Tutorials PDF
This slide shows the current situation of the organization through the total losses in millions experienced because of different types of the cyber attacks. Deliver an awe inspiring pitch with this creative reverse proxy server it cyber attacks on the main server of company ppt icon graphics tutorials pdf bundle. Topics like losses organization, due to cyberattacks, costs can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Global Cyber Terrorism Incidents On The Rise IT How To Protect Company From Trojan Attacks Summary PDF
This slide explains how to protect the company from trojan attacks which include procedures such as installing advanced antivirus software. This is a global cyber terrorism incidents on the rise it how to protect company from trojan attacks summary pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like install a good antivirus programm, web application firewall waf, stick to reliable sources, avoid third party downloads. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
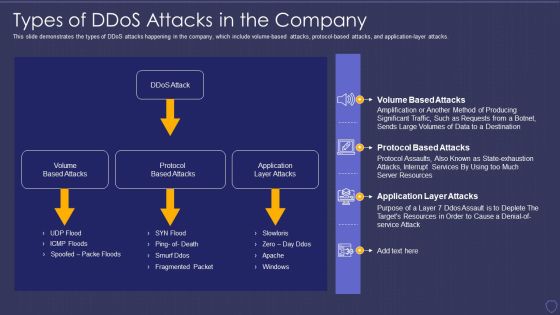
Global Cyber Terrorism Incidents On The Rise IT Types Of Ddos Attacks In The Company Elements PDF
This slide demonstrates the types of DDoS attacks happening in the company, which include volume-based attacks, protocol-based attacks, and application-layer attacks. Deliver and pitch your topic in the best possible manner with this global cyber terrorism incidents on the rise it types of ddos attacks in the company elements pdf. Use them to share invaluable insights on volume based attacks, protocol based attacks, application layer attacks and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Appropriate Information Management In Healthcare Sector To Decrease Cyber Attacks Ppt PowerPoint Presentation Complete Deck With Slides
This complete presentation has PPT slides on wide range of topics highlighting the core areas of your business needs. It has professionally designed templates with relevant visuals and subject driven content. This presentation deck has total of fourty four slides. Get access to the customizable templates. Our designers have created editable templates for your convenience. You can edit the colour, text and font size as per your need. You can add or delete the content if required. You are just a click to away to have this ready made presentation. Click the download button now.

Operational Efficiency Execution Strategy Improve Quality Operational Process Improvement Plan Graphics PDF
This slide provides information about the fourth step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Assigning Resources. This is a operational efficiency execution strategy improve quality operational process improvement plan graphics pdfS template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like team, resource, process, communication. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Operational Efficiency Execution Strategy Improve Quality Operational Process Improvement Plan Steps Icons PDF
This slide provides information about the first and the foremost step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e. Process Mapping. Presenting operational efficiency execution strategy improve quality operational process improvement plan steps icons pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like process improvement, applications, graphic software, accountability. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Operational Efficiency Execution Strategy Improve Quality Operational Process Improvement Plan Steps In Detail Formats PDF
This slide provides information about the seventh step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e Monitoring and Optimization. This is a operational efficiency execution strategy improve quality operational process improvement plan steps in detail formats pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like performance, process optimization, implementation costs. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Operational Process Improvement Plan Steps In Detail Process Analysis Brochure PDF
This slide provides information about the second step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e. Process Analysis. Presenting operational process improvement plan steps in detail process analysis brochure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like analysis, analysis process. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
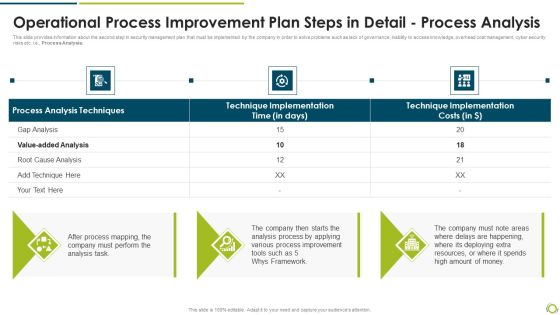
Operational Process Improvement Plan Steps In Detail Process Analysis Formats PDF
This slide provides information about the second step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Process Analysis. Presenting operational process improvement plan steps in detail process analysis formats pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like technique implementation, process analysis techniques, process improvement. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Operational Process Improvement Plan Steps In Detail Assigning Resources Background PDF
This slide provides information about the fourth step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e. Assigning Resources. Presenting operational process improvement plan steps in detail assigning resources background pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like reducing communication issues, perform process visualizations, roles and responsibilities. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

 Home
Home