Cyber Security Operations

Data Wiper Spyware Attack Reasons Behind Ukraine And Russian Cyber Warfare Introduction PDF
This slide describes the reasons behind Ukraine and Russia cyber warfare, including NATOs eastward expansion, Ukraine is not a real country according to Putin, and so on.Deliver an awe inspiring pitch with this creative data wiper spyware attack reasons behind ukraine and russian cyber warfare introduction pdf bundle. Topics like reasons behind ukraine and russian cyber warfare can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
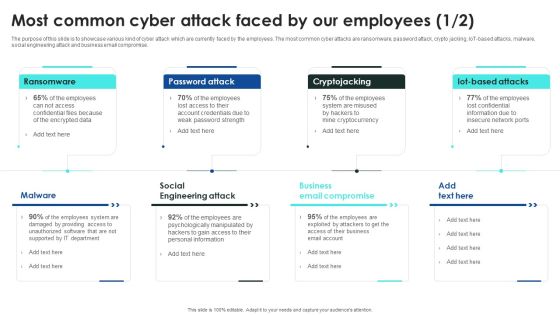
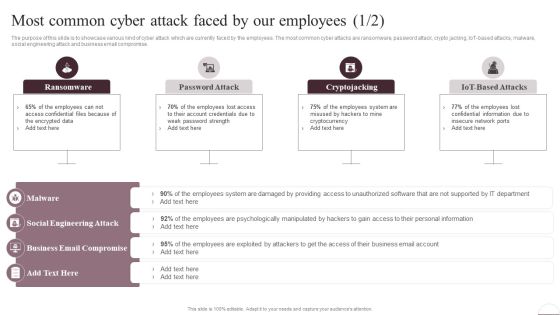
Implementing Cybersecurity Awareness Program To Prevent Attacks Most Common Cyber Attack Faced Pictures PDF
The purpose of this slide is to showcase various kind of cyber attack which are currently faced by the employees. The most common cyber attacks are ransomware, password attack, crypto jacking, IoT-based attacks, malware, social engineering attack and business email compromise. Are you searching for a Implementing Cybersecurity Awareness Program To Prevent Attacks Most Common Cyber Attack Faced Pictures PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Implementing Cybersecurity Awareness Program To Prevent Attacks Most Common Cyber Attack Faced Pictures PDF from Slidegeeks today.

Russian Cyber Attacks On Ukraine IT Website Defacements Ddos Template PDF
This slide represents the other attacks carried out by Russia on Ukraine, such as website defacement, distributed denial-of-service attacks, and website clones. This is a russian cyber attacks on ukraine it website defacements ddos template pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security, service. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
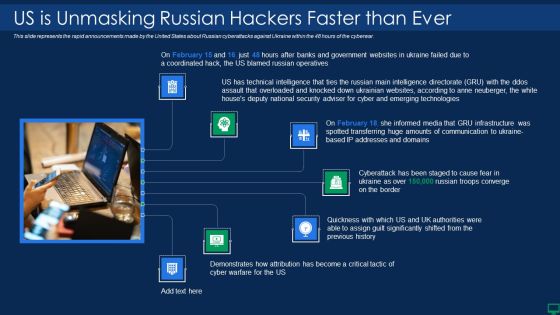
Russian Cyber Attacks On Ukraine IT Us Is Unmasking Russian Inspiration PDF
This slide represents the rapid announcements made by the United States about Russian cyberattacks against Ukraine within the 48 hours of the cyberwar. Presenting russian cyber attacks on ukraine it us is unmasking russian inspiration pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like technical, security, communication. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Russian Cyber Attacks On Ukraine IT Facebook And Twitter Suggest Rules PDF
This slide depicts Facebook and Twitters suggestion for Ukrainian citizens to close or lock their social media accounts as there are high chances of getting hacked in the hours of the war. This is a russian cyber attacks on ukraine it facebook and twitter suggest rules pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like social media, accounts, strategy, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
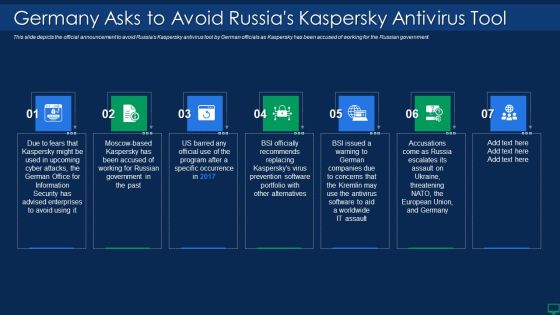
Russian Cyber Attacks On Ukraine IT Germany Asks To Avoid Russias Sample PDF
This slide depicts the official announcement to avoid Russias Kaspersky antivirus tool by German officials as Kaspersky has been accused of working for the Russian government. This is a russian cyber attacks on ukraine it germany asks to avoid russias sample pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information, security, portfolio. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Data Wiper Spyware Attack Shuckworm Continues Cyber Espionage Attacks Against Ukraine Diagrams PDF
This slide represents the continuous cyber-espionage attacks held by the Shuckworm group against Ukraine. Most of these attacks were phishing emails to spread the malware among devices that could control remotely.Deliver an awe inspiring pitch with this creative data wiper spyware attack shuckworm continues cyber espionage attacks against ukraine diagrams pdf bundle. Topics like shuckworm continues cyber espionage attacks against ukraine can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Picture Of Cyber Attack Warning Ppt PowerPoint Presentation Model Background Images PDF
Presenting this set of slides with name picture of cyber attack warning ppt powerpoint presentation model background images pdf. This is a three stage process. The stages in this process are picture of cyber attack warning. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Threat Assessment For Cyber Attack Ppt PowerPoint Presentation File Sample PDF
Presenting this set of slides with name threat assessment for cyber attack ppt powerpoint presentation file sample pdf. This is a three stage process. The stages in this process are threat assessment for cyber attack. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Phishing Scams And Attacks Icon To Steal Confidential Data Elements PDF
Showcasing this set of slides titled cyber phishing scams and attacks icon to steal confidential data elements pdf. The topics addressed in these templates are cyber phishing scams and attacks icon to steal confidential data. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Data Wiper Spyware Attack Cyclops Blink Cyber Attack Against Ukraine Background PDF
This slide describes the cyclops blink cyber attack held by Russia on official Ukrainian websites created by the Sandworm organization to replace the VPN filters.Presenting data wiper spyware attack cyclops blink cyber attack against ukraine background pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like cyclops blink cyber attack against ukraine In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
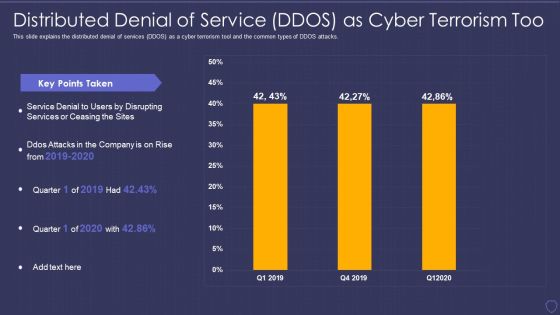
Global Cyber Terrorism Incidents On The Rise IT Distributed Denial Of Service Template PDF
This slide explains the distributed denial of services DDOS as a cyber terrorism tool and the common types of DDOS attacks. Deliver an awe inspiring pitch with this creative global cyber terrorism incidents on the rise it distributed denial of service template pdf bundle. Topics like distributed denial of service ddos as cyber terrorism too can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Vector Showing Information Protection From Cyber Attack Ppt PowerPoint Presentation Gallery Guidelines PDF
Persuade your audience using this vector showing information protection from cyber attack ppt powerpoint presentation gallery guidelines pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including vector showing information protection from cyber attack. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Prevention Of Information Most Common Cyber Attack Faced By Our Employees Structure PDF
The purpose of this slide is to showcase various kind of cyber attack which are currently faced by the employees. The most common cyber attacks are ransomware, password attack, crypto jacking, IoT-based attacks, malware, social engineering attack and business email compromise. Are you searching for a Prevention Of Information Most Common Cyber Attack Faced By Our Employees Structure PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort youve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Prevention Of Information Most Common Cyber Attack Faced By Our Employees Structure PDF from Slidegeeks today.

Most Common Cyber Attack Faced By Our Employees Ppt Infographic Template Topics PDF
The purpose of this slide is to showcase various kind of cyber attack which are currently faced by the employees. The most common cyber attacks are ransomware, password attack, crypto jacking, iot-based attacks, malware, social engineering attack and business email compromise. This Most Common Cyber Attack Faced By Our Employees Ppt Infographic Template Topics PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Most Common Cyber Attack Faced By Our Employees Ppt Infographic Template Topics PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today.

Data Wiper Spyware Attack Hermetic Wiper Cyber Attack Against Ukraine Slides PDF
This slide depicts the hermetic wiper attack on Ukrainian corporations, detected by a threat intelligence agency on February 23rd, and it damaged the master boot record through Ease US Partition Master.Deliver an awe inspiring pitch with this creative data wiper spyware attack hermetic wiper cyber attack against ukraine slides pdf bundle. Topics like hermetic wiper cyber attack against ukraine can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Phishing Scams And Attacks Dashboard With Improvement Curve Sample PDF
Mentioned slide showcases a comprehensive dashboard used to measure the cyber phishing attacks. Information covered in this slide is related to organization health risk, attack vendors, most vulnerable employees to attacks, improvement curve. Pitch your topic with ease and precision using this cyber phishing scams and attacks dashboard with improvement curve sample pdf. This layout presents information on cyber phishing scams and attacks dashboard with improvement curve. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Table Of Contents For Russian Cyber Attacks On Ukraine Cell Summary PDF
This is a table of contents for russian cyber attacks on ukraine cell summary pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like protect, cybersecurity, cyber cell, concerned. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Data Wiper Spyware Attack Does Ukraine And Russia Cyber Warfare Kill People Professional PDF
This slide describes if Ukraine and Russia cyber warfare is killing people and German cybersecurity expert Matthias Schulze said people have died due to misinformation efforts in earlier conflicts.Deliver an awe inspiring pitch with this creative data wiper spyware attack does ukraine and russia cyber warfare kill people professional pdf bundle. Topics like result of misinformation, protection become, susceptible targets can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Comparative Assessment Of Anti Phishing Software To Prevent Cyber Scams And Attacks Structure PDF
Mentioned slide showcases comparison of various softwares which can be used to prevent cyber phishing attacks. The key features of softwares are spam filters, customizable filtering, malicious file integration, integration, report attacks etc. Showcasing this set of slides titled comparative assessment of anti phishing software to prevent cyber scams and attacks structure pdf. The topics addressed in these templates are comparative assessment of anti phishing software to prevent cyber scams and attacks. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
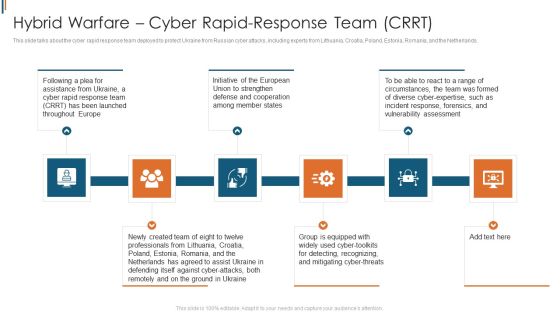
Ukraine Cyberwarfare Hybrid Warfare Cyber Rapid Response Team Crrt Structure Pdf
This slide talks about the cyber rapid response team deployed to protect Ukraine from Russian cyber attacks, including experts from Lithuania, Croatia, Poland, Estonia, Romania, and the Netherlands. Presenting ukraine cyberwarfare hybrid warfare cyber rapid response team crrt structure pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Initiative of the European Union to strengthen defense and cooperation among member states, Group is equipped with widely used cyber toolkits for detecting, recognizing, and mitigating cyber threats. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
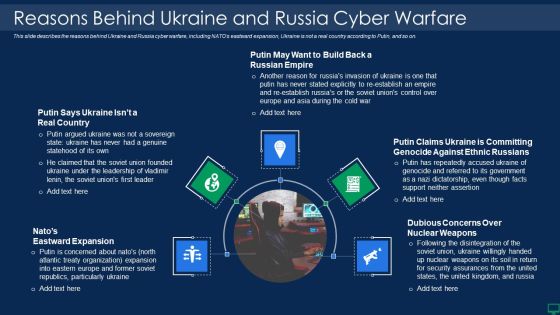
Russian Cyber Attacks On Ukraine IT Reasons Behind Ukraine And Russia Graphics PDF
This slide describes the reasons behind Ukraine and Russia cyber warfare, including NATOs eastward expansion, Ukraine is not a real country according to Putin, and so on. Presenting russian cyber attacks on ukraine it reasons behind ukraine and russia graphics pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like reasons behind ukraine and russia cyber warfare. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Terrorism Assault Average Loss To Firms In European Countries Slides PDF
This slide depicts the average loss to firms in European countries, representing Germany as the most affected country. Deliver and pitch your topic in the best possible manner with this cyber terrorism assault average loss to firms in european countries slides pdf Use them to share invaluable insights on German businesses, average loss , cyber terrorist attack and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Loss Caused By Different Types Of Cyber Attacks Ppt File Good PDF
This slide represents the different types of cyber attacks throughout the year, including the percentage of total loss caused by these attacks. Deliver an awe inspiring pitch with this creative loss caused by different types of cyber attacks ppt file good pdf bundle. Topics like organization, cost can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Ukraine Cyberwarfare Hacking Groups Launching Cyber Proxy War Against Russia Guidelines Pdf
This slide depicts the hacking groups such as the Anonymous hacker group, Conti ransomware gang, threat actors in Belarus launching cyber proxy war over Ukraine attacks by Russia. Presenting ukraine cyberwarfare hacking groups launching cyber proxy war against russia guidelines pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like hacking groups such as the Anonymous hacker group, Conti ransomware gang, threat actors in Belarus launching cyber proxy war over Ukraine attacks by Russia.. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Russian Cyber Attacks On Ukraine IT Banks On Alert For Russian Infographics PDF
This slide represents that banks are on alert for Russian reprisal cyber attacks on Society for Worldwide Interbank Financial Telecommunication Swift. Deliver an awe inspiring pitch with this creative russian cyber attacks on ukraine it banks on alert for russian infographics pdf bundle. Topics like system, global, payments can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Data Wiper Spyware Attack Ukraine And Russia Cyber Warfare Impact On Western Countries Themes PDF
This slide represents the Ukraine and Russia cyber warfare impact on western countries such as the United States, United Kingdom, and Estonia.Deliver an awe inspiring pitch with this creative data wiper spyware attack ukraine and russia cyber warfare impact on western countries themes pdf bundle. Topics like united kingdom advise, businesses lookout for unusual, russian activity can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Attacks On The Main Server Of Company Reverse Proxy For Load Balancing Mockup PDF
This slide shows the current situation of the organization through the total losses in millionsexperienced because of different types of the cyber attacks.Deliver an awe inspiring pitch with this creative Cyber Attacks On The Main Server Of Company Reverse Proxy For Load Balancing Mockup PDF bundle. Topics like Losses Organization, Due Cyberattacks, Based Attacks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Digital Investigation Icon For Cyber Attack Prevention Ppt PowerPoint Presentation Gallery Summary PDF
Persuade your audience using this digital investigation icon for cyber attack prevention ppt powerpoint presentation gallery summary pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including digital investigation icon for cyber attack prevention. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Agenda For Continuous Development Evaluation Plan To Eliminate Cyber Attacks Mockup PDF
This is a agenda for continuous development evaluation plan to eliminate cyber attacks mockup pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like agenda for continuous development evaluation plan to eliminate cyber attacks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Safety Breach Response Playbook Identifying The Origin And Type Of Cyber Incident Structure PDF
Following slide portrays information about the cyber incident source of origin, their description and type. Members can use this slide to effectively identify the source and type of any cyber attack. Want to ace your presentation in front of a live audience Our Safety Breach Response Playbook Identifying The Origin And Type Of Cyber Incident Structure PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

Cybersecurity Assessment Matrix Of Cyber Risks Ppt Icon Graphics Pictures PDF
This slide depicts the cyberattacks surface based on different property types. It also covers the attacks based on web or mobile applications, online payments, employee devices. Deliver an awe inspiring pitch with this creative cybersecurity assessment matrix of cyber risks ppt icon graphics pictures pdf bundle. Topics like assessment matrix of cyber risks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Identifying The Origin And Type Of Cyber Improving Cybersecurity With Incident Summary PDF
Following slide portrays information about the cyber incident source of origin, their description and type. Members can use this slide to effectively identify the source and type of any cyber attack.Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Identifying The Origin And Type Of Cyber Improving Cybersecurity With Incident Summary PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Identifying The Origin And Type Of Cyber Improving Cybersecurity With Incident Summary PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Multi Layered Approach To Prevent Cyber Phishing Scams And Attacks Themes PDF
Mentioned slide showcases approaches which can be implemented by organization to prevent cyber phishing attack. The approaches covered in the slide are attack prevention techniques, recognizing phishing emails, protecting firm from undetected emails etc. Presenting multi layered approach to prevent cyber phishing scams and attacks themes pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including email, implement, system. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
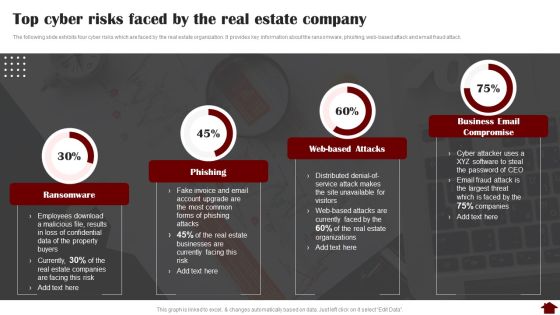
Top Cyber Risks Faced By The Real Estate Company Pictures PDF
The following slide exhibits four cyber risks which are faced by the real estate organization. It provides key information about the ransomware, phishing, web-based attack and email fraud attack. Deliver an awe inspiring pitch with this creative Top Cyber Risks Faced By The Real Estate Company Pictures PDF bundle. Topics like Ransomware, Phishing, Business Email Compromise can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Threats Response Playbook Identifying The Origin And Type Of Cyber Incident Rules PDF
Following slide portrays information about the cyber incident source of origin, their description and type. Members can use this slide to effectively identify the source and type of any cyber attack.This is a IT Threats Response Playbook Identifying The Origin And Type Of Cyber Incident Rules PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like External Removable, Malicious Attachment, Loss Valuable. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Data Wiper Spyware Attack Ukraine And Russia Cyber Warfare Russian Vigilante Hacker Sample PDF
This slide depicts the Russian vigilante hacker who was able to bring down some official Ukrainian websites and one military website along with his group of 6 hackers.Deliver and pitch your topic in the best possible manner with this data wiper spyware attack ukraine and russia cyber warfare russian vigilante hacker sample pdf Use them to share invaluable insights on ukraine and russia cyber warfare russian vigilante hacker and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Data Wiper Spyware Attack Cyber Attacks On Ukraine Are Conspicuous Elements PDF
This slide represents the conspicuous Russian cyber-attacks on Ukraine, including the attacks on government and banking websites, hacking of the countrys railway computer networks, etc.This is a data wiper spyware attack cyber attacks on ukraine are conspicuous elements pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like ukraine launched distributed, russian websites, belarusian hackers You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
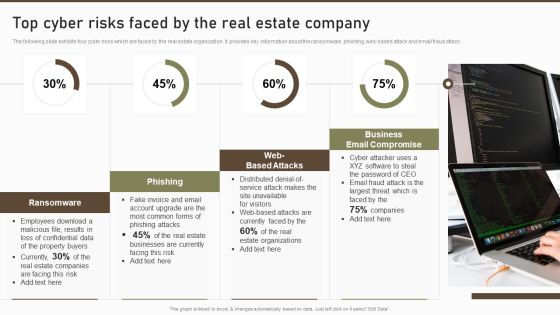
Top Cyber Risks Faced By The Real Estate Company Diagrams PDF
The following slide exhibits four cyber risks which are faced by the real estate organization. It provides key information about the ransomware, phishing, web-based attack and email fraud attack. Deliver an awe inspiring pitch with this creative Top Cyber Risks Faced By The Real Estate Company Diagrams PDF bundle. Topics like Ransomware Business Compromise, Businesses Currently can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Safety Incident Management Statistics Associated To Workplace Threats Elements PDF
This slide provides details regarding statistics associated to workplace threats that firms face in terms of data records theft, workplace violence, financial phishing, etc. Deliver and pitch your topic in the best possible manner with this cyber safety incident management statistics associated to workplace threats elements pdf. Use them to share invaluable insights on cyber attacks costs, organizations, organizations have, organizations face, data records and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Russian Cyber Attacks On Ukraine IT Cybersecurity Risks Of An Escalating Icons PDF
This slide represents the cybersecurity risks associated with Russia and Ukraine conflict that are the most serious cyber threat, and many organizations are advised to take precautions. This is a russian cyber attacks on ukraine it cybersecurity risks of an escalating icons pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like capabilities, economic, measures, severe, cybersecurity. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Data Wiper Spyware Attack Banks On Alert For Russian Reprisal Cyber Attacks On Swift Sample PDF
This slide represents that banks are on alert for Russian reprisal cyber attacks on Society for Worldwide Interbank Financial Telecommunication Swift. This is a data wiper spyware attack banks on alert for russian reprisal cyber attacks on swift sample pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like payments messaging system, military industrial complex, institutions suspended You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Major Cyber Phishing Scams And Attacks With Key Strategies Slides PDF
Mentioned slide showcases various cyber phishing attacks such as deceptive, spear, whaling and vishing. It provides detailed information about likelihood of attack, examples of attacks and strategies which can be implemented to overcome phishing attacks. Showcasing this set of slides titled major cyber phishing scams and attacks with key strategies slides pdf. The topics addressed in these templates are target, information, email. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Ukraine Cyberwarfare Shuck Worm Continues Cyber Espionage Attacks Against Ukraine Pictures Pdf
This slide represents the continuous cyber espionage attacks held by the shuck worm group against Ukraine. Most of these attacks were phishing emails to spread the malware among devices that could control remotely. Presenting ukraine cyberwarfare shuck worm continues cyber espionage attacks against ukraine pictures pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like organization typically, cybersecurity, evidence of attempted assaults. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Protection From Cyber Attacks Prediction From Machine Learning Ppt PowerPoint Presentation File Show
Presenting this set of slides with name protection from cyber attacks prediction from machine learning ppt powerpoint presentation file show. This is a five stage process. The stages in this process are technology, social network, social engineering. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Four Stages Of Protecting Functional Technology From Cyber Attacks Guidelines PDF
Persuade your audience using this four stages of protecting functional technology from cyber attacks guidelines pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including aware, vigilant, resilient. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Prevention Of Information Determining The Actors Behind Most Significant Cyber Attack Diagrams PDF
The purpose of this slide is to outline different actors who are involved in the most critical cyber attack. Online criminals, foreign governments, hackers and malicious insiders are some of the key players who are responsible for cyber attack. Present like a pro with Prevention Of Information Determining The Actors Behind Most Significant Cyber Attack Diagrams PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether youre in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
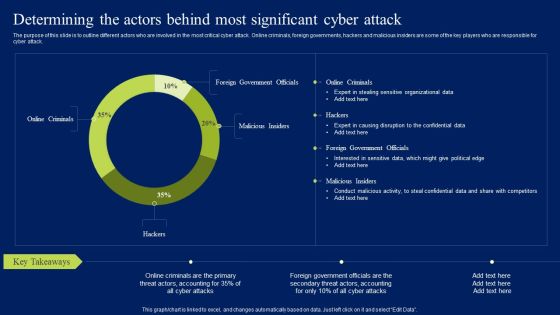
Determining The Actors Behind Most Significant Cyber Attack Ppt Layouts Mockup PDF
The purpose of this slide is to outline different actors who are involved in the most critical cyber attack. Online criminals, foreign governments, hackers and malicious insiders are some of the key players who are responsible for cyber attack. Want to ace your presentation in front of a live audience Our Determining The Actors Behind Most Significant Cyber Attack Ppt Layouts Mockup PDF can help you do that by engaging all the users towards you.. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.
Russian Cyber Attacks On Ukraine IT Threat Actors Supporting Russia And Ukraine Icons PDF
This slide shows the threat actors supporting Russia and Ukraine, such as hacker organization Anonymous, Cyber Partisan hacking organization, and Conti ransomware gang. Presenting russian cyber attacks on ukraine it threat actors supporting russia and ukraine icons pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like organization, systems, servers, planned, analyzing. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Data Wiper Spyware Attack Hybrid Warfare Cyber Rapid Response Download PDF
This slide talks about the cyber rapid response team deployed to protect Ukraine from Russian cyberattacks, including experts from Lithuania, Croatia, Poland, Estonia, Romania, and the Netherlands.This is a data wiper spyware attack hybrid warfare cyber rapid response download pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like launched throughout, cooperation among, vulnerability assessment You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
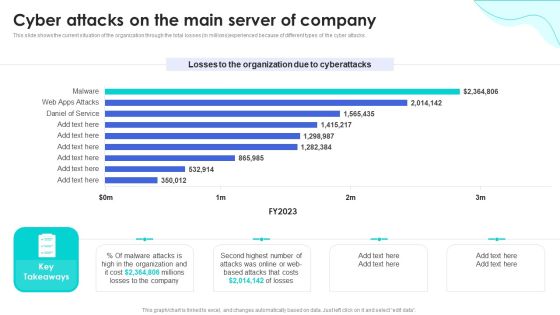
Reverse Proxy Web Server Cyber Attacks On The Main Server Of Company Background PDF
This slide shows the current situation of the organization through the total losses in millions experienced because of different types of the cyber attacks. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Reverse Proxy Web Server Cyber Attacks On The Main Server Of Company Background PDF can be your best option for delivering a presentation. Represent everything in detail using Reverse Proxy Web Server Cyber Attacks On The Main Server Of Company Background PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Ukraine Cyberwarfare Banks On Alert For Russian Reprisal Cyber Attacks On Swift Diagrams Pdf
This slide represents that banks are on alert for Russian reprisal cyber attacks on Society for Worldwide Interbank Financial Telecommunication Swift. This is a ukraine cyberwarfare banks on alert for russian reprisal cyber attacks on swift diagrams pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like global transaction networks payment messaging system might be targeted as a bottleneck, big banks are concerned that russian cyber assaults are becoming more common after seven of the nations, lenders were removed from swifts global payments messaging system. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Understanding The Frequency And Weightage Of Cyber Attacks By Departments Professional PDF
The purpose of this slide is to showcase the frequency and weightage of different cyber attacks on multiple departments. The major departments mentioned in the slide are financial, marketing, information technology IT and human resource HR. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Understanding The Frequency And Weightage Of Cyber Attacks By Departments Professional PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Understanding The Frequency And Weightage Of Cyber Attacks By Departments Professional PDF today and make your presentation stand out from the rest.

Recent Technologies In IT Industry Various Types Of Cyber Attacks On System Microsoft PDF
This slide explains Various types of cyber attacks on system on a system such as malware, phishing, man in the middle, distributed denial of service, brute force, SQL injection, and domain name system. Get a simple yet stunning designed Recent Technologies In IT Industry Various Types Of Cyber Attacks On System Microsoft PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Recent Technologies In IT Industry Various Types Of Cyber Attacks On System Microsoft PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Classify Assets Vulnerable To Cyber Attack Ppt PowerPoint Presentation File Infographics PDF
The following slide depicts some major assets that are more prone to cyber-attack. It mainly includes elements such as sales record, sales lead record, company internal database, customer and product information etc. If you are looking for a format to display your unique thoughts, then the professionally designed Classify Assets Vulnerable To Cyber Attack Ppt PowerPoint Presentation File Infographics PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Classify Assets Vulnerable To Cyber Attack Ppt PowerPoint Presentation File Infographics PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Cyber Terrorism Assault Financial Loss Faced By The Business Summary PDF
This slide depicts the average financial loss faced by the business when projects of different scales are attacked.This is a cyber terrorism assault financial loss faced by the business summary pdf template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like projects are targeted, cyber terrorists, attack on large You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
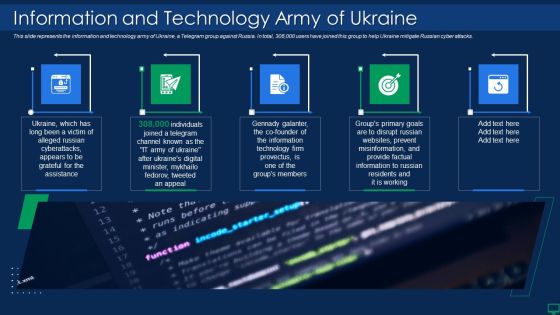
Russian Cyber Attacks On Ukraine IT Information And Technology Brochure PDF
This slide represents the information and technology army of Ukraine, a Telegram group against Russia. In total, 308,000 users have joined this group to help Ukraine mitigate Russian cyber attacks. Presenting russian cyber attacks on ukraine it information and technology brochure pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like technology, information. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Russian Cyber Attacks On Ukraine IT For The First Time In History Ideas PDF
This slide represents the official announcement from Lotem Finkelstein, head of threat intelligence at Check Point Software, that anyone can join Ukraine and Russia cyber warfare. Presenting russian cyber attacks on ukraine it for the first time in history ideas pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like technologies, global, organizations, community. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Business Threats Landscape Dashboard With Cyber Attacks Analysis Ppt Summary Brochure PDF
This slide illustrates risk landscape dashboard with cyber attacks analysis which contains malware attack frequency, country wise attacks, top 10 attacks, etc. It can assist IT managers in analyzing top threats so that they can be dealt with proper efficiency. Pitch your topic with ease and precision using this Business Threats Landscape Dashboard With Cyber Attacks Analysis Ppt Summary Brochure PDF. This layout presents information on Malware Attack Frequency, Every Minute, Every Second. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
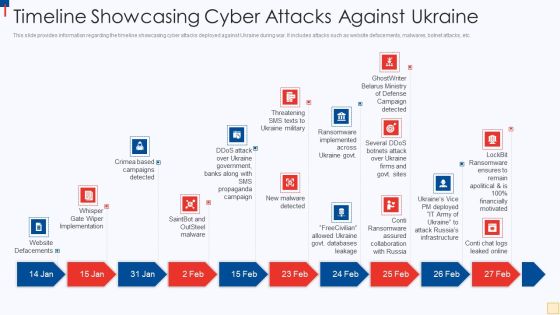
Ukraine Vs Russia Examining Timeline Showcasing Cyber Attacks Against Ukraine Ideas PDF
This slide provides information regarding the timeline showcasing cyber attacks deployed against Ukraine during war. It includes attacks such as website defacements, malwares, botnet attacks, etc. Presenting Ukraine Vs Russia Examining Timeline Showcasing Cyber Attacks Against Ukraine Ideas PDF to provide visual cues and insights. Share and navigate important information on ten stages that need your due attention. This template can be used to pitch topics like Website Defacements, Saintbot And Outsteel Malware, New Malware Detected, Threatening SMS Texts To Ukraine Military. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Understanding The Frequency And Weightage Of Cyber Attacks By Departments Inspiration PDF
The purpose of this slide is to showcase the frequency and weightage of different cyber attacks on multiple departments. The major departments mentioned in the slide are financial, marketing, information technology IT and human resource HR.Deliver and pitch your topic in the best possible manner with this Understanding The Frequency And Weightage Of Cyber Attacks By Departments Inspiration PDF. Use them to share invaluable insights on Financial Department, Marketing Team, Engineering Attack and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Data Wiper Spyware Attack Are There International Laws Establishing Cyber Policies Professional PDF
This slide describes the establishment of cyber policies by international laws, including the Budapest Convention on Cybercrime and the United Nations Group of Governmental Experts.Presenting data wiper spyware attack are there international laws establishing cyber policies professional pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like international agreement, coordinate state, responses to cybercrime In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Data Wiper Spyware Attack International Cyber Aid To Ukraine Icons PDF
This slide describes the international cyber assistance to Ukraine by 6 European Union nations such as Lithuania, the Netherlands, Poland, Estonia, Romania, and Croatia.Presenting data wiper spyware attack international cyber aid to ukraine icons pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like might interrupt, critical services, jeopardizing national In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Table Of Contents For Russian Cyber Attacks On Ukraine Elements PDF
Presenting table of contents for russian cyber attacks on ukraine elements pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like cybersecurity, websites, technical, analysis. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
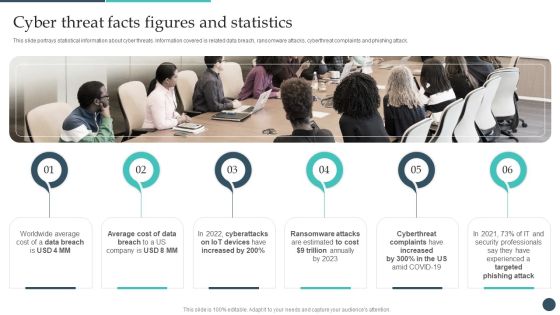
Safety Breach Response Playbook Cyber Threat Facts Figures And Statistics Demonstration PDF
This slide portrays statistical information about cyber threats. Information covered is related data breach, ransomware attacks, cyberthreat complaints and phishing attack. Boost your pitch with our creative Safety Breach Response Playbook Cyber Threat Facts Figures And Statistics Demonstration PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you dont have to invest time in any additional work. Just grab the template now and use them.
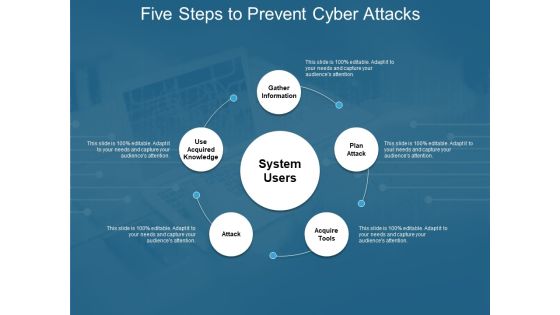
Five Steps To Prevent Cyber Attacks Ppt PowerPoint Presentation Infographic Template Inspiration
Presenting this set of slides with name five steps to prevent cyber attacks ppt powerpoint presentation infographic template inspiration. This is a five stage process. The stages in this process are technology, social network, social engineering. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Steps To Stay Safe From Cyber Attacks Threat Modelling Ppt PowerPoint Presentation Infographics Gallery
Presenting this set of slides with name steps to stay safe from cyber attacks threat modelling ppt powerpoint presentation infographics gallery. This is a six stage process. The stages in this process are technology, social network, social engineering. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Appropriate Information Management In Healthcare Sector To Decrease Cyber Attacks For Icons Slide Inspiration PDF
Presenting our innovatively structured appropriate information management in healthcare sector to decrease cyber attacks for icons slide inspiration pdf set of slides. The slides contain a hundred percent editable icons. You can replace these icons without any inconvenience. Therefore, pick this set of slides and create a striking presentation.
Icons Slide For Continuous Development Evaluation Plan To Eliminate Cyber Attacks Structure PDF
Introducing our well designed icons slide for continuous development evaluation plan to eliminate cyber attacks structure pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
Icons Slide For Russian Cyber Attacks On Ukraine IT Pictures PDF
Presenting our innovatively structured icons slide for russian cyber attacks on ukraine it pictures pdf set of slides. The slides contain a hundred percent editable icons. You can replace these icons without any inconvenience. Therefore, pick this set of slides and create a striking presentation.
Russian Cyber Attacks On Ukraine IT Hacker Group Anonymous Has Waged Icons PDF
This slide depicts the anonymous organization and how they have started a cyberwar against Russia by gathering worldwide hackers through Twitter. Deliver and pitch your topic in the best possible manner with this russian cyber attacks on ukraine it hacker group anonymous has waged icons pdf. Use them to share invaluable insights on hacker group anonymous has waged a cyberwar against russia and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Physical Systems Architecture Physical Layer Ppt Infographics Infographic Template PDF
This slide represents the physical layer of cyber physical system architecture, including the devices used at this level, such as sensor units and actuator units and their tasks. Deliver and pitch your topic in the best possible manner with this Cyber Physical Systems Architecture Physical Layer Ppt Infographics Infographic Template PDF. Use them to share invaluable insights on Applications Services, Communication Networks, Physical Infrastructures and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Threats Response Playbook Cyber Threat Facts Figures And Statistics Themes PDF
This slide portrays statistical information about cyber threats. Information covered is related data breach, ransomware attacks, cyberthreat complaints and phishing attack.This is a IT Threats Response Playbook Cyber Threat Facts Figures And Statistics Themes PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Ransomware Attacks, Cyberthreat Complaints, Trillion Annually. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Russian Cyber Attacks On Ukraine IT Technical Analysis Of Ddos Attacks Structure PDF
This slide represents the technical analysis of DDoS attacks against Ukrainian websites by showing the internet traffic to the Oschad Bank website on 15-16 February 2022. Deliver an awe inspiring pitch with this creative russian cyber attacks on ukraine it technical analysis of ddos attacks structure pdf bundle. Topics like technical analysis of ddos attacks against ukrainian websites can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
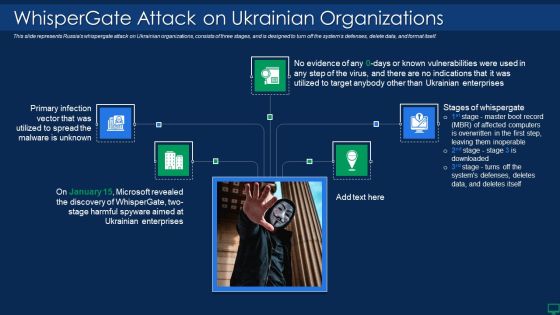
Russian Cyber Attacks On Ukraine IT Whispergate Attack On Ukrainian Microsoft PDF
This is a russian cyber attacks on ukraine it whispergate attack on ukrainian microsoft pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like target, enterprises. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Exploitation IT Impact Of Ethical Hackers On Business Template PDF
This slide represents the impact of ethical hackers on business by describing the decreased number of malicious attacks on the networks, such as DDOS attacks, online attacks, etc. Deliver an awe inspiring pitch with this creative cyber exploitation it impact of ethical hackers on business template pdf bundle. Topics like impact of ethical hackers on business can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Best Practices To Prevent Cyber Attacks Ppt PowerPoint Presentation File Model PDF
The following slide illustrates some activities to minimize the probability of cybercrimes within the organization. It includes elements such as utilizing anti-virus, preventing to open suspicious emails, keeping systems up-to date etc. Find highly impressive Best Practices To Prevent Cyber Attacks Ppt PowerPoint Presentation File Model PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Best Practices To Prevent Cyber Attacks Ppt PowerPoint Presentation File Model PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
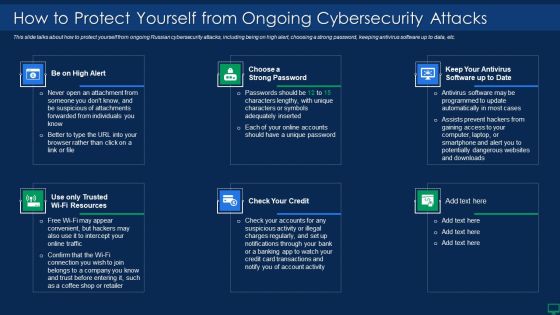
Russian Cyber Attacks On Ukraine IT How To Protect Yourself Summary PDF
This slide talks about how to protect yourself from ongoing Russian cybersecurity attacks, including being on high alert, choosing a strong password, keeping antivirus software up to data, etc. Presenting russian cyber attacks on ukraine it how to protect yourself summary pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like resources, account, potentially. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Analyse Impact Of Cyber Attack On Valuable Assets Ppt PowerPoint Presentation File Styles PDF
The following slide depicts the consequences of data breach threats to prevent information leakage. It mainly includes elements such as impact on revenue, protection cost, liability if lost, weightage criteria, asset importance etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Analyse Impact Of Cyber Attack On Valuable Assets Ppt PowerPoint Presentation File Styles PDF can be your best option for delivering a presentation. Represent everything in detail using Analyse Impact Of Cyber Attack On Valuable Assets Ppt PowerPoint Presentation File Styles PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Types Of Cyber Attacks Encountered By Employees Ppt PowerPoint Presentation File Infographics PDF
The following slide showcases the various types of cyber-attacks faced by staff to determine and formulate action plan. It includes elements such as malware, ransomware, man in the middle, phishing, denial of service etc. Present like a pro with Types Of Cyber Attacks Encountered By Employees Ppt PowerPoint Presentation File Infographics PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Russian Cyber Attacks On Ukraine IT Steps To Prepare For Cyberattacks Demonstration PDF
This slide represents the steps to take right now to prepare for cyberattacks by Russia, including access exposure, minimizing attack surface, executing the basics, and so on. Deliver an awe inspiring pitch with this creative russian cyber attacks on ukraine it steps to prepare for cyberattacks demonstration pdf bundle. Topics like organizations, network, system, enterprises, business can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
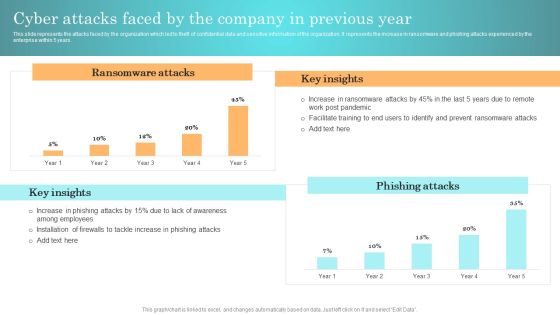
Incident Response Techniques Deployement Cyber Attacks Faced By The Company In Previous Year Inspiration PDF
This slide represents the attacks faced by the organization which led to theft of confidential data and sensitive information of the organization. It represents the increase in ransomware and phishing attacks experienced by the enterprise within 5 years. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Incident Response Techniques Deployement Cyber Attacks Faced By The Company In Previous Year Inspiration PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Incident Response Techniques Deployement Cyber Attacks Faced By The Company In Previous Year Inspiration PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Cyber Exploitation IT Distributed Denial Of Service Ddos Attacks Professional PDF
This slide represents the distributed denial of service attacks faced by the company, including the total number of attacks compared to 2019 and 2022. Deliver and pitch your topic in the best possible manner with this cyber exploitation it distributed denial of service ddos attacks professional pdf. Use them to share invaluable insights on distributed denial of service ddos attacks and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
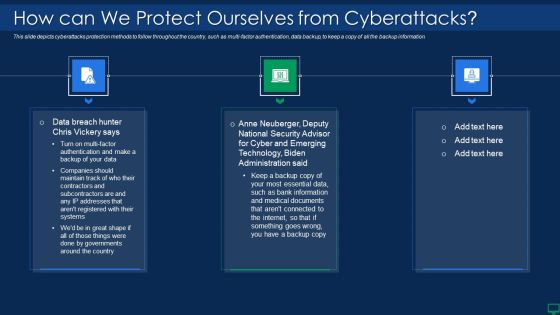
Russian Cyber Attacks On Ukraine IT How Can We Protect Ourselves Rules PDF
This slide depicts cyberattacks protection methods to follow throughout the country, such as multi factor authentication, data backup, to keep a copy of all the backup information. This is a russian cyber attacks on ukraine it how can we protect ourselves rules pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like internet, documents, information, data. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Prevention Of Information Understanding The Frequency And Weightage Of Cyber Attacks Professional PDF
The purpose of this slide is to showcase the frequency and weightage of different cyber attacks on multiple departments. The major departments mentioned in the slide are financial, marketing, information technology IT and human resource HR. Present like a pro with Prevention Of Information Understanding The Frequency And Weightage Of Cyber Attacks Professional PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether youre in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
Russian Cyber Attacks On Ukraine IT Triolan Suffers Severe Icons PDF
This slide describes the severe cyberattacks and infrastructure destruction experienced by major internet provider Triolan during the Russian Invasion. Deliver and pitch your topic in the best possible manner with this russian cyber attacks on ukraine it triolan suffers severe icons pdf. Use them to share invaluable insights on equipment, required, service, globally and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Table Of Contents For Russian Cyber Attacks On Ukraineteam Mockup PDF
This is a table of contents for russian cyber attacks on ukraineteam mockup pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organizations, technology, potential, accounts, team. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Terrorism Assault How To Protect Company From Trojan Attacks Demonstration PDF
This slide explains how to protect the company from trojan attacks which include procedures such as installing advanced antivirus software. This is a cyber terrorism assault how to protect company from trojan attacks demonstration pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like device conventional, next generation antivirus, prevent trojan infection You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Physical Systems In Water Distribution Systems Ppt Professional Background Image PDF
This slide represents the application of CPS in water distribution systems, including the tools such as the Attack Model and Toolbox to protect the system from attacks. Deliver an awe inspiring pitch with this creative Cyber Physical Systems In Water Distribution Systems Ppt Professional Background Image PDF bundle. Topics like Devices, Network, Distribution Systems can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
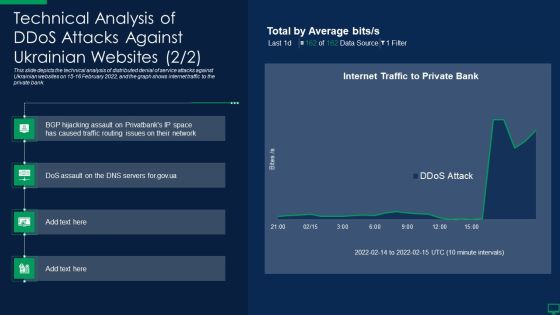
Russian Cyber Attacks On Ukraine IT Technical Analysis Of Ddos Attacks Against Designs PDF
This slide depicts the technical analysis of distributed denial of service attacks against Ukrainian websites on 15 16 February 2022, and the graph shows internet traffic to the private bank. Deliver and pitch your topic in the best possible manner with this russian cyber attacks on ukraine it technical analysis of ddos attacks against designs pdf. Use them to share invaluable insights on technical analysis of ddos attacks against ukrainian websites and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Successful Risk Administration Top Cyber Risks Faced By The Real Estate Company Pictures PDF
The following slide exhibits four cyber risks which are faced by the real estate organization. It provides key information about the ransomware, phishing, web-based attack and email fraud attack. The Successful Risk Administration Top Cyber Risks Faced By The Real Estate Company Pictures PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Russian Cyber Attacks On Ukraine IT Impact Of Defacement Attacks Portrait PDF
This slide shows the impact of defacement attacks and fake news on the public, and Meta has banned Russian media on its platforms, and Russia has restricted access to Facebook. This is a russian cyber attacks on ukraine it impact of defacement attacks portrait pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information, fundamental, method, material, social media. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Safety Incident Management Determine Sequence Phases For Threat Attack Contd Control Inspiration PDF
This slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. This is a cyber safety incident management determine sequence phases for threat attack contd control inspiration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like installation, covering tracks, actions and objectives, command and control. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Safety Incident Management Determine Sequence Phases For Threat Attack Rules PDF
This slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. Presenting cyber safety incident management determine sequence phases for threat attack rules pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like reconnaissance, weaponization, exploitation, delivery. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Hybrid Based Cyber Physical Systems Model Ppt Infographic Template Layout Ideas PDF
This slide represents the hybrid based cyber physical system model, including the features such as heterogeneous systems, networked, and so on. Presenting Hybrid Based Cyber Physical Systems Model Ppt Infographic Template Layout Ideas PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Dynamic Behavior, Development, Concurrent Systems. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
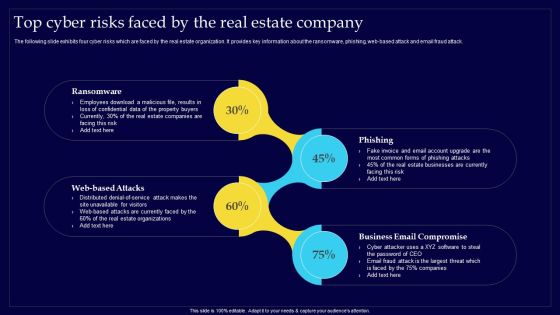
Executing Risk Mitigation Top Cyber Risks Faced By The Real Estate Company Structure PDF
The following slide exhibits four cyber risks which are faced by the real estate organization. It provides key information about the ransomware, phishing, web-based attack and email fraud attack. Retrieve professionally designed Executing Risk Mitigation Top Cyber Risks Faced By The Real Estate Company Structure PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Top Cyber Risks Faced By The Real Estate Company Enhancing Process Improvement By Regularly Information PDF
The following slide exhibits four cyber risks which are faced by the real estate organization. It provides key information about the ransomware, phishing, web-based attack and email fraud attack. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Top Cyber Risks Faced By The Real Estate Company Enhancing Process Improvement By Regularly Information PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Russian Cyber Attacks On Ukraine IT Ongoing Onslaught Of Russia Structure PDF
This slide represents the ongoing onslaught of Russia on Ukraine from December 2015 to Jan 2022. Russia has attacked Ukraine and other countries in many ways. This is a russian cyber attacks on ukraine it ongoing onslaught of russia structure pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like systems, industrial, networks, email. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Attacks Faced By The Company In Previous Year Portrait PDF
This slide represents the attacks faced by the organization which led to theft of confidential data and sensitive information of the organization. It represents the increase in ransomware and phishing attacks experienced by the enterprise within 5 years. Make sure to capture your audiences attention in your business displays with our gratis customizable Cyber Attacks Faced By The Company In Previous Year Portrait PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Cyber Terrorism Assault Types Of Ddos Attacks In The Company Sample PDF
This slide demonstrates the types of DDoS attacks happening in the company, which include volume-based attacks, protocol-based attacks, and application layer attacks. This is a cyber terrorism assault types of ddos attacks in the company sample pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like volume based attacks, protocol based attacks, application layer attacks You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Continuous Development Evaluation Plan To Eliminate Cyber Attacks Ppt PowerPoint Presentation Complete Deck With Slides
Pitch yourself both in house and outside by utilizing this complete deck. This continuous development evaluation plan to eliminate cyber attacks ppt powerpoint presentation complete deck with slides focuses on key fundamentals of the topic, displayed using different slides. With a total of forty seven slides, this template is the best tool you can use to persuade your audience. It will not only help you create great presentations but also induce strategic thinking because of its well researched content and graphics. You can easily personalize any of the elements to suit your unique business setting. Additionally, it can be saved in PNG, JPG, and PDF formats to save your time and resources.

Russian Cyber Attacks On Ukraine IT Continued Impact Of Ongoing Microsoft PDF
This slide shows the continued impact of ongoing cyberattacks on Ukrainian internet providers and how these cyberattacks are causing internet outages throughout the country. This is a russian cyber attacks on ukraine it continued impact of ongoing microsoft pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like sources, service, network, internet. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

3 Stage Plan To Prevent And Recover From Cyber Attack Ppt Ideas Show PDF
This slide signifies three step process to maintain and recover from ransomware and computer malfunction. It covers information about stages like prepare recovery plan, limit damage scope and incrementally remove risk. Persuade your audience using this 3 Stage Plan To Prevent And Recover From Cyber Attack Ppt Ideas Show PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Prepare Recovery Plan, Limit Scope Damage, Incrementally Remove Risks. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Terrorism Assault Use Of Strong Encrypted Password In The Company Icons PDF
This slide demonstrates the need to have encrypted passwords for various online accounts and indicates how almost every employee has the same password.Deliver and pitch your topic in the best possible manner with this cyber terrorism assault use of strong encrypted password in the company icons pdf Use them to share invaluable insights on use of strong encrypted password in the company and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Table Of Contents For Cyber Network Simulation Platform Capital Funding Pitch Deck Slides PDF
Deliver and pitch your topic in the best possible manner with this table of contents for cyber network simulation platform capital funding pitch deck slides pdf Use them to share invaluable insights on our go to market plan, our key team members, key growth drivers for vr industry and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Global Cyber Terrorism Incidents On The Rise IT Confidential Data Should Be Backup Structure PDF
This slide emphasizes the significance of backing up private data, which enables for data recovery in the event of an attack. Presenting global cyber terrorism incidents on the rise it confidential data should be backup structure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like confidential data should be backup. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Global Cyber Terrorism Incidents On The Rise IT Financial Loss Faced By The Business Designs PDF
This slide depicts the average financial loss faced by the business when projects of different scales are attacked. This is a global cyber terrorism incidents on the rise it financial loss faced by the business designs pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like targeted, revenue, financial. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Phishing Scams And Attacks Ppt PowerPoint Presentation Complete With Slides
If designing a presentation takes a lot of your time and resources and you are looking for a better alternative, then this cyber phishing scams and attacks ppt powerpoint presentation complete with slides is the right fit for you. This is a prefabricated set that can help you deliver a great presentation on the topic. All the fourteen slides included in this sample template can be used to present a birds-eye view of the topic. These slides are also fully editable, giving you enough freedom to add specific details to make this layout more suited to your business setting. Apart from the content, all other elements like color, design, theme are also replaceable and editable. This helps in designing a variety of presentations with a single layout. Not only this, you can use this PPT design in formats like PDF, PNG, and JPG once downloaded. Therefore, without any further ado, download and utilize this sample presentation as per your liking.
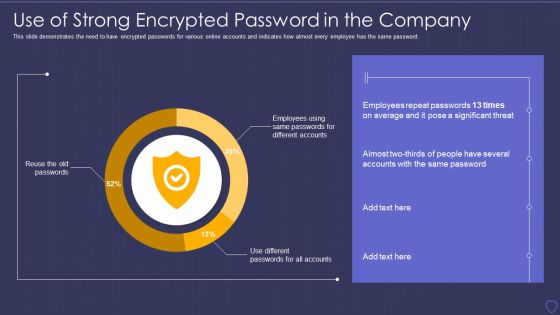
Global Cyber Terrorism Incidents On The Rise IT Use Of Strong Encrypted Password Download PDF
This slide demonstrates the need to have encrypted passwords for various online accounts and indicates how almost every employee has the same password. Deliver and pitch your topic in the best possible manner with this global cyber terrorism incidents on the rise it use of strong encrypted password download pdf. Use them to share invaluable insights on use of strong encrypted password in the company and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
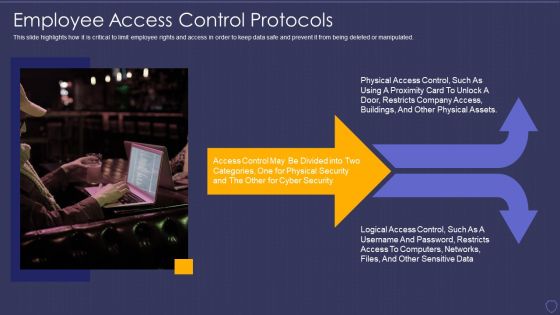
Global Cyber Terrorism Incidents On The Rise IT Employee Access Control Protocols Download PDF
This slide highlights how it is critical to limit employee rights and access in order to keep data safe and prevent it from being deleted or manipulated. Presenting global cyber terrorism incidents on the rise it employee access control protocols download pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like employee access control protocols. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Physical Systems In Water Distribution Systems Ppt PowerPoint Presentation File Backgrounds PDF
This slide represents the application of CPS in water distribution systems, including the tools such as the Attack Model and Toolbox to protect the system from attacks. Welcome to our selection of the Cyber Physical Systems In Water Distribution Systems Ppt PowerPoint Presentation File Backgrounds PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

Cyber Exploitation IT Loss Of Customers And Client Information Guidelines PDF
This slide represents the loss of information that happened in the company and the causes of the data loss, including theft, hardware destruction, computer viruses, and human error. Deliver and pitch your topic in the best possible manner with this cyber exploitation it loss of customers and client information guidelines pdf. Use them to share invaluable insights on computer viruses, software corruption, hardware failure, hardware destruction, human error and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Exploitation IT Preventing Measures For Social Media Accounts Themes PDF
This slide represents the preventing measures for social media accounts, including setting up login notifications, updating social media login credentials, using anti-malware software, and reviewing company policies. Presenting cyber exploitation it preventing measures for social media accounts themes pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like social media policies, anti malware software, social media login credentials. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Safety Incident Management Determine Staff Training Schedule For Skills Enhancement Ideas PDF
The employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. Presenting cyber safety incident management determine staff training schedule for skills enhancement ideas pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like advanced software training, advanced skills training, training module . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Safety Incident Management Determine Threat Management Team Structure Professional PDF
The threat management team generally comprise of senior management personnel that have authority and resources to accelerate the companys internal incident response. They will be responsible in managing human impacts both employees and community, company reputation, share values, and corporate assets. This is a cyber safety incident management determine threat management team structure professional pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like determine threat management team structure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
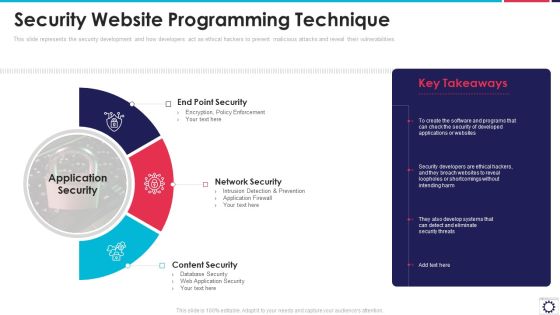
Website Programming IT Security Website Programming Technique Ppt PowerPoint Presentation File Infographics PDF
This slide represents the security development and how developers act as ethical hackers to prevent malicious attacks and reveal their vulnerabilities. Presenting website programming it security website programming technique ppt powerpoint presentation file infographics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like end point security, network security, content security, application security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Russian Cyber Attacks On Ukraine IT Ppt PowerPoint Presentation Complete With Slides
Induce strategic thinking by presenting this complete deck. Enthrall your audience by deploying this thought provoking PPT deck. It can be downloaded in both standard and widescreen aspect ratios, thus making it a complete package to use and deploy. Convey your thoughts and actions using the sixty four slides presented in this complete deck. Additionally, feel free to alter its components like color, graphics, design, etc, to create a great first impression. Grab it now by clicking on the download button below.

Distributed Computing Security Of Data And Networks In Edge Computing Ideas PDF
This slide represents the security of data and networks in edge computing. It also shows that data is secure because data is not traveling on any network however, edge devices are vulnerable.This is a Distributed Computing Security Of Data And Networks In Edge Computing Ideas PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Conduct Analytics, Devices Themselves, Vulnerability You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Major Reasons For Poor Security Management In The Company Download PDF
This slide shows some of the major reasons for poor security management in the company along with tips in order to resolve the issue. Deliver an awe inspiring pitch with this creative major reasons for poor security management in the company download pdf bundle. Topics like applications, operating systems, network, security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
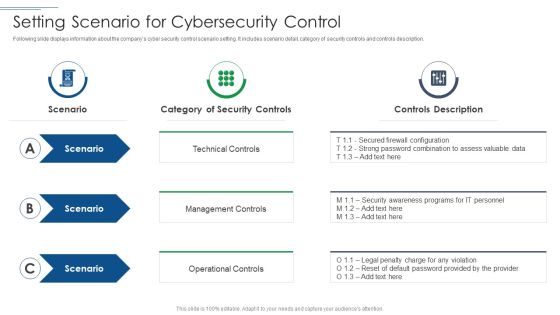
IT Security Risk Management Approach Introduction Setting Scenario For Cybersecurity Control Professional PDF
This is a IT Security Risk Management Approach Introduction Setting Scenario For Cybersecurity Control Professional PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Technical Control, Management Controls, Operational Controls. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Online Payment Service Payment Security And Fraud Management Solutions Portrait PDF
Payment security and fraud management solutions for the user to limit losses while maintain a high level of customer satisfaction. Presenting online payment service payment security and fraud management solutions portrait pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like operational costs, behavioural analytics, mobile application. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

Organizational Network Security Awareness Staff Learning Organization Impact Metrics Strategic Structure PDF
This slides the metrics That assess how your security awareness plan serves the overall security system of your company, and therefore the organizations mission. Deliver and pitch your topic in the best possible manner with this organizational network security awareness staff learning organization impact metrics strategic structure pdf. Use them to share invaluable insights on human resources, security operations, organization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
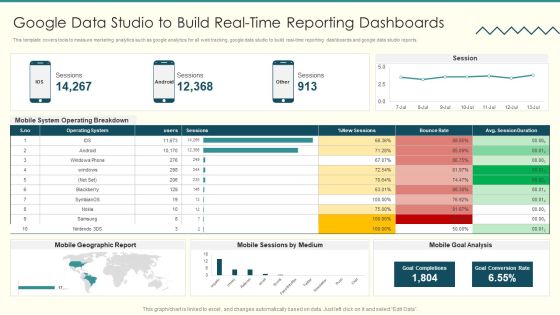
Security And Performance Digital Marketing Google Data Studio To Build Realtime Reporting Dashboards Information PDF
This template covers tools to measure marketing analytics such as google analytics for all web tracking, google data studio to build real time reporting dashboards and google data studio reports.Deliver an awe inspiring pitch with this creative Security And Performance Digital Marketing Google Data Studio To Build Realtime Reporting Dashboards Information PDF bundle. Topics like Operating Breakdown, Session Duration, Goal Completions can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

SDN Security Architecture Factors Influencing Software Defined Networking SDN Adoption Summary PDF
This slide represents the factors influencing SDN adoption, including cultural change, security risks, interoperability, scalability, performance, and reliability. SDN is appealing regarding network simplicity and investment, and operational cost savings. This modern and well arranged SDN Security Architecture Factors Influencing Software Defined Networking SDN Adoption Summary PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
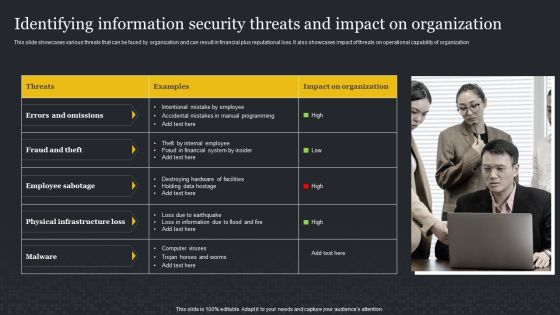
Identifying Information Security Threats And Impact On Organization Cybersecurity Risk Assessment Formats PDF
This slide showcases various threats that can be faced by organization and can result in financial plus reputational loss. It also showcases impact of threats on operational capability of organization. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Identifying Information Security Threats And Impact On Organization Cybersecurity Risk Assessment Formats PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Identifying Information Security Threats And Impact On Organization Cybersecurity Risk Assessment Formats PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Elements Of IT Security Disaster Recovery Planning Ppt Icon Rules PDF
This slide depicts the disaster recovery plan in the network security model and what strategies an organization needs to adopt to recover from an attack or natural disaster. This is a elements of information technology security disaster recovery planning ppt outline background pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like business, security, operations, business. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

White Hat Hacker Vs Black Hat Hacker Security Ppt File Example PDF
This slide represents a comparison between white hat hackers and black hat hackers based on the factors such as legality, ownership, and motive. Deliver and pitch your topic in the best possible manner with this white hat hacker vs black hat hacker security ppt file example pdf. Use them to share invaluable insights on ownership, networks, organizations, security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Common Methods Used To Threaten IT Security IT Ppt Inspiration Rules PDF
This slide depicts the standard methods used to threaten cyber-security by cybercriminals or attackers. It also shows the reasons for these threats and preventions from these threats. This is a common methods used to threaten it security it ppt inspiration rules pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like malware, daniel of service, man in the middle, sql injection, phishing. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Web App Firewall Services IT Types Of Web Application Firewall Security Models Background PDF
This slide represents the various types of WAF security models, including the whitelist or negative security model, blacklist or positive security model, and hybrid security model. Presenting web app firewall services it types of web application firewall security models background pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like applications, organizations. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Types Of Web Application Firewall Security Models WAF Platform Themes PDF
This slide represents the various types of WAF security models, including the whitelist or negative security model, blacklist or positive security model, and hybrid security model. Presenting Types Of Web Application Firewall Security Models WAF Platform Themes PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like White List Access Control, Black List Access Control. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

SDN Security Architecture Features Of Software Defined Networking SDN Infographics PDF
This slide depicts the features of software defined networking that is intended to make a network more versatile and manageable. It includes streamlining operations, reducing time to market, developing customizable networks, and laying the foundation for intention. This SDN Security Architecture Features Of Software Defined Networking SDN Infographics PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The SDN Security Architecture Features Of Software Defined Networking SDN Infographics PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Electoral Mechanism IT Voting System Standards Security Ppt Professional Sample PDF
This slide represents the security standard of the voting system that ensures the security of voting machines to prevent them from being tempered or manipulated through physical security, auditability, and internet connection. Deliver an awe inspiring pitch with this creative electoral mechanism it voting system standards security ppt professional sample pdf bundle. Topics like physical security of equipment and ballots, auditability, internet connection can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
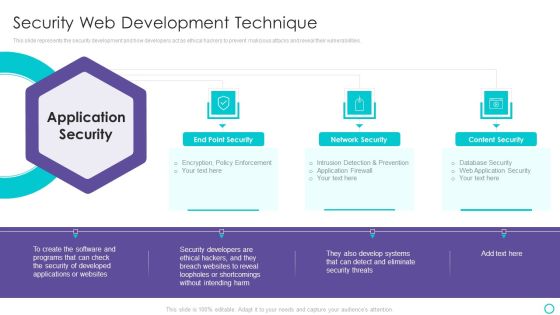
Website Designing And Development Service Security Web Development Technique Themes PDF
This slide represents the security development and how developers act as ethical hackers to prevent malicious attacks and reveal their vulnerabilities.This is a Website Designing And Development Service Security Web Development Technique Themes PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Network Security, Content Security, Loopholes Or Shortcomings You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Online Network Security Against Hackers And Internet Threats Ppt PowerPoint Presentation File Show PDF
Persuade your audience using this online network security against hackers and internet threats ppt powerpoint presentation file show pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including online network security against hackers and internet threats. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

WAF Introduction Types Of Web Application Firewall Security Models Information PDF
This slide represents the various types of WAF security models, including the whitelist or negative security model, blacklist or positive security model, and hybrid security model. Are you searching for a WAF Introduction Types Of Web Application Firewall Security Models Information PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download WAF Introduction Types Of Web Application Firewall Security Models Information PDF from Slidegeeks today.

Cybersecurity Risk Scorecard Information Security Companies Risk Coverage Scorecard Icons PDF
Deliver an awe inspiring pitch with this creative cybersecurity risk scorecard information security companies risk coverage scorecard icons pdf bundle. Topics like hacker protection, network security, cubit score can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Distributed Computing IT Security Of Data And Networks In Edge Computing Themes PDF
This slide represents the security of data and networks in edge computing. It also shows that data is secure because data is not traveling on any network however, edge devices are vulnerable. Presenting distributed computing it security of data and networks in edge computing themes pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like organization, data storage, computing security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Coder Checking Business Internet Security Threats Ppt PowerPoint Presentation Gallery Model PDF
Persuade your audience using this coder checking business internet security threats ppt powerpoint presentation gallery model pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including coder checking business internet security threats. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

5G Network Applications And Features Security Architecture In 5G Technology Elements PDF
This slide represents the security architecture in 5G technology, including the system-wide security tasks and 5G function element deployments or vertical security. The components include devices, global wireless solutions, access and network, applications and cloud infrastructure, and user ID administration. Whether you have daily or monthly meetings, a brilliant presentation is necessary. 5G Network Applications And Features Security Architecture In 5G Technology Elements PDF can be your best option for delivering a presentation. Represent everything in detail using 5G Network Applications And Features Security Architecture In 5G Technology Elements PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Identifying Employees For Information Security Training Programme Cybersecurity Risk Assessment Pictures PDF
This slide showcases plan that can help organization to conduct training for employees for information security risk management. It will enable employees to monitor risks and resolve them in timely manner. There are so many reasons you need a Identifying Employees For Information Security Training Programme Cybersecurity Risk Assessment Pictures PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Execution Of ICT Strategic Plan Overview Of Business ICT Security For Data Protection Sample PDF
This slide represents overview of ICT information and communication technology business security. It covers types and features for security such as network security, endpoint security etc. Welcome to our selection of the Execution Of ICT Strategic Plan Overview Of Business ICT Security For Data Protection Sample PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
Hacker Icon For Online Security Ppt PowerPoint Presentation Styles Example PDF
Persuade your audience using this hacker icon for online security ppt powerpoint presentation styles example pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including hacker icon for online security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

IT Security Hacker Altered Business Practices Due To Hacking Structure PDF
This slide represents that hackers forced the company to alter business practices followed by years and shut down online shopping stores in some regions.Deliver an awe inspiring pitch with this creative IT Security Hacker Altered Business Practices Due To Hacking Structure PDF bundle. Topics like Stored Information, Personal Information, Social Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Steps For Information Security Risk Management Cybersecurity Risk Assessment Mockup PDF
This slide steps which can help organization to implement information security risk management program in organization. Its key steps are identify, protect, detect and respond. Create an editable Steps For Information Security Risk Management Cybersecurity Risk Assessment Mockup PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Steps For Information Security Risk Management Cybersecurity Risk Assessment Mockup PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

IT Security Hacker Benefits Of Ethical Hackers To Business Diagrams PDF
This slide depicts the benefits of ethical hackers to the business, including regaining the trust of customers and clients, setting a secure network setup, and finding flaws in our infrastructure from a hackers point of view.Presenting IT Security Hacker Benefits Of Ethical Hackers To Business Diagrams PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Consumer And Investor, Assist In The Protection, Prevents Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Execution Of ICT Strategic Plan Network Security Model To Effective Communication Demonstration PDF
This slide represents the network security model for effective communication in the organization. It covers information regarding security threats, firewalls, virtual private networks, etc. Get a simple yet stunning designed Execution Of ICT Strategic Plan Network Security Model To Effective Communication Demonstration PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Execution Of ICT Strategic Plan Network Security Model To Effective Communication Demonstration PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Elements Of IT Security End User Education Ppt Summary Portrait PDF
This slide shows the end-user education within the network security model. It also represents various factors that effective training plans should involve. Presenting elements of information technology security end user education ppt model graphics pictures pdf to provide visual cues and insights. Share and navigate important information on ten stages that need your due attention. This template can be used to pitch topics like elements of information technology security end user education. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Solarwinds Security Event Manager Ethical Hacking Tool Ppt Show Clipart Images PDF
This slide represents the SolarWinds security event manager ethical hacking tool and its features such as integrity monitoring, easy to use user interface, built-in compliance reports, etc. Presenting solarwinds security event manager ethical hacking tool ppt show clipart images pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like network, security program, dashboard, system. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
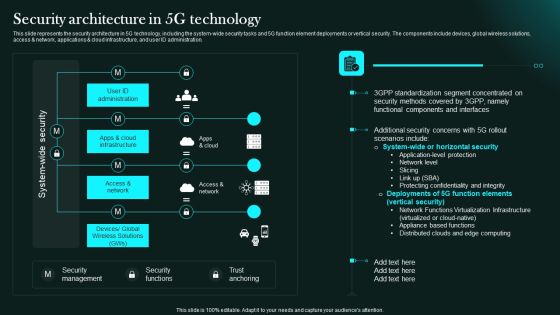
Security Architecture In 5G Technology 5G Network Functional Architecture Clipart PDF
This slide represents the security architecture in 5G technology, including the system-wide security tasks and 5G function element deployments or vertical security. The components include devices, global wireless solutions, access network, applications cloud infrastructure, and user ID administration.Retrieve professionally designed Security Architecture In 5G Technology 5G Network Functional Architecture Clipart PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You Do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Software Defined Networking Development Strategies What Role Does SDN Play In Customer Security Brochure PDF
This slide represents the role of software-defined networking in customer security. It allows clients to have separate settings for each type of network traffic and permits a low-security public-facing network for regular information. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Software Defined Networking Development Strategies What Role Does SDN Play In Customer Security Brochure PDF can be your best option for delivering a presentation. Represent everything in detail using Software Defined Networking Development Strategies What Role Does SDN Play In Customer Security Brochure PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Cybersecurity Risk Scorecard Information Security Scorecard For Company With Risk Gap Professional PDF
Presenting cybersecurity risk scorecard information security scorecard for company with risk gap professional pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like protective technology, continuous security monitoring, training of employees. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Workforce Security Realization Coaching Plan Problem Faced By The Organization Ppt Styles PDF
This slide covers the problem faced by organization caused by employees due to lack of security awareness training programs. This is a workforce security realization coaching plan problem faced by the organization ppt styles pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity, social engineering, financial impact, organization, security awareness. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Firewall As A Service Fwaas Working And Security Features Ppt File Guidelines PDF
This slide describes the working and security features of the firewall as a service. The purpose of this slide is to demonstrate the working of the firewall as a service, including its security features such as packet filtering, network monitoring, IPsec, SSL VPN support, DPI, and IP mapping. Create an editable Firewall As A Service Fwaas Working And Security Features Ppt File Guidelines PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Firewall As A Service Fwaas Working And Security Features Ppt File Guidelines PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Information Technology Security Highest Number Of Malware Attacks In Departments Ppt Styles Slide Portrait PDF
This slide depicts the impact of network security training on an organization. It also shows how trained employees can reduce network attacks in the organization. Deliver and pitch your topic in the best possible manner with this information technology security highest number of malware attacks in departments ppt styles slide portrait pdf. Use them to share invaluable insights on phishing, network, intrusion, inadvertent disclosure and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Deploying SDN System What Role Does SDN Play In Customer Security Structure PDF
This slide represents the role of software-defined networking in customer security. It allows clients to have separate settings for each type of network traffic and permits a low-security public-facing network for regular information. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Deploying SDN System What Role Does SDN Play In Customer Security Structure PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Deploying SDN System What Role Does SDN Play In Customer Security Structure PDF.

Web App Firewall Services IT Security Use Cases Of Web Application Firewall Deployment Brochure PDF
This slide represents the security use cases of web application firewall and how it would stop cyberattacks such as DDoS attacks, malicious bot abuse, and customer data breaches. Presenting web app firewall services it security use cases of web application firewall deployment brochure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like network, application, performance, material. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
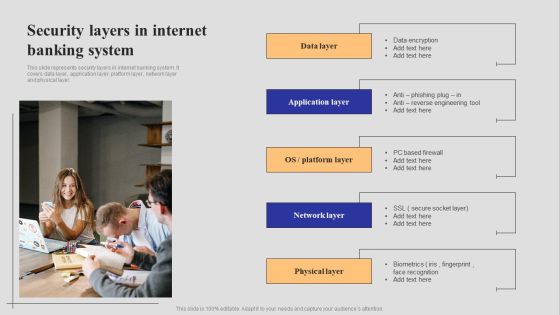
Introduction To Digital Banking Services Security Layers In Internet Banking System Guidelines PDF
This slide represents security layers in internet banking system. It covers data layer, application layer, platform layer, network layer and physical layer. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Introduction To Digital Banking Services Security Layers In Internet Banking System Guidelines PDF can be your best option for delivering a presentation. Represent everything in detail using Introduction To Digital Banking Services Security Layers In Internet Banking System Guidelines PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Allocating Budget For Information Security Risk Management Programme Cybersecurity Risk Assessment Brochure PDF
This slide showcase budget to be allocated for conducting training for information security risk management. It showcases budget for areas like cybersecurity awareness, threat detection and risk management. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Allocating Budget For Information Security Risk Management Programme Cybersecurity Risk Assessment Brochure PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Global Cloud Based Email Security Market Key Players Ppt Model Graphics Example PDF
Presenting this set of slides with name global cloud based email security market key players ppt model graphics example pdf. The topics discussed in these slides are company name, founded in, headquarters, market share, geographical presence, no of employees. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
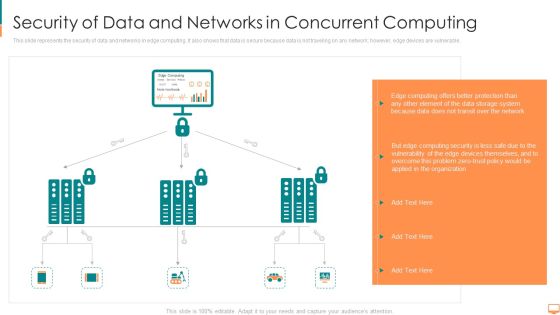
Security Of Data And Networks In Concurrent Computing Ppt File Themes PDF
This slide represents the security of data and networks in edge computing. It also shows that data is secure because data is not traveling on any network however, edge devices are vulnerable. This is a security of data and networks in concurrent computing ppt file themes pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like computing, transit, storage, system, protection, network. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
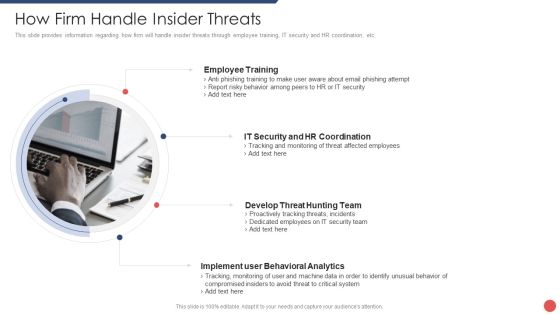
Security Functioning Centre How Firm Handle Insider Threats Ppt Summary Background Image PDF
This slide provides information regarding how firm will handle insider threats through employee training, IT security and HR coordination, etc. This is a security functioning centre how firm handle insider threats ppt summary background image pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employee training, develop threat hunting team, implement user behavioral analytics. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
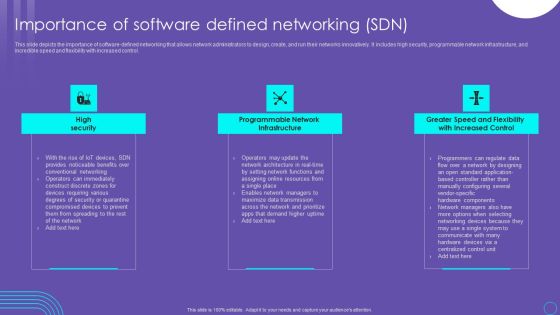
SDN Security Architecture Importance Of Software Defined Networking SDN Graphics PDF
This slide depicts the importance of software defined networking that allows network administrators to design, create, and run their networks innovatively. It includes high security, programmable network infrastructure, and incredible speed and flexibility with increased control. Are you searching for a SDN Security Architecture Importance Of Software Defined Networking SDN Graphics PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download SDN Security Architecture Importance Of Software Defined Networking SDN Graphics PDF from Slidegeeks today.

IT Security Hacker Impact Of Ethical Hackers On Business Slides PDF
This slide represents the impact of ethical hackers on business by describing the decreased number of malicious attacks on the networks, such as DDOS attacks, online attacks, etc.Deliver an awe inspiring pitch with this creative IT Security Hacker Impact Of Ethical Hackers On Business Slides PDF bundle. Topics like Key Takeaways, Daniels Of Service, After Employing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Evolution Of Wireless Technologies What Security Features Does 5G 5Th Generation Portrait PDF
This slide depicts the security features included in 5th generation technology, such as new cryptographic techniques for individual component protection, network slicing, encryption of IMSI to avoid eavesdropping spots, authentication confirmation, and secure network for sensitive data. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Evolution Of Wireless Technologies What Security Features Does 5G 5Th Generation Portrait PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Evolution Of Wireless Technologies What Security Features Does 5G 5Th Generation Portrait PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Timeline For Information Security Risk Management Training Cybersecurity Risk Assessment Pictures PDF
This slide showcases timeline that can help organization to conduct training for information security risk management programme. It also showcases weekly and step progress. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Timeline For Information Security Risk Management Training Cybersecurity Risk Assessment Pictures PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Timeline For Information Security Risk Management Training Cybersecurity Risk Assessment Pictures PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

SDN Security Architecture Use Cases Of Software Defined Networking SDN Formats PDF
This slide represents the use cases of software defined networking, a developing technology that will eventually replace physical network designs with software controlled networking architecture. It shows its use in DevOps, campus networks, service provider networks, and data center security. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give SDN Security Architecture Use Cases Of Software Defined Networking SDN Formats PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable SDN Security Architecture Use Cases Of Software Defined Networking SDN Formats PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today
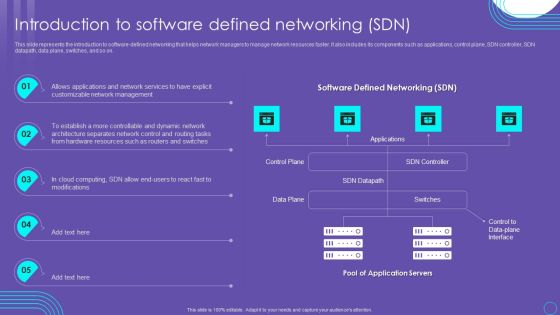
SDN Security Architecture Introduction To Software Defined Networking SDN Information PDF
This slide represents the introduction to software defined networking that helps network managers to manage network resources faster. It also includes its components such as applications, control plane, SDN controller, SDN datapath, data plane, switches, and so on. Presenting this PowerPoint presentation, titled SDN Security Architecture Introduction To Software Defined Networking SDN Information PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this SDN Security Architecture Introduction To Software Defined Networking SDN Information PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable SDN Security Architecture Introduction To Software Defined Networking SDN Information PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Open Radio Access Network IT Role Of Security In Open RAN Standards Inspiration PDF
This slide represents the role of security in open RAN, which is built on the zero trust model. It means not to trust anybody and all the authorized and unauthorized devices, personnel, or networks have to go through some security checks. Present like a pro with Open Radio Access Network IT Role Of Security In Open RAN Standards Inspiration PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Cybersecurity Guidelines IT Security Awareness And Training Policy Overview Portrait PDF
This slide represents the security awareness and training policy. It covers that the training program should be designed by management, and employees will sign a confidentiality agreement after getting the training. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Cybersecurity Guidelines IT Security Awareness And Training Policy Overview Portrait PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Cybersecurity Guidelines IT Security Awareness And Training Policy Overview Portrait PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Empowering Network Agility Through SDN What Role Does SDN Play In Customer Security Professional PDF
This slide represents the role of software defined networking in customer security. It allows clients to have separate settings for each type of network traffic and permits a low security public facing network for regular information. This Empowering Network Agility Through SDN What Role Does SDN Play In Customer Security Professional PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Best Work From Home Data Security Practices Improving Cybersecurity With Incident Inspiration PDF
Purpose of this slide is to provide information about the best data security practices that can be followed by employees who are working from home. Practices covered are configure WIFI encryption, avoid external devices, system update etc.Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Best Work From Home Data Security Practices Improving Cybersecurity With Incident Inspiration PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Best Work From Home Data Security Practices Improving Cybersecurity With Incident Inspiration PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
Gap Assessment Of Organization Information Security Cybersecurity Risk Assessment Ideas PDF
This slide showcases gap assessment of information security capabilities of organization. It also provides solutions to tackle the problems faced by company like frequent malware attacks and lack of awareness among employees. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Gap Assessment Of Organization Information Security Cybersecurity Risk Assessment Ideas PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Gap Assessment Of Organization Information Security Cybersecurity Risk Assessment Ideas PDF.

Implementing Cybersecurity Awareness Program To Prevent Attacks Strategies We Will Implement To Make Security Icons PDF
The purpose of this slide is to exhibit variety of strategies which can be used to engage employees in the security awareness training plan. The strategies highlighted in the slide are gamification, personalization, high-quality content and variety. Get a simple yet stunning designed Implementing Cybersecurity Awareness Program To Prevent Attacks Strategies We Will Implement To Make Security Icons PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Implementing Cybersecurity Awareness Program To Prevent Attacks Strategies We Will Implement To Make Security Icons PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Security Use Cases Of Web Application Firewall Deployment WAF Platform Ideas PDF
This slide represents the security use cases of web application firewall and how it would stop cyberattacks such as DDoS attacks, malicious bot abuse, and customer data breaches. This is a Security Use Cases Of Web Application Firewall Deployment WAF Platform Ideas PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Mitigate Ddos Attacks, Prevent Customer Data Breach, Block Malicious Bot Abuse. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Execution Of ICT Strategic Plan Key ICT Security Measures Used By Businesses Ideas PDF
This slide represents essential information and communication technology ICT security measures businesses use. It covers strong password authentication, data backup, network access control, etc. Create an editable Execution Of ICT Strategic Plan Key ICT Security Measures Used By Businesses Ideas PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Execution Of ICT Strategic Plan Key ICT Security Measures Used By Businesses Ideas PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Cybersecurity Risk Administration Plan Budget For Information Security Management Elements PDF
Mentioned slide shows budget for managing information security. It includes information such as functional area, software name, training duration, training cost, number of employees and total training cost.Presenting Cybersecurity Risk Administration Plan Budget For Information Security Management Elements PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Incident Management, Asset Management, Risk Management In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Budget For Information Security Risk Management Cybersecurity Risk Assessment Demonstration PDF
This slide showcases budget that can should be allocated for different information security risk management activities. It provides information about employees training, software implementation, risk monitoring and data backup. Want to ace your presentation in front of a live audience Our Budget For Information Security Risk Management Cybersecurity Risk Assessment Demonstration PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

Agenda For Organizational Network Security Awareness Staff Learning Ppt Styles Master Slide PDF
Deliver an awe-inspiring pitch with this creative agenda for organizational network security awareness staff learning ppt styles master slide pdf bundle. Topics like employees identifying, cybersecurity incidents, information systems can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Technology Security IT Safety Tips Protection Against IT Attacks Ppt Layouts Outfit PDF
This slide represents various tips or procedures that can be followed to prevent an organizations network security from cyberattacks or networkcriminals. This is a information technology security it safety tips protection against it attacks ppt layouts outfit pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like network, antivirus, systems, sources, unsecured. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

What Role Does SDN Play In Customer Security Ppt Outline Portrait PDF
This slide represents the role of software-defined networking in customer security. It allows clients to have separate settings for each type of network traffic and permits a low-security public-facing network for regular information. Do you know about Slidesgeeks What Role Does SDN Play In Customer Security Ppt Outline Portrait PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

 Home
Home