Cyber Security Image
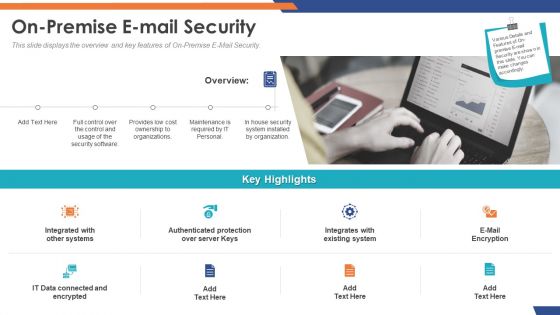
Email Security Market Research Report On Premise E Mail Security Mockup PDF
Presenting this set of slides with name email security market research report on premise e mail security mockup pdf. This is a two stage process. The stages in this process are integrated with other systems, authenticated protection over server keys, integrates with existing system, e mail encryption. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Global Cloud Based Email Security Market On Premise E Mail Security Topics PDF
Presenting this set of slides with name global cloud based email security market on premise e mail security topics pdf. This is a two stage process. The stages in this process are integrated with other systems, authenticated protection over server keys, integrates with existing system, e mail encryption. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
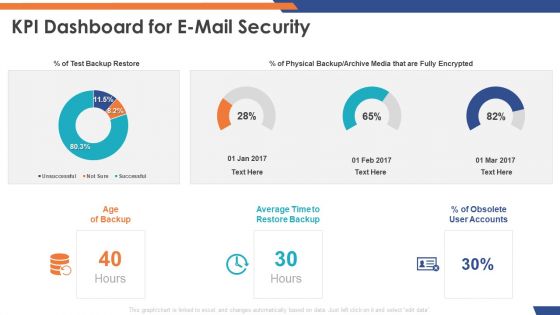
Email Security Market Research Report KPI Dashboard For E Mail Security Graphics PDF
Presenting this set of slides with name email security market research report kpi dashboard for e mail security graphics pdf. The topics discussed in these slides are test backup restore, physical backup or archive media that are fully encrypted, obsolete user accounts, average time to restore backup. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

IT Security Automation Tools Integration Security Automation Integrates Tools Systems Summary PDF
This slide highlights the security automation platform which showcases its key features it also showcases the importance and value of security tools, people and system procedures. This is a IT Security Automation Tools Integration Security Automation Integrates Tools Systems Summary PDF template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Intrusion Detection System, Firewalls, Secure Email Gateways. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
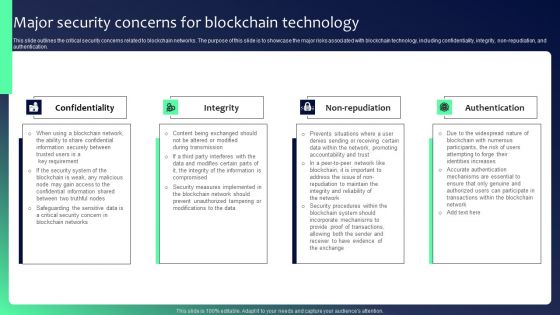
Blockchain Security Solutions Deployment Major Security Concerns For Blockchain Graphics PDF
This slide outlines the critical security concerns related to blockchain networks. The purpose of this slide is to showcase the major risks associated with blockchain technology, including confidentiality, integrity, non-repudiation, and authentication. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Blockchain Security Solutions Deployment Major Security Concerns For Blockchain Graphics PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Blockchain Security Solutions Deployment Major Security Concerns For Blockchain Graphics PDF today and make your presentation stand out from the rest
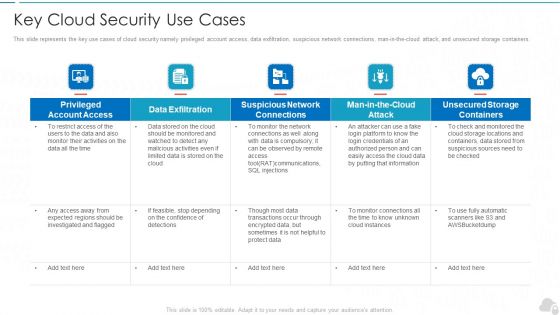
Key Cloud Security Use Cases Cloud Computing Security IT Ppt Visual Aids Ideas PDF
This slide represents the key use cases of cloud security namely privileged account access, data exfiltration, suspicious network connections, man-in-the-cloud attack, and unsecured storage containe. Deliver an awe inspiring pitch with this creative key cloud security use cases cloud computing security it ppt visual aids ideas pdf bundle. Topics like privileged account access, data exfiltration, suspicious network connections, man in the cloud attack, unsecured storage containers can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Camera System Company Profile Our Security Services And Solutions Topics PDF
This slide highlights the security company services which includes CCTV, mobile app software, occupancy sensor, audio video solution. Co2 monitor, door sensor, leak detector, smoke detector and indoor camera.Presenting Security Camera System Company Profile Our Security Services And Solutions Topics PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Networking Solution, Display Solutions, Occupancy Sensor. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
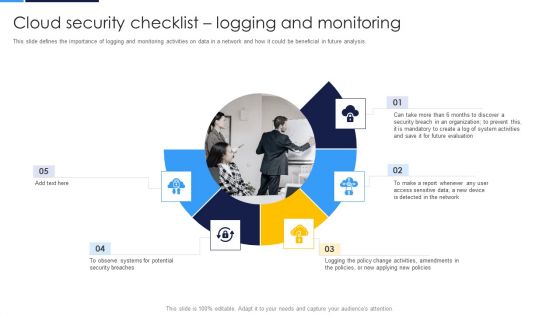
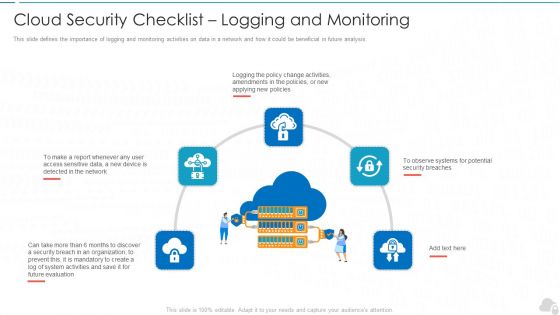
Cloud Security Assessment Cloud Security Checklist Logging And Monitoring Information PDF
This slide defines the importance of logging and monitoring activities on data in a network and how it could be beneficial in future analysis.Presenting Cloud Security Assessment Cloud Security Checklist Logging And Monitoring Information PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Security Breaches, Access Sensitive, System Activities In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Information Security Cloud Security Checklist Logging And Monitoring Ppt Show Information PDF
This slide defines the importance of logging and monitoring activities on data in a network and how it could be beneficial in future analysis. Presenting Cloud Information Security Cloud Security Checklist Logging And Monitoring Ppt Show Information PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Future Evaluation, New Policies, Potential Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

SDN Security Architecture What Role Does SDN Play In Customer Security Mockup PDF
This slide represents the role of software defined networking in customer security. It allows clients to have separate settings for each type of network traffic and permits a low security public facing network for regular information. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. SDN Security Architecture What Role Does SDN Play In Customer Security Mockup PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Cloud Security Assessment Checklist To Implement Cloud Security In Business Ideas PDF
This slide shows the checklist to implement cloud security in business, including policies and procedures, access control, networking, backup data, security patches, etc.This is a Cloud Security Assessment Checklist To Implement Cloud Security In Business Ideas PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Access Control, Data Encryption, Logging And Monitoring You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Best Data Security Software Case Study For Company Online Database Security Proposal Template PDF
Presenting this set of slides with name best data security software case study for company online database security proposal template pdf. This is a three stage process. The stages in this process are problem, our solution, results. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Best Data Security Software Our Expertise For Company Online Database Security Proposal Formats PDF
Presenting this set of slides with name best data security software our expertise for company online database security proposal formats pdf. This is a three stage process. The stages in this process are mobile app development, onsite developer, business intelligence analytics. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
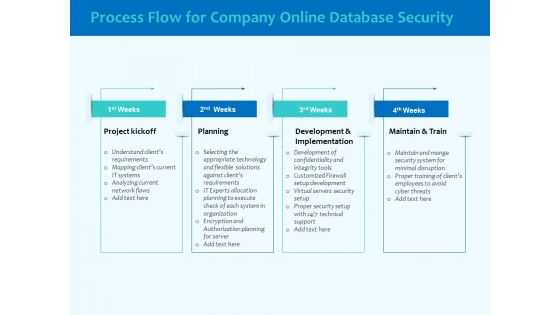
Best Data Security Software Process Flow For Company Online Database Security Elements PDF
Presenting this set of slides with name best data security software process flow for company online database security elements pdf. This is a four stage process. The stages in this process are project kickoff, planning, development and implementation, maintain and train. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Best Data Security Software Timeframe For Company Online Database Security Proposal Topics PDF
Presenting this set of slides with name best data security software timeframe for company online database security proposal topics pdf. This is a four stage process. The stages in this process are project kickoff, planning, development and implementation, result. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Workforce Security Realization Coaching Plan Agenda For Workforce Security Realization Coaching Plan Topics PDF
Presenting workforce security realization coaching plan agenda for workforce security realization coaching plan topics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like cybersecurity, information, information systems, threats, training. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

Organizational Network Security Awareness Staff Learning Where Is The Gap In Security Programs Template PDF
This slide covers the problems in the organization regarding security awareness training along with the gap and solution to overcome those gaps. This is a organizational network security awareness staff learning where is the gap in security programs template pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employees, management, organizations, targeted training, procedures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
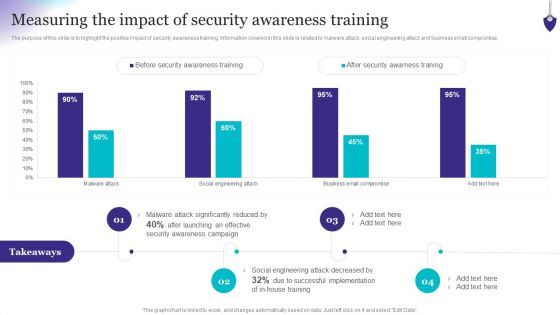
Organizing Security Awareness Measuring The Impact Of Security Awareness Training Background PDF
The purpose of this slide is to highlight the positive impact of security awareness training. Information covered in this slide is related to malware attack, social engineering attack and business email compromise. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Organizing Security Awareness Measuring The Impact Of Security Awareness Training Background PDF from Slidegeeks and deliver a wonderful presentation.

Online Security Assessment Tools Used To Identify Security Threats Slides PDF
This slide showcases digital safety assessment tools used to safeguard vulnerable operations systems in the organization. It provides information regarding protocol scanner, web application scanner, network scanner and attack simulation tool. Persuade your audience using this Online Security Assessment Tools Used To Identify Security Threats Slides PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Network Scanners, Attack Simulation Tool, Web Application Scanner. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
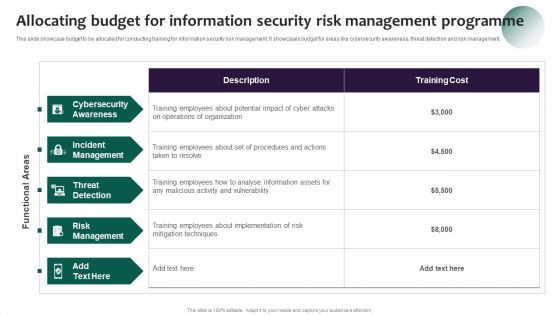
Information Systems Security And Risk Management Plan Allocating Budget For Information Security Risk Management Demonstration PDF
This slide showcase budget to be allocated for conducting training for information security risk management. It showcases budget for areas like cybersecurity awareness, threat detection and risk management Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Information Systems Security And Risk Management Plan Allocating Budget For Information Security Risk Management Demonstration PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Information Systems Security And Risk Management Plan Allocating Budget For Information Security Risk Management Demonstration PDF.
Security And Surveillance Company Profile Our Security Services And Solutions Icons PDF
This slide highlights the security company services which includes CCTV, mobile app software, occupancy sensor, audio video solution. Co2 monitor, door sensor, leak detector, smoke detector and indoor camera.This is a Security And Surveillance Company Profile Our Security Services And Solutions Icons PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Networking Solution, Display Solutions, Occupancy Sensor. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Checklist Data Encryption Cloud Computing Security IT Ppt Summary Tips PDF
This slide represents the importance of data encryption in cloud security and what type of data should always be encrypted through private keys. This is a cloud security checklist data encryption cloud computing security it ppt summary tips pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like safeguard, data servers, network, encryption. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
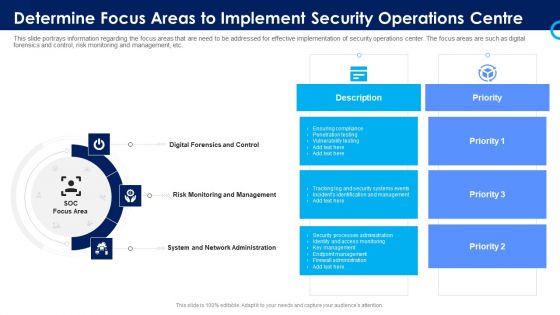
Organizational Security Solutions Determine Focus Areas To Implement Security Operations Centre Sample PDF
This slide portrays information regarding the focus areas that are need to be addressed for effective implementation of security operations center. The focus areas are such as digital forensics and control, risk monitoring and management, etc. This is a organizational security solutions determine focus areas to implement security operations centre sample pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like digital forensics and control, risk monitoring and management, system and network administration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
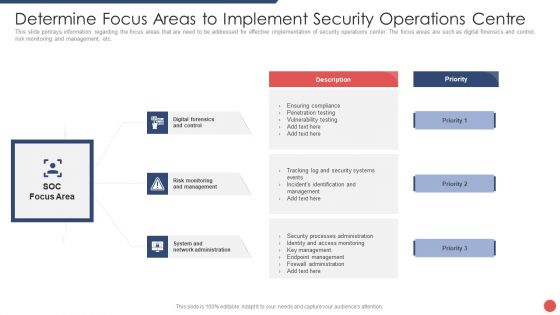
Security Functioning Centre Determine Focus Areas To Implement Security Operations Centre Demonstration PDF
This slide portrays information regarding the focus areas that are need to be addressed for effective implementation of security operations center. The focus areas are such as digital forensics and control, risk monitoring and management, etc. This is a security functioning centre determine focus areas to implement security operations centre demonstration pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like risk monitoring, management, system and network administration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Cloud Security Checklist Logging And Monitoring Cloud Computing Security IT Ppt Show Example PDF
This slide defines the importance of logging and monitoring activities on data in a network and how it could be beneficial in future analysis. This is a cloud security checklist logging and monitoring cloud computing security it ppt show example pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like evaluation, organization, policies, potential, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
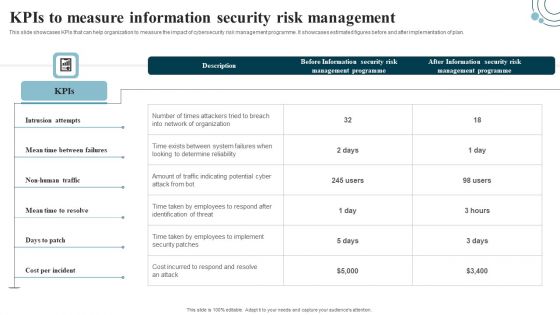
Developing IT Security Strategy Kpis To Measure Information Security Risk Management Graphics PDF
This slide showcases KPIs that can help organization to measure the impact of cybersecurity risk management programme. It showcases estimated figures before and after implementation of plan. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Developing IT Security Strategy Kpis To Measure Information Security Risk Management Graphics PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Developing IT Security Strategy Kpis To Measure Information Security Risk Management Graphics PDF today and make your presentation stand out from the rest.

Best Data Security Software Next Steps For Company Online Database Security Infographics PDF
Presenting this set of slides with name best data security software next steps for company online database security infographics pdf. This is a two stage process. The stages in this process are discuss the desired changes, accept the proposal, once we get the notification of your proposal acceptance, we will send you the separate copy of the signed contract for your record. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
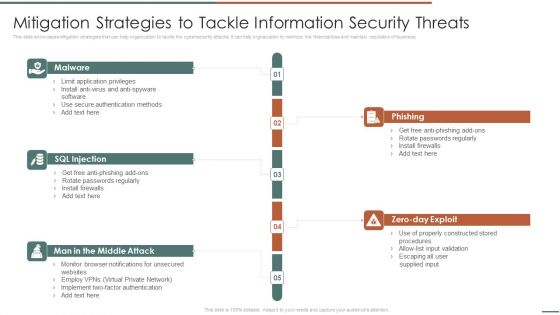
Information Security Risk Evaluation Mitigation Strategies To Tackle Information Security Threats Designs PDF
This slide showcases mitigation strategies that can help organization to tackle the cybersecurity attacks. It can help orgnaization to minimize the financial loss and maintain reputation of business.Presenting Information Security Risk Evaluation Mitigation Strategies To Tackle Information Security Threats Designs PDF to provide visual cues and insights. Share and navigate important information on fivestages that need your due attention. This template can be used to pitch topics like Phishing, Rotate Passwords, Install Firewalls. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security Information Technology Security Awareness Training For Staff Ppt Slide PDF
This slide represents the cybersecurity awareness training program for staff, including the name of the participants and what modules would be covered under training daily. Presenting it security information technology security awareness training for staff ppt slide pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like senior executives, developers, front line staff, it teams, project managers. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Mitigation Strategies To Tackle Information Security Threats Information Security Risk Administration Ideas PDF
This slide showcases mitigation strategies that can help organization to tackle the cybersecurity attacks. It can help organization to minimize the financial loss and maintain reputation of business.Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Mitigation Strategies To Tackle Information Security Threats Information Security Risk Administration Ideas PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Mitigation Strategies To Tackle Information Security Threats Information Security Risk Administration Ideas PDF.

Developing IT Security Strategy Mitigation Strategies To Tackle Information Security Sample PDF
This slide showcases mitigation strategies that can help organization to tackle the cybersecurity attacks. It can help organization to minimize the financial loss and maintain reputation of business. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Developing IT Security Strategy Mitigation Strategies To Tackle Information Security Sample PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Developing IT Security Strategy Mitigation Strategies To Tackle Information Security Sample PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers
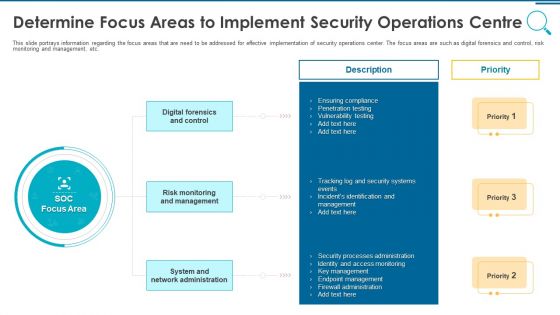
Information And Technology Security Operations Determine Focus Areas To Implement Security Operations Centre Download PDF
This slide portrays information regarding the focus areas that are need to be addressed for effective implementation of security operations center. The focus areas are such as digital forensics and control, risk monitoring and management, etc. This is a information and technology security operations determine focus areas to implement security operations centre download pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like digital forensics and control, risk monitoring and management, system and network administration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security And Process Integration Determine Focus Areas To Implement Security Operations Centre Sample PDF
This slide portrays information regarding the focus areas that are need to be addressed for effective implementation of security operations center. The focus areas are such as digital forensics and control, risk monitoring and management, etc. This is a security and process integration determine focus areas to implement security operations centre sample pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like digital forensics and control, risk monitoring and management, system and network administration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
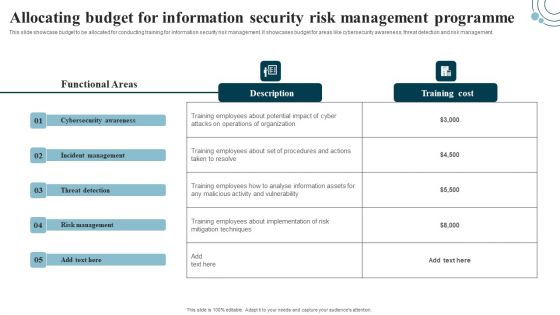
Developing IT Security Strategy Allocating Budget For Information Security Risk Background PDF
This slide showcase budget to be allocated for conducting training for information security risk management. It showcases budget for areas like cybersecurity awareness, threat detection and risk management. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Developing IT Security Strategy Allocating Budget For Information Security Risk Background PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Information Systems Security And Risk Management Plan Mitigation Strategies To Tackle Information Security Threats Information PDF
This slide showcases mitigation strategies that can help organization to tackle the cybersecurity attacks. It can help organization to minimize the financial loss and main reputation of business. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Information Systems Security And Risk Management Plan Mitigation Strategies To Tackle Information Security Threats Information PDF from Slidegeeks and deliver a wonderful presentation.
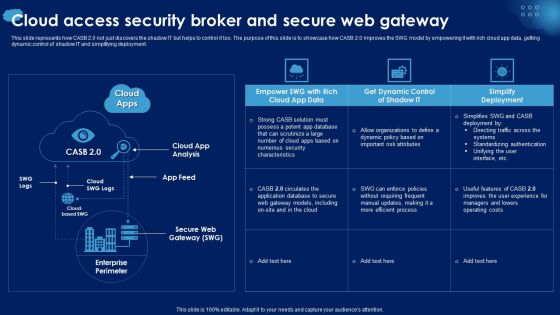
Cloud Access Security Broker And Secure Web Gateway Ppt PowerPoint Presentation Diagram Images PDF
This slide represents how CASB 2.0 not just discovers the shadow IT but helps to control it too. The purpose of this slide is to showcase how CASB 2.0 improves the SWG model by empowering it with rich cloud app data, getting dynamic control of shadow IT and simplifying deployment. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cloud Access Security Broker And Secure Web Gateway Ppt PowerPoint Presentation Diagram Images PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cloud Access Security Broker And Secure Web Gateway Ppt PowerPoint Presentation Diagram Images PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
Facebook Email Marketing Ppt PowerPoint Presentation File Background Image Cpb
This is a facebook email marketing ppt powerpoint presentation file background image cpb. This is a five stage process. The stages in this process are facebook email marketing.

Types Phishing Email Ppt PowerPoint Presentation Outline Background Image Cpb
Presenting this set of slides with name types phishing email ppt powerpoint presentation outline background image cpb. This is an editable Powerpoint five stages graphic that deals with topics like types phishing email to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

B2B Promotional Communication Techniques To Improve Brand Image Themes PDF
The following slides outline the business to business marketing communication strategies. It covers information about social media, email marketing, website and SEO. Presenting B2B Promotional Communication Techniques To Improve Brand Image Themes PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Social Media, Email Marketing, Website, SEO. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Most Effective Marketing Channels For Boosting Brand Image Topics PDF
This slide consists of most commonly used marketing channels used by marketers to target the audience. The channels opted by businesses are social media, email, blog website, influencer marketing, display ads, paid ads etc. Showcasing this set of slides titled Most Effective Marketing Channels For Boosting Brand Image Topics PDF. The topics addressed in these templates are Preference, Content Advertising, Collaborations. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Contact Details Ppt PowerPoint Presentation Ideas Background Image
This is a contact details ppt powerpoint presentation ideas background image. This is a three stage process. The stages in this process are email id contact details, business, management, strategy.

Marketing Strategy Ppt PowerPoint Presentation Model Background Image
This is a marketing strategy ppt powerpoint presentation model background image. This is a eight stage process. The stages in this process are social media, email marketing, marketing strategy, collaboration, blog.
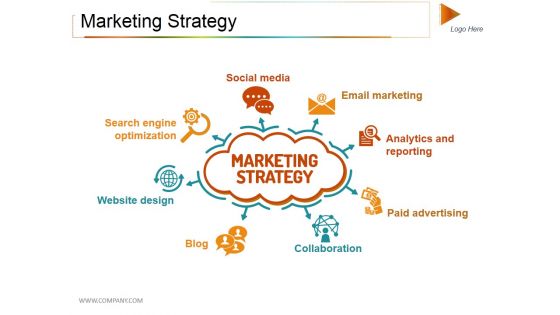
Marketing Strategy Ppt PowerPoint Presentation Professional Background Image
This is a marketing strategy ppt powerpoint presentation professional background image. This is a eight stage process. The stages in this process are social media, email marketing, collaboration, blog, website design.

Internet Advertising Steps Example Powerpoint Slide Background Image
This is a internet advertising steps example powerpoint slide background image. This is a eight stage process. The stages in this process are website and blog, social media, blog, email, relationships, analytics, forum, banner, internet advertising.

Active Incident Dashboard Ppt Powerpoint Slide Background Image
This is a active incident dashboard ppt powerpoint slide background image. This is a three stage process. The stages in this process are status, priority, aging, receivers by volume, renee, hssadmin, chris, administrator, admin, category, email, employee setup, equipment, general, literature, no category, breck fix, change management, general, active incident created this week, oldest active priority, active incident created this month, thursday.

Safety Breach Response Playbook Performing Cyber Training Exercises For Securing Diagrams PDF
Purpose of this slide is to address and perform various cyber training exercises in order to secure companys assets. Exercises covered are defense in depth, capture the flag etc. Slidegeeks is here to make your presentations a breeze with Safety Breach Response Playbook Performing Cyber Training Exercises For Securing Diagrams PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, youre sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether youre giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

IT Cyber Threat Prevention Technology Market Topics PDF
This slide provides the statistical data for IT security software user market to help business and organizations enhance process efficiency. Major security technology are authentication, IoT, Zero trust, Cloud, application security, etc. Pitch your topic with ease and precision using this IT Cyber Threat Prevention Technology Market Topics PDF. This layout presents information on Key Insights, Progressive Rate, Technology. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Cyber Safety Awareness Program Plan Ppt Icon Smartart PDF
This slide covers plan related to cyber security awareness. It includes timeline pertaining to preparation, detection, analysis, eradication, recover and post incident of a security lapse. Presenting Cyber Safety Awareness Program Plan Ppt Icon Smartart PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Post Inside, Eradicate and Recover, Detection, Analysis. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
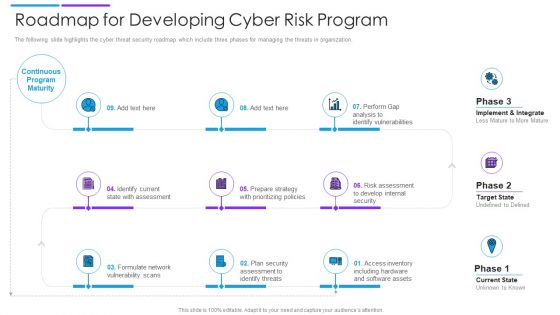
Roadmap For Developing Cyber Risk Program Download PDF
The following slide highlights the cyber threat security roadmap which include three phases for managing the threats in organization. Persuade your audience using this roadmap for developing cyber risk program download pdf. This PPT design covers nine stages, thus making it a great tool to use. It also caters to a variety of topics including internal security, software assets, identify threats. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Building Cyber Risk Prevention In Financial Services Sector Elements PDF
The slide showcases the steps to develop the cyber resiliency of financial services industry. It covers steps like secure by design, zero trust, third party cyber risk assessment, security awareness training and cyber insurance. Persuade your audience using this Building Cyber Risk Prevention In Financial Services Sector Elements PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Secure By Design, Zero Trust, Security Awareness Training. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Agenda Of Enhancing Cyber Safety With Vulnerability Administratio Professional PDF
This is a agenda of enhancing cyber safety with vulnerability administratio professional pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security intelligence, log management and compliance, provides security services. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Best Practices For Cyber Safety At Job Safety Infographics PDF
This slide covers the best practices for cyber safety at workplace which includes protecting the data, using strong password protection, connecting to the secure wi-fi, investing in security systems, etc. Presenting best practices for cyber safety at job safety infographics pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including protecting data, connect to secure wi fi, invest in security systems, strong password protection. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
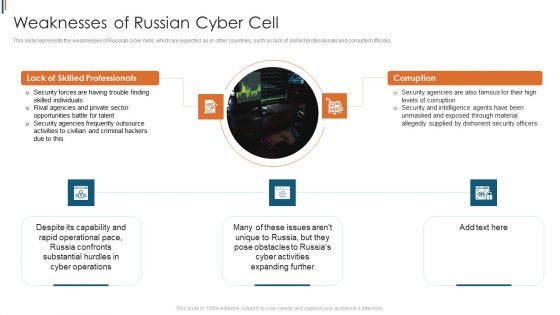
Ukraine Cyberwarfare Weaknesses Of Russian Cyber Cell Brochure Pdf
This slide represents the weaknesses of Russian cyber cells, which are expected as in other countries, such as lack of skilled professionals and corrupted officials. Presenting ukraine cyberwarfare weaknesses of russian cyber cell brochure pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like security forces are having trouble finding skilled individuals, rival agencies and private sector opportunities battle for talent, security agencies frequently outsource activities to civilian and criminal hackers due to this. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Sensing Components Of Cyber Physical Systems Ppt PowerPoint Presentation Diagram Images PDF
This slide depicts the sensing components of cyber security systems, including sensors, aggregators, actuators, and their operations and position on the architecture. Find highly impressive Sensing Components Of Cyber Physical Systems Ppt PowerPoint Presentation Diagram Images PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Sensing Components Of Cyber Physical Systems Ppt PowerPoint Presentation Diagram Images PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
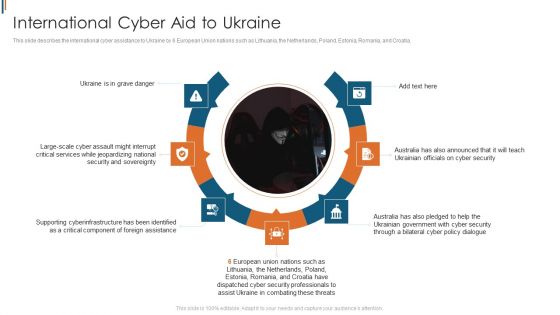
Ukraine Cyberwarfare International Cyber Aid To Ukraine Brochure Pdf
This slide describes the international cyber assistance to Ukraine by 6 European Union nations such as Lithuania, the Netherlands, Poland, Estonia, Romania, and Croatia. This is a ukraine cyberwarfare international cyber aid to ukraine brochure pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like ukraine is in grave danger, australia has also announced that it will teach ukrainian officials on cyber security, australia has also pledged to help the ukrainian government with cyber security through a bilateral cyber policy dialogue. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
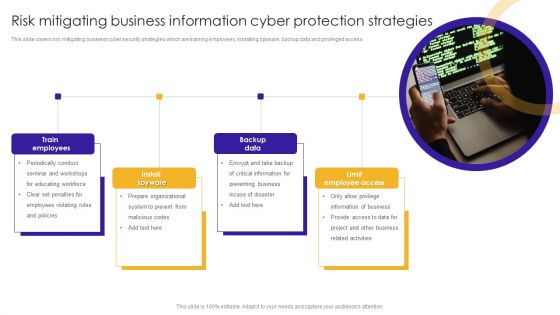
Risk Mitigating Business Information Cyber Protection Strategies Themes PDF
This slide covers risk mitigating business cyber security strategies which are training employees, installing spyware, backup data and privileged access.Presenting Risk Mitigating Business Information Cyber Protection Strategies Themes PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Train Employees, Information Business, Related Activities. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
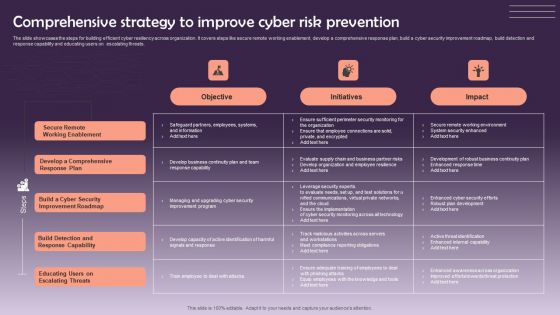
Comprehensive Strategy To Improve Cyber Risk Prevention Graphics PDF
The slide showcases the steps for building efficient cyber resiliency across organization. It covers steps like secure remote working enablement, develop a comprehensive response plan, build a cyber security improvement roadmap, build detection and response capability and educating users on escalating threats. Pitch your topic with ease and precision using this Comprehensive Strategy To Improve Cyber Risk Prevention Graphics PDF. This layout presents information on Objective, Initiatives, Impact. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Enhancing Cyber Safety With Vulnerability Administration SIEM Integrations Inspiration PDF
This is a enhancing cyber safety with vulnerability administration siem integrations inspiration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security events, network logs, applications and devices, it infrastructure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
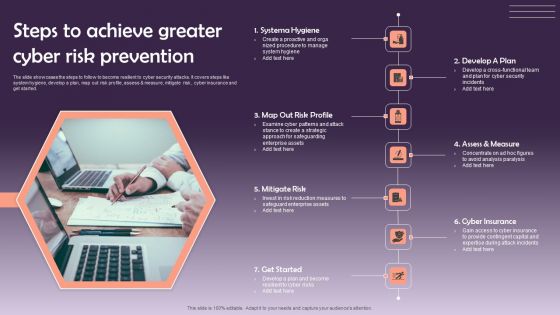
Steps To Achieve Greater Cyber Risk Prevention Infographics PDF
The slide showcases the steps to follow to become resilient to cyber security attacks. It covers steps like system hygiene, develop a plan, map out risk profile, assess and measure, mitigate risk, cyber insurance and get started. Presenting Steps To Achieve Greater Cyber Risk Prevention Infographics PDF to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including Systema Hygiene, Develop A Plan, Mitigate Risk. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
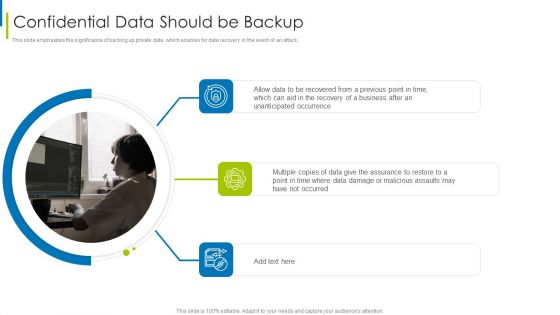
Cyber Terrorism Assault Confidential Data Should Be Backup Brochure PDF
This slide emphasizes the significance of backing up private data, which enables for data recovery in the event of an attack.Presenting cyber terrorism assault confidential data should be backup brochure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Cyber Security Assessment, Limited Access Privileges, Employee Training In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
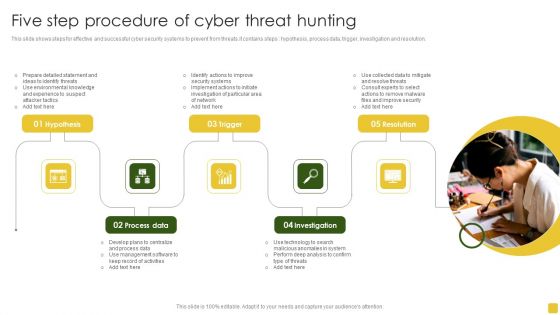
Five Step Procedure Of Cyber Threat Hunting Introduction PDF
This slide shows steps for effective and successful cyber security systems to prevent from threats.it contains steps hypothesis, process data, trigger, investigation and resolution. Persuade your audience using this Five Step Procedure Of Cyber Threat Hunting Introduction PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Prepare Detailed, Management Software, Management Software. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
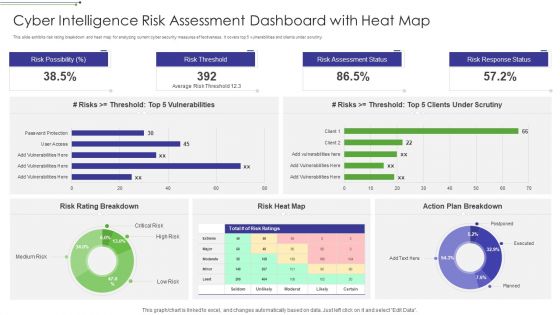
Cyber Intelligence Risk Assessment Dashboard With Heat Map Portrait PDF
This slide exhibits risk rating breakdown and heat map for analyzing current cyber security measures effectiveness. It covers top 5 vulnerabilities and clients under scrutiny. Pitch your topic with ease and precision using this Cyber Intelligence Risk Assessment Dashboard With Heat Map Portrait PDF This layout presents information on Risk Rating Breakdown, Action Plan Breakdown, Risk Possibility It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
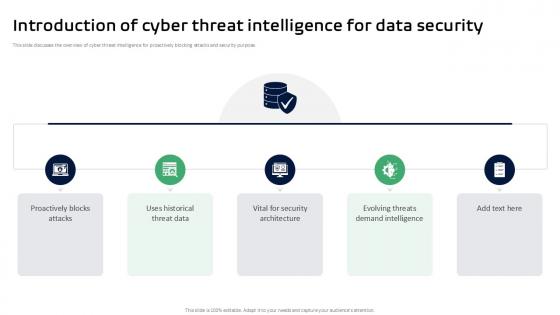
Introduction Of Cyber Threat Intelligence For Threat Intelligence Ppt Template
This slide discusses the overview of cyber threat intelligence for proactively blocking attacks and security purpose. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Introduction Of Cyber Threat Intelligence For Threat Intelligence Ppt Template was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Introduction Of Cyber Threat Intelligence For Threat Intelligence Ppt Template

Ways To Control Cyber Protection And Privacy Issues Diagrams PDF
The following slide illustrates some ways to monitor cybersecurity and privacy issues. It includes activities such as protecting CRM platform, keeping security system updated, modifying passwords regularly etc. Persuade your audience using this Ways To Control Cyber Protection And Privacy Issues Diagrams PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Change Passwords Regularly, Regular Backups, Protect CRM Platform. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
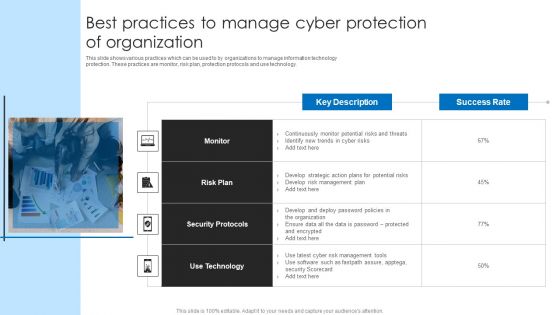
Best Practices To Manage Cyber Protection Of Organization Microsoft PDF
This slide shows various practices which can be used to by organizations to manage information technology protection. These practices are monitor, risk plan, protection protocols and use technology. Persuade your audience using this Best Practices To Manage Cyber Protection Of Organization Microsoft PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Risk Plan, Security Protocols, Technology. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
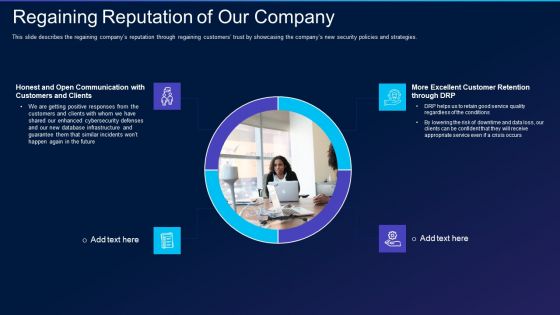
Cyber Exploitation IT Regaining Reputation Of Our Company Demonstration PDF
This slide describes the regaining companys reputation through regaining customers trust by showcasing the companys new security policies and strategies. This is a cyber exploitation it regaining reputation of our company demonstration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like regaining reputation of our company. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
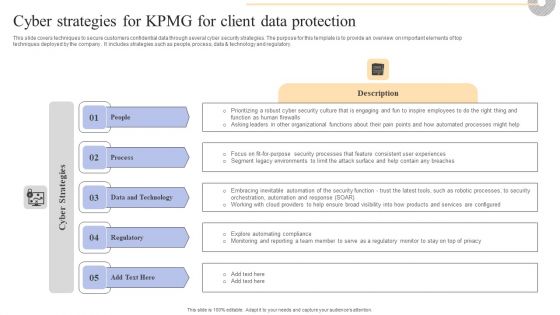
Cyber Strategies For KPMG For Client Data Protection Pictures PDF
This slide covers techniques to secure customers confidential data through several cyber security strategies. The purpose for this template is to provide an overview on important elements of top techniques deployed by the company . It includes strategies such as people, process, data and technology and regulatory. Boost your pitch with our creative Cyber Strategies For KPMG For Client Data Protection Pictures PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

4 Steps For Developing IT Security Plan Professional PDF
This slide represents 4 steps for developing cyber security strategy such as understanding cyber threats, assessing cyber security maturity, determining steps to improve cyber security program and documentation. Presenting 4 Steps For Developing IT Security Plan Professional PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Documenting Cyber Security Plan, Assessing Cyber Security Maturity, Organizations. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
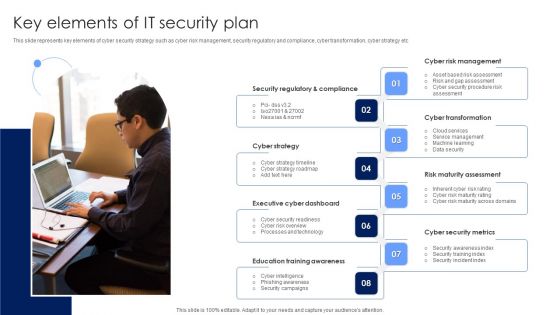
Key Elements Of IT Security Plan Background PDF
This slide represents key elements of cyber security strategy such as cyber risk management, security regulatory and compliance, cyber transformation, cyber strategy etc. Persuade your audience using this Key Elements Of IT Security Plan Background PDF. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Strategy, Executive Cyber Dashboard, Education Training Awareness. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Utilizing Cyber Technology For Change Process Consumer Insights Microsoft PDF
The needs and expectations of the modern consumer healthcare consumer in this example are rising with technological developments, the most important being anytime, anywhere access. Presenting utilizing cyber technology for change process consumer insights microsoft pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like security of personal data, reliable information online for health issues, gather health data through wearables and other technological devices, convenient, on the go access to health information, quick connection with healthcare services and doctors for care. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Global Cyber Terrorism Incidents On The Rise IT Checklist To Deal With Cyber Terrorism Threats Key Template PDF
This slide represents the checklist to deal with cyber-terrorism threats which involve 24 7 monitoring, employee training, keeping software updated. Presenting global cyber terrorism incidents on the rise it checklist to deal with cyber terrorism threats key template pdf to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like employee training, monitoring, cyber security assessment, incident response plan, limited access privileges. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Global Cyber Terrorism Incidents On The Rise IT Checklist To Deal With Cyber Terrorism Threats Infographics PDF
This slide represents the checklist to deal with cyber-terrorism threats which involve 24 7 monitoring, employee training, keeping software updated. This is a global cyber terrorism incidents on the rise it checklist to deal with cyber terrorism threats infographics pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employee training, monitoring, cyber security assessment, incident response plan, limited access privileges. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Blockchain Technology Applications For Cyber Threat Prevention Icons PDF
This slides represents various application of blockchain technology in enhancing cyber safety which helps to speed up data transfer procedures, offer secure transactions, and lower compliance expenses. Key components are IoT security, secure private messaging, etc. Presenting Blockchain Technology Applications For Cyber Threat Prevention Icons PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Prevention, Infrastructure, System . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Country Wise Security Strategies For Digital Terrorism Professional PDF
This slide shows various strategies adopted by different countries to eliminate threat of cyber attacks. It include various risk area covered such as Hostile cyber attacks, International Cyber Attacks etc. Presenting Country Wise Security Strategies For Digital Terrorism Professional PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including National Strategy, Cyber Security, International Cyber. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Picture Of Cyber Attack Warning Ppt PowerPoint Presentation Model Background Images PDF
Presenting this set of slides with name picture of cyber attack warning ppt powerpoint presentation model background images pdf. This is a three stage process. The stages in this process are picture of cyber attack warning. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
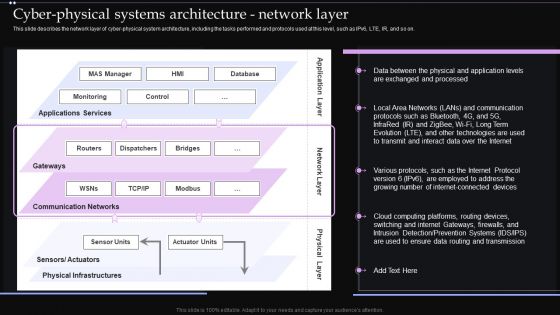
Cyber Physical Systems Architecture Network Layer Ppt PowerPoint Presentation Diagram Images PDF
This slide describes the network layer of cyber physical system architecture, including the tasks performed and protocols used at this level, such as IPv6, LTE, IR, and so on. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Cyber Physical Systems Architecture Network Layer Ppt PowerPoint Presentation Diagram Images PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
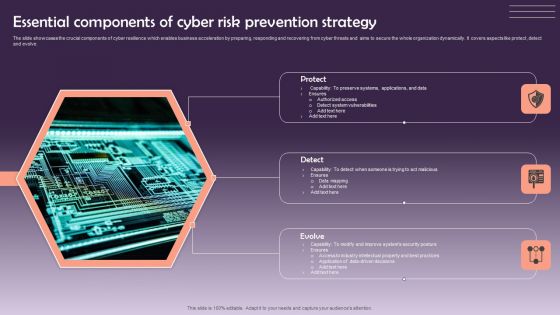
Essential Components Of Cyber Risk Prevention Strategy Information PDF
The slide showcases the crucial components of cyber resilience which enables business acceleration by preparing, responding and recovering from cyber threats and aims to secure the whole organization dynamically. It covers aspects like protect ,detect and evolve. Presenting Essential Components Of Cyber Risk Prevention Strategy Information PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Protect, Detect, Evolve. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Real Time Assessment Of Security Threats Ppt PowerPoint Presentation Complete Deck With Slides
This complete deck acts as a great communication tool. It helps you in conveying your business message with personalized sets of graphics, icons etc. Comprising a set of sixty five slides, this complete deck can help you persuade your audience. It also induces strategic thinking as it has been thoroughly researched and put together by our experts. Not only is it easily downloadable but also editable. The color, graphics, theme any component can be altered to fit your individual needs. So grab it now.

Data Integration Architecture To Manage Cyber Risk Pictures PDF
This slide showcases the structure to manage cybersecurity threats and risk of any organization. It includes steps such as identifying user with data access, protecting data accessibility, secure networks, install and updating antivirus, developing plan for managing disasters etc. Presenting Identify, Protect, Detect to dispense important information. This template comprises Five stages. It also presents valuable insights into the topics including Data Integration Architecture To Manage Cyber Risk Pictures PDF. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Crime Hackers In Powerpoint And Google Slides Cpb
Introducing our well-designed Cyber Crime Hackers In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Cyber Crime Hackers. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience.

Rsa Cyber Attack In Powerpoint And Google Slides Cpb
Introducing our well designed Rsa Cyber Attack In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Rsa Cyber Attack. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience.

Direct Cyber Attack In Powerpoint And Google Slides Cpb
Introducing our well-designed Direct Cyber Attack In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Direct Cyber Attack. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience.

Cyber Multiple Attack In Powerpoint And Google Slides Cpb
Introducing our well designed Cyber Multiple Attack In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Cyber Multiple Attack. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience.
Cyber Crime Growing Rate In Powerpoint And Google Slides Cpb
Presenting our innovatively-designed set of slides titled Cyber Crime Growing Rate In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Cyber Crime Growing Rate that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design.
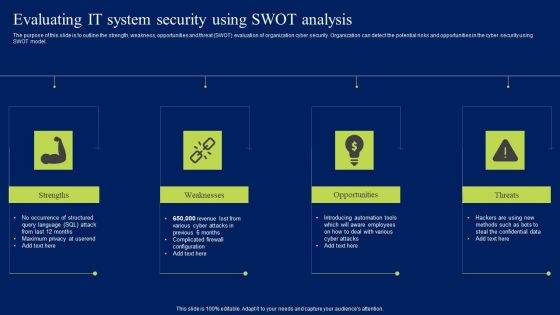
Evaluating IT System Security Using Swot Analysis Ppt Pictures Clipart Images PDF
The purpose of this slide is to outline the strength, weakness, opportunities and threat SWOT evaluation of organization cyber security. Organization can detect the potential risks and opportunities in the cyber security using SWOT model. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Evaluating IT System Security Using Swot Analysis Ppt Pictures Clipart Images PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Evaluating IT System Security Using Swot Analysis Ppt Pictures Clipart Images PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today

Comparison Of Various Cyber Protection Software Portrait PDF
This slide shows comparative analysis of various cyber protection tools which can be used by organizations for IT safety. It includes features, compatibility, price and ratings. Pitch your topic with ease and precision using this Comparison Of Various Cyber Protection Software Portrait PDF. This layout presents information on Compatibility, Price, Security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Maersk Cyber Attack In Powerpoint And Google Slides Cpb
Presenting our innovatively-designed set of slides titled Maersk Cyber Attack In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Maersk Cyber Attack that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design.

Table Of Contents Cyber Safety Incident Management Formats PDF
Presenting table of contents cyber safety incident management formats pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like ensuring financial assets security, leveraging workforce, budget assessment, impact assessment, dashboard . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Assessing Organizations Cyber Risk Prevention Level Template PDF
The slide showcases cyber resilience matrix to assess the level of organizations that excel at cyber resilience, but also align with the business strategy to achieve better business outcomes. It covers four levels business blockers, cyber champions, the vulnerable and cyber risk takers. Presenting Assessing Organizations Cyber Risk Prevention Level Template PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Cybersecurity Resilience, Cyber Champions. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Crime Hacking Technology Threats Ppt PowerPoint Presentation Layouts Example
Presenting this set of slides with name cyber crime hacking technology threats ppt powerpoint presentation layouts example. This is a one stage process. The stage in this process is cyber crime hacking technology threats. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Social Media Cyber Crime Ppt PowerPoint Presentation Ideas File Formats
Presenting this set of slides with name social media cyber crime ppt powerpoint presentation ideas file formats. This is a one stage process. The stage in this process is social media cyber crime. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Cyber Crime And War Strategies Icon Summary PDF
Presenting Cyber Crime And War Strategies Icon Summary PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Cyber, Crime, War Strategies Icon This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
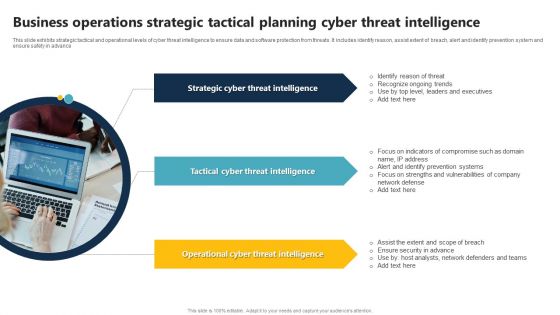
Business Operations Strategic Tactical Planning Cyber Threat Intelligence Summary PDF
This slide exhibits strategic tactical and operational levels of cyber threat intelligence to ensure data and software protection from threats. It includes identify reason, assist extent of breach, alert and identify prevention system and ensure safety in advance. Persuade your audience using this Business Operations Strategic Tactical Planning Cyber Threat Intelligence Summary PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Strategic Cyber Threat Intelligence, Tactical Cyber Threat Intelligence, Operational Cyber Threat Intelligence. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Attack Protection Ppt PowerPoint Presentation Model Inspiration Cpb Pdf
Presenting this set of slides with name cyber attack protection ppt powerpoint presentation model inspiration cpb pdf. This is an editable Powerpoint four stages graphic that deals with topics like cyber attack protection to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Cyber Threat Analysis Sample Diagram Presentation Visual Aids
This is a cyber threat analysis sample diagram presentation visual aids. This is a four stage process. The stages in this process are successful attack, system susceptibility, threat accessibility, threat capability.

Ways To Stop Cyber Attacks Ppt PowerPoint Presentation Inspiration Outline
Presenting this set of slides with name ways to stop cyber attacks ppt powerpoint presentation inspiration outline. This is a one stage process. The stage in this process is ways to stop cyber attacks. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Cyber Risk Icon Indicating Malware Attack Elements PDF
Presenting cyber risk icon indicating malware attack elements pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including cyber risk icon indicating malware attack. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Icon For Minimizing Online Risk And Cyber Attacks Mockup PDF
Presenting Icon For Minimizing Online Risk And Cyber Attacks Mockup PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Icon Minimizing, Online Risk, Cyber Attacks. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
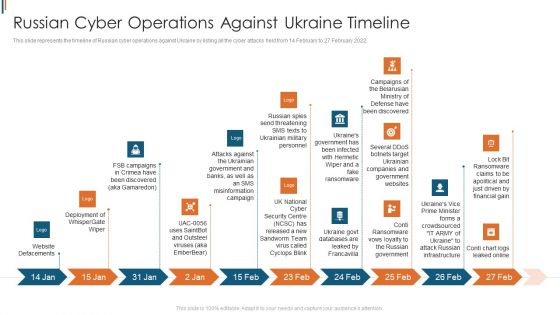
Ukraine Cyberwarfare Russian Cyber Operations Against Ukraine Timeline Portrait Pdf
This slide represents the timeline of Russian cyber operations against Ukraine by listing all the cyber attacks held from 14 February to 27 February 2022. Presenting ukraine cyberwarfare russian cyber operations against ukraine timeline portrait pdf to provide visual cues and insights. Share and navigate important information on ten stages that need your due attention. This template can be used to pitch topics like deployment of whispergate wiper, website defacements, campaigns of the belarusian ministry of defense have been discovered. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Two Factor Authentication Icon For Cyber Threat Prevention Background PDF
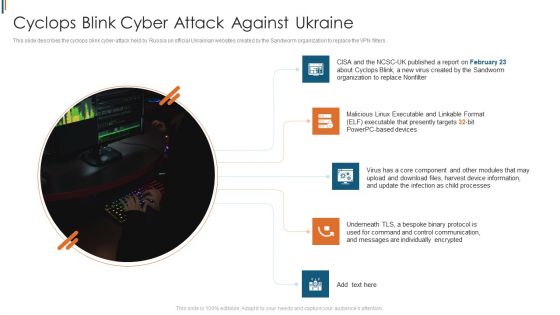
Ukraine Cyberwarfare Cyclops Blink Cyber Attack Against Ukraine Demonstration Pdf
This slide describes the cyclops blink cyber attack held by Russia on official Ukrainian websites created by the Sandworm organization to replace the VPN filters. Presenting ukraine cyberwarfare cyclops blink cyber attack against ukraine demonstration pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Virus has a core component and other modules that may upload and download files, harvest device information, and update the infection as child processes. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Major Statistics Of Cyber Phishing Scams And Attacks Designs PDF
Mentioned slide showcases key facts of cyber phishing attack. The facts covered in the slide are loss of confidential data, compromised accounts, ransomware attacks, financial loss and other malware attacks such as trojans. Pitch your topic with ease and precision using this major statistics of cyber phishing scams and attacks designs pdf. This layout presents information on major statistics of cyber phishing scams and attacks. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
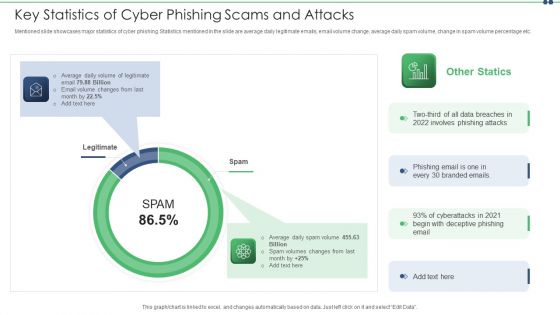
Key Statistics Of Cyber Phishing Scams And Attacks Pictures PDF
Mentioned slide showcases major statistics of cyber phishing. Statistics mentioned in the slide are average daily legitimate emails, email volume change, average daily spam volume, change in spam volume percentage etc. Persuade your audience using this key statistics of cyber phishing scams and attacks pictures pdf. This PPT design covers two stages, thus making it a great tool to use. It also caters to a variety of topics including average, email. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Preventing Cyber Crimes Vector Icon Ppt PowerPoint Presentation Styles Slides
Presenting this set of slides with name preventing cyber crimes vector icon ppt powerpoint presentation styles slides. This is a one stage process. The stages in this process are technology, social network, social engineering. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Data Safety Initiatives Communication Plan For Cyber Breaches Topics PDF
Mentioned slide portrays communication plan that company will use for effectively managing cyber breaches. Sections covered here are what to communicate, description, delivery method, frequency and responsible. Presenting data safety initiatives communication plan for cyber breaches topics pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like communicate, delivery method, frequency, responsible, product report. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Safety Incident Management Determine Threat Scenario Analysis Background PDF
This slide provides details regarding threat scenario assessment by understanding various phases of threat actor attack on victim. Presenting cyber safety incident management determine threat scenario analysis background pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like determine threat scenario analysis. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
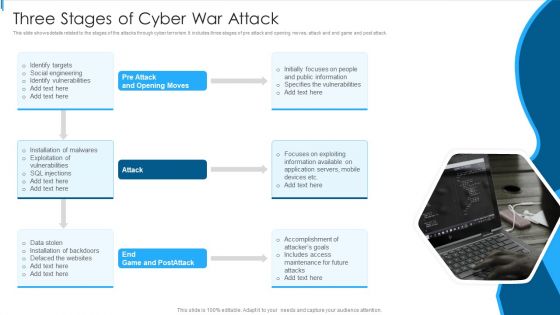
Three Stages Of Cyber War Attack Sample PDF
This slide shows details related to the stages of the attacks through cyber terrorism. It includes three stages of pre attack and opening moves, attack and end game and post attack.Persuade your audience using this Three Stages Of Cyber War Attack Sample PDF This PPT design covers one stage, thus making it a great tool to use. It also caters to a variety of topics including Public Information, Specifies Vulnerabilities, Focuses Exploiting Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

How Chatgpt Can Help In Preventing Cyber Crimes Slides PDF
This slide demonstrates the various applications of ChatGPT in the field of cybersecurity. The purpose of this slide is to explain how ChatGPT can help in predicting and avoiding cyber crimes. These include threat intelligence, anomaly detection, predictive analytics, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download How Chatgpt Can Help In Preventing Cyber Crimes Slides PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
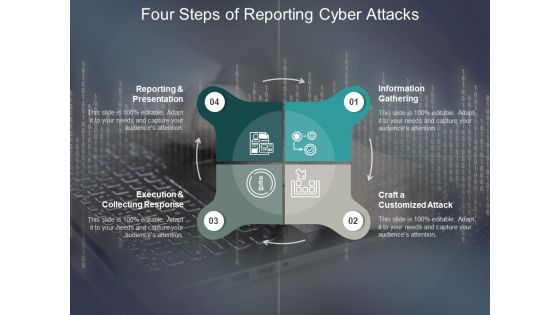
Four Steps Of Reporting Cyber Attacks Ppt PowerPoint Presentation Guidelines
Presenting this set of slides with name four steps of reporting cyber attacks ppt powerpoint presentation guidelines. This is a four stage process. The stages in this process are technology, social network, social engineering. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Exploitation IT Email Prevention Guidelines For Employees Formats PDF
This slide depicts the email prevention guidelines for employees, including spam filters and multi-factor authentication for email login credentials. Presenting cyber exploitation it email prevention guidelines for employees formats pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like usage of a spam filter, usage of mfa. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
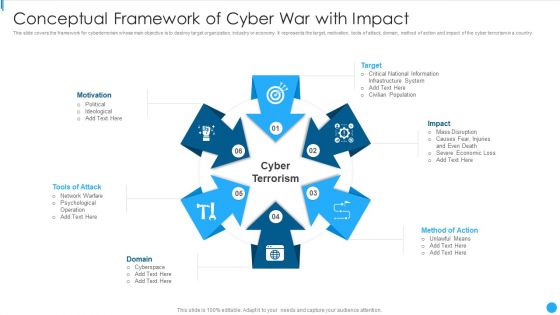
Conceptual Framework Of Cyber War With Impact Demonstration PDF
This slide covers the framework for cyberterrorism whose main objective is to destroy target organization, industry or economy. It represents the target, motivation, tools of attack, domain, method of action and impact of the cyber terrorism in a country.Presenting Conceptual Framework Of Cyber War With Impact Demonstration PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including National Information, Infrastructure System, Civilian Population This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
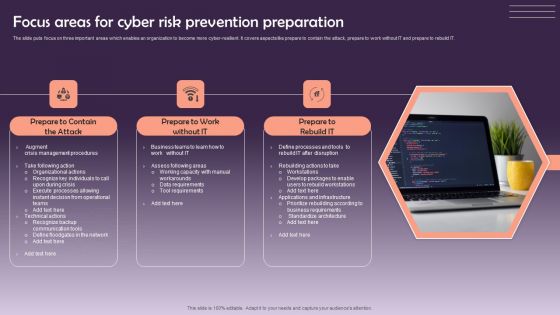
Focus Areas For Cyber Risk Prevention Preparation Pictures PDF
The slide puts focus on three important areas which enables an organization to become more cyber-resilient. It covers aspects like prepare to contain the attack, prepare to work without IT and prepare to rebuild IT. Persuade your audience using this Focus Areas For Cyber Risk Prevention Preparation Pictures PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Prepare To Contain, Prepare To Work, Prepare To Rebuild. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
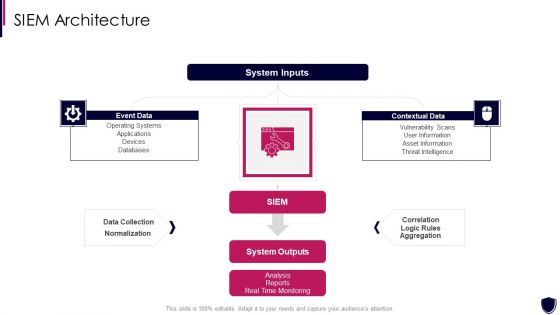
Enhancing Cyber Safety With Vulnerability Administration SIEM Architecture Information PDF
Presenting enhancing cyber safety with vulnerability administration siem architecture information pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like event data, contextual data, system inputs, system outputs, data collection. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
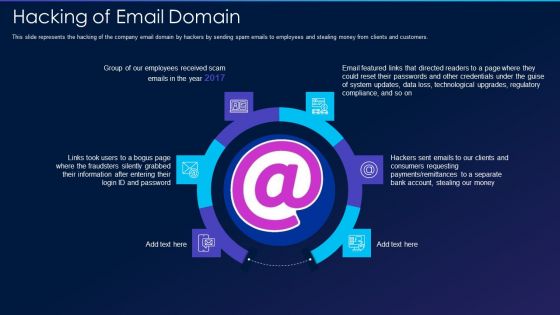
Cyber Exploitation IT Hacking Of Email Domain Professional PDF
This slide represents the hacking of the company email domain by hackers by sending spam emails to employees and stealing money from clients and customers. Presenting cyber exploitation it hacking of email domain professional pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like hacking of email domain. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Five Year Cyber Information Safety Career Growth Roadmap Background
We present our five year cyber information safety career growth roadmap background. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched five year cyber information safety career growth roadmap background in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
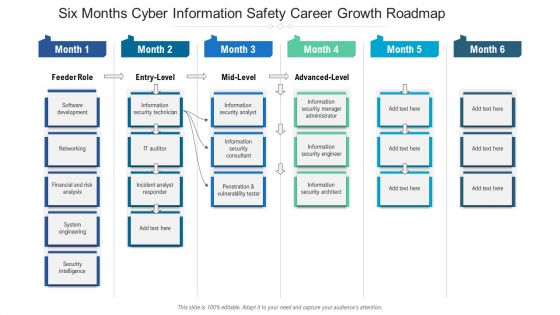
Six Months Cyber Information Safety Career Growth Roadmap Portrait
We present our six months cyber information safety career growth roadmap portrait. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched six months cyber information safety career growth roadmap portrait in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
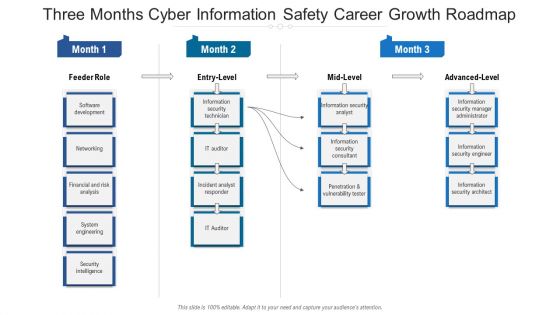
Three Months Cyber Information Safety Career Growth Roadmap Sample
We present our three months cyber information safety career growth roadmap sample. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched three months cyber information safety career growth roadmap sample in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Agenda For Russian Cyber Attacks On Ukraine Summary PDF
This is a agenda for russian cyber attacks on ukraine summary pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like technical, analysis, websites, globally. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Exploitation IT Is Ethical Hacking Legal Inspiration PDF
This slide shows the legality of ethical hacking, how ethical hackers work official permission, and companies hire them to protect their networks and computer systems from malicious attacks. Presenting cyber exploitation it is ethical hacking legal inspiration pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like is ethical hacking legal. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
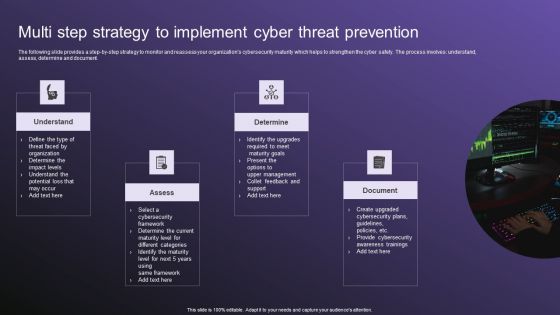
Multi Step Strategy To Implement Cyber Threat Prevention Guidelines PDF
The following slide provides a step by step strategy to monitor and reassess your organizations cybersecurity maturity which helps to strengthen the cyber safety. The process involves understand, assess, determine and document. Persuade your audience using this Multi Step Strategy To Implement Cyber Threat Prevention Guidelines PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Determine, Document, Assess. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

 Home
Home