Cyber Crime

Cybersecurity Risk Assessment And Administration Plan Ppt PowerPoint Presentation Complete Deck With Slides
Take advantage of this well-researched and professionally-designed Cybersecurity Risk Assessment And Administration Plan Ppt PowerPoint Presentation Complete Deck With Slides to ace your next business meeting. Use this PPT complete deck to impress the management with your ideas for business growth and revenue increase. Use the seventy two slide Template Bundle to leave no stone unturned as you present each step of your process. Employ the visual tools within the slides such as graphs, charts, and tables to ensure that the audience can never look away from the presentation. With attractive visuals, easy to understand structure, and your knowledge, your presentation will have the attention it deserves. Download this PPT Template from the link below.
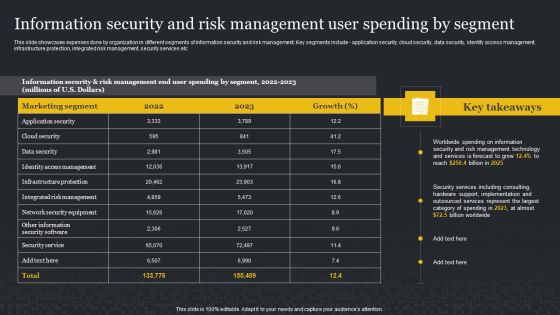
Information Security And Risk Management User Spending By Segment Cybersecurity Risk Assessment Rules PDF
This slide showcases expenses done by organization in different segments of information security and risk management. Key segments include application security, cloud security, data security, identify access management, infrastructure protection, integrated risk management, security services etc. This Information Security And Risk Management User Spending By Segment Cybersecurity Risk Assessment Rules PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Market Growth Of Information Security Industry Cybersecurity Risk Assessment Portrait PDF
This slide showcases graph for information security industry market growth in past and upcoming financial years. It can help to forecast the compounded annual growth rate of industry. Do you know about Slidesgeeks Market Growth Of Information Security Industry Cybersecurity Risk Assessment Portrait PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
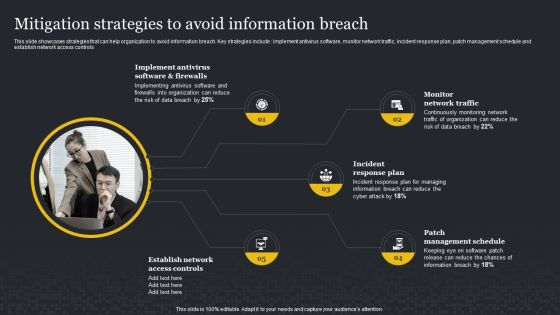
Mitigation Strategies To Avoid Information Breach Cybersecurity Risk Assessment Professional PDF
This slide showcases strategies that can help organization to avoid information breach. Key strategies include implement antivirus software, monitor network traffic, incident response plan, patch management schedule and establish network access controls. Present like a pro with Mitigation Strategies To Avoid Information Breach Cybersecurity Risk Assessment Professional PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
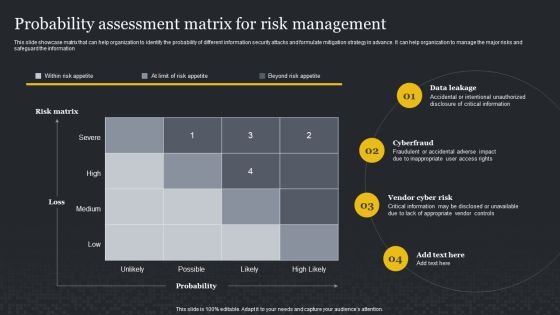
Probability Assessment Matrix For Risk Management Cybersecurity Risk Assessment Professional PDF
This slide showcase matrix that can help organization to identify the probability of different information security attacks and formulate mitigation strategy in advance. It can help organization to manage the major risks and safeguard the information. Slidegeeks is here to make your presentations a breeze with Probability Assessment Matrix For Risk Management Cybersecurity Risk Assessment Professional PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
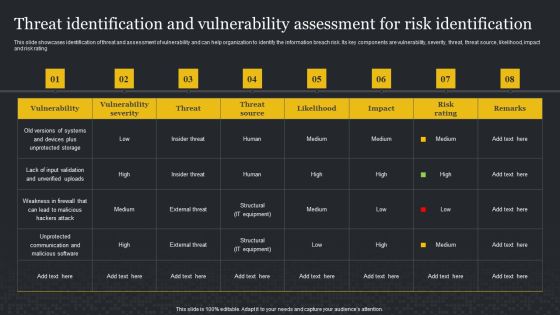
Threat Identification And Vulnerability Assessment For Risk Identification Cybersecurity Risk Assessment Demonstration PDF
This slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Threat Identification And Vulnerability Assessment For Risk Identification Cybersecurity Risk Assessment Demonstration PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Challenges And Solutions In Information Security Risk Management Cybersecurity Risk Assessment Demonstration PDF
This slide showcases challenges involved in formulating risk management program for information security. It also shows solutions to tackle the challenges and impact of implementing them. This modern and well-arranged Challenges And Solutions In Information Security Risk Management Cybersecurity Risk Assessment Demonstration PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
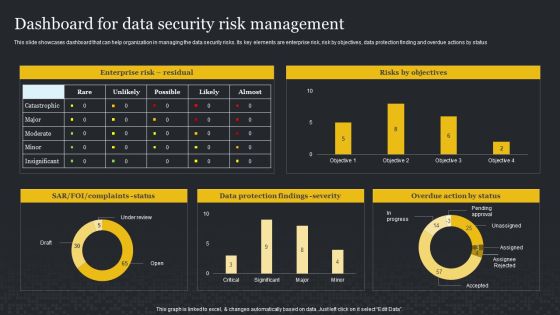
Dashboard For Data Security Risk Management Cybersecurity Risk Assessment Template PDF
This slide showcases dashboard that can help organization in managing the data security risks. Its key elements are enterprise risk, risk by objectives, data protection finding and overdue actions by status. Welcome to our selection of the Dashboard For Data Security Risk Management Cybersecurity Risk Assessment Template PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 parcent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
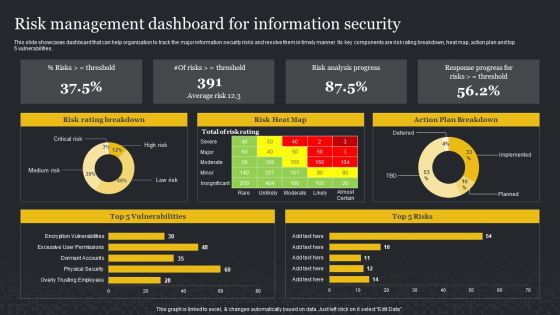
Risk Management Dashboard For Information Security Cybersecurity Risk Assessment Sample PDF
This slide showcases dashboard that can help organization to track the major information security risks and resolve them in timely manner. Its key components are risk rating breakdown, heat map, action plan and top 5 vulnerabilities. This Risk Management Dashboard For Information Security Cybersecurity Risk Assessment Sample PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Checklist For Information Security Risk Management Cybersecurity Risk Assessment Summary PDF
This slide showcases checklist that can help to ensure formulate and implementing data security risk management program in organization. Its key components are activity, assigned to and status. Do you know about Slidesgeeks Checklist For Information Security Risk Management Cybersecurity Risk Assessment Summary PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

Classifying Various Security Issues And Attacks Improving Cybersecurity Incident Elements PDF
Purpose of this slide is to show the classification of different security issues and attacks. Categories covered are majorly internal as well as external issues and attacks.Slidegeeks is here to make your presentations a breeze with Classifying Various Security Issues And Attacks Improving Cybersecurity Incident Elements PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you Are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Implementing Cybersecurity Awareness Program To Prevent Attacks Ppt PowerPoint Presentation Complete Deck With Slides
This Implementing Cybersecurity Awareness Program To Prevent Attacks Ppt PowerPoint Presentation Complete Deck With Slides is a primer on how to capitalize on business opportunities through planning, innovation, and market intelligence. The content-ready format of the complete deck will make your job as a decision-maker a lot easier. Use this ready made PowerPoint Template to help you outline an extensive and legible plan to capture markets and grow your company on the right path, at an exponential pace. What is even more amazing is that this presentation is completely editable and 100 percent customizable. This seventy five slide complete deck helps you impress a roomful of people with your expertise in business and even presentation. Craft such a professional and appealing presentation for that amazing recall value. Download now.

Implementing Cybersecurity Awareness Program To Prevent Attacks Dos And Donts Of Prevention Inspiration PDF
The purpose of this slide is to showcase the Does and do nots of ransomware prevention attack. The slide covers information about updating the software, installing a firewall software, using reliable website and sources etc. Slidegeeks is here to make your presentations a breeze with Implementing Cybersecurity Awareness Program To Prevent Attacks Dos And Donts Of Prevention Inspiration PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
Implementing Cybersecurity Awareness Program To Prevent Attacks Measuring The Impact Of Security Awareness Icons PDF
The purpose of this slide is to highlight the positive impact of security awareness training. Information covered in this slide is related to malware attack, social engineering attack and business email compromise. The Implementing Cybersecurity Awareness Program To Prevent Attacks Measuring The Impact Of Security Awareness Icons PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Cybersecurity Guidelines IT Byod Lost Stolen Hacked Or Damaged Equipment Designs PDF
This slide describes the scenarios of lost, stolen, hacked, or damaged personal equipment under BYOD policy. It also includes that remote wipe software should be installed on employees devices to remove the work data remotely in case of theft. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Cybersecurity Guidelines IT Byod Lost Stolen Hacked Or Damaged Equipment Designs PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Cybersecurity Guidelines IT Critical Components Of Information Technology Policy Structure PDF
This slide depicts the critical components of information technology policy, and it includes integrity, confidentiality, and availability, including how these components work. Slidegeeks is here to make your presentations a breeze with Cybersecurity Guidelines IT Critical Components Of Information Technology Policy Structure PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Cybersecurity Guidelines IT Email And Chat Policy Objective And Guidelines Introduction PDF
This slide represents the email and chat policy, including its objective and general guidelines. It also includes the ways to ensure email security which covers the installation of antivirus and spam filters. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Cybersecurity Guidelines IT Email And Chat Policy Objective And Guidelines Introduction PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Cybersecurity Guidelines IT Vendor Management Policy Overview And Considerations Diagrams PDF
This slide represents the vendor management policy, and it also includes points to be considered when choosing a vendor. This policy is about the vendor with whom organizations share their critical information. Slidegeeks is here to make your presentations a breeze with Cybersecurity Guidelines IT Vendor Management Policy Overview And Considerations Diagrams PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Cybersecurity Guidelines IT Company Stipend For Bring Your Own Device Policy Download PDF
This slide represents the company stipend for BYOD policy, including the stats for 2022, such as percent the age of employees using their personal devices, BYOD generated value of each worker per year, and so on. Present like a pro with Cybersecurity Guidelines IT Company Stipend For Bring Your Own Device Policy Download PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Cybersecurity Operations Cybersecops Critical Functional Areas Of Secops Teams Background PDF
This slide describes the critical functions of security operations. The purpose of this slide is to demonstrate the various functions performed by SecOps teams in an organization. The main functions include threat intelligence, security monitoring, incident response, forensics and root cause analysis, etc. Boost your pitch with our creative Cybersecurity Operations Cybersecops Critical Functional Areas Of Secops Teams Background PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Cybersecurity Operations Cybersecops Impact Of Secops Implementation On Business Guidelines PDF
This slide represents the impact of implementing security operations in an organization. The purpose of this slide is to demonstrate how SecOps can benefit a company. The benefits include streamlined IT operations, prioritizing merge and consolidating proactive security, and so on. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Cybersecurity Operations Cybersecops Impact Of Secops Implementation On Business Guidelines PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Cybersecurity Operations Cybersecops SOC As A Service Overview And Main Functions Rules PDF
This slide represents the overview and primary functions of SOC-as-a-Service. The purpose of this slide is to demonstrate the various critical functions and key features, and it also covers the reasons for organizations to adopt the subscription-based model. Slidegeeks is here to make your presentations a breeze with Cybersecurity Operations Cybersecops SOC As A Service Overview And Main Functions Rules PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Cybersecurity Operations Cybersecops Overview And Benefits Of Virtual SOC Model Infographics PDF
This slide represents the overview, benefits and disadvantages of virtual security operation center model. The purpose of this slide is to highlight the advantage, disadvantages and alternative approaches for VSOC such as outsourcing of virtual SOC model. This modern and well arranged Cybersecurity Operations Cybersecops Overview And Benefits Of Virtual SOC Model Infographics PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Cybersecurity Operations Cybersecops Roles And Responsibilities Of Security Operations Microsoft PDF
This slide outlines the roles and responsibilities of the security operations center team. The purpose of this slide is to showcase the roles as well as duties of the SOC team. The prominent roles include incident responder, security investigator, advanced security analyst, SOC manager, and security engineer. Welcome to our selection of the Cybersecurity Operations Cybersecops Roles And Responsibilities Of Security Operations Microsoft PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

Cybersecurity Operations Cybersecops Limitations Of SOC As A Service Model Template PDF
This slide depicts the challenges of adopting SOC as a service. The purpose of this slide is to highlight the main limitations of SOC as a service, including the onboarding process, enterprising data security, cost of log delivery, regulatory considerations, no dedicated IT security team, and limited customized options. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Cybersecurity Operations Cybersecops Limitations Of SOC As A Service Model Template PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Cybersecurity Operations Cybersecops RACI Matrix For SOC As A Service Security Model Microsoft PDF
This slide outlines the RACI matrix for the SOC-as-a-Service security model. The purpose of this slide is to highlight the various roles and responsibilities in a SOC as a Service environment. The main roles include SOC manager, security analyst, security architecture, compliance auditor, and SOC coordinator. Slidegeeks is here to make your presentations a breeze with Cybersecurity Operations Cybersecops RACI Matrix For SOC As A Service Security Model Microsoft PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Desktop Security Management Elements Of Computer Security Information Security Portrait PDF
This slide depicts the information security methodology and core information security principles such as confidentiality, integrity, and availability. Presenting desktop security management elements of computer security information security portrait pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like social media, information security, organization, network. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
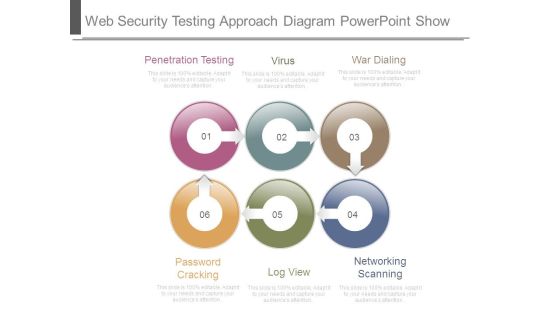
Web Security Testing Approach Diagram Powerpoint Show
This is a web security testing approach diagram powerpoint show. This is a six stage process. The stages in this process are penetration testing, virus, war dialing, password cracking, log view, networking scanning.

Four Computer Security Processes Portrait PDF
This slide shows the four step by step processes used in information technology security. It includes penetration testing, VPN configuration, network security audit checklist and privileged password management. Presenting Four Computer Security Processes Portrait PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Penetration Testing, Configuration, Password Management This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Approaches To Implement Advanced Cybersecurity Monitoring Plan Ppt PowerPoint Presentation Complete Deck With Slides
This complete deck acts as a great communication tool. It helps you in conveying your business message with personalized sets of graphics, icons etc. Comprising a set of fortyfour slides, this complete deck can help you persuade your audience. It also induces strategic thinking as it has been thoroughly researched and put together by our experts. Not only is it easily downloadable but also editable. The color, graphics, theme any component can be altered to fit your individual needs. So grab it now.

Mitigating Cybersecurity Threats And Vulnerabilities Ppt PowerPoint Presentation Complete Deck With Slides
This complete deck acts as a great communication tool. It helps you in conveying your business message with personalized sets of graphics, icons etc. Comprising a set of seventy slides, this complete deck can help you persuade your audience. It also induces strategic thinking as it has been thoroughly researched and put together by our experts. Not only is it easily downloadable but also editable. The color, graphics, theme any component can be altered to fit your individual needs. So grab it now.

Cybersecurity Risk Administration Plan Ppt PowerPoint Presentation Complete Deck With Slides
Induce strategic thinking by presenting this complete deck. Enthrall your audience by deploying this thought provoking PPT deck. It can be downloaded in both standard and widescreen aspect ratios, thus making it a complete package to use and deploy. Convey your thoughts and actions using the fifty eight slides presented in this complete deck. Additionally, feel free to alter its components like color, graphics, design, etc, to create a great first impression. Grab it now by clicking on the download button below.

5G Network Technology Value Enabler 1 5G Resilient Networks System Ppt Layouts Diagrams PDF
This slide provides details regarding value enabler for operator as 5G resilient networks system including importance and key components associated to it. This is a 5g network technology value enabler 1 5g resilient networks system ppt layouts diagrams pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like service availability, security assurance, secured identities and protocols. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Value Enabler 1 5G Resilient Networks System 5G Network Architecture Instructions Sample PDF
This slide provides details regarding value enabler for operator as 5G resilient networks system including importance and key components associated to it. Presenting Value Enabler 1 5G Resilient Networks System 5G Network Architecture Instructions Sample PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Service Availability, Security Assurance, Secured Identities. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Five Attributes Of Web Enabled Network For Telecommunication And Networks Guidelines PDF
This slide represents the five key characteristics of using extranet for telecommunication and networks. It includes features such as data security, faster communication, flexibility, cost and authentication. Persuade your audience using this Five Attributes Of Web Enabled Network For Telecommunication And Networks Guidelines PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Data Security, Faster Communication, Flexibility. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Illustration Of Global Success Key PowerPoint Templates Ppt Backgrounds For Slides 0213
We present our Illustration Of Global Success Key PowerPoint Templates PPT Backgrounds For Slides 0213.Present our Globe PowerPoint Templates because It can Conjure up grand ideas with our magical PowerPoint Templates and Slides. Leave everyone awestruck by the end of your presentation. Present our Earth PowerPoint Templates because Our PowerPoint Templates and Slides will Activate the energies of your audience. Get their creative juices flowing with your words. Present our Security PowerPoint Templates because you should Experience excellence with our PowerPoint Templates and Slides. They will take your breath away. Use our Success PowerPoint Templates because You can Channelise the thoughts of your team with our PowerPoint Templates and Slides. Urge them to focus on the goals you have set. Use our Future PowerPoint Templates because You are an avid believer in ethical practices. Highlight the benefits that accrue with our PowerPoint Templates and Slides.Use these PowerPoint slides for presentations relating to Global network with success key, globe, earth, success, future, security. The prominent colors used in the PowerPoint template are Green, Yellow, Gray.

Developing Firm Security Strategy Plan Information Security Process To Manage Firms Sensitive Data Introduction PDF
This slide provides information about information security process in order to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc. This is a developing firm security strategy plan information security process to manage firms sensitive data introduction pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like privileged password management, daily tasks performed by network administrator, network security audit checklist. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Project Security Administration IT Information Security Process To Manage Firms Sensitive Data Summary PDF
This slide provides information about information security process in order to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc. Deliver an awe inspiring pitch with this creative project security administration it information security process to manage firms sensitive data summary pdf bundle. Topics like privileged password management, daily tasks performed by network administrator, network security audit checklist can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Essential Pillars Of Cloud Security Brochure PDF
This slide shows the four essential pillars of cloud security, namely visibility and consistency, process-based security, network security, and identity security. This is a Essential Pillars Of Cloud Security Brochure PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Process Based Security, Network Security, Identity Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

SDN Security Architecture What Role Does SDN Play In Customer Security Mockup PDF
This slide represents the role of software defined networking in customer security. It allows clients to have separate settings for each type of network traffic and permits a low security public facing network for regular information. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. SDN Security Architecture What Role Does SDN Play In Customer Security Mockup PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
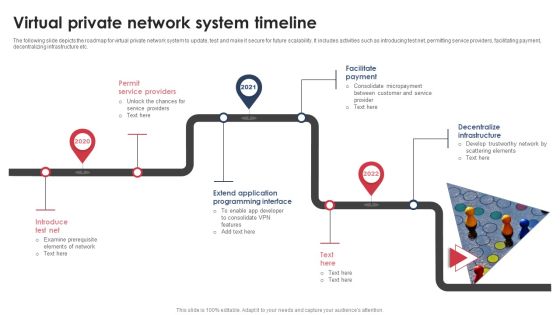
Virtual Private Network System Timeline Graphics PDF
The following slide depicts the roadmap for virtual private network system to update, test and make it secure for future scalability. It includes activities such as introducing test net, permitting service providers, facilitating payment, decentralizing infrastructure etc. Presenting Virtual Private Network System Timeline Graphics PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Permit Service Providers, Facilitate Payment, Decentralize Infrastructure. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cloud Information Security Key Cloud Security Use Cases Ppt Gallery Templates PDF
This slide represents the key use cases of cloud security namely privileged account access, data exfiltration, suspicious network connections, man-in-the-cloud attack, and unsecured storage containers. Deliver an awe inspiring pitch with this creative Cloud Information Security Key Cloud Security Use Cases Ppt Gallery Templates PDF bundle. Topics like Privileged Account, Data Exfiltration, Suspicious Network can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Business Diagrams Templates Umbrella And Symbol PowerPoint Ppt Backgrounds For Slides
We present our business diagrams templates umbrella and symbol PowerPoint PPT backgrounds for slides.Download and present our Security PowerPoint Templates because You canTake a leap off the starting blocks with our PowerPoint Templates and Slides. They will put you ahead of the competition in quick time. Download our Shapes PowerPoint Templates because Our PowerPoint Templates and Slides are Clear and concise. Use them and dispel any doubts your team may have. Present our Business PowerPoint Templates because our PowerPoint Templates and Slides are the string of your bow. Fire of your ideas and conquer the podium. Use our Internet PowerPoint Templates because Your success is our commitment. Our PowerPoint Templates and Slides will ensure you reach your goal. Present our Computer PowerPoint Templates because you can Set pulses racing with our PowerPoint Templates and Slides. They will raise the expectations of your team.Use these PowerPoint slides for presentations relating to 3d, Access, Business, Close, Computer, Concept, Connection, Data, Digital, Firewall, Global, Guard, Information, Internet, Laptop, Light, Metal, Network, Office, Online, Pc, Personal, Privacy, Protection, Render, Safe, Secure, Security, Shield, Sign, Silver, Steel, Success, Support, Symbol, Technology, Umbrella, Virus, Web. The prominent colors used in the PowerPoint template are Blue, White, Gray. Use our business diagrams templates umbrella and symbol PowerPoint PPT backgrounds for slides will get their audience's attention. We assure you our Digital PowerPoint templates and PPT Slides will get their audience's attention. Use our business diagrams templates umbrella and symbol PowerPoint PPT backgrounds for slides help you meet deadlines which are an element of today's workplace. Just browse and pick the slides that appeal to your intuitive senses. Customers tell us our Data PowerPoint templates and PPT Slides provide you with a vast range of viable options. Select the appropriate ones and just fill in your text. Presenters tell us our business diagrams templates umbrella and symbol PowerPoint PPT backgrounds for slides are aesthetically designed to attract attention. We guarantee that they will grab all the eyeballs you need. PowerPoint presentation experts tell us our Digital PowerPoint templates and PPT Slides will make you look like a winner.
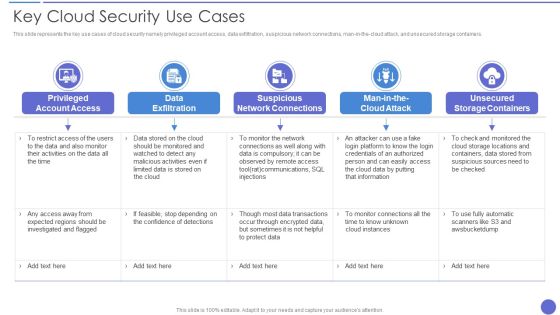
Key Cloud Security Use Cases Elements PDF
This slide represents the key use cases of cloud security namely privileged account access, data exfiltration, suspicious network connections, man in the cloud attack, and unsecured storage containers. Presenting Key Cloud Security Use Cases Elements PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Data Exfiltration, Suspicious Network Connections, Privileged Account Access. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Security Key Elements Of Data Security Ppt Pictures Show PDF
This slide represents the different elements of data security such as application security, network security, information security, etc. Presenting information security key elements of data security ppt pictures show pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like network security, application security, cloud security, operational security, information security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
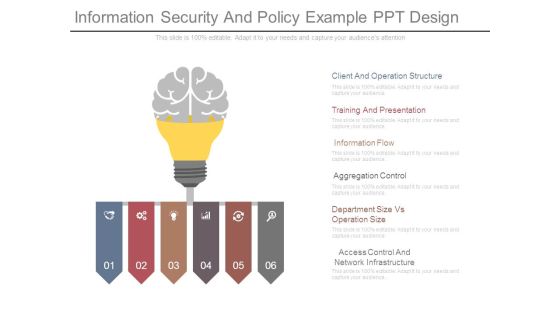
Information Security And Policy Example Ppt Design
This is a information security and policy example ppt design. This is a six stage process. The stages in this process are client and operation structure, training and presentation, information flow, aggregation control, department size vs operation size, access control and network infrastructure.

Securing Operations Of Logistics Through Integrated Iot Guidelines PDF
This slide showcases securing operations of logistics through integrated internet of things IoT. It provides details such as field network, automation network, process network, operations, operating system, remote access, etc. Deliver and pitch your topic in the best possible manner with this Securing Operations Of Logistics Through Integrated Iot Guidelines PDF. Use them to share invaluable insights on Iot Security System, Potential Impact, Warehouse and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Essential Pillars Of Cloud Security Cloud Computing Security IT Ppt Design Ideas PDF
This slide shows the four essential pillars of cloud security, namely visibility and consistency, process-based security, network security, and identity security. Presenting essential pillars of cloud security cloud computing security it ppt design ideas pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like visibility and consistency, process based security, network security, identity security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Market Network Expansion For Business Information Protection Sample PDF
This slide covers market network expansion for business network which includes allocated budget, security policy compliance, risk mitigation and audit. Showcasing this set of slides titled Market Network Expansion For Business Information Protection Sample PDF. The topics addressed in these templates are Business Security, Related Decision, Making Structure. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
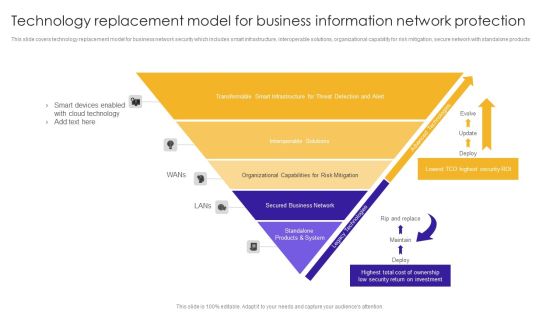
Technology Replacement Model For Business Information Network Protection Structure PDF
This slide covers technology replacement model for business network security which includes smart infrastructure, interoperable solutions, organizational capability for risk mitigation, secure network with standalone products.Showcasing this set of slides titled Technology Replacement Model For Business Information Network Protection Structure PDF. The topics addressed in these templates are Smart Devices, Cloud Technology, Transformable Smart. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cloud Information Security Essential Pillars Of Cloud Security Ppt File Elements PDF
This slide shows the four essential pillars of cloud security, namely visibility and consistency, process-based security, network security, and identity security. This is a Cloud Information Security Essential Pillars Of Cloud Security Ppt File Elements PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Network Security, Identity Security, Visibility Consistency. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Public And Private Cloud Network For Securing Data Stored From Various Source Icon Ppt PowerPoint Presentation Icon Backgrounds PDF
Presenting public and private cloud network for securing data stored from various source icon ppt powerpoint presentation icon backgrounds pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including public and private cloud network for securing data stored from various source icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Public And Private Cloud Network Icon With Secure User Information Ppt PowerPoint Presentation Infographic Template Skills PDF
Presenting public and private cloud network icon with secure user information ppt powerpoint presentation infographic template skills pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including public and private cloud network icon with secure user information. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
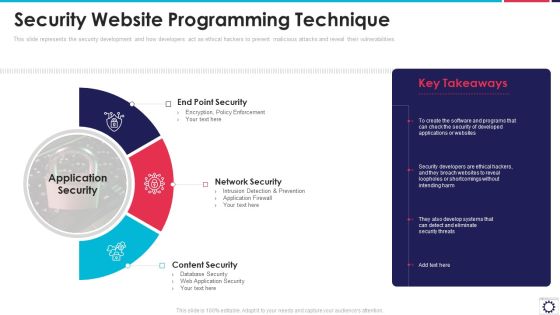
Website Programming IT Security Website Programming Technique Ppt PowerPoint Presentation File Infographics PDF
This slide represents the security development and how developers act as ethical hackers to prevent malicious attacks and reveal their vulnerabilities. Presenting website programming it security website programming technique ppt powerpoint presentation file infographics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like end point security, network security, content security, application security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Requirement Matrix For Integrating Physical Network With Virtual Network Sample PDF
This slides provides a matrix to understand interrelationship between the availability of features and the requirements for physical network in order to validate if physical network meets certain requirements for virtual features to be implemented.Deliver an awe inspiring pitch with this creative requirement matrix for integrating physical network with virtual network sample pdf bundle. Topics like metadata service, security groups, managed nonvlan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Checklist To Implement Cloud Security In Business Cloud Computing Security IT Ppt Infographic Template Example File
This slide shows the checklist to implement cloud security in business, including policies and procedures, access control, networking, backup data, security patches, etc. Deliver an awe inspiring pitch with this creative checklist to implement cloud security in business cloud computing security it ppt infographic template example file bundle. Topics like networking, policies and procedures, logging and monitoring, data encryption, security patches and updates can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Developing 5G Wireless Cellular Network Value Enabler 1 5G Resilient Networks System Clipart PDF
This slide provides details regarding value enabler for operator as 5G resilient networks system including importance and key components associated to it. This is a Developing 5G Wireless Cellular Network Value Enabler 1 5G Resilient Networks System Clipart PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Assurance, Service Availability, Protocols. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Content Delivery Network Edge Server Features Of Content Delivery Network Infographics PDF
This slide explains the features of content delivery networks such as protection against DDoS protection, HTTPS services, analytics, etc. Presenting Content Delivery Network Edge Server Features Of Content Delivery Network Infographics PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Measures, Advanced Security, Service. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Overview Of Security Operations Centre Sample PDF
This slide provides information regarding the overview of security operations center associated with firms business units, management, steering committee, external and internal system.Deliver and pitch your topic in the best possible manner with this overview of security operations centre sample pdf. Use them to share invaluable insights on command and control, network security monitoring, threat intelligence and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
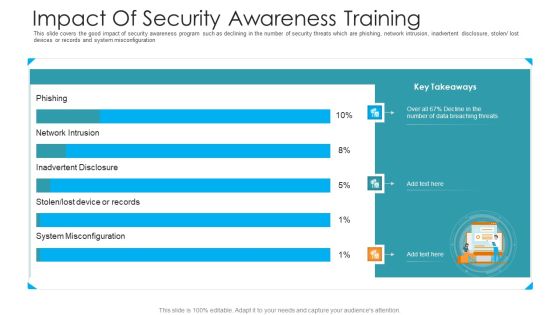
Impact Of Security Awareness Training Hacking Prevention Awareness Training For IT Security Infographics PDF
This slide covers the good impact of security awareness program such as declining in the number of security threats which are phishing, network intrusion, inadvertent disclosure, stolen or lost devices or records and system misconfiguration. Deliver an awe inspiring pitch with this creative impact of security awareness training hacking prevention awareness training for it security infographics pdf bundle. Topics like system misconfiguration, network intrusion breakdown, phishing breakdown can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

 Home
Home