Cyber Security Image

Cyber Terrorism Assault Types Of Ddos Attacks In The Company Sample PDF
This slide demonstrates the types of DDoS attacks happening in the company, which include volume-based attacks, protocol-based attacks, and application layer attacks. This is a cyber terrorism assault types of ddos attacks in the company sample pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like volume based attacks, protocol based attacks, application layer attacks You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Russian Cyber Attacks On Ukraine IT Continued Impact Of Ongoing Microsoft PDF
This slide shows the continued impact of ongoing cyberattacks on Ukrainian internet providers and how these cyberattacks are causing internet outages throughout the country. This is a russian cyber attacks on ukraine it continued impact of ongoing microsoft pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like sources, service, network, internet. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

3 Stage Plan To Prevent And Recover From Cyber Attack Ppt Ideas Show PDF
This slide signifies three step process to maintain and recover from ransomware and computer malfunction. It covers information about stages like prepare recovery plan, limit damage scope and incrementally remove risk. Persuade your audience using this 3 Stage Plan To Prevent And Recover From Cyber Attack Ppt Ideas Show PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Prepare Recovery Plan, Limit Scope Damage, Incrementally Remove Risks. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Continuous Development Evaluation Plan To Eliminate Cyber Attacks Ppt PowerPoint Presentation Complete Deck With Slides
Pitch yourself both in house and outside by utilizing this complete deck. This continuous development evaluation plan to eliminate cyber attacks ppt powerpoint presentation complete deck with slides focuses on key fundamentals of the topic, displayed using different slides. With a total of forty seven slides, this template is the best tool you can use to persuade your audience. It will not only help you create great presentations but also induce strategic thinking because of its well researched content and graphics. You can easily personalize any of the elements to suit your unique business setting. Additionally, it can be saved in PNG, JPG, and PDF formats to save your time and resources.

Login Screen And Credit Card Security PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Login Screen And Credit Card Security PowerPoint Templates PPT Backgrounds For Slides 0113.Download and present our Computer PowerPoint Templates because you can Add colour to your speech with our PowerPoint Templates and Slides. Your presentation will leave your audience speechless. Use our Technology PowerPoint Templates because Our PowerPoint Templates and Slides are truly out of this world. Even the MIB duo has been keeping tabs on our team. Present our Network Diagrams PowerPoint Templates because It can Bubble and burst with your ideas. Use our Security PowerPoint Templates because You can Stir your ideas in the cauldron of our PowerPoint Templates and Slides. Cast a magic spell on your audience. Download and present our Signs PowerPoint Templates because You can Raise a toast with our PowerPoint Templates and Slides. Spread good cheer amongst your audience.Use these PowerPoint slides for presentations relating to One notebook with a login screen and a credit card, computer, technology, network diagrams, security, signs. The prominent colors used in the PowerPoint template are Blue, Gray, White. You can be sure our Login Screen And Credit Card Security PowerPoint Templates PPT Backgrounds For Slides 0113 effectively help you save your valuable time. Use our screen PowerPoint templates and PPT Slides provide great value for your money. Be assured of finding the best projection to highlight your words. You can be sure our Login Screen And Credit Card Security PowerPoint Templates PPT Backgrounds For Slides 0113 are visually appealing. Customers tell us our with PowerPoint templates and PPT Slides are effectively colour coded to prioritise your plans They automatically highlight the sequence of events you desire. People tell us our Login Screen And Credit Card Security PowerPoint Templates PPT Backgrounds For Slides 0113 are second to none. People tell us our credit PowerPoint templates and PPT Slides will make the presenter look like a pro even if they are not computer savvy.
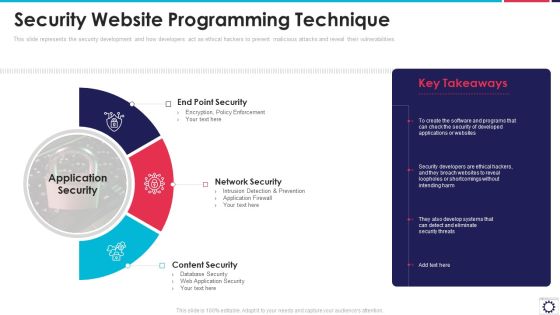
Website Programming IT Security Website Programming Technique Ppt PowerPoint Presentation File Infographics PDF
This slide represents the security development and how developers act as ethical hackers to prevent malicious attacks and reveal their vulnerabilities. Presenting website programming it security website programming technique ppt powerpoint presentation file infographics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like end point security, network security, content security, application security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Global Cyber Terrorism Incidents On The Rise IT Financial Loss Faced By The Business Designs PDF
This slide depicts the average financial loss faced by the business when projects of different scales are attacked. This is a global cyber terrorism incidents on the rise it financial loss faced by the business designs pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like targeted, revenue, financial. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Safety Incident Management Determine Threat Management Team Structure Professional PDF
The threat management team generally comprise of senior management personnel that have authority and resources to accelerate the companys internal incident response. They will be responsible in managing human impacts both employees and community, company reputation, share values, and corporate assets. This is a cyber safety incident management determine threat management team structure professional pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like determine threat management team structure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Safety Incident Management Different Kinds Of Insider Digital Threats Download PDF
This slide provides details regarding various kinds of insider digital threats such as malicious insider, negligent insider, third party insider, etc. This is a cyber safety incident management different kinds of insider digital threats download pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like malicious insider, negligent or careless insider, third party insider. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Safety Incident Management Impact Analysis Of Successful Threat Management Implementation Summary PDF
This slide depicts the impact of successful implementation of threat management in terms improved incident management and customer satisfaction and depicts that how much the focus area has been improved from the previous state. This is a cyber safety incident management impact analysis of successful threat management implementation summary pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like focus area, past state, present state, benefit. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Safety Incident Management Various Types Of Workplace Violence And Threats Infographics PDF
This slide provides details regarding various types of workplace violence threats created by people in terms of stalking, physical assault, harassment or intimidation, etc. This is a cyber safety incident management various types of workplace violence and threats infographics pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like stalking, physical assault, harassment or intimidation, property damage, weapon assault . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Enhancing Cyber Safety With Vulnerability Administration Estimating Total Cost Of Ownership Designs PDF
This slide covers the total cost of ownership incurred by SIEM services which focuses on the costs of hardware, software, infrastructure, and support. This is a enhancing cyber safety with vulnerability administration estimating total cost of ownership designs pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like hardware, infrastructure, software, support. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Enhancing Cyber Safety With Vulnerability Administration Our Management Team Information PDF
This slide covers the details of the management team along with their job profile and brief description about their work. This is a enhancing cyber safety with vulnerability administration our management team information pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like our management team. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Enhancing Cyber Safety With Vulnerability Administration Threat Intelligence Services Information PDF
This slide covers the threat intelligence services such as global intelligence, local intelligence, and other effective threat detection services. This is a enhancing cyber safety with vulnerability administration threat intelligence services information pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like global intelligence, local intelligence, other services. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Enhancing Cyber Safety With Vulnerability Administration Our Companys Mission Vision Demonstration PDF
This slide provides the details of our company mission, vision and values to provide unique services to the customers. This is a enhancing cyber safety with vulnerability administration our companys mission vision demonstration pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like our mission, our vision, our values. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Enhancing Cyber Safety With Vulnerability Administration Our SIEM Companys Milestones Demonstration PDF
This slide provides the milestones of our company such as foundation year, revenue generation, profitability, etc. This is a enhancing cyber safety with vulnerability administration our siem companys milestones demonstration pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like our siem companys milestones. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Safety Incident Management Ppt PowerPoint Presentation Complete Deck With Slides
Pitch yourself both in house and outside by utilizing this complete deck. This cyber safety incident management ppt powerpoint presentation complete deck with slides focuses on key fundamentals of the topic, displayed using different slides. With a total of sixty seven slides, this template is the best tool you can use to persuade your audience. It will not only help you create great presentations but also induce strategic thinking because of its well researched content and graphics. You can easily personalize any of the elements to suit your unique business setting. Additionally, it can be saved in PNG, JPG, and PDF formats to save your time and resources.

Cyber Network Simulation Platform Capital Funding Pitch Deck Understanding The Market Potential Icons PDF
Purpose of the following slide is to show the TAM SAM and SOM of the VR Industry market as it displays the total addressable market, the serviceable available market and the actual target market for the organization This is a cyber network simulation platform capital funding pitch deck understanding the market potential icons pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like total available market, serviceable available market, actual target market You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Key Locked With Chain Security PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Key Locked With Chain Security PowerPoint Templates PPT Backgrounds For Slides 0113.Present our Chains PowerPoint Templates because Our PowerPoint Templates and Slides will let Your superior ideas hit the target always and everytime. Use our Security PowerPoint Templates because It can Leverage your style with our PowerPoint Templates and Slides. Charm your audience with your ability. Download and present our Business PowerPoint Templates because our PowerPoint Templates and Slides will give your ideas the shape. Download and present our Shapes PowerPoint Templates because It will Raise the bar of your Thoughts. They are programmed to take you to the next level. Present our Leadership PowerPoint Templates because Our PowerPoint Templates and Slides will weave a web of your great ideas. They are gauranteed to attract even the most critical of your colleagues.Use these PowerPoint slides for presentations relating to Chain locked, Chains, Security, Business, Shapes, Leadership. The prominent colors used in the PowerPoint template are Yellow, Gray, White. PowerPoint presentation experts tell us our Key Locked With Chain Security PowerPoint Templates PPT Backgrounds For Slides 0113 are specially created by a professional team with vast experience. They diligently strive to come up with the right vehicle for your brilliant Ideas. Use our Business PowerPoint templates and PPT Slides will make you look like a winner. The feedback we get is that our Key Locked With Chain Security PowerPoint Templates PPT Backgrounds For Slides 0113 are designed by professionals The feedback we get is that our Business PowerPoint templates and PPT Slides are effectively colour coded to prioritise your plans They automatically highlight the sequence of events you desire. People tell us our Key Locked With Chain Security PowerPoint Templates PPT Backgrounds For Slides 0113 are visually appealing. Professionals tell us our PowerPoint templates and PPT Slides are incredible easy to use.

Cyber Safety Awareness Program Ppt PowerPoint Presentation Complete Deck With Slides
Share a great deal of information on the topic by deploying this Cyber Safety Awareness Program Ppt PowerPoint Presentation Complete Deck With Slides. Support your ideas and thought process with this prefabricated set. It includes a set of twelve slides slides, all fully modifiable and editable. Each slide can be restructured and induced with the information and content of your choice. You can add or remove large content boxes as well, to make this PPT slideshow more personalized. Its high-quality graphics and visuals help in presenting a well-coordinated pitch. This PPT template is also a resourceful tool to take visual cues from and implement the best ideas to help your business grow and expand. The main attraction of this well-formulated deck is that everything is editable, giving you the freedom to adjust it to your liking and choice. Changes can be made in the background and theme as well to deliver an outstanding pitch. Therefore, click on the download button now to gain full access to this multifunctional set.

Data Network Security With Lock Showing Online Safety Icon Ppt PowerPoint Presentation Infographic Template Graphics PDF
Presenting this set of slides with name data network security with lock showing online safety icon ppt powerpoint presentation infographic template graphics pdf. This is a two stage process. The stages in this process are data network security with lock showing online safety icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Laptop Under Umbrella Security PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Laptop Under Umbrella Security PowerPoint Templates PPT Backgrounds For Slides 0113.Download and present our Umbrellas PowerPoint Templates because You can Double your output with our PowerPoint Templates and Slides. They make beating deadlines a piece of cake. Present our Security PowerPoint Templates because You can Channelise the thoughts of your team with our PowerPoint Templates and Slides. Urge them to focus on the goals you have set. Download our Computer PowerPoint Templates because you can Set pulses racing with our PowerPoint Templates and Slides. They will raise the expectations of your team. Download and present our Network Diagrams PowerPoint Templates because our PowerPoint Templates and Slides are the string of your bow. Fire of your ideas and conquer the podium. Download and present our Signs PowerPoint Templates because You canTake a leap off the starting blocks with our PowerPoint Templates and Slides. They will put you ahead of the competition in quick time.Use these PowerPoint slides for presentations relating to Laptop computer under umbrella, umbrellas, security, computer, network diagrams, signs. The prominent colors used in the PowerPoint template are Red, Blue, Gray. Use our Laptop Under Umbrella Security PowerPoint Templates PPT Backgrounds For Slides 0113 have awesome images to get your point across. The feedback we get is that our security PowerPoint templates and PPT Slides are incredible easy to use. Customers tell us our Laptop Under Umbrella Security PowerPoint Templates PPT Backgrounds For Slides 0113 will generate and maintain the level of interest you desire. They will create the impression you want to imprint on your audience. Customers tell us our network PowerPoint templates and PPT Slides are effectively colour coded to prioritise your plans They automatically highlight the sequence of events you desire. Presenters tell us our Laptop Under Umbrella Security PowerPoint Templates PPT Backgrounds For Slides 0113 provide you with a vast range of viable options. Select the appropriate ones and just fill in your text. Presenters tell us our computer PowerPoint templates and PPT Slides are designed by professionals
Online Technology Security Chip Icon For Network Safety Ppt PowerPoint Presentation File Graphics Example PDF
Persuade your audience using this online technology security chip icon for network safety ppt powerpoint presentation file graphics example pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including online technology security chip icon for network safety. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cloud Based Email Security Market Report Industry Challenges Ppt Infographics File Formats PDF
Use this slide to show the major industry challenges in E Mail Security market. Presenting cloud based email security market report industry challenges ppt infographics file formats pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like threat of serverless apps, iot threat, threat of ransomware. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Business Network Security Vector Icon Ppt PowerPoint Presentation Gallery Examples PDF
Presenting this set of slides with name business network security vector icon ppt powerpoint presentation gallery examples pdf. This is a three stage process. The stages in this process are business network security vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Vector Showing Wide Area Network Security Analysis Ppt PowerPoint Presentation Summary Templates PDF
Presenting this set of slides with name vector showing wide area network security analysis ppt powerpoint presentation summary templates pdf. This is a three stage process. The stages in this process are vector showing wide area network security analysis. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Virus Safety Shield Lock Icon For Online Security Ppt PowerPoint Presentation Infographic Template Picture PDF
Presenting this set of slides with name virus safety shield lock icon for online security ppt powerpoint presentation infographic template picture pdf. This is a three stage process. The stages in this process are virus safety shield lock icon for online security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Online Security Lock With Chain On Computer Screen Ppt PowerPoint Presentation Infographic Template Brochure PDF
Presenting this set of slides with name online security lock with chain on computer screen ppt powerpoint presentation infographic template brochure pdf. This is a one stage process. The stage in this process is online security lock with chain on computer screen. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Security Settings To Prevent Online Threats Ppt PowerPoint Presentation Gallery Structure PDF
Presenting security settings to prevent online threats ppt powerpoint presentation gallery structure pdf to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including security settings to prevent online threats. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Human Online Security Shield Vector Icon Ppt PowerPoint Presentation Portfolio Gallery PDF
Presenting this set of slides with name human online security shield vector icon ppt powerpoint presentation portfolio gallery pdf. This is a three stage process. The stages in this process are human online security shield vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Russian Cyber Attacks On Ukraine IT Ppt PowerPoint Presentation Complete With Slides
Induce strategic thinking by presenting this complete deck. Enthrall your audience by deploying this thought provoking PPT deck. It can be downloaded in both standard and widescreen aspect ratios, thus making it a complete package to use and deploy. Convey your thoughts and actions using the sixty four slides presented in this complete deck. Additionally, feel free to alter its components like color, graphics, design, etc, to create a great first impression. Grab it now by clicking on the download button below.

Distributed Computing Security Of Data And Networks In Edge Computing Ideas PDF
This slide represents the security of data and networks in edge computing. It also shows that data is secure because data is not traveling on any network however, edge devices are vulnerable.This is a Distributed Computing Security Of Data And Networks In Edge Computing Ideas PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Conduct Analytics, Devices Themselves, Vulnerability You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Enhancing Cyber Safety With Vulnerability Administration Ppt PowerPoint Presentation Complete Deck With Slides
This complete deck acts as a great communication tool. It helps you in conveying your business message with personalized sets of graphics, icons etc. Comprising a set of sixty one slides, this complete deck can help you persuade your audience. It also induces strategic thinking as it has been thoroughly researched and put together by our experts. Not only is it easily downloadable but also editable. The color, graphics, theme any component can be altered to fit your individual needs. So grab it now.

Cybersecurity Risk Administration Plan Defining Categories Of Information Security Threats Inspiration PDF
This slide shows the categorization of information security threats. Categories covered are human error, natural disaster, software attacks and environmental control failures.This is a Cybersecurity Risk Administration Plan Defining Categories Of Information Security Threats Inspiration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Natural Disaster, Environmental Control Failures, Deliberate Software Attacks You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

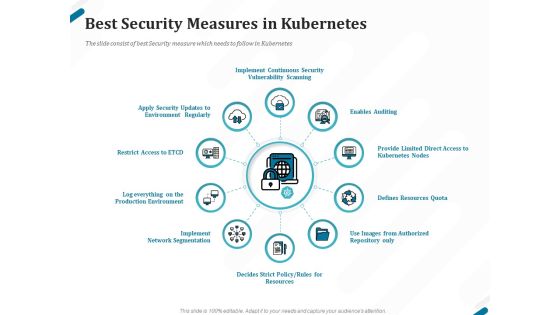
Understanding The Kubernetes Components Through Diagram Best Security Measures In Kubernetes Themes PDF
Presenting this set of slides with name understanding the kubernetes components through diagram best security measures in kubernetes themes pdf. This is a ten stage process. The stages in this process are implement continuous security vulnerability scanning, enables auditing, provide limited direct access to kubernetes nodes, defines resources quota, use images from authorized repository only, defines strict policy, rules for resources, implement network segmentation. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Understanding The Kubernetes Concepts And Architecture Best Security Measures In Kubernetes Ppt Outline Templates PDF
Presenting this set of slides with name understanding the kubernetes concepts and architecture best security measures in kubernetes ppt outline templates pdf. This is a ten stage process. The stages in this process are implement continuous security vulnerability scanning, enables auditing, provide limited direct access to kubernetes nodes, defines resources quota, use images from authorized repository only, defines strict policy, rules for resources, implement network segmentation. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Driving Digital Transformation Through Kubernetes And Containers Best Security Measures In Kubernetes Template PDF
Presenting this set of slides with name driving digital transformation through kubernetes and containers best security measures in kubernetes template pdf. This is a ten stage process. The stages in this process are implement continuous security vulnerability scanning, enables auditing, provide limited direct access to kubernetes nodes, defines resources quota, use images from authorized repository only, defines strict policy, rules for resources, implement network segmentation. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Kubernetes Containers Architecture Overview Best Security Measures In Kubernetes Ppt Pictures File Formats PDF
Presenting this set of slides with name kubernetes containers architecture overview best security measures in kubernetes ppt pictures file formats pdf. This is a ten stage process. The stages in this process are implement continuous security vulnerability scanning, enables auditing, provide limited direct access to kubernetes nodes, defines resources quota, use images from authorized repository only, defines strict policy, rules for resources, implement network segmentation. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
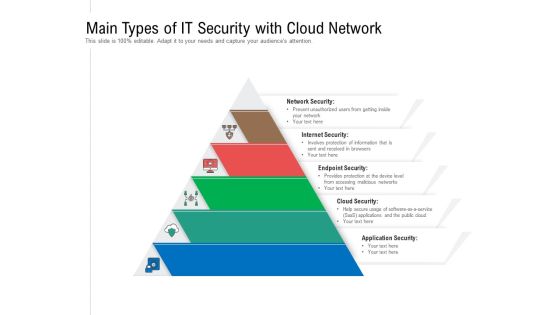
Main Types Of IT Security With Cloud Network Ppt PowerPoint Presentation Gallery Design Ideas PDF
Persuade your audience using this main types of it security with cloud network ppt powerpoint presentation gallery design ideas pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including network security, internet security, endpoint security, cloud security, application security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Online Security Expert Certification System Ppt PowerPoint Presentation Professional Themes PDF
Presenting this set of slides with name online security expert certification system ppt powerpoint presentation professional themes pdf. This is a ten stage process. The stages in this process are social network program, information security program, online trading security program, web protection program, unauthorized access protection program, virus protection program, password security program, wireless security program, identity protection program, spyware protection program. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
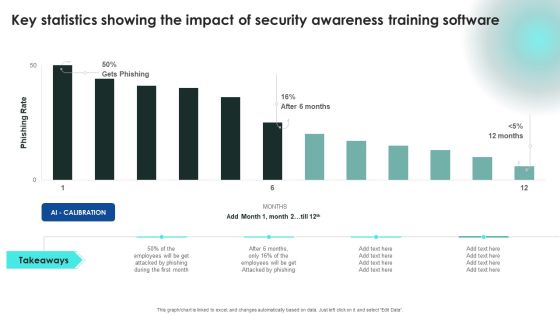
Implementing Cybersecurity Awareness Program To Prevent Attacks Key Statistics Showing The Impact Of Security Clipart PDF
This modern and well arranged Implementing Cybersecurity Awareness Program To Prevent Attacks Key Statistics Showing The Impact Of Security Clipart PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Web App Firewall Services IT Types Of Web Application Firewall Security Models Background PDF
This slide represents the various types of WAF security models, including the whitelist or negative security model, blacklist or positive security model, and hybrid security model. Presenting web app firewall services it types of web application firewall security models background pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like applications, organizations. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Types Of Web Application Firewall Security Models WAF Platform Themes PDF
This slide represents the various types of WAF security models, including the whitelist or negative security model, blacklist or positive security model, and hybrid security model. Presenting Types Of Web Application Firewall Security Models WAF Platform Themes PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like White List Access Control, Black List Access Control. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Email Security Market Research Report Industry Trends Ppt Infographics Styles PDF
Presenting this set of slides with name email security market research report industry trends ppt infographics styles pdf. This is a six stage process. The stages in this process are balance between risk and resilience, supply chain security, security adaptive approach. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Global Cloud Based Email Security Market Industry Trends Ppt Professional Example PDF
Presenting this set of slides with name global cloud based email security market industry trends ppt professional example pdf. This is a six stage process. The stages in this process are balance between risk and resilience, supply chain security, security adaptive approach. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

SDN Security Architecture Factors Influencing Software Defined Networking SDN Adoption Summary PDF
This slide represents the factors influencing SDN adoption, including cultural change, security risks, interoperability, scalability, performance, and reliability. SDN is appealing regarding network simplicity and investment, and operational cost savings. This modern and well arranged SDN Security Architecture Factors Influencing Software Defined Networking SDN Adoption Summary PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Challenges And Solutions In Information Security Risk Management Cybersecurity Risk Assessment Demonstration PDF
This slide showcases challenges involved in formulating risk management program for information security. It also shows solutions to tackle the challenges and impact of implementing them. This modern and well-arranged Challenges And Solutions In Information Security Risk Management Cybersecurity Risk Assessment Demonstration PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
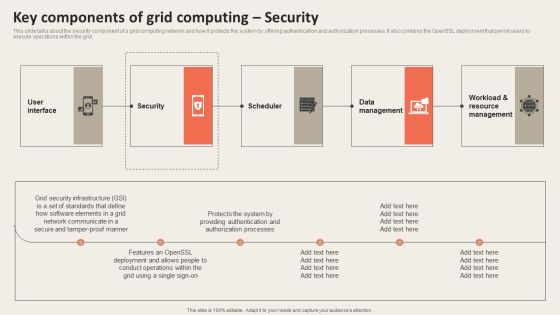
Grid Computing Applications Key Components Of Grid Computing Security Guidelines PDF
This slide talks about the security component of a grid computing network and how it protects the system by offering authentication and authorization processes. It also contains the OpenSSL deployment that permit users to execute operations within the grid. This modern and well arranged Grid Computing Applications Key Components Of Grid Computing Security Guidelines PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Cognitive Sensing Innovation CR Wsns In Military And Public Security Applications Inspiration PDF
This slide depicts the use of cognitive radio wireless sensor networks in the military and public security applications, including targeting, command and control, information collection, battlefield surveillance, assistant intelligence, and targeting. This modern and well-arranged Cognitive Sensing Innovation CR Wsns In Military And Public Security Applications Inspiration PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Cloud Based Email Security Market Report Industry Trends Ppt Styles Diagrams PDF
Major trends of the E mail security industry are shown in this slide. This is a cloud based email security market report industry trends ppt styles diagrams pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security system, artificial intelligence, supply chain security, security adaptive approach. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Steps Of Online Security With Icons Ppt PowerPoint Presentation Gallery Portfolio PDF
Presenting this set of slides with name steps of online security with icons ppt powerpoint presentation gallery portfolio pdf. This is a eight stage process. The stages in this process are mobile security, computer security, secure payment. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Common Methods Used To Threaten IT Security IT Ppt Inspiration Rules PDF
This slide depicts the standard methods used to threaten cyber-security by cybercriminals or attackers. It also shows the reasons for these threats and preventions from these threats. This is a common methods used to threaten it security it ppt inspiration rules pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like malware, daniel of service, man in the middle, sql injection, phishing. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity Risk Administration Plan Setting Scenario For Security Control Topics PDF
Following slide displays security control scenario setting. It includes scenario detail, category of security controls and controls description.Presenting Cybersecurity Risk Administration Plan Setting Scenario For Security Control Topics PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Category Of Security Controls, Controls Description, Secured Firewall Configuration In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Distributed Computing IT Security Of Data And Networks In Edge Computing Themes PDF
This slide represents the security of data and networks in edge computing. It also shows that data is secure because data is not traveling on any network however, edge devices are vulnerable. Presenting distributed computing it security of data and networks in edge computing themes pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like organization, data storage, computing security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Upgrading Total Project Safety IT Information Security Process To Manage Firms Sensitive Data Structure PDF
This slide provides information about information security process in order to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc. Presenting upgrading total project safety it information security process to manage firms sensitive data structure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like privileged password management, daily tasks performed by network administrator, network security audit checklist. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Based Email Security Market Report Industry Drivers Ppt Ideas Files PDF
Major drivers for E Mail security industry are shown in this slide. This is a cloud based email security market report industry drivers ppt ideas files pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like international market, supply chain security, growth. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Based Email Security Market Report Industry Overview Ppt Show Background Designs PDF
Use this slide displays a complete overview of the E Mail security industry. Presenting cloud based email security market report industry overview ppt show background designs pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like industry overview. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Online Security System For Business Quality Control Ppt PowerPoint Presentation Gallery Templates PDF
Presenting this set of slides with name online security system for business quality control ppt powerpoint presentation gallery templates pdf. This is a six stage process. The stages in this process are network engineering program, information security management, social engineering program, ethical hacking program, crime investigation program, internet security program. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Comparative Analysis Email Security Network Gateway Ppt Outline Graphics Template PDF
The following slide showcases comparison of email security gateways along with features rating and price. Main gateways included are mimecast, ironscales, avanan and trustifi. Showcasing this set of slides titled Comparative Analysis Email Security Network Gateway Ppt Outline Graphics Template PDF. The topics addressed in these templates are Gateway Device Establishment, Establish Strong, Identity For Gateway. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

IT Security Awareness Topics To Considered For Effective Training Program Brochure PDF
This slide covers cybersecurity awareness topics to considered for effective training. It involves topics such as removable media, cloud security, public wi-fi and physical security. Presenting IT Security Awareness Topics To Considered For Effective Training Program Brochure PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Removable Media, Cloud Security, Physical Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

 Home
Home