Cyber Governance

Russian Cyber Attacks On Ukraine IT Impact Of Defacement Attacks Portrait PDF
This slide shows the impact of defacement attacks and fake news on the public, and Meta has banned Russian media on its platforms, and Russia has restricted access to Facebook. This is a russian cyber attacks on ukraine it impact of defacement attacks portrait pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information, fundamental, method, material, social media. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Russian Cyber Attacks On Ukraine IT Continued Impact Of Ongoing Microsoft PDF
This slide shows the continued impact of ongoing cyberattacks on Ukrainian internet providers and how these cyberattacks are causing internet outages throughout the country. This is a russian cyber attacks on ukraine it continued impact of ongoing microsoft pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like sources, service, network, internet. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Intelligent Computing System Statistics Of The CPS Provider Company Download PDF
This slide represents the strengths of the CPS company, and it includes the total amount of annual employee donations, volunteer hours, community ambassadors, and 24 into 7 support. Presenting Cyber Intelligent Computing System Statistics Of The CPS Provider Company Download PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Technologies, Market Trends, Affordable Pricing. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Automation Framework Enterprise Network IT Security Automation Background PDF
This slide highlights the network security automation which includes orchestrating network security, optimizing network security infrastructure, security policy automation and integration network with DevOps. Boost your pitch with our creative Cyber Security Automation Framework Enterprise Network IT Security Automation Background PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Cyber Security Automation Framework Right Time To Add Automation In Security Microsoft PDF
This slide depicts that what is the right time to invest in security automation it showcases failed human insights high time for resolution, high security breaches, no additional budget to hire security team. Want to ace your presentation in front of a live audience Our Cyber Security Automation Framework Right Time To Add Automation In Security Microsoft PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Cyber Security Automation Framework Security Processes That Cant Be Automated Topics PDF
The following slide highlights the three processes of the security which cannot be automated which includes threat modeling, penetration testing and bug bounty program. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Cyber Security Automation Framework Security Processes That Cant Be Automated Topics PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Table Of Contents For Series Of Cyber Security Attacks Against Ukraine 2022 Website Template PDF
Retrieve professionally designed Table Of Contents For Series Of Cyber Security Attacks Against Ukraine 2022 Website Template PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Table Of Contents Series Of Cyber Security Attacks Against Ukraine 2022 Elements PDF
Slidegeeks has constructed Table Of Contents Series Of Cyber Security Attacks Against Ukraine 2022 Elements PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

Handling Cyber Threats Digital Era Defining Business Priorities To Ensure Ppt Gallery Brochure PDF
This slide illustrates the key business priorities of the organization such as efficient risk management, standardized incident management process to ensure information security. Presenting handling cyber threats digital era defining business priorities to ensure ppt gallery brochure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like efficient risk management, standardized incident management process, transparent communication. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Most Effective It Security Tools For Protection Against Insider Threat In Cyber Security Inspiration PDF
This slide shows most effective IT security tools for protection against insider threats. It provides information about data loss prevention DLP, user and entity behavior UEBA, identity and access management IAM and security information and event management SIEM. Persuade your audience using this Most Effective It Security Tools For Protection Against Insider Threat In Cyber Security Inspiration PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Data Loss Prevention, Identity And Access, Management. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Tools Diagrams PDF
This slide provides information about some of the best security monitoring tools that are available with the security monitoring manager and what tool is selected by the security monitoring manager based on tool implementation costs, tool implementation time etc. Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring tools diagrams pdf bundle. Topics like cybersecurity monitoring tools to be implemented can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
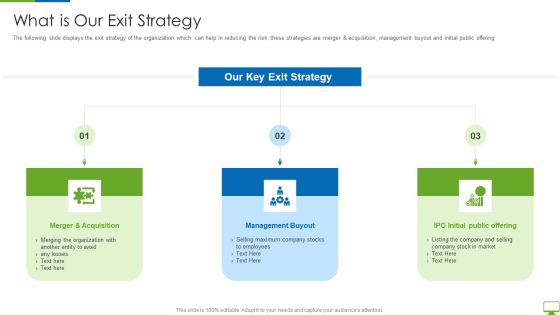
Cyber Network Simulation Platform Capital Funding Pitch Deck What Is Our Exit Strategy Guidelines PDF
The following slide displays the exit strategy of the organization which can help in reducing the risk, these strategies are merger and acquisition, management buyout and initial public offering Presenting cyber network simulation platform capital funding pitch deck what is our exit strategy guidelines pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like merger and acquisition, management buyout, initial public offering In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Mitigation Techniques To Reduce Insider Threat In Cyber Security Rules PDF
This slide shows mitigation techniques for reduction of insider threats. It provides information such as precise data managed, user access reduction and maintaining vigilance. Presenting Mitigation Techniques To Reduce Insider Threat In Cyber Security Rules PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Manage Data Precisely, Limit User Access, Maintain Vigilance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Month Wise Cyber Safety Awareness Training Program Ppt Styles Display PDF
This slide covers month wise security awareness schedule for users depending on requirement. It includes elements such as deployment and baseline testing, SAT, target testing, management and incident reporting. Showcasing this set of slides titled Month Wise Cyber Safety Awareness Training Program Ppt Styles Display PDF. The topics addressed in these templates are Security Awareness Training, Targeted Testing, Management And Reporting. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Training Frequency For Cyber Safety Awareness Program Ppt Pictures Graphics PDF
This slide covers frequency of training to be provided as per prescribed format. It includes elements such as clicking suspicious links, use of simple passwords, workstation security management, public network management, etc. as per multiple time duration. Showcasing this set of slides titled Training Frequency For Cyber Safety Awareness Program Ppt Pictures Graphics PDF. The topics addressed in these templates are Training Included, Once Per Month, Frequency Training. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Security Automation Framework Unified Platform Integration For Security Automation Template PDF
This slide highlights the unifies platform integration for security automation which includes firewalls, intrusion prevention system, security information and event management and privileged access management. Present like a pro with Cyber Security Automation Framework Unified Platform Integration For Security Automation Template PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Analysis Brochure PDF
This slide provides information about the ninth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Review and Risk Analysis. Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring analysis brochure pdf bundle. Topics like cybersecurity monitoring plan steps in detail review and risk analysis can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Timing Clipart PDF
This slide provides information about the seventh step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Providing Resilient and Synchronized Timing. Deliver and pitch your topic in the best possible manner with this continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring timing clipart pdf. Use them to share invaluable insights on cybersecurity monitoring plan steps in detail providing resilient and synchronized timing and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Measures And Ways To Mitigate Template PDF
This slide provides information about the ways and measures through which the company and security monitoring managers can overcome the problems and issues related to Security Monitoring. Deliver and pitch your topic in the best possible manner with this continuous development evaluation plan eliminate cyber attacks measures and ways to mitigate template pdf. Use them to share invaluable insights on malware attacks, pnishing attacks, ransomware and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Network Simulation Platform Capital Funding Pitch Deck Our Key Team Members Background PDF
Purpose of the following slide is to show the team management of the organization as it displays the details of the team members such as name, designation image etc.This is a cyber network simulation platform capital funding pitch deck our key team members background pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like our key team members You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Cyber Network Simulation Platform Capital Funding Pitch Deck Providing An Insight Topics PDF
Purpose of the following slide is to show the team management of the organization as it displays the details of the team members such as name, designation image etc.Presenting cyber network simulation platform capital funding pitch deck providing an insight topics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like providing an insight into our team In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Handling Cyber Threats Digital Era Information Security Program Values To Business Ppt Slides Background Designs PDF
Following slide displays the major program values to companys business. Values here are divided in two areas namely detection and response and attack surface management. This is a handling cyber threats digital era information security program values to business ppt slides background designs pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information security program values to business. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Due Diligence Procedure With Risk Sensing And Profiling Topics PDF
The slide communicates key activities a buyer should consider for conducting an effective virtual due diligence. These tasks are risk sensing, expert discussion, external data recovery, penetration testing, evidence collection and review and risk profiling. Presenting Cyber Due Diligence Procedure With Risk Sensing And Profiling Topics PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Risk Sensing, Risk Profiling, Management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Insider Threat In Cyber Security User Tracking Sheet With Impact Assessment Inspiration PDF
This slide shows user tracking sheet for insider threat with impact assessment. It provides details such as user behavior, indicator type, impact on security information and event manage SIEM, impact on interference framework, etc. Showcasing this set of slides titled Insider Threat In Cyber Security User Tracking Sheet With Impact Assessment Inspiration PDF. The topics addressed in these templates are Indicator Type, Impact On SIEM, Interference Framework. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Key Initiatives To Detect Insider Threat In Cyber Security Designs PDF
This slide shows best practices for detecting insider threats. It provides information such as heavy screening of new hires, apply user access management, conduct security awareness training, monitor employee behavior, etc. Presenting Key Initiatives To Detect Insider Threat In Cyber Security Designs PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Screen Carefully, Secure Access, Conduct Training. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Incident Escalation Response Flowchart Ppt PowerPoint Presentation File Infographic Template PDF
The following slide depicts the incident response chart to determine actions to be taken to escalate issue and manage security. It includes elements such as incident identification, informing security team, performing initial analysis, communicating to key members etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Cyber Incident Escalation Response Flowchart Ppt PowerPoint Presentation File Infographic Template PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Managing Cyber Security Incident Ppt PowerPoint Presentation Complete Deck With Slides
This Managing Cyber Security Incident Ppt PowerPoint Presentation Complete Deck With Slides acts as backup support for your ideas, vision, thoughts, etc. Use it to present a thorough understanding of the topic. This PPT slideshow can be utilized for both in-house and outside presentations depending upon your needs and business demands. Entailing twenty slides with a consistent design and theme, this template will make a solid use case. As it is intuitively designed, it suits every business vertical and industry. All you have to do is make a few tweaks in the content or any other component to design unique presentations. The biggest advantage of this complete deck is that it can be personalized multiple times once downloaded. The color, design, shapes, and other elements are free to modify to add personal touches. You can also insert your logo design in this PPT layout. Therefore a well-thought and crafted presentation can be delivered with ease and precision by downloading this Managing Cyber Security Incident Ppt PowerPoint Presentation Complete Deck With Slides PPT slideshow.

Deploying Cyber Security Incident Response Administration Ppt PowerPoint Presentation Complete Deck With Slides
Starting a presentation on business is a decision to make. As you think about it, you realize that everything is a decision. Our Deploying Cyber Security Incident Response Administration Ppt PowerPoint Presentation Complete Deck With Slides will make all your business tasks and decisions a bit easier, with its emphasis on planning. The sixty nine slide complete deck allows you to present the daily challenges of business in your own way to your team, key stakeholders, and external vendors etc. With each slide being 100 percent editable and customizable, you may decide to fiddle around with the design or the content ready nature to arrive at your own, presentation on a topic of your choosing. Download now.

Deploying Cyber Security Incident Response Administration Benefits Of Implementing Formats PDF
This slide represents the advantages of implementing a software which protects web applications from variety of application layer attacks. It includes key benefits of implementing web application firewall such as defense, fights vulnerabilities etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Deploying Cyber Security Incident Response Administration Benefits Of Implementing Formats PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Deploying Cyber Security Incident Response Administration Common Sources Of Precursors Diagrams PDF
This slide represents the common sources of signs which indicates that an incident may occur in the future. It includes details related to common sources of precursors and indicators such as IDPSs, SIEMs, network device logs etc. This modern and well arranged Deploying Cyber Security Incident Response Administration Common Sources Of Precursors Diagrams PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Cyber Risks And Incident Response Playbook Ppt PowerPoint Presentation Complete Deck With Slides
This Cyber Risks And Incident Response Playbook Ppt PowerPoint Presentation Complete Deck With Slides is a primer on how to capitalize on business opportunities through planning, innovation, and market intelligence. The content-ready format of the complete deck will make your job as a decision-maker a lot easier. Use this ready-made PowerPoint Template to help you outline an extensive and legible plan to capture markets and grow your company on the right path, at an exponential pace. What is even more amazing is that this presentation is completely editable and 100 percent customizable. This fifity slide complete deck helps you impress a roomful of people with your expertise in business and even presentation. Craft such a professional and appealing presentation for that amazing recall value. Download now.
Operational Risk Assessment And Management Plan Enterprise Cyber Risk Management Dashboard Icons PDF
This slide represents dashboard representing details related to management of strategic risks in the organization. It includes details related to risk rating breakdown, risk heat map, top 5 vulnerabilities etc. Slidegeeks is here to make your presentations a breeze with Operational Risk Assessment And Management Plan Enterprise Cyber Risk Management Dashboard Icons PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Organizations Risk Management And IT Security Prioritized Cyber Security Threats With Risk Mitigation Plan Demonstration PDF
This slide highlights the cyber security threats with key risks and their mitigation plan and owner with risk reduction timeline. Are you searching for a Organizations Risk Management And IT Security Risk Assessment Table With Actions And Escalation Level Background PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Organizations Risk Management And IT Security Risk Assessment Table With Actions And Escalation Level Background PDF from Slidegeeks today.

Cyber Risks And Incident Response Playbook Real Time Incident Management Dashboard Guidelines PDF
Following slide illustrate KPI dashboard that can be used by organizations to track real time incident data. KPIs covered are number of tickets, average resolution time per customer, incidents registered per month. This Cyber Risks And Incident Response Playbook Real Time Incident Management Dashboard Guidelines PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Plan Slides PDF
This slide provides information about the eighth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Aligning the Incident Management Policies and Plan. This is a continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring plan slides pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail aligning the incident management policies and plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Way To Overcome Security Monitoring Themes PDF
This slide provides information about the way that the company and security monitoring manager must choose in order to solve the challenge problem related to Malware Attacks and other potential security monitoring challenges. The solution is to set up an advanced Cybersecurity Monitoring Plan in place with the help of a set series of steps mentioned in the slide. This is a continuous development evaluation plan eliminate cyber attacks way to overcome security monitoring themes pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like monitoring, systems, management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Activity Structure PDF
This slide provides information about the fourth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Monitoring User Activity. This is a continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring activity structure pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail monitoring user activity. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Apability Inspiration PDF
This slide provides information about the sixth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Setting up a Centralized Collection and Analysis Capability. This is a continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring apability inspiration pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail setting up a centralized collection and analysis capability. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Policies Inspiration PDF
This slide provides information about the first and the foremost step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Establishing a Security Monitoring Strategy and Supporting Policies. Presenting continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring policies inspiration pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like cybersecurity monitoring plan steps in detail establish a security monitoring strategy and supporting policies. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring System Formats PDF
This slide provides information about the fifth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Fine Tune Monitoring System. This is a continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring system formats pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail fine tune monitoring system. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Traffic Sample PDF
This slide provides information about the third step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Monitoring Network Traffic. This is a continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring traffic sample pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail monitoring network traffic. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security Department Cases Action Plan Response Report Ppt PowerPoint Presentation File Layout PDF
This slide highlights tracking sheet of security incidents occurred in several departments in an organization. The purpose of this template is to provide information to the management about security breaches in the company. It includes elements such as number of incidents, cost per incident, team responsiveness rates, status of action taken, etc. Pitch your topic with ease and precision using this Cyber Security Department Cases Action Plan Response Report Ppt PowerPoint Presentation File Layout PDF. This layout presents information on Key Components, Cost Per Incident, Team Responsiveness. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

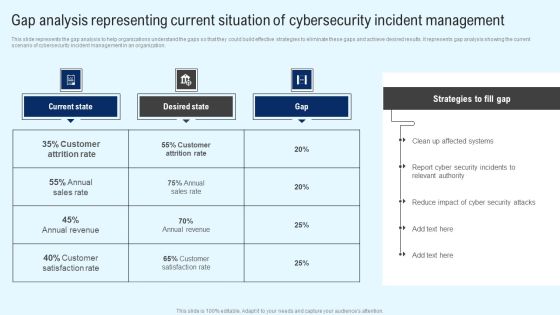
CYBER Security Breache Response Strategy Gap Analysis Representing Current Situation Cybersecurity Incident Professional PDF
This slide represents the gap analysis to help organizations understand the gaps so that they could build effective strategies to eliminate these gaps and achieve desired results. It represents gap analysis showing the current scenario of cybersecurity incident management in an organization. Slidegeeks has constructed CYBER Security Breache Response Strategy Gap Analysis Representing Current Situation Cybersecurity Incident Professional PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.
Implementing Cyber Security Incident Gap Analysis Representing Current Situation Ideas PDF
This slide represents the gap analysis to help organizations understand the gaps so that they could build effective strategies to eliminate these gaps and achieve desired results. It represents gap analysis showing the current scenario of cybersecurity incident management in an organization. Retrieve professionally designed Implementing Cyber Security Incident Gap Analysis Representing Current Situation Ideas PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Cyber Security Administration In Organization Ppt PowerPoint Presentation Complete Deck With Slides
This complete presentation has PPT slides on wide range of topics highlighting the core areas of your business needs. It has professionally designed templates with relevant visuals and subject driven content. This presentation deck has total of sixty eight slides. Get access to the customizable templates. Our designers have created editable templates for your convenience. You can edit the colour, text and font size as per your need. You can add or delete the content if required. You are just a click to away to have this ready made presentation. Click the download button now.

Enhancing Cyber Safety With Vulnerability Administration Ppt PowerPoint Presentation Complete Deck With Slides
This complete deck acts as a great communication tool. It helps you in conveying your business message with personalized sets of graphics, icons etc. Comprising a set of sixty one slides, this complete deck can help you persuade your audience. It also induces strategic thinking as it has been thoroughly researched and put together by our experts. Not only is it easily downloadable but also editable. The color, graphics, theme any component can be altered to fit your individual needs. So grab it now.
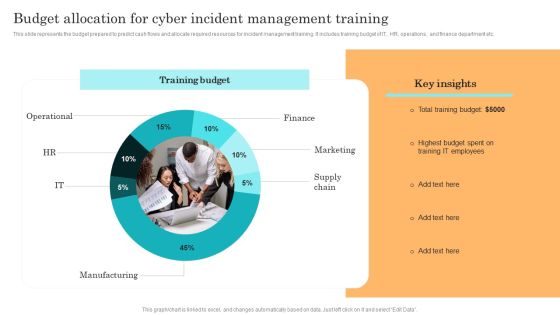
Incident Response Techniques Deployement Budget Allocation For Cyber Incident Management Training Rules PDF
This slide represents the budget prepared to predict cash flows and allocate required resources for incident management training. It includes training budget of IT, HR, operations, and finance department etc. Boost your pitch with our creative Incident Response Techniques Deployement Benefits Of Implementing Web Application Firewall Brochure PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Cyber Security Risk Management Plan Ppt PowerPoint Presentation Complete Deck With Slides
This complete deck acts as a great communication tool. It helps you in conveying your business message with personalized sets of graphics, icons etc. Comprising a set of fifty six slides, this complete deck can help you persuade your audience. It also induces strategic thinking as it has been thoroughly researched and put together by our experts. Not only is it easily downloadable but also editable. The color, graphics, theme any component can be altered to fit your individual needs. So grab it now.

Series Of Cyber Security Attacks Against Ukraine 2022 Germany Asks To Avoid Russias Kaspersky Antivirus Tool Diagrams PDF
This slide depicts the official announcement to avoid russias kaspersky antivirus tool by german officials as kaspersky has been accused of working for the russian government. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Series Of Cyber Security Attacks Series Of Cyber Security Attacks Against Ukraine 2022 Germany Asks To Avoid Russias Kaspersky Antivirus Tool Diagrams PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Series Of Cyber Security Attacks Series Of Cyber Security Attacks Against Ukraine 2022 Germany Asks To Avoid Russias Kaspersky Antivirus Tool Diagrams PDF today and make your presentation stand out from the rest.

Building An IT Strategy Plan For Business Expansion Risk Management Plan To Manage Cyber Threats Professional PDF
This slide provides information regarding risk management plan to monitor cyber threats including details about threat, vulnerability, asset, impact, likelihood, risk and control initiatives. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Building An IT Strategy Plan For Business Expansion Risk Management Plan To Manage Cyber Threats Professional PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Building An IT Strategy Plan For Business Expansion Risk Management Plan To Manage Cyber Threats Professional PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Information Systems Security And Risk Management Plan Cyber Attacks Faced By Organization In Previous Financial Year Graphics PDF
This slide showcases information security attacks faced by organization in past financial year. It can help company to assess different type of cyber attacks and formulate strategies to tackle them. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Information Systems Security And Risk Management Plan Cyber Attacks Faced By Organization In Previous Financial Year Graphics PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Implementing Cybersecurity Awareness Program To Prevent Attacks Recognizing The Cyber Security Gaps Faced By Key Elements PDF
The purpose of this slide is to outline the different cyber security gaps which are faced by employees, line and senior managers. Information covered in this slide is related to ransomware, password attack, crypto-jacking, IoT-based attack, malware etc. Find a pre designed and impeccable Implementing Cybersecurity Awareness Program To Prevent Attacks Recognizing The Cyber Security Gaps Faced By Key Elements PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Series Of Cyber Security Attacks Against Ukraine 2022 Hacker Group Anonymous Has Waged A Cyberwar Against Russia Summary PDF
This slide depicts the anonymous organization and how they have started a cyberwar against russia by gathering worldwide hackers through twitter. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Series Of Cyber Security Attacks Against Ukraine 2022 Hacker Group Anonymous Has Waged A Cyberwar Against Russia Summary PDF can be your best option for delivering a presentation. Represent everything in detail using Series Of Cyber Security Attacks Against Ukraine 2022 Hacker Group Anonymous Has Waged A Cyberwar Against Russia Summary PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Series Of Cyber Security Attacks Against Ukraine 2022 Us Is Unmasking Russian Hackers Faster Than Ever Guidelines PDF
This slide represents the rapid announcements made by the united states about russian cyberattacks against ukraine within the 48 hours of the cyberwar. Explore a selection of the finest Series Of Cyber Security Attacks Against Ukraine 2022 Us Is Unmasking Russian Hackers Faster Than Ever Guidelines PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Series Of Cyber Security Atta to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Agenda For Cyber Security And Phishing Awareness Training Hacking Prevention Awareness Training For IT Security Sample PDF
Presenting agenda for cyber security and phishing awareness training hacking prevention awareness training for it security sample pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like safeguard, integrity, cybersecurity, training. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Series Of Cyber Security Attacks Against Ukraine 2022 Steps To Prepare For Cyberattacks By Russia Microsoft PDF
This slide represents the steps to take right now to prepare for cyberattacks by russia, including access exposure, minimizing attack surface, executing the basics, and so on. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Series Of Cyber Security Attacks Against Ukraine 2022 Steps To Prepare For Cyberattacks By Russia Microsoft PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Global Cyber Terrorism Incidents On The Rise IT How To Prevent Ddos Attacks In The Company Designs PDF
This slide represents the ways to prevent DDoS attacks in the company, which include network monitoring, updating security elements, etc. Presenting global cyber terrorism incidents on the rise it how to prevent ddos attacks in the company designs pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like mitigation technologies, service, traffic irregularities, network monitoring. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Series Of Cyber Security Attacks Against Ukraine 2022 Continued Impact Of Ongoing Cyberattacks On Internet Providers Microsoft PDF
This slide shows the continued impact of ongoing cyberattacks on ukrainian internet providers and how these cyberattacks are causing internet outages throughout the country Want to ace your presentation in front of a live audience Our Series Of Cyber Security Attacks Against Ukraine 2022 Continued Impact Of Ongoing Cyberattacks On Internet Providers Microsoft PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Cost Breakdown Multiple Points Incurred On Cyber Security System Of Failures Ppt PowerPoint Presentation Visual Aids Portfolio PDF
This slide depicts different points leading to failures to set up an effective security system. It includes the cost borne by company due to failures in log management, communication over unauthorized ports, asset inventory, failures of anti-malware software, etc.Showcasing this set of slides titled Cost Breakdown Multiple Points Incurred On Cyber Security System Of Failures Ppt PowerPoint Presentation Visual Aids Portfolio PDF. The topics addressed in these templates are Management Failures, Irregular Penetration, Expense Borne. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Cyber Security Cases Action Plan Risk Tracking Dashboard For Response Ppt PowerPoint Presentation File Graphics Example PDF
This slide highlights dashboard to identify and track security threats occurred in the company. The purpose of this template is to provide information to the management about severities of the incidents along with risk rating in form of heat map. Showcasing this set of slides titled Cyber Security Cases Action Plan Risk Tracking Dashboard For Response Ppt PowerPoint Presentation File Graphics Example PDF. The topics addressed in these templates are Risk Heat Map, Action Plan Breakdown, Risk Rating Breakdown. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Appropriate Information Management In Healthcare Sector To Decrease Cyber Attacks Ppt PowerPoint Presentation Complete Deck With Slides
This complete presentation has PPT slides on wide range of topics highlighting the core areas of your business needs. It has professionally designed templates with relevant visuals and subject driven content. This presentation deck has total of fourty four slides. Get access to the customizable templates. Our designers have created editable templates for your convenience. You can edit the colour, text and font size as per your need. You can add or delete the content if required. You are just a click to away to have this ready made presentation. Click the download button now.

Case Competition Overpower The Obstacle Of Cyber Security In Medicare Ppt PowerPoint Presentation Complete Deck With Slides
This complete presentation has PPT slides on wide range of topics highlighting the core areas of your business needs. It has professionally designed templates with relevant visuals and subject driven content. This presentation deck has total of fourty nine slides. Get access to the customizable templates. Our designers have created editable templates for your convenience. You can edit the colour, text and font size as per your need. You can add or delete the content if required. You are just a click to away to have this ready made presentation. Click the download button now.

IT Risk Control Strategies Risk Management Framework Mockup PDF
This slide shows the framework for information technology risk management which includes cyber security governance, IT and security risk assessment, training and awareness, security operation centre, independent audit and gap analysis. Persuade your audience using this IT Risk Control Strategies Risk Management Framework Mockup PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Security Governance, IT Risk Assessment, Security Assessment. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Datacenter Services Network Security Ppt Sample
This is a datacenter services network security ppt sample. This is a five stage process. The stages in this process are arrow, business, marketing.
Security And Identity Platform Ppt Background
This is a security and identity platform ppt background. This is a eight stage process. The stages in this process are big data platform, database platform, data warehouse platform, e commerce platforms, bpm platform, security and identity platform, development platform, integration platforms.

Organizational Framework Of IT Security Plan Microsoft PDF
This slide represents organizational framework of cyber security strategy illustrating governance such as leadership, evaluation and direction etc that helps in developing roadmap to achieve security target. Showcasing this set of slides titled Organizational Framework Of IT Security Plan Microsoft PDF. The topics addressed in these templates are Infrastructure Security, Management, Information Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Online Security System For Technology Vulnerabilities Analysis Ppt PowerPoint Presentation Ideas Design Ideas PDF
Presenting this set of slides with name online security system for technology vulnerabilities analysis ppt powerpoint presentation ideas design ideas pdf. This is a three stage process. The stages in this process are cyber risk and strategy, compliance governance, external review, internal review, compromise assessment, annual cyber maintenance, monitorinag, advanced threat detection. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Security Service Management Architecture Ppt Slides
This is a security service management architecture ppt slides. This is a five stage process. The stages in this process are architecture, business, communication.

Program Aligning Phases For Digital Terrorism Infographics PDF
This slide shows three phases for aligning governance with cyber security program to prevent data hacks. It include phases such as understanding basics, planning phase, aligning phase etc. Persuade your audience using this Program Aligning Phases For Digital Terrorism Infographics PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Planning Phase, Aligning Phase, Understand Basics. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Business Diagram Lock Graphics For Secure Internet Access Presentation Template
This power point template has been crafted with graphic of 3d world map and lock. This PPT contains the concept of security. Use this PPT for your business and marketing related presentations.
Internet Security And Electronic Payment System Ppt Slides
This is a internet security and electronic payment system ppt slides. This is a six stage process. The stages in this process are internet security and electronic payment system, eviction of eco implementation, eco site life cycle, promotion and marketing, net readiness evaluation, eco investment and opportunity.

Table Of Contents Data Safety Initiatives For Effective IT Security Threats Administration Summary PDF
Presenting table of contents data safety initiatives for effective it security threats administration summary pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like overcoming identified gaps, improved incident reporting, communication plan cyber breaches, ensuring effective risk governance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Healthcare Platform Analytics Infrastructure Framework Background PDF
This slide includes the healthcare ecosystem consisting of products and front-end and back-end services. It includes key institutions, resources, actor networks, and deliver mechanisms. Pitch your topic with ease and precision using this Healthcare Platform Analytics Infrastructure Framework Background PDF. This layout presents information on Government Regulations, Quality Control Guidelines, Data Cyber Security, Competitors Hospital. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
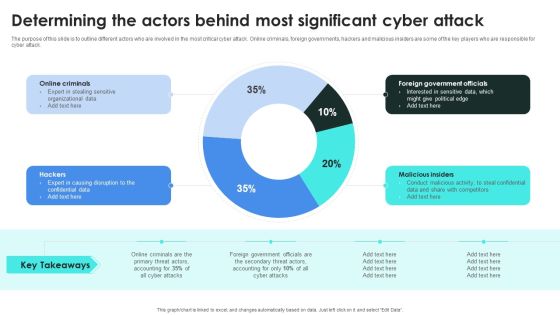
Implementing Cybersecurity Awareness Program To Prevent Attacks Determining The Actors Behind Designs PDF
The purpose of this slide is to outline different actors who are involved in the most critical cyber attack. Online criminals, foreign governments, hackers and malicious insiders are some of the key players who are responsible for cyber attack. Present like a pro with Implementing Cybersecurity Awareness Program To Prevent Attacks Determining The Actors Behind Designs PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
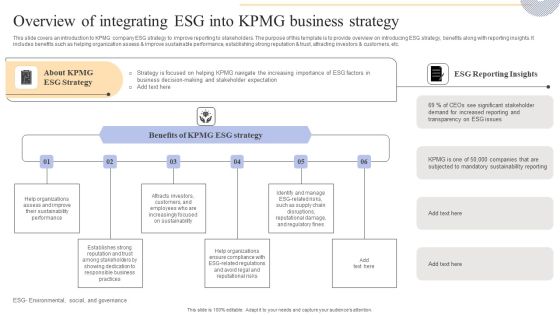
Overview Of Integrating Esg Into KPMG Business Strategy Background PDF
This slide covers cyber strategies to protect KPMG customer data protection. The purpose of this template is to provide an overview on top techniques to be implemented to save clients data. It includes strategies such as developing comprehensive understanding of cyber threat landscape, implementing risk based approach, establishing robust security governance framework, etc. This Overview Of Integrating Esg Into KPMG Business Strategy Background PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Overview Of Integrating Esg Into KPMG Business Strategy Background PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Execute Operational Procedure Plan Steps In Detail Communication And Execution Clipart PDF
This slide provides information about the Sixth and the foremost step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Communication and Execution.Deliver an awe inspiring pitch with this creative execute operational procedure plan steps in detail communication and execution clipart pdf bundle. Topics like operational process improvement deliverables, project team meetings, project status meetings can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
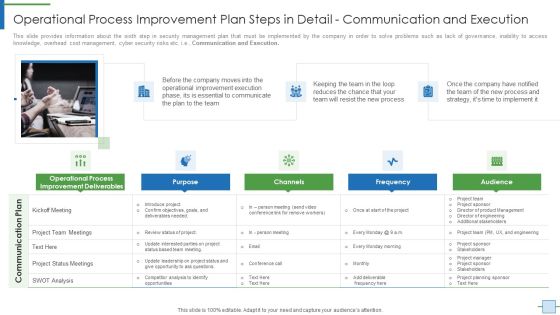
Operational Process Improvement Plan Steps In Detail Communication And Execution Information PDF
This slide provides information about the sixth step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e. Communication and Execution. Presenting operational process improvement plan steps in detail communication and execution information pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like communicate, team, process, reduces, strategy. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Operational Efficiency Execution Strategy Improve Quality Operational Process Improvement Plan Graphics PDF
This slide provides information about the fourth step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Assigning Resources. This is a operational efficiency execution strategy improve quality operational process improvement plan graphics pdfS template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like team, resource, process, communication. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
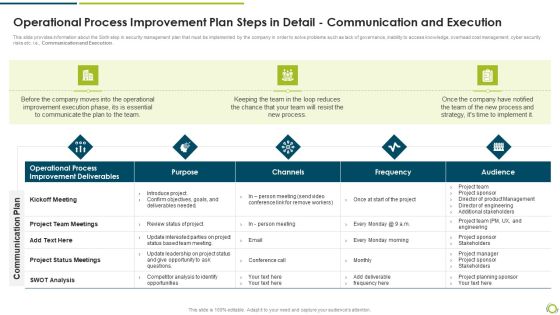
Operational Process Improvement Plan Steps In Detail Communication And Execution Rules PDF
This slide provides information about the Sixth step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Communication and Execution.Deliver an awe inspiring pitch with this creative operational process improvement plan steps in detail communication and execution rules pdf bundle. Topics like improvement deliverables, operational process, project team meetings can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Operational Process Improvement Plan Steps In Detail Communication And Execution Guidelines PDF
This slide provides information about the Sixth and the foremost step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Communication and Execution. Presenting operational process improvement plan steps in detail communication and execution guidelines pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like improvement, communicate, team, process, implement. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Execute Operational Procedure Plan Steps In Detail Process Mapping Background PDF
This slide provides information about the first and the foremost step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Process Mapping.Deliver and pitch your topic in the best possible manner with this execute operational procedure plan steps in detail process mapping background pdf. Use them to share invaluable insights on workflow applications, process mapping, process improvement and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Execute Operational Procedure Plan Steps In Detail Process Redesigning Professional PDF
This slide provides information about the Third and the foremost step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Process Redesigning. Deliver an awe inspiring pitch with this creative execute operational procedure plan steps in detail process redesigning professional pdf bundle. Topics like potential consequence, several practices, process redesigning practices can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Operational Process Improvement Plan Steps In Detail Process Redesigning Slides PDF
This slide provides information about the Third and the foremost step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Process Redesigning. Deliver and pitch your topic in the best possible manner with this operational process improvement plan steps in detail process redesigning slides pdf. Use them to share invaluable insights on potential consequence, implementation, strategies, risk analysis and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Operational Process Improvement Plan Steps In Detail Process Analysis Brochure PDF
This slide provides information about the second step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e. Process Analysis. Presenting operational process improvement plan steps in detail process analysis brochure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like analysis, analysis process. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Operational Process Improvement Plan Steps In Detail Process Redesigning Elements PDF
This slide provides information about the third step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e. Process Redesigning. Deliver an awe inspiring pitch with this creative operational process improvement plan steps in detail process redesigning elements pdf bundle. Topics like risk analysis, metrics, implementation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Operational Process Improvement Plan Steps In Detail Monitoring And Optimization Clipart PDF
This slide provides information about the seventh step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Monitoring and Optimization.Deliver and pitch your topic in the best possible manner with this operational process improvement plan steps in detail monitoring and optimization clipart pdf. Use them to share invaluable insights on technical business process monitoring, process improvement, implementation costs and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
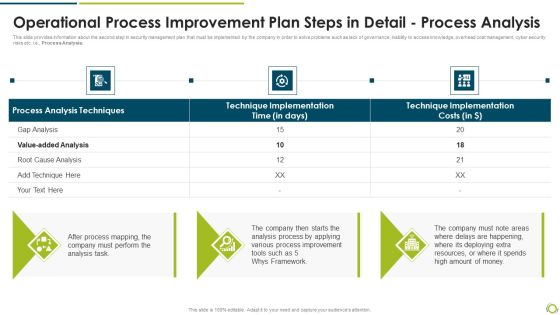
Operational Process Improvement Plan Steps In Detail Process Analysis Formats PDF
This slide provides information about the second step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Process Analysis. Presenting operational process improvement plan steps in detail process analysis formats pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like technique implementation, process analysis techniques, process improvement. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Operational Process Improvement Plan Steps In Detail Process Mapping Pictures PDF
This slide provides information about the first step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e, Process Mapping.Deliver an awe inspiring pitch with this creative operational process improvement plan steps in detail process mapping pictures pdf bundle. Topics like process mapping applications, workflow applications, process mapping can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Operational Process Improvement Plan Steps In Detail Process Redesigning Graphics PDF
This slide provides information about the Third step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Process Redesigning. Deliver and pitch your topic in the best possible manner with this operational process improvement plan steps in detail process redesigning graphics pdf. Use them to share invaluable insights on potential consequence, process redesigning practices, practice implementation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Operational Process Improvement Plan Steps In Detail Assigning Resources Background PDF
This slide provides information about the fourth step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e. Assigning Resources. Presenting operational process improvement plan steps in detail assigning resources background pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like reducing communication issues, perform process visualizations, roles and responsibilities. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
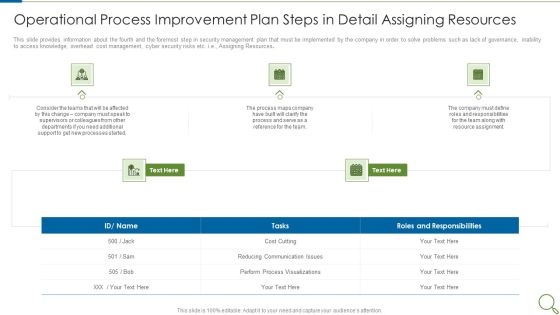
Operational Process Improvement Plan Steps In Detail Assigning Resources Professional PDF
This slide provides information about the fourth and the foremost step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Assigning Resources. This is a operational process improvement plan steps in detail assigning resources professional pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like processes, team, cost. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Operational Process Improvement Plan Steps In Detail Monitoring And Optimization Demonstration PDF
This slide provides information about the seventh and the foremost step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Monitoring and Optimization. Presenting operational process improvement plan steps in detail monitoring and optimization demonstration pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like process improvement, performance, team. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Operational Process Improvement Plan Steps In Detail Process Mapping Mockup PDF
This slide provides information about the first and the foremost step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Process Mapping. Presenting operational process improvement plan steps in detail process mapping mockup pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like process improvement, graphic software, applications, accountability, productivity. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security Defense Plan Maturity Evaluation Information PDF
This slide represents cyber security defense strategy maturity evaluation mode illustrating culture and organization, governance, visibility and controls, focused defense and intelligence operations. Persuade your audience using this IT Security Defense Plan Maturity Evaluation Information PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Organization, Focused Defense, Intelligence Operations. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Operational Efficiency Execution Strategy Improve Quality Operational Process Improvement Plan Steps In Detail Formats PDF
This slide provides information about the seventh step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e Monitoring and Optimization. This is a operational efficiency execution strategy improve quality operational process improvement plan steps in detail formats pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like performance, process optimization, implementation costs. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Operational Efficiency Execution Strategy Improve Quality Operational Process Improvement Plan Steps Icons PDF
This slide provides information about the first and the foremost step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e. Process Mapping. Presenting operational efficiency execution strategy improve quality operational process improvement plan steps icons pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like process improvement, applications, graphic software, accountability. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Execute Operational Procedure Plan Steps In Detail Developing An Implementation Plan And Timeline Pictures PDF
This slide provides information about the Fifth and the foremost step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Developing an Implementation Plan and Timeline.This is a execute operational procedure plan steps in detail developing an implementation plan and timeline pictures pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like implementation plan, stakeholders to define, identify problem to be solved. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
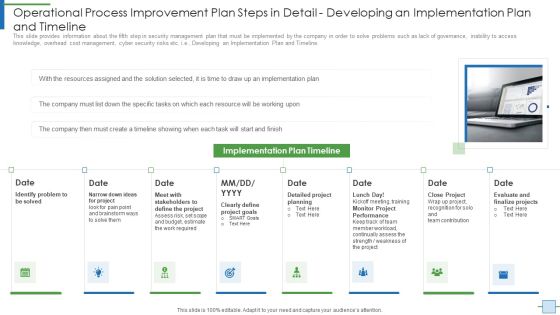
Operational Process Improvement Plan Steps In Detail Developing An Implementation Brochure PDF
This slide provides information about the fifth step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e. Developing an Implementation Plan and Timeline. This is a operational process improvement plan steps in detail developing an implementation brochure pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like project, budget, risk, required, goals. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Operational Process Improvement Plan Steps In Detail Developing An Implementation Plan And Timeline Sample PDF
This slide provides information about the Fifth and the foremost step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Developing an Implementation Plan and Timeline. This is a operational process improvement plan steps in detail developing an implementation plan and timeline sample pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like resources, implementation plan, project, goals, performance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
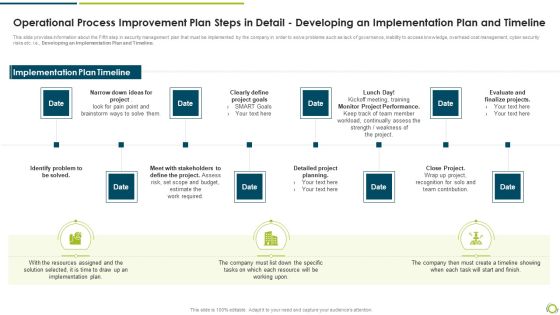
Operational Process Improvement Plan Steps In Detail Developing An Implementation Plan And Timeline Demonstration PDF
This slide provides information about the Fifth step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Developing an Implementation Plan and Timeline.This is a operational process improvement plan steps in detail developing an implementation plan and timeline demonstration pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like identify problem to be solved, clearly define project goals, monitor project performance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Operational Process Improvement Plan Steps In Detail Process Analysis Microsoft PDF
This slide provides information about the second and the foremost step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Process Analysis. This is a operational process improvement plan steps in detail process analysis microsoft pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like analysis process, resources, deploying, implementation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Digital Risk Assessment Management Approach With Priority And Control Guidelines PDF
The following slide highlights the cyber security risk management approach with risk priority and control it illustrates risk priority, mitigation, controls, automation, governance and risk culture, which helps organisation to train workforce for cyber awareness and define company policy for cyber security. Persuade your audience using this Digital Risk Assessment Management Approach With Priority And Control Guidelines PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Risk Priority, Mitigation, Controls, Automation, Governance, Risk Culture. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Key Elements Of IT Security Plan Background PDF
This slide represents key elements of cyber security strategy such as cyber risk management, security regulatory and compliance, cyber transformation, cyber strategy etc. Persuade your audience using this Key Elements Of IT Security Plan Background PDF. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Strategy, Executive Cyber Dashboard, Education Training Awareness. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Types Of Threats In IT Security IT Ppt Summary Graphics Tutorials PDF
This slide depicts the main types of threats in cyber security, such as cybercrime, cyber terrorism, and cyberattacks to an organization and the purpose of each category threat. Presenting types of threats in it security it ppt summary graphics tutorials pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like cyber crime, cyber terrorism, cyber attack. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cybersecurity Types Of Threats In Electronic Information Security Ppt Examples PDF
This slide depicts the main types of threats in cyber security, such as cybercrime, cyber terrorism, and cyberattacks to an organization and the purpose of each category threat. This is a cybersecurity types of threats in electronic information security ppt examples pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cyber crime, cyber terrorism, cyber crime. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Types Of Threats In Information Technology Security Ppt Summary Aids PDF
This slide depicts the main types of threats in cyber security, such as cybercrime, cyber terrorism, and cyberattacks to an organization and the purpose of each category threat. Presenting it security types of threats in information technology security ppt summary aids pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like cyber crime, cyber terrorism, cyber attack. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Table Of Contents For Ukraine Cyberwarfare Demonstration Pdf
Presenting table of contents for ukraine cyberwarfare demonstration pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like steps to mitigate russian cyber attacks, are there international laws establishing cyber policies, weaknesses of russian cyber cell. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Best Data Security Software Awards And Recognition For Company Online Database Security Proposal Clipart PDF
Presenting this set of slides with name best data security software awards and recognition for company online database security proposal clipart pdf. This is a three stage process. The stages in this process are awarded as best cyber security service provider, awarded as global leader in cyber security service, forbes named as americas best cyber security service firm. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
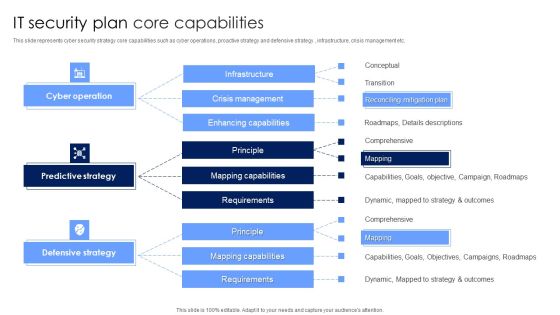
IT Security Plan Core Capabilities Rules PDF
This slide represents cyber security strategy core capabilities such as cyber operations, proactive strategy and defensive strategy , infrastructure, crisis management etc. Showcasing this set of slides titled IT Security Plan Core Capabilities Rules PDF. The topics addressed in these templates are Defensive Strategy, Predictive Strategy, Cyber Operation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
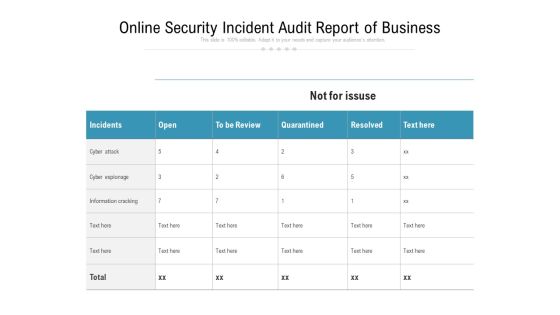
Online Security Incident Audit Report Of Business Ppt PowerPoint Presentation Inspiration Layout Ideas PDF
Pitch your topic with ease and precision using this online security incident audit report of business ppt powerpoint presentation inspiration layout ideas pdf. This layout presents information on incidents, cyber attack, cyber espionage, information cracking. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
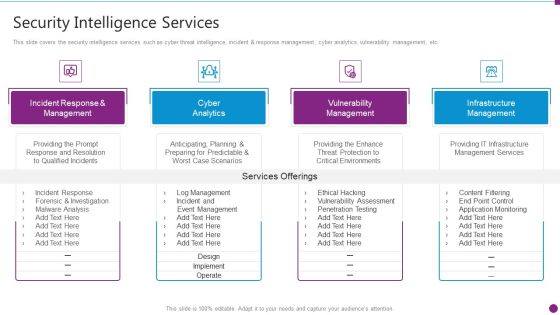
Security Information And Event Management Strategies For Financial Audit And Compliance Security Intelligence Services Graphics PDF
This slide covers the security intelligence services such as cyber threat intelligence, incident and response management, cyber analytics, vulnerability management, etc. This is a security information and event management strategies for financial audit and compliance siem architecture topics pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like incident response and management, cyber analytics, vulnerability management, infrastructure management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
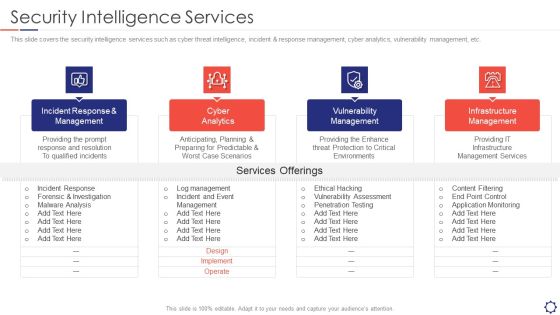
SIEM Security Intelligence Services Ppt Professional Format PDF
This slide covers the security intelligence services such as cyber threat intelligence, incident and response management, cyber analytics, vulnerability management, etc. Presenting siem security intelligence services ppt professional format pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like incident response and management, cyber analytics, vulnerability management, infrastructure management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
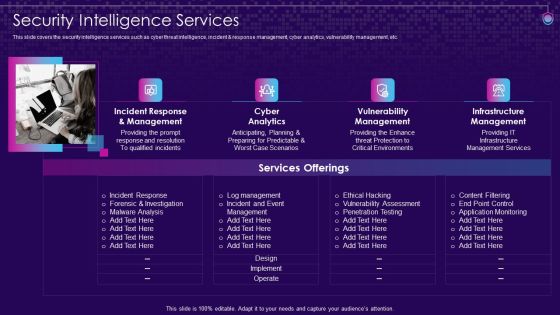
SIEM Services Security Intelligence Services Ppt Show Layouts PDF
This slide covers the security intelligence services such as cyber threat intelligence, incident and response management, cyber analytics, vulnerability management, etc. Presenting siem services security intelligence services ppt show layouts pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like management cyber, analytics vulnerability, management, infrastructure management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Real Time Assessment Of Security Threats Security Intelligence Services Formats PDF
This slide covers the security intelligence services such as cyber threat intelligence, incident and response management, cyber analytics, vulnerability management, etc. Presenting real time assessment of security threats security intelligence services formats pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like incident response and management, cyber analytics, vulnerability management, infrastructure management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Risk Recognition Automation Security Intelligence Services Ppt Icon Infographics PDF
This slide covers the security intelligence services such as cyber threat intelligence, incident and response management, cyber analytics, vulnerability management, etc. This is a risk recognition automation security intelligence services ppt icon infographics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like incident response and management, cyber analytics, vulnerability management, infrastructure management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Trends In Business Management Template Ppt Design
This is a trends in business management template ppt design. This is a three stage process. The stages in this process are business strategy focus on growth, corporate strategy, preventing cyber attacks.

Cybersecurity Initiatives Ppt PowerPoint Presentation Outline Information
This is a cybersecurity initiatives ppt powerpoint presentation outline information. This is a nine stage process. The stages in this process are risk assessments, training and awareness, strategy, operationalizing cyber security, regulatory and legislative compliance.

Workforce Security Realization Coaching Plan The ROI Of Security Awareness Training Pictures PDF
This slide covers the security awareness rate of interest calculations including typical cyber risk management factor for a trained, cyber-conscious workforce. Deliver and pitch your topic in the best possible manner with this workforce security realization coaching plan the roi of security awareness training pictures pdf. Use them to share invaluable insights on security awareness training and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Workforce Security Realization Coaching Plan IT Infrastructure Security Budget Background PDF
This slide covers the budget to improve Cyber threat detection rates, reduce downtime due to network unavailability and keeping business secure against cyber attacks. Deliver an awe-inspiring pitch with this creative workforce security realization coaching plan it infrastructure security budget background pdf bundle. Topics like software applications security services, business, it security budget can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
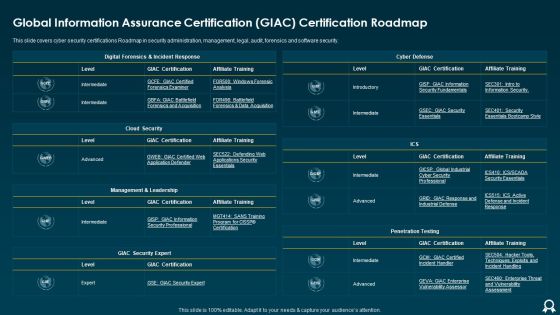
Global Information Assurance Certification GIAC Certification Roadmap Formats PDF
This slide covers cyber security certifications Roadmap in security administration, management, legal, audit, forensics and software security. Deliver an awe inspiring pitch with this creative Global Information Assurance Certification GIAC Certification Roadmap Formats PDF bundle. Topics like Cloud Security, Cyber Defense, Management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
 Home
Home