Corporate Risk

Core Problem Intermediate Cause Ppt Background
This is a core problem intermediate cause ppt background. This is a four stage process. The stages in this process are problem core, problem diagram, in depth cause, problem core.

Checklist To Manage Agile Threat Modelling Ppt File Demonstration PDF
This slide provides information regarding checklist to handle the agile threat model by managing focus areas such as threat analysis, collaboration with delivery team, issues prioritization and resolution, project wrapping up and closure, etc. Create an editable Checklist To Manage Agile Threat Modelling Ppt File Demonstration PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Checklist To Manage Agile Threat Modelling Ppt File Demonstration PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Checklist To Manage Agile Threat Modelling Ppt Show Template PDF
This slide provides information regarding checklist to handle the agile threat model by managing focus areas such as threat analysis, collaboration with delivery team, issues prioritization and resolution, project wrapping up and closure, etc. Create an editable Checklist To Manage Agile Threat Modelling Ppt Show Template PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Checklist To Manage Agile Threat Modelling Ppt Show Template PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Cyber Safety Incident Management Determine Threat Scenario Analysis Background PDF
This slide provides details regarding threat scenario assessment by understanding various phases of threat actor attack on victim. Presenting cyber safety incident management determine threat scenario analysis background pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like determine threat scenario analysis. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Internet Security Threat Analysis Requirements And Goals Ideas PDF
This slide exhibits data breach security requirement with major goals and requirements. It includes multiple section like- securing cardholder data, manage vulnerability program and so on. Showcasing this set of slides titled internet security threat analysis requirements and goals ideas pdf. The topics addressed in these templates are internet security threat analysis requirements and goals. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Threat And Vulnerability Administration Plan Analysis Dashboard Slides PDF
This slide defines the dashboard for analyzing the threat and vulnerability program. It includes information related to the exposure, configuration and severity score. Showcasing this set of slides titled Threat And Vulnerability Administration Plan Analysis Dashboard Slides PDF. The topics addressed in these templates are Exposure Score, Configuration Score, Severity Distribution. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Overview Of Key Insights From Cyber Threat Statistics Themes PDF
This slide covers statistics based on cyber crime trends. It includes stats on data thefts, mobile securities, security skills, data breach cost, etc. Showcasing this set of slides titled Overview Of Key Insights From Cyber Threat Statistics Themes PDF. The topics addressed in these templates are Overview Of Key Insights, Cyber Threat Statistics . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Intelligence Architecture For Comprehensive Threat Evaluation Mockup PDF
This slide depicts an system architecture for complete threat evaluation using cyber intelligence to control the number of cyber-attacks. It includes testing methods, functions, categories, items and properties. Showcasing this set of slides titled Intelligence Architecture For Comprehensive Threat Evaluation Mockup PDF. The topics addressed in these templates are Performance, Timeliness, Customization. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Problem Solving In Business Layout Powerpoint Slide Show
This is a problem solving in business layout powerpoint slide show. This is a three stage process. The stages in this process are problem, idea, solution.

SWOT Analysis Of HCL Plus Logistics Company Threats Rules PDF
This slide shows some threats that may effect the company in future course of time and impact the company profits. Some potential threats are Intense Competition from Rivalries , Rising Fuel Costs , Government Regulations and Currency Fluctuations etc. Deliver and pitch your topic in the best possible manner with this swot analysis of hcl plus logistics company threats rules pdf. Use them to share invaluable insights on technologies, market, technology, costs, customer and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security Operations Framework To Monitor Security Threats Demonstration PDF
This slide display security operations threat detection and eradication process in order to increase security at all stages of development. It includes new security incident, response to threat, root cause analysis, etc. Pitch your topic with ease and precision using this Security Operations Framework To Monitor Security Threats Demonstration PDF. This layout presents information on Execute Mitigation, Develop, Strategy. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Ppt Slides Business Roadblocks Ahead Traffic Cones PowerPoint Templates
PPT_Slides_Business_RoadBlocks_Ahead_Traffic_Cones_PowerPoint_templates-These high quality powerpoint pre-designed slides and powerpoint templates have been carefully created by our professional team to help you impress your audience. All slides have been created and are 100% editable in powerpoint. Each and every property of any graphic - color, size, orientation, shading, outline etc. can be modified to help you build an effective powerpoint presentation. Any text can be entered at any point in the powerpoint template or slide. Simply DOWNLOAD, TYPE and PRESENT! These PowerPoint presentation slides can be used to represent themes relating to --3d, alert, attention, background, barrier, boundary, bright, build, caution, color, cone, construction, danger, drawing, equipment, forbidden, highway, icon, illustration, object, obstacle, plastic, reflection, repair, road, safety, security, shadow, shape, sign, signal, site, stop, street, striped, symbol, traffic, transportation, warning, work-PPT_Slides_Business_RoadBlocks_Ahead_Traffic_Cones_PowerPoint_templates
Icons Slide For Threat Management At Workplace Elements Pdf
Introducing our well designed icons slide for threat management at workplace elements pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.

Threat Management Model With Performance Strategy Topics PDF
Showcasing this set of slides titled Threat Management Model With Performance Strategy Topics PDF. The topics addressed in these templates are Monthly Performance Plan, Weekly Performance Plan, Annual Performance Plan. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Problem Template 2 Ppt PowerPoint Presentation Picture
This is a problem template 2 ppt powerpoint presentation picture. This is a two stage process. The stages in this process are first problem, second problem.

6 Stage Process For Prevention Of Work Mishap To Optimize Production Rate Background PDF
This slide signifies the stages on prevention and measurement on maintain workforce environment. It includes steps like hazard assessment, accident investigation, policies, training, measurement and management commitment Persuade your audience using this 6 Stage Process For Prevention Of Work Mishap To Optimize Production Rate Background PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Hazard Assessment, Investigation, Policies Procedures. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Organizational Security Solutions Contingency Plan For Threat Handling Pictures PDF
This slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations. Deliver an awe inspiring pitch with this creative organizational security solutions contingency plan for threat handling pictures pdf bundle. Topics like contingency considerations, mainframe systems, security, implementation, technologies integration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
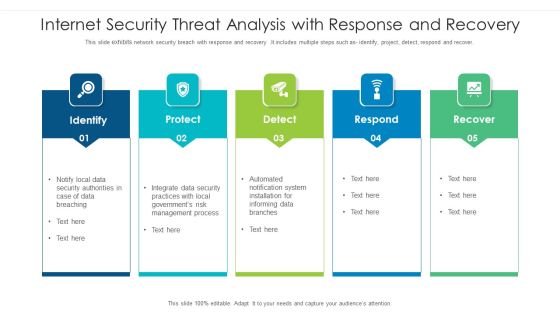
Internet Security Threat Analysis With Response And Recovery Information PDF
This slide exhibits network security breach with response and recovery .It includes multiple steps such as- identify, project, detect, respond and recover. Pitch your topic with ease and precision using this internet security threat analysis with response and recovery information pdf. This layout presents information on internet security threat analysis with response and recovery. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Key Security Considerations For 5G For Threat Handling Elements PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver an awe inspiring pitch with this creative Key Security Considerations For 5G For Threat Handling Elements PDF bundle. Topics like System Configuration, Security Policies, Information Interception can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
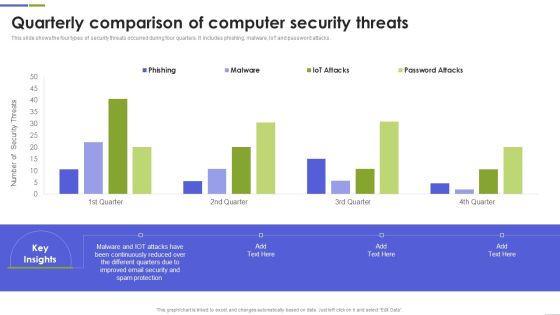
Quarterly Comparison Of Computer Security Threats Mockup PDF
This slide shows the four types of security threats occurred during four quarters. It includes phishing, malware, IoT and password attacks. Pitch your topic with ease and precision using this Quarterly Comparison Of Computer Security Threats Mockup PDF This layout presents information on Continuously Reduced, Different Quarters, Spam Protection It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Key Security Considerations For 5G For Threat Handling Icons PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver and pitch your topic in the best possible manner with this Key Security Considerations For 5G For Threat Handling Icons PDF. Use them to share invaluable insights on Denial Of Service, Information Interception, Application Plane Data and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
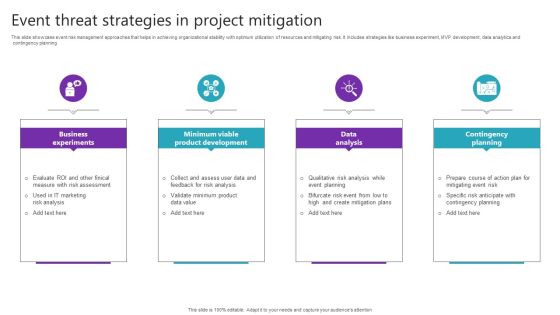
Event Threat Strategies In Project Mitigation Diagrams PDF
Presenting Event Threat Strategies In Project Mitigation Diagrams PDF to dispense important information. This template comprises Four stages. It also presents valuable insights into the topics including Business Experiments, Minimum Viable, Product Development. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

How To Intensify Project Threats Path Of Issue Resolution Rules PDF
This is a how to intensify project threats path of issue resolution rules pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like normal day to day business, problem solving, issues escalation process. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Business Problem Solving Case Studies Powerpoint Slide Ideas
This is a business problem solving case studies powerpoint slide ideas. This is a three stage process. The stages in this process are problem, solution, results.
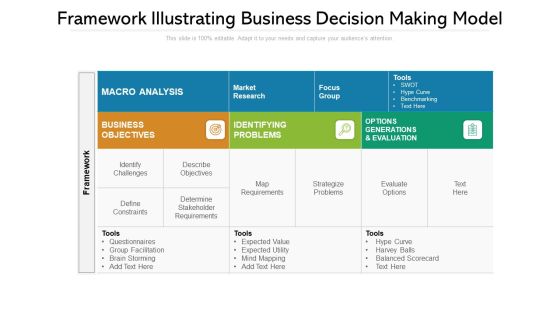
Framework Illustrating Problem Solving Model Rules PDF
Showcasing this set of slides titled framework illustrating problem solving model rules pdf. The topics addressed in these templates are market research, macro analysis, business objectives, determine stakeholder requirements. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
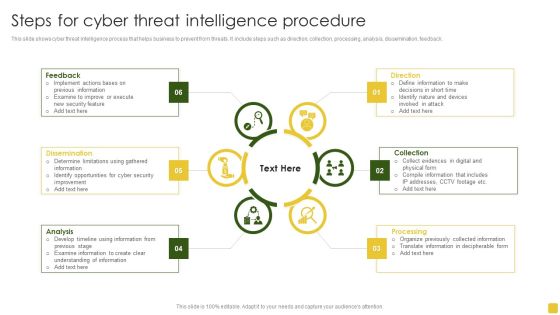
Steps For Cyber Threat Intelligence Procedure Ideas PDF
This slide shows cyber threat intelligence process that helps business to prevent from threats. It include steps such as direction, collection, processing, analysis, dissemination, feedback.Persuade your audience using this Steps For Cyber Threat Intelligence Procedure Ideas PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Previous Information, Examine Improve, Determine Limitations. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Puzzle Problem Ppt PowerPoint Presentation Icon Outline
This is a puzzle problem ppt powerpoint presentation icon outline. This is a five stage process. The stages in this process are puzzle, solution, problem, marketing, management.
Puzzle Solution Problem Ppt PowerPoint Presentation Information
This is a puzzle solution problem ppt powerpoint presentation information. This is a four stage process. The stages in this process are puzzle, solution, problem, marketing, management.

Recognition And Threat Ppt PowerPoint Presentation Complete With Slides
This Recognition And Threat Ppt PowerPoint Presentation Complete With Slides acts as backup support for your ideas, vision, thoughts, etc. Use it to present a thorough understanding of the topic. This PPT slideshow can be utilized for both in-house and outside presentations depending upon your needs and business demands. Entailing eleven slides with a consistent design and theme, this template will make a solid use case. As it is intuitively designed, it suits every business vertical and industry. All you have to do is make a few tweaks in the content or any other component to design unique presentations. The biggest advantage of this complete deck is that it can be personalized multiple times once downloaded. The color, design, shapes, and other elements are free to modify to add personal touches. You can also insert your logo design in this PPT layout. Therefore a well-thought and crafted presentation can be delivered with ease and precision by downloading this Recognition And Threat Ppt PowerPoint Presentation Complete With Slides PPT slideshow.
Major Threat Icon Ppt PowerPoint Presentation Complete Deck With Slides
This Major Threat Icon Ppt PowerPoint Presentation Complete Deck With Slides acts as backup support for your ideas, vision, thoughts, etc. Use it to present a thorough understanding of the topic. This PPT slideshow can be utilized for both in-house and outside presentations depending upon your needs and business demands. Entailing Twelve slides with a consistent design and theme, this template will make a solid use case. As it is intuitively designed, it suits every business vertical and industry. All you have to do is make a few tweaks in the content or any other component to design unique presentations. The biggest advantage of this complete deck is that it can be personalized multiple times once downloaded. The color, design, shapes, and other elements are free to modify to add personal touches. You can also insert your logo design in this PPT layout. Therefore a well-thought and crafted presentation can be delivered with ease and precision by downloading this Major Threat Icon Ppt PowerPoint Presentation Complete Deck With Slides PPT slideshow.

Threats Associated With Service Quality Ppt PowerPoint Presentation Layouts
This is a threats associated with service quality ppt powerpoint presentation layouts. This is a four stage process. The stages in this process are customer expectation often change, each customer contact is a moment of truth.

Cybersecurity Operations Cybersecops Security Operations Threat Management Brochure PDF
This slide depicts the security operations threat management process. The purpose of this slide is to showcase the various stages and operations included in the security operations threat management process. The steps include discovery, preliminary investigation, triage, extended investigation, and contain and respond. The Cybersecurity Operations Cybersecops Security Operations Threat Management Brochure PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
Threat Intelligence System Architecture For Reliable Data Collection Pictures PDF
This slide represents an architecture for gathering reliable data and sustainable computing based on a block chain proposed cyber threat intelligence framework . It includes three layers device, feed and cloud. Showcasing this set of slides titled Threat Intelligence System Architecture For Reliable Data Collection Pictures PDF. The topics addressed in these templates are Cloud Server, Accurate Information Storing, Open Source Service. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Solution Problem Business PowerPoint Templates And PowerPoint Themes 0612
Solution Problem Business PowerPoint Templates And PowerPoint Themes Business-Microsoft Powerpoint Templates and Background with red and green puzzle pieces

Cyber Security Automation Framework Time To Fix Security Threat With Manual Testing Inspiration PDF
This slide highlights the time to fix the security threat and error with manual testing in bar graph format. It covers key takeaways which explains how much percent of error are fixed in 1 to 3 hour, 3 to 6 hour and working day etc. This Cyber Security Automation Framework Time To Fix Security Threat With Manual Testing Inspiration PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Cyber Security Automation Framework Time To Fix Security Threat With Manual Testing Inspiration PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, don not wait, grab the presentation templates today.

Business Consulting Architecture With Problem Driven Approach Summary PDF
This template covers about identification of problem, building problem driven structure, lead analysis to provide recommendations. Pitch your topic with ease and precision using this Business Consulting Architecture With Problem Driven Approach Summary PDF. This layout presents information on Identify Problem, Problem Driven Structure, Lead Analysis. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Porters 5 Force Analysis Threat Ppt PowerPoint Presentation Gallery Deck
Presenting this set of slides with name porters 5 force analysis threat ppt powerpoint presentation gallery deck. This is a five stage process. The stages in this process are threat of new entrants, bargaining power of suppliers, bargaining power of buyers, threat substitute products or services, rivalry among existing competitors. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

SIEM Threat Intelligence Services Ppt Layouts Background PDF
This slide covers the threat intelligence services such as global intelligence, local intelligence, and other effective threat detection services. Presenting siem threat intelligence services ppt layouts background pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Local Intelligence, Global Intelligence, Other Services. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Swot Analysis Of Adc Cosmetics Company Threats Guidelines PDF
This slide shows some threats that may effect the company in future course of time and impact the company profits. Some potential threats are Intense Competition from Similar Companies , Changes in Consumer Demand and Preferences , Government Regulations and Currency Fluctuations etc. This is a swot analysis of adc cosmetics company threats guidelines pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like intense competition, consumer demand, currency fluctuations, threat. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
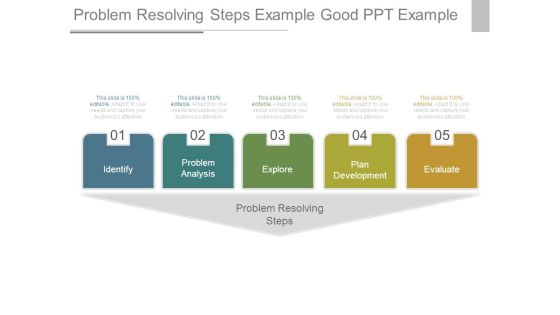
Problem Resolving Steps Example Good Ppt Example
This is a problem resolving steps example good ppt example. This is a five stage process. The stages in this process are identify, problem analysis, explore, plan development, evaluate, problem resolving steps.

Dropbox Fundraising Elevator The Problem Ideas PDF
Deliver and pitch your topic in the best possible manner with this dropbox fundraising elevator the problem ideas pdf. Use them to share invaluable insights on the problem and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Real Time Assessment Of Security Threats Table Of Contents Real Time Assessment Of Security Threats Mockup PDF
Deliver an awe inspiring pitch with this creative real time assessment of security threats table of contents real time assessment of security threats mockup pdf bundle. Topics like company overview, challenges and solutions, services offered, siem hosting models, siem architecture can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
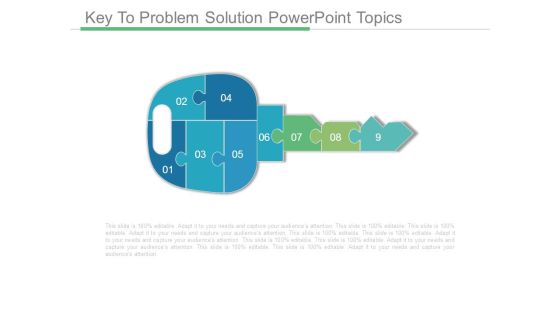
Key To Problem Solution Powerpoint Topics
This is a key to problem solution powerpoint topics. This is a nine stage process. The stages in this process are key, problem, solution, security, presentation.

Internet Security Threat Analysis Report Chart Introduction PDF
Following slide exhibits security and data breach report chart it includes major statistics such as- loss or theft of data, failure to redirect data and data posting to incorrect recipient. Pitch your topic with ease and precision using this internet security threat analysis report chart introduction pdf. This layout presents information on internet security threat analysis report chart. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Process For Responding To Internet Security Threats Template PDF
This slide exhibits process for responding to security data breach. It includes multiple steps such as- analyzing the current damage, keeping record how much damage is caused and so on. Pitch your topic with ease and precision using this process for responding to internet security threats template pdf. This layout presents information on process for responding to internet security threats. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Problem Solution Business PowerPoint Templates And PowerPoint Themes 0612
Problem Solution Business PowerPoint Templates And PowerPoint Themes PPT Slides-Microsoft Powerpoint Templates and Background with signpost about success and failure
Display Marketing Business Problem Ppt Powerpoint Presentation Icon Samples Cpb
This is a display marketing business problem ppt powerpoint presentation icon samples cpb. This is a five stage process. The stages in this process are display marketing business problem.

Problem Business PowerPoint Templates And PowerPoint Backgrounds 0811
Microsoft PowerPoint Template and Background with attacking problems solving techniques asking questions

Threats And Vulnerability Administration Plan Process Guidelines PDF
This slide defines the functions and process adopted by the threats and vulnerability management program. It includes information related to identifying, evaluating, treating and reporting vulnerabilities. Presenting Threats And Vulnerability Administration Plan Process Guidelines PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Evaluating Vulnerabilities, Reporting Vulnerabilities, Treating Vulnerabilities, Identifying Vulnerabilities. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

SWOT Strength Threats Ppt PowerPoint Presentation Inspiration Clipart Images
Presenting this set of slides with name swot strength threats ppt powerpoint presentation inspiration clipart images. This is a four stage process. The stages in this process are swot, strength, weakness, opportunities, threats. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Swot Strength Threat Ppt PowerPoint Presentation File Master Slide
Presenting this set of slides with name swot strength threat ppt powerpoint presentation file master slide. This is a four stage process. The stages in this process are swot, strength, weakness, opportunities, threat. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
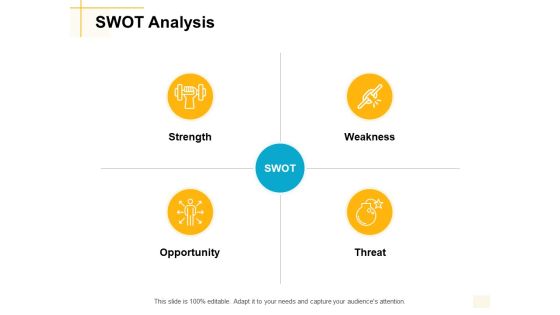
Swot Analysis Threat Ppt PowerPoint Presentation Infographics Guide
Presenting this set of slides with name swot analysis threat ppt powerpoint presentation infographics guide. This is a four stage process. The stages in this process are strength, opportunity, weakness, threat, marketing. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

SWOT Strength Threat Ppt PowerPoint Presentation Gallery Introduction
Presenting this set of slides with name swot strength threat ppt powerpoint presentation gallery introduction. This is a four stage process. The stages in this process are swot, strength, weakness, opportunities, threats. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Threat Management Ppt PowerPoint Presentation Topics Cpb
Presenting this set of slides with name cyber threat management ppt powerpoint presentation topics cpb. This is a four stage process. The stages in this process are cyber threat management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

SWOT Analyses Threats Ppt PowerPoint Presentation Slides Background Designs
Presenting this set of slides with name swot analyses threats ppt powerpoint presentation slides background designs. This is a four stage process. The stages in this process are strength, weakness, opportunity, threats. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Crime Hacking Technology Threats Ppt PowerPoint Presentation Layouts Example
Presenting this set of slides with name cyber crime hacking technology threats ppt powerpoint presentation layouts example. This is a one stage process. The stage in this process is cyber crime hacking technology threats. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Internet Security Threat Icon On Computer Elements PDF
Presenting internet security threat icon on computer elements pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including internet security threat icon on computer. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Functional Technology Icon For Security Threat Detection Structure PDF
Presenting functional technology icon for security threat detection structure pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including functional technology icon for security threat detection. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
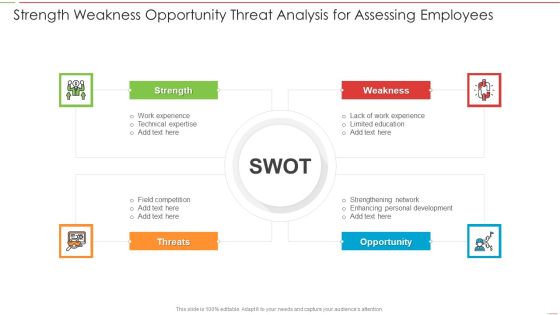
Strength Weakness Opportunity Threat Analysis For Assessing Employees Information PDF
Presenting Strength Weakness Opportunity Threat Analysis For Assessing Employees Information PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Strength, Weakness, Threats, Opportunity. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Strength Weakness Opportunity Threat Analysis For Marketing Growth Ideas PDF
Presenting Strength Weakness Opportunity Threat Analysis For Marketing Growth Ideas PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Strength, Weakness, Threats, Opportunity. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
 Home
Home