Confirmation

Software Migration Planning Phases Weekly Timeline Summary PDF
Mentioned slide showcases sequence of weekly events planned for a successful software migration. It includes various phases like pre testing migration, migration testing, post migration testing and verification. Showcasing this set of slides titled Software Migration Planning Phases Weekly Timeline Summary PDF. The topics addressed in these templates are Migration Testing, Post Migration Testing, Verification. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Functioning Of Serverless Computing Security Related Challenges In Serverless Technology Graphics PDF
The purpose of the following slide is to show the various challenges that may present to the organization, these issues can be authentication issues, no-proper monitoring, and third-party dependency. This is a functioning of serverless computing security related challenges in serverless technology graphics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like authentication issues, dependency third party, improper monitoring and controlling. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
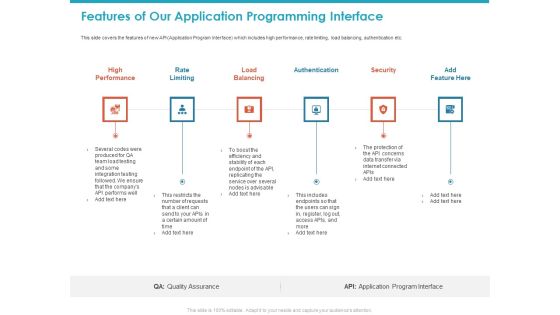
Features Of Our Application Programming Interface Ppt Layouts Layout Ideas PDF
This slide covers the features of new API Application Program Interface which includes high performance, rate limiting, load balancing, authentication etc. This is a features of our application programming interface ppt layouts layout ideas pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like high performance, rate limiting, load balancing, authentication, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Importance Of Marketing Plan To Meet Targets Ppt Professional Graphics Tutorials PDF
This slide covers importance of marketing strategy such as customer demographics, SMART strategy, consistency, creating timeline and authenticity that helps company to accomplish marketing objectives. Presenting importance of marketing plan to meet targets ppt professional graphics tutorials pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including brand authentic, create timeline, consistency, target demographics, smart strategy. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

5G Network Technology Determine Identity And Access Management With 5G Ppt Inspiration Outfit PDF
This slide provides details regarding identity and access management with 5G in terms of 5G identifiers and 5G authentication. This is a 5g network technology determine identity and access management with 5g ppt inspiration outfit pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like 5g identifiers, 5g authentication. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
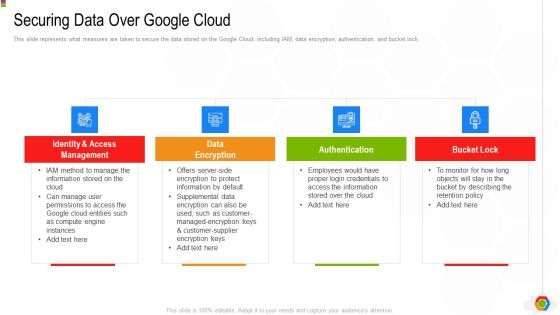
Google Cloud Console IT Securing Data Over Google Cloud Ppt Pictures Slides PDF
This slide represents what measures are taken to secure the data stored on the Google Cloud, including IAM, data encryption, authentication, and bucket lock. This is a google cloud console it securing data over google cloud ppt pictures slides pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like identity and access management, data encryption, authentication, bucket lock. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Phase 3 Respond To Cloud Protection Issues Cloud Computing Security IT Ppt Gallery Rules PDF
This slide represents phase 3 of cloud security, such as respond to cloud protection issues. It includes an advanced authentication process, manages cloud access standards when new services come up, and eliminates malware from cloud services. Deliver and pitch your topic in the best possible manner with this phase 3 respond to cloud protection issues cloud computing security it ppt gallery rules pdf. Use them to share invaluable insights on authentication process, service, web policies and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Enterprise Cloud Security Solutions Cloud Computing Security IT Ppt Professional Slide Download PDF
This slide describes the enterprise cloud security solutions, including multi-factor authentication, managing accounts and service proactively, being careful about shadow IT, and analyzing the cost-benefits of hybrid cloud. Deliver and pitch your topic in the best possible manner with this enterprise cloud security solutions cloud computing security it ppt professional slide download pdf. Use them to share invaluable insights on analyze, services, authentication, business, organizations and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

How Does Cloud Security Work Identity And Access Management Iam Cloud Computing Security IT Ppt Infographics Picture PDF
This slide represents the identity and access management in a cloud security system that is based on authentication, authorization, access control, and central user repository. Presenting how does cloud security work identity and access management iam cloud computing security it ppt infographics picture pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like authentication, authorization, access management, central user repository. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Peloton Capital Raising Elevator Peloton Brand Values Demonstration PDF
This slide provides the glimpse about the peloton brand values, what they are known for such as empowering, optimistic, premium, authentic, captivating, etc. This is a peloton capital raising elevator peloton brand values demonstration pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like captivating, empowering, optimistic, premium, authentic. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Computing Technology Implementation Plan Security Related Challenges In Serverless Technology Ideas PDF
The purpose of the following slide is to show the various challenges that may present to the organization, these issues can be authentication issues, no-proper monitoring, and third-party dependency. Presenting cloud computing technology implementation plan security related challenges in serverless technology ideas pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like improper monitoring and controlling, authentication issues, dependency on third party. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Elaborative Summary Of Different Offline Marketing Methods Benefits And Advantages Topics PDF
This slide shows some key benefits of implementing Offline Marketing Strategy to the company such as higher authenticity value, faster feedback, enhanced loyalty and relationship building, variety of choice, offline marketing strategies are reusable etc. This is a elaborative summary of different offline marketing methods benefits and advantages topics pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like higher authenticity value, variety of choice, loyalty and relationship building You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Corporate Brand Story Practices In Electric Vehicle Company Rules PDF
The following slide highlights the corporate brand story practices in electric vehicle company illustrating authentic, proactive, content, change and measure as key headings for developing brand narrative and monitor their effect. Persuade your audience using this corporate brand story practices in electric vehicle company rules pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including authentic, proactive, content. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Internet Marketing Playbook Brand Voice Chart For Launching The New Product Template PDF
This slide illustrates brand voice chart of the company covering voice characteristics along with description.. Voice characteristics covered in the chart are authentic, passionate, helpful etc. Deliver and pitch your topic in the best possible manner with this Internet Marketing Playbook Brand Voice Chart For Launching The New Product Template PDF. Use them to share invaluable insights on Voice Characteristics Authentic, Passionate Innovation Solution, Customer Needs Provide and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cloud Information Security Enterprise Cloud Security Solutions Ppt Ideas File Formats PDF
This slide describes the enterprise cloud security solutions, including multi-factor authentication, managing accounts and service proactively, being careful about shadow IT, and analyzing the cost-benefits of hybrid cloud. Presenting Cloud Information Security Enterprise Cloud Security Solutions Ppt Ideas File Formats PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Multi Factor Authentication, Cost Benefits, Hybrid Cloud. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Information Security Phase 3 Respond To Cloud Protection Issues Ppt Layouts Influencers PDF
This slide represents phase 3 of cloud security, such as respond to cloud protection issues. It includes an advanced authentication process, manages cloud access standards when new services come up, and eliminates malware from cloud services. Deliver and pitch your topic in the best possible manner with this Cloud Information Security Phase 3 Respond To Cloud Protection Issues Ppt Layouts Influencers PDF. Use them to share invaluable insights on Advanced Authentication, Cloud Access, Eliminate Malware and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cloud Information Security How Does Cloud Security Work Identity And Access Management IAM Formats PDF
This slide represents the identity and access management in a cloud security system that is based on authentication, authorization, access control, and central user repository. Presenting Cloud Information Security How Does Cloud Security Work Identity And Access Management IAM Formats PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Central Repository, Access Management, Authorization Authentication. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Phase 3 Respond To Cloud Protection Issues Ideas PDF
This slide represents phase 3 of cloud security, such as respond to cloud protection issues. It includes an advanced authentication process, manages cloud access standards when new services come up, and eliminates malware from cloud services. This is a Phase 3 Respond To Cloud Protection Issues Ideas PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Information, Cloud Service, Advanced Authentication Process. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
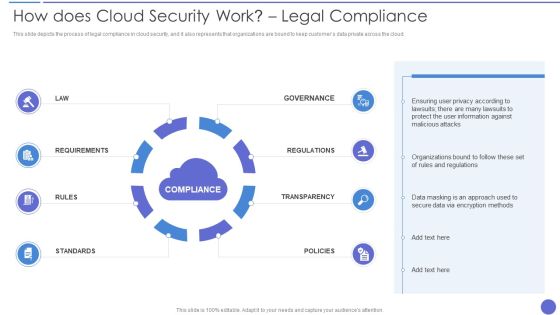
How Does Cloud Security Work Legal Compliance Background PDF
This slide represents the identity and access management in a cloud security system that is based on authentication, authorization, access control, and central user repository. Presenting How Does Cloud Security Work Legal Compliance Background PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Authorization, Authentication, Access Management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Assessment Phase 3 Respond To Cloud Protection Issues Topics PDF
This slide represents phase 3 of cloud security, such as respond to cloud protection issues. It includes an advanced authentication process, manages cloud access standards when new services come up, and eliminates malware from cloud services.Deliver and pitch your topic in the best possible manner with this Cloud Security Assessment Phase 3 Respond To Cloud Protection Issues Topics PDF Use them to share invaluable insights on Authentication Process, Access Standards, Eliminate Malware and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

CRM Implementation Strategy Securing Our Data With CRM Summary PDF
This slide highlights the data security using CRM which incorporates IP restriction, two factor authentication, data storage, communication protection and data security.This is a CRM Implementation Strategy Securing Our Data With CRM Summary PDF template with various stages. Focus and dispense information on One stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Factor Authentication, Communication Protection, Restrict Unauthorized. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Sales CRM Cloud Solutions Deployment Securing Our Data With CRM Infographics PDF
This slide highlights the data security using CRM which incorporates IP restriction, two factor authentication, data storage, communication protection and data security.This is a Sales CRM Cloud Solutions Deployment Securing Our Data With CRM Infographics PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Factor Authentication, Storage And Failover, Communication Protection. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Consultancy Services Company Profile Company Introduction And Its Core Values Sample PDF
This slide focuses on detailed company introduction which includes founded year, industry, headquarters and specialities with core values such as sustainability, honesty, integrity, ethical, innovation and authenticity.Presenting IT Consultancy Services Company Profile Company Introduction And Its Core Values Sample PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Sustainability, Authenticity, Innovation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Google Cloud Computing System Securing Data Over Google Cloud Microsoft PDF
This slide represents what measures are taken to secure the data stored on the Google Cloud, including IAM, data encryption, authentication, and bucket lock. Presenting Google Cloud Computing System Securing Data Over Google Cloud Microsoft PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Access Management, Data Encryption, Authentication. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
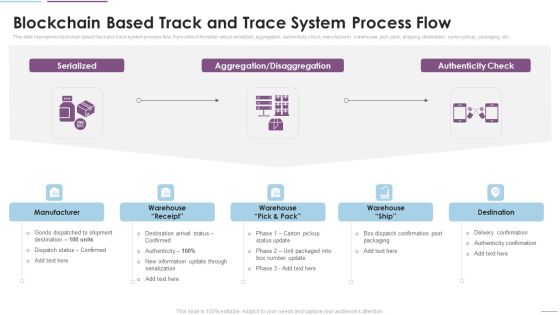
Supply Chain Management Blockchain Based Track And Trace System Process Flow Graphics PDF
This slide represents blockchain based track and trace system process flow. It provides information about serialized, aggregation, authenticity check, manufacturer, warehouse, pick, pack, shipping, destination, carton pickup, packaging, etc. Presenting Supply Chain Management Blockchain Based Track And Trace System Process Flow Graphics PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Authenticity Check, Manufacturer, Serialized. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Developing 5G Wireless Cellular Network Determine Identity And Access Management With 5G Download PDF
This slide provides details regarding identity and access management with 5G in terms of 5G identifiers and 5G authentication. This is a Developing 5G Wireless Cellular Network Determine Identity And Access Management With 5G Download PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like 5G Identifiers, 5G Authentication . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Insider Threat In Cyber Security Discovery Flowchart Of IT Company Template PDF
This slide shows information technology company flowchart indicating insider threat discovery. It provides information such as user request for service, authentication check, starting session, role based access control RBAC, permission checks, etc. Persuade your audience using this Insider Threat In Cyber Security Discovery Flowchart Of IT Company Template PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Terminate Session, Allow Access, Authentication Service. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Brand Promotion Communication Strategy Techniques To Improve Brand Communication Microsoft PDF
This slide covers various tactics to enhance the brand communication process. It includes techniques such as authentic communication strategy, showcasing brand personality, maintaining transparency, and providing solutions to customers problems. Presenting Brand Promotion Communication Strategy Techniques To Improve Brand Communication Microsoft PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Authentic Communication Strategy, Showcase Brand Personality, Maintain Transparency. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Technology Threat Mitigation Methods Preventive IT Technical Control Measures Information PDF
The following slide highlights the preventive information technical controls which includes authentication, authorization, enable control enforcement, nonrepudiation, secured communications and secured transactions. Presenting Information Technology Threat Mitigation Methods Preventive IT Technical Control Measures Information PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Authorization, Secured Communications, Authentication. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Intelligent Computing System Safety And Security Objectives In Cyber Physical Systems Ideas PDF
This slide represents cyber physical systems safety and security objectives, including confidentiality, integrity, availability, authenticity, and robustness. Presenting Cyber Intelligent Computing System Safety And Security Objectives In Cyber Physical Systems Ideas PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Availability, Authenticity, Robustness, Integrity. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Different Supportive Leadership Models Deployed In Organization Guidelines PDF
This slide covers four types of leadership models and description of its working. It involves four models such as authoritative model, authentic exec, coaching leader and group think model. Pitch your topic with ease and precision using this Different Supportive Leadership Models Deployed In Organization Guidelines PDF. This layout presents information on Leadership Models, Authoritative Model, Authentic Exec. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Blockchain Based Track And Trace System Process Flow Diagrams PDF
This slide represents blockchain based track and trace system process flow. It provides information about serialized, aggregation, authenticity check, manufacturer, warehouse, pick, pack, shipping, destination, carton pickup, packaging, etc. This is a Blockchain Based Track And Trace System Process Flow Diagrams PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Manufacturer, Destination, Authenticity Check. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Key Strategies For Data Protection And Privacy Rules PDF
The following slide showcases some techniques to ensure data security and privacy. It includes elements such as authentication, data encryption, network security, access controls etc. Persuade your audience using this Key Strategies For Data Protection And Privacy Rules PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Authentication, Data Encryption, Network Security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Security Components To Enhance Processes Tools Used For Cyber Security Goals Introduction PDF
This slide outlines the tools used to achieve cyber security goals such as confidentiality, integrity, and availability. The tools for confidentiality include encryption, access control, authentication, authentication, authorization, and physical security. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Cyber Security Components To Enhance Processes Tools Used For Cyber Security Goals Introduction PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

IT Security Awareness Training Program To Enhance Effectiveness Of Employees Structure PDF
This slide covers cybersecurity awareness training to enhance effectiveness of employees. It involves document management, passwords and authentication and social engineering and phishing. Persuade your audience using this IT Security Awareness Training Program To Enhance Effectiveness Of Employees Structure PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Document Management, Passwords And Authentication, Social, Engineering And Phishing. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Application Of Blockchain Technology In Supply Chain Management Introduction PDF
This slide shows the application of Blockchain technology for successful transportation of goods. It also includes the key areas of blockchain that are inventory and cargo tracking, authentication and quality check, automotive supplier payment, meat traceability. Persuade your audience using this Application Of Blockchain Technology In Supply Chain Management Introduction PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Inventory And Cargo Tracking, Authentication And Quality Check, Automotive Supplier Payments. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Innovative Strategies To Evaluate Impact Of Employee Training Microsoft PDF
This slide covers innovative strategies to evaluate training program effectiveness. It involves strategies such as virtual authentication, intelligent measurement, software adoption, HR analytics platform and feedback. Persuade your audience using this Innovative Strategies To Evaluate Impact Of Employee Training Microsoft PDF. This PPT design covers Seven stages, thus making it a great tool to use. It also caters to a variety of topics including Feedback And Survey, Measuring Software Adoption, Visual Authentication Of Effectiveness. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Online Certificate Security And Privacy Measures Ppt Ideas Gallery PDF
This slide showcases the features do digital security have for security. It includes features such as authentication, confidentiality, integrity, non-repudiation and access control. Persuade your audience using this Online Certificate Security And Privacy Measures Ppt Ideas Gallery PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Security Measures, Functions, Authentication, Confidentiality. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Best Practices For Business To Increase Online Security Introduction PDF
This slide highlights best practices for business to increase digital safety which help prevent and mitigate inherent risk. It provides information about antivirus, software upgradation, suspicious emails, VPN and 2 factor authentication. Presenting Best Practices For Business To Increase Online Security Introduction PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Security Vulnerabilities, Factor Authentication, Avoid Suspicious Emails. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
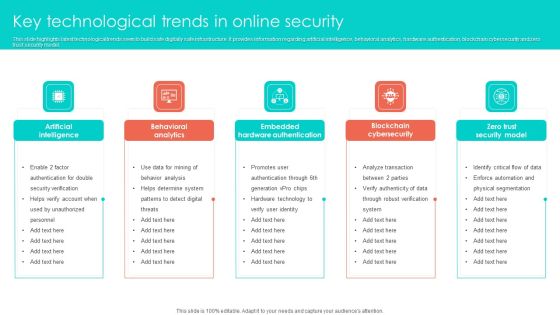
Key Technological Trends In Online Security Clipart PDF
This slide highlights latest technological trends seen to build safe digitally safe infrastructure. It provides information regarding artificial intelligence, behavioral analytics, hardware authentication, blockchain cybersecurity and zero trust security model. Persuade your audience using this Key Technological Trends In Online Security Clipart PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Behavioral Analytics, Artificial Intelligence, Embedded Hardware Authentication. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
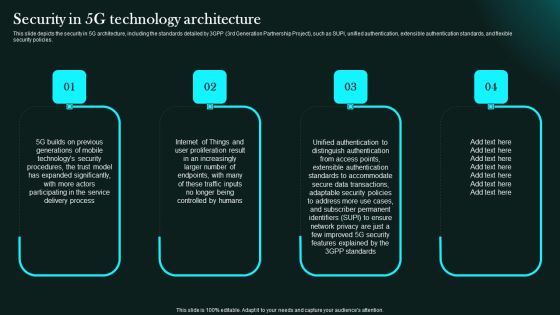
Security In 5G Technology Architecture 5G Network Functional Architecture Clipart PDF
This slide depicts the security in 5G architecture, including the standards detailed by 3GPP 3rd Generation Partnership Project, such as SUPI, unified authentication, extensible authentication standards, and flexible security policies.Slidegeeks has constructed Security In 5G Technology Architecture 5G Network Functional Architecture Clipart PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Advantages Of Artificial Intelligence In Mobile App Development Infographics PDF
This slide signifies the benefits of artificial intelligence in mobile app development. It covers information about powerful app authentication, improved security, recommendation services and AI powered chatbot Pitch your topic with ease and precision using this Advantages Of Artificial Intelligence In Mobile App Development Infographics PDF. This layout presents information on Powerful App Authentication, Improved Security, Recommendation Services. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Business Data Encryption Security Management Technology Ideas PDF
This slide highlights the role of encryption technology which is used by business and organisation to protect the confidentiality of digital data storage and transmission. Key components are authentication, privacy, regulatory compliance and security. Presenting Business Data Encryption Security Management Technology Ideas PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Authentication, Privacy, Regulatory Compliance, Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

IT Security Management Technology User Market Guidelines PDF
The following slide provides the statistical data for user market of IT risk assessment and mitigation software to make business process efficient. The technology used are authentication, firewalls, encryption, data masking and data backup. Showcasing this set of slides titled IT Security Management Technology User Market Guidelines PDF. The topics addressed in these templates are Authentication, Firewalls, Encryption, Data Masking, Data Backup. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Three Ways To Decrease Digital Email Bounce Professional PDF
This slide shows various ways which can be used to reduce email bounce rate of the company. It covers points such as maintain email list hygiene, domain authentication and monitor email analytics. Presenting Three Ways To Decrease Digital Email Bounce Professional PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Domain Authentication, Monitor Email Analytics, Maintain Email List Hygiene. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Smart Phone Device Security Best Practices Structure PDF
This slide shows key practices for protecting business data of mobile. The purpose of this slide is to highlight latest practices that can be used for securing mobile data. It include practices such as enable user authentication, update OS system, etc. Presenting Smart Phone Device Security Best Practices Structure PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Enable User Authentication, Avoid Using Public Wi Fi, Follow BYOD Policy. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Key Factors To Identify And Access Management Technique Strategy Elements PDF
This slide shows essential factors of IAM strategy. The purpose of this slide is to highlight essential activities for implementing IAM strategy model. It include factors such as authentication, authorization and user management , etc Persuade your audience using this Key Factors To Identify And Access Management Technique Strategy Elements PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Authentication, Management, Repository. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Bring Your Own Device Security Policy Trust Model Architecture Three Stage Process Rules PDF
This slide showcases BYOD trust model architecture three stage process, it concentrates on securing resource access independent of network location, subject, or asset. It also includes phases such as authentication, record keeping. evidence collection , etc. Persuade your audience using this Bring Your Own Device Security Policy Trust Model Architecture Three Stage Process Rules PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Record Keeping, Evidence Collection, Authentication . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
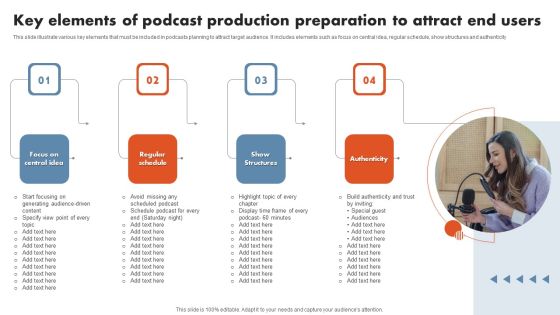
Key Elements Of Podcast Production Preparation To Attract End Users Demonstration PDF
This slide illustrate various key elements that must be included in podcasts planning to attract target audience. It includes elements such as focus on central idea, regular schedule, show structures and authenticity. Presenting Key Elements Of Podcast Production Preparation To Attract End Users Demonstration PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Authenticity, Show Structures, Regular Schedule. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
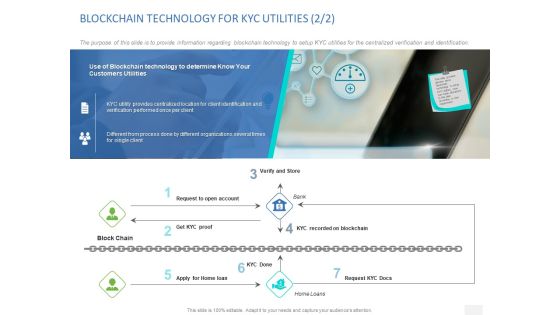
Organizational Socialization Blockchain Technology For Kyc Utilities Different Ppt Gallery PDF
The purpose of this slide is to provide information regarding blockchain technology to setup KYC utilities for the centralized verification and identification. This is a organizational socialization blockchain technology for kyc utilities different ppt gallery pdf. template with various stages. focus and dispense information on seven stages using this creative set, that comes with editable features. it contains large content boxes to add your information on topics like centralized location, identification verification, performed different, organizations several, technology determine. you can also showcase facts, figures, and other relevant content using this ppt layout. grab it now.

Addressing Stages Essential For Devops Environment Setup Contd IT Infrastructure By Executing Devops Approach Structure PDF
This slide provides information regarding various stages essential for setting up DevOps environment in terms of design, build and implementation, verification. Presenting addressing stages essential for devops environment setup contd it infrastructure by executing devops approach structure pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like design build and implementation, verification. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
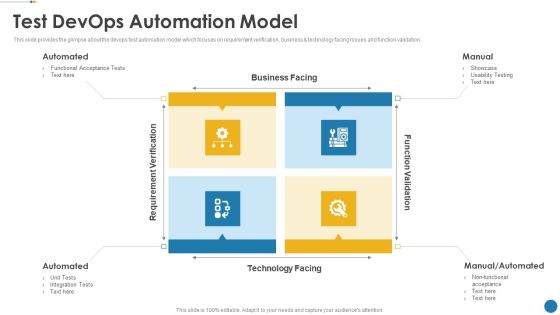
IT Operations Automation Test Devops Automation Model Microsoft PDF
This slide provides the glimpse about the devops test automation model which focuses on requirement verification, business and technology facing issues and function validation.This is a It operations automation test devops automation model microsoft pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like requirement verification, function validation, manual or automated. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Infrastructure As Code For Devops Growth IT Addressing Stages Essential For Devops Environment Setup Contd Introduction PDF
This slide provides information regarding various stages essential for setting up DevOps environment in terms of design, build and implementation, verification. Presenting infrastructure as code for devops growth it addressing stages essential for devops environment setup contd introduction pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like design build and implementation, verification. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
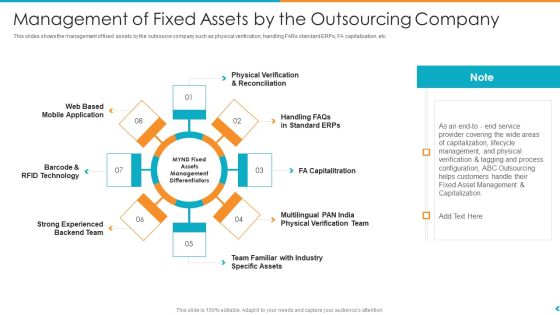
Fund Outsourcing Upgrade Efficiency Efficacy Fund Function Management Of Fixed Assets By The Outsourcing Company Ppt File Images
This slides shows the management of fixed assets by the outsource company such as physical verification, handling FARs standard ERPs, FA capitalization, etc. Presenting fund outsourcing upgrade efficiency efficacy fund function management of fixed assets by the outsourcing company ppt file images to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like barcode and rfid technology, fa capitalitration, web based mobile application, physical verification and reconciliation, handling faqs in standard erps. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Data Center Infrastructure Management IT Data Center Migration Phase Assessment Structure PDF
This slide depicts the data center migration phase that includes assessment, planning, validation, migration, and verification and optimization. Presenting data center infrastructure management it data center migration phase assessment structure pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like assessment, planning, validation, migration, verification and optimization. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Data Center Infrastructure Management IT Timeline For Migrating Data To Data Center Brochure PDF
This slide depicts the timeline for migrating data to the data center, including various phases such as assessment, planning, validation, migration, and verification and optimization. This is a data center infrastructure management it timeline for migrating data to data center brochure pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like planning, assessment, validation, migration, verification optimization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Software Development And IT Operations Infrastructure Development IT Addressing Stages Essential For Devops Background PDF
This slide provides information regarding various stages essential for setting up DevOps environment in terms of design, build and implementation, verification. Presenting software development and it operations infrastructure development it addressing stages essential for devops background pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like design build and implementation, verification. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Improvising Hiring Process Important Steps To Consider After Job Acceptance By Candidate Microsoft PDF
This slide provides information regarding essential steps to consider after accepting job by candidate in terms of documentation process, employment verification process, contacting candidate, joining date follow up, etc. This is a improvising hiring process important steps to consider after job acceptance by candidate microsoft pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like documentation process, employment verification process, contacting candidates, present employment resignation, joining date follow up. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
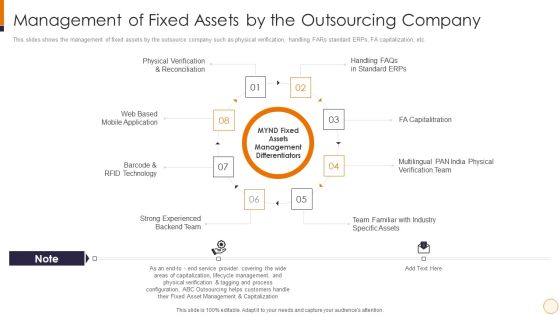
SME And Startups Financing Services Management Of Fixed Assets By The Outsourcing Company Sample PDF
This slides shows the management of fixed assets by the outsource company such as physical verification, handling FARs standard ERPs, FA capitalization, etc. This is a sme and startups financing services management of fixed assets by the outsourcing company sample pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like fa capitalitration, barcode and rfid technology, web based mobile application, handling faqs in standard erps, physical verification and reconciliation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
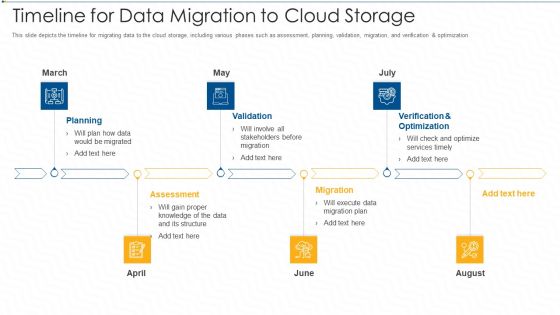
Timeline For Data Migration To Cloud Storage Ppt Pictures Portfolio PDF
This slide depicts the timeline for migrating data to the cloud storage, including various phases such as assessment, planning, validation, migration, and verification and optimization. This is a timeline for data migration to cloud storage ppt pictures portfolio pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like planning, validation, assessment, migration, verification and optimization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
 Home
Home