Construction Safety

Recent Technologies In IT Industry Cyber Security Technology Market Overview Download PDF
This slide explains Cyber security technology market overview with top players in the year 2021. It also predicts market growth and compound annual growth rate from year 2021 till 2028. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Recent Technologies In IT Industry Cyber Security Technology Market Overview Download PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Recent Technologies In IT Industry Cyber Security Technology Market Overview Download PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.

Execution Of ICT Strategic Plan Data Encryption Model For Effective Information Security Guidelines PDF
This slide represents data encryption model for effective information security. It includes data encoding, data decoding, backup repository etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Execution Of ICT Strategic Plan Data Encryption Model For Effective Information Security Guidelines PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Execution Of ICT Strategic Plan Data Encryption Model For Effective Information Security Guidelines PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Cognitive Sensor Network CR Wsns In Military And Public Security Applications Template PDF
This slide depicts the use of cognitive radio wireless sensor networks in the military and public security applications, including targeting, command and control, information collection, battlefield surveillance, assistant intelligence, and targeting. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cognitive Sensor Network CR Wsns In Military And Public Security Applications Template PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cognitive Sensor Network CR Wsns In Military And Public Security Applications Template PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Dashboard To Track IT Security Incidents Prevailing Across Firm Infographics PDF
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Dashboard To Track IT Security Incidents Prevailing Across Firm Infographics PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Dashboard To Track IT Security Incidents Prevailing Across Firm Infographics PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Series Of Cyber Security Attacks Against Ukraine 2022 Russian Cyber Operations Against Ukraine Timeline Guidelines PDF
This slide represents the timeline of russian cyber operations against ukraine by listing all the cyber attacks held from 14 february to 27 february 2022. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Series Of Cyber Security Attacks Against Ukraine 2022 Russian Cyber Operations Against Ukraine Timeline Guidelines PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Series Of Cyber Security Attacks Against Ukraine 2022 Russian Cyber Operations Against Ukraine Timeline Guidelines PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
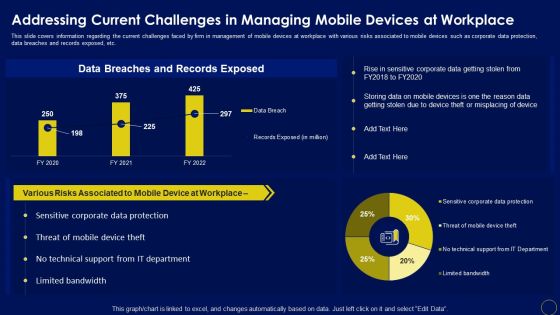
Addressing Current Challenges In Managing Business Mobile Device Security Management Summary PDF
This slide covers information regarding the current challenges faced by firm in management of mobile devices at workplace with various risks associated to mobile devices such as corporate data protection, data breaches and records exposed, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Addressing Current Challenges In Managing Business Mobile Device Security Management Summary PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Addressing Current Challenges In Managing Business Mobile Device Security Management Summary PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Cloud Content Delivery Network Data Security Handled By CDN Guidelines PDF
This slide demonstrates how CDN protects data by issuing TLS or SSL certificates, blocking Bots and crawlers, and defending against DDoS assaults. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cloud Content Delivery Network Data Security Handled By CDN Guidelines PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cloud Content Delivery Network Data Security Handled By CDN Guidelines PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Security Software Company Investor Funding Pitch Deck Financial Projections Information PDF
This slide showcases forecasted growth of company that will assist investors to determine future potential of business and make investment decision that will be amost profitable for them. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Security Software Company Investor Funding Pitch Deck Financial Projections Information PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Security Software Company Investor Funding Pitch Deck Financial Projections Information PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
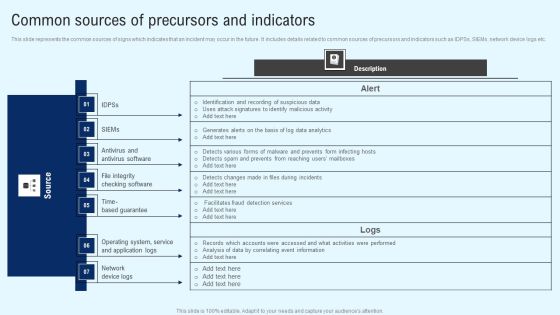
Implementing Cyber Security Incident Common Sources Of Precursors And Indicators Inspiration PDF
This slide represents the common sources of signs which indicates that an incident may occur in the future. It includes details related to common sources of precursors and indicators such as IDPSs, SIEMs, network device logs etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Implementing Cyber Security Incident Common Sources Of Precursors And Indicators Inspiration PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Implementing Cyber Security Incident Common Sources Of Precursors And Indicators Inspiration PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
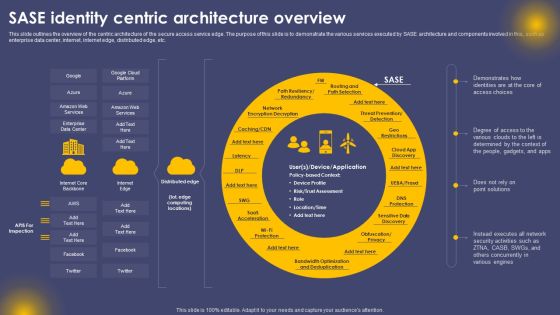
SASE Identity Centric Architecture Overview Ppt Pictures Layouts PDF
This slide outlines the overview of the centric architecture of the secure access service edge. The purpose of this slide is to demonstrate the various services executed by SASE architecture and components involved in this, such as enterprise data center, internet, internet edge, distributed edge, etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward SASE Identity Centric Architecture Overview Ppt Pictures Layouts PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal SASE Identity Centric Architecture Overview Ppt Pictures Layouts PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Introduction To Branchless Banking In Next Generation Payments Structure PDF
This slide covers introduction to branchless banking services offered by banking sector. The purpose of this template is to provide an overview on benefits of using branchless banking services. It includes advantages such as supporting multiple transactions, advanced payment security, contactless payment solutions along with categories covering digital wallets, IVR bill payments, API bill payments and credit card bills. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Introduction To Branchless Banking In Next Generation Payments Structure PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Introduction To Branchless Banking In Next Generation Payments Structure PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Omnichannel Strategy Implementation For Banking Solutions Factors Driving Usability Of Omnichannel Inspiration PDF
This slide covers imperative drivers that helps in usability of omnichannel banking services. It includes factors such a multi-channel experience, ease of integration, customizable, highly secure and easy adaptability. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Omnichannel Strategy Implementation For Banking Solutions Factors Driving Usability Of Omnichannel Inspiration PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Omnichannel Strategy Implementation For Banking Solutions Factors Driving Usability Of Omnichannel Inspiration PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.

Virtual WAN Architecture Benefits Of Software Defined Wide Area Network Ideas PDF
This slide outlines the various advantages of the software-defined wide-area network to businesses. The purpose of this slide is to demonstrate the multiple benefits of SD-WAN, including improved security, better application experience, simplified management and optimized cloud connectivity. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Virtual WAN Architecture Benefits Of Software Defined Wide Area Network Ideas PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Virtual WAN Architecture Benefits Of Software Defined Wide Area Network Ideas PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers

Cybersecurity Operations Cybersecops Benefits Of Implementing Secops Icons PDF
This slide represents the main advantages of deploying security operations in an organization. The purpose of this slide is to showcase the critical benefits of SecOps implementation, covering an increased workforce to deal with threats, fewer buggy apps, quick response to threats, fewer security breaches, and so on. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cybersecurity Operations Cybersecops Benefits Of Implementing Secops Icons PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cybersecurity Operations Cybersecops Benefits Of Implementing Secops Icons PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
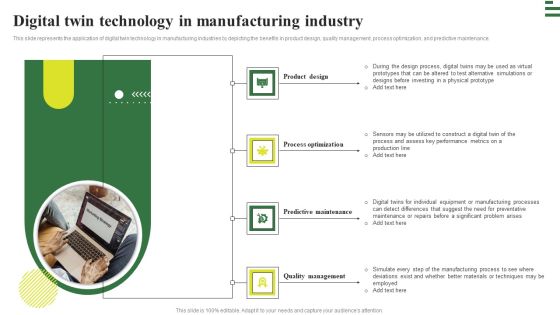
Transforming Manufacturing With Automation Digital Twin Technology Download PDF
This slide represents the application of digital twin in supply chain management to predict the quality of packaging materials, improve shipment security, warehouse design, and operational performance optimization, and create a logistics system. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Transforming Manufacturing With Automation Digital Twin Technology Download PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Transforming Manufacturing With Automation Digital Twin Technology Download PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.

Cloud Based Computing Analysis Managing Compliance In Multi Cloud Environment Summary PDF
This slide covers the policies for managing compliance in multi cloud such as securing cloud user information, optimizing resource usage and value, optimizing system and resource usage etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cloud Based Computing Analysis Managing Compliance In Multi Cloud Environment Summary PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cloud Based Computing Analysis Managing Compliance In Multi Cloud Environment Summary PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers

Data Governance IT Responsibilities Of A Data Steward In Stewardship Program Introduction PDF
This slide represents a data stewards responsibilities, including data cataloging, monitoring, data workflows, advocacy, and security. They are also responsible for maintaining appropriate data lineage that will help them and stakeholders. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Data Governance IT Responsibilities Of A Data Steward In Stewardship Program Introduction PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Data Governance IT Responsibilities Of A Data Steward In Stewardship Program Introduction PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Key Features And Benefits Of Cloud Project Management Topics PDF
The following slide depicts major features and benefits of cloud based project management. It provides details about reliability, integration, collaboration, secure backup, free monthly trials, remote team support, etc.Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Key Features And Benefits Of Cloud Project Management Topics PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Key Features And Benefits Of Cloud Project Management Topics PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.

Confidential Computing System Technology Technologies Used To Protect Data In Use Inspiration PDF
This slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Confidential Computing System Technology Technologies Used To Protect Data In Use Inspiration PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Confidential Computing System Technology Technologies Used To Protect Data In Use Inspiration PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Improving Business Procedures Enterprise Resource Planning System Drafting ERP Budget To Plan Cost Professional PDF
The following slide covers the enterprise resource planning ERP budget to project and estimate software cost accurately. It includes elements such as hardware, software, facility, network, security, contingency etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Improving Business Procedures Enterprise Resource Planning System Drafting ERP Budget To Plan Cost Professional PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Improving Business Procedures Enterprise Resource Planning System Drafting ERP Budget To Plan Cost Professional PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
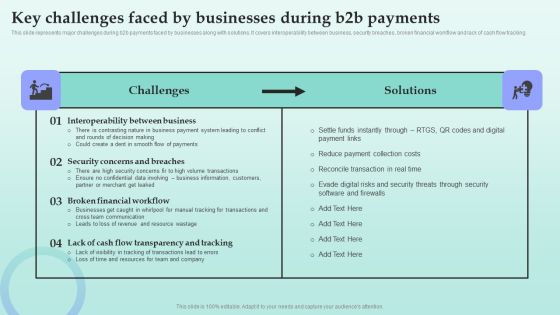
Strategies For Successful Customer Base Development In B2b M Commerce Key Challenges Faced By Businesses During B2b Background PDF
This slide represents major challenges during b2b payments faced by businesses along with solutions. It covers interoperability between business, security breaches, broken financial workflow and lack of cash flow tracking. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Strategies For Successful Customer Base Development In B2b M Commerce Key Challenges Faced By Businesses During B2b Background PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Strategies For Successful Customer Base Development In B2b M Commerce Key Challenges Faced By Businesses During B2b Background PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.

Cyber Attack Incident Tracking Dashboard Ppt PowerPoint Presentation File Styles PDF
The following slide depicts the number of cyber-attacks incurred during year end to monitor security trends. It includes elements such as prevented, allowed attacks, additional threats detected, number of infected hosts and malicious files etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cyber Attack Incident Tracking Dashboard Ppt PowerPoint Presentation File Styles PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cyber Attack Incident Tracking Dashboard Ppt PowerPoint Presentation File Styles PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
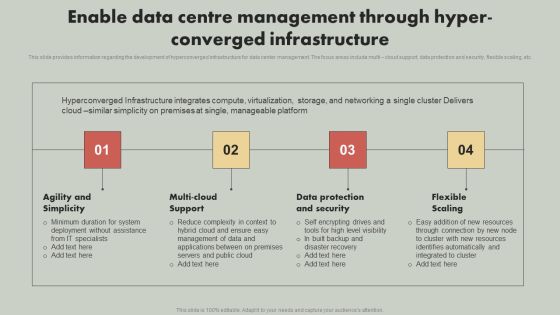
IT Reducing Costs And Management Tips Enable Data Centre Management Through Hyper Converged Infrastructure Elements PDF
This slide provides information regarding the development of hyperconverged infrastructure for data center management. The focus areas include multi cloud support, data protection and security, flexible scaling, etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward IT Reducing Costs And Management Tips Enable Data Centre Management Through Hyper Converged Infrastructure Elements PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal IT Reducing Costs And Management Tips Enable Data Centre Management Through Hyper Converged Infrastructure Elements PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
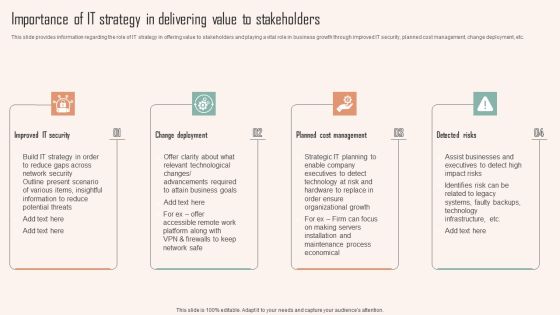
Importance Of IT Strategy In Delivering Value To Stakeholders Ppt PowerPoint Presentation File Infographic Template PDF
This slide provides information regarding the role of IT strategy in offering value to stakeholders and playing a vital role in business growth through improved IT security, planned cost management, change deployment, etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Importance Of IT Strategy In Delivering Value To Stakeholders Ppt PowerPoint Presentation File Infographic Template PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Importance Of IT Strategy In Delivering Value To Stakeholders Ppt PowerPoint Presentation File Infographic Template PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.

Associate Marketing Company Outline Our Unique Selling Proposition USP Microsoft PDF
This slide highlights the Yashbiz company unique selling proposition which includes more than 80 products, secure shopping, 100 percent delivery and paid shipping. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Associate Marketing Company Outline Our Unique Selling Proposition USP Microsoft PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Associate Marketing Company Outline Our Unique Selling Proposition USP Microsoft PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

WAF Introduction Best Practices For Successful Web Application Firewall Implementation Brochure PDF
This slide represents the steps to be considered by organizations to maximize the benefits of WAF. The purpose of this slide is to showcase the best practices businesses can consider for successful web application firewall implementation, such as support for app security goals, evaluation and testing, and resource listing. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward WAF Introduction Best Practices For Successful Web Application Firewall Implementation Brochure PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal WAF Introduction Best Practices For Successful Web Application Firewall Implementation Brochure PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.

Saas Continuous Income Generation Model For Software Startup Challenges In Recurring Business Model Guidelines PDF
The purpose of the following slide is to show multiple challenges that the company can face while implementing a recurring revenue model , these challenges can be customer management, Payment security and invoicing. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Saas Continuous Income Generation Model For Software Startup Challenges In Recurring Business Model Guidelines PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Saas Continuous Income Generation Model For Software Startup Challenges In Recurring Business Model Guidelines PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.

Software Defined Networking Development Strategies Factors Influencing Software Defined Networking Template PDF
This slide represents the factors influencing SDN adoption, including cultural change, security risks, interoperability, scalability, performance, and reliability. SDN is appealing regarding network simplicity and investment, and operational cost savings. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Software Defined Networking Development Strategies Factors Influencing Software Defined Networking Template PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Software Defined Networking Development Strategies Factors Influencing Software Defined Networking Template PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.

Comprehensive Resource Guide To Master GPT 3 GPT 3 Apps For Search Glean Inspiration PDF
This slide showcases GPT 3 application Glean which is helpful artificial intelligence oriented tool for automating business knowledge generation and transfer needs. It provides details about adaptive AI, personalization, security, etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Comprehensive Resource Guide To Master GPT 3 GPT 3 Apps For Search Glean Inspiration PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Comprehensive Resource Guide To Master GPT 3 GPT 3 Apps For Search Glean Inspiration PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.

Cashless Payment Strategies To Enhance Business Performance Impact Assessment Of Mobile Wallet Application Professional PDF
Mentioned slide provides information about mobile wallet payment implementation impact on business activities. It includes impacts such as easy customer data analytics, offer reward and loyalty points, smooth workflow, and improved security. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cashless Payment Strategies To Enhance Business Performance Impact Assessment Of Mobile Wallet Application Professional PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cashless Payment Strategies To Enhance Business Performance Impact Assessment Of Mobile Wallet Application Professional PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers
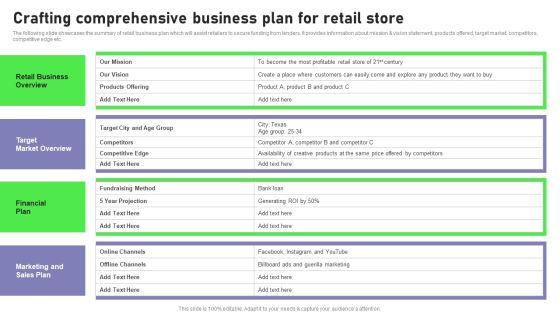
Retail Outlet Opening To Enhance Product Sale Crafting Comprehensive Business Graphics PDF
The following slide showcases the summary of retail business plan which will assist retailers to secure funding from lenders. It provides information about mission and vision statement, products offered, target market, competitors, competitive edge etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Retail Outlet Opening To Enhance Product Sale Crafting Comprehensive Business Graphics PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Retail Outlet Opening To Enhance Product Sale Crafting Comprehensive Business Graphics PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Cybersecurity Operations Cybersecops Problems With Current Network System Formats PDF
This slide represents the severity level of application vulnerabilities and the number of total attacks. The purpose of this slide is to showcase the various threats caused by security vulnerabilities. The main threats include sensitive data leakage, unauthorized access to data and apps, and so on. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cybersecurity Operations Cybersecops Problems With Current Network System Formats PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cybersecurity Operations Cybersecops Problems With Current Network System Formats PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
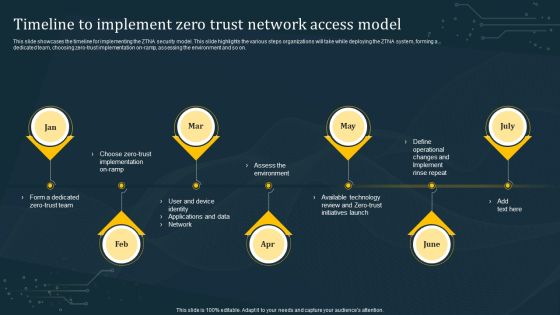
Timeline To Implement Zero Trust Network Access Model Rules PDF
This slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Timeline To Implement Zero Trust Network Access Model Rules PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Timeline To Implement Zero Trust Network Access Model Rules PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers

Agile Approach In Information Technology Projects Seven Properties Of Crystal Clear Themes PDF
This slide covers properties of crystal clear programming such as easy access to users, personal safety, focus, agile technical environment, frequent delivery, reflection improvement, osmotic communication etc., Slidegeeks has constructed Agile Approach In Information Technology Projects Seven Properties Of Crystal Clear Themes PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Project Management Software Capital Raising Deck Why Invest With Us Download PDF
Following slide showcases benefits that are offered by company to assure business safety. It include pointers such as consistent backups, development processes, encryption, code review etc. Slidegeeks has constructed Project Management Software Capital Raising Deck Why Invest With Us Download PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

Use Cases Of Service Robots In Different Sectors Ideas PDF
The purpose of this slide is to outline the various applications of service robots. The use cases discusses are cleaning, checking and maintenance, construction, hospitality, manufacturing, agriculture, logistics, security and defense mechanisms, etc. Slidegeeks has constructed Use Cases Of Service Robots In Different Sectors Ideas PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Table Of Contents For Blockchain Security Solutions Deployment Ideas PDF
Slidegeeks has constructed Table Of Contents For Blockchain Security Solutions Deployment Ideas PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
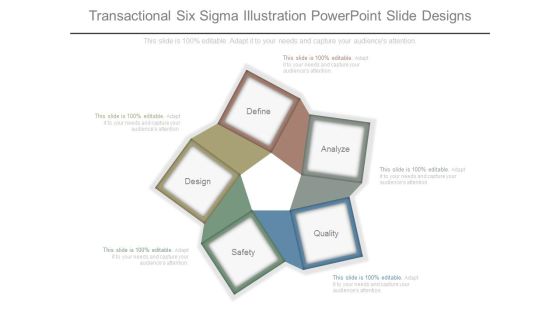
Transactional Six Sigma Illustration Powerpoint Slide Designs
This is a transactional six sigma illustration powerpoint slide designs. This is a five stage process. The stages in this process are define, design, safety, quality, analyze.

Building Positive Relationships Example Ppt Design
This is a building positive relationships example ppt design. This is a seven stage process. The stages in this process are safety, trust, respect, connect, identify, close, plan.

Agency Performance Ppt PowerPoint Presentation Background Designs
This is a agency performance ppt powerpoint presentation background designs. This is a four stage process. The stages in this process are transcore, viewability, brand safety, ad fraud.

Digital Dashboard Resource Kit Ppt Powerpoint Slides Design
This is a digital dashboard resource kit ppt powerpoint slides design. This is a four stage process. The stages in this process are sales rate, progress, profits, safety.

Transactional Six Sigma Illustration Ppt Inspiration
This is a transactional six sigma illustration ppt inspiration. This is a six stage process. The stages in this process are safety, quality, design, measure, analyze, control.

Cyber Security Incident Response KPI Dashboard Microsoft PDF
This slide represents dashboard showing the key metrics of cyber security incident response. It includes key performance indicators such as risk score, compliance status, threat level etc. Slidegeeks has constructed Cyber Security Incident Response KPI Dashboard Microsoft PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

Organizing Security Awareness Outlook Of Social Engineering Attack Ideas PDF
The purpose of this slide is to showcase an example of social engineering attack. It also covers information about how the social engineering attack work and spread malware. Slidegeeks has constructed Organizing Security Awareness Outlook Of Social Engineering Attack Ideas PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Information Security Purpose Limitation Principle Of GDPR Law Graphics PDF
This slide depicts the purpose limitation principle, which states that you should be clear from the start about the reasons and intentions for collecting and processing data. Slidegeeks has constructed Information Security Purpose Limitation Principle Of GDPR Law Graphics PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

Information Systems Security And Risk Management Plan Timeline Professional PDF
Slidegeeks has constructed Information Systems Security And Risk Management Plan Timeline Professional PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
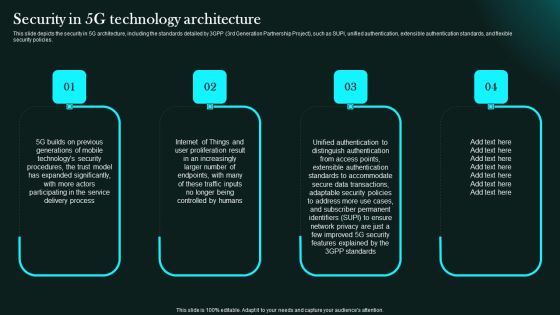
Security In 5G Technology Architecture 5G Network Functional Architecture Clipart PDF
This slide depicts the security in 5G architecture, including the standards detailed by 3GPP 3rd Generation Partnership Project, such as SUPI, unified authentication, extensible authentication standards, and flexible security policies.Slidegeeks has constructed Security In 5G Technology Architecture 5G Network Functional Architecture Clipart PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Table Of Contents Of Security Control Techniques For Real Estate Project Portrait PDF
Slidegeeks has constructed Table Of Contents Of Security Control Techniques For Real Estate Project Portrait PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

IT System Risk Management Guide Technical Security Control Model With Supporting Function Themes PDF
The following slide highlights the technical security control model which showcases different relationships and also includes supporting technical control function for protection and security. Slidegeeks has constructed IT System Risk Management Guide Technical Security Control Model With Supporting Function Themes PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

Table Of Contents Series Of Cyber Security Attacks Against Ukraine 2022 Elements PDF
Slidegeeks has constructed Table Of Contents Series Of Cyber Security Attacks Against Ukraine 2022 Elements PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

Determine Standard Mobile Device Management Components Business Mobile Device Security Sample PDF
This slide provides information regarding essential standard mobile device management components terms of central management console, registry.Slidegeeks has constructed Determine Standard Mobile Device Management Components Business Mobile Device Security Sample PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Table Of Contents Security Automation To Analyze And Mitigate Cyberthreats Diagrams PDF
Slidegeeks has constructed Table Of Contents Security Automation To Analyze And Mitigate Cyberthreats Diagrams PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Kpis To Measure Information Security Risk Management Cybersecurity Risk Assessment Infographics PDF
This slide showcases KPIs that can help organization to measure the impact of cybersecurity risk management programme. It showcases estimated figures before and after implementation of plan. Slidegeeks has constructed Kpis To Measure Information Security Risk Management Cybersecurity Risk Assessment Infographics PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Table Of Contents For Developing IT Security Strategy To Prevent Data Assets Pictures PDF
Slidegeeks has constructed Table Of Contents For Developing IT Security Strategy To Prevent Data Assets Pictures PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

IT Policies And Procedures Password Creation And Management Policy Diagrams PDF
This slide depicts the password creation and management policy that explains how to create, implement, and review a defined procedure for establishing, updating, and maintaining strong and secure passwords. Slidegeeks has constructed IT Policies And Procedures Password Creation And Management Policy Diagrams PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

CRM Software Deployment Journey Implementation Steps Introduction For Identifying Introduction PDF
This slide covers the process of determining the CRM users and creating their roles and profiles in order to maintain data security. Slidegeeks has constructed CRM Software Deployment Journey Implementation Steps Introduction For Identifying Introduction PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Digital Risk Assessment Process For Cloud Services Ppt Pictures Topics PDF
The following slide highlights the cyber security process for cloud computing, cloud storage and cloud analytics storage. It depict identification, network security, data safety, application safety, monitoring and policy control to govern, protect and control the cloud services. Persuade your audience using this Digital Risk Assessment Process For Cloud Services Ppt Pictures Topics PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Identification, Data Safety, Monitoring, Policy Control. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Deployment Of Omnichannel Banking Solutions Introduction To Secure Self Service Bill Payment Kiosks Portrait PDF
This slide covers brief introduction about kiosks technology launched by banking sector as an initiative towards omnichannel strategy. The purpose of this template is to provide information to users about the features and benefits of using self service kiosk for their banking needs. It includes benefits such as accepting all payment options, providing real-time data transmission, transaction reporting, bilingual interface, etc. Slidegeeks has constructed Deployment Of Omnichannel Banking Solutions Introduction To Secure Self Service Bill Payment Kiosks Portrait PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

Business Diagram Graphics Of Three Pen Drives Presentation Template
Graphic of three pen drives has been sued to craft this power point template diagram. This PPT contain the concept of data storage and safety. Use this PPT for business and technology related presentations.
Business Framework Entry Barrier PowerPoint Presentation
This business framework power point template has been crafted with graphic of traffic barrier and cones. This diagram template may be used for traffic rules related topics and build exclusive presentations on safety.

 Home
Home