AI PPT Maker
Templates
PPT Bundles
Design Services
Business PPTs
Business Plan
Management
Strategy
Introduction PPT
Roadmap
Self Introduction
Timelines
Process
Marketing
Agenda
Technology
Medical
Startup Business Plan
Cyber Security
Dashboards
SWOT
Proposals
Education
Pitch Deck
Digital Marketing
KPIs
Project Management
Product Management
Artificial Intelligence
Target Market
Communication
Supply Chain
Google Slides
Research Services
 One Pagers
One PagersAll Categories
-
Home
- Customer Favorites
- Construction Safety Plan
Construction Safety Plan

IT Communication Infrastructure Services Download PDF
The following slide demonstrates information and communication technology infrastructure services for optimizing output, mitigate internal and external security threat. It includes components such as operations and network management etc. Persuade your audience using this IT Communication Infrastructure Services Download PDF. This PPT design covers two stages, thus making it a great tool to use. It also caters to a variety of topics including Applications, Description, Operations Management . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Application Development Life Cycle Phase 2 Designing The Product Architecture Template PDF
This slide depicts the designing of the product architecture phase of SDLC, including the factors documented in the DDS sheet such as risk assessment, product resilience, design flexibility, cost, etc. Presenting application development life cycle phase 2 designing the product architecture template pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like overview and importance of secure sdlc. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
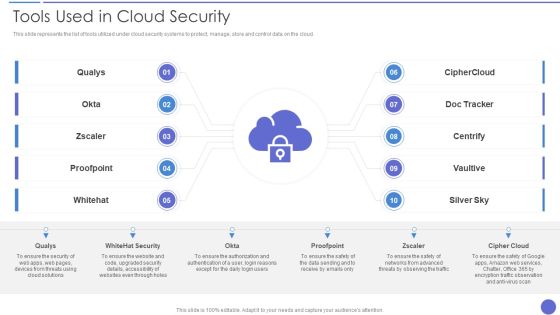
Tools Used In Cloud Security Template PDF
This slide represents the list of tools utilized under cloud security systems to protect, manage, store and control data on the cloud. Presenting Tools Used In Cloud Security Template PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Qualys, Whitehat Security, Cipher Cloud. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Techniques And Strategies To Reduce Security Management Risks Security Risk Management Assessment Checklist Demonstration PDF
This slide shows a security risk management assessment checklist with multiple categories.Presenting techniques and strategies to reduce security management risks security risk management assessment checklist demonstration pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like information security policy, security of third party access, responding to security In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Corporate Security And Risk Management Table Of Contents Corporate Security And Risk Download PDF
Presenting corporate security and risk management table of contents corporate security and risk download pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like current scenario assessment, ensuring physical security, securing firm from natural calamity threats, handling cyber threats to secure digital assets. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cybersecurity Training Workshop On Security Breach Trends Icon Designs PDF
Presenting Cybersecurity Training Workshop On Security Breach Trends Icon Designs PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Cybersecurity Training, Workshop On Security, Breach Trends Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
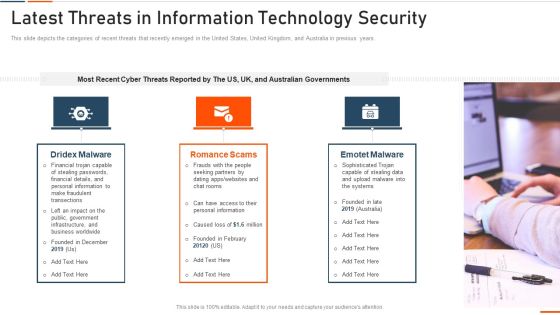
Latest Threats In Information Technology Security Ppt Pictures Designs PDF
This slide represents the different elements of Network security such as application security, network security, information security, etc. This is a latest threats in information technology security ppt pictures designs pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like network security, cloud security, application security, operational security, information security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

PCI Certification For Increasing Security Of Online Transactions Designs PDF
This slide depicts payment card industry PCI certification for increasing security of online transactions. It provides information about authorization, 2 way authentication, one time password OTP, repository, cyber attacks, compliance, data breach, etc. Presenting this PowerPoint presentation, titled PCI Certification For Increasing Security Of Online Transactions Designs PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this PCI Certification For Increasing Security Of Online Transactions Designs PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable PCI Certification For Increasing Security Of Online Transactions Designs PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

CYBER Security Breache Response Strategy Ways To Detect Cyber Security Incidents Sample PDF
This slide represents the activities through which cyber incident management team can effectively and efficiently detect cyber security incidents. It includes various ways of detecting cyber security incidents such as unusual behavior from privileged user accounts etc. Create an editable CYBER Security Breache Response Strategy Ways To Detect Cyber Security Incidents Sample PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. CYBER Security Breache Response Strategy Ways To Detect Cyber Security Incidents Sample PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Information Security Storage Limitation Principle Of GDPR Law Designs PDF
This slide conveys the GDPR laws storage limitation principle, which prohibits you from holding personal data for longer than is required and requires you to justify your reasons for maintaining data. Get a simple yet stunning designed Information Security Storage Limitation Principle Of GDPR Law Designs PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Information Security Storage Limitation Principle Of GDPR Law Designs PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Service Provider Contract Review Agreement Checklist Information PDF
Purpose of this slide is to showcase contract checklist for service provider. It includes involvement of IT team, security specific language, setting benchmarks and auditing vendors. Showcasing this set of slides titled service provider contract review agreement checklist information pdf. The topics addressed in these templates are service provider contract review agreement checklist. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

CYBER Security Breache Response Strategy Key Lessons Learned By Organization From Cyber Security Incident Graphics PDF
This slide represents the key takeaways for the cyber security incident management team after they effectively respond to and manage the cyber attacks experienced by the organization. It includes key lessons learned by organization such as ransomware is here to stay etc. This CYBER Security Breache Response Strategy Key Lessons Learned By Organization From Cyber Security Incident Graphics PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
Elements Of Information Technology Security Information Technology Security Ppt Inspiration Icons PDF
This slide represents the network security element of network security and different network security methods such as firewalls, email security, web security, and antivirus software. Presenting elements of information technology security information technology security ppt inspiration icons pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like network security methods, tools, techniques, respond. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Pillars Of Cloud Security Visibility And Consistency Demonstration PDF
This slide depicts the visibility and consistency pillar of cloud security, and it further includes asset inventory, best cloud framework, and data security. Presenting Pillars Of Cloud Security Visibility And Consistency Demonstration PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Best Cloud Framework, Data Security, Asset Inventory. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Hard And Soft Facility Management Services Developing Tactical Fm Services Microsoft PDF
This slide highlights hard and soft facility management services which are offered by the company which includes cleaning services, support services, security services, catering services and technical services.The Hard And Soft Facility Management Services Developing Tactical Fm Services Microsoft PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
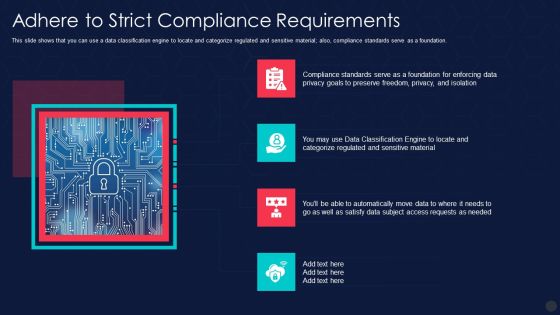
Information Privacy IT Adhere To Strict Compliance Requirements Slides PDF
This slide shows that you can use a data classification engine to locate and categorize regulated and sensitive material also, compliance standards serve as a foundation. Presenting information privacy it adhere to strict compliance requirements slides pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like adhere to strict compliance requirements. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Checklist Networking Cloud Computing Security IT Ppt Show Samples PDF
This slide defines the importance of network security under cloud security. It also shows how data should transfer over a network to protect it from malicious attacks. Presenting cloud security checklist networking cloud computing security it ppt show samples pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like security, mechanisms, security, critical data. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security Automation Tools Integration Table Of Contents Ppt Ideas Graphic Tips PDF
This is a IT Security Automation Tools Integration Table Of Contents Ppt Ideas Graphic Tips PDF template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Ineffective Security System, Security Automation, Architecture And Importance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
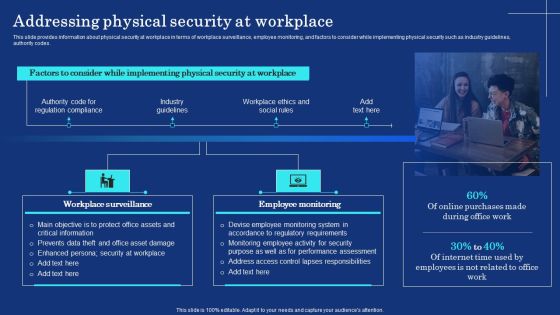
Organizational Assets Security Management Strategy Addressing Physical Security At Workplace Mockup PDF
This slide provides information about physical security at workplace in terms of workplace surveillance, employee monitoring, and factors to consider while implementing physical security such as industry guidelines, authority codes. Create an editable Organizational Assets Security Management Strategy Addressing Physical Security At Workplace Mockup PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Organizational Assets Security Management Strategy Addressing Physical Security At Workplace Mockup PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Eight Key Steps Of Successful Testing Process Ppt PowerPoint Presentation Model Visuals PDF
Persuade your audience using this eight key steps of successful testing process ppt powerpoint presentation model visuals pdf. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including keyword testing, object driven testing, manual tests. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Determine New Roles Pivotal For Successful Devops Security Designs PDF
This slide provides information regarding the new roles considered as pivotal for successful DevOps in terms of DevOps evangelist, release manager, automation architect integration specialist. Presenting determine new roles pivotal for successful devops security designs pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like manager, management, coordination. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Evaluation Of HR Security Policy And Procedure Diagrams PDF
Persuade your audience using this Evaluation Of HR Security Policy And Procedure Diagrams PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Evaluation HR Security, Policy Procedure. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
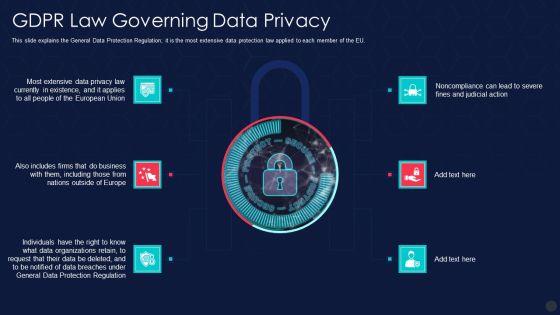
Information Privacy IT Gdpr Law Governing Data Privacy Ideas PDF
This slide explains the General Data Protection Regulation it is the most extensive data protection law applied to each member of the EU. Presenting information privacy it gdpr law governing data privacy ideas pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like gdpr law governing data privacy. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Privacy IT Importance Of Data Privacy Professional PDF
This slide illustrates the importance of data privacy in terms of developing trust with customers that value privacy and assisting with data management. Presenting information privacy it importance of data privacy professional pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like importance of data privacy. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Privacy IT Monitor And Detect Abnormal Activity On Sensitive Data Structure PDF
This slide highlights that you will have continuous monitoring and detection of abnormal activities of all the organizations data. Presenting information privacy it monitor and detect abnormal activity on sensitive data structure pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like monitor and detect abnormal activity on sensitive data. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Privacy IT Purpose Limitation Principle Of Gdpr Law Topics PDF
This slide depicts the purpose limitation principle, which states that you should be clear from the start about the reasons and intentions for collecting and processing data. Presenting information privacy it purpose limitation principle of gdpr law topics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like rpose limitation principle of gdpr law. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

SIEM Logging Sources SIEM Services Ppt Inspiration Format PDF
This slide covers the logging sources for SIEM which uses different devices such as security, network, servers, and applications. Presenting siem logging sources siem services ppt inspiration format pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like siem logging sources. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Elements Of IT Security IT Information Security Ppt Background Image PDF
This slide depicts the information security methodology and core information security principles such as confidentiality, integrity, and availability. Presenting elements of it security it information security ppt background image pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like integrity, confidentiality, availability. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Burp Suite Ethical Hacking Tool Ppt Portfolio Skills PDF
This slide depicts the burp suite ethical hacking tool, including its features such as open source and custom built software, easy to use login sequence recorder, crawl, and scan automation, etc. Presenting burp suite ethical hacking tool ppt portfolio skills pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like security, application, information. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Threats Contract Breaches With Clients Cloud Computing Security IT Ppt Ideas Introduction PDF
This slide defines the contract breaches with clients and customers that could be the biggest threat to the organizational data. Presenting cloud security threats contract breaches with clients cloud computing security it ppt ideas introduction pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like business, organization, sensitive data stored. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Allocate Team Roles And Responsibilities Ppt PowerPoint Presentation File Show PDF
The following slide showcases the key roles and responsibilities of cyber security team to enhance decision making and goal accomplishment. It includes activities such as developing information security strategies, managing security architecture, planning disaster recovery etc. Slidegeeks is here to make your presentations a breeze with Allocate Team Roles And Responsibilities Ppt PowerPoint Presentation File Show PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

How Does Cloud Security Work Governance Professional PDF
This slide describes how a cloud security system works and what controls or measures are implemented to secure the data over the cloud. Presenting How Does Cloud Security Work Governance Professional PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Access Management, Business Continuity Planning, Data Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security Automation Systems Guide Unified Platform Integration For Security Automation Background PDF
This slide highlights the unifies platform integration for security automation which includes firewalls, intrusion prevention system, security information and event management and privileged access management. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit IT Security Automation Systems Guide Unified Platform Integration For Security Automation Background PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.

Executing Devops Framework Global Devops Market Trends Themes PDF
Mentioned slide provides information about the trends of DevOps Market. Trends covered in the slide are Cloud-Native DevOps, Serverless Architecture, Security and DevSecOps. This is a Executing Devops Framework Global Devops Market Trends Themes PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Undeterred Growth, Cloud Native DevOps, Rise Serverless Architecture, Enhanced Security and DevSecOps. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Enhanced Protection Corporate Event Administration Role Of Security Operations Centre In Security Operations Brochure PDF
This slide portrays information regarding the role of security operations center in SecOps and how firm behave before, after and towards SecOps implementation. Presenting enhanced protection corporate event administration role of security operations centre in security operations brochure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like organizational, collaborate, security, analysts. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Elements Of Information Technology Security Application Security Ppt Portfolio Inspiration PDF
This slide defines application security and categories of application threats and tools to perform application security to prevent cyberattacks. Presenting elements of information technology security application security ppt portfolio inspiration pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like required, information, customers, interest, assets. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Authentication Process Flow Of Verification Factors For User Profile Authentication Icon Portrait PDF
Persuade your audience using this authentication process flow of verification factors for user profile authentication icon portrait pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including authentication process flow of verification factors for user profile authentication icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Company Vulnerability Administration Need For Vulnerability Management Introduction PDF
Presenting company vulnerability administration need for vulnerability management introduction pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like detective controls, responsive controls, vulnerability management is a standard process, implementing a vulnerability management program. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
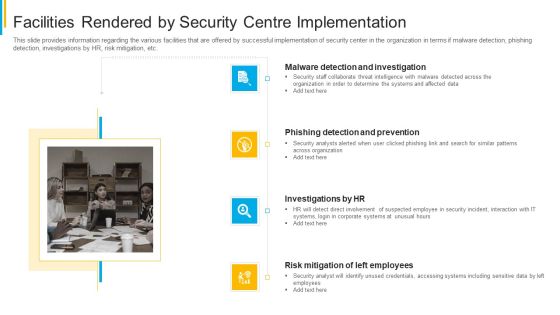
Project Security Administration IT Facilities Rendered By Security Centre Implementation Clipart PDF
This slide provides information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. Presenting project security administration it facilities rendered by security centre implementation clipart pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like malware detection and investigation, phishing detection and prevention, investigations by hr, risk mitigation of left employees. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Table Of Contents For Workplace Security Management Program Graphics PDF
If you are looking for a format to display your unique thoughts, then the professionally designed Table Of Contents For Workplace Security Management Program Graphics PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Table Of Contents For Workplace Security Management Program Graphics PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Agenda For Cyber Security Breache Response Strategy Slides PDF
Find a pre designed and impeccable Agenda For Cyber Security Breache Response Strategy Slides PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Table Of Contents For Web App Firewall Services IT Guidelines PDF
Presenting table of contents for web app firewall services it guidelines pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like services, application, security, deployment, implementation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Icon Showcasing Effective Online Security Policy Topics PDF
Persuade your audience using this Icon Showcasing Effective Online Security Policy Topics PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Icon Showcasing Effective, Online Security Policy. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cloud Intelligence Framework For Application Consumption Case Study 2 Banks Cyber Security Infrastructure Microsoft PDF
The slide provides the case study of a banking company that covered the details related to cybersecurity challenge faced by the bank, and major approach suggested by the technology company to resolve the challenges. This is a cloud intelligence framework for application consumption case study 2 banks cyber security infrastructure microsoft pdf template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like process workflows, industry standard security metrics, implemented. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Standards And Control Frameworks Ppt PowerPoint Presentation File Icon PDF
This slide provides an overview of the cloud security protocols and control frameworks. The purpose of this slide is to showcase the various information security standards and control frameworks, including ISO-27001, ISO-27017, ISO-27018, GDPR, SOC reporting, PCI DSS, and HIPAA. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Cloud Security Standards And Control Frameworks Ppt PowerPoint Presentation File Icon PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.
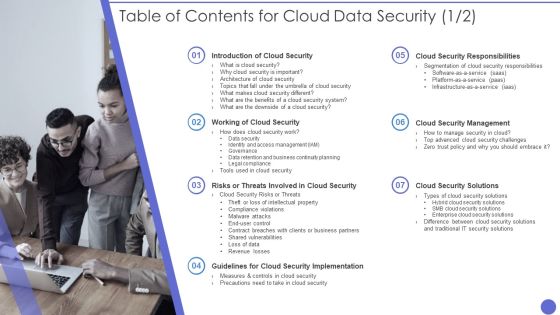
Table Of Contents For Cloud Data Security Formats PDF
Presenting Table Of Contents For Cloud Data Security Formats PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Cloud Security, Security System, Benefits. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Architecture At Scale How To Execute A Cloud Infrastructure Evaluation Determining Ideal Future State Background PDF
This slide emphasize on reviewing current status if company found any gaps in the internal cloud infrastructure and prioritizing approaches to those gaps based on security issues. Presenting cloud architecture at scale how to execute a cloud infrastructure evaluation determining ideal future state background pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like cloud infrastructure, security issues, operational risk. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
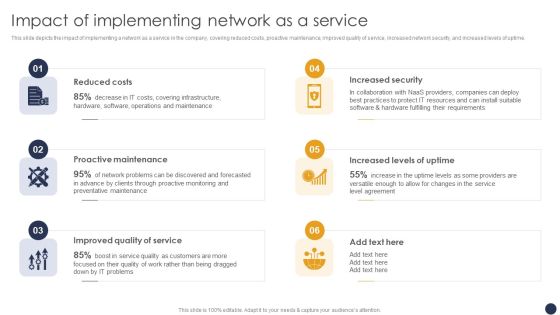
Integrating Naas Service Model Impact Of Implementing Network As A Service Ppt Slides Ideas PDF
This slide depicts the impact of implementing a network as a service in the company, covering reduced costs, proactive maintenance, improved quality of service, increased network security, and increased levels of uptime. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Integrating Naas Service Model Impact Of Implementing Network As A Service Ppt Slides Ideas PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Conventional Source Of Real Estate Finance Commercial Banks Ppt Gallery Elements PDF
This slide describes Commercial Banks as a Conventional Source of Real Estate Finance along with interest rate and general description. Presenting conventional source of real estate finance commercial banks ppt gallery elements pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like financing source, information security, business management and handling, benefits of commercial banks. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Sources Of Real Estate Financing Available With ADC Investment Company Ppt Infographic Template Slide Download PDF
This slide shows the sources of real estate finance that are available with the company such as Conventional and Unconventional Sources. Presenting sources of real estate financing available with adc investment company ppt infographic template slide download pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like investment, commercial, insurance, security, equity finance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Risk Recognition Automation Siem Architecture Flowchart Ppt Summary Example File PDF
This slide covers the security incident and event management flowchart which shows the flow of the SIEM system components wherein data, collector, and central engine are focused. Presenting risk recognition automation siem architecture flowchart ppt summary example file pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like reporting, dashboard, data mining, algorithm. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
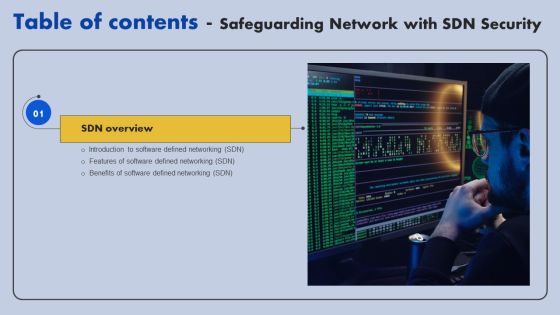
Safeguarding Network With SDN Security Table Of Contents Ppt Visual Aids Files PDF
This slide represents the schematic elements of software-defined networking, such as the northbound interface, SDN controller, and southbound interface. These components transmit the information throughout the SDN architecture. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Safeguarding Network With SDN Security Table Of Contents Ppt Visual Aids Files PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Implementing Cyber Security Incident Management Table Of Contents Clipart PDF
Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Implementing Cyber Security Incident Management Table Of Contents Clipart PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Implementing Cyber Security Incident Management Table Of Contents Clipart PDF today and make your presentation stand out from the rest.
Information Technology Security Key Strategies Icon Slides PDF
Persuade your audience using this Information Technology Security Key Strategies Icon Slides PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Information Technology Security, Key Strategies Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Hard And Soft Facility Management Services Microsoft PDF
This slide highlights hard and soft facility management services which are offered by the company which includes cleaning services, support services, security services, catering services and technical services. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Hard And Soft Facility Management Services Microsoft PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Hard And Soft Facility Management Services Microsoft PDF.

Investment Service Provider Capital Raising Elevator Impressive Value Proposition Portrait PDF
This slide caters details about value proposition by FinTech platform by focusing on rendering rapid and effective solutions to customers. Presenting investment service provider capital raising elevator impressive value proposition portrait pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like requirements, security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Security Operations Training Department Program Icon Introduction PDF
Persuade your audience using this Information Security Operations Training Department Program Icon Introduction PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Information Security, Operations Training, Department Program, Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Checklist To Implement Cloud Security In Business Microsoft PDF
This slide shows the checklist to implement cloud security in business, including policies and procedures, access control, networking, backup data, security patches, etc. Presenting Checklist To Implement Cloud Security In Business Microsoft PDF to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like Access Control, Networking, Security Patches And Updates. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Agenda Of Food Security Excellence Ppt Model Visuals PDF
Presenting agenda of food security excellence ppt model visuals pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like maintaining, process, management, raising quality. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Agenda IT Security Automation Systems Guide Sample PDF
Find a pre designed and impeccable Agenda IT Security Automation Systems Guide Sample PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Agenda Organizations Risk Management And IT Security Portrait PDF
Find a pre designed and impeccable Agenda Organizations Risk Management And IT Security Portrait PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Agenda For Deploying Cyber Security Incident Response Administration Guidelines PDF
Find a pre designed and impeccable Agenda For Deploying Cyber Security Incident Response Administration Guidelines PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Agenda For Information Security Ppt PowerPoint Presentation File Styles PDF
Find a pre designed and impeccable Agenda For Information Security Ppt PowerPoint Presentation File Styles PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Agenda Securing Market Leadership Through Competitive Excellence Pictures PDF
Find a pre designed and impeccable Agenda Securing Market Leadership Through Competitive Excellence Pictures PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Agenda Implementing Cyber Security Incident Management Template PDF
Find a pre designed and impeccable Agenda Implementing Cyber Security Incident Management Template PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
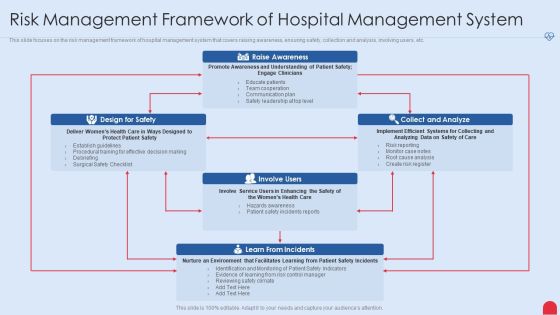
Enhancing Hospital Software System Risk Management Framework Of Hospital Management System Rules PDF
This slide focuses on the risk management framework of hospital management system that covers raising awareness, ensuring safety, collection and analysis, involving users, etc. Deliver an awe inspiring pitch with this creative enhancing hospital software system risk management framework of hospital management system rules pdf bundle. Topics like design for safety, collect and analyze, learn from incidents can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
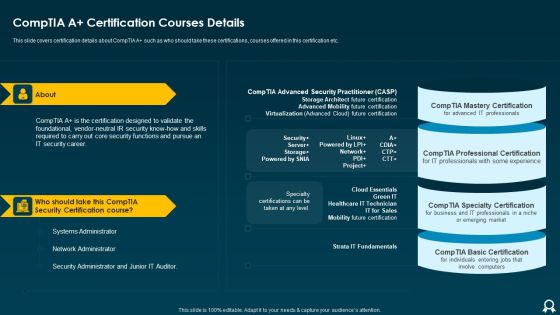
IT Data Services Certification Programs Comptia A Certification Courses Details Formats PDF
Presenting IT Data Services Certification Programs Comptia A Certification Courses Details Formats PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Security Certification Course, Network Administrator, Systems Administrator. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Loss Prevention Icon With Security System Guidelines PDF
Persuade your audience using this Loss Prevention Icon With Security System Guidelines PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Security System, Loss Prevention Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Information Security Program Values To Business Ppt File Smartart PDF
Following slide displays the major program values to companys business. Values here are divided in two areas namely detection and response and attack surface management. Presenting information security program values to business ppt file smartart pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like reduce, security, network, environment, management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Current Security Management Challenges The Company Is Facing Download PDF
Presenting current security management challenges the company is facing download pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like potential insider threats, external security breaches, rise of caas. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Deployment Of Omnichannel Banking Solutions Introduction To Secure Self Service Bill Payment Kiosks Portrait PDF
This slide covers brief introduction about kiosks technology launched by banking sector as an initiative towards omnichannel strategy. The purpose of this template is to provide information to users about the features and benefits of using self service kiosk for their banking needs. It includes benefits such as accepting all payment options, providing real-time data transmission, transaction reporting, bilingual interface, etc. Slidegeeks has constructed Deployment Of Omnichannel Banking Solutions Introduction To Secure Self Service Bill Payment Kiosks Portrait PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

Security Techniques For Digital Terrorism Icon Elements PDF
Persuade your audience using this Security Techniques For Digital Terrorism Icon Elements PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Digital Terrorism Icon, Security Techniques. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Exploitation IT Use Of Security Programs Mockup PDF
This slide represents the usage of security programs such as secure socket layer, web application firewall, website, and software scanners that will secure and help detect malicious attacks. Presenting cyber exploitation it use of security programs mockup pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like secure sockets layer, web application firewall, website and software scanners. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Effective IT Risk Management Process Information Security Decision Template PDF
Presenting effective it risk management process information security decision template pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like implement, resource allocation, risk factors, standardize. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Case Study 2 Banks Cyber Security Infrastructure Mockup PDF
Presenting case study 2 banks cyber security infrastructure mockup pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like case study 2 banks cyber security infrastructure. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber IT Security Vulnerability Analysis Checklist Microsoft PDF
This slide contains the checklist of multiple human threats human error, dishonesty, social engineering attacks and general threats with their impact and probability to occur in the business. Persuade your audience using this Cyber IT Security Vulnerability Analysis Checklist Microsoft PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Security, Awareness, Systems. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

3 Key Areas For Document Management Security Controls Ideas PDF
This slide presents the key areas of security control that enable companies to manage information access and permissions. It includes cryptography, best practice guidelines, compliance certifications and attestations. Persuade your audience using this 3 Key Areas For Document Management Security Controls Ideas PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Cryptography, Practice Guidelines, Attestations. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
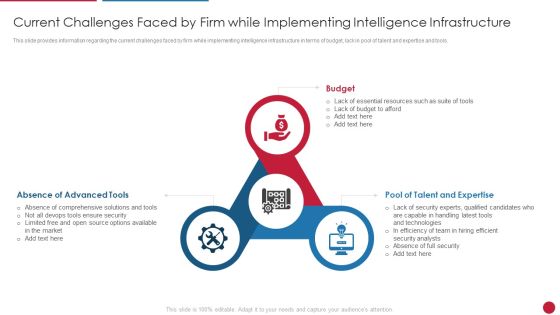
Facilitating IT Intelligence Architecture Current Challenges Faced By Firm While Implementing Graphics PDF
This slide provides information regarding the current challenges faced by firm while implementing intelligence infrastructure in terms of budget, lack in pool of talent and expertise and tools. This is a Facilitating IT Intelligence Architecture Current Challenges Faced By Firm While Implementing Graphics PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Absence Of Advanced Tools, Pool Of Talent And Expertise, Efficient Security Analysts You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
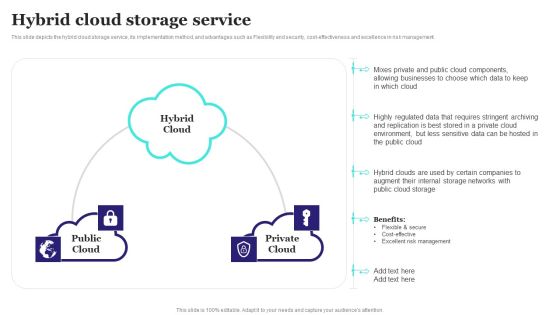
Hybrid Cloud Storage Service Ppt PowerPoint Presentation File Pictures PDF
This slide depicts the hybrid cloud storage service, its implementation method, and advantages such as Flexibility and security, cost-effectiveness and excellence in risk management. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Hybrid Cloud Storage Service Ppt PowerPoint Presentation File Pictures PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Hybrid Cloud Storage Service Ppt PowerPoint Presentation File Pictures PDF.S
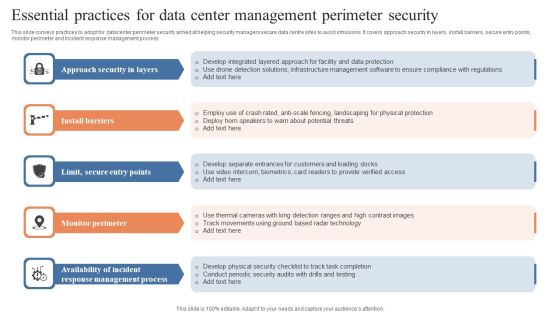
Essential Practices For Data Center Management Perimeter Security Guidelines PDF
This slide conveys practices to adopt for datacenter perimeter security aimed at helping security managers secure data centre sites to avoid intrusions. It covers approach security in layers, install barriers, secure entry points, monitor perimeter and incident response management process. Persuade your audience using this Essential Practices For Data Center Management Perimeter Security Guidelines PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Approach Security Layers, Install Barriers, Monitor Perimeter. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Information Security Data Privacy In Financial Institutions Mockup PDF
This slide represents the data privacy in financial institutions which decreases the possibility of fines and reputational damage as a result of unlawful disclosure. This Information Security Data Privacy In Financial Institutions Mockup PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Information Security Data Privacy In Financial Institutions Mockup PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today.

Cyber Security Incident Management Checklist During An Incident Inspiration PDF
This slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident management during the occurrence of the incident. The Cyber Security Incident Management Checklist During An Incident Inspiration PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Cloud Computing Security Ppt Portfolio Background Images PDF
Presenting cloud computing security ppt portfolio background images pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like security dimensions, customers, security categories. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Computing Testing Framework With Database Icons PDF
This template covers about framework of cloud testing with data base and service level agreement. Further, it cover about testing repository with security. Persuade your audience using this cloud computing testing framework with database icons pdf. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including service, application, system. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

KPI Metrics Security Icon With Dashboard Template PDF
Persuade your audience using this KPI Metrics Security Icon With Dashboard Template PDF. This PPT design covers two stages, thus making it a great tool to use. It also caters to a variety of topics including Kpi Metrics, Security Icon, Dashboard. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

IT Security Management And Management Icon Introduction PDF
Persuade your audience using this IT Security Management And Management Icon Introduction PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including IT, Security, Management. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Security Governance And Management Process Icon Introduction PDF
Persuade your audience using this Security Governance And Management Process Icon Introduction PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Security, Governance, Management Process. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Electronic Voting System Voting System Standards Security Template PDF
This slide represents the security standard of the voting system that ensures the security of voting machines to prevent them from being tempered or manipulated through physical security, auditability, and internet connection.Presenting Electronic Voting System Voting System Standards Security Template PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Manipulated Tampered, Ensuring Security, Security Include. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Solutions To Overcome Security Operations Challenges Template PDF
This slide outlines solutions to overcome challenges faced by security operations teams in order to deal with an increasing number of cyber attacks. It includes challenges such as skill shortage, lack of automation, large volume of data, and work processes integration. Persuade your audience using this Solutions To Overcome Security Operations Challenges Template PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Lack Of Automation, Work Processes Integration, Data Security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
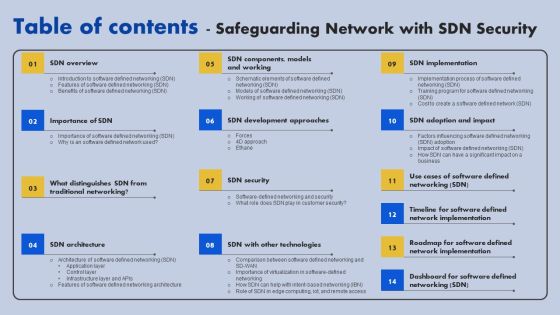
Table Of Contents Safeguarding Network With SDN Security Ppt Ideas Design Ideas PDF
If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Table Of Contents Safeguarding Network With SDN Security Ppt Ideas Design Ideas PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.

Agenda IT Security Automation Tools Integration Ppt Summary Design Templates PDF
This is a Agenda IT Security Automation Tools Integration Ppt Summary Design Templates PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like IT Environment, Security Processes, Security Automation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Query Slide Diagram For Secure Cash Endowment Rules PDF
Persuade your audience using this query slide diagram for secure cash endowment rules pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including query slide diagram for secure cash endowment. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Standard Computing Vs Modern Information Security Icon Microsoft PDF
Persuade your audience using this Standard Computing Vs Modern Information Security Icon Microsoft PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Standard Computing, Modern Information Security Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Security Risk Analysis Shield Software Icon Themes PDF
Persuade your audience using this Cyber Security Risk Analysis Shield Software Icon Themes PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Security Risk Analysis, Shield Software Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Information Security Adhere To Strict Compliance Requirements Diagrams PDF
This slide shows that you can use a data classification engine to locate and categorize regulated and sensitive material also, compliance standards serve as a foundation. If you are looking for a format to display your unique thoughts, then the professionally designed Information Security Adhere To Strict Compliance Requirements Diagrams PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Information Security Adhere To Strict Compliance Requirements Diagrams PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Evaluating IT System Security Using SWOT Analysis Portrait PDF
The purpose of this slide is to outline the strength, weakness, opportunities and threat SWOT evaluation of organization cyber security. Organization can detect the potential risks and opportunities in the cyber security using SWOT model. Presenting Evaluating IT System Security Using SWOT Analysis Portrait PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Strengths, Weakness, Opportunities. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Role Based Access Control RBAC Securities Icon Demonstration PDF
Persuade your audience using this Role Based Access Control RBAC Securities Icon Demonstration PDF. This PPT design covers Three stages, thus making it a great tool to use. It also caters to a variety of topics including Role Based, Access Control. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Information Security Challenges Users Face In Data Privacy Sample PDF
This slide outlines the challenges users face in data privacy, including online tracking, losing control of data, lack of transparency, social media, and cybercrime. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Information Security Challenges Users Face In Data Privacy Sample PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Information Security Challenges Users Face In Data Privacy Sample PDF.

Blockchain Security Solutions Deployment Advantages Of Blockchain Technology Brochure PDF
This slide represents the various advantages of blockchain technology based on information security, digital freedom, privacy, and lower transaction fees. Find a pre-designed and impeccable Blockchain Security Solutions Deployment Advantages Of Blockchain Technology Brochure PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Manpower Corporate Security Business Profile Swot Analysis Introduction PDF
This slide highlights the security guard company management team which includes companys chairman and MD, head of security operations, training, strategic growth and site. Presenting Manpower Corporate Security Business Profile Swot Analysis Introduction PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Strengths, Weaknesses, Opportunities, Threats. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Various Kpis To Measure Computer Security System Portrait PDF
This slide shows the different KPIs used to measure IT security system. These are level of preparedness, intrusion attempts, days to patch, incidents reported etc. Persuade your audience using this Various Kpis To Measure Computer Security System Portrait PDF This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Performance Indicators, Excepted Results, Actual Results Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Information Technology Security Risk Assessment Grid Information PDF
The following slide depicts the analysis of IT security to prevent loss of confidentiality and integrity. The matrix constitutes of elements such as risk, likelihood, its impact and overall threat level. Persuade your audience using this Information Technology Security Risk Assessment Grid Information PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Loss Of Privacy, System Integrity, Loss Of Data. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Handling Cyber Threats Digital Era Information Security Program Values To Business Ppt Slides Background Designs PDF
Following slide displays the major program values to companys business. Values here are divided in two areas namely detection and response and attack surface management. This is a handling cyber threats digital era information security program values to business ppt slides background designs pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information security program values to business. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Key Stakeholders Of Cyber Security Awareness Training Mockup PDF
Presenting Key Stakeholders Of Cyber Security Awareness Training Mockup PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Senior Mangers, Line Managers, Employees. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
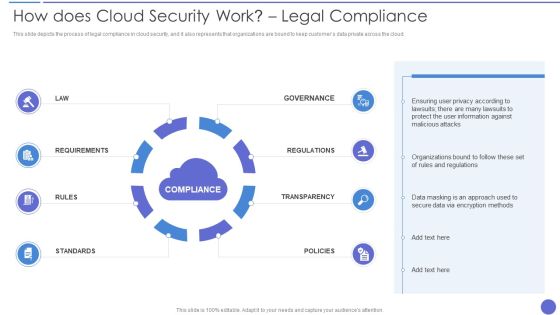
How Does Cloud Security Work Legal Compliance Background PDF
This slide represents the identity and access management in a cloud security system that is based on authentication, authorization, access control, and central user repository. Presenting How Does Cloud Security Work Legal Compliance Background PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Authorization, Authentication, Access Management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
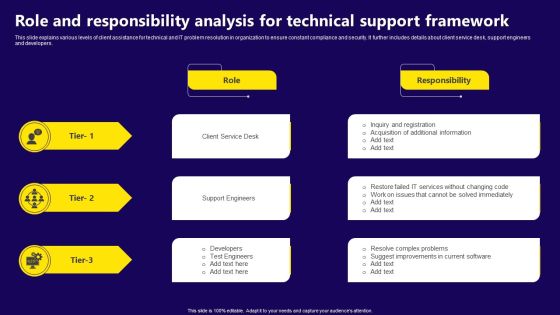
Role And Responsibility Analysis For Technical Support Framework Download PDF
This slide explains various levels of client assistance for technical and IT problem resolution in organization to ensure constant compliance and security. It further includes details about client service desk, support engineers and developers. Presenting Role And Responsibility Analysis For Technical Support Framework Download PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Client Service Desk, Support Engineers, Developers, Test Engineers. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
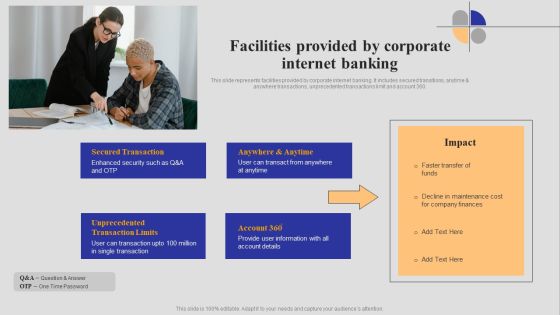
Introduction To Digital Banking Services Facilities Provided By Corporate Internet Banking Themes PDF
This slide represents facilities provided by corporate internet banking. It includes secured transitions, anytime and anywhere transactions, unprecedented transactions limit and account 360. Create an editable Introduction To Digital Banking Services Facilities Provided By Corporate Internet Banking Themes PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Introduction To Digital Banking Services Facilities Provided By Corporate Internet Banking Themes PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

How Does Cloud Security Work Identity And Access Management Iam Cloud Computing Security IT Ppt Infographics Picture PDF
This slide represents the identity and access management in a cloud security system that is based on authentication, authorization, access control, and central user repository. Presenting how does cloud security work identity and access management iam cloud computing security it ppt infographics picture pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like authentication, authorization, access management, central user repository. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Business Cyber Security Risk Assessment Process Inspiration PDF
The slide shows cyber threat detection and protection measures in order to eliminate the potential risks to the business. The steps include identifying, detecting, responding, protecting, and recovering. Persuade your audience using this Business Cyber Security Risk Assessment Process Inspiration PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Identify, Detect, Respond, Protect, Recover. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
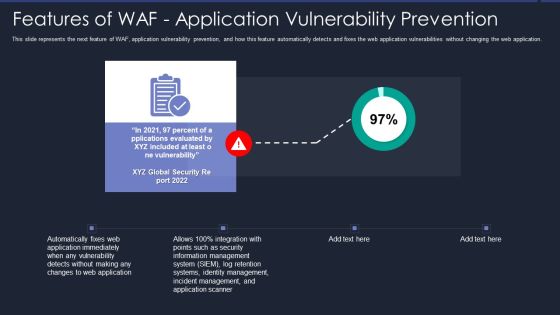
Web App Firewall Services IT Features Of WAF Application Vulnerability Prevention Information PDF
This slide represents the next feature of WAF, application vulnerability prevention, and how this feature automatically detects and fixes the web application vulnerabilities without changing the web application. Presenting web app firewall services it features of waf application vulnerability prevention information pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like management, security, application, information. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Major Roles And Responsibilities Of Financial Security Team Sample PDF
The following slide Major roles and responsibilities of financial security department . It includes information about risk level determination, laws and regulations, team training, operational compliance, automatic workflows, red flags, etc. Slidegeeks is here to make your presentations a breeze with Major Roles And Responsibilities Of Financial Security Team Sample PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Security Functioning Centre Facilities Offered By Successful Implementation Infographics PDF
This slide portrays information regarding the various facilities that are offered by successful implementation of SecOps in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. Presenting security functioning centre facilities offered by successful implementation infographics pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like risk mitigation, investigations, employees. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security Hacker Is Ethical Hacking Legal Rules PDF
This slide shows the legality of ethical hacking, how ethical hackers work official permission, and companies hire them to protect their networks and computer systems from malicious attacks.Presenting IT Security Hacker Is Ethical Hacking Legal Rules PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Improve Defense, Anonymous Thieves, Qualified Cybersecurity. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Implementing Cybersecurity Awareness Program To Prevent Attacks Strategies We Will Implement To Make Security Icons PDF
The purpose of this slide is to exhibit variety of strategies which can be used to engage employees in the security awareness training plan. The strategies highlighted in the slide are gamification, personalization, high-quality content and variety. Get a simple yet stunning designed Implementing Cybersecurity Awareness Program To Prevent Attacks Strategies We Will Implement To Make Security Icons PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Implementing Cybersecurity Awareness Program To Prevent Attacks Strategies We Will Implement To Make Security Icons PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
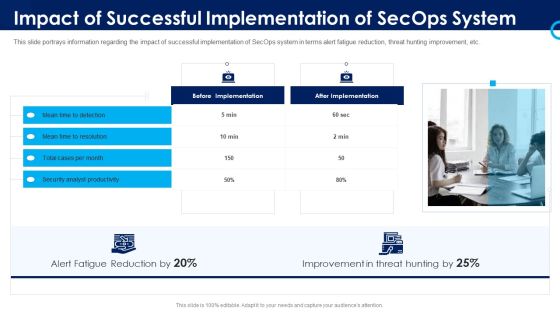
Organizational Security Solutions Impact Of Successful Implementation Of Secops System Designs PDF
This slide portrays information regarding the impact of successful implementation of SecOps system in terms alert fatigue reduction, threat hunting improvement, etc. Presenting organizational security solutions impact of successful implementation of secops system designs pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like security, analyst, improvement, reduction. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information And Technology Security Operations Prerequisites For Effective Secops Implementation Designs PDF
This slide portrays information regarding the prerequisites that essential for effective implementation of SecOps in terms of development and operations team, etc. This is a information and technology security operations prerequisites for effective secops implementation designs pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like development, data available, security with compliance, operations team. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Roles And Responsibilities Assigned In Quality Management Process Food Security Excellence Ppt Outline Design Templates PDF
This slide outlines roles and responsibilities such as project manager, quality manager, system integrator, etc. that are assigned to people who are involved in quality management process. Presenting roles and responsibilities assigned in quality management process food security excellence ppt outline design templates pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like project manager, technical manager, quality manager, system integrator, test team. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Policies And Procedures Information Security Policy For Employees Download PDF
Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our IT Policies And Procedures Information Security Policy For Employees Download PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into IT Policies And Procedures Information Security Policy For Employees Download PDF.

Security Automation To Analyze And Mitigate Cyberthreats Impacts Of Ineffective Information Designs PDF
This slide highlights the impacts of ineffective information technology security at organization level which includes average cost of security, average time to identify data breach and total legitimate risks.If you are looking for a format to display your unique thoughts, then the professionally designed Security Automation To Analyze And Mitigate Cyberthreats Impacts Of Ineffective Information Designs PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Security Automation To Analyze And Mitigate Cyberthreats Impacts Of Ineffective Information Designs PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
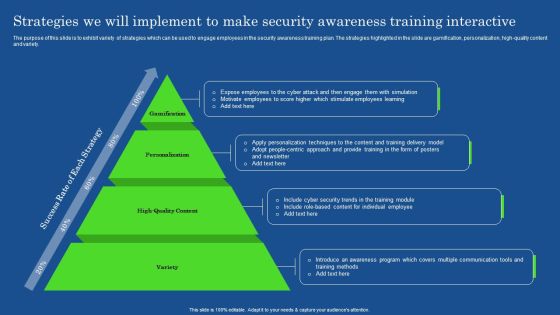
Strategies We Will Implement To Make Security Awareness Training Interactive Structure PDF
The purpose of this slide is to exhibit variety of strategies which can be used to engage employees in the security awareness training plan. The strategies highlighted in the slide are gamification, personalization, high-quality content and variety. Explore a selection of the finest Strategies We Will Implement To Make Security Awareness Training Interactive Structure PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Strategies We Will Implement To Make Security Awareness Training Interactive Structure PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

SIEM Services Companys Enhanced Features And Capabilities Ppt Styles Summary PDF
This slide provides the details about the companys main features and additional features such as threat detection, investigation, security monitoring, normalization, etc. Presenting siem services companys enhanced features and capabilities ppt styles summary pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like threat detection, investigation, normalization. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

SIEM Services What Sets Us Apart Ppt Infographic Template Backgrounds PDF
This slide covers the reasons why our company is different from other SIEM companies since they have qualities such as attractive TCO and ROI, improved IT productivity, etc. Presenting siem services what sets us apart ppt infographic template backgrounds pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security devices, ownership, dynamic business, improvement it. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

SIEM Software Challenges With Solutions SIEM Services Ppt Inspiration Ideas PDF
This slide covers the challenges and solutions of security information and event management software such as workforce limitations, weak responsiveness, dynamic data limitations, etc. Presenting siem software challenges with solutions siem services ppt inspiration ideas pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like workforce limitations, dynamic data limitations, responsiveness. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Developing Business Analytics Framework Determine Capabilities Infrastructure Contd Portrait PDF
This slide covers information regarding capabilities that are required in order to enable intelligent infrastructure in terms of configuration automation, proactive analysis of security threats, etc. Presenting Developing Business Analytics Framework Determine Capabilities Infrastructure Contd Portrait PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Configuration Automation, Connection Devices, Infrastructure Services In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Risk Management Model For Data Security Roles And Responsibilities For Managing Information Professional PDF
Following slide demonstrates various roles and responsibilities for information security management. Responsibilities covered are security policy development, asset classification and security framework development. This is a Risk Management Model For Data Security Roles And Responsibilities For Managing Information Professional PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Role, Position, Responsibility, Chief Information Officer, Information Management Manager. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Technology Threat Mitigation Methods Security Criteria And Control Measures For IT System Vulnerabilities Themes PDF
This slide highlights the security criteria for information technology system vulnerabilities with security area which includes management security, operational security and technical security. Presenting Information Technology Threat Mitigation Methods Security Criteria And Control Measures For IT System Vulnerabilities Themes PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Management Security, Operational Security, Technical Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

KYC Transaction Monitoring System Business Security Risks Identified During Transaction Monitoring Designs PDF
This slide showcases risks identified during transaction monitoring. It provides information about anti money laundering fines, staff productivity, motivation, organizational profitability, compliance, fees, false positive, workload, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give KYC Transaction Monitoring System Business Security Risks Identified During Transaction Monitoring Designs PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable KYC Transaction Monitoring System Business Security Risks Identified During Transaction Monitoring Designs PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Securing Market Leadership Through Competitive Excellence Company Overview Five Guys Designs PDF
The following slide exhibits complete overview of Five Guys company related to food industry. Information covered in this slide is related to companys mission statement, major stakeholders, products offered, key details and facts and figures. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Securing Market Leadership Through Competitive Excellence Company Overview Five Guys Designs PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Securing Market Leadership Through Competitive Excellence Company Overview Five Guys Designs PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Infrastructure Designing And Administration 4 Dimensions Of Infrastructure Security Pictures PDF
This is a infrastructure designing and administration 4 dimensions of infrastructure security pictures pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like people, data, applications, infrastructure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Client Account Management Business Requirement Status Template PDF
This slide shows account management requirement process with action status. It includes steps such as add clients, remove users, secure access etc. with requirement id and color legend indicating actions. Persuade your audience using this Client Account Management Business Requirement Status Template PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Account Management, Implemented, Proposed. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Security Administration In Organization Addressing Various Ways To Handle Insider Cyber Threats Designs PDF
This slide provides details regarding various ways to handle insider cyber threats in terms of periodic risk assessment, end user informing, etc. This is a cyber security administration in organization addressing various ways to handle insider cyber threats designs pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like assessment, networks, individuals, determine. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
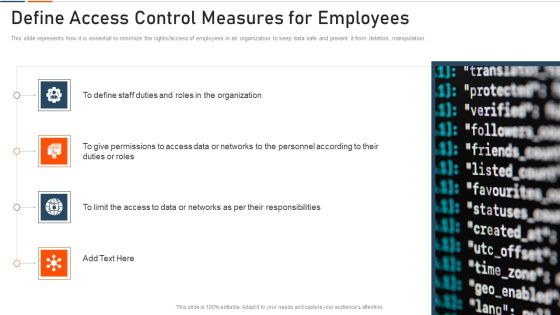
Information Technology Security Define Access Control Measures For Employees Ppt Professional Design Templates PDF
This slide represents how it is essential to minimize the rights access of employees in an organization to keep data safe and prevent it from deletion, manipulation. This is a information technology security define access control measures for employees ppt professional design templates pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like staff duties, organization, roles, access, permissions. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Techniques And Strategies To Reduce Security Management Risks Table Of Contents Structure PDF
Presenting techniques and strategies to reduce security management risks table of contents structure pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like identifying goals and objectives, risk assessment and analysis, adopting access controls. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
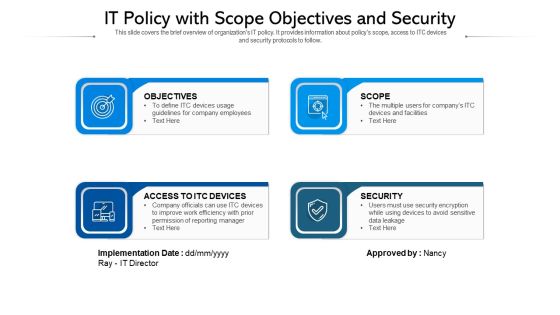
IT Policy With Scope Objectives And Security Ppt PowerPoint Presentation Infographics Show PDF
This slide covers the brief overview of organizations IT policy. It provides information about policys scope, access to ITC devices and security protocols to follow. Persuade your audience using this IT policy with scope objectives and security ppt powerpoint presentation infographics show pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including objectives, access to itc devices, security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
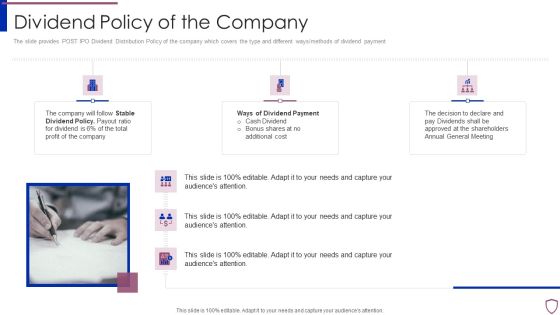
Financing Catalogue For Security Underwriting Agreement Dividend Policy Of The Company Elements PDF
The slide provides POST IPO Dividend Distribution Policy of the company which covers the type and different ways or methods of dividend payment. Presenting financing catalogue for security underwriting agreement dividend policy of the company elements pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like stable dividend policy, ways of dividend payment. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Table Of Contents For Developing IT Security Strategy To Prevent Data Assets Guidelines PDF
Do you know about Slidesgeeks Table Of Contents For Developing IT Security Strategy To Prevent Data Assets Guidelines PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

Information Technology Policy And Processes Security Awareness And Training Policy Overview Mockup PDF
This slide represents the security awareness and training policy. It covers that the training program should be designed by management, and employees will sign a confidentiality agreement after getting the training. Presenting this PowerPoint presentation, titled Information Technology Policy And Processes Security Awareness And Training Policy Overview Mockup PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Information Technology Policy And Processes Security Awareness And Training Policy Overview Mockup PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Information Technology Policy And Processes Security Awareness And Training Policy Overview Mockup PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Table Of Contents For Info Security Ppt PowerPoint Presentation File Sample PDF
Presenting table of contents for info security ppt powerpoint presentation file sample pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like managing information security, information security budget, information security roadmap timeline, information security implementation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Agenda For Executing Security Management Program To Mitigate Threats And Safeguard Confidential Organizational Data Clipart PDF
Presenting Agenda for executing security management program to mitigate threats and safeguard confidential organizational data clipart pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like effective response procedures, intentional or otherwise, enable organizational. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Table Of Contents KYC Transaction Monitoring System For Business Security Global Brochure PDF
Slidegeeks is here to make your presentations a breeze with Table Of Contents KYC Transaction Monitoring System For Business Security Global Brochure PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Cloud Intelligence Framework For Application Consumption Intelligent Infrastructure Lays The Foundation For The Digital Business Summary PDF
The slide provides the key details of the process that how intelligent infrastructure can digitalize the operations process in any organization. To explain this, slide provides details about monitoring, prediction, optimizing, learning, and analyzing. Presenting cloud intelligence framework for application consumption intelligent infrastructure lays the foundation for the digital business summary pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security, operations, proactively analyzes, optimize cost and performance, analyzes infrastructure services. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download

Table Of Contents Developing Information Technology Security Awareness Training Program For Employees Graphics PDF
If you are looking for a format to display your unique thoughts, then the professionally designed Table Of Contents Developing Information Technology Security Awareness Training Program For Employees Graphics PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Table Of Contents Developing Information Technology Security Awareness Training Program For Employees Graphics PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Table Of Contents Increasing Information Security Awareness In Company Using Various Techniques Clipart PDF
If you are looking for a format to display your unique thoughts, then the professionally designed Table Of Contents Increasing Information Security Awareness In Company Using Various Techniques Clipart PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Table Of Contents Increasing Information Security Awareness In Company Using Various Techniques Clipart PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Incorporating HIS To Enhance Healthcare Services Healthcare Information Technology Trends To Transform Processes Professional PDF
This slide covers healthcare information technology trends to ensure effective transformation of health services. It involves key trends such as internet of medical things, cognitive automation and cyber security and data privacy. If you are looking for a format to display your unique thoughts, then the professionally designed Incorporating HIS To Enhance Healthcare Services Healthcare Information Technology Trends To Transform Processes Professional PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Incorporating HIS To Enhance Healthcare Services Healthcare Information Technology Trends To Transform Processes Professional PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Smart Home Security Solutions Company Profile Existing Channel Development Strategy Infographics PDF
This slide highlights the security company channel development strategy which covers direct to home strategy including new incentive scheme and extra margin to channel hubs. It also includes inside sales strategy which focus on lead referral partners. Presenting Smart Home Security Solutions Company Profile Existing Channel Development Strategy Infographics PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Direct To Home, Incentive Scheme Hubs. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Our Strategies To Secure Network Load Balancer Ppt Outline Topics PDF
This slide represents the strategies to secure the network load balancer by protecting servers at the physical level, controlling network traffic, security app features, and more. Presenting our strategies to secure network load balancer ppt outline topics pdf to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like our strategies to secure network load balancer. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Table Of Contents IT Security Automation Tools Integration Ppt Gallery Aids PDF
Presenting Table Of Contents IT Security Automation Tools Integration Ppt Gallery Aids PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Security Automation Stages, Protection Platform, Security Orchestration. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Table Of Contents For Info Security Wd Ppt PowerPoint Presentation Gallery Maker PDF
Presenting table of contents for info security wd ppt powerpoint presentation gallery maker pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like cyber risk assessment, steps for mitigation, cyber risk identification, key elements of information security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Table Of Contents For Cloud Computing Security IT Monitoring Ppt Styles Introduction PDF
Presenting table of contents for cloud computing security it monitoring ppt styles introduction pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like cloud security, business, implement, roadmap, data encryption. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
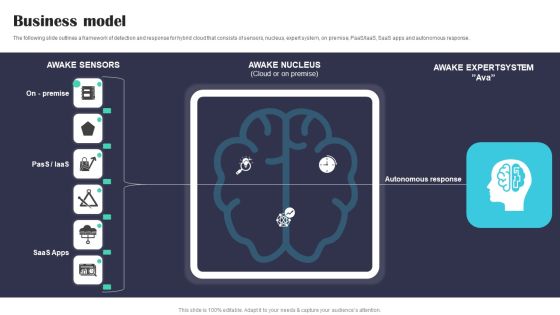
Security Software Company Investor Funding Pitch Deck Business Model Structure PDF
The following slide outlines a framework of detection and response for hybrid cloud that consists of sensors, nucleus, expert system, on premise, PaaS or IaaS, SaaS apps and autonomous response. Create an editable Security Software Company Investor Funding Pitch Deck Business Model Structure PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Security Software Company Investor Funding Pitch Deck Business Model Structure PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Table Of Contents For Comprehensive Guide For Ensuring IT Infrastructure Security Slides PDF
If you are looking for a format to display your unique thoughts, then the professionally designed Table Of Contents For Comprehensive Guide For Ensuring IT Infrastructure Security Slides PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Table Of Contents For Comprehensive Guide For Ensuring IT Infrastructure Security Slides PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Timeline Demonstration Of Years 2013 To 2019 PowerPoint Templates Ppt Slides Graphics
We present our TimeLine demonstration of years 2013 to 2019 PowerPoint Templates PPT Slides Graphics.Download and present our Marketing PowerPoint Templates because networking is an imperative in todays world. You need to access the views of others. Similarly you need to give access to them of your abilities. Use our Timelines PowerPoint Templates because this slide is Designed to help bullet-point your views and thoughts. Download and present our Business PowerPoint Templates because you have secured a name for yourself in the domestic market. Now the time is right to spread your reach to other countries. Download our Arrows PowerPoint Templates because you can Grab the attention of your team with this eye catching template signifying . Download and present our Time planning PowerPoint Templates because this Layout can explain the relevance of the different layers and stages in getting down to your core competence, ability and desired result.Use these PowerPoint slides for presentations relating to Art, Background, Button, Call, City, Colorful, Concept, Country, Destination, Editable, Flag, Fuel, Geography, Graphic, Home, Icon, Illustration, Journey, Land, Locate, Location, Macro, Map, Mapping, Mark, Navigate, Needle, Petrol, Pin, Pinpoint, Place, Pointing, Pump, Push, Pushpin, Restaurant, Road, Roadmap, Service, Set, Shiny, Space, Symbol, Town, Travel, Trip. The prominent colors used in the PowerPoint template are Green, Gray, Black. PowerPoint presentation experts tell us our TimeLine demonstration of years 2013 to 2019 PowerPoint Templates PPT Slides Graphics are Energetic. Customers tell us our City PowerPoint templates and PPT Slides are Vintage. Customers tell us our TimeLine demonstration of years 2013 to 2019 PowerPoint Templates PPT Slides Graphics are Magical. Customers tell us our Call PowerPoint templates and PPT Slides are Dazzling. PowerPoint presentation experts tell us our TimeLine demonstration of years 2013 to 2019 PowerPoint Templates PPT Slides Graphics are Energetic. People tell us our Destination PowerPoint templates and PPT Slides are Tranquil.

Table Of Contents For Cyber Physical System To Enhance Security Topics PDF
Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Table Of Contents For Cyber Physical System To Enhance Security Topics PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Table Of Contents For Cyber Physical System To Enhance Security Topics PDF today and make your presentation stand out from the rest.

Table Of Contents Development And Integration Of Cyber Security Incident Administration Portrait PDF
If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Table Of Contents Development And Integration Of Cyber Security Incident Administration Portrait PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Table Of Contents For Information Technology Security Ppt File Mockup PDF
Presenting table of contents for information technology security ppt file mockup pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like security implementation, managing it security, it security budget, it security roadmap timeline . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Financing Catalogue For Security Underwriting Agreement Table Of Contents Mockup PDF
Presenting financing catalogue for security underwriting agreement table of contents mockup pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like company overview, market overview, deal overview. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Table Of Contents Organizations Risk Management And IT Security Workplace Elements PDF
If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Table Of Contents Organizations Risk Management And IT Security Workplace Elements PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.

Table Of Contents Fordeploying Cyber Security Incident Response Administration Structure PDF
If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Table Of Contents Fordeploying Cyber Security Incident Response Administration Structure PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.

Table Of Contents For Securing Market Leadership Through Competitive Excellence Demonstration PDF
If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Table Of Contents For Securing Market Leadership Through Competitive Excellence Demonstration PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.

Table Of Contents For IT Professional Data Certification Program Security Icons PDF
Presenting Table Of Contents For IT Professional Data Certification Program Security Icons PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Certified Information Systems, Security Professional. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Agenda For Safeguarding Network With SDN Security Ppt Layouts Information PDF
If you are looking for a format to display your unique thoughts, then the professionally designed Agenda For Safeguarding Network With SDN Security Ppt Layouts Information PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Agenda For Safeguarding Network With SDN Security Ppt Layouts Information PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
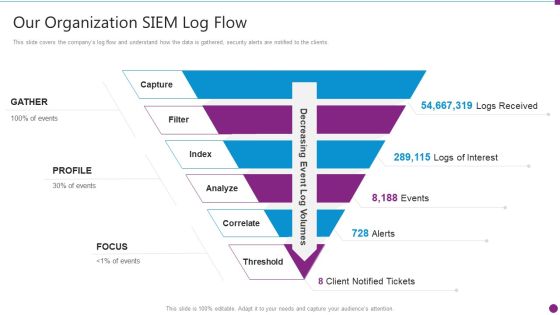
Security Information And Event Management Strategies For Financial Audit And Compliance Our Organization SIEM Log Flow Designs PDF
This slide covers the companys log flow and understand how the data is gathered, security alerts are notified to the clients. This is a security information and event management strategies for financial audit and compliance our organization siem log flow designs pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like our organization siem log flow. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
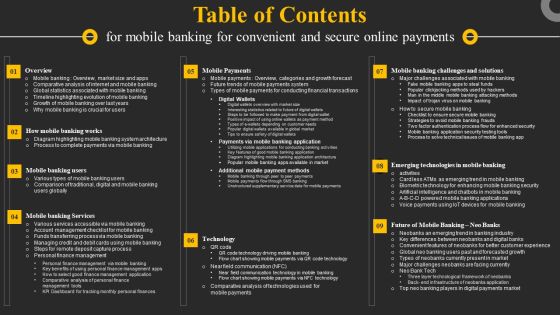
Table Of Contents For Mobile Banking For Convenient And Secure Online Payments Ppt Ideas Shapes PDF
Slidegeeks is here to make your presentations a breeze with Table Of Contents For Mobile Banking For Convenient And Secure Online Payments Ppt Ideas Shapes PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

P2P Ledger Pros And Cons Of Private Blockchain Diagrams PDF
This slide represents the Pros and cons of the private blockchain framework based on factors such as speed, flexibility, trust-building, and security.Find a pre-designed and impeccable P2P Ledger Pros And Cons Of Private Blockchain Diagrams PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Business Information And Security Risk Mitigation Strategy Ppt PowerPoint Presentation File Format PDF
Persuade your audience using this business information and security risk mitigation strategy ppt powerpoint presentation file format pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including business information and security risk mitigation strategy. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Ensuring Mobile Device Compliance And Policy Enforcement Mobile Device Security Management Slides PDF
This slide provides information regarding mobile device compliance and policy enforcement with automated device setup, dynamic workflows and policies, etc.Presenting Ensuring Mobile Device Compliance And Policy Enforcement Mobile Device Security Management Slides PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Automated Device, Enforcement Automation, Device Compliance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Technology Security Implementation Of Strong Password Policy Ppt File Infographic Template PDF
This slide depicts the importance of having strong passwords for different online accounts. It also shows the number of users who use the same password across other accounts. Presenting information technology security implementation of strong password policy ppt file infographic template pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like implementation of strong password policy. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Role IT Team Digital Transformation Role Of Chief Information Security Officer Summary PDF
This slide covers the role of chief information security officer which includes embed security information, stay informed, hire solid security staff, etc. Presenting role it team digital transformation role of chief information security officer summary pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like security information, security staff, monthly reports. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Agenda For Series Of Cyber Security Attacks Against Ukraine 2022 Sample PDF
Find a pre designed and impeccable Agenda For Series Of Cyber Security Attacks Against Ukraine 2022 Sample PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Agenda For Integrating Data Privacy System To Enhance Security Ppt Professional Layout PDF
Find a pre-designed and impeccable Agenda For Integrating Data Privacy System To Enhance Security Ppt Professional Layout PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Agenda For Organizing Security Awareness Training To Minimize Downtime Ideas PDF
Find a pre-designed and impeccable Agenda For Organizing Security Awareness Training To Minimize Downtime Ideas PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Agenda For KYC Transaction Monitoring System For Business Security Sample PDF
Find a pre designed and impeccable Agenda For KYC Transaction Monitoring System For Business Security Sample PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Agenda For Comprehensive Guide For Ensuring IT Infrastructure Security Graphics PDF
Find a pre-designed and impeccable Agenda For Comprehensive Guide For Ensuring IT Infrastructure Security Graphics PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Important Attributes Of Block Chain With Better Security Ppt PowerPoint Presentation Pictures Sample PDF
Persuade your audience using this important attributes of block chain with better security ppt powerpoint presentation pictures sample pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including decentralized system, authenticity, increased capacity. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Table Of Contents For Information Technology Security Requirement Ppt Styles Sample PDF
This slide depicts the categories of recent threats that table of contents for information technology security requirement ppt styles sample pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like latest threats in information technology security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cashless Payment Strategies To Enhance Business Performance Best Practices To Maintain Digital Wallet Security Brochure PDF
Mentioned slide exhibits various best practices which can be implemented by followed by businesses to secure e-wallets. It includes best practices such as enable passwords, secure network connections, install reliable applications, secure login credentials, and keep personal data private. Retrieve professionally designed Cashless Payment Strategies To Enhance Business Performance Best Practices To Maintain Digital Wallet Security Brochure PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Certified Information Systems Security Collection Of Information Technology Certifications Download PDF
This slide covers CISSP certification details such as what is the CISSP how to become certified, how to prepare for CISSP and why to get CISSP certifications. Presenting certified information systems security collection of information technology certifications download pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like information systems, network security, information network, organization, average. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Steps To Ensure Machine Driven Learning Security Ppt Inspiration Structure PDF
This slide defines steps to ensure the security of robotic process automation, and it covers guarantee accountability for bot activities, protection from abuse, frauds, logs and bot development. Presenting steps to ensure machine driven learning security ppt inspiration structure pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like system, management, development, accountability. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Agenda Development And Integration Of Cyber Security Incident Administration Information PDF
Slidegeeks is here to make your presentations a breeze with Agenda Development And Integration Of Cyber Security Incident Administration Information PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Prevention Of Information Key Benefits Of Cyber Security Awareness Training Inspiration PDF
The purpose of this slide is to delineate several advantages of security awareness training. Driving awareness, reducing data breach threat, prevention of downtime and improving the customer confidence are some of the key benefits which are highlighted in the slide. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Prevention Of Information Key Benefits Of Cyber Security Awareness Training Inspiration PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Prevention Of Information Key Benefits Of Cyber Security Awareness Training Inspiration PDF
