Cyber Governance

Process Flow For Detecting Insider Threat In Cyber Security Mockup PDF
This slide shows insider threat detection process flow. It contains information such as administrator, personal devices, behavior, detection system, behavior analysis, security auditing, terminating user access, etc. Presenting Process Flow For Detecting Insider Threat In Cyber Security Mockup PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including User Authentication, Insider Attacker, Administrator, Controlled Access. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Systems Graphics PDF
This slide provides information about the second step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Monitoring All Systems. Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring systems graphics pdf bundle. Topics like cybersecurity monitoring plan steps in detail monitoring all systems can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
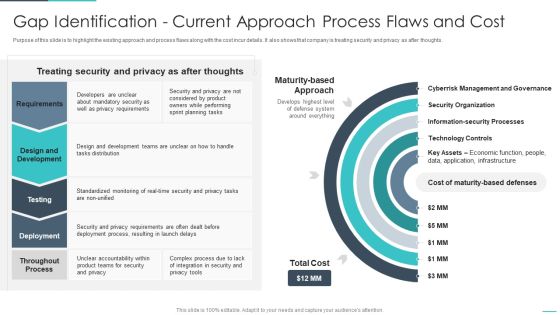
Handling Cyber Threats Digital Era Gap Identification Current Approach Process Ppt Outline Objects PDF
Purpose of this slide is to highlight the existing approach and process flaws along with the cost incur details. It also shows that company is treating security and privacy as after thoughts. Deliver and pitch your topic in the best possible manner with this handling cyber threats digital era gap identification current approach process ppt outline objects pdf. Use them to share invaluable insights on gap identification current approach process flaws and cost and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
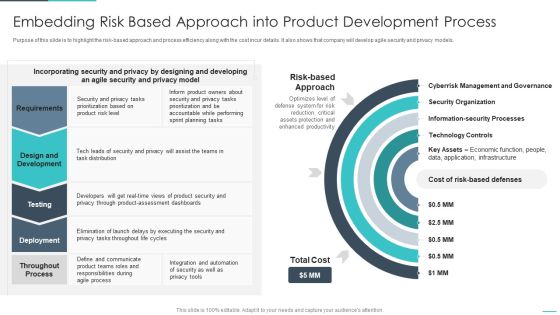
Handling Cyber Threats Digital Era Embedding Risk Based Approach Into Product Ppt Gallery Designs PDF
Purpose of this slide is to highlight the risk-based approach and process efficiency along with the cost incur details. It also shows that company will develop agile security and privacy models. Deliver an awe inspiring pitch with this creative handling cyber threats digital era embedding risk based approach into product ppt gallery designs pdf bundle. Topics like embedding risk based approach into product development process can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Risk Management Plan Setting Scenario For Security Control Microsoft PDF
Following slide displays security control scenario setting. It includes scenario detail, category of security controls and controls description. This is a cyber security risk management plan setting scenario for security control microsoft pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like category of security controls, campaign description, technical controls, management controls, operational controls. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security Automation Framework Managed Detection And Response Layer For Expert Monitoring Background PDF
This slide highlights the slide Managed Detection and Response security layer which include alter monitoring, attack investigation, threat hunting, and incident response. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Cyber Security Automation Framework Managed Detection And Response Layer For Expert Monitoring Background PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Cyber Safety Incident Management Determine Sequence Phases For Threat Attack Rules PDF
This slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. Presenting cyber safety incident management determine sequence phases for threat attack rules pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like reconnaissance, weaponization, exploitation, delivery. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Safety Incident Management Determine Staff Training Schedule For Skills Enhancement Ideas PDF
The employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. Presenting cyber safety incident management determine staff training schedule for skills enhancement ideas pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like advanced software training, advanced skills training, training module . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Safety Incident Management Different Kinds Of Insider Digital Threats Download PDF
This slide provides details regarding various kinds of insider digital threats such as malicious insider, negligent insider, third party insider, etc. This is a cyber safety incident management different kinds of insider digital threats download pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like malicious insider, negligent or careless insider, third party insider. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

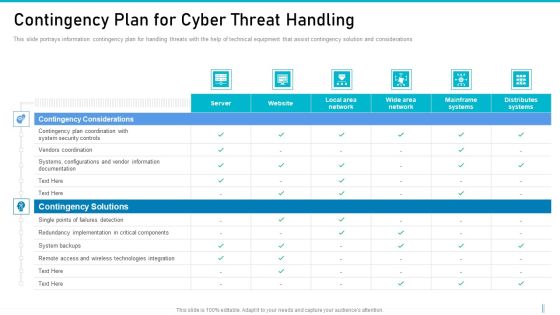
Corporate Security And Risk Management Contingency Plan For Cyber Threat Handling Structure PDF
This slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations Presenting corporate security and risk management contingency plan for cyber threat handling structure pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like contingency solutions, contingency considerations . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
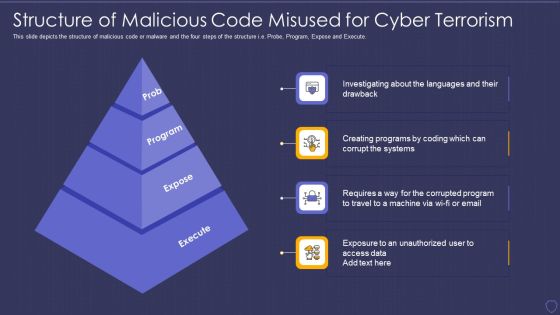
Global Cyber Terrorism Incidents On The Rise IT Structure Of Malicious Diagrams PDF
This slide depicts the structure of malicious code or malware and the four steps of the structure i.e. Probe, Program, Expose and Execute. Presenting global cyber terrorism incidents on the rise it structure of malicious diagrams pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like prob, program, expose, execute. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

5 Practices Of Information And Cyber Security Risk Management Graphics PDF
Mentioned slide delineates best practices for information security risk management. Knowledge of IT environment and assets, developing risk management strategy, embedding risk management into organization culture, continuous risk assessment and security protocols are the practices covered in this slide. Presenting 5 practices of information and cyber security risk management graphics pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including know it environment and assets, develop risk management strategy, enforce strict security protocols. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Key Features Of Managed Cyber Security Solutions Service Ppt Pictures Layouts PDF
This slide depicts the features of managed security service such as automated mechanism, management of security devices, etc. It provides information about the different benefits which security service providers provides to the organizations. Presenting Key Features Of Managed Cyber Security Solutions Service Ppt Pictures Layouts PDF to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including Deploy Network, Management System, Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Multiple Types Of Managed Cyber Security Solutions Services Ppt Styles Layout Ideas PDF
This slide exhibits the different types of managed security services such as risk management, virtual CISO and security awareness education. It also provides information about the multiple offerings of each service. Persuade your audience using this Multiple Types Of Managed Cyber Security Solutions Services Ppt Styles Layout Ideas PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Risk Management, Offerings, Security Awareness Education, Virtual CISO. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Four Dimensions Of Managed Cyber Security Solutions Service Ppt Pictures Model PDF
The following slide outlines the key dimensions of managed security service such as security information and event management, online staff augmentation, network security architecture and threat detection and alerts. Pitch your topic with ease and precision using this Four Dimensions Of Managed Cyber Security Solutions Service Ppt Pictures Model PDF. This layout presents information on Security Information, Event Management, Staff Augmentation. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Comparative Assessment Of Managed Cyber Security Solutions Service Packages Ppt Gallery Inspiration PDF
Mentioned slide delineates comparison of managed security service packages on the basis of bronze, silver and gold plan. The services covered in the packages are incident prevention, detection and response. Showcasing this set of slides titled Comparative Assessment Of Managed Cyber Security Solutions Service Packages Ppt Gallery Inspiration PDF. The topics addressed in these templates are Threat Intelligence, Vulnerability Management, Monitoring. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cybersecurity Integrated Structure To Manage Cyber Risk Ppt Show Elements PDF
This slide showcases the structure to manage cybersecurity threats and risk of any organization. It includes steps like identifying user with data access, protecting data accessibility, secure networks, install and updating antivirus, developing plan for managing disasters etc. Persuade your audience using this Cybersecurity Integrated Structure To Manage Cyber Risk Ppt Show Elements PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Recover, Respond, Detect, Identify. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Information And Cyber Data Safety Risk Management Maturity Levels Elements PDF
Mentioned slide showcase maturity stages of information security risk management, which will assist company to develop comprehensive cybersecurity strategy. The maturity stages could be Partial informed repetitive and adaptive. Presenting information and cyber data safety risk management maturity levels elements pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including partial, informed, repetitive, adaptive. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Key Practices For Selecting Managed Cyber Security Solutions Service Provider Ppt Professional Aids PDF
The following slide exhibits four practices for selecting managed security service provider. Expertise, cost, business requirements and testimonials are some of the practices which will help the organization in selecting trusted security providers. Persuade your audience using this Key Practices For Selecting Managed Cyber Security Solutions Service Provider Ppt Professional Aids PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Expertise, Cost, Business Requirements, Testimonials. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Major Tools For Managed Cyber Security Solutions Service Ppt Infographics Graphics Tutorials PDF
Mentioned slide outlines various tools for managed security service. Email security software, endpoint protection and firewall are some of the comprehensive tools which will assist the organization in closely monitoring the advance threats. Showcasing this set of slides titled Major Tools For Managed Cyber Security Solutions Service Ppt Infographics Graphics Tutorials PDF. The topics addressed in these templates are Endpoint Protection, Firewall, Email Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Managed Cyber Security Solutions Service Threat Detection Process Ppt Portfolio Pictures PDF
The following slide highlights multistep process of managed security service to mitigate IT risks. It covers step such as operational readiness review, use cases, email notification, security analysis and event resolution. Presenting Managed Cyber Security Solutions Service Threat Detection Process Ppt Portfolio Pictures PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Event Resolution, Security Analysis, Use Cases, Operational Readiness Review. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Overview Of Cloud Managed Cyber Security Solutions Service Ppt Portfolio Structure PDF
The following slide indicates key features of cloud managed security service. The features covered in the slide are low cost, data loss prevention, customized solutions and proactive maintenance and support. Presenting Overview Of Cloud Managed Cyber Security Solutions Service Ppt Portfolio Structure PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Low Cost, Customized Solutions, Additional Benefits. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Report Summary Of Managed Cyber Security Solutions Service Ppt Portfolio Slides
The following slide illustrates report summary of managed security service which includes details about responsibility of service provider, what constitutes an emergency, response time by service provider and time of reporting. Showcasing this set of slides titled Report Summary Of Managed Cyber Security Solutions Service Ppt Portfolio Slides. The topics addressed in these templates are Responsibility Of Service Provider, Time Of Reporting, Data Breach. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Various Cyber Security Threats And Strategies To Manage Network Service Solutions Ppt File Portrait PDF
This slide highlights different types of cybersecurity threat such as malware, phishing, trojan horse and rootkit. The template also provides information about various strategies which will assist IT department to manage its network services. Persuade your audience using this Various Cyber Security Threats And Strategies To Manage Network Service Solutions Ppt File Portrait PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Malware, Phishing, Rootkit, Trojan Horse. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Application Security Approaches To Manage Cyber It Service Solution Ppt Styles Slide Portrait PDF
This slide exhibits the various application security approaches which can be implemented by organization to manage their IT services. The key approaches are design review, code review and application security audit Showcasing this set of slides titled Application Security Approaches To Manage Cyber It Service Solution Ppt Styles Slide Portrait PDF. The topics addressed in these templates are Design Review, Code Review, Approaches, Application Security Audit. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Business Plan For Managed Cyber Security Solutions Service Ppt Infographic Template Topics PDF
This slide outlines the business plan for managed security service which includes services such as antivirus, anti-malware, anti-spam etc. it also provides information about the total cost of services, status of purchase, security goal, etc. Pitch your topic with ease and precision using this Business Plan For Managed Cyber Security Solutions Service Ppt Infographic Template Topics PDF. This layout presents information on Revenue, Security Goal, IT Security Budget. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Comparison Of Managed Cyber Security Solutions Service Packages Ppt Ideas Mockup PDF
This slide shows comparison of different managed security service packages like silver, gold, platinum and diamond offered by service providers to the companies. It provides information about malware protection, security awareness, ransomware prevention etc. Pitch your topic with ease and precision using this Comparison Of Managed Cyber Security Solutions Service Packages Ppt Ideas Mockup PDF. This layout presents information on Email Security, Phishing Awareness, Security Awareness. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Ensuring Effective Managed Cyber Security Solutions Service By Installing Various Components Ppt Styles Example PDF
The following slide highlights components of managed security service along with the expected cost. Software, antivirus and security monitoring are some of the components which will assist the organization in improving its IT security. Showcasing this set of slides titled Ensuring Effective Managed Cyber Security Solutions Service By Installing Various Components Ppt Styles Example PDF. The topics addressed in these templates are Security Monitoring, Antivirus, Components. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Key Challenges With Managed Cyber Security Solutions Service Providers Ppt Pictures Visual Aids PDF
This slide outlines the different challenges faced by the companies with managed security service providers. The key challenges are lack of skilled staff, too many alerts and support experience. Presenting Key Challenges With Managed Cyber Security Solutions Service Providers Ppt Pictures Visual Aids PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Too Many Alerts, Support Experience, Lack Skilled Staff. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Dashboard For Insider Threat In Cyber Security Cases Management Background PDF
This slide shows insider threat dashboard for managing multiple cases. It provides information such as active and closed, high and low risk cases, status, user, case time, policy alerts, content update, etc. Showcasing this set of slides titled Dashboard For Insider Threat In Cyber Security Cases Management Background PDF. The topics addressed in these templates are Total Policy Alerts, High, Low, Time Case Opened. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Insider Threat In Cyber Security Management Plan With Case Status Graphics PDF
This slide shows plan for managing insider risk with case status. It provides information about users, alert, status, severity, time detected, action plan, etc. Pitch your topic with ease and precision using this Insider Threat In Cyber Security Management Plan With Case Status Graphics PDF. This layout presents information on Requires Review, Action Plan, Case Status. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Role Of Insider Threat In Cyber Security Management Technologies In Banking Industry Infographics PDF
This slide shows role of insider threat management technologies in banking industry. It provides information about identifying user risk, protecting from data loss and accelerating threat response. Presenting Role Of Insider Threat In Cyber Security Management Technologies In Banking Industry Infographics PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Identifying User Risk, Accelerating Threat Response, Protecting Data Loss. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Security Tactic For Process Management For IT Roadmap Six Months Clipart
Presenting the cyber security tactic for process management for it roadmap six months clipart. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Cyber Security Tactic For Process Management For IT Roadmap Three Months Demonstration
Presenting our jaw dropping cyber security tactic for process management for it roadmap three months demonstration. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.

Cyber Security Risk Management Plan Asset Criticality Of Identified System Components Mockup PDF
Following slide demonstrates the asset criticality of identified system components. It covers details such as system name, component used, impact rating, criticality rating and failure cost. Deliver and pitch your topic in the best possible manner with this cyber security risk management plan asset criticality of identified system components mockup pdf. Use them to share invaluable insights on system name, component used, impact rating, criticality rating, failure cost and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security Risk Management Plan Threat Identification And Vulnerability Impact Assessment Brochure PDF
Following slide shows threat identification and vulnerability impact assessment. It covers information of threat agent, affected assets, potential vulnerability, vulnerability ranking, its rank and threats to firm. Deliver and pitch your topic in the best possible manner with this cyber security risk management plan threat identification and vulnerability impact assessment brochure pdf. Use them to share invaluable insights on threat agent, affected assets, potential vulnerability, vulnerability ranking, threats to firm and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security Risk Management Plan Defining Categories Of Information Security Threats Structure PDF
This slide shows the categorization of information security threats. Categories covered are human error, natural disaster, software attacks and environmental control failures. This is a cyber security risk management plan defining categories of information security threats structure pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like human error, natural disaster, environmental control failures, deliberate software attacks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security Risk Management Plan Introducing Information Security Risk Assessment Process Workflow Elements PDF
Following slide illustrates information security risk assessment process workflow. It covers 6 stages namely system characterization, threat identification, vulnerability identification, risk analysis, risk remedies and documented results. This is a cyber security risk management plan introducing information security risk assessment process workflow elements pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like characterize system, identify vulnerabilities, identify threats, recommend remediation measures, analyze risks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security Risk Management Plan Mitigation Plan For Resolving Encountered Threat Pictures PDF
Mentioned slide shows mitigation plan for resolving encountered threat. It covers details about encountered threat, its description, risk level, mitigation plan, resources required, responsible person, expected resolution time and communication mode. Deliver an awe inspiring pitch with this creative cyber security risk management plan mitigation plan for resolving encountered threat pictures pdf bundle. Topics like threat encountered, mitigation plan, responsible person, communication mode, risk level can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Risk Management For Organization Essential Assets Contingency Plan For Cyber Threat Handling Download PDF
This slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations. Deliver and pitch your topic in the best possible manner with this risk management for organization essential assets contingency plan for cyber threat handling download pdf. Use them to share invaluable insights on server, website, local area network, wide area network, mainframe systems, distributes systems and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

E Business And Cyber Risk Management Ppt PowerPoint Presentation Complete With Slides
Pitch yourself both in house and outside by utilizing this complete deck. This e business and cyber risk management ppt powerpoint presentation complete with slides focuses on key fundamentals of the topic, displayed using different slides. With a total of fifty two slides, this template is the best tool you can use to persuade your audience. It will not only help you create great presentations but also induce strategic thinking because of its well researched content and graphics. You can easily personalize any of the elements to suit your unique business setting. Additionally, it can be saved in PNG, JPG, and PDF formats to save your time and resources.

Cyber Safety Incident Management Ppt PowerPoint Presentation Complete Deck With Slides
Pitch yourself both in house and outside by utilizing this complete deck. This cyber safety incident management ppt powerpoint presentation complete deck with slides focuses on key fundamentals of the topic, displayed using different slides. With a total of sixty seven slides, this template is the best tool you can use to persuade your audience. It will not only help you create great presentations but also induce strategic thinking because of its well researched content and graphics. You can easily personalize any of the elements to suit your unique business setting. Additionally, it can be saved in PNG, JPG, and PDF formats to save your time and resources.

Cyber Safety Incident Management Current Potential Implications Faced By Firm As Threats Clipart PDF
This slide provides information regarding the potential implications or concerns existing in firm in terms of increase in issues related to employees such as lack of expertise, ineffectiveness in handling issues, reported financial losses due to financial threats and data breaches with records exposed. Deliver an awe inspiring pitch with this creative cyber safety incident management current potential implications faced by firm as threats clipart pdf bundle. Topics like issues related to employees, data breaches and records exposed, reported financial losses due to increase security threats can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Safety Incident Management How Financial Risk Can Be Controlled Formats PDF
This slide provides details regarding various ways through financial risks can be controlled by handling liquidity risk, foreign exchange risk and credit exchange risk. Presenting cyber safety incident management how financial risk can be controlled formats pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like handling liquidity risk, handling foreign exchange risk, handling credit exchange risk . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Safety Incident Management Incident Reporting By Different Departments Brochure PDF
This slide will help in providing an overview of the various reported incidents, average cost per incident and number of people involved in the various incidents across different departments. Presenting cyber safety incident management incident reporting by different departments brochure pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like incident reporting by different departments. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Safety Incident Management Key Activities Checklist Associated To Insider Threat Program Download PDF
This slide provides details regarding checklist associated to insider threat program in terms of plan and collect, review and analyze and strategic framework development. Deliver and pitch your topic in the best possible manner with this cyber safety incident management key activities checklist associated to insider threat program download pdf. Use them to share invaluable insights on plan and collet, review and analyze, develop strategic framework, key activities and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Safety Incident Management Various Types Of Workplace Violence And Threats Infographics PDF
This slide provides details regarding various types of workplace violence threats created by people in terms of stalking, physical assault, harassment or intimidation, etc. This is a cyber safety incident management various types of workplace violence and threats infographics pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like stalking, physical assault, harassment or intimidation, property damage, weapon assault . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Corporate Security And Risk Management Addressing Indicators Associated To Insider Cyber Threats Topics PDF
This slide provides details regarding indicators associated to insider threats in terms of traits, demeanor and goals, etc. This is a corporate security and risk management addressing indicators associated to insider cyber threats topics pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like excessive orphaned files or user accounts, no proper authentication levels, data exfiltration . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Managed Cyber Security Solutions Ppt PowerPoint Presentation Complete Deck With Slides
This complete deck covers various topics and highlights important concepts. It has PPT slides which cater to your business needs. This complete deck presentation emphasizes Managed Cyber Security Solutions Ppt PowerPoint Presentation Complete Deck With Slides and has templates with professional background images and relevant content. This deck consists of total of twenty four slides. Our designers have created customizable templates, keeping your convenience in mind. You can edit the colour, text and font size with ease. Not just this, you can also add or delete the content if needed. Get access to this fully editable complete presentation by clicking the download button below.

Cyber Risks And Incident Response Playbook Incident Management Workflow Infographics PDF
Welcome to our selection of the Cyber Risks And Incident Response Playbook Incident Management Workflow Infographics PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

Implementing Cyber Security Incident Management Ppt PowerPoint Presentation Complete Deck With Slides
This Implementing Cyber Security Incident Management Ppt PowerPoint Presentation Complete Deck With Slides is designed to help you retain your audiences attention. This content-ready PowerPoint Template enables you to take your audience on a journey and share information in a way that is easier to recall. It helps you highlight the crucial parts of your work so that the audience does not get saddled with information download. This seventy slide PPT Deck comes prepared with the graphs and charts you could need to showcase your information through visuals. You only need to enter your own data in them. Download this editable PowerPoint Theme and walk into that meeting with confidence.

Organizing Security Awareness Most Common Cyber Attack Faced By Our Employees Mockup PDF
The Organizing Security Awareness Most Common Cyber Attack Faced By Our Employees Mockup PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Utilizing Cyber Technology For Change Process Digital Strategy Roadmap Information PDF
This is a utilizing cyber technology for change process digital strategy roadmap information pdf. template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like setting the foundations strong, rolling out top priority services, expansion and diversification, achieving full potential, digital capability and maturity assessment, introduction of learning management system. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Exploitation IT Benefits Of Ethical Hackers To Business Brochure PDF
This slide depicts the benefits of ethical hackers to the business, including regaining the trust of customers and clients, setting a secure network setup, and finding flaws in our infrastructure from a hackers point of view. Presenting cyber exploitation it benefits of ethical hackers to business brochure pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security, evaluations, maintaining. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Exploitation IT Hacking Of Our Social Media Accounts Template PDF
This slide represents the hacking of a companys social media accounts such as Facebook and Instagram by hackers in 2022 and the amount of money by running scam ads. This is a cyber exploitation it hacking of our social media accounts template pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like hacking of our social media accounts. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Exploitation IT Preventing Measures For Social Media Accounts Themes PDF
This slide represents the preventing measures for social media accounts, including setting up login notifications, updating social media login credentials, using anti-malware software, and reviewing company policies. Presenting cyber exploitation it preventing measures for social media accounts themes pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like social media policies, anti malware software, social media login credentials. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Global Cyber Terrorism Incidents On The Rise IT Confidential Data Should Be Backup Structure PDF
This slide emphasizes the significance of backing up private data, which enables for data recovery in the event of an attack. Presenting global cyber terrorism incidents on the rise it confidential data should be backup structure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like confidential data should be backup. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Global Cyber Terrorism Incidents On The Rise IT Disaster Recovery Plan For The Business Template PDF
This slide illustrates the elements that will be taken into account when establishing a recovery plan for company to go back to business swiftly and successfully. This is a global cyber terrorism incidents on the rise it disaster recovery plan for the business template pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like make a complete inventory of all assets, make a risk assessment, determine the importance of assets. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
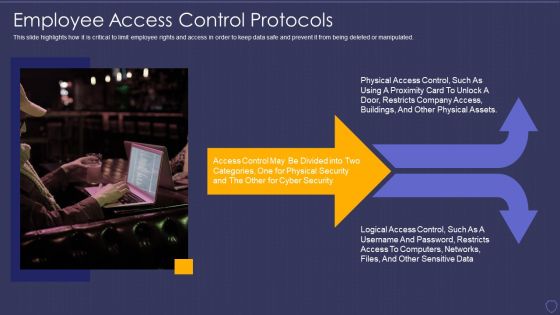
Global Cyber Terrorism Incidents On The Rise IT Employee Access Control Protocols Download PDF
This slide highlights how it is critical to limit employee rights and access in order to keep data safe and prevent it from being deleted or manipulated. Presenting global cyber terrorism incidents on the rise it employee access control protocols download pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like employee access control protocols. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Global Cyber Terrorism Incidents On The Rise IT Financial Loss Faced By The Business Designs PDF
This slide depicts the average financial loss faced by the business when projects of different scales are attacked. This is a global cyber terrorism incidents on the rise it financial loss faced by the business designs pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like targeted, revenue, financial. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

 Home
Home