Cyber Security Image
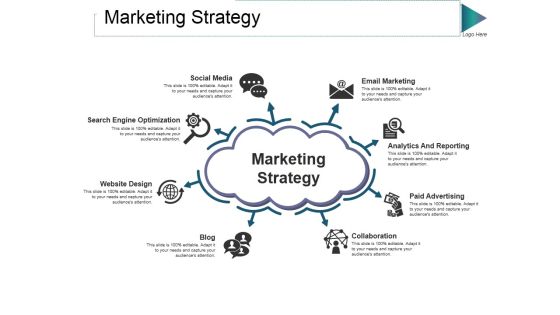
Marketing Strategy Ppt PowerPoint Presentation Model Background Image
This is a marketing strategy ppt powerpoint presentation model background image. This is a eight stage process. The stages in this process are social media, email marketing, marketing strategy, collaboration, blog.
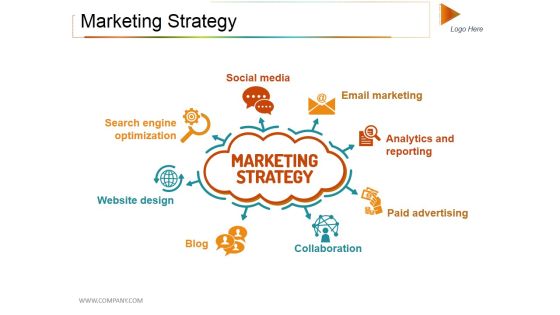
Marketing Strategy Ppt PowerPoint Presentation Professional Background Image
This is a marketing strategy ppt powerpoint presentation professional background image. This is a eight stage process. The stages in this process are social media, email marketing, collaboration, blog, website design.

Internet Advertising Steps Example Powerpoint Slide Background Image
This is a internet advertising steps example powerpoint slide background image. This is a eight stage process. The stages in this process are website and blog, social media, blog, email, relationships, analytics, forum, banner, internet advertising.
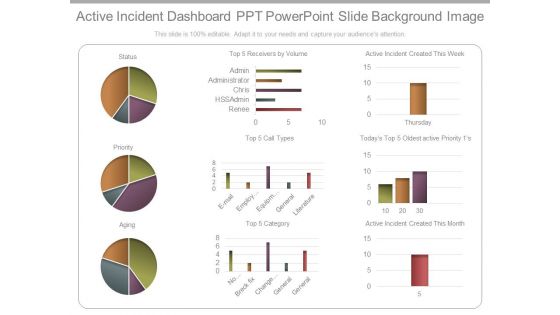
Active Incident Dashboard Ppt Powerpoint Slide Background Image
This is a active incident dashboard ppt powerpoint slide background image. This is a three stage process. The stages in this process are status, priority, aging, receivers by volume, renee, hssadmin, chris, administrator, admin, category, email, employee setup, equipment, general, literature, no category, breck fix, change management, general, active incident created this week, oldest active priority, active incident created this month, thursday.

Ukraine Cyberwarfare International Cyber Aid To Ukraine Brochure Pdf
This slide describes the international cyber assistance to Ukraine by 6 European Union nations such as Lithuania, the Netherlands, Poland, Estonia, Romania, and Croatia. This is a ukraine cyberwarfare international cyber aid to ukraine brochure pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like ukraine is in grave danger, australia has also announced that it will teach ukrainian officials on cyber security, australia has also pledged to help the ukrainian government with cyber security through a bilateral cyber policy dialogue. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Risk Mitigating Business Information Cyber Protection Strategies Themes PDF
This slide covers risk mitigating business cyber security strategies which are training employees, installing spyware, backup data and privileged access.Presenting Risk Mitigating Business Information Cyber Protection Strategies Themes PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Train Employees, Information Business, Related Activities. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Comprehensive Strategy To Improve Cyber Risk Prevention Graphics PDF
The slide showcases the steps for building efficient cyber resiliency across organization. It covers steps like secure remote working enablement, develop a comprehensive response plan, build a cyber security improvement roadmap, build detection and response capability and educating users on escalating threats. Pitch your topic with ease and precision using this Comprehensive Strategy To Improve Cyber Risk Prevention Graphics PDF. This layout presents information on Objective, Initiatives, Impact. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
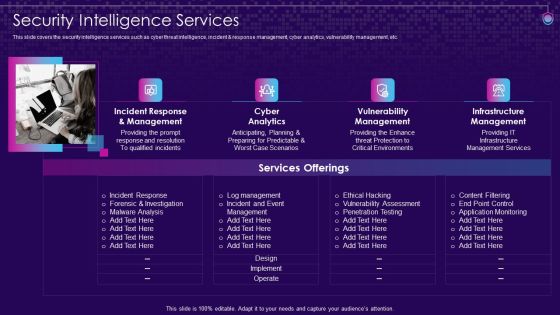
SIEM Services Security Intelligence Services Ppt Show Layouts PDF
This slide covers the security intelligence services such as cyber threat intelligence, incident and response management, cyber analytics, vulnerability management, etc. Presenting siem services security intelligence services ppt show layouts pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like management cyber, analytics vulnerability, management, infrastructure management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
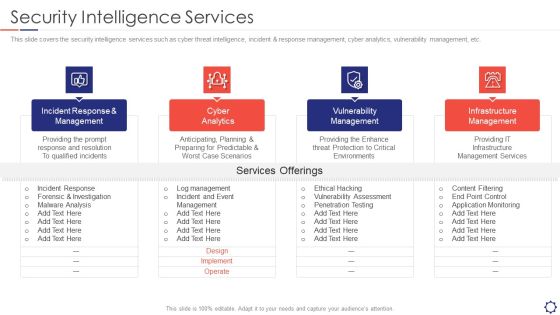
SIEM Security Intelligence Services Ppt Professional Format PDF
This slide covers the security intelligence services such as cyber threat intelligence, incident and response management, cyber analytics, vulnerability management, etc. Presenting siem security intelligence services ppt professional format pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like incident response and management, cyber analytics, vulnerability management, infrastructure management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Risk Recognition Automation Security Intelligence Services Ppt Icon Infographics PDF
This slide covers the security intelligence services such as cyber threat intelligence, incident and response management, cyber analytics, vulnerability management, etc. This is a risk recognition automation security intelligence services ppt icon infographics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like incident response and management, cyber analytics, vulnerability management, infrastructure management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Enhancing Cyber Safety With Vulnerability Administration SIEM Integrations Inspiration PDF
This is a enhancing cyber safety with vulnerability administration siem integrations inspiration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security events, network logs, applications and devices, it infrastructure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
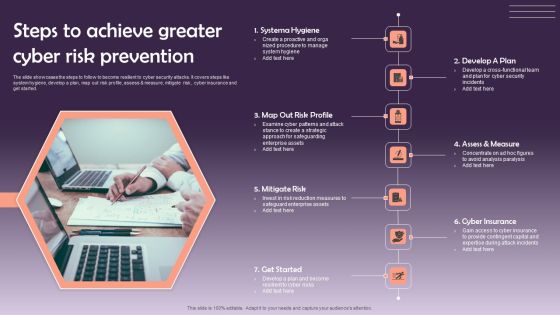
Steps To Achieve Greater Cyber Risk Prevention Infographics PDF
The slide showcases the steps to follow to become resilient to cyber security attacks. It covers steps like system hygiene, develop a plan, map out risk profile, assess and measure, mitigate risk, cyber insurance and get started. Presenting Steps To Achieve Greater Cyber Risk Prevention Infographics PDF to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including Systema Hygiene, Develop A Plan, Mitigate Risk. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Terrorism Assault Confidential Data Should Be Backup Brochure PDF
This slide emphasizes the significance of backing up private data, which enables for data recovery in the event of an attack.Presenting cyber terrorism assault confidential data should be backup brochure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Cyber Security Assessment, Limited Access Privileges, Employee Training In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Five Step Procedure Of Cyber Threat Hunting Introduction PDF
This slide shows steps for effective and successful cyber security systems to prevent from threats.it contains steps hypothesis, process data, trigger, investigation and resolution. Persuade your audience using this Five Step Procedure Of Cyber Threat Hunting Introduction PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Prepare Detailed, Management Software, Management Software. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Intelligence Risk Assessment Dashboard With Heat Map Portrait PDF
This slide exhibits risk rating breakdown and heat map for analyzing current cyber security measures effectiveness. It covers top 5 vulnerabilities and clients under scrutiny. Pitch your topic with ease and precision using this Cyber Intelligence Risk Assessment Dashboard With Heat Map Portrait PDF This layout presents information on Risk Rating Breakdown, Action Plan Breakdown, Risk Possibility It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
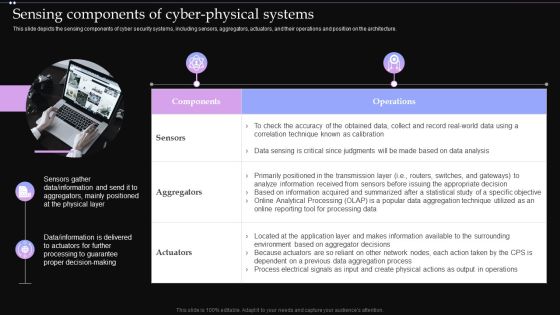
Sensing Components Of Cyber Physical Systems Ppt PowerPoint Presentation Diagram Images PDF
This slide depicts the sensing components of cyber security systems, including sensors, aggregators, actuators, and their operations and position on the architecture. Find highly impressive Sensing Components Of Cyber Physical Systems Ppt PowerPoint Presentation Diagram Images PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Sensing Components Of Cyber Physical Systems Ppt PowerPoint Presentation Diagram Images PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Ways To Control Cyber Protection And Privacy Issues Diagrams PDF
The following slide illustrates some ways to monitor cybersecurity and privacy issues. It includes activities such as protecting CRM platform, keeping security system updated, modifying passwords regularly etc. Persuade your audience using this Ways To Control Cyber Protection And Privacy Issues Diagrams PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Change Passwords Regularly, Regular Backups, Protect CRM Platform. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Best Practices To Manage Cyber Protection Of Organization Microsoft PDF
This slide shows various practices which can be used to by organizations to manage information technology protection. These practices are monitor, risk plan, protection protocols and use technology. Persuade your audience using this Best Practices To Manage Cyber Protection Of Organization Microsoft PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Risk Plan, Security Protocols, Technology. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Exploitation IT Regaining Reputation Of Our Company Demonstration PDF
This slide describes the regaining companys reputation through regaining customers trust by showcasing the companys new security policies and strategies. This is a cyber exploitation it regaining reputation of our company demonstration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like regaining reputation of our company. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Strategies For KPMG For Client Data Protection Pictures PDF
This slide covers techniques to secure customers confidential data through several cyber security strategies. The purpose for this template is to provide an overview on important elements of top techniques deployed by the company . It includes strategies such as people, process, data and technology and regulatory. Boost your pitch with our creative Cyber Strategies For KPMG For Client Data Protection Pictures PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Evaluating IT System Security Using Swot Analysis Ppt Pictures Clipart Images PDF
The purpose of this slide is to outline the strength, weakness, opportunities and threat SWOT evaluation of organization cyber security. Organization can detect the potential risks and opportunities in the cyber security using SWOT model. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Evaluating IT System Security Using Swot Analysis Ppt Pictures Clipart Images PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Evaluating IT System Security Using Swot Analysis Ppt Pictures Clipart Images PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today

Evaluating IT System Security Using SWOT Analysis Portrait PDF
The purpose of this slide is to outline the strength, weakness, opportunities and threat SWOT evaluation of organization cyber security. Organization can detect the potential risks and opportunities in the cyber security using SWOT model. Presenting Evaluating IT System Security Using SWOT Analysis Portrait PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Strengths, Weakness, Opportunities. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Strategies For Safety And Security In Hotel Industry Sample PDF
This slide outlines measures to ensure safety and security in hospitality sectors. It highlights four basic ways i.e. cyber security, add intelligence to video surveillance, internal theft and fraud and establish evergreen background screening protocol.Persuade your audience using this Strategies For Safety And Security In Hotel Industry Sample PDF This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Security, Internal Theft And Fraud, Establish Evergreen Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Types Of IT Security Control Assessment Model Clipart PDF
This slide presents a framework showing multiple types of IT cyber security control to protect system integrity and information. It includes key components such as COBIT, CIS control, NIST cyber security, HITRUST CSF, NIST SP model and ISO series. Persuade your audience using this Types Of IT Security Control Assessment Model Clipart PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Options, Framework, Controls. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
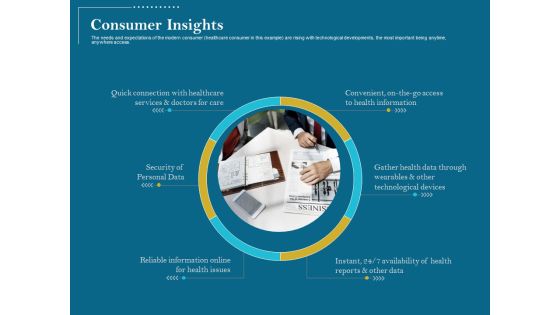
Utilizing Cyber Technology For Change Process Consumer Insights Microsoft PDF
The needs and expectations of the modern consumer healthcare consumer in this example are rising with technological developments, the most important being anytime, anywhere access. Presenting utilizing cyber technology for change process consumer insights microsoft pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like security of personal data, reliable information online for health issues, gather health data through wearables and other technological devices, convenient, on the go access to health information, quick connection with healthcare services and doctors for care. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
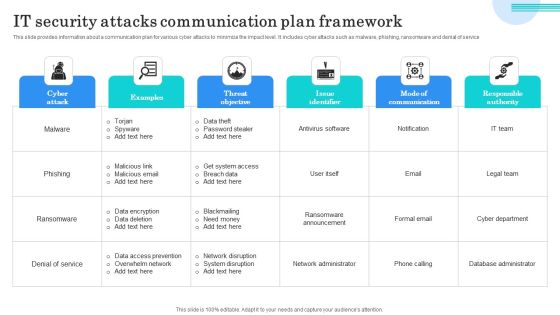
IT Security Attacks Communication Plan Framework Graphics PDF
This slide provides information about a communication plan for various cyber attacks to minimize the impact level. It includes cyber attacks such as malware, phishing, ransomware and denial of service. Showcasing this set of slides titled IT Security Attacks Communication Plan Framework Graphics PDF. The topics addressed in these templates are Data Theft, Password Stealer, Get System Access. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Global Cyber Terrorism Incidents On The Rise IT Checklist To Deal With Cyber Terrorism Threats Key Template PDF
This slide represents the checklist to deal with cyber-terrorism threats which involve 24 7 monitoring, employee training, keeping software updated. Presenting global cyber terrorism incidents on the rise it checklist to deal with cyber terrorism threats key template pdf to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like employee training, monitoring, cyber security assessment, incident response plan, limited access privileges. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Global Cyber Terrorism Incidents On The Rise IT Checklist To Deal With Cyber Terrorism Threats Infographics PDF
This slide represents the checklist to deal with cyber-terrorism threats which involve 24 7 monitoring, employee training, keeping software updated. This is a global cyber terrorism incidents on the rise it checklist to deal with cyber terrorism threats infographics pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employee training, monitoring, cyber security assessment, incident response plan, limited access privileges. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Blockchain Technology Applications For Cyber Threat Prevention Icons PDF
This slides represents various application of blockchain technology in enhancing cyber safety which helps to speed up data transfer procedures, offer secure transactions, and lower compliance expenses. Key components are IoT security, secure private messaging, etc. Presenting Blockchain Technology Applications For Cyber Threat Prevention Icons PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Prevention, Infrastructure, System . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
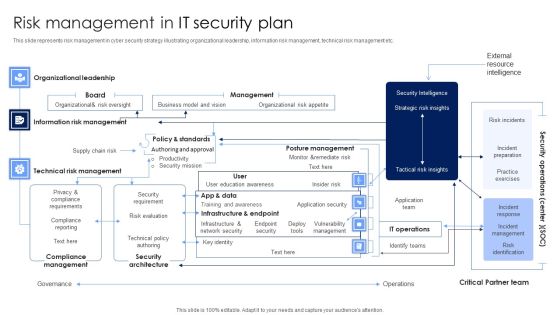
Risk Management In IT Security Plan Rules PDF
This slide represents risk management in cyber security strategy illustrating organizational leadership, information risk management, technical risk management etc. Pitch your topic with ease and precision using this Risk Management In IT Security Plan Rules PDF. This layout presents information on Security Architecture, Compliance Management, Technical Risk Management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

6 Level IT Security Plan Maturity Model Slides PDF
This slide represent 6 level cyber security strategy maturity model illustrating levels such as initial, developing, defined, managed, optimization and unified. Pitch your topic with ease and precision using this 6 Level IT Security Plan Maturity Model Slides PDF. This layout presents information on Awareness, Organization Security, Metrics To Measure. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

IT Security For Remote Workplace Plan Checklist Introduction PDF
This slide represents cyber security for remote workplace checklist illustrating approval of remote platforms, employee training, deployment of firewall etc. Pitch your topic with ease and precision using this IT Security For Remote Workplace Plan Checklist Introduction PDF. This layout presents information on Security Measures, Employees, Team. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
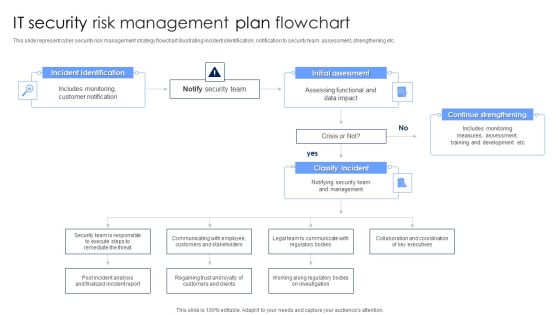
IT Security Risk Management Plan Flowchart Diagrams PDF
This slide represent cyber security risk management strategy flowchart illustrating incident identification, notification to security team, assessment, strengthening etc. Persuade your audience using this IT Security Risk Management Plan Flowchart Diagrams PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Incident Identification, Initial Assessment, Continue Strengthening. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
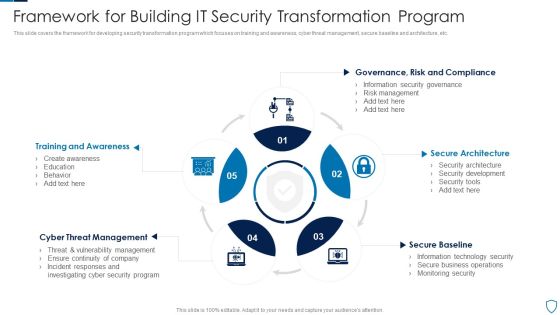
Framework For Building IT Security Transformation Program Pictures PDF
This slide covers the framework for developing security transformation program which focuses on training and awareness, cyber threat management, secure baseline and architecture, etc.Presenting Framework For Building IT Security Transformation Program Pictures PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Training Awareness, Threat Management, Secure Architecture This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
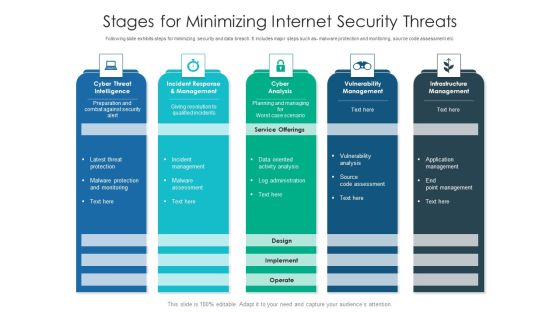
Stages For Minimizing Internet Security Threats Ideas PDF
Following slide exhibits steps for minimizing security and data breach. It includes major steps such as- malware protection and monitoring, source code assessment etc. Pitch your topic with ease and precision using this stages for minimizing internet security threats ideas pdf. This layout presents information on infrastructure management, cyber analysis, vulnerability management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

5 Step Approach In IT Security Plan Framework Designs PDF
This slide represents 5 step approach in cyber security strategy framework such as identifying, protecting, detecting, responding and recovering that are been adopted by various organization. Presenting 5 Step Approach In IT Security Plan Framework Designs PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Protect, Detect, Respond. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

IT Security Plan Across Key Financial Areas Portrait PDF
This slide represents cyber security strategy across key financial areas illustrating talent centric, strategic and innovative, risk focused, intelligence driven and resilient and scalable. Presenting IT Security Plan Across Key Financial Areas Portrait PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Strategic And Innovative, Risk Focused, Intelligence Driven. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Key Components Of IT Security Communication Plan Mockup PDF
This slide illustrates various components of a cyber security communication plan that must be included for plan development. It includes plan, train, stress test, event communication and repair reputation. Presenting Key Components Of IT Security Communication Plan Mockup PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Plan, Train, Stress Test. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Key Elements Of IT Security IT Ppt Pictures Inspiration PDF
This slide represents the different elements of cyber security such as application security, network security, information security, etc. This is a key elements of it security it ppt pictures inspiration pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like application security, network security, end user education, cloud security, operational security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Addressing The Various Security Incidents And Attacks Icons PDF
Purpose of this slide is to educate team members about different security incidents and attacks. It includes information about traditional security incidents, cyber security attacks and common techniques.Create an editable Addressing The Various Security Incidents And Attacks Icons PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Addressing The Various Security Incidents And Attacks Icons PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
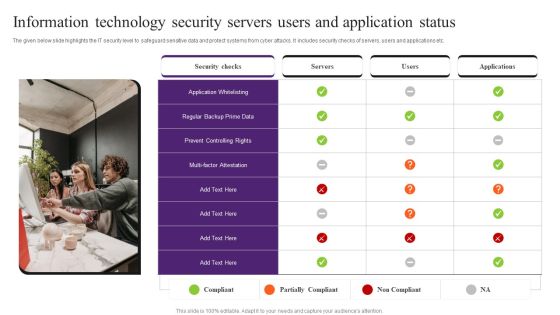
Information Technology Security Servers Users And Application Status Pictures PDF
The given below slide highlights the IT security level to safeguard sensitive data and protect systems from cyber attacks. It includes security checks of servers, users and applications etc. Presenting Information Technology Security Servers Users And Application Status Pictures PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Application Whitelisting, Security Checks, Information Technology Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
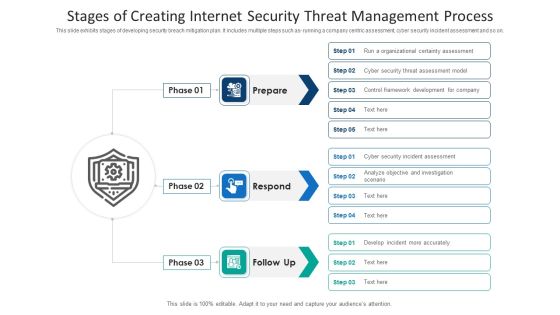
Stages Of Creating Internet Security Threat Management Process Information PDF
This slide exhibits stages of developing security breach mitigation plan. It includes multiple steps such as- running a company centric assessment, cyber security incident assessment and so on. Presenting stages of creating internet security threat management process information pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including stages of creating internet security threat management process. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Annual Information Technology Security Investment Analysis And Projection Portrait PDF
The following slide depicts the key areas of investment in IT security to safeguard business from risks and cyber attacks. It includes the current and the previous year spending along with the estimated growth. Presenting Annual Information Technology Security Investment Analysis And Projection Portrait PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Cloud Security, Security Services, Identity Access Management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Steps To Deploy People Centric Work Culture Security Background PDF
The following slide showcases steps to enforce human centric security system to empower employees in handling useful information. It includes elements such as establishing environment for people centric security PCS, promoting culture of cyber security, etc. Presenting Steps To Deploy People Centric Work Culture Security Background PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Converting Cybersecurity, Punishment System, Protection Practices. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Prevention Of Information Measuring Security Awareness Campaign Results Pictures PDF
The purpose of this slide is to showcase various key performance indicator KPIs which can assist the company to effectively track cyber security awareness campaign results. The KPIs are phishing rate, self-reported incidents, security breaches, cost of security breach and campaign participation rate. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Prevention Of Information Measuring Security Awareness Campaign Results Pictures PDF from Slidegeeks and deliver a wonderful presentation.

5 Layer IT Proactive Security Plan Topics PDF
This slide represents cyber proactive security strategy illustrating customer data, continuous learning, reaction to security threats, understanding security posture etc. Persuade your audience using this 5 Layer IT Proactive Security Plan Topics PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Organization Understanding, Organization Reaction, Organization Continuous Learning. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Latest Trends For Mobile Smart Phone Security Icons PDF
This slide shows current trends for securing mobile phone against potential cyber attacks and loss of sensitive data. It include trends such as rise in security automation, increasing threat modelling and SAST-DAST integration etc qPresenting Latest Trends For Mobile Smart Phone Security Icons PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Increasing Security, SAST DAST Integration, Increasing Threat Modelling. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
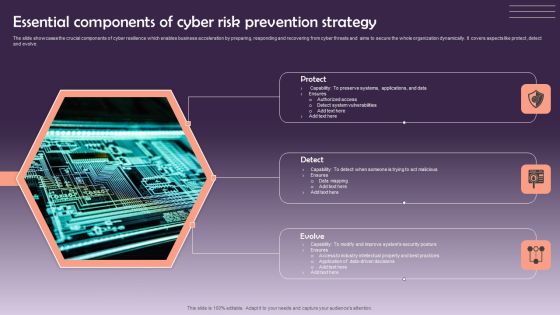
Essential Components Of Cyber Risk Prevention Strategy Information PDF
The slide showcases the crucial components of cyber resilience which enables business acceleration by preparing, responding and recovering from cyber threats and aims to secure the whole organization dynamically. It covers aspects like protect ,detect and evolve. Presenting Essential Components Of Cyber Risk Prevention Strategy Information PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Protect, Detect, Evolve. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
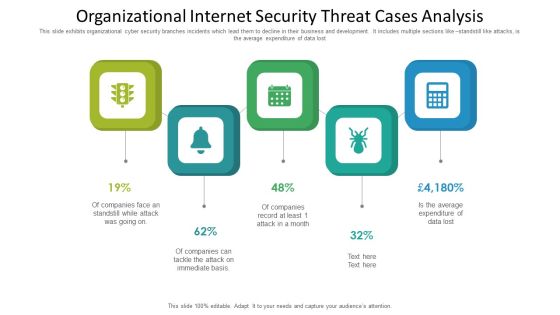
Organizational Internet Security Threat Cases Analysis Information PDF
This slide exhibits organizational cyber security branches incidents which lead them to decline in their business and development. It includes multiple sections like standstill like attacks, is the average expenditure of data lost. Presenting organizational internet security threat cases analysis information pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including organizational internet security threat cases analysis. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
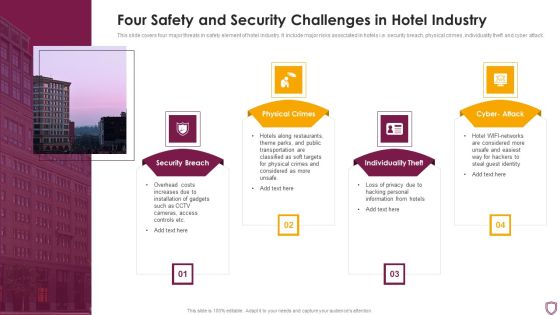
Four Safety And Security Challenges In Hotel Industry Topics PDF
This slide covers four major threats in safety element of hotel industry. It include major risks associated in hotels i.e. security breach, physical crimes, individuality theft and cyber attack. Persuade your audience using this Four Safety And Security Challenges In Hotel Industry Topics PDF This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Security Breach, Physical Crimes, Individuality Theft Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
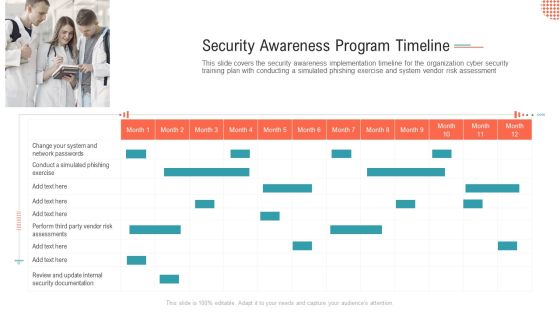
Security Awareness Program Timeline Ppt Outline Microsoft PDF
This slide covers the security awareness implementation timeline for the organization cyber security training plan with conducting a simulated phishing exercise and system vendor risk assessment.This is a security awareness program timeline ppt outline microsoft pdf. template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like conduct a simulated phishing exercise, change your system and network passwords. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Operations Application For IT Infrastructure Protection Template PDF
This slide highlight security operations SecOps use cases that could protect the business data. Some of the use cases include user-reported security incidents, infrastructure vulnerability response IVR, automation and orchestration, and SIR or VR reporting. Presenting Security Operations Application For IT Infrastructure Protection Template PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Infrastructure Vulnerability Response, Cyber Threat Intelligence, Fraud Reporting Automation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Solutions To Overcome Security Operations Challenges Template PDF
This slide outlines solutions to overcome challenges faced by security operations teams in order to deal with an increasing number of cyber attacks. It includes challenges such as skill shortage, lack of automation, large volume of data, and work processes integration. Persuade your audience using this Solutions To Overcome Security Operations Challenges Template PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Lack Of Automation, Work Processes Integration, Data Security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

IT Security Incident Escalation Communication Plan Flowchart Structure PDF
This slide illustrates a flow chart of the cyber security incident escalation communication plan to manage an attack and minimize the impact. It includes elements such as security team, incident identifier vendor notification etc. Presenting IT Security Incident Escalation Communication Plan Flowchart Structure PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Incident Identifier, Vendor Notification, Website Gets Crashed. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

The ROI Of Security Awareness Training Ppt Slides Background PDF
This slide covers the security awareness rate of interest calculations including typical cyber risk management factor for a trained, cyberconscious workforce.This is a the roi of security awareness training ppt slides background pdf. template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like costs from routine security practices, costs from productivity loss. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Pricing Plan Of Security Awareness Packages Elements PDF
The purpose of this slide is to showcase the pricing plan of cyber security awareness package. It covers information about the total number of employees along with different packages such as silver, gold, platinum and diamond. This is a Pricing Plan Of Security Awareness Packages Elements PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Pricing Plan, Security Awareness, Packages. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Awareness Packages Offered By Third Party Clipart PDF
The purpose of this slide is to highlight cyber security awareness packages such as silver, gold, platinum and diamond which are offered by third party to the businesses. The package includes key features such as unlimited phishing security tests, automated awareness training campaign etc. This is a Security Awareness Packages Offered By Third Party Clipart PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Unlimited Phishing, Automated Awareness, Industry Benchmarking. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
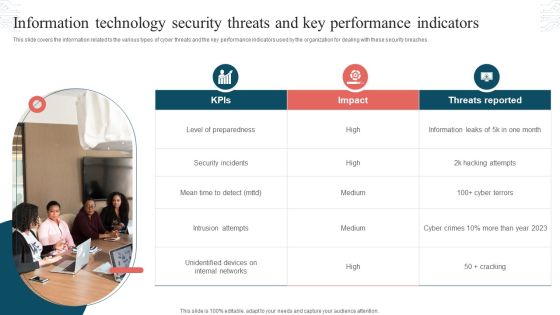
Information Technology Security Threats And Key Performance Indicators Formats PDF
This slide covers the information related to the various types of cyber threats and the key performance indicators used by the organization for dealing with these security breaches. Presenting Information Technology Security Threats And Key Performance Indicators Formats PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Threats Reported, Security Incidents, Intrusion Attempts. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
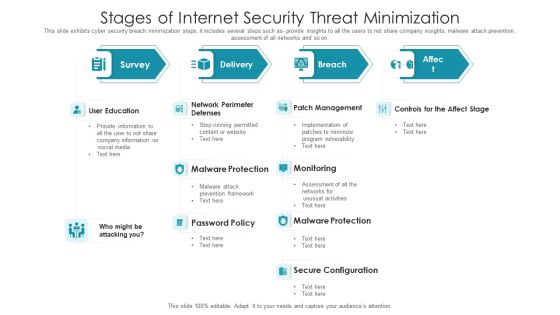
Stages Of Internet Security Threat Minimization Summary PDF
This slide exhibits cyber security breach minimization steps, it includes several steps such as- provide insights to all the users to not share company insights, malware attack prevention, assessment of all networks and so on. Pitch your topic with ease and precision using this stages of internet security threat minimization summary pdf. This layout presents information on patch management, monitoring, malware protection, secure configuration, user education. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Effective Online Security Risk Assessment Process Inspiration PDF
This slide showcases digital safety risk assessment process which helps identify potential cyber vulnerabilities. It provides steps such as asset prioritization, identify threat, analyze controls, assess impact and recommend controls. Persuade your audience using this Effective Online Security Risk Assessment Process Inspiration PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Card Data Security, Cross Border Transactions, Payment Methods. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

IT Security Defense Plan Maturity Evaluation Information PDF
This slide represents cyber security defense strategy maturity evaluation mode illustrating culture and organization, governance, visibility and controls, focused defense and intelligence operations. Persuade your audience using this IT Security Defense Plan Maturity Evaluation Information PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Organization, Focused Defense, Intelligence Operations. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Best Practices To Develop IT Security Communication Plan Diagrams PDF
This slide illustrates various best practices for developing an effective Cyber security communication plan. It includes best practices such as make plan flexible, provide visibility to audience and keep relevant and engaging content. Presenting Best Practices To Develop IT Security Communication Plan Diagrams PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Make Plan Flexible, Provide Visibility Audience, Keep Relevant Engaging. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

IT Security Incident Response Communication Plan Development Background PDF
This slide illustrates steps to develop a cyber security incident response communication plan to minimize impact level. It includes steps such as formulate team activation process, designate person, create criteria for law involvement etc. Presenting IT Security Incident Response Communication Plan Development Background PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Formulate Team Activation, Designate Person, Formulate Communication Template. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
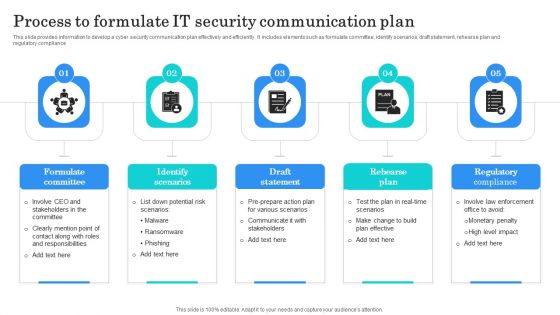
Process To Formulate IT Security Communication Plan Clipart PDF
This slide provides information to develop a cyber security communication plan effectively and efficiently. It includes elements such as formulate committee, identify scenarios, draft statement, rehearse plan and regulatory compliance. Presenting Process To Formulate IT Security Communication Plan Clipart PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Formulate Committee, Identify Scenarios, Draft Statement. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Asset Identification For Information Security Risk Management Topics PDF
This slide showcases identification of asset which can help organization to formulate risk monitoring plan. It can help to monitor the asset in real time for any data breach or cyber attack This is a Asset Identification For Information Security Risk Management Topics PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Customers Database, Products Database, Sales Database. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Data Integration Architecture To Manage Cyber Risk Pictures PDF
This slide showcases the structure to manage cybersecurity threats and risk of any organization. It includes steps such as identifying user with data access, protecting data accessibility, secure networks, install and updating antivirus, developing plan for managing disasters etc. Presenting Identify, Protect, Detect to dispense important information. This template comprises Five stages. It also presents valuable insights into the topics including Data Integration Architecture To Manage Cyber Risk Pictures PDF. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Picture Of Cyber Attack Warning Ppt PowerPoint Presentation Model Background Images PDF
Presenting this set of slides with name picture of cyber attack warning ppt powerpoint presentation model background images pdf. This is a three stage process. The stages in this process are picture of cyber attack warning. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Comparison Of Various Security Awareness Training Software Demonstration PDF
The purpose of this slide is to drawn comparison of multiple software which can be used to provide cyber security training to the key stakeholders. Information covered in this slide is related to phishing simulations, security reporting, individualized security training plan etc. If you are looking for a format to display your unique thoughts, then the professionally designed Comparison Of Various Security Awareness Training Software Demonstration PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Comparison Of Various Security Awareness Training Software Demonstration PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
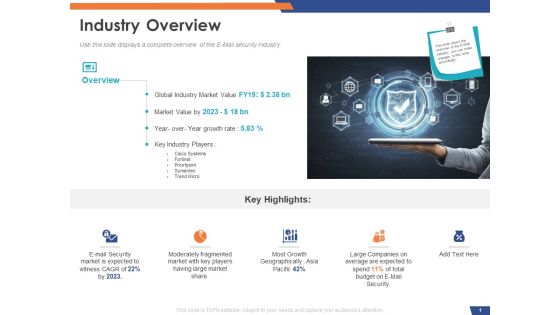
Email Security Market Research Report Industry Overview Ppt Outline Graphic Images PDF
Presenting this set of slides with name email security market research report industry overview ppt outline graphic images pdf. This is a two stage process. The stages in this process are moderately fragmented market with key players having large market share, global industry market value, key industry players. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Comparison Of Various Cyber Protection Software Portrait PDF
This slide shows comparative analysis of various cyber protection tools which can be used by organizations for IT safety. It includes features, compatibility, price and ratings. Pitch your topic with ease and precision using this Comparison Of Various Cyber Protection Software Portrait PDF. This layout presents information on Compatibility, Price, Security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

PCI Certification For Increasing Security Of Online Transactions Designs PDF
This slide depicts payment card industry PCI certification for increasing security of online transactions. It provides information about authorization, 2 way authentication, one time password OTP, repository, cyber attacks, compliance, data breach, etc. Presenting this PowerPoint presentation, titled PCI Certification For Increasing Security Of Online Transactions Designs PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this PCI Certification For Increasing Security Of Online Transactions Designs PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable PCI Certification For Increasing Security Of Online Transactions Designs PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Table Of Contents Cyber Safety Incident Management Formats PDF
Presenting table of contents cyber safety incident management formats pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like ensuring financial assets security, leveraging workforce, budget assessment, impact assessment, dashboard . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Computer System Security PowerPoint Templates And PowerPoint Themes 1012
Computer System Security PowerPoint Templates And PowerPoint Themes 1012-Deliver amazing Presentations with our above template consists of laptop and lifesaver. This image represents the concept of computer help or assistance. This template also depicts the concept of computer security. Use this template for web services, technical support etc. It signifies assistance, nteworking, rescue and save. It is a useful captivating tool conceived to enable you to define your message in your Business PPT presentations. Deliver amazing presentations to mesmerize your audience.-Computer System Security PowerPoint Templates And PowerPoint Themes 1012-This PowerPoint template can be used for presentations relating to-Computer network , marketing, finance, internet, computer, technology

PCI Certification For Increasing Security Of Online Transactions Background PDF
This slide depicts payment card industry PCI certification for increasing security of online transactions. It provides information about authorization, 2 way authentication, one time password OTP, repository, cyber attacks, compliance, data breach, etc. Explore a selection of the finest PCI Certification For Increasing Security Of Online Transactions Background PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our PCI Certification For Increasing Security Of Online Transactions Background PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Cyber Physical Systems Architecture Network Layer Ppt PowerPoint Presentation Diagram Images PDF
This slide describes the network layer of cyber physical system architecture, including the tasks performed and protocols used at this level, such as IPv6, LTE, IR, and so on. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Cyber Physical Systems Architecture Network Layer Ppt PowerPoint Presentation Diagram Images PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Assessing Organizations Cyber Risk Prevention Level Template PDF
The slide showcases cyber resilience matrix to assess the level of organizations that excel at cyber resilience, but also align with the business strategy to achieve better business outcomes. It covers four levels business blockers, cyber champions, the vulnerable and cyber risk takers. Presenting Assessing Organizations Cyber Risk Prevention Level Template PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Cybersecurity Resilience, Cyber Champions. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Pricing Plan Of Security Awareness Packages Slides PDF
The purpose of this slide is to showcase the pricing plan of cyber security awareness package. It covers information about the total number of employees along with different packages such as silver, gold, platinum and diamond. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Pricing Plan Of Security Awareness Packages Slides PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Prevention Of Information Operational Outlook Of Security Awareness Structure PDF
The purpose of this slide is to showcase the general outlook of cyber security awareness training software. The slide covers information about opened simulations, links clicked, reported, attachments opened, data entered. Slidegeeks has constructed Prevention Of Information Operational Outlook Of Security Awareness Structure PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
Prevention Of Information Security Awareness Training Program Challenges Icons PDF
The purpose of this slide is to exhibit biggest cyber security awareness challenges which is faced by the organization. Outdated content, burden on administrators, low employee participation rate and employees losing interest are some of the key challenges which are highlighted in the slide. Want to ace your presentation in front of a live audience Our Prevention Of Information Security Awareness Training Program Challenges Icons PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

Security Awareness Training Program Challenges Ppt Styles Clipart PDF
The purpose of this slide is to exhibit biggest cyber security awareness challenges which is faced by the organization. Outdated content, burden on administrators, low employee participation rate and employees losing interest are some of the key challenges which are highlighted in the slide. Take your projects to the next level with our ultimate collection of Security Awareness Training Program Challenges Ppt Styles Clipart PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.

Business Operations Strategic Tactical Planning Cyber Threat Intelligence Summary PDF
This slide exhibits strategic tactical and operational levels of cyber threat intelligence to ensure data and software protection from threats. It includes identify reason, assist extent of breach, alert and identify prevention system and ensure safety in advance. Persuade your audience using this Business Operations Strategic Tactical Planning Cyber Threat Intelligence Summary PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Strategic Cyber Threat Intelligence, Tactical Cyber Threat Intelligence, Operational Cyber Threat Intelligence. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Crime Hacking Technology Threats Ppt PowerPoint Presentation Layouts Example
Presenting this set of slides with name cyber crime hacking technology threats ppt powerpoint presentation layouts example. This is a one stage process. The stage in this process is cyber crime hacking technology threats. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Social Media Cyber Crime Ppt PowerPoint Presentation Ideas File Formats
Presenting this set of slides with name social media cyber crime ppt powerpoint presentation ideas file formats. This is a one stage process. The stage in this process is social media cyber crime. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Crime And War Strategies Icon Summary PDF
Presenting Cyber Crime And War Strategies Icon Summary PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Cyber, Crime, War Strategies Icon This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Threat Analysis Sample Diagram Presentation Visual Aids
This is a cyber threat analysis sample diagram presentation visual aids. This is a four stage process. The stages in this process are successful attack, system susceptibility, threat accessibility, threat capability.

Ways To Stop Cyber Attacks Ppt PowerPoint Presentation Inspiration Outline
Presenting this set of slides with name ways to stop cyber attacks ppt powerpoint presentation inspiration outline. This is a one stage process. The stage in this process is ways to stop cyber attacks. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Risk Icon Indicating Malware Attack Elements PDF
Presenting cyber risk icon indicating malware attack elements pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including cyber risk icon indicating malware attack. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Icon For Minimizing Online Risk And Cyber Attacks Mockup PDF
Presenting Icon For Minimizing Online Risk And Cyber Attacks Mockup PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Icon Minimizing, Online Risk, Cyber Attacks. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Attack Protection Ppt PowerPoint Presentation Model Inspiration Cpb Pdf
Presenting this set of slides with name cyber attack protection ppt powerpoint presentation model inspiration cpb pdf. This is an editable Powerpoint four stages graphic that deals with topics like cyber attack protection to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
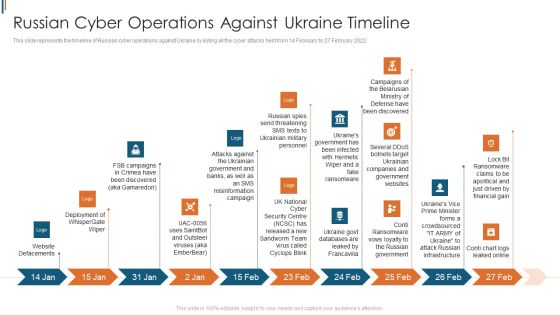
Ukraine Cyberwarfare Russian Cyber Operations Against Ukraine Timeline Portrait Pdf
This slide represents the timeline of Russian cyber operations against Ukraine by listing all the cyber attacks held from 14 February to 27 February 2022. Presenting ukraine cyberwarfare russian cyber operations against ukraine timeline portrait pdf to provide visual cues and insights. Share and navigate important information on ten stages that need your due attention. This template can be used to pitch topics like deployment of whispergate wiper, website defacements, campaigns of the belarusian ministry of defense have been discovered. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Two Factor Authentication Icon For Cyber Threat Prevention Background PDF
Presenting Two Factor Authentication Icon For Cyber Threat Prevention Background PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Two Factor Authentication, Cyber Threat, Prevention. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Major Statistics Of Cyber Phishing Scams And Attacks Designs PDF
Mentioned slide showcases key facts of cyber phishing attack. The facts covered in the slide are loss of confidential data, compromised accounts, ransomware attacks, financial loss and other malware attacks such as trojans. Pitch your topic with ease and precision using this major statistics of cyber phishing scams and attacks designs pdf. This layout presents information on major statistics of cyber phishing scams and attacks. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
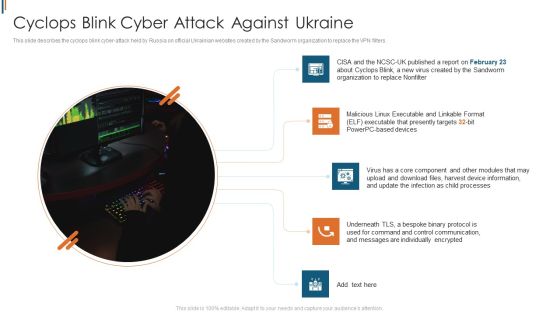
Ukraine Cyberwarfare Cyclops Blink Cyber Attack Against Ukraine Demonstration Pdf
This slide describes the cyclops blink cyber attack held by Russia on official Ukrainian websites created by the Sandworm organization to replace the VPN filters. Presenting ukraine cyberwarfare cyclops blink cyber attack against ukraine demonstration pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Virus has a core component and other modules that may upload and download files, harvest device information, and update the infection as child processes. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Data Safety Initiatives Communication Plan For Cyber Breaches Topics PDF
Mentioned slide portrays communication plan that company will use for effectively managing cyber breaches. Sections covered here are what to communicate, description, delivery method, frequency and responsible. Presenting data safety initiatives communication plan for cyber breaches topics pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like communicate, delivery method, frequency, responsible, product report. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Key Statistics Of Cyber Phishing Scams And Attacks Pictures PDF
Mentioned slide showcases major statistics of cyber phishing. Statistics mentioned in the slide are average daily legitimate emails, email volume change, average daily spam volume, change in spam volume percentage etc. Persuade your audience using this key statistics of cyber phishing scams and attacks pictures pdf. This PPT design covers two stages, thus making it a great tool to use. It also caters to a variety of topics including average, email. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Safety Incident Management Determine Threat Scenario Analysis Background PDF
This slide provides details regarding threat scenario assessment by understanding various phases of threat actor attack on victim. Presenting cyber safety incident management determine threat scenario analysis background pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like determine threat scenario analysis. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Preventing Cyber Crimes Vector Icon Ppt PowerPoint Presentation Styles Slides
Presenting this set of slides with name preventing cyber crimes vector icon ppt powerpoint presentation styles slides. This is a one stage process. The stages in this process are technology, social network, social engineering. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Three Stages Of Cyber War Attack Sample PDF
This slide shows details related to the stages of the attacks through cyber terrorism. It includes three stages of pre attack and opening moves, attack and end game and post attack.Persuade your audience using this Three Stages Of Cyber War Attack Sample PDF This PPT design covers one stage, thus making it a great tool to use. It also caters to a variety of topics including Public Information, Specifies Vulnerabilities, Focuses Exploiting Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Four Steps Of Reporting Cyber Attacks Ppt PowerPoint Presentation Guidelines
Presenting this set of slides with name four steps of reporting cyber attacks ppt powerpoint presentation guidelines. This is a four stage process. The stages in this process are technology, social network, social engineering. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

How Chatgpt Can Help In Preventing Cyber Crimes Slides PDF
This slide demonstrates the various applications of ChatGPT in the field of cybersecurity. The purpose of this slide is to explain how ChatGPT can help in predicting and avoiding cyber crimes. These include threat intelligence, anomaly detection, predictive analytics, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download How Chatgpt Can Help In Preventing Cyber Crimes Slides PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Conceptual Framework Of Cyber War With Impact Demonstration PDF
This slide covers the framework for cyberterrorism whose main objective is to destroy target organization, industry or economy. It represents the target, motivation, tools of attack, domain, method of action and impact of the cyber terrorism in a country.Presenting Conceptual Framework Of Cyber War With Impact Demonstration PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including National Information, Infrastructure System, Civilian Population This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Focus Areas For Cyber Risk Prevention Preparation Pictures PDF
The slide puts focus on three important areas which enables an organization to become more cyber-resilient. It covers aspects like prepare to contain the attack, prepare to work without IT and prepare to rebuild IT. Persuade your audience using this Focus Areas For Cyber Risk Prevention Preparation Pictures PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Prepare To Contain, Prepare To Work, Prepare To Rebuild. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Enhancing Cyber Safety With Vulnerability Administration SIEM Architecture Information PDF
Presenting enhancing cyber safety with vulnerability administration siem architecture information pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like event data, contextual data, system inputs, system outputs, data collection. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Exploitation IT Email Prevention Guidelines For Employees Formats PDF
This slide depicts the email prevention guidelines for employees, including spam filters and multi-factor authentication for email login credentials. Presenting cyber exploitation it email prevention guidelines for employees formats pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like usage of a spam filter, usage of mfa. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Five Year Cyber Information Safety Career Growth Roadmap Background
We present our five year cyber information safety career growth roadmap background. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched five year cyber information safety career growth roadmap background in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
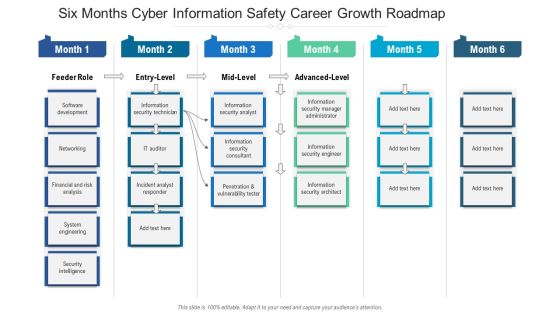
Six Months Cyber Information Safety Career Growth Roadmap Portrait
We present our six months cyber information safety career growth roadmap portrait. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched six months cyber information safety career growth roadmap portrait in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Three Months Cyber Information Safety Career Growth Roadmap Sample
We present our three months cyber information safety career growth roadmap sample. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched three months cyber information safety career growth roadmap sample in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Cyber Exploitation IT Hacking Of Email Domain Professional PDF
This slide represents the hacking of the company email domain by hackers by sending spam emails to employees and stealing money from clients and customers. Presenting cyber exploitation it hacking of email domain professional pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like hacking of email domain. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Multi Step Strategy To Implement Cyber Threat Prevention Guidelines PDF
The following slide provides a step by step strategy to monitor and reassess your organizations cybersecurity maturity which helps to strengthen the cyber safety. The process involves understand, assess, determine and document. Persuade your audience using this Multi Step Strategy To Implement Cyber Threat Prevention Guidelines PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Determine, Document, Assess. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Exploitation IT Is Ethical Hacking Legal Inspiration PDF
This slide shows the legality of ethical hacking, how ethical hackers work official permission, and companies hire them to protect their networks and computer systems from malicious attacks. Presenting cyber exploitation it is ethical hacking legal inspiration pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like is ethical hacking legal. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Icons Slide For Cyber Safety Incident Management Information PDF
Introducing our well designed icons slide for cyber safety incident management information pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.

Agenda For Russian Cyber Attacks On Ukraine Summary PDF
This is a agenda for russian cyber attacks on ukraine summary pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like technical, analysis, websites, globally. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Safety Incident Management Threat Management Action Plan Sample PDF
The threat management action plan will help in keeping the track of various potential threats that are existing in the firm. The person responsible in handling the threats will keep track of the duration in which threat is resolved. Presenting cyber safety incident management threat management action plan sample pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like threat identification, threat treatment. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Safety Incident Management Workplace Employee Assistance Program Microsoft PDF
The employee assistance program will help firm in enhancing their well being at workplace and enable them to handle critical situations. This program will render services like clinical services, work and life services and employer services, etc. Presenting cyber safety incident management workplace employee assistance program microsoft pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like clinical services, work and life services, employer services. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Elements Of Botnet Hacking And Cyber Criminal Attacks Brochure PDF
This slide illustrates key elements of botnet attacks. It includes elements such as compromised devices, command and control servers, botnet use, quiet threat, etc. Persuade your audience using this Elements Of Botnet Hacking And Cyber Criminal Attacks Brochure PDF. This PPT design covers Four stages, thus making it a great tool to use. It also caters to a variety of topics including Compromised Devices, Command Control Servers, Botnet Use, Quiet Threat. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Exploitation IT Purpose Of Hackers Infographics PDF
This slide describes the common types of cybercrime such as identity theft, computer fraud, privacy breach, electronic money laundering, electronic funds transfer, and so on. This is a cyber exploitation it purpose of hackers infographics pdf template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like computer fraud, privacy breach, electronic money laundering, electronic funds transfer, denial of service attacks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Exploitation IT Introduction To Ethical Hacking Introduction PDF
This slide depicts ethical hacking and how ethical hackers could be an asset to a company that can prevent malicious attacks on a computer system or network. This is a cyber exploitation it introduction to ethical hacking introduction pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like introduction to ethical hacking. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Mitigating Cybersecurity Threats And Vulnerabilities Addressing Cyber Threats Portrait PDF
This slide provides details regarding insider threats identified in various industries such as healthcare, manufacturing, government, energy, etc. This is a mitigating cybersecurity threats and vulnerabilities addressing cyber threats portrait pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like healthcare, manufacturing, government, energy. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
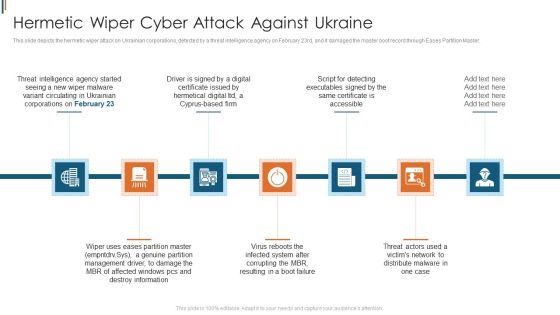
Ukraine Cyberwarfare Hermetic Wiper Cyber Attack Against Ukraine Designs Pdf
This slide depicts the hermetic wiper attack on Ukrainian corporations, detected by a threat intelligence agency on February 23rd, and it damaged the master boot record through Eases Partition Master. This is a ukraine cyberwarfare hermetic wiper cyber attack against ukraine designs pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like script for detecting executables signed by the same certificate is accessible, virus reboots the infected system after corrupting the mbr, resulting in a boot failure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
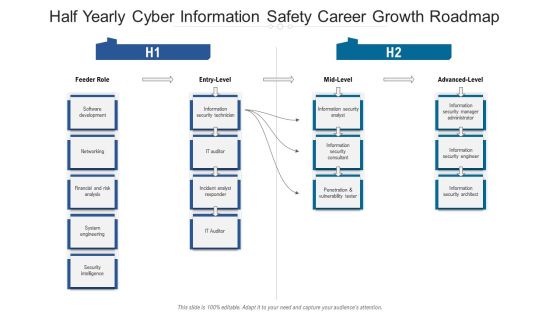
Half Yearly Cyber Information Safety Career Growth Roadmap Designs
Presenting the half yearly cyber information safety career growth roadmap designs. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Quarterly Cyber Information Safety Career Growth Roadmap Elements
Presenting the quarterly cyber information safety career growth roadmap elements. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Cyber Safety Incident Management Roles And Responsibilities Pictures PDF
This slide provides details regarding roles and responsibilities assigned to ensure minimum violence work environment. This is a cyber safety incident management roles and responsibilities pictures pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employee responsibilities, human resources responsibilities, internal investigations unit responsibilities, unit supervisor or manager responsibilities. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Cyber Threat Organizational Prevention Based Strategy Plan Template PDF
This slide presents prevention, detection and correction plan for cybersecurity and management that helps in avoiding critical situations and data loss. It includes plan for technology, processes and human activity that takes place in organisation. Introducing Cyber Threat Organizational Prevention Based Strategy Plan Template PDF. to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Technology, Processes, Human Activity, using this template. Grab it now to reap its full benefits.
Email Security Vector Icon Ppt PowerPoint Presentation Model Example Topics
Presenting this set of slides with name email security vector icon ppt powerpoint presentation model example topics. This is a four stage process. The stages in this process are email security vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
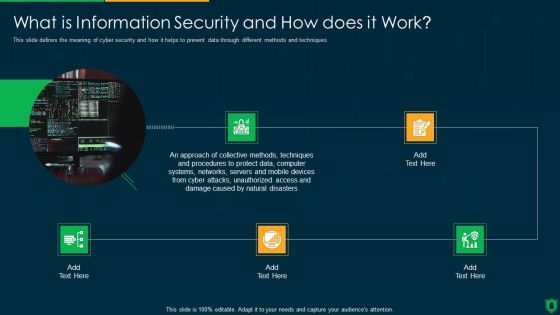
Info Security What Is Information Security And How Does It Work Ppt PowerPoint Presentation File Clipart PDF
This slide defines the meaning of cyber security and how it helps to prevent data through different methods and techniques. This is a info security what is information security and how does it work ppt powerpoint presentation file clipart pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like collective methods, techniques and procedures, protect data, computer systems, networks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Email Security Market Research Report Industry Challenges Ppt Ideas PDF
Presenting this set of slides with name email security market research report industry challenges ppt ideas pdf. This is a five stage process. The stages in this process are threat of ransomware, threat of serverless apps, iot threat. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

National Security Americana PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our National Security Americana PowerPoint Templates PPT Backgrounds For Slides 0113.Download our Security PowerPoint Templates because Our PowerPoint Templates and Slides will bullet point your ideas. See them fall into place one by one. Download our Americana PowerPoint Templates because You will get more than you ever bargained for. Use our Signs PowerPoint Templates because our PowerPoint Templates and Slides will give your ideas the shape. Download and present our Success PowerPoint Templates because Our PowerPoint Templates and Slides will weave a web of your great ideas. They are gauranteed to attract even the most critical of your colleagues. Use our Business PowerPoint Templates because Our PowerPoint Templates and Slides will let you meet your Deadlines.Use these PowerPoint slides for presentations relating to National security key, americana, security, signs, success, business. The prominent colors used in the PowerPoint template are Yellow, Blue, Red. Customers tell us our National Security Americana PowerPoint Templates PPT Backgrounds For Slides 0113 will make the presenter successul in his career/life. PowerPoint presentation experts tell us our PowerPoint templates and PPT Slides are designed by professionals You can be sure our National Security Americana PowerPoint Templates PPT Backgrounds For Slides 0113 will make you look like a winner. Customers tell us our PowerPoint templates and PPT Slides will generate and maintain the level of interest you desire. They will create the impression you want to imprint on your audience. Professionals tell us our National Security Americana PowerPoint Templates PPT Backgrounds For Slides 0113 have awesome images to get your point across. You can be sure our success PowerPoint templates and PPT Slides are aesthetically designed to attract attention. We guarantee that they will grab all the eyeballs you need.

Winning Strategies To Improve Organization Data Security Pictures PDF
The following slide highlights a winning strategy to avoid data security breach in the organization. Businesses can protect the confidential data by following strategies such as security audit, establishing strong password, back up sensitive data, and improve cyber-security. Presenting Winning Strategies To Improve Organization Data Security Pictures PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Security Audit, Establish Strong, Sensitive Data. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

E Mail Locked Security PowerPoint Templates And PowerPoint Backgrounds 0211
Microsoft PowerPoint Template and Background with graphic concept email with padlock

E Mail Locked Security PowerPoint Themes And PowerPoint Slides 0211
Microsoft PowerPoint Theme and Slide with graphic concept email with padlock

Traditional Perimeter Based Network Security Overview And Limitations Inspiration PDF
This slide represents the overview of traditional perimeter-based network security. The purpose of this slide is to showcase the various challenges of conventional perimeter-based security and how ZTNA can overcomethose challenges. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Traditional Perimeter Based Network Security Overview And Limitations Inspiration PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Various Online Security Services With Antivirus Firewall Ppt PowerPoint Presentation File Background Images PDF
Presenting this set of slides with name various online security services with antivirus firewall ppt powerpoint presentation file background images pdf. This is a eight stage process. The stages in this process are global secure, computer security, mobile security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Icons Slide For Cloud Based Email Security Market Report Ppt Infographics Graphic Images PDF
Introducing our well designed icons slide for cloud based email security market report ppt infographics graphic images pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.

Cloud Network Security Dimensions And Sections Ppt PowerPoint Presentation Icon Background Images PDF
Presenting cloud network security dimensions and sections ppt powerpoint presentation icon background images pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like security, service, threats. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Organizational Network Staff Learning Security Awareness Tracking Kpis Event Ppt Slides Clipart Images PDF
Presenting organizational network staff learning security awareness tracking kpis event ppt slides clipart images pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like compliance, security culture, incident reduction. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

Solarwinds Security Event Manager Ethical Hacking Tool Ppt Show Clipart Images PDF
This slide represents the SolarWinds security event manager ethical hacking tool and its features such as integrity monitoring, easy to use user interface, built-in compliance reports, etc. Presenting solarwinds security event manager ethical hacking tool ppt show clipart images pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like network, security program, dashboard, system. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Network Security Devices Computer Network Ppt PowerPoint Presentation Visual Aids Background Images Cpb Pdf
Presenting this set of slides with name network security devices computer network ppt powerpoint presentation visual aids background images cpb pdf. This is an editable Powerpoint three stages graphic that deals with topics like network security devices computer network to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Network Monitoring Management Security Ppt PowerPoint Presentation Summary Clipart Images Cpb
Presenting this set of slides with name network monitoring management security ppt powerpoint presentation summary clipart images cpb. This is an editable Powerpoint five stages graphic that deals with topics like network monitoring management security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Web Application Security Testing Vector Icon Ppt PowerPoint Presentation Pictures Clipart Images
Presenting this set of slides with name web application security testing vector icon ppt powerpoint presentation pictures clipart images. This is a one stage process. The stages in this process are Penetration Testing, Internal Testing, Gaining access. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

CVV On Debit Card For Security Ppt PowerPoint Presentation Pictures Background Images
Presenting this set of slides with name cvv on debit card for security ppt powerpoint presentation pictures background images. This is a one stage process. The stages in this process are credit card, atm card, online purchase. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Information Security Prepare And Deploy Strong IT Policies Ppt Gallery Images PDF
This slide represents the value of having strong IT policies within an organization regarding software, hardware, passwords, and data transfer. Deliver an awe inspiring pitch with this creative information security prepare and deploy strong it policies ppt gallery images pdf bundle. Topics like management, network, device, data can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
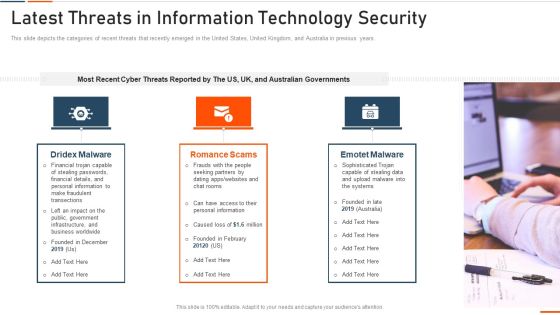
Latest Threats In Information Technology Security Ppt Pictures Designs PDF
This slide represents the different elements of Network security such as application security, network security, information security, etc. This is a latest threats in information technology security ppt pictures designs pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like network security, cloud security, application security, operational security, information security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Online Security Requirements For Iot Devices And Systems Graphics PDF
This slide showcases digital security requirements for IOT devices which help analyze security security threats and vulnerabilities. It provides information regarding email encryption, data integrity, security policy and monitoring and user authentication. Pitch your topic with ease and precision using this Online Security Requirements For Iot Devices And Systems Graphics PDF. This layout presents information on Device Management, Security Policy, Security Monitoring. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Example Of Security Testing Services Ppt Powerpoint Guide
This is a example of security testing services ppt powerpoint guide. This is a eight stage process. The stages in this process are security management, access security, application security, networking security, test delivery, results and analysis, technology enablement, test development and publishing.

Levels Of Security Concerns In Cloud Network Download PDF
The slide showcases levels of security concerns that measure user and device authentication. The elements are virtual machine security , network security , interface security , privacy concerns etc. Presenting Levels Of Security Concerns In Cloud Network Download PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Virtual Machine Security, Interface Security, Network Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Network Security Enterprise Ppt Powerpoint Presentation Infographics Templates Cpb
This is a network security enterprise ppt powerpoint presentation infographics templates cpb. This is a five stage process. The stages in this process are network security enterprise.

Online Security Ppt PowerPoint Presentation Pictures Layout Ideas Cpb
This is a online security ppt powerpoint presentation pictures layout ideas cpb. This is a four stage process. The stages in this process are online security.
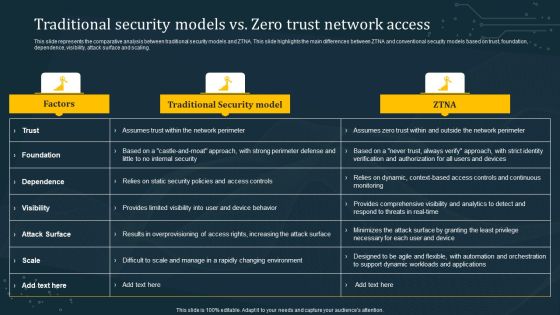
Traditional Security Models Vs Zero Trust Network Access Summary PDF
This slide represents the comparative analysis between traditional security models and ZTNA. This slide highlights the main differences between ZTNA and conventional security models based on trust, foundation, dependence, visibility, attack surface and scaling. This modern and well-arranged Traditional Security Models Vs Zero Trust Network Access Summary PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Electronic Voting System Voting System Standards Security Template PDF
This slide represents the security standard of the voting system that ensures the security of voting machines to prevent them from being tempered or manipulated through physical security, auditability, and internet connection.Presenting Electronic Voting System Voting System Standards Security Template PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Manipulated Tampered, Ensuring Security, Security Include. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
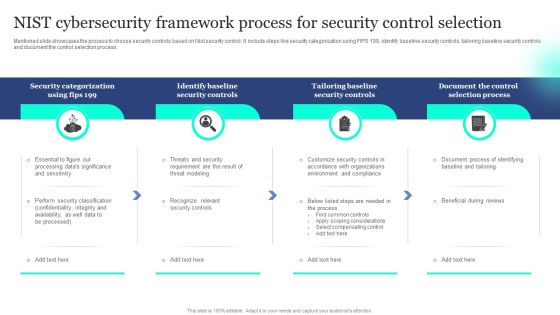
NIST Cybersecurity Framework Process For Security Control Selection Introduction PDF
Mentioned slide showcases the process to choose security controls based on Nist security control. It include steps like security categorization using FIPS 199, identify baseline security controls, tailoring baseline security controls and document the control selection process. Presenting NIST Cybersecurity Framework Process For Security Control Selection Introduction PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Security Controls, Tailoring Baseline, Selection Process. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
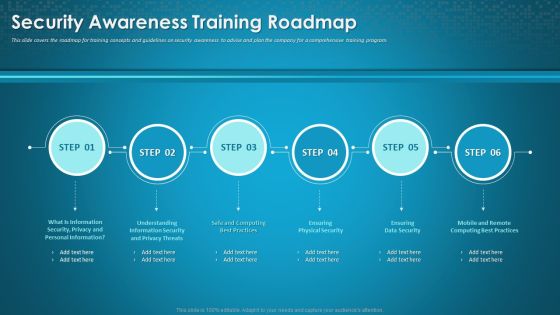
Organizational Network Staff Learning Security Awareness Training Roadmap Sample PDF
This slide covers the roadmap for training concepts and guidelines on security awareness to advise and plan the company for a comprehensive training program. Presenting organizational network staff learning security awareness training roadmap sample pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like ensuring data security, information security and privacy threats, ensuring physical security. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

Organizational Network Staff Learning Security Awareness Program Checklist Background PDF
This slide covers the Checklist that will help organizations prepare and implement their safety awareness training. The details listed below can be used to promote preparation and education planning in the area of security awareness. Presenting organizational network staff learning security awareness program checklist background pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security awareness program, implementing security awareness, sustaining security awareness. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
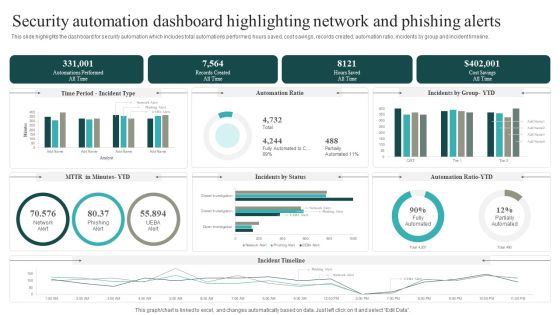
Security Automation Dashboard Highlighting Network And Phishing Alerts Microsoft PDF
This slide highlights the dashboard for security automation which includes total automations performed, hours saved, cost savings, records created, automation ratio, incidents by group and incident timeline. This modern and well arranged Security Automation Dashboard Highlighting Network And Phishing Alerts Microsoft PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Process Of Web Security Testing And Analysis Ppt Design
This is a process of web security testing and analysis ppt design. This is a six stage process. The stages in this process are error handing, controlled access, session management, network security, server and code management, data access.
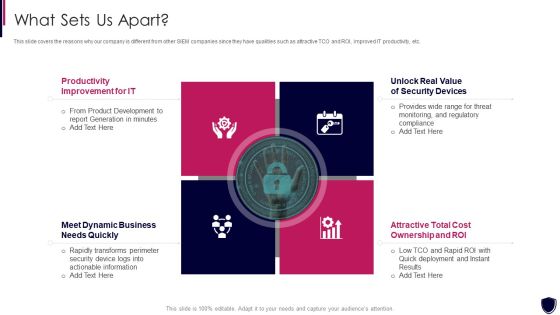
Enhancing Cyber Safety With Vulnerability Administration What Sets Us Apart Microsoft PDF
This slide covers the reasons why our company is different from other SIEM companies since they have qualities such as attractive TCO and ROI, improved IT productivity, etc. This is a enhancing cyber safety with vulnerability administration what sets us apart microsoft pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like productivity improvement for it, meet dynamic business , needs quickly unlock real value of security devices, attractive total cost ownership and roi. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Benefits Reaped Through Cloud Network Security Sample PDF
The slide showcases benefits of cloud security that continuously help monitor, identify, analyze and mitigate attacks. The elements are optimize security cost, automated security, response time , centralize security with easy management , reliability with easy access . Presenting Benefits Reaped Through Cloud Network Security Sample PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Optimize Security Cost, Response Time, Future Considerations. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Sample Network Security Diagram Ppt Example Of Ppt
This is a sample network security diagram ppt example of ppt. This is a six stage process. The stages in this process are network security, analyse, plan, design, implement, operate, optimize.

Modern Digital Smart Phone Device Security Methods Elements PDF
This slide shows major categories of mobile device security approaches. The purpose of this slide is to highlight effective approaches for protecting business data. It include methods such as endpoint protection and email security, etc. Persuade your audience using this Modern Digital Smart Phone Device Security Methods Elements PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Endpoint Protection, Secure Web Gateway, Email Security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Determine Established Security Centre Overview Ppt Show Visual Aids PDF
This slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. Deliver an awe inspiring pitch with this creative determine established security centre overview ppt show visual aids pdf bundle. Topics like security, network, systems, management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security And Surveillance Company Profile Our Expertise Professional PDF
This slide highlights the security company expertise which includes integrated control of devices, internet protocol, RFID based security, wireless based communication and locality surveillance. Presenting Security And Surveillance Company Profile Our Expertise Professional PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Secure Environment, Communication Infrastructure, Physical Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Five Elements Of Cloud Services Security Brochure PDF
This slide includes elements of cloud computing security to assure network protection and efficient management. It contains five elements architecture, security, due diligence, authentication, monitor and visibility.Presenting Five Elements Of Cloud Services Security Brochure PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Security Coverage, Intrusion Detection, Computing Regulations. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

6 Step Process To Implement Information Availability Security Icons PDF
This slide represents 6 step process to implement data availability security illustrating simplified recording, on site maintenance and online security, training, record disposal and plan. Presenting 6 step process to implement information availability security icons pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including required, develop, security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
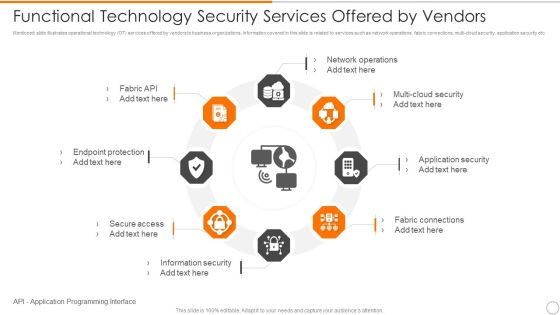
Functional Technology Security Services Offered By Vendors Microsoft PDF
Persuade your audience using this functional technology security services offered by vendors microsoft pdf. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including network operations, security, application security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Checklist To Implement Cloud Security In Business Microsoft PDF
This slide shows the checklist to implement cloud security in business, including policies and procedures, access control, networking, backup data, security patches, etc. Presenting Checklist To Implement Cloud Security In Business Microsoft PDF to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like Access Control, Networking, Security Patches And Updates. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Computing Security Management Technology Framework Elements PDF
This slide illustrates a strategic framework for cloud security technology which is used in various aspects of data and network protection. Key components are disaster recovery, governance, monitoring, user access management, data security etc. Persuade your audience using this Cloud Computing Security Management Technology Framework Elements PDF. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including User Access Management, Data Security, Hardware And Software, Network Security, Monitoring, Governance. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
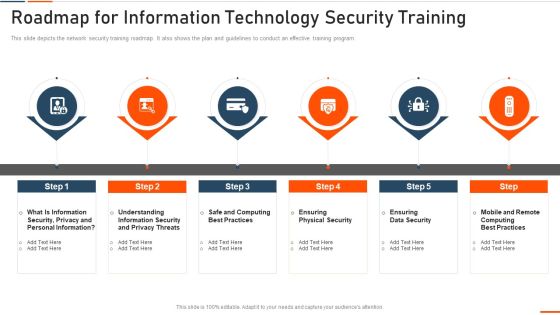
Roadmap For Information Technology Security Training Ppt Ideas Influencers PDF
This slide depicts the network security training roadmap. It also shows the plan and guidelines to conduct an effective training program. This is a roadmap for roadmap for information technology security training ppt ideas influencers pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like rmation security, computing best practices, physical security, data security . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
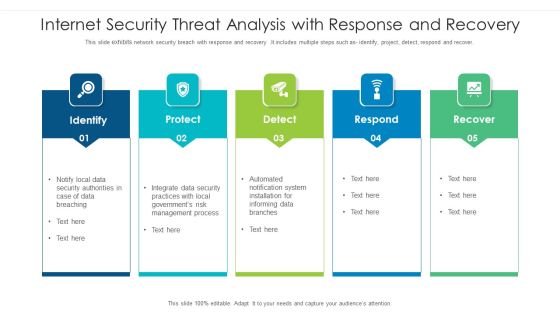
Internet Security Threat Analysis With Response And Recovery Information PDF
This slide exhibits network security breach with response and recovery .It includes multiple steps such as- identify, project, detect, respond and recover. Pitch your topic with ease and precision using this internet security threat analysis with response and recovery information pdf. This layout presents information on internet security threat analysis with response and recovery. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Our Clients Security And Surveillance Company Profile Graphics PDF
This slide highlights the security company reputed clients which showcases client name, contract term and product or service including CCTV, wireless solution, CO2 monitor, door sensor, and fire fighting system. Deliver an awe inspiring pitch with this creative Our Clients Security And Surveillance Company Profile Graphics PDF bundle. Topics like Fighting System, Security Surveillance, Wireless Networking can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Differentiating 2 Items Graphic For Free Internet Security Guidelines PDF
Deliver an awe inspiring pitch with this creative differentiating 2 items graphic for free internet security guidelines pdf bundle. Topics like differentiating 2 items graphic for free internet security reviews can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Sample Of Internet Of Things Security Ppt Sample Ppt Files
This is a sample of internet of things security ppt sample ppt files. This is a five stage process. The stages in this process are personalized information service intelligent transportation environmental monitoring, cloud computing intelligent computing, interest mobile communication network satellite nets, network infrastructure and communication protocols, supports layer, network layer, perceptual layer, application layer, network security management, rfid reader sensor gpb.
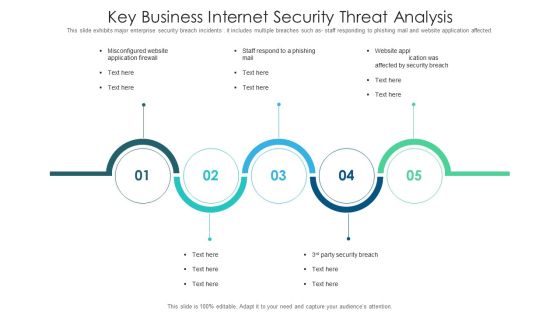
Key Business Internet Security Threat Analysis Slides PDF
This slide exhibits major enterprise security breach incidents . it includes multiple breaches such as staff responding to phishing mail and website application affected. Presenting key business internet security threat analysis slides pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including key business internet security threat analysis. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Differentiating 2 Items Illustration For Free Internet Security Clipart PDF
Presenting differentiating 2 items illustration for free internet security clipart pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like differentiating 2 items illustration for free internet security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Organizational Network Staff Learning Security Awareness Tracking Kpis Demonstration PDF
This slide covers the key performance for security awareness training including compliance, security culture and incident reduction. This is a organizational network staff learning security awareness tracking kpis demonstration pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like compliance, security culture, incident reduction. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Online Certificate Security And Privacy Measures Ppt Ideas Gallery PDF
This slide showcases the features do digital security have for security. It includes features such as authentication, confidentiality, integrity, non-repudiation and access control. Persuade your audience using this Online Certificate Security And Privacy Measures Ppt Ideas Gallery PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Security Measures, Functions, Authentication, Confidentiality. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Security Camera System Company Profile Our Expertise Pictures PDF
This slide highlights the security company expertise which includes integrated control of devices, internet protocol, RFID based security, wireless based communication and locality surveillance. This is a Security Camera System Company Profile Our Expertise Pictures PDF template with various stages. Focus and dispense information on Eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Internet Protocol, Physical Security, Communication Infrastructure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Real Time Assessment Of Security Threats SIEM Integrations Slides PDF
Presenting real time assessment of security threats siem integrations slides pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security events, network logs, applications and devices, it infrastructure. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Certified Information Systems Security Professional Cissp Examination Details Topics PDF
Presenting Certified Information Systems Security Professional Cissp Examination Details Topics PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Software Development, Security Assessment, Communications And Network. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Ways To Improve Digital Banking Security Elements PDF
This slide mentions the ways to improve online banking security for seamless customer experience. It includes industry standard security protocol, skipping public Wi-Fi, changing password regularly and asking for text alerts. Presenting Ways To Improve Digital Banking Security Elements PDF to dispense important information. This template comprises Four stages. It also presents valuable insights into the topics including Industry Standard Security Protocol, Skip Public Wifi, Change Passwords Regularly. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Network Cloud Network Security Analysis Icon Icons PDF
Persuade your audience using this Network Cloud Network Security Analysis Icon Icons PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Network Cloud, Network Security, Analysis Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Web Acceleration Security Software Shopping Carts Ppt Example
This is a web acceleration security software shopping carts ppt example. This is a eight stage process. The stages in this process are web acceleration, security software, shopping carts, data services, portals and intranets, domain name services, hosted application, cloud computing.

 Home
Home