Construction Safety Plan
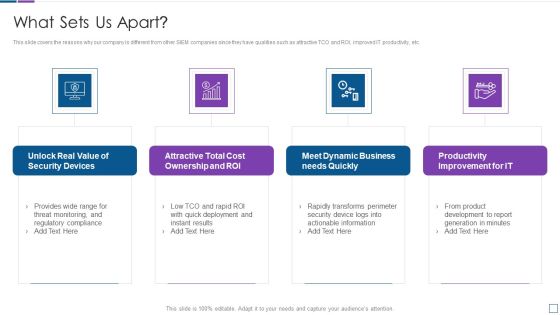
Real Time Assessment Of Security Threats What Sets Us Apart Microsoft PDF
This slide covers the reasons why our company is different from other SIEM companies since they have qualities such as attractive TCO and ROI, improved IT productivity, etc. Presenting real time assessment of security threats what sets us apart microsoft pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security devices, cost ownership and roi, dynamic business, productivity improvement. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information And Technology Security Operations Timeframe For Incident Management Graphics PDF
This slide provides information regarding entire duration of incident handling process which occur in various phases. Presenting information and technology security operations timeframe for incident management graphics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like activity phase, description, working hours. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Mobile Device Management For Ios Platform Business Mobile Device Security Management Themes PDF
This slide provides information regarding mobile device management for iOS platform with device enrollment program, anti theft protection, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Mobile Device Management For Ios Platform Business Mobile Device Security Management Themes PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Mobile Device Management For Ios Platform Business Mobile Device Security Management Themes PDF today and make your presentation stand out from the rest.

Cyber Risks And Incident Response Playbook Performing Cyber Training Exercises For Securing The Assets Mockup PDF
Purpose of this slide is to address and perform various cyber training exercises in order to secure companys assets. Exercises covered are defense in depth, capture the flag etc. Retrieve professionally designed Cyber Risks And Incident Response Playbook Performing Cyber Training Exercises For Securing The Assets Mockup PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Blockchain Security Solutions Deployment Blockchain Hashing SHA 256 Algorithm Formats PDF
This slide talks about the hashing SHA-256 algorithm used in blockchain technology, including its properties. The purpose of this slide is to give an overview of hashing and its properties, such as collision resistance, deterministic, quick, and irreversible. Create an editable Blockchain Security Solutions Deployment Blockchain Hashing SHA 256 Algorithm Formats PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Blockchain Security Solutions Deployment Blockchain Hashing SHA 256 Algorithm Formats PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Handling Several Food Ingredients Quality Food Security Excellence Ppt Styles Template PDF
This slide provides information regarding handling of food ingredients quality for various kinds of ingredients such as liquid, dry ingredient and oil. Presenting handling several food ingredients quality food security excellence ppt styles template pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like liquid ingredients, dry ingredients, oil. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Corporate Security And Risk Management Determine Sequence Phases For Threat Attack Ideas PDF
This slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. Presenting corporate security and risk management determine sequence phases for threat attack ideas pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like reconnaissance, weaponization, delivery, exploitation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
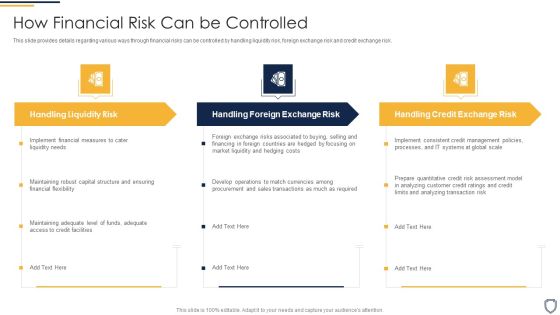
Corporate Security And Risk Management How Financial Risk Can Be Controlled Infographics PDF
This slide provides details regarding various ways through financial risks can be controlled by handling liquidity risk, foreign exchange risk and credit exchange risk. Presenting corporate security and risk management how financial risk can be controlled infographics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like handling liquidity risk, handling foreign exchange risk, handling credit exchange risk . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Heroku Cloud Application Impact On Customer Icons PDF
This slide highlights overall impact of Heroku cloud application on customers of industries using this platform. It further includes various impacts such as customer experience, accessibility, privacy and security, and future readiness. Welcome to our selection of the Heroku Cloud Application Impact On Customer Icons PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today

Security Information And Event Management Strategies For Financial Audit And Compliance SIM Vs SEM Vs SIEM Sample PDF
Presenting security information and event management strategies for financial audit and compliance sim vs sem vs siem sample pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like security information management, security event management, security information and event management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

NIST Cybersecurity Framework Implementation Tier Categories Rules PDF
The slide showcases Nist cyber security framework tiers which categorize your organizations security processes, it helps to analyze which tier your organization belongs to and what your current systems security requirements are. The tiers are as following partial, risk informed, repeatable and adaptive. Persuade your audience using this NIST Cybersecurity Framework Implementation Tier Categories Rules PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Partial, Risk Informed, Repeatable . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Security Information And Event Management Strategies For Financial Audit And Compliance What Sets Us Apart Pictures PDF
This slide covers the reasons why our company is different from other SIEM companies since they have qualities such as attractive TCO and ROI, improved IT productivity, etc. Presenting security information and event management strategies for financial audit and compliance what sets us apart pictures pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like cost ownership and roi, security devices, dynamic business, productivity improvement for it. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Information And Event Management Strategies For Financial Audit And Compliance Need For SIEM Software Download PDF
This slide covers the need for the SIEM software which focuses on detecting incidents, compliance regulations, and incident management. Presenting security information and event management strategies for financial audit and compliance need for siem software download pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like detecting incidents, compliance with regulations, efficient incident management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Various Aspects Of Business Management Solution Structure PDF
This slide exhibits different aspects of enterprise software that support business applications and operations. It contains five key aspects architecture, security, performance, format and cost. Persuade your audience using this Various Aspects Of Business Management Solution Structure PDF. This PPT design covers Four stages, thus making it a great tool to use. It also caters to a variety of topics including Architecture, Security, Performance. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
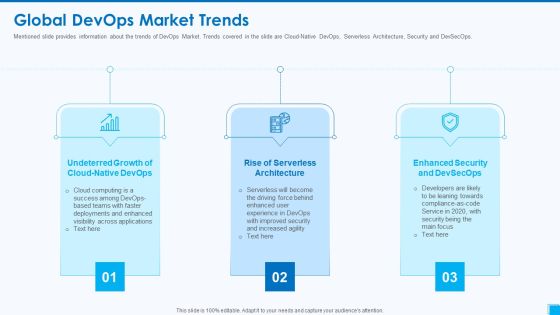
Devops Tools And Configuration IT Global Devops Market Trends Ppt Pictures Show PDF
Mentioned slide provides information about the trends of DevOps Market. Trends covered in the slide are Cloud-Native DevOps, Serverless Architecture, Security and DevSecOps. This is a devops tools and configuration it global devops market trends ppt pictures show pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like undeterred growth of cloud native devops, rise of serverless architecture, enhanced security and devsecops. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

NIST Cybersecurity Framework Best Practices Topics PDF
The slide highlights the best practices to be followed in order to overcome various implementation challenges of Nist framework for cyber security. It covers understand, automate, prioritize and talent acquisition. Persuade your audience using this NIST Cybersecurity Framework Best Practices Topics PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Understand, Automate, Talent Acquisition. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
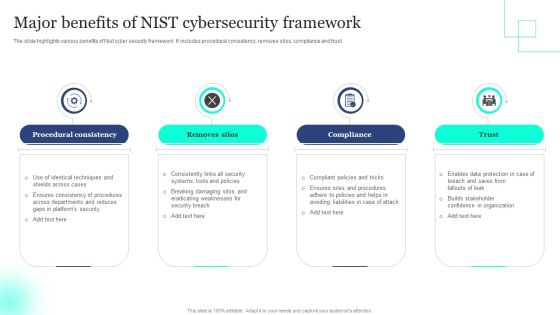
Major Benefits Of NIST Cybersecurity Framework Elements PDF
The slide highlights various benefits of Nist cyber security framework. It includes procedural consistency, removes silos, compliance and trust. Presenting Major Benefits Of NIST Cybersecurity Framework Elements PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Procedural Consistency, Removes Silos, Compliance . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Agile Quality Control Framework IT QA Testing Methodologies Nonfunctional Information PDF
This slide shows the non functional methodologies for Quality assurance testing. Methodologies covered in the slide are Vulnerability, usability testing, compatible testing and performance testing. Presenting agile quality control framework it qa testing methodologies functional themes pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security, software, performance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Business Application Threat Modeling Procedure Designs PDF
This slide contains application threat modeling process to evaluate and manage risks. It includes four steps identify fundamentals, data flow, security profile and recommendations. Persuade your audience using this Business Application Threat Modeling Procedure Designs PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Examine Existing, Understand Capabilities, Recommendations. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Implementing An Effective Ecommerce Management Framework Challenges Faced By Ecommerce Marketing Manager Graphics PDF
This slide represents the hurdles and business challenges faced by marketing manager of ABC ecommerce firm in the current scenario. It includes business challenges such as customers exploding expectations, agility, data security, customer retention and omni-channel experience. Create an editable Implementing An Effective Ecommerce Management Framework Challenges Faced By Ecommerce Marketing Manager Graphics PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre-designed presentation templates help save time. Implementing An Effective Ecommerce Management Framework Challenges Faced By Ecommerce Marketing Manager Graphics PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

RUP Model Management And Control Change Software Ppt Slides Designs PDF
This slide represents how management and control change software is easy in the rational unified process RUP also determines work and security domains. This is a rup model management and control change software ppt slides designs pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like development, management, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Business Insurance Business Analysis Method Ppt Portfolio Graphics Example PDF
Presenting business insurance business analysis method ppt portfolio graphics example pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like business, organization, revenues, securing. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Effects Of Inadequate Report For Quality Management System Clipart PDF
This slide showcases the adverse effects of poor document control on the organizations quality management system. The purpose is to take action on time. It includes fines, efficiency, storage space, security breaches, and violation of regulations. Persuade your audience using this Effects Of Inadequate Report For Quality Management System Clipart PDF. This PPT design covers Five stages, thus making it a great tool to use. It also caters to a variety of topics including Storage Space, Security Breaches, Violation Of Regulations. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Emerging Trends Of Business Management Solution Template PDF
This slide contains emerging software development trends that focuses on automation and technical advancement to enhance business processes It includes four trends rise of hybrid and progressive apps, cyber security, low code platforms and artificial intelligence. Persuade your audience using this Emerging Trends Of Business Management Solution Template PDF. This PPT design covers Four stages, thus making it a great tool to use. It also caters to a variety of topics including Hybrid Apps, Cyber Security, Low Code Platforms. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Database Management Software System Features Topics PDF
This slide defines the features of database management software system. It includes information related to data structuring, security protocols and backup. Persuade your audience using this Database Management Software System Features Topics PDF. This PPT design covers Five stages, thus making it a great tool to use. It also caters to a variety of topics including Data Normalization, Security Protocols, Data Structuring. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Risks Of Legacy Application And Traditional Technology Mockup PDF
This slide defines the risk involved in using legacy system. It includes information related to operational cost, security vulnerabilities, system incompatibility, talent pool, etc. Persuade your audience using this Risks Of Legacy Application And Traditional Technology Mockup PDF. This PPT design covers Five stages, thus making it a great tool to use. It also caters to a variety of topics including Increasing Operational Costs, Security Vulnerabilities, System Incompatibility. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Steps For Hybrid Cloud Technology Maturity Assessment Process Microsoft PDF
This slide showcases steps to develop hybrid cloud technology assessment process which helps improve cloud performance. It provides information regarding cloud infrastructure, private cloud, cloud security, cloud management and monitoring. Persuade your audience using this Steps For Hybrid Cloud Technology Maturity Assessment Process Microsoft PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Develop Cloud Infrastructure, Cloud Security, Cloud Monitoring. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

5 Data Management Challenges Faced By Marketing And Sales Team Summary PDF
This slide highlights challenges faced by marketing and sales personnel in customer data integration. Key challenges included here are data extraction, maintaining data quality, data integration, data security and choosing team for data management. Persuade your audience using this 5 Data Management Challenges Faced By Marketing And Sales Team Summary PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Data Integration, Data Security, Right Team. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Strategy To Be Adopted 2 Educate And Increase Employee Awareness Inspiration PDF
This slide shows the strategy to be adopted by the company i.e. Educate and provide proper data security training to the employees, make them familiar with latest security techniques etc. along with the need of such strategy and how it is to be implemented that will give benefit to the company. Presenting strategy to be adopted 2 educate and increase employee awareness inspiration pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like strategy to be adopted 2 educate and increase employee awareness. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Strategy To Be Adopted 2 Educate And Increase Employee Awareness Infographics PDF
This slide shows the strategy to be adopted by the company i.e. Educate and provide proper data security training to the employees, make them familiar with latest security techniques etc. along with the need of such strategy and how it is to be implemented that will give benefit to the company. Presenting strategy to be adopted 2 educate and increase employee awareness infographics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like strategy to be adopted 2 educate and increase employee awareness. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Strategy To Be Adopted 1 Data Encryption Ppt Gallery Skills PDF
This slide shows the strategy to be adopted by the company i.e. Encrypt the data in order to protect data, ensure security across multiple devices, move data securely, maintain data integrity etc. along with the need of such strategy and how it is to be implemented that will give benefit to the company. Presenting strategy to be adopted 1 data encryption ppt gallery skills pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like strategy to be adopted 1 data encryption. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
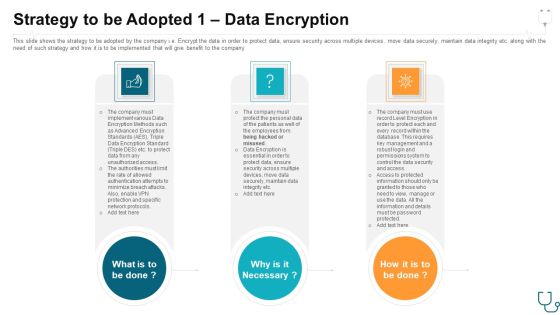
Strategy To Be Adopted 1 Data Encryption Ppt Model Deck PDF
This slide shows the strategy to be adopted by the company i.e. Encrypt the data in order to protect data, ensure security across multiple devices, move data securely, maintain data integrity etc. along with the need of such strategy and how it is to be implemented that will give benefit to the company. Presenting strategy to be adopted 1 data encryption ppt model deck pdf. to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like strategy to be adopted 1 data encryption. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Strategies For Software Development Testing And Production Of Salesforce Marketing Cloud Portrait PDF
This slide showcases strategies of salesforce marketing cloud which are separate enterprise account, use test folders with in one business unit and separate business unit. Persuade your audience using this Strategies For Software Development Testing And Production Of Salesforce Marketing Cloud Portrait PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Business Unit, Data Security, Deployment. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Classified Data Memo Record With Strategic Goals Overview Of Systems And Controls Summary Of Barwash 99 Rules PDF
The slide provides information about the detailed overview of the systems and controls protocol that will be followed by Barwash 99 in their operations in order to achieve the strategic objectives. Presenting classified data memo record with strategic goals overview of systems and controls summary of barwash 99 rules pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like billing systems and inventory controls, security, food production and preparation, personnel. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Market Analysis Of Retail Sector Retail Price Management Goals Ppt File Graphics Download PDF
Presenting market analysis of retail sector retail price management goals ppt file graphics download pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like performance metrics, campaigns, security, analysis, price transparency. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Key Steps Of Threat Modelling Procedure Brochure PDF
This slide exhibits steps of threat modelling process to identify security requirements in business systems. It includes five steps determine objectives, visualize, analyse risks, mitigate and validate.Persuade your audience using this Key Steps Of Threat Modelling Procedure Brochure PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Determine Objectives, Preventative Solutions, Determine Various Ways. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Various Types Of Data Accuracy Risks Guidelines PDF
The slide shows data integrity risks to define different types of errors. Various types of threats included are human error, transfer error and error due to malicious acts.Persuade your audience using this Various Types Of Data Accuracy Risks Guidelines PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Recording Mistakes, File Transportation, Security Threats. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
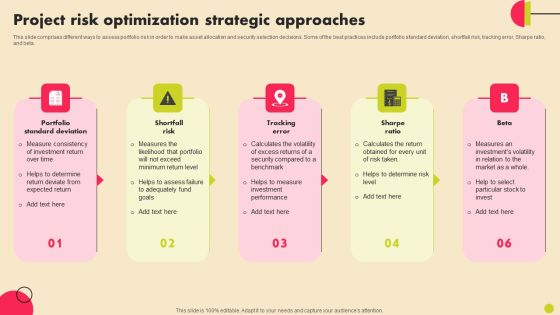
Project Risk Optimization Strategic Approaches Formats PDF
This slide comprises different ways to assess portfolio risk in order to make asset allocation and security selection decisions. Some of the best practices include portfolio standard deviation, shortfall risk, tracking error, Sharpe ratio, and beta. Persuade your audience using this Project Risk Optimization Strategic Approaches Formats PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Portfolio Standard Deviation, Shortfall Risk, Tracking Error. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Strategy To Be Adopted 3 Restrict Access To Physical Devices Guidelines PDF
This slide shows the strategy to be adopted by the company i.e. restricting the access of Physical devices to authorized personnel only in order to avoid data misuse data leakage, security breach etc. along with the need of such strategy and how it is to be implemented that will give benefit to the company. Presenting strategy to be adopted 3 restrict access to physical devices guidelines pdf to provide visual cues and insights. Share and navigate important information on strategy to be adopted 3 restrict access to physical devices guidelines pdf stages that need your due attention. This template can be used to pitch topics like strategy to be adopted 3 restrict access to physical devices. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Strategy To Be Adopted 3 Restrict Access To Physical Devices Pictures PDF
This slide shows the strategy to be adopted by the company i.e. restricting the access of Physical devices to authorized personnel only in order to avoid data misuse data leakage, security breach etc. along with the need of such strategy and how it is to be implemented that will give benefit to the company. Presenting strategy to be adopted 3 restrict access to physical devices pictures pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like strategy to be adopted 3 restrict access to physical devices. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Infotech Solutions Research And Development Company Summary Case Study Software Development Summary PDF
This slide shows the case study which includes challenge faced by client for development of integrated environment and infrastructure for secure holistic software development and operations. Company provide customized software solution with data encryption. Presenting Infotech Solutions Research And Development Company Summary Case Study Software Development Summary PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Challenge, Solution, Result. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
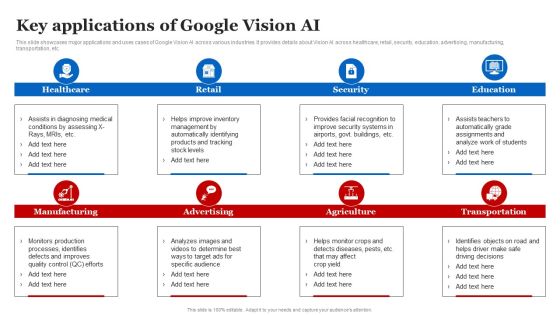
Key Applications Of Google Vision AI Introduction PDF
This slide showcases major applications and uses cases of Google Vision AI across various industries. It provides details about Vision AI across healthcare, retail, security, education, advertising, manufacturing, transportation, etc. Find a pre-designed and impeccable Key Applications Of Google Vision AI Introduction PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
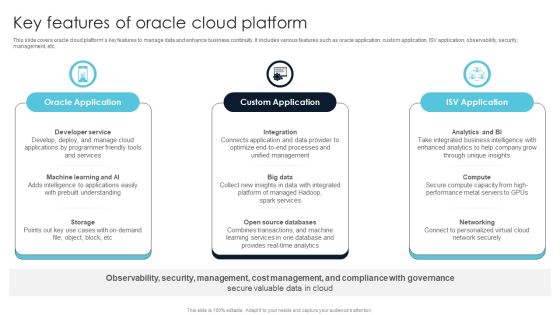
Ultimate Guide For Cloud Platform Deployment Key Features Of Oracle Cloud Platform Diagrams PDF
This slide covers oracle cloud platforms key features to manage data and enhance business continuity. It includes various features such as oracle application, custom application, ISV application, observability, security, management, etc. Find a pre-designed and impeccable Ultimate Guide For Cloud Platform Deployment Key Features Of Oracle Cloud Platform Diagrams PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
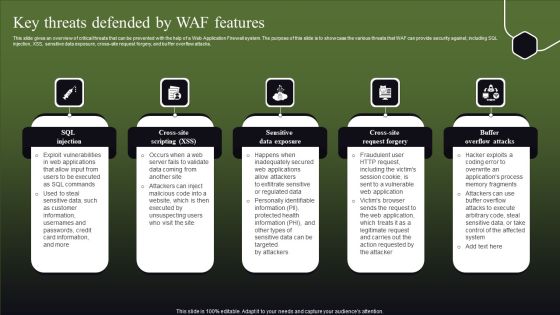
Key Threats Defended By WAF Features Ppt Pictures Elements PDF
This slide gives an overview of critical threats that can be prevented with the help of a Web Application Firewall system. The purpose of this slide is to showcase the various threats that WAF can provide security against, including SQL injection, XSS, sensitive data exposure, cross-site request forgery, and buffer overflow attacks. Explore a selection of the finest Key Threats Defended By WAF Features Ppt Pictures Elements PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Key Threats Defended By WAF Features Ppt Pictures Elements PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Future Trends Related To AI Based Marketing Ppt Slides Files PDF
This slide showcases future trends of artificial intelligence oriented marketing which marketers can refer for expanding their potential promotional options in long run. It provides details about large language models, cyber security, multimodal AI, vertical solutions, responsible AI, etc. Get a simple yet stunning designed Future Trends Related To AI Based Marketing Ppt Slides Files PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Future Trends Related To AI Based Marketing Ppt Slides Files PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Building Positive Relationships Example Ppt Design
This is a building positive relationships example ppt design. This is a seven stage process. The stages in this process are safety, trust, respect, connect, identify, close, plan.

Case Study 4 Improving Patient Security And Reducing Risk Of Violence Graphics PDF
Presenting case study 4 improving patient security and reducing risk of violence graphics pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like building management, security management, power management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
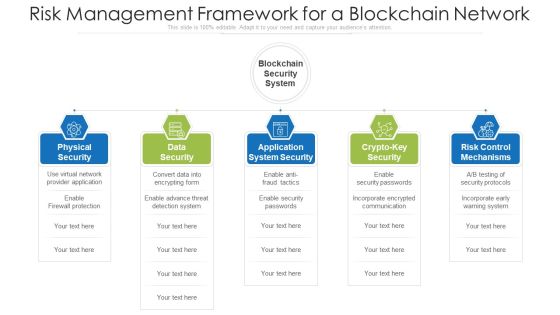
Risk Management Framework For A Blockchain Network Ppt PowerPoint Presentation Portfolio Format Ideas PDF
Persuade your audience using this risk management framework for a blockchain network ppt powerpoint presentation portfolio format ideas pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including application system security, risk control mechanisms, physical security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Embedded Internet Of Things Model With Customer Platform Ppt PowerPoint Presentation Infographics Pictures PDF
Presenting embedded internet of things model with customer platform ppt powerpoint presentation infographics pictures pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including inside secure crypto, inside secure boot and firmware update, software framework. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
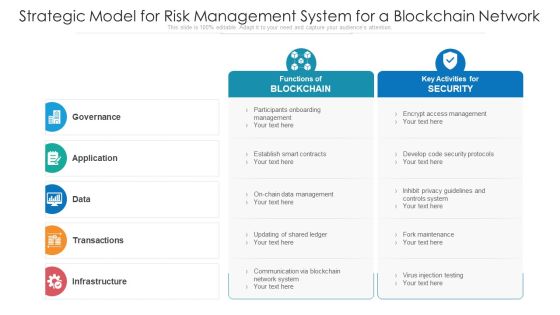
Strategic Model For Risk Management System For A Blockchain Network Ppt PowerPoint Presentation Professional Example File PDF
Persuade your audience using this strategic model for risk management system for a blockchain network ppt powerpoint presentation professional example file pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Participants Onboarding Management, Encrypt Access Management, Develop Code Security Protocols. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Uniformed Security Next Steps In The Security Guard Services Proposal Rules PDF
Presenting uniformed security next steps in the security guard services proposal rules pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like next steps. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Policies And Procedures Password Creation And Management Policy Diagrams PDF
This slide depicts the password creation and management policy that explains how to create, implement, and review a defined procedure for establishing, updating, and maintaining strong and secure passwords. Slidegeeks has constructed IT Policies And Procedures Password Creation And Management Policy Diagrams PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Organizing Security Awareness Outlook Of Social Engineering Attack Ideas PDF
The purpose of this slide is to showcase an example of social engineering attack. It also covers information about how the social engineering attack work and spread malware. Slidegeeks has constructed Organizing Security Awareness Outlook Of Social Engineering Attack Ideas PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Cloud Security Assessment How Does Cloud Security Work Data Security Diagrams PDF
This slide represents the data recovery and business continuity plan in cloud security and what to consider while making a business continuity plan.Presenting Cloud Security Assessment How Does Cloud Security Work Data Security Diagrams PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Impact Analysis, Recovery Strategies, Plan Development. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Table Of Contents Series Of Cyber Security Attacks Against Ukraine 2022 Elements PDF
Slidegeeks has constructed Table Of Contents Series Of Cyber Security Attacks Against Ukraine 2022 Elements PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

Table Of Contents Security Automation To Analyze And Mitigate Cyberthreats Diagrams PDF
Slidegeeks has constructed Table Of Contents Security Automation To Analyze And Mitigate Cyberthreats Diagrams PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Cyber Security Incident Response KPI Dashboard Microsoft PDF
This slide represents dashboard showing the key metrics of cyber security incident response. It includes key performance indicators such as risk score, compliance status, threat level etc. Slidegeeks has constructed Cyber Security Incident Response KPI Dashboard Microsoft PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

Secure Access Service Edge Architecture Characteristics Ppt Summary Portfolio PDF
This slide represents the architectural characteristics of a secure access service edge. The purpose of this slide is to showcase the features of SASE architecture that include identity-driven, cloud-native, support for all edges, and global distribution. Make sure to capture your audiences attention in your business displays with our gratis customizable Secure Access Service Edge Architecture Characteristics Ppt Summary Portfolio PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

IT Security Risk Management Dashboard With Risk Rating And Breakdown Pictures PDF
This slide displays dashboard for real- time tracking and management of cybersecurity risk to help company formulate appropriate mitigation strategies. It includes kpis such as response plan progress, heat map, action plan, top 5 vulnerabilities, etc. Pitch your topic with ease and precision using this IT Security Risk Management Dashboard With Risk Rating And Breakdown Pictures PDF. This layout presents information on Risk Rating Breakdown, Action Plan Breakdown, Risk Probability Score, Risk Analysis Progress. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Strategic Risk Assessment Framework For IT Security Risk Management Ideas PDF
This slide showcases flow diagram to plan efficient management of cybersecurity risks for the organization for threat reduction. It includes steps such as understanding company strategies, data gathering, preliminary risk profiling, action plan, etc. Presenting Strategic Risk Assessment Framework For IT Security Risk Management Ideas PDF to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including Strategic Risk, Cybersecurity, Management Framework, Data Gathering. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
 Home
Home