AI PPT Maker
Templates
PPT Bundles
Design Services
Business PPTs
Business Plan
Management
Strategy
Introduction PPT
Roadmap
Self Introduction
Timelines
Process
Marketing
Agenda
Technology
Medical
Startup Business Plan
Cyber Security
Dashboards
SWOT
Proposals
Education
Pitch Deck
Digital Marketing
KPIs
Project Management
Product Management
Artificial Intelligence
Target Market
Communication
Supply Chain
Google Slides
Research Services
 One Pagers
One PagersAll Categories
-
Home
- Customer Favorites
- Construction Safety
Construction Safety

Web Tools To Prevent Cyber Security Attack Ppt Summary Graphic Tips PDF
This slide defines the web tools to prevent from cyber attacks. It includes information related to different softwares, features and description. Showcasing this set of slides titled Web Tools To Prevent Cyber Security Attack Ppt Summary Graphic Tips PDF. The topics addressed in these templates are Software Tools, Solarwinds Identity Monitor, Free Tool. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Table Of Contents Organizations Risk Management And IT Security Workplace Elements PDF
If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Table Of Contents Organizations Risk Management And IT Security Workplace Elements PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.

Table Of Contents For Business Mobile Device Security Management And Mitigation Tips Pictures PDF
If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Table Of Contents For Business Mobile Device Security Management And Mitigation Tips Pictures PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.

Table Of Contents Fordeploying Cyber Security Incident Response Administration Structure PDF
If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Table Of Contents Fordeploying Cyber Security Incident Response Administration Structure PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.

Table Of Contents For Information Systems Security And Risk Management Plan Brochure PDF
If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Table Of Contents For Information Systems Security And Risk Management Plan Brochure PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Information Systems Security And Risk Management Plan Our Mission Infographics PDF
The Information Systems Security And Risk Management Plan Our Mission Infographics PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Enterprise Resource Planning Assessment Model To Improve Cyber Security Performance Guidelines PDF
This slide signifies the enterprise resource planning skill evaluation to increase employee productivity. It covers information about grouping, technology ,process and functional related. Showcasing this set of slides titled Enterprise Resource Planning Assessment Model To Improve Cyber Security Performance Guidelines PDF. The topics addressed in these templates are Regular Major Releases, Application Scanner, Implement Assessment. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
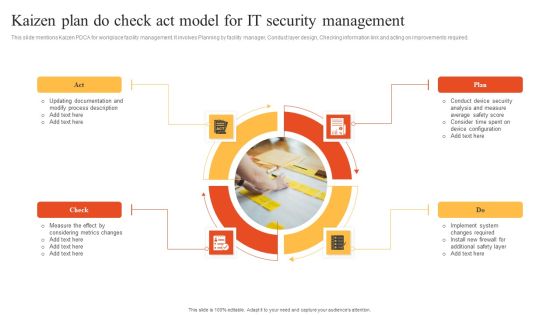
Kaizen Plan Do Check Act Model For IT Security Management Information PDF
This slide mentions Kaizen PDCA for workplace facility management. It involves Planning by facility manager, Conduct layer design, Checking information link and acting on improvements required. Presenting Kaizen Plan Do Check Act Model For IT Security Management Information PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Check, Plan, Act. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Table Of Contents For Securing Market Leadership Through Competitive Excellence Demonstration PDF
If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Table Of Contents For Securing Market Leadership Through Competitive Excellence Demonstration PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.

Table Of Contents Development And Integration Of Cyber Security Incident Administration Portrait PDF
If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Table Of Contents Development And Integration Of Cyber Security Incident Administration Portrait PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Table Of Contents For Implementing Cyber Security Incident Management Guidelines PDF
If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Table Of Contents For Implementing Cyber Security Incident Management Guidelines PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Enhancing Cloud Security With CASB Table Of Contents Ppt PowerPoint Presentation File Backgrounds PDF
This Enhancing Cloud Security With CASB Table Of Contents Ppt PowerPoint Presentation File Backgrounds PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The product features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Factors To Be Considered Before Selecting Information Technology Process Automation Brochure PDF
This slide showcases elements to think about before choosing automation solution. This template aims on deploying IT services in systematic manner and improving efficiency throughout organization. It covers aspects such as security, user-interface, etc. Persuade your audience using this Factors To Be Considered Before Selecting Information Technology Process Automation Brochure PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Understanding Organizational Needs, User Friendly Interface Design, Security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Business Charts For Portfolio Evaluation Powerpoint Slide Designs Download
This is a business charts for portfolio evaluation powerpoint slide designs download. This is a five stage process. The stages in this process are peso govt debt securities, foreign govt debt securities, peso corporate debt securities, dollar corporate debt securities, equity.

Capital Raising Pitch Presentation Competitive Landscape For LBS App Designs PDF
Following slide differentiates the offering of companies with its competitors based on self-service features namely secure login, reward codes, customer support and popup notifications. Deliver and pitch your topic in the best possible manner with this Capital Raising Pitch Presentation Competitive Landscape For LBS App Designs PDF. Use them to share invaluable insights on Location Based Services, Offline Access To Content, Customer Support, Popup Notifications and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Industrial Security System For Large Areas Technology Process Ppt PowerPoint Presentation Complete Deck
Boost your confidence and team morale with this well-structured industrial security system for large areas technology process ppt powerpoint presentation complete deck. This prefabricated set gives a voice to your presentation because of its well-researched content and graphics. Our experts have added all the components very carefully, thus helping you deliver great presentations with a single click. Not only that, it contains a set of eleven slides that are designed using the right visuals, graphics, etc. Various topics can be discussed, and effective brainstorming sessions can be conducted using the wide variety of slides added in this complete deck. Apart from this, our PPT design contains clear instructions to help you restructure your presentations and create multiple variations. The color, format, design anything can be modified as deemed fit by the user. Not only this, it is available for immediate download. So, grab it now.

Security Model Awareness Management Ppt PowerPoint Presentation Complete Deck With Slides
Boost your confidence and team morale with this well-structured security model awareness management ppt powerpoint presentation complete deck with slides. This prefabricated set gives a voice to your presentation because of its well-researched content and graphics. Our experts have added all the components very carefully, thus helping you deliver great presentations with a single click. Not only that, it contains a set of eleven slides that are designed using the right visuals, graphics, etc. Various topics can be discussed, and effective brainstorming sessions can be conducted using the wide variety of slides added in this complete deck. Apart from this, our PPT design contains clear instructions to help you restructure your presentations and create multiple variations. The color, format, design anything can be modified as deemed fit by the user. Not only this, it is available for immediate download. So, grab it now.

Security Governance Procedure Management Plan Ppt PowerPoint Presentation Complete Deck With Slides
Boost your confidence and team morale with this well-structured security governance procedure management plan ppt powerpoint presentation complete deck with slides. This prefabricated set gives a voice to your presentation because of its well-researched content and graphics. Our experts have added all the components very carefully, thus helping you deliver great presentations with a single click. Not only that, it contains a set of twelve slides that are designed using the right visuals, graphics, etc. Various topics can be discussed, and effective brainstorming sessions can be conducted using the wide variety of slides added in this complete deck. Apart from this, our PPT design contains clear instructions to help you restructure your presentations and create multiple variations. The color, format, design anything can be modified as deemed fit by the user. Not only this, it is available for immediate download. So, grab it now.

Supplier Risk Assessment In Procurement Information Security Ppt PowerPoint Presentation Complete Deck With Slides
Boost your confidence and team morale with this well-structured supplier risk assessment in procurement information security ppt powerpoint presentation complete deck with slides. This prefabricated set gives a voice to your presentation because of its well-researched content and graphics. Our experts have added all the components very carefully, thus helping you deliver great presentations with a single click. Not only that, it contains a set of ninteen slides that are designed using the right visuals, graphics, etc. Various topics can be discussed, and effective brainstorming sessions can be conducted using the wide variety of slides added in this complete deck. Apart from this, our PPT design contains clear instructions to help you restructure your presentations and create multiple variations. The color, format, design anything can be modified as deemed fit by the user. Not only this, it is available for immediate download. So, grab it now.

Employee Security Coaching Matrix Ppt PowerPoint Presentation Complete Deck With Slides
Boost your confidence and team morale with this well-structured employee security coaching matrix ppt powerpoint presentation complete deck with slides. This prefabricated set gives a voice to your presentation because of its well-researched content and graphics. Our experts have added all the components very carefully, thus helping you deliver great presentations with a single click. Not only that, it contains a set of twelve slides that are designed using the right visuals, graphics, etc. Various topics can be discussed, and effective brainstorming sessions can be conducted using the wide variety of slides added in this complete deck. Apart from this, our PPT design contains clear instructions to help you restructure your presentations and create multiple variations. The color, format, design anything can be modified as deemed fit by the user. Not only this, it is available for immediate download. So, grab it now.

Hotel Protection And Security Ppt PowerPoint Presentation Complete Deck With Slides
Boost your confidence and team morale with this well-structured Hotel Protection And Security Ppt PowerPoint Presentation Complete Deck With Slides. This prefabricated set gives a voice to your presentation because of its well-researched content and graphics. Our experts have added all the components very carefully, thus helping you deliver great presentations with a single click. Not only that, it contains a set of eleven slides that are designed using the right visuals, graphics, etc. Various topics can be discussed, and effective brainstorming sessions can be conducted using the wide variety of slides added in this complete deck. Apart from this, our PPT design contains clear instructions to help you restructure your presentations and create multiple variations. The color, format, design anything can be modified as deemed fit by the user. Not only this, it is available for immediate download. So, grab it now.

Information Technology Security Program Ppt PowerPoint Presentation Complete Deck With Slides
Boost your confidence and team morale with this well-structured Information Technology Security Program Ppt PowerPoint Presentation Complete Deck With Slides. This prefabricated set gives a voice to your presentation because of its well-researched content and graphics. Our experts have added all the components very carefully, thus helping you deliver great presentations with a single click. Not only that, it contains a set of twelve slides that are designed using the right visuals, graphics, etc. Various topics can be discussed, and effective brainstorming sessions can be conducted using the wide variety of slides added in this complete deck. Apart from this, our PPT design contains clear instructions to help you restructure your presentations and create multiple variations. The color, format, design anything can be modified as deemed fit by the user. Not only this, it is available for immediate download. So, grab it now.

Security For Cloud Based Systems Ppt PowerPoint Presentation Complete Deck With Slides
Boost your confidence and team morale with this well structured Security For Cloud Based Systems Ppt PowerPoint Presentation Complete Deck With Slides. This prefabricated set gives a voice to your presentation because of its well researched content and graphics. Our experts have added all the components very carefully, thus helping you deliver great presentations with a single click. Not only that, it contains a set of seventeen slides that are designed using the right visuals, graphics, etc. Various topics can be discussed, and effective brainstorming sessions can be conducted using the wide variety of slides added in this complete deck. Apart from this, our PPT design contains clear instructions to help you restructure your presentations and create multiple variations. The color, format, design anything can be modified as deemed fit by the user. Not only this, it is available for immediate download. So, grab it now.

IT Security Risk Management Ppt PowerPoint Presentation Complete Deck With Slides
Boost your confidence and team morale with this well-structured IT Security Risk Management Ppt PowerPoint Presentation Complete Deck With Slides. This prefabricated set gives a voice to your presentation because of its well-researched content and graphics. Our experts have added all the components very carefully, thus helping you deliver great presentations with a single click. Not only that, it contains a set of twelve slides that are designed using the right visuals, graphics, etc. Various topics can be discussed, and effective brainstorming sessions can be conducted using the wide variety of slides added in this complete deck. Apart from this, our PPT design contains clear instructions to help you restructure your presentations and create multiple variations. The color, format, design anything can be modified as deemed fit by the user. Not only this, it is available for immediate download. So, grab it now.

Data Security Audit Questionnaire Ppt PowerPoint Presentation Complete Deck With Slides Survey
Boost your confidence and team morale with this well-structured Data Security Audit Questionnaire Ppt PowerPoint Presentation Complete Deck With Slides Survey. This prefabricated set gives a voice to your presentation because of its well-researched content and graphics. Our experts have added all the components very carefully, thus helping you deliver great presentations with a single click. Not only that, it contains a set of six slides that are designed using the right visuals, graphics, etc. Various topics can be discussed, and effective brainstorming sessions can be conducted using the wide variety of slides added in this complete deck. Apart from this, our PPT design contains clear instructions to help you restructure your presentations and create multiple variations. The color, format, design anything can be modified as deemed fit by the user. Not only this, it is available for immediate download. So, grab it now.

Piggy Bank Secured With Padlock Finance PowerPoint Templates Ppt Backgrounds For Slides 1212
We present our Piggy Bank Secured With Padlock Business Finance PowerPoint Templates PPT Backgrounds For Slides 1212.Download and present our Business PowerPoint Templates because you have secured a name for yourself in the domestic market. Now the time is right to spread your reach to other countries. Download and present our Marketing PowerPoint Templates because networking is an imperative in todays world. You need to access the views of others. Similarly you need to give access to them of your abilities. Download our Future PowerPoint Templates because you must Evolve the strategy to take you down the required path with appropriate, efficient and effective marketing along the way. Use our Finance PowerPoint Templates because let this slide illustrates others piggyback on you to see well over the horizon. Use our Targets PowerPoint Templates because this is Aesthetically designed to make a great first impression this template highlights .Use these PowerPoint slides for presentations relating to Piggy bank secured with padlock and chain, business, marketing, finance, targets, future. The prominent colors used in the PowerPoint template are Red, White, Black. We assure you our Piggy Bank Secured With Padlock Business Finance PowerPoint Templates PPT Backgrounds For Slides 1212 are Youthful. Customers tell us our padlock PowerPoint templates and PPT Slides are Exuberant. You can be sure our Piggy Bank Secured With Padlock Business Finance PowerPoint Templates PPT Backgrounds For Slides 1212 are Wistful. People tell us our business PowerPoint templates and PPT Slides are Great. Presenters tell us our Piggy Bank Secured With Padlock Business Finance PowerPoint Templates PPT Backgrounds For Slides 1212 are Striking. People tell us our chain PowerPoint templates and PPT Slides are One-of-a-kind.

Padlock On Laptop Internet Security PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Padlock On Laptop Internet Security PowerPoint Templates PPT Backgrounds For Slides 0113.Download our Technology PowerPoint Templates because It will Give impetus to the hopes of your colleagues. Our PowerPoint Templates and Slides will aid you in winning their trust. Download our Internet PowerPoint Templates because It can Bubble and burst with your ideas. Use our Computer PowerPoint Templates because You can Zap them with our PowerPoint Templates and Slides. See them reel under the impact. Download and present our Shapes PowerPoint Templates because you can Add colour to your speech with our PowerPoint Templates and Slides. Your presentation will leave your audience speechless. Download our Network diagrams PowerPoint Templates because You should Press the right buttons with our PowerPoint Templates and Slides. They will take your ideas down the perfect channel.Use these PowerPoint slides for presentations relating to protect your computer, security concept, network diagrams, technology, computer, internet, shapes. The prominent colors used in the PowerPoint template are Blue, Gray, Yellow. PowerPoint presentation experts tell us our Padlock On Laptop Internet Security PowerPoint Templates PPT Backgrounds For Slides 0113 help you meet deadlines which are an element of today's workplace. Just browse and pick the slides that appeal to your intuitive senses. PowerPoint presentation experts tell us our network PowerPoint templates and PPT Slides will help you be quick off the draw. Just enter your specific text and see your points hit home. You can be sure our Padlock On Laptop Internet Security PowerPoint Templates PPT Backgrounds For Slides 0113 are designed to make your presentations professional. PowerPoint presentation experts tell us our computer PowerPoint templates and PPT Slides are designed by a team of presentation professionals. Presenters tell us our Padlock On Laptop Internet Security PowerPoint Templates PPT Backgrounds For Slides 0113 help you meet deadlines which are an element of today's workplace. Just browse and pick the slides that appeal to your intuitive senses. PowerPoint presentation experts tell us our security PowerPoint templates and PPT Slides are designed by a team of presentation professionals.
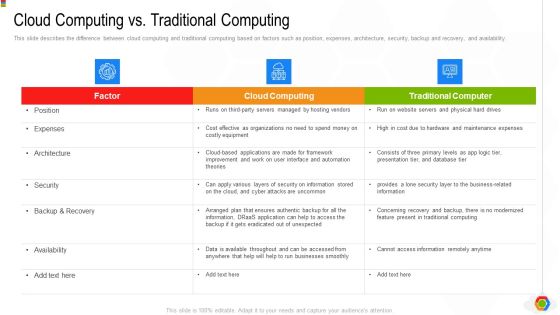
Google Cloud Console IT Cloud Computing Vs Traditional Computing Ppt File Ideas PDF
This slide describes the difference between cloud computing and traditional computing based on factors such as position, expenses, architecture, security, backup and recovery, and availability. Deliver an awe inspiring pitch with this creative google cloud console it cloud computing vs traditional computing ppt file ideas pdf bundle. Topics like security, backup and recovery, architecture, expenses, position can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cios Guide To Optimize Role Of Management In Effective Information Security Governance Diagrams PDF
This slide provides information regarding role of management in effective information security governance in strategic alignment , risk management, integration, value delivery, etc. Retrieve professionally designed Cios Guide To Optimize Role Of Management In Effective Information Security Governance Diagrams PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Organizations Risk Management And IT Security Residual Risk From IT Control Measures Slides PDF
This slide highlights the implementation control with residual risk which includes information technology risks and threats are controlled and minimized by system control measures. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Organizations Risk Management And IT Security Residual Risk From IT Control Measures Slides PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Organizations Risk Management And IT Security Residual Risk From IT Control Measures Slides PDF today and make your presentation stand out from the rest.
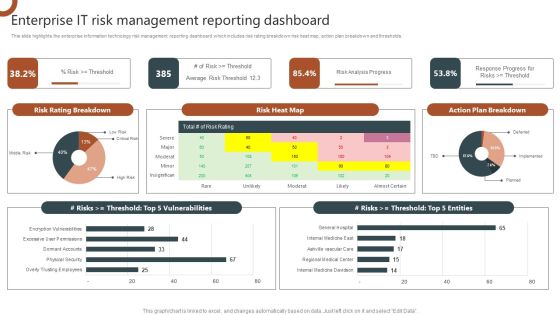
Organizations Risk Management And IT Security Enterprise IT Risk Management Reporting Dashboard Diagrams PDF
This slide highlights the enterprise information technology risk management reporting dashboard which includes risk rating breakdown risk heat map, action plan breakdown and thresholds. This Organizations Risk Management And IT Security Enterprise IT Risk Management Reporting Dashboard Diagrams PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Organizations Risk Management And IT Security Enterprise IT Risk Management Reporting Dashboard Diagrams PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today.

Organizations Risk Management And IT Security Impact Of IT Risks On Organization Structure PDF
This slide highlights the impacts of information technology risks on organization which includes graph for overspend project budget and data breach for 2021 year. Explore a selection of the finest Organizations Risk Management And IT Security Impact Of IT Risks On Organization Structure PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Organizations Risk Management And IT Security Impact Of IT Risks On Organization Structure PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Organizations Risk Management And IT Security Risk Assessment Table With Actions And Escalation Level Background PDF
This slide highlights the risks assessment table which includes three type of groups risks, group description of risks, action required for risk and risk escalation. Retrieve professionally designed Organizations Risk Management And IT Security Technical Security Control Model With Supporting Function Structure PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Series Of Cyber Security Attacks Against Ukraine 2022 Ongoing Onslaught Of Russia On Ukraine Introduction PDF
This slide represents the ongoing onslaught of russia on ukraine from december 2015 to jan 2022. Russia has attacked ukraine and other countries in many ways. If you are looking for a format to display your unique thoughts, then the professionally designed Series Of Cyber Security Attacks Against Ukraine 2022 Ongoing Onslaught Of Russia On Ukraine Introduction PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Series Of Cyber Security Attacks Against Ukraine 2022 Ongoing Onslaught Of Russia On Ukraine Introduction PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Series Of Cyber Security Attacks Against Ukraine 2022 Whispergate Attack On Ukrainian Organizations Information PDF
This slide represents russias whisper gate attack on ukrainian organizations, consists of three stages, and is designed to turn off the systems defenses, delete data, and format itself. Are you searching for a Series Of Cyber Security Attacks Against Ukraine 2022 Whispergate Attack On Ukrainian Organizations Information PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Series Of Cyber Security Attacks Against Ukraine 2022 Whispergate Attack On Ukrainian Organizations Information PDF from Slidegeeks today.

Series Of Cyber Security Attacks Against Ukraine 2022 International Cyber Aid To Ukraine Graphics PDF
This slide describes the international cyber assistance to ukraine by 6 european union nations such as lithuania, the netherlands, poland, estonia, romania, and croatia. Get a simple yet stunning designed Series Of Cyber Security Attacks Against Ukraine 2022 International Cyber Aid To Ukraine Graphics PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Series Of Cyber Security Attacks Against Ukraine 2022 International Cyber Aid To Ukraine Graphics PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
Organizing Security Awareness KPI Metrics Dashboard To Effectively Track Cyber Threat Icons PDF
The purpose of this slide is to highlight performance KPI dashboard used to monitor the cyber threat management.. The metrics highlighted in the slide are risk score, compliance status, threat level, monitoring and operational status. This Organizing Security Awareness KPI Metrics Dashboard To Effectively Track Cyber Threat Icons PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Organizing Security Awareness KPI Metrics Dashboard To Effectively Track Cyber Threat Icons PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, dont wait, grab the presentation templates today.

Probability Assessment Matrix For Risk Management Information Security Risk Administration Pictures PDF
This slide showcase matrix that can help organization to identify the probability of different information security attacks and formulate mitigation strategy in advance. It can help organization to manage the major risks and safeguard the information.This Probability Assessment Matrix For Risk Management Information Security Risk Administration Pictures PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
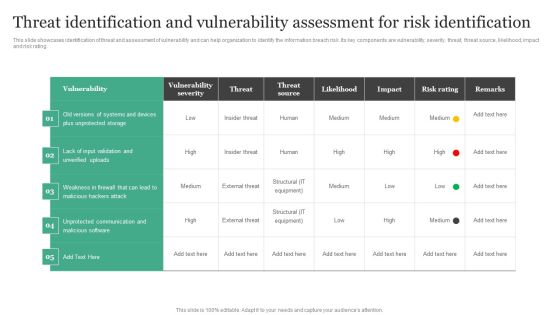
Threat Identification And Vulnerability Assessment For Risk Identification Information Security Risk Administration Slides PDF
This slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating.Get a simple yet stunning designed Threat Identification And Vulnerability Assessment For Risk Identification Information Security Risk Administration Slides PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Threat Identification And Vulnerability Assessment For Risk Identification Information Security Risk Administration Slides PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Addressing Staff Training Schedule With Cost Business Mobile Device Security Management And Mitigation Diagrams PDF
The employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. This Addressing Staff Training Schedule With Cost Business Mobile Device Security Management And Mitigation Diagrams PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Addressing Staff Training Schedule With Cost Business Mobile Device Security Management And Mitigation Diagrams PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today.

Mobile Device Management For Ios Platform Business Mobile Device Security Management Themes PDF
This slide provides information regarding mobile device management for iOS platform with device enrollment program, anti theft protection, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Mobile Device Management For Ios Platform Business Mobile Device Security Management Themes PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Mobile Device Management For Ios Platform Business Mobile Device Security Management Themes PDF today and make your presentation stand out from the rest.

Table Of Contents For Business Mobile Device Security Management And Mitigation Sample PDF
If you are looking for a format to display your unique thoughts, then the professionally designed Table Of Contents For Business Mobile Device Security Management And Mitigation Sample PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Table Of Contents For Business Mobile Device Security Management And Mitigation Sample PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Managing E Commerce Business Accounting Pci Certification For Increasing Security Of Online Transactions Download PDF
This slide depicts payment card industry PCI certification for increasing security of online transactions. It provides information about authorization, 2 way authentication, one time password OTP, repository, cyber attacks, compliance, data breach, etc. The Managing E Commerce Business Accounting Pci Certification For Increasing Security Of Online Transactions Download PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
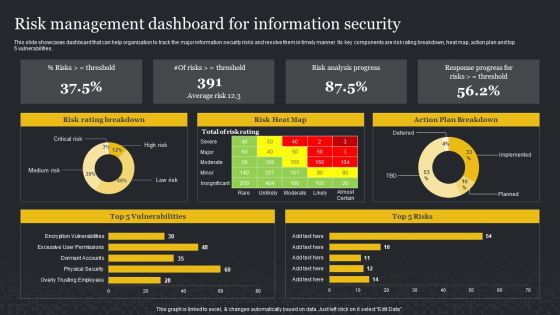
Risk Management Dashboard For Information Security Cybersecurity Risk Assessment Sample PDF
This slide showcases dashboard that can help organization to track the major information security risks and resolve them in timely manner. Its key components are risk rating breakdown, heat map, action plan and top 5 vulnerabilities. This Risk Management Dashboard For Information Security Cybersecurity Risk Assessment Sample PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Prevention Of Information Cyber Security Awareness Checklist To Ensure IT Asset Portrait PDF
The purpose of this slide is to outline a comprehensive checklist which can be used to ensure information technology IT asset protection. It cover points such as operating system is up to date, employees are using strong password policy etc. Get a simple yet stunning designed Prevention Of Information Cyber Security Awareness Checklist To Ensure IT Asset Portrait PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Prevention Of Information Cyber Security Awareness Checklist To Ensure IT Asset Portrait PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
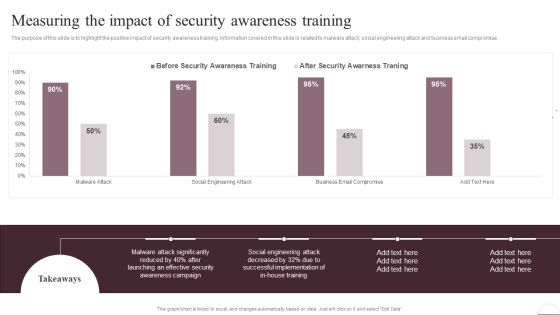
Prevention Of Information Measuring The Impact Of Security Awareness Training Ideas PDF
The purpose of this slide is to highlight the positive impact of security awareness training. Information covered in this slide is related to malware attack, social engineering attack and business email compromise. The Prevention Of Information Measuring The Impact Of Security Awareness Training Ideas PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Prevention Of Information Overview Of Cyber Security Awareness Course Icons PDF
The purpose of this slide is to provide a glimpse of the selected cyber security awareness course. It covers information about the instructor details, course content, attendees and learning outcome. This Prevention Of Information Overview Of Cyber Security Awareness Course Icons PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Classifying Various Security Issues And Attacks Improving Cybersecurity Incident Elements PDF
Purpose of this slide is to show the classification of different security issues and attacks. Categories covered are majorly internal as well as external issues and attacks.Slidegeeks is here to make your presentations a breeze with Classifying Various Security Issues And Attacks Improving Cybersecurity Incident Elements PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you Are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Cyber Physical System To Enhance Security Strategic Planning Process For Cps Demonstration PDF
This slide represents the security strategic planning process for CPS, including business strategy, technology roadmap, vision statement environment trends, current state assessment, and so on. Slidegeeks is here to make your presentations a breeze with Cyber Physical System To Enhance Security Strategic Planning Process For Cps Demonstration PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, youre sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether youre giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Deploying Cyber Security Incident Response Administration Comparative Analysis Of Web Application Graphics PDF
This slide represents the comparison between various web application firewall products based on multiple parameters to help organization select the best web application firewall for their organization. It includes comparison between WAF products based on features such as cookie tampering etc. This Deploying Cyber Security Incident Response Administration Comparative Analysis Of Web Application Graphics PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Deploying Cyber Security Incident Response Administration Comparative Analysis Of Web Application Graphics PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today.

Deploying Cyber Security Incident Response Administration User Awareness Training Program Pictures PDF
This slide represents the training program conducted by the incident management team for end users to help them identify and mitigate the cyber security incidents before they occur. It includes details related to training topic, method, date, trainer and budget. The Deploying Cyber Security Incident Response Administration User Awareness Training Program Pictures PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Deploying Cyber Security Incident Response Administration Cyber Attacks Faced By The Company Sample PDF
This slide represents the attacks faced by the organization which led to theft of confidential data and sensitive information of the organization. It represents the increase in ransomware and phishing attacks experienced by the enterprise within 5 years. Get a simple yet stunning designed Deploying Cyber Security Incident Response Administration Cyber Attacks Faced By The Company Sample PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Deploying Cyber Security Incident Response Administration Cyber Attacks Faced By The Company Sample PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Information Security Data Privacy In Social Media Ppt PowerPoint Presentation File Portfolio PDF
This slide shows that information privacy laws are beneficial for both social media platforms and their users, as it protects companies from any unnecessary penalties while providing users the required data protection. Get a simple yet stunning designed Information Security Data Privacy In Social Media Ppt PowerPoint Presentation File Portfolio PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Information Security Data Privacy In Social Media Ppt PowerPoint Presentation File Portfolio PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Information Security Five Data Privacy Rules Ppt PowerPoint Presentation File Deck PDF
This slide outlines the five data privacy rules, which are consent, purpose, disposal and destruction, access and security, accountability and disclosure. Slidegeeks is here to make your presentations a breeze with Information Security Five Data Privacy Rules Ppt PowerPoint Presentation File Deck PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Information Security Introduction To Data Privacy Ppt PowerPoint Presentation Diagram Images PDF
This slide provides a quick overview of data privacy, which refers to a persons capacity to control how much of their personal information is shared. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Information Security Introduction To Data Privacy Ppt PowerPoint Presentation Diagram Images PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Information Security Introduction To Data Privacy Ppt PowerPoint Presentation Diagram Images PDF today and make your presentation stand out from the rest.

Deploying AI To Enhance Managing Cyber Security In Manufacturing 30 Days Plan Formats PDF
This slide describes the first 30 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Slidegeeks is here to make your presentations a breeze with Deploying AI To Enhance Managing Cyber Security In Manufacturing 30 Days Plan Formats PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, youre sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether youre giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Cyber Risks And Incident Response Playbook Classifying Various Security Issues And Attacks Microsoft PDF
Purpose of this slide is to show the classification of different security issues and attacks. Categories covered are majorly internal as well as external issues and attacks. Slidegeeks is here to make your presentations a breeze with Cyber Risks And Incident Response Playbook Classifying Various Security Issues And Attacks Microsoft PD With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, youre sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether youre giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Cyber Risks And Incident Response Playbook Performing Cyber Training Exercises For Securing The Assets Mockup PDF
Purpose of this slide is to address and perform various cyber training exercises in order to secure companys assets. Exercises covered are defense in depth, capture the flag etc. Retrieve professionally designed Cyber Risks And Incident Response Playbook Performing Cyber Training Exercises For Securing The Assets Mockup PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
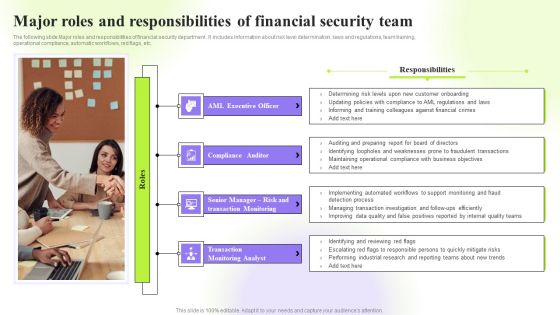
Techniques To Monitor Transactions Major Roles And Responsibilities Of Financial Security Team Pictures PDF
The following slide Major roles and responsibilities of financial security department . It includes information about risk level determination, laws and regulations, team training, operational compliance, automatic workflows, red flags, etc. Retrieve professionally designed Techniques To Monitor Transactions Major Roles And Responsibilities Of Financial Security Team Pictures PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

KYC Transaction Monitoring System Business Security Suspicious Activity Reporting Process Flow Summary PDF
This slide showcases process flow of suspicious activity reporting SAR. It provides information about transaction alert, purpose, patterns, customer behavior, client lifestyle, negative news, adverse media, sanctions, anti money laundering AML, etc. Get a simple yet stunning designed KYC Transaction Monitoring System Business Security Suspicious Activity Reporting Process Flow Summary PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit KYC Transaction Monitoring System Business Security Suspicious Activity Reporting Process Flow Summary PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

KYC Transaction Monitoring System Business Security Cryptocurrency Transaction Monitoring Guidelines PDF
This slide showcases cryptocurrency transaction monitoring with alert status. It provides information about address, risk level, currencies, bitcoin, Ethereum, date added, deposits, case status, alerts, deposits, darknet, etc. This KYC Transaction Monitoring System Business Security Cryptocurrency Transaction Monitoring Guidelines PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The KYC Transaction Monitoring System Business Security Cryptocurrency Transaction Monitoring Guidelines PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today.

KYC Transaction Monitoring System Business Security Determining Residual Risks Topics PDF
This slide showcases assessment matrix to determine residual risks. It provides information about inherent risks, control assessment, satisfaction, visibility, risk management controls, data analytics, etc. Explore a selection of the finest KYC Transaction Monitoring System Business Security Determining Residual Risks Topics PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our KYC Transaction Monitoring System Business Security Determining Residual Risks Topics PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

KYC Transaction Monitoring System Business Security Timeline Implementing Transaction Summary PDF
This slide showcases timeline to introduce transaction monitoring system. It provides information about scenario planning, threshold setting, deployment, project management office PMO, project planning, scenario identification, data source identification, etc. Get a simple yet stunning designed KYC Transaction Monitoring System Business Security Timeline Implementing Transaction Summary PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit KYC Transaction Monitoring System Business Security Timeline Implementing Transaction Summary PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Company Rules And Regulations Manual Data Protection And Information Security Policy And Procedure Download PDF
This slide highlights the data protection and information security policy which includes policy and procedures of IT policy and it is applicable to all the employees and enforcement of the policy. Slidegeeks is here to make your presentations a breeze with Company Rules And Regulations Manual Data Protection And Information Security Policy And Procedure Download PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Information Systems Security And Risk Management Plan Mitigation Strategies To Avoid Information Breach Graphics PDF
This slide showcases strategies that can help organization to avoid information breach. Key strategies include implement antivirus software, monitor network traffic, incident response plan, patch management schedule and establish network access controls. Explore a selection of the finest Information Systems Security And Risk Management Plan Mitigation Strategies To Avoid Information Breach Graphics PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Information Systems Security And Risk Management Plan Mitigation Strategies To Avoid Information Breach Graphics PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
Implementing Cybersecurity Awareness Program To Prevent Attacks Measuring The Impact Of Security Awareness Icons PDF
The purpose of this slide is to highlight the positive impact of security awareness training. Information covered in this slide is related to malware attack, social engineering attack and business email compromise. The Implementing Cybersecurity Awareness Program To Prevent Attacks Measuring The Impact Of Security Awareness Icons PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Implementing Cybersecurity Awareness Program To Prevent Attacks Overview Of Cyber Security Awareness Course Microsoft PDF
The purpose of this slide is to provide a glimpse of the selected cyber security awareness course. It covers information about the instructor details, course content, attendees and learning outcome. This Implementing Cybersecurity Awareness Program To Prevent Attacks Overview Of Cyber Security Awareness Course Microsoft PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Public Relations Guide To Enhance Brand Credibility Budget Securing Tips For Public Relations Summary PDF
This slide shows various tips which can be used by organizations to while developing marketing budget. It includes aligning marketing outcome with organizational goals, strategic insights and highlight impacts. Get a simple yet stunning designed Public Relations Guide To Enhance Brand Credibility Budget Securing Tips For Public Relations Summary PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Public Relations Guide To Enhance Brand Credibility Budget Securing Tips For Public Relations Summary PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Cyber Security Awareness Checklist To Ensure It Asset Protection Ppt Model Shapes PDF
The purpose of this slide is to outline a comprehensive checklist which can be used to ensure information technology IT asset protection. It cover points such as operating system is up to date, employees are using strong password policy etc. Create an editable Cyber Security Awareness Checklist To Ensure It Asset Protection Ppt Model Shapes PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Cyber Security Awareness Checklist To Ensure It Asset Protection Ppt Model Shapes PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Table Of Contents Developing Information Technology Security Awareness Training Program For Employees Graphics PDF
If you are looking for a format to display your unique thoughts, then the professionally designed Table Of Contents Developing Information Technology Security Awareness Training Program For Employees Graphics PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Table Of Contents Developing Information Technology Security Awareness Training Program For Employees Graphics PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Strategies We Will Implement To Make Security Awareness Training Interactive Graphics PDF
The purpose of this slide is to exhibit variety of strategies which can be used to engage employees in the security awareness training plan. The strategies highlighted in the slide are gamification, personalization, high-quality content and variety. Slidegeeks is here to make your presentations a breeze with Strategies We Will Implement To Make Security Awareness Training Interactive Graphics PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Agenda For Developing IT Security Strategy To Prevent Data Assets Portrait PDF
If you are looking for a format to display your unique thoughts, then the professionally designed Agenda For Developing IT Security Strategy To Prevent Data Assets Portrait PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Agenda For Developing IT Security Strategy To Prevent Data Assets Portrait PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Developing IT Security Strategy Cyber Attacks Faced By Organization In Previous Summary PDF
This slide showcases information security attacks faced by organization in past financial year. It can help company to assess different type of cyber attacks and formulate strategies to tackle them. Retrieve professionally designed Developing IT Security Strategy Cyber Attacks Faced By Organization In Previous Summary PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Developing IT Security Strategy Risk Assessment Matrix With Vulnerability And Threat Level Download PDF
This slide showcases assessment matrix to identify risk associated with different class of information assists. It calculates severity of risk on the basis of threat and vulnerability level. This Developing IT Security Strategy Risk Assessment Matrix With Vulnerability And Threat Level Download PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Developing IT Security Strategy Risk Assessment Matrix With Vulnerability And Threat Level Download PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today.

Implementing Management System To Enhance Ecommerce Processes Importance Of Secure Ecommerce Payment Systems Graphics PDF
This slide represents the importance of payment gateways in facilitating systemized payment methods and providing consumers with fast and flexible way for making payments. It includes benefits of ecommerce payment systems such as meets digital needs, customer retention, security etc. The Implementing Management System To Enhance Ecommerce Processes Importance Of Secure Ecommerce Payment Systems Graphics PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Table Of Contents Increasing Information Security Awareness In Company Using Various Techniques Clipart PDF
If you are looking for a format to display your unique thoughts, then the professionally designed Table Of Contents Increasing Information Security Awareness In Company Using Various Techniques Clipart PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Table Of Contents Increasing Information Security Awareness In Company Using Various Techniques Clipart PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Incident Response Techniques Deployement Strategies To Analyze Cyber Security Incidents Sample PDF
This slide represents the techniques to be used by the organizations to analyze the impact of cyber security incidents on business operations. It includes strategies for analyzing cyber incidents such as profile network and systems etc. Slidegeeks is here to make your presentations a breeze with Incident Response Techniques Deployement Key Parameters To Select Cyber Security Containment Strategy Information PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
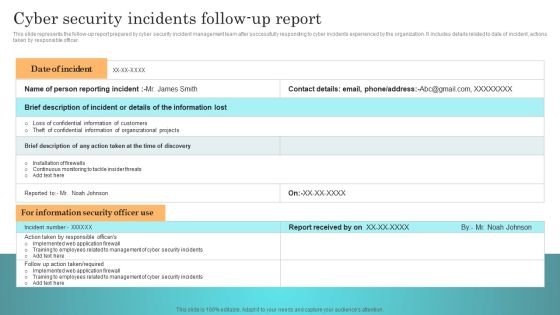
Incident Response Techniques Deployement Cyber Security Incidents Follow Up Report Template PDF
This slide represents the follow-up report prepared by cyber security incident management team after successfully responding to cyber incidents experienced by the organization. It includes details related to date of incident, actions taken by responsible officer. The Incident Response Techniques Deployement Cyber Security Incidents Follow Up Report Template PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Incident Response Techniques Deployement Impact Of Implementing Cyber Security Incident Management Formats PDF
This slide represents the comparison between current and past scenario to analyze the impact of cyber security incident management on business operations. It includes analysis of KPIs such engagement, satisfaction, turnover rate etc. Retrieve professionally designed Incident Response Techniques Deployement Impact Of Implementing Cyber Security Incident Management Formats PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
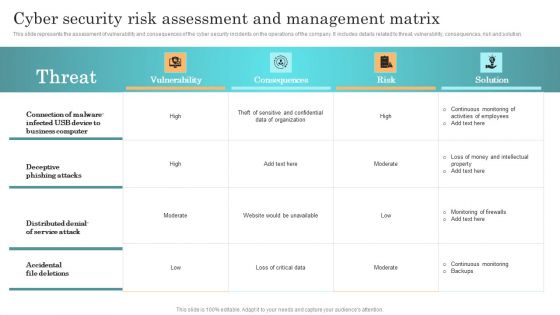
Incident Response Techniques Deployement Cyber Security Risk Assessment And Management Matrix Download PDF
This slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution. Slidegeeks is here to make your presentations a breeze with Incident Response Techniques Deployement Cyber Security Risk Assessment And Management Matrix Download PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Incident Response Techniques Deployement Cyber Security Systems Monitoring Report Microsoft PDF
This slide represents the report to effectively monitor the networks and systems of the organization. It includes kpis such as total intrusion attempts, mean detect team, mean resolve time etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Incident Response Techniques Deployement Cyber Security Systems Monitoring Report Microsoft PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Incident Response Techniques Deployement Cyber Security Systems Monitoring Report Microsoft PDF today and make your presentation stand out from the rest.
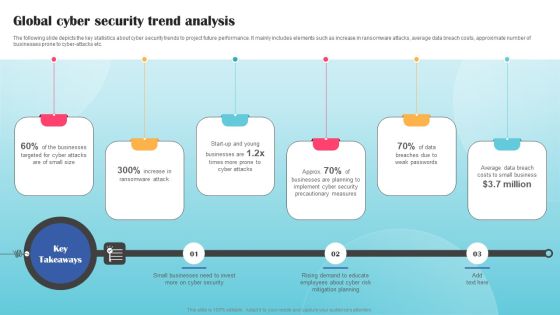
Global Cyber Security Trend Analysis Ppt PowerPoint Presentation File Styles PDF
The following slide depicts the key statistics about cyber security trends to project future performance. It mainly includes elements such as increase in ransomware attacks, average data breach costs, approximate number of businesses prone to cyber-attacks etc. The Global Cyber Security Trend Analysis Ppt PowerPoint Presentation File Styles PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Dashboard To Track IT Security Incidents Prevailing Across Firm Ppt PowerPoint Presentation File Outline PDF
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Slidegeeks is here to make your presentations a breeze with Dashboard To Track IT Security Incidents Prevailing Across Firm Ppt PowerPoint Presentation File Outline PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Secure Web Gateways SWG Setup And Working Ppt Show Tips PDF
This slide depicts the methods to setup the secure web gateways and their working. The purpose of this slide is to demonstrate the various ways in which organizations can install the SWGs. It also caters to the working and functions performed by SWGs to protect data and safe browsing on the internet. Slidegeeks is here to make your presentations a breeze with Secure Web Gateways SWG Setup And Working Ppt Show Tips PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Organizational Assets Security Management Strategy Determine User Access Controls Levels Diagrams PDF
This slide provides information about information user access controls levels for access critical assets and information associated to firm and levels of access for administrator, maintainer, guest or disabled. Get a simple yet stunning designed Organizational Assets Security Management Strategy Determine User Access Controls Levels Diagrams PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Organizational Assets Security Management Strategy Determine User Access Controls Levels Diagrams PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Organizational Assets Security Management Strategy How To Handle Financial Crisis At Workplace Formats PDF
This slide covers information regarding how firm can handle financial crisis by safeguarding financial stability in terms of abundant cash requirements, overhead analysis, currency hedging, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Organizational Assets Security Management Strategy How To Handle Financial Crisis At Workplace Formats PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Organizational Assets Security Management Strategy How To Handle Financial Crisis At Workplace Formats PDF today and make your presentation stand out from the rest.

Workplace Security Management Program Ppt PowerPoint Presentation Complete Deck With Slides
Using this ready-made PowerPoint slide, you can incorporate your own data to make an impact with your business innovation and clarity of goals. Use this brilliantly designed Workplace Security Management Program Ppt PowerPoint Presentation Complete Deck With Slides to showcase how ultimately all business concepts are related. This presentation template can also be used to record resource allocation in a visual form. The twenty one Slide Workplace Security Management Program Ppt PowerPoint Presentation Complete Deck With Slides is suitable for all your business needs, where you need to make sure that all bases are covered. Download this PPT template now to start a journey on your chosen business, with customer satisfaction the key aim.

Security Software Company Investor Funding Pitch Deck Core Team Guidelines PDF
The following slide showcases key personnel of executive team of IT company which are CEO, chief architect, VP marketing, sales, product, engineering, chief data scientist, chief scientist, etc. Get a simple yet stunning designed Security Software Company Investor Funding Pitch Deck Core Team Guidelines PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Security Software Company Investor Funding Pitch Deck Core Team Guidelines PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Security Software Company Investor Funding Pitch Deck Investment Ask Clipart PDF
This slide represents the information related to the investment requirements to the investors for seeking needed funds and the purpose of seeking finance. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Security Software Company Investor Funding Pitch Deck Investment Ask Clipart PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Security Software Company Investor Funding Pitch Deck Investment Ask Clipart PDF today and make your presentation stand out from the rest.

Security Software Company Investor Funding Pitch Deck Allocation Of Funds Portrait PDF
This slide showcases areas where the funds that are collected in series C funding round will be allocated like- marketing, sales and research and development. If you are looking for a format to display your unique thoughts, then the professionally designed Security Software Company Investor Funding Pitch Deck Allocation Of Funds Portrait PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Security Software Company Investor Funding Pitch Deck Allocation Of Funds Portrait PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Securing Market Leadership Through Competitive Excellence Conducting USP Analysis For The Brand Topics PDF
The following slide exhibits evaluation of various unique selling point USP which will guide organizations in defining the brand USP and stand out from the major competitors. The analysis is drawn on the basis of common, interesting, unique and dull USP. Get a simple yet stunning designed Securing Market Leadership Through Competitive Excellence Conducting USP Analysis For The Brand Topics PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Securing Market Leadership Through Competitive Excellence Conducting USP Analysis For The Brand Topics PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Deployment Of Omnichannel Banking Solutions Introduction To Secure Digital Wallets For Financial Transactions Template PDF
This slide covers brief summary of digital wallets provided by banking sector to facilitate financial transactions. The purpose of this template is to provide the benefits derived from using e-wallets. It includes benefits such as offering more prominent security, discount and rewards, eliminates role of physical banks, streamlines checkout process, etc. Retrieve professionally designed Deployment Of Omnichannel Banking Solutions Introduction To Secure Digital Wallets For Financial Transactions Template PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

CYBER Security Breache Response Strategy Budget Allocation For Cyber Incident Management Training Topics PDF
This slide represents the budget prepared to predict cash flows and allocate required resources for incident management training. It includes training budget of IT, HR, operations, and finance department etc. Create an editable CYBER Security Breache Response Strategy Budget Allocation For Cyber Incident Management Training Topics PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. CYBER Security Breache Response Strategy Budget Allocation For Cyber Incident Management Training Topics PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

CYBER Security Breache Response Strategy Cyber Supply Chain Risk Management Dashboard Inspiration PDF
This slide shows the dashboard representing details related to management of supply chain risks by the incident management team. It includes details related to KPIs such as policy and compliance, resource security hygiene etc. The CYBER Security Breache Response Strategy Cyber Supply Chain Risk Management Dashboard Inspiration PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Implementing Cyber Security Incident Consequences Of Data Breaches Faced By Organization Infographics PDF
This slide represents the impact of data breaches experienced by an enterprise. It includes data breaches of hacking, unintended disclosure, physical loss, payment card fraud etc. Create an editable Implementing Cyber Security Incident Consequences Of Data Breaches Faced By Organization Infographics PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Implementing Cyber Security Incident Consequences Of Data Breaches Faced By Organization Infographics PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Implementing Cyber Security Incident Cyber Supply Chain Risk Dashboard Download PDF
This slide shows the dashboard representing details related to management of supply chain risks by the incident management team. It includes details related to KPIs such as policy and compliance, resource security hygiene etc. Slidegeeks is here to make your presentations a breeze with Implementing Cyber Security Incident Cyber Supply Chain Risk Dashboard Download PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Table Of Contents For Comprehensive Guide For Ensuring IT Infrastructure Security Slides PDF
If you are looking for a format to display your unique thoughts, then the professionally designed Table Of Contents For Comprehensive Guide For Ensuring IT Infrastructure Security Slides PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Table Of Contents For Comprehensive Guide For Ensuring IT Infrastructure Security Slides PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Timeline To Implement Cloud Access Security Broker Ppt PowerPoint Presentation File Styles PDF
This slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Slidegeeks is here to make your presentations a breeze with Timeline To Implement Cloud Access Security Broker Ppt PowerPoint Presentation File Styles PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Blockchain Security Solutions Deployment Blockchain Hashing SHA 256 Algorithm Formats PDF
This slide talks about the hashing SHA-256 algorithm used in blockchain technology, including its properties. The purpose of this slide is to give an overview of hashing and its properties, such as collision resistance, deterministic, quick, and irreversible. Create an editable Blockchain Security Solutions Deployment Blockchain Hashing SHA 256 Algorithm Formats PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Blockchain Security Solutions Deployment Blockchain Hashing SHA 256 Algorithm Formats PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Blockchain Security Solutions Deployment How Blockchain Prevents Fraud And Data Theft Themes PDF
This slide describes the different methods used by blockchain technology to prevent data from fraud and stealing. The purpose of this slide is to showcase the various techniques and technologies used in blockchain technology to prevent fraud and data theft. Get a simple yet stunning designed Blockchain Security Solutions Deployment How Blockchain Prevents Fraud And Data Theft Themes PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Blockchain Security Solutions Deployment How Blockchain Prevents Fraud And Data Theft Themes PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

3d Locked Notebook Security PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our 3d Locked Notebook Security PowerPoint Templates PPT Backgrounds For Slides 0113.Download and present our Technology PowerPoint Templates because you should Whip up a frenzy with our PowerPoint Templates and Slides. They will fuel the excitement of your team. Use our Shapes PowerPoint Templates because You are an avid believer in ethical practices. Highlight the benefits that accrue with our PowerPoint Templates and Slides. Use our Business PowerPoint Templates because our PowerPoint Templates and Slides are the string of your bow. Fire of your ideas and conquer the podium. Present our Computer PowerPoint Templates because You should Bet on your luck with our PowerPoint Templates and Slides. Be assured that you will hit the jackpot. Download and present our Signs PowerPoint Templates because Our PowerPoint Templates and Slides will let you Hit the target. Go the full distance with ease and elan.Use these PowerPoint slides for presentations relating to Vector Notebook Lockable pattern, shapes, technology, business, computer, signs. The prominent colors used in the PowerPoint template are Yellow, Gray, Black. You can be sure our 3d Locked Notebook Security PowerPoint Templates PPT Backgrounds For Slides 0113 are designed to make your presentations professional. Professionals tell us our Lockable PowerPoint templates and PPT Slides are designed to make your presentations professional. Customers tell us our 3d Locked Notebook Security PowerPoint Templates PPT Backgrounds For Slides 0113 will get their audience's attention. Presenters tell us our pattern PowerPoint templates and PPT Slides will make the presenter successul in his career/life. We assure you our 3d Locked Notebook Security PowerPoint Templates PPT Backgrounds For Slides 0113 are incredible easy to use. Presenters tell us our pattern PowerPoint templates and PPT Slides will help you be quick off the draw. Just enter your specific text and see your points hit home.

Computing Technology Industry Association Certification Career Roadmap Professional PDF
The following slide showcases certification roadmap for computing technology industry. It shows accreditations in information security, network and cloud technologies, hardware services infrastructure and IT management and strategy for beginner, intermediate, advanced and expert levels. Persuade your audience using this Computing Technology Industry Association Certification Career Roadmap Professional PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Information Security, Network And Cloud Technologies, IT Management And Strategy. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Digital Trends In Customer Finance Market Template PDF
The slide highlights various digital and tech based trends in consumer financing and lending market. It includes key components like better customer experience, enhanced security, greater Omni channel capabilities, Non banking institutions market entry and AI tools. Persuade your audience using this Digital Trends In Customer Finance Market Template PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Evaluate Data, Ensure Security, Lending Services. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Hurdles In Business Data Security In Trade Secret Ppt PowerPoint Presentation Pictures Master Slide PDF
Showcasing this set of slides titled hurdles in business data security in trade secret ppt powerpoint presentation pictures master slide pdf. The topics addressed in these templates are once trade secret is made public, it can be accessed by anyone, difficult to enforce than patent, level of protection granted to trade is generally considered weak and is different from country country. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Picture Of Trade Secret Security Merits Ppt PowerPoint Presentation Model Shapes PDF
Pitch your topic with ease and precision using this picture of trade secret security merits ppt powerpoint presentation model shapes pdf. This layout presents information on trade secret doe not require registration cost, they have immediate effect, they do not require compliance with official procedures such as disclosure of information to any government authority, they are not limited with time unless patents are not revealed to the public. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Online Settlement Revolution Payment Security And Fraud Management Solutions Analysis Ppt Slides File Formats PDF
From prevention to detection and resolution, Data Fraud Management solutions allow you to leverage proven technologies to create customized strategies that help limit losses while maintaining a high level of customer satisfaction. Presenting online settlement revolution payment security and fraud management solutions analysis ppt slides file formats pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like before the payment, on the payment page, after the payment. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Information And Technology Security Operations Current Challenges Faced By Firm While Implementing Secops Slides PDF
This slide portrays information regarding the present challenges faced by firm while implementing SecOps system including budget constraint, absence of pool of talent and expertise and lack of essential tools. Presenting information and technology security operations current challenges faced by firm while implementing secops slides pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like budget tools, pool of talent and expertise. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Organizational Security Solutions Current Challenges Faced By Firm While Implementing Secops Topics PDF
This slide portrays information regarding the present challenges faced by firm while implementing SecOps system including budget constraint, absence of pool of talent and expertise and lack of essential tools. Presenting organizational security solutions current challenges faced by firm while implementing secops topics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like budget tools, pool of talent and expertise. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Security Functioning Centre Current Challenges Faced By Firm While Implementing Secops Topics PDF
This slide portrays information regarding the present challenges faced by firm while implementing SecOps system including budget constraint, absence of pool of talent and expertise and lack of essential tools. Presenting security functioning centre current challenges faced by firm while implementing secops topics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like budget, pool of talent and expertise, tools. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Functioning Centre Various Technologies For Effective Secops Process Template PDF
This slide portrays information regarding the different technologies that can be used by firm in order to implement effective SecOps process in firm. Presenting security functioning centre various technologies for effective secops process template pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like event management, cyber threat intelligence, network traffic analysis. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
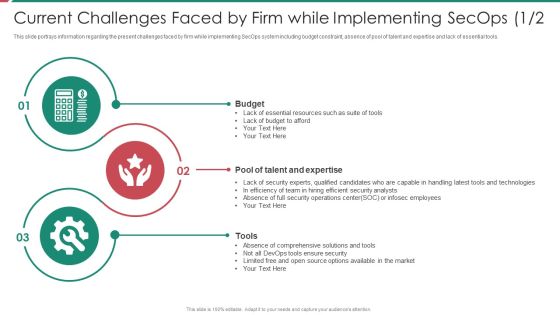
Security And Process Integration Current Challenges Faced By Firm While Implementing Secops Budget Ideas PDF
This slide portrays information regarding the present challenges faced by firm while implementing SecOps system including budget constraint, absence of pool of talent and expertise and lack of essential tools. Presenting security and process integration current challenges faced by firm while implementing secops budget ideas pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like budget, tools, pool of talent and expertise. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security And Process Integration Current Challenges Faced By Firm While Implementing Secops Tools Clipart PDF
This slide portrays information regarding the present challenges faced by firm while implementing SecOps system including budget constraint, absence of pool of talent and expertise and lack of essential tools. Presenting security and process integration current challenges faced by firm while implementing secops tools clipart pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like budget, tools, pool of talent and expertise. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Handling Several Food Ingredients Quality Food Security Excellence Ppt Styles Template PDF
This slide provides information regarding handling of food ingredients quality for various kinds of ingredients such as liquid, dry ingredient and oil. Presenting handling several food ingredients quality food security excellence ppt styles template pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like liquid ingredients, dry ingredients, oil. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Improving Product Packaging To Ensure Food Quality Food Security Excellence Ppt Slides Template PDF
This slide provides information regarding improving of product packaging in order to ensure food quality and details about essential details needed to be present on product packaging. Presenting improving product packaging to ensure food quality food security excellence ppt slides template pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like product preparation, product storage, usage, ingredients, allergen risk caution. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Assessment Matrix Of Cyber Risks IT Security IT Ppt Ideas Display PDF
This slide depicts the cyberattacks surface based on different property types. It also covers the attacks based on web or mobile applications, online payments, employee devices. Presenting assessment matrix of cyber risks it security it ppt ideas display pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like industrial, multifamily, data center, retail, health care. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Dispose Data And Equipment Properly IT Security IT Ppt Icon Clipart Images PDF
This slide depicts the importance of disposal of the data and equipment that is not in use anymore and restricts the employees who already left the organization. Presenting dispose data and equipment properly it security it ppt icon clipart images pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like dispose data and equipment properly. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Implementation Of Strong Password Policy IT Security IT Ppt Styles Topics PDF
This slide depicts the importance of having strong passwords for different online accounts. It also shows the number of users who use the same password across other accounts. Presenting implementation of strong password policy it security it ppt styles topics pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like implementation of strong password policy. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Computing Technology Implementation Plan Security Related Challenges In Serverless Technology Ideas PDF
The purpose of the following slide is to show the various challenges that may present to the organization, these issues can be authentication issues, no-proper monitoring, and third-party dependency. Presenting cloud computing technology implementation plan security related challenges in serverless technology ideas pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like improper monitoring and controlling, authentication issues, dependency on third party. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Risk Management Plan Incident Management Workflow Process Diagram Infographics PDF
Following slide presents the incident management workflow of the firm. It covers five phases namely incident occurrence, team organizing, action taken, incident resolution and fail over report. Presenting cyber security risk management plan incident management workflow process diagram infographics pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like fail over report, incident resolution, organize your team, incident occurs, team takes action. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Developing Firm Security Strategy Plan Addressing Vital Records Maintenance Centre Inspiration PDF
The team will keep the track of crucial information and the location where these records are kept also the alternate backup location of the records and the other sources through which records can be retrieved. Presenting developing firm security strategy plan addressing vital records maintenance centre inspiration pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like description, primary location of records, alternate backup location of records, other sources to obtain records. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
