Cyber Security Image
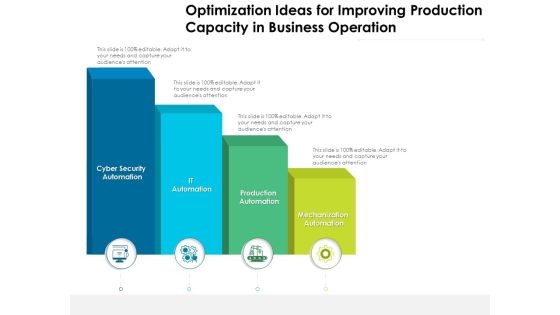
Optimization Ideas For Improving Production Capacity In Business Operation Ppt PowerPoint Presentation Outline Visual Aids PDF
Presenting this set of slides with name optimization ideas for improving production capacity in business operation ppt powerpoint presentation outline visual aids pdf. This is a four stage process. The stages in this process are mechanization automation, production automation, it automation, cyber security automation. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

NIST Cybersecurity Framework Implementation Tier Categories Rules PDF
The slide showcases Nist cyber security framework tiers which categorize your organizations security processes, it helps to analyze which tier your organization belongs to and what your current systems security requirements are. The tiers are as following partial, risk informed, repeatable and adaptive. Persuade your audience using this NIST Cybersecurity Framework Implementation Tier Categories Rules PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Partial, Risk Informed, Repeatable . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Steps Of Digital Risk Assessment In Organisation Ppt Infographics Templates PDF
The following slide highlights the steps of cyber security in organisation depicting network security, awareness, malware, external media, configuration, user privilege, incident management, monitoring and distant working. Presenting Steps Of Digital Risk Assessment In Organisation Ppt Infographics Templates PDF to dispense important information. This template comprises nine stages. It also presents valuable insights into the topics including Network Security, Awareness, Malware, External Media. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
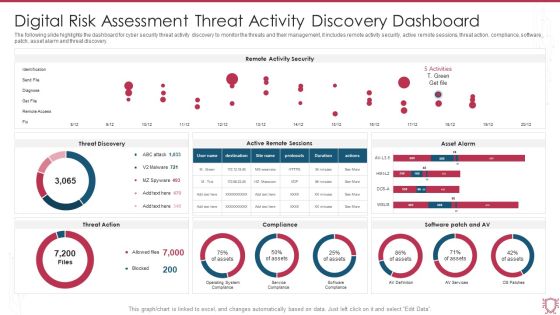
Digital Risk Assessment Threat Activity Discovery Dashboard Ppt Ideas Skills PDF
The following slide highlights the dashboard for cyber security threat activity discovery to monitor the threats and their management, it includes remote activity security, active remote sessions, threat action, compliance, software patch, asset alarm and threat discovery. Pitch your topic with ease and precision using this Digital Risk Assessment Threat Activity Discovery Dashboard Ppt Ideas Skills PDF. This layout presents information on Remote Activity Security, Threat Discovery, Asset Alarm. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
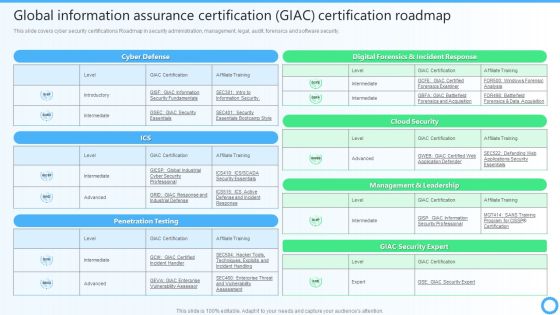
Global Information Assurance Certification GIAC Certification Roadmap IT Certifications To Enhance Template PDF
This slide covers cyber security certifications Roadmap in security administration, management, legal, audit, forensics and software security.This Global Information Assurance Certification GIAC Certification Roadmap IT Certifications To Enhance Template PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Cybersecurity Impact On Organization After Implementing Ppt Summary Influencers PDF
This slide depicts the impact of cyber security training on an organization. It also shows how trained employees can reduce cyber attacks in the organization. Presenting cybersecurity impact on organization after implementing ppt summary influencers pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like network intrusion, inadvertent disclosure, system misconfiguration. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Three Layers Of Digital Risk Assessment Management Process Ppt Summary Visual Aids PDF
The following slide highlights the three layers of cyber security management process which are dependent on people, process and technology, it helps company to manage cyber risks such as phishing attacks, data loss and exposed vulnerabilities. Presenting Three Layers Of Digital Risk Assessment Management Process Ppt Summary Visual Aids PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including People, Process, Technology. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Digital Risk Assessment Incident Response Plan For Attack Ppt Backgrounds PDF
The following slide highlights the cyber security incident response plan for attack illustrating objective, planning and action, which helps the management to take decision for risk mitigation strategy and allocation of budget and resources depending on criticality of cyber attack. Persuade your audience using this Digital Risk Assessment Incident Response Plan For Attack Ppt Backgrounds PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Objective, Planning, Action. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Technology Trends Impacting Digital Loans Ppt Summary Model PDF
This slide shows the impacts of technology trends on digital lending to enhance the customer service and simplify the process. It includes credit decision automation, personalized products, focus on cyber attacks, etc. Persuade your audience using this Technology Trends Impacting Digital Loans Ppt Summary Model PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Credit Decision Automation, Personalized Products, Focus Cyber Security . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Digital Risk Assessment Threat Intelligence Cycle Ppt Ideas Outfit PDF
The following slide highlights the cyber security threat intelligence cycle illustrating direction, collection, processing, analysis, reporting and action for quick fix of cyber threat and incident of breach to minimize the downtime of system. Persuade your audience using this Digital Risk Assessment Threat Intelligence Cycle Ppt Ideas Outfit PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Reporting, Analysis, Processing, Direction. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Threat Intelligence Use Cases And Objectives Demonstration PDF
This slide provides the use cases of cyber threat intelligence enabling security teams to understand and prepare for the challenges of an anticipated cyber threat. It covers aspects such as use case, objective and intelligence requirement. Presenting Threat Intelligence Use Cases And Objectives Demonstration PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Incident Analysis, Containment Remediation, Hunt Missions. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Setting Scenario For Cybersecurity Control Ppt Pictures Graphics Tutorials PDF
Following slide displays information about the companys cyber security control scenario setting. It includes scenario detail, category of security controls and controls description. Presenting setting scenario for cybersecurity control ppt pictures graphics tutorials pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like management controls, technical controls, operational controls. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Implementing Cybersecurity Awareness Program To Prevent Attacks How Much Employees Are Aware Elements PDF
The purpose of this slide is to showcase the cyber security assessment test result. It covers information about the pass fail rate of employees who received the security awareness training and fail rate by age. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Implementing Cybersecurity Awareness Program To Prevent Attacks How Much Employees Are Aware Elements PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

IT OT Organizational Structure Based On Target And Culture Convergence Strategy Mockup PDF
This slide covers IT or OT cyber security organizational structure useful to train OT teams in IT cybersecurity to speak the same language and, conversely, train IT cybersecurity teams in OT to know the problems that need to be addressed. Presenting IT OT Organizational Structure Based On Target And Culture Convergence Strategy Mockup PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Architecture Boards, Security Architecture, Awareness and Training. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Operational Process Improvement Plan Steps In Detail Assigning Resources Background PDF
This slide provides information about the fourth step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e. Assigning Resources. Presenting operational process improvement plan steps in detail assigning resources background pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like reducing communication issues, perform process visualizations, roles and responsibilities. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Operational Process Improvement Plan Steps In Detail Process Mapping Mockup PDF
This slide provides information about the first and the foremost step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Process Mapping. Presenting operational process improvement plan steps in detail process mapping mockup pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like process improvement, graphic software, applications, accountability, productivity. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
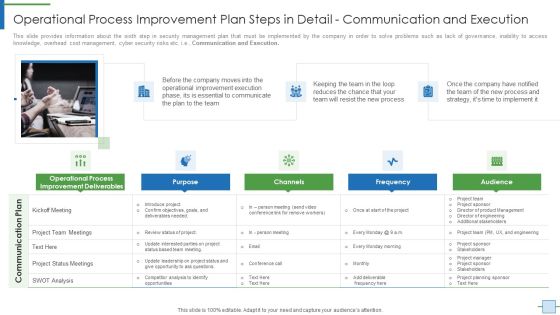
Operational Process Improvement Plan Steps In Detail Communication And Execution Information PDF
This slide provides information about the sixth step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e. Communication and Execution. Presenting operational process improvement plan steps in detail communication and execution information pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like communicate, team, process, reduces, strategy. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Operational Process Improvement Plan Steps In Detail Process Analysis Brochure PDF
This slide provides information about the second step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e. Process Analysis. Presenting operational process improvement plan steps in detail process analysis brochure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like analysis, analysis process. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
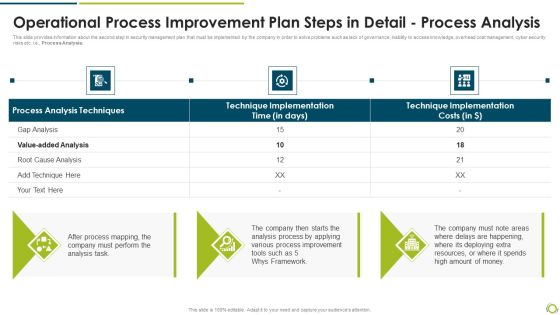
Operational Process Improvement Plan Steps In Detail Process Analysis Formats PDF
This slide provides information about the second step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Process Analysis. Presenting operational process improvement plan steps in detail process analysis formats pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like technique implementation, process analysis techniques, process improvement. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Operational Process Improvement Plan Steps In Detail Communication And Execution Guidelines PDF
This slide provides information about the Sixth and the foremost step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Communication and Execution. Presenting operational process improvement plan steps in detail communication and execution guidelines pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like improvement, communicate, team, process, implement. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Operational Process Improvement Plan Steps In Detail Monitoring And Optimization Demonstration PDF
This slide provides information about the seventh and the foremost step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Monitoring and Optimization. Presenting operational process improvement plan steps in detail monitoring and optimization demonstration pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like process improvement, performance, team. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Operational Efficiency Execution Strategy Improve Quality Operational Process Improvement Plan Graphics PDF
This slide provides information about the fourth step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Assigning Resources. This is a operational efficiency execution strategy improve quality operational process improvement plan graphics pdfS template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like team, resource, process, communication. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Operational Process Improvement Plan Steps In Detail Process Redesigning Graphics PDF
This slide provides information about the Third step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Process Redesigning. Deliver and pitch your topic in the best possible manner with this operational process improvement plan steps in detail process redesigning graphics pdf. Use them to share invaluable insights on potential consequence, process redesigning practices, practice implementation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Digital Risk Assessment Process For Cloud Services Ppt Pictures Topics PDF
The following slide highlights the cyber security process for cloud computing, cloud storage and cloud analytics storage. It depict identification, network security, data safety, application safety, monitoring and policy control to govern, protect and control the cloud services. Persuade your audience using this Digital Risk Assessment Process For Cloud Services Ppt Pictures Topics PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Identification, Data Safety, Monitoring, Policy Control. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Future Innovative Techniques For Global Digital Terrorism Background PDF
This slide show future upcoming techniques for tackling global cyber terrorism attacks and providing overall security to business data. It include techniques like permanent remote work security, regular automation and zero-trust principles etc. Persuade your audience using this Future Innovative Techniques For Global Digital Terrorism Background PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Improve Response Capability, Identify Supply Chain Risks, Automate Regularly. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Smart Venture Digitial Transformation IT OT Organizational Structure Based On Target Download PDF
This slide covers IT or OT cyber security organizational structure useful to train OT teams in IT cybersecurity to speak the same language and, conversely, train IT cybersecurity teams in OT to know the problems that need to be addressed. This is a Smart Venture Digitial Transformation IT OT Organizational Structure Based On Target Download PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Enterprise CIO, Product Heads, Crisis Management, IT Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Major Real Estate Technology Challenges And Solutions Template PDF
The slide showcases the challenges associated with the integration of property technology with corresponding solutions. It covers area of concerns like privacy, cyber security and licensing. Pitch your topic with ease and precision using this Major Real Estate Technology Challenges And Solutions Template PDF. This layout presents information on Data Storage Risks, Property Security Controls, Payment Terms. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
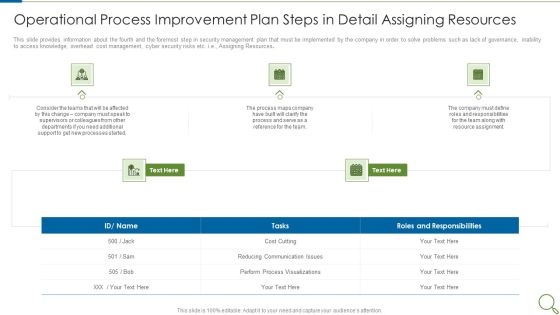
Operational Process Improvement Plan Steps In Detail Assigning Resources Professional PDF
This slide provides information about the fourth and the foremost step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Assigning Resources. This is a operational process improvement plan steps in detail assigning resources professional pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like processes, team, cost. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Playbook For Enterprise Transformation Administration Digital Transformation Trends We Can Adopt Professional PDF
The following slide displays the key trends that can be adopted by the organization, these trends can impact the transformation journey can help in achieving operational excellence. These trends can be usage of Hyper automation, cyber security tools, usage of AI etc. This is a Playbook For Enterprise Transformation Administration Digital Transformation Trends We Can Adopt Professional PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Data Deconstruction, Security Tools, Organizations Operations. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Five Phases Of Cybersecurity Incident Management Topics PDF
This slide represents the stages of the process which aims towards minimizing the impact of cyber security incidents on operational functions. It includes cyber security incident management stages such as plan and prepare, detect and report etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Five Phases Of Cybersecurity Incident Management Topics PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Five Phases Of Cybersecurity Incident Management Topics PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Cybersecurity Training Program Budget And Schedule Dates Graphics PDF
This slide covers the training schedule for various cyber security incidents program. It further includes budget allocated, training duration, dates for training and review sessions.Showcasing this set of slides titled Cybersecurity Training Program Budget And Schedule Dates Graphics PDF. The topics addressed in these templates are Malware Attack, Emergency Report, Capability Level. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Data Analysis Reporting Tools Ppt PowerPoint Presentation Professional Layout Cpb Pdf
Presenting this set of slides with name data analysis reporting tools ppt powerpoint presentation professional layout cpb pdf. This is an editable Powerpoint four stages graphic that deals with topics like cyber security detection response to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
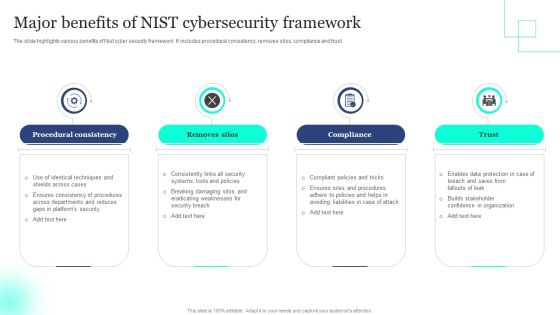
Major Benefits Of NIST Cybersecurity Framework Elements PDF
The slide highlights various benefits of Nist cyber security framework. It includes procedural consistency, removes silos, compliance and trust. Presenting Major Benefits Of NIST Cybersecurity Framework Elements PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Procedural Consistency, Removes Silos, Compliance . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Optimizing Tasks Team Collaboration Agile Operations Prioritizing Agile Software Development Tasks Guidelines PDF
Presenting this set of slides with name optimizing tasks team collaboration agile operations prioritizing agile software development tasks guidelines pdf. This is a five stage process. The stages in this process are quick delivery of project deliverables, enhancing team communication, customer collaboration, minimize cyber security risk. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Smart Venture Digitial Transformation Single Database For Two Separate IT OT Socs Inspiration PDF
This slide covers single database structure for two IT or OT socs including network security, multi cloud security, security operations , open ecosystems etc. Presenting Smart Venture Digitial Transformation Single Database For Two Separate IT OT Socs Inspiration PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Network Security, Multi Cloud Security, Device Access, Application Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Questionnaire Indicating Supplier Risk Assessment Of It Vendor Themes PDF
This slide showcases questionnaire indicating procurement risk assessment of information technology IT vendor. It contains information such as category, question reference, information security, data center security and web application security. Pitch your topic with ease and precision using this questionnaire indicating supplier risk assessment of it vendor themes pdf. This layout presents information on information security, data center security, web application security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

E Mail Internet PowerPoint Templates And PowerPoint Backgrounds 0111
Microsoft PowerPoint Template and Background with 3d image conceptual 3d text email

IT OT Team Responsibilities Based On Target And Culture Sharing Demonstration PDF
This slide covers IT OT cyber security Team responsibilities including security department, security functions etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our IT OT Team Responsibilities Based On Target And Culture Sharing Demonstration PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into IT OT Team Responsibilities Based On Target And Culture Sharing Demonstration PDF.

Allocate Team Roles And Responsibilities Ppt PowerPoint Presentation File Show PDF
The following slide showcases the key roles and responsibilities of cyber security team to enhance decision making and goal accomplishment. It includes activities such as developing information security strategies, managing security architecture, planning disaster recovery etc. Slidegeeks is here to make your presentations a breeze with Allocate Team Roles And Responsibilities Ppt PowerPoint Presentation File Show PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

1 Cloud Computing Concept With Mobile Wireless Email Device Connected To The Cloud Ppt Slides
This image slide displays cloud computing concept with mobile wireless email devices connected to the cloud. This image slide has been crafted with graphic of cloud and various icons representing communication on blue color background. This image slide depicts cloud computing on wireless devices. Use this image slide, in your presentations to explain concepts like cloud computing, technology and business. This image slide will enhance the quality of your presentations.

1 Cloud Computing Icons Phone Ringing Email Social Laptop Tweet Communication Ppt Slides
This image slide displays cloud computing icons phone ringing, email, social, laptop, tweet and communication. This image slide has been crafted with graphic of clouds printed various icons representing communication and technology. This image slide depicts cloud computing on wireless devices. Use this image slide, in your presentations to explain concepts like cloud computing, technology and business. This image slide will enhance the quality of your presentations.

Table Of Contents For Ukraine Cyberwarfare Demonstration Pdf
Presenting table of contents for ukraine cyberwarfare demonstration pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like steps to mitigate russian cyber attacks, are there international laws establishing cyber policies, weaknesses of russian cyber cell. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
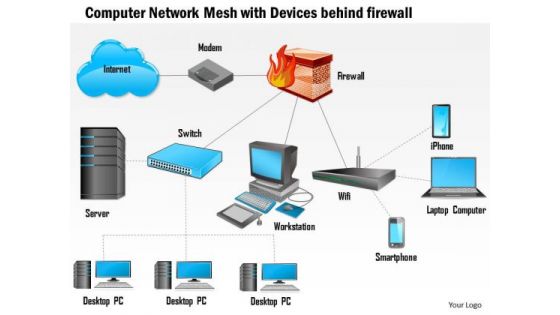
1 Computer Network Mesh With Devices Behind Firewall Connected To The Internet Ppt Slides
This image slide displays computer network mesh with devices behind firewall connected to the internet. This image slide has been crafted with graphic of cloud, technology devices and firewall application icon. This image slide depicts cloud computing and security. You may change size, color and orientation of any icon to your liking. Use this PowerPoint template, in your presentations to explain concepts like cloud computing, technology, networking and security. This image slide will enhance the quality of your presentations.

Cybersecurity Resilience Frameworks For Organization Protection Information PDF
The slide showcases the framework types of cybersecurity resilience to help organizations in securing and protecting data from cyberattacks. It covers national institute of standards and technology framework, center for internet security critical security controls, so 27001 and iso 27002 international organization for standardization and payment card industry data security standard. Presenting Cybersecurity Resilience Frameworks For Organization Protection Information PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Data Security, Organization For Standardization, Security Controls. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

1 Computer Behind A Firewall With Outgoing Data And Network Switch Ppt Slides
This image slide displays computer behind a firewall with outgoing data and network switch. This image slide has been crafted with graphic of computer, cloud, server and firewall icon. This image slide depicts cloud computing security. You may change size, color and orientation of any icon to your liking. Use this PowerPoint template, in your presentations to explain concepts like cloud computing, technology, networking and security. This image slide will enhance the quality of your presentations.

Cybersecurity Hardware And Software Update In Company Ppt Inspiration Rules PDF
This slide depicts the hardware or software update measure under the cyber security model. It also tells the current status of the devices that need to update in the organization. This is a cybersecurity hardware and software update in company ppt inspiration rules pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like technology, secure, network, systems. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
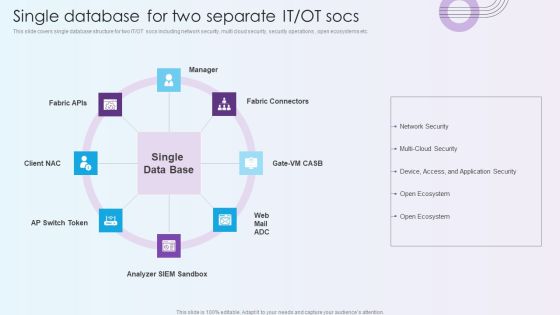
Digitalization Of Operative Enterprises Single Database For Two Separate IT OT Socs Structure PDF
This slide covers single database structure for two IT or OT socs including network security, multi cloud security, security operations , open ecosystems etc.This is a Digitalization Of Operative Enterprises Single Database For Two Separate IT OT Socs Structure PDF template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Analyzer, Network Security, Multi Cloud Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
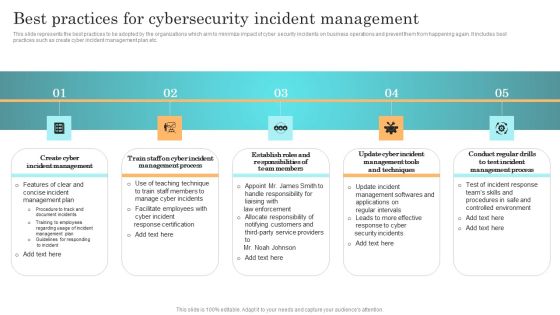
Incident Response Techniques Deployement Best Practices For Cybersecurity Incident Management Diagrams PDF
This slide represents the best practices to be adopted by the organizations which aim to minimize impact of cyber security incidents on business operations and prevent them from happening again. It includes best practices such as create cyber incident management plan etc. If you are looking for a format to display your unique thoughts, then the professionally designed Incident Response Techniques Deployement Best Practices For Cybersecurity Incident Management Diagrams PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Incident Response Techniques Deployement Best Practices For Cybersecurity Incident Management Diagrams PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Incident Response Techniques Deployement Key Issues Faced By Organization Due To Cybersecurity Incidents Infographics PDF
This slide shows the challenges faced by enterprise due to increase in cyber attacks. It includes cyber security incidents experienced by the organization such as cloud computing issues, theft of sensitive information, ransomware attacks etc. Get a simple yet stunning designed Incident Response Techniques Deployement Key Issues Faced By Organization Due To Cybersecurity Incidents Infographics PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Incident Response Techniques Deployement Key Issues Faced By Organization Due To Cybersecurity Incidents Infographics PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Key Issues Faced By Organization Due To Cybersecurity Incidents Themes PDF
This slide shows the challenges faced by enterprise due to increase in cyber attacks. It includes cyber security incidents experienced by the organization such as cloud computing issues, theft of sensitive information, ransomware attacks etc. Slidegeeks is here to make your presentations a breeze with Key Issues Faced By Organization Due To Cybersecurity Incidents Themes PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Best Practices For Cybersecurity Incident Management Summary PDF
This slide represents the best practices to be adopted by the organizations which aim to minimize impact of cyber security incidents on business operations and prevent them from happening again. It includes best practices such as create cyber incident management plan etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Best Practices For Cybersecurity Incident Management Summary PDF can be your best option for delivering a presentation. Represent everything in detail using Best Practices For Cybersecurity Incident Management Summary PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Best Practices For Cybersecurity Incident Management Infographics PDF
This slide represents the best practices to be adopted by the organizations which aim to minimize impact of cyber security incidents on business operations and prevent them from happening again. It includes best practices such as create cyber incident management plan etc. Boost your pitch with our creative Best Practices For Cybersecurity Incident Management Infographics PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Forecast Analysis Technique IT Outliers Model For Predictive Modeling Elements PDF
This slide talks about the outliers model used for predictive analytics, including its use cases, impact and algorithm used in it, such as the generalized linear model for two values. This model helps banking, finance, and cyber security organizations to detect fraud and cyber crimes. Slidegeeks is here to make your presentations a breeze with Forecast Analysis Technique IT Outliers Model For Predictive Modeling Elements PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
Overview Of Integrating Esg Into KPMG Business Strategy Background PDF
This slide covers cyber strategies to protect KPMG customer data protection. The purpose of this template is to provide an overview on top techniques to be implemented to save clients data. It includes strategies such as developing comprehensive understanding of cyber threat landscape, implementing risk based approach, establishing robust security governance framework, etc. This Overview Of Integrating Esg Into KPMG Business Strategy Background PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Overview Of Integrating Esg Into KPMG Business Strategy Background PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Ukraine Cyberwarfare How Can We Protect Ourselves From Cyberattacks Designs Pdf
This slide depicts cyberattacks protection methods to follow throughout the country, such as multi-factor authentication, data backup, to keep a copy of all the backup information. Presenting ukraine cyberwarfare how can we protect ourselves from cyberattacks designs pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like anne neuberger, deputy national security advisor for cyber and emerging technology, biden administration said. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
How Will Quantum Computing Help Enterprises Ppt Icon Deck PDF
This slide represents the application of quantum computing in different industries and how it will enhance their business growth, income and security from cyber attacks. Presenting How Will Quantum Computing Help Enterprises Ppt Icon Deck PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Transform Cybersecurity, Complex Business, Accelerate Autonomous Vehicles. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Assessment Test To Measure Effectiveness Of Training Plan Professional PDF
purpose of this slide is to outline a comprehensive assessment test which can be used by the trainer to evaluate the effectiveness of cyber security training plan. The questions covered in the slide is related to spam, ways to protect from cyberbullying etc. Presenting Assessment Test To Measure Effectiveness Of Training Plan Professional PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Collecting Sensitive, Performing Unauthorized, Hurting Statement. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
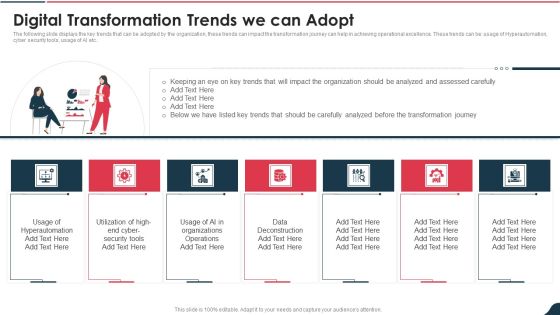
Electronic Playbook Digital Transformation Trends We Can Adopt Microsoft PDF
The following slide displays the key trends that can be adopted by the organization, these trends can impact the transformation journey can help in achieving operational excellence. These trends can be usage of Hyperautomation, cyber security tools, usage of AI etc.Presenting electronic playbook digital transformation trends we can adopt microsoft pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like digital transformation trends we can adopt In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
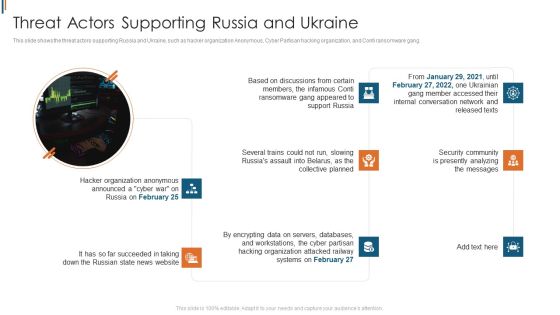
Ukraine Cyberwarfare Threat Actors Supporting Russia And Ukraine Graphics Pdf
This slide shows the threat actors supporting Russia and Ukraine, such as hacker organization Anonymous, Cyber Partisan hacking organization, and Conti ransomware gang. This is a ukraine cyberwarfare threat actors supporting russia and ukraine graphics pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security community is presently analyzing the messages, hacker organization anonymous announced, several trains could not run, slowing russias assault. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Operational Efficiency Execution Strategy Improve Quality Operational Process Improvement Plan Steps Icons PDF
This slide provides information about the first and the foremost step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e. Process Mapping. Presenting operational efficiency execution strategy improve quality operational process improvement plan steps icons pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like process improvement, applications, graphic software, accountability. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

 Home
Home