Construction Safety

Top Four Network IT Security Analysis Tools Guidelines PDF
This slide covers the tools used for the security analysis of the networks with their usage according to their needs on different occasions. It also includes the price or cost of these tools. Persuade your audience using this Top Four Network IT Security Analysis Tools Guidelines PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Network IT Security, Analysis Tools. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Business Security And Automation Control System Demonstration PDF
The purpose of this slide is to highlight the incorporation between business security and automation system which enables faster threat detection along with prominent control measures. The automated security system includes alarm systems, fire emergency buttons, control systems, and surveillance systems. Persuade your audience using this Business Security And Automation Control System Demonstration PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Siren Alarm Systems, Fire Emergency Buttons, Surveillance Systems, Control System. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Key Elements Of IT Security Plan Background PDF
This slide represents key elements of cyber security strategy such as cyber risk management, security regulatory and compliance, cyber transformation, cyber strategy etc. Persuade your audience using this Key Elements Of IT Security Plan Background PDF. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Strategy, Executive Cyber Dashboard, Education Training Awareness. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Security Problems Management And Action Plan Microsoft PDF
The following slide illustrates the cyber security risk management plan to outline business security threats and draft proposed strategies. It also includes elements such as objectives, issues, breach response actions, employee training etc. Persuade your audience using this Cyber Security Problems Management And Action Plan Microsoft PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Objectives, Breach Response Actions, Employee Training. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Data Security Management Tool Assessment Matrix Microsoft PDF
This slide highlights a tools comparison matrix for data security governance and management. It includes key components such as threat intelligence, advanced data governance, source score, data helpdesk, price and customer satisfaction. Persuade your audience using this Data Security Management Tool Assessment Matrix Microsoft PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Threat Intelligence, Advanced Data Governance, Secure Score. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

IT Security Risk Management Implementation Process Brochure PDF
The following slide explains implementation method for cybersecurity risk management for the organization to ensure protection of key business data. It includes steps such as categorize, security controls, implementation, assess, etc. Persuade your audience using this IT Security Risk Management Implementation Process Brochure PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Monitor, Authorize, Assess, Implementation, Security Controls, Categorize System. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Security Operations Essential Functions For Customer Satisfaction Inspiration PDF
This slide highlights key functions performed by SecOps team members in order to meet IT infrastructure network security objectives. It includes security monitoring, threat intelligence, triage and investigations, incident response, and root cause analysis. Persuade your audience using this Security Operations Essential Functions For Customer Satisfaction Inspiration PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Triage And Investigation, Incident Response, Root Course Analysis. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Solutions To Overcome Security Operations Challenges Template PDF
This slide outlines solutions to overcome challenges faced by security operations teams in order to deal with an increasing number of cyber attacks. It includes challenges such as skill shortage, lack of automation, large volume of data, and work processes integration. Persuade your audience using this Solutions To Overcome Security Operations Challenges Template PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Lack Of Automation, Work Processes Integration, Data Security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Security Program Hazards Management Strategy Topics PDF
This slide provides a strategy for cyber security risk management which helps business and organizations to secure the data and information. Key elements are understand, assess, determine and document.Persuade your audience using this Cyber Security Program Hazards Management Strategy Topics PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Understand, Determine. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
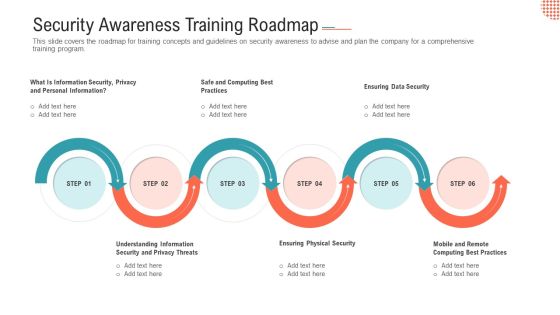
Security Awareness Training Roadmap Ppt Layouts Layouts PDF
This slide covers the roadmap for training concepts and guidelines on security awareness to advise and plan the company for a comprehensive training program.Presenting security awareness training roadmap ppt layouts layouts pdf. to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like safe and computing best practices, ensuring data security, ensuring physical security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Operations Management Skills Software Security Skills Pictures PDF
This slide provides the glimpse about the software security skills such as security training, code analysis, change management, compliance monitoring, threat investigation, vulnerability management, etc. Presenting operations management skills software security skills pictures pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security training, code analysis, change management, compliance monitoring, threat investigation, vulnerability management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Technology Skills Gap Analysis Priorities Clipart PDF
This slide illustrates the top IT security concerns for business managers. It includes data loss prevention, firewalls, access management, cloud security, risk management, legal compliance and predictive analysis. Showcasing this set of slides titled cyber security technology skills gap analysis priorities clipart pdf. The topics addressed in these templates are cyber security technology skills gap analysis priorities. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
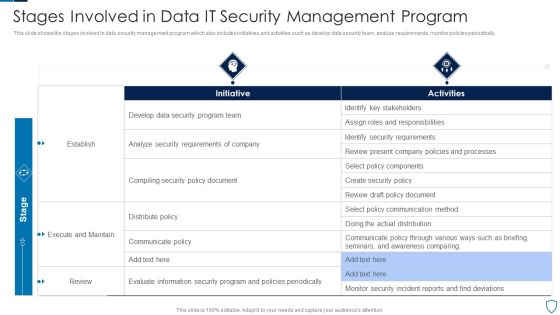
Stages Involved In Data IT Security Management Program Diagrams PDF
This slide shows the stages involved in data security management program which also includes initiatives and activities such as develop data security team, analyze requirements, monitor policies periodically.Pitch your topic with ease and precision using this Stages Involved In Data IT Security Management Program Diagrams PDF This layout presents information on Identify Stakeholders, Security Requirements, Execute Maintain It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Checklist To Implement Cloud Security In Business Microsoft PDF
This slide shows the checklist to implement cloud security in business, including policies and procedures, access control, networking, backup data, security patches, etc. Presenting Checklist To Implement Cloud Security In Business Microsoft PDF to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like Access Control, Networking, Security Patches And Updates. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

How Does Cloud Security Work Governance Professional PDF
This slide describes how a cloud security system works and what controls or measures are implemented to secure the data over the cloud. Presenting How Does Cloud Security Work Governance Professional PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Access Management, Business Continuity Planning, Data Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Team Analytics Dashboard With KPI Metrics Icons PDF
The following slide shows cyber analytics dashboard to monitor and inspect threats and accordingly plan preventive actions. It includes open and resolved incidents and tickets. Pitch your topic with ease and precision using this Cyber Security Team Analytics Dashboard With KPI Metrics Icons PDF. This layout presents information on Energy Security Team, Digital Security Center, Security Operations Center. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Users Password IT Security Analysis Dashboard Elements PDF
This slide displays the analysis of the users password security in an organization to make sure that the users confidential details are safe. It includes security gains, password evaluation, active users data, activities of password, etc. Showcasing this set of slides titled Users Password IT Security Analysis Dashboard Elements PDF. The topics addressed in these templates are Password Evaluation Score, Security Gains. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Effective Security Operations Tools To Prevent Cyber Threats Formats PDF
This slide includes some SecOps tools that provide a more secure working environment to organisations by improving collaboration between operations and security teams. It includes elements such as tools, pricing, features, rating, free version, and free trial. Pitch your topic with ease and precision using this Effective Security Operations Tools To Prevent Cyber Threats Formats PDF. This layout presents information on Develops, Organization Security, Compliance Requirements. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Database Access Security Measures For Businesses Portrait PDF
This slide represents the security measures for data access within an organization. This template aims to demonstrate secure data access techniques and their benefits. The components include workforce training, implementing a data-centric security plan, deploying a multi-factor authentication policy, etc. Pitch your topic with ease and precision using this Database Access Security Measures For Businesses Portrait PDF. This layout presents information on Methods, Benefits, Actions. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Addressing Role Of Chief Security Officer At Workplace Clipart PDF
This slide provides information regarding role of chief security officer at workplace and determine their key priorities in terms of day to day operations, security, compliance, innovation, etc. Create an editable Addressing Role Of Chief Security Officer At Workplace Clipart PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Addressing Role Of Chief Security Officer At Workplace Clipart PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
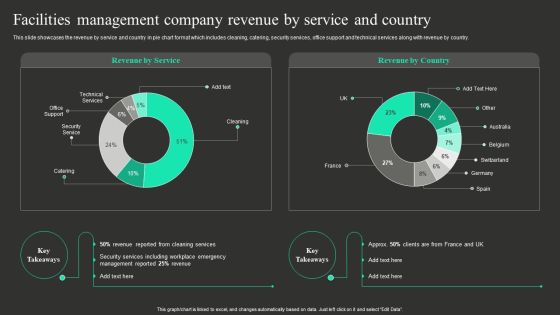
Facilities Management Company Revenue By Service And Country Information PDF
This slide showcases the revenue by service and country in pie chart format which includes cleaning, catering, security services, office support and technical services along with revenue by country. If you are looking for a format to display your unique thoughts, then the professionally designed Facilities Management Company Revenue By Service And Country Information PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Facilities Management Company Revenue By Service And Country Information PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
Eight Steps Infographics To Improve Cyber Security Icons PDF
Persuade your audience using this eight steps infographics to improve cyber security icons pdf. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including threats, knowledge, monitoring, authentication, protection. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
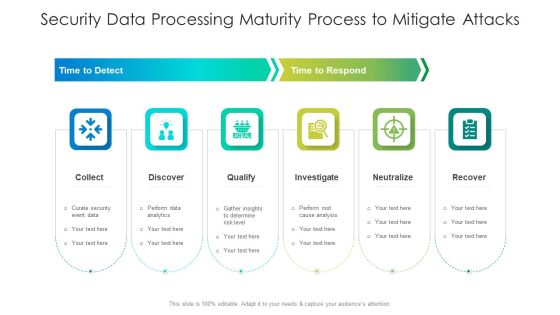
Security Data Processing Maturity Process To Mitigate Attacks Ideas PDF
Persuade your audience using this security data processing maturity process to mitigate attacks ideas pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including qualify, analysis, determine. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Role Based Access Control RBAC Securities Icon Demonstration PDF
Persuade your audience using this Role Based Access Control RBAC Securities Icon Demonstration PDF. This PPT design covers Three stages, thus making it a great tool to use. It also caters to a variety of topics including Role Based, Access Control. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Information Technology Solutions Business Profile Client Reviews And Testimonials Information PDF
This slides focuses on client testimonials post using our products and services which helps to build credibility and reliability to business and helps in decision making process. Presenting Information Technology Solutions Business Profile Client Reviews And Testimonials Information PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Been Connected, Evolving Moving, Excellent Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Data Center Infrastructure Technologies What Are Service Meshes Topics PDF
This slide depicts service meshes and how it works to enable speedy, reliable and secure communication among containerized and temporary application infrastructure services. Explore a selection of the finest Data Center Infrastructure Technologies What Are Service Meshes Topics PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Data Center Infrastructure Technologies What Are Service Meshes Topics PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

E Commerce Circle Examples Ppt Powerpoint Slides
This is a e commerce circle examples ppt powerpoint slides. This is a seven stage process. The stages in this process are business e commerce, security services, web hosting, shopping cart, web design, merchant processing, online marketing, data storage.

Value Chain Analysis Strategic Management Ppt Summary
This is a value chain analysis strategic management ppt summary. This is a seven stage process. The stages in this process are securing raw materials and other resources, research and development, product design, production, marketing, distribution, customer service.

Topics That Fall Under The Umbrella Of Cloud Security Cloud Computing Security IT Ppt Model Example Introduction PDF
This slide shows the various topics that fall under the umbrella of cloud security, namely data center security, access control, threat prevention, threat detection, threat mitigation, redundancy, and legal compliance. Presenting topics that fall under the umbrella of cloud security cloud computing security it ppt model example introduction pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like data centre security, threat prevention, access control, threat detection, threat mitigation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Banking Overview Diagram Sample Ppt Slides
This is a banking overview diagram sample ppt slides. This is a one stage process. The stages in this process are banking and finance, wealth management, network security and solution, systems integration, commercial banking, database development and administration, data warehouse solutions, consumer banking, ui, ux, application design and development, project management, business analysis and quality assurance, investment banking, architecture services, big data and cloud computing.

Case Study 2 Banks Cyber Security Infrastructure Mockup PDF
Presenting case study 2 banks cyber security infrastructure mockup pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like case study 2 banks cyber security infrastructure. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
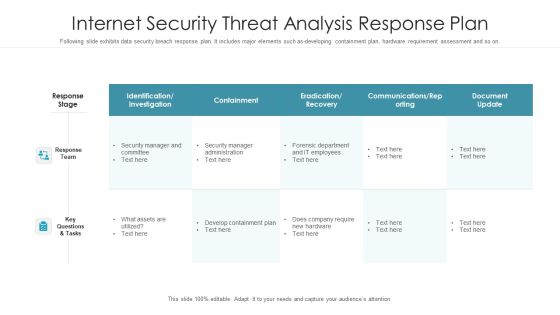
Internet Security Threat Analysis Response Plan Graphics PDF
Following slide exhibits data security breach response plan. It includes major elements such as-developing containment plan, hardware requirement assessment and so on. Pitch your topic with ease and precision using this internet security threat analysis response plan graphics pdf. This layout presents information on response team, response stage, key questions and tasks. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Internet Security Threat Analysis With Customer Centric Approach Mockup PDF
Data security breach steps with customer centric approach. It includes 5 steps such as- proactive and preventive analysis, data protection as the default and so on. Showcasing this set of slides titled internet security threat analysis with customer centric approach mockup pdf. The topics addressed in these templates are data minimization, data protection, proactive and preventive. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
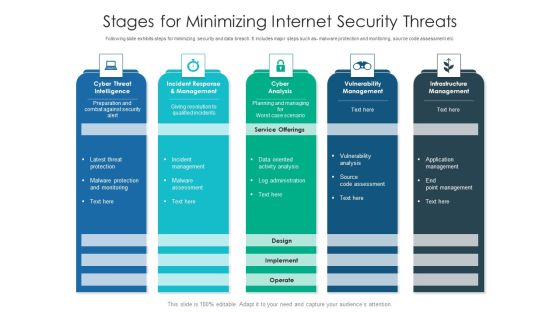
Stages For Minimizing Internet Security Threats Ideas PDF
Following slide exhibits steps for minimizing security and data breach. It includes major steps such as- malware protection and monitoring, source code assessment etc. Pitch your topic with ease and precision using this stages for minimizing internet security threats ideas pdf. This layout presents information on infrastructure management, cyber analysis, vulnerability management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Current Security Management Challenges The Company Is Facing Download PDF
Presenting current security management challenges the company is facing download pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like potential insider threats, external security breaches, rise of caas. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Differentiating 2 Items Illustration For Free Internet Security Clipart PDF
Presenting differentiating 2 items illustration for free internet security clipart pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like differentiating 2 items illustration for free internet security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Risk Management Plan Table Of Contents Pictures PDF
Presenting cyber security risk management plan table of contents pictures pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like present scenario, roles and responsibilities, training and budget, dashboards, security infrastructure performance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Risk Security Company Users And Protection Introduction PDF
The following slide highlights the cyber threat security companies with its users retailers, BFSI, large scale enterprises, protection and pricing. Showcasing this set of slides titled cyber risk security company users and protection introduction pdf. The topics addressed in these templates are company, users, protection. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Real Time Assessment Of Security Threats SIEM Integrations Slides PDF
Presenting real time assessment of security threats siem integrations slides pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security events, network logs, applications and devices, it infrastructure. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Multipoint Checklist To Improve Computer Security Guidelines PDF
This slide shows comprehensive checklist used to enhance information technology security. It includes email phishing training, anti virus and malware use, password changes etc. Showcasing this set of slides titled Multipoint Checklist To Improve Computer Security Guidelines PDF The topics addressed in these templates are Frequent System, Control Administrative, System Password All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
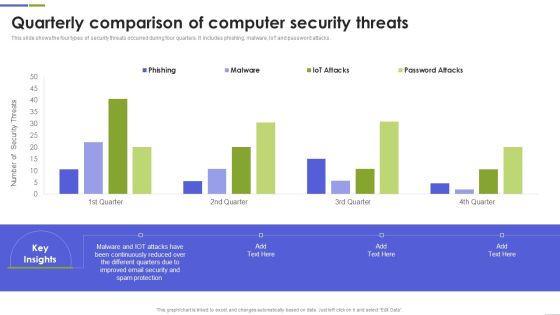
Quarterly Comparison Of Computer Security Threats Mockup PDF
This slide shows the four types of security threats occurred during four quarters. It includes phishing, malware, IoT and password attacks. Pitch your topic with ease and precision using this Quarterly Comparison Of Computer Security Threats Mockup PDF This layout presents information on Continuously Reduced, Different Quarters, Spam Protection It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Certified Information Systems Security Professional Cissp Examination Details Topics PDF
Presenting Certified Information Systems Security Professional Cissp Examination Details Topics PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Software Development, Security Assessment, Communications And Network. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
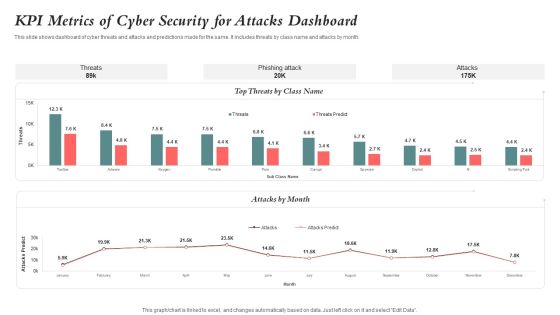
KPI Metrics Of Cyber Security For Attacks Dashboard Guidelines PDF
This slide shows dashboard of cyber threats and attacks and predictions made for the same. It includes threats by class name and attacks by month. Showcasing this set of slides titled KPI Metrics Of Cyber Security For Attacks Dashboard Guidelines PDF. The topics addressed in these templates are Kpi Metrics, Cyber Security, Attacks Dashboard. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Security Risks Associated With Electronic Data Interchange Technology Guidelines PDF
This slide provides glimpse about different risks compromising security that are associated with Electronic Data Interchange technology. It includes risks such as disclosure, message modification, sequence modification, etc.Showcasing this set of slides titled Security Risks Associated With Electronic Data Interchange Technology Guidelines PDF. The topics addressed in these templates are Private Multilateral, Multilateral Common, Carrier Dependent. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
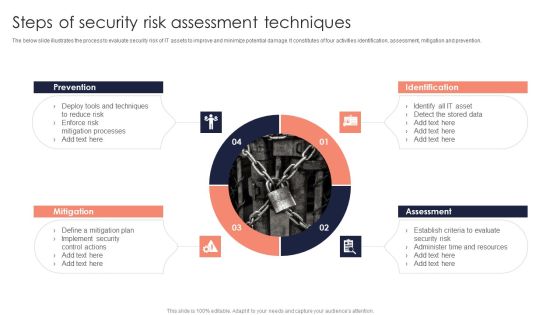
Steps Of Security Risk Assessment Techniques Introduction PDF
The below slide illustrates the process to evaluate security risk of IT assets to improve and minimize potential damage. It constitutes of four activities identification, assessment, mitigation and prevention. Showcasing this set of slides titled Steps Of Security Risk Assessment Techniques Introduction PDF. The topics addressed in these templates are Prevention, Identification, Assessment, Mitigation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cloud Network Security Tools And Package Graphics PDF
The slide represents tools encapsulated in cloud computing security software. The elements include computing tools, software such as SaaS, PaaS, IaaS and pricing package. Showcasing this set of slides titled Cloud Network Security Tools And Package Graphics PDF. The topics addressed in these templates are Saas, Paas, Iaas. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

One Page Internet Security Management Sheet PDF Document PPT Template
Presenting you an exemplary One Page Internet Security Management Sheet PDF Document PPT Template. Our one-pager template comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this One Page Internet Security Management Sheet PDF Document PPT Template Download now.

Cyber Security Business Communication Strategies Plan Background PDF
This slide shows communication strategy plan used to spread awareness regarding cyber security among employees. It includes communication objectives, activity, mode of communication and accountable person etc. Showcasing this set of slides titled Cyber Security Business Communication Strategies Plan Background PDF. The topics addressed in these templates are Communication Objective, Activity, Mode Communication. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
RCA Action Plan For Business Cyber Security Icons PDF
This slide shows root cause analysis action plan to identify and provide strategies for overcoming cyber security threats. It include root cause, action plan and outcomes, etc. Showcasing this set of slides titled RCA Action Plan For Business Cyber Security Icons PDF Elements. The topics addressed in these templates are Root Cause, Action Plan, Outcomes. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Benchmark Analysis For Data Security Software Mockup PDF
This slide shows comparison analysis of different data security software in order to choose the most suitable one. It include benchmarks like data privacy, data integrity and authentication etc. Showcasing this set of slides titled Benchmark Analysis For Data Security Software Mockup PDF. The topics addressed in these templates are Data Privacy, Data Integrity, Authentication. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
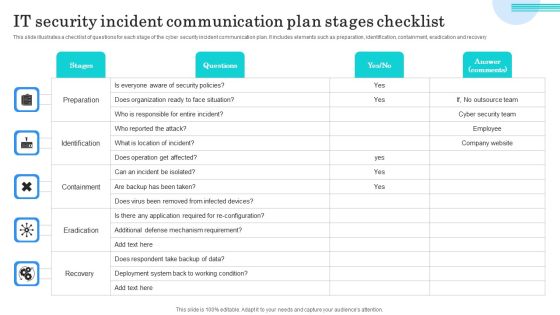
IT Security Incident Communication Plan Stages Checklist Topics PDF
This slide illustrates a checklist of questions for each stage of the cyber security incident communication plan. It includes elements such as preparation, identification, containment, eradication and recovery. Showcasing this set of slides titled IT Security Incident Communication Plan Stages Checklist Topics PDF. The topics addressed in these templates are Preparation, Identification, Containment. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Blockchain Security Solutions Deployment Advantages Of Blockchain Technology Brochure PDF
This slide represents the various advantages of blockchain technology based on information security, digital freedom, privacy, and lower transaction fees. Find a pre-designed and impeccable Blockchain Security Solutions Deployment Advantages Of Blockchain Technology Brochure PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Cyber Security Incident Response Process Flow Chart Information PDF
This slide represents the flow chart representing the detection and reaction to cyber security incidents, determination of their scope and risk and reduction of likelihood of incident from reoccurring. It starts with incident declaration and ends with system recovery. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cyber Security Incident Response Process Flow Chart Information PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cyber Security Incident Response Process Flow Chart Information PDF.
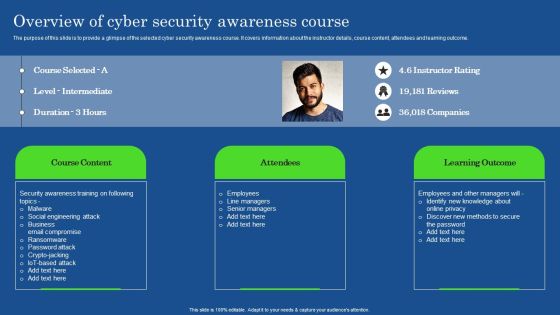
Overview Of Cyber Security Awareness Course Brochure PDF
The purpose of this slide is to provide a glimpse of the selected cyber security awareness course. It covers information about the instructor details, course content, attendees and learning outcome. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Overview Of Cyber Security Awareness Course Brochure PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Overview Of Cyber Security Awareness Course Brochure PDF.

Cyber Security Crisis Management Action Plan Timeline Topics PDF
This slide represents the timeline of effective management and minimization of impact of cyber security incidents on the business of the company. It includes details related to incident response, business continuity and review and recovery. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cyber Security Crisis Management Action Plan Timeline Topics PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cyber Security Crisis Management Action Plan Timeline Topics PDF

Information Systems Security And Risk Management Plan Challenges And Solutions In Information Security Risk Management Summary PDF
This slide showcases challenges involved in formulating risk management program for information security. It also shows solutions to tackle the challenges and impact of implementing them. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Information Systems Security And Risk Management Plan Challenges And Solutions In Information Security Risk Management Summary PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Information Systems Security And Risk Management Plan Challenges And Solutions In Information Security Risk Management Summary PDF
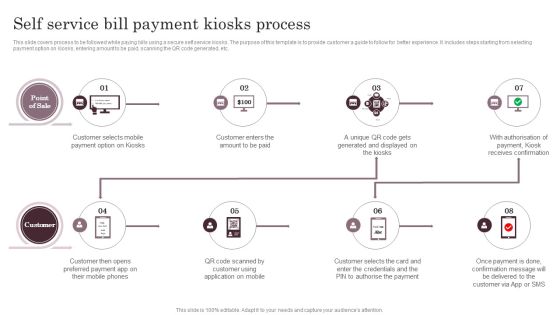
Omnichannel Services Solution In Financial Sector Self Service Bill Payment Kiosks Process Download PDF
This slide covers process to be followed while paying bills using a secure self service kiosks. The purpose of this template is to provide customer a guide to follow for better experience. It includes steps starting from selecting payment option on kiosks, entering amount to be paid, scanning the QR code generated, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Omnichannel Services Solution In Financial Sector Self Service Bill Payment Kiosks Process Download PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Omnichannel Services Solution In Financial Sector Self Service Bill Payment Kiosks Process Download PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
Dollar Symbol Under Umbrella With Icons Powerpoint Templates
This business diagram has been designed with graphic of dollar symbol under umbrella. This infographic design can be used for concept of dollar saving. Use this amazing slide for business and marketing related presentations.

Current State Of Security Automation With Projected Development Rules PDF
This slide highlights the current state of security automation in the pie chart format. It includes projected development of security automation and state of security automation. If you are looking for a format to display your unique thoughts, then the professionally designed Current State Of Security Automation With Projected Development Rules PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Current State Of Security Automation With Projected Development Rules PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Comparison Of Various Security Awareness Training Software Demonstration PDF
The purpose of this slide is to drawn comparison of multiple software which can be used to provide cyber security training to the key stakeholders. Information covered in this slide is related to phishing simulations, security reporting, individualized security training plan etc. If you are looking for a format to display your unique thoughts, then the professionally designed Comparison Of Various Security Awareness Training Software Demonstration PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Comparison Of Various Security Awareness Training Software Demonstration PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
 Home
Home