Computer Security

Computer Security Ppt Diagram Example Ppt Presentation
This is a computer security ppt diagram example ppt presentation. This is a eight stage process. The stages in this process are application guard, antivirus, passwords, firewall, attack detection, system guard, file lock, process quarantine.

Three Types Of Computer Security Designs PDF
This slide shows the various types of information technology security. It includes network, end point and internet security. Presenting Three Types Of Computer Security Designs PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Network Security, Point Security, Internet Security This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Four Computer Security Processes Portrait PDF
This slide shows the four step by step processes used in information technology security. It includes penetration testing, VPN configuration, network security audit checklist and privileged password management. Presenting Four Computer Security Processes Portrait PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Penetration Testing, Configuration, Password Management This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Computer Security Technology Evaluation Process Download PDF
This slide signifies the technical assessment process on company security. It steps include identify, analyse, prioritize and monitoring. Presenting computer security technology evaluation process download pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including identify, analyse, prioritize, monitoring. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Four Computer Security Threats Rules PDF
This slide shows the 4 threats to cyber security. It includes phishing attacks, cloud jacking, IoT devices and insider threats.Pitch your topic with ease and precision using this Four Computer Security Threats Rules PDF This layout presents information on Data Manipulation, Attacker Attempts, Sensitive Information It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Computer Security Ppt PowerPoint Presentation Complete Deck
Improve your presentation delivery using this Computer Security Ppt PowerPoint Presentation Complete Deck With Slides. Support your business vision and objectives using this well-structured PPT deck. This template offers a great starting point for delivering beautifully designed presentations on the topic of your choice. Comprising twelve this professionally designed template is all you need to host discussion and meetings with collaborators. Each slide is self-explanatory and equipped with high-quality graphics that can be adjusted to your needs. Therefore, you will face no difficulty in portraying your desired content using this PPT slideshow. This PowerPoint slideshow contains every important element that you need for a great pitch. It is not only editable but also available for immediate download and utilization. The color, font size, background, shapes everything can be modified to create your unique presentation layout. Therefore, download it now.

Cloud Computing Security Architecture Icon Slides PDF
Presenting Cloud Computing Security Architecture Icon Slides PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Cloud Computing, Security Architecture Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Desktop Security Management Compliance Dashboard Of Computer Security Graphics PDF
This slide depicts the cyber security compliance report on how data and hardware are monitored in different categories such as standard, regulation, and asset type control. Deliver an awe inspiring pitch with this creative desktop security management compliance dashboard of computer security graphics pdf bundle. Topics like compliance dashboard of computer security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Desktop Security Management Roadmap For Computer Security Training Graphics PDF
This slide depicts the cyber security training roadmap. It also shows the plan and guidelines to conduct an effective training program. Presenting desktop security management roadmap for computer security training graphics pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like information, security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Desktop Security Management Key Elements Of Computer Security Download PDF
This slide represents the different elements of cyber security such as application security, network security, information security, etc. This is a desktop security management key elements of computer security download pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like planning, information security, application security, network security, cloud security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Desktop Security Management Complete Computer Security Implementation Checklist Demonstration PDF
This slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. Presenting desktop security management complete computer security implementation checklist demonstration pdf to provide visual cues and insights. Share and navigate important information on twelve stages that need your due attention. This template can be used to pitch topics like technology, systems, organizations, information. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Desktop Security Management Latest Threats In Computer Security Inspiration PDF
This slide depicts the categories of recent threats that recently emerged in the United States, United Kingdom, and Australia in previous years. Presenting desktop security management latest threats in computer security inspiration pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like financial, information, systems. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Computer Security PowerPoint Templates And PowerPoint Themes 1012
Computer Security PowerPoint Templates And PowerPoint Themes 1012-With the move to high speed internet connection comes the greater possibility of your business being the target of an attack. One use of the term computer security refers to technology to implement a secure operating system. The Above Template will help you and your partners to understand the importance of Computer Security. Deliver amazing presentations to mesmerize your audience with our Security Template.-Computer Security PowerPoint Templates And PowerPoint Themes 1012-This PowerPoint template can be used for presentations relating to-Protect your computer, security, communication, computer, technology, background

Computer Security Ppt PowerPoint Presentation Complete Deck With Slides
This is a computer security ppt powerpoint presentation complete deck with slides. This is a one stage process. The stages in this process are computer security, business, planning, strategy, marketing.

Computer Security Vector Icon Ppt PowerPoint Presentation File Outline PDF
Presenting this set of slides with name computer security vector icon ppt powerpoint presentation file outline pdf. This is a three stage process. The stages in this process are computer security vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Thank You Computer Security Ppt PowerPoint Presentation Outline Guidelines
This is a thank you computer security ppt powerpoint presentation outline guidelines. This is a one stage process. The stages in this process are thank you.

Computer Security Business Ppt PowerPoint Presentation Layouts Background Cpb
Presenting this set of slides with name computer security business ppt powerpoint presentation layouts background cpb. This is an editable Powerpoint five stages graphic that deals with topics like computer security business to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Computer Security Ppt PowerPoint Presentation Layouts Format Ideas Cpb
Presenting this set of slides with name computer security ppt powerpoint presentation layouts format ideas cpb. This is an editable Powerpoint three stages graphic that deals with topics like computer security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Computer Security Plan Ppt PowerPoint Presentation Visual Aids Show Cpb
Presenting this set of slides with name computer security plan ppt powerpoint presentation visual aids show cpb. This is an editable Powerpoint four stages graphic that deals with topics like computer security plan to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Types Computer Security Ppt PowerPoint Presentation File Templates Cpb
Presenting this set of slides with name types computer security ppt powerpoint presentation file templates cpb. This is an editable Powerpoint four stages graphic that deals with topics like types computer security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Business Computer Security Ppt PowerPoint Presentation Slide Cpb
Presenting this set of slides with name business computer security ppt powerpoint presentation slide cpb. This is an editable Powerpoint five stages graphic that deals with topics like business computer security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Computer Security Attack Ppt PowerPoint Presentation File Templates Cpb Pdf
Presenting this set of slides with name computer security attack ppt powerpoint presentation file templates cpb pdf. This is an editable Powerpoint three stages graphic that deals with topics like computer security attack to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Computer Security Incident Handling Optimizing Cybersecurity Framework Roadmap Designs PDF
Presenting this set of slides with name computer security incident handling optimizing cybersecurity framework roadmap designs pdf. The topics discussed in these slides are implement enterprise security program, implement control environment, implement security processes. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Cybersecurity Maintenance Checklist Background PDF
Presenting this set of slides with name computer security incident handling cybersecurity maintenance checklist background pdf. The topics discussed in these slides are system monitoring real time, backup monitoring, preventive maintenance, virus scanning, security patches, executive reporting, review and planning meeting. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Determining Firm Current Capabilities Inspiration PDF
Presenting this set of slides with name computer security incident handling determining firm current capabilities inspiration pdf. The topics discussed in these slides are identify, protect, detect, response, recovery. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Cybersecurity Management Action Plan Graphics PDF
Presenting this set of slides with name computer security incident handling cybersecurity management action plan graphics pdf. The topics discussed in these slides are risk identification, risk treatment. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Cybersecurity Risk Management Worksheet Ideas PDF
Presenting this set of slides with name computer security incident handling cybersecurity risk management worksheet ideas pdf. The topics discussed in these slides are identified risk, risk likelihood, risk severity, implement controls, risk treatment, responsible person. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Dashboard Cyber Risk Management Download PDF
Presenting this set of slides with name computer security incident handling dashboard cyber risk management download pdf. The topics discussed in these slides are risk rating breakdown, risk heat map, action plan breakdown, risk analysis progress, response progress for risks. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Clustered Column Ppt Show Styles PDF
Presenting this set of slides with name computer security incident handling clustered column ppt show styles pdf. The topics discussed in these slides are product 1, product 2. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Dashboard Ppt Model Introduction PDF
Presenting this set of slides with name computer security incident handling dashboard ppt model introduction pdf. This is a three stage process. The stages in this process are minimum, medium, maximum. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Financial Ppt Portfolio Pictures PDF
Presenting this set of slides with name computer security incident handling financial ppt portfolio pictures pdf. This is a three stage process. The stages in this process are revenue, deposits, net income. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Our Mission Ppt Styles Slides PDF
Presenting this set of slides with name computer security incident handling our mission ppt styles slides pdf. This is a three stage process. The stages in this process are vision, mission, goal. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Our Team Ppt Model Files PDF
Presenting this set of slides with name computer security incident handling our team ppt model files pdf. This is a four stage process. The stages in this process are our team. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Thank You Ppt Summary Designs PDF
Presenting this set of slides with name computer security incident handling thank you ppt summary designs pdf. This is a one stage process. The stages in this process are thank you. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Essential Contingency Plan Strategies Ideas PDF
Presenting this set of slides with name computer security incident handling essential contingency plan strategies ideas pdf. The topics discussed in these slides are contingency considerations, contingency solutions. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Present Concerns Impeding Cybersecurity Formats PDF
Presenting this set of slides with name computer security incident handling present concerns impeding cybersecurity formats pdf. The topics discussed in these slides are reported financial losses due to increase in cybercrimes, data branches and records exposed. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Recovery Task List Maintenance Background PDF
Presenting this set of slides with name computer security incident handling recovery task list maintenance background pdf. The topics discussed in these slides are task no., task description, estimated time, actual time, assigned to, comments. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Timeframe For Incident Management Infographics PDF
Presenting this set of slides with name computer security incident handling timeframe for incident management infographics pdf. The topics discussed in these slides are incident logging, ticket creation, incident categorization, incident prioritization, incident resolution, incident closure. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Vital Records Maintenance Register Icons PDF
Presenting this set of slides with name computer security incident handling vital records maintenance register icons pdf. The topics discussed in these slides are primary location of records, alternate location of records, other sources to obtain records. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Multipoint Checklist To Improve Computer Security Guidelines PDF
This slide shows comprehensive checklist used to enhance information technology security. It includes email phishing training, anti virus and malware use, password changes etc. Showcasing this set of slides titled Multipoint Checklist To Improve Computer Security Guidelines PDF The topics addressed in these templates are Frequent System, Control Administrative, System Password All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
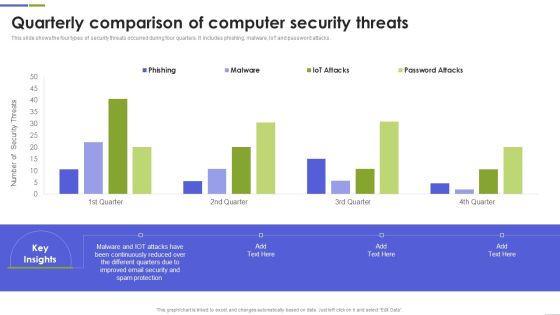
Quarterly Comparison Of Computer Security Threats Mockup PDF
This slide shows the four types of security threats occurred during four quarters. It includes phishing, malware, IoT and password attacks. Pitch your topic with ease and precision using this Quarterly Comparison Of Computer Security Threats Mockup PDF This layout presents information on Continuously Reduced, Different Quarters, Spam Protection It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Computer Security Incident Handling Agenda For Cybersecurity Management Slides PDF
Presenting this set of slides with name computer security incident handling agenda for cybersecurity management slides pdf. The topics discussed in these slides are determining roles and responsibilities of senior management and executives who are responsible in risk management, presenting optimize cybersecurity risk framework to senior management and executives. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Various Kpis To Measure Computer Security System Portrait PDF
This slide shows the different KPIs used to measure IT security system. These are level of preparedness, intrusion attempts, days to patch, incidents reported etc. Persuade your audience using this Various Kpis To Measure Computer Security System Portrait PDF This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Performance Indicators, Excepted Results, Actual Results Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Computer Security Dashboard With Incident And Threat Management Rules PDF
This slide shows the dashboard of cyber security with incidents and threat management. It includes overall progress, risk identified , number of critical incidents, initiative , incident and threat management etc.Showcasing this set of slides titled Computer Security Dashboard With Incident And Threat Management Rules PDF The topics addressed in these templates are Critical Incidents, Risks Identified, Compliance All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
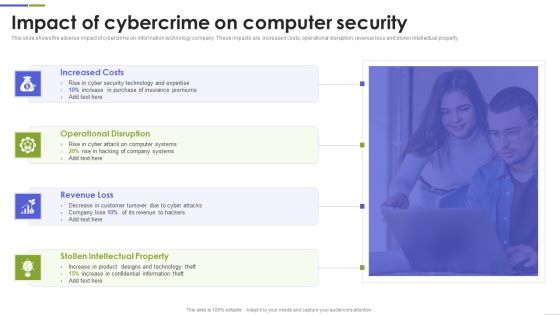
Impact Of Cybercrime On Computer Security Formats PDF
This slide shows the adverse impact of cybercrime on information technology company. These impacts are increased costs, operational disruption, revenue loss and stolen intellectual property. Persuade your audience using this Impact Of Cybercrime On Computer Security Formats PDF This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Increased Costs, Operational Disruption, Revenue Loss Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Technology Guide For Serverless Computing Cloud Computing Security Designs PDF
Presenting technology guide for serverless computing cloud computing security designs pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like security categories, security domains, security risks, security threats, security dimensions. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Various Strategies For Cloud Computing Security Brochure PDF
This slide shows strategies which can be used by organizations for cloud computing security. These strategies are end to end data encryption, secure data transfers, local data backups, etc. Showcasing this set of slides titled Various Strategies For Cloud Computing Security Brochure PDF. The topics addressed in these templates are Various Strategies, For Cloud, Computing Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Factors For Cloud Computing Security Assessment Ppt Gallery Deck PDF
Presenting Factors For Cloud Computing Security Assessment Ppt Gallery Deck PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Factors For, Cloud Computing, Security Assessment. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cloud Computing Security Management Ppt PowerPoint Presentation Outline Icons Cpb
Presenting this set of slides with name cloud computing security management ppt powerpoint presentation outline icons cpb. This is an editable Powerpoint four stages graphic that deals with topics like cloud computing security management to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
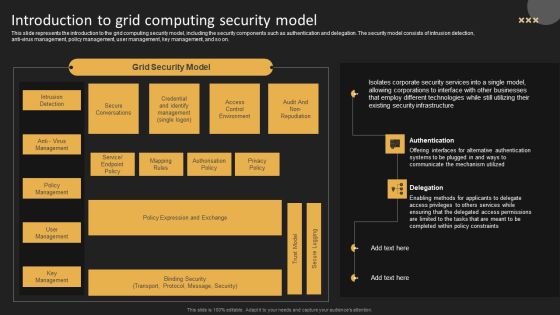
Introduction To Grid Computing Security Model Template PDF
This slide represents the introduction to the grid computing security model, including the security components such as authentication and delegation. The security model consists of intrusion detection, anti virus management, policy management, user management, key management, and so on. Get a simple yet stunning designed Introduction To Grid Computing Security Model Template PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Introduction To Grid Computing Security Model Template PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Cloud Computing Security Plan Quarterly Roadmap For Data Protection Brochure
We present our cloud computing security plan quarterly roadmap for data protection brochure. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched cloud computing security plan quarterly roadmap for data protection brochure in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Cloud Computing Security Five Years Roadmap With Deployment Plan Designs
We present our cloud computing security five years roadmap with deployment plan designs. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched cloud computing security five years roadmap with deployment plan designs in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Cloud Computing Security Ppt Portfolio Background Images PDF
Presenting cloud computing security ppt portfolio background images pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like security dimensions, customers, security categories. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Computing Security IT Icons Slide Ppt Inspiration Guidelines PDF
Introducing our well designed cloud computing security it icons slide ppt inspiration guidelines pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.

Timeline Cloud Computing Security IT Ppt Layouts Slide Portrait PDF
Presenting timeline cloud computing security it ppt layouts slide portrait pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like timeline, 2015 to 2021. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Financial Cloud Computing Security IT Ppt Slides Grid PDF
This is a financial cloud computing security it ppt slides grid pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like minimum, medium, maximum. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Computing Security Half Yearly Roadmap With Deployment Plan Guidelines
Presenting our innovatively structured cloud computing security half yearly roadmap with deployment plan guidelines Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

Cloud Computing Security Plan Quarterly Roadmap For IT Project Slides
Presenting our innovatively structured cloud computing security plan quarterly roadmap for it project slides Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

Cloud Computing Security Plan Quarterly Roadmap With Key Enablers Information
Introducing our cloud computing security plan quarterly roadmap with key enablers information. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

Cloud Computing Security Quarterly Roadmap With Deployment Plan Themes
Introducing our cloud computing security quarterly roadmap with deployment plan themes. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

Cloud Computing Security Architecture Shared Responsibilities Brochure PDF
The slide shows cloud security shared responsibilities for users and service providers. It includes client data protection and supervision, data and information security, application level security and platform and infrastructure security. Showcasing this set of slides titled Cloud Computing Security Architecture Shared Responsibilities Brochure PDF. The topics addressed in these templates are Client Data Protection, Data Information Security, Application Level Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Applications Of Confidential Computing Security Management Technology Sample PDF
The following slide contains the area of benefits where confidential computing is used to ensure data is secured and encrypted against malware attacks. Key uses are data protection, guard business process, collaboration and customer satisfaction. Presenting Applications Of Confidential Computing Security Management Technology Sample PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Data Protection, Guard Business Process, Collaboration, Customer Satisfaction. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cloud Computing Security Architecture Training Program Guidelines PDF
The slide shows a training schedule overview for cloud security. It includes training of identify and assess management, compute and configuration management, data protection and automation, networking and logging, compliance, incident response and penetration testing and cloud wars. Showcasing this set of slides titled Cloud Computing Security Architecture Training Program Guidelines PDF. The topics addressed in these templates are Identify Access Management, Compute Configuration Management, Data Protection Automation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cloud Computing Security Management Technology Framework Elements PDF
This slide illustrates a strategic framework for cloud security technology which is used in various aspects of data and network protection. Key components are disaster recovery, governance, monitoring, user access management, data security etc. Persuade your audience using this Cloud Computing Security Management Technology Framework Elements PDF. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including User Access Management, Data Security, Hardware And Software, Network Security, Monitoring, Governance. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cloud Computing Security Plan Quarterly Roadmap With Multiple Phases Download
Presenting the cloud computing security plan quarterly roadmap with multiple phases download. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Cloud Computing Security Six Months Roadmap With Deployment Plan Themes
Presenting the cloud computing security six months roadmap with deployment plan themes. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Cloud Computing Security Three Months Roadmap With Deployment Plan Introduction
Presenting our jaw dropping cloud computing security three months roadmap with deployment plan introduction. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.

Key Components Of Grid Computing Security Structure PDF
This slide talks about the security component of a grid computing network and how it protects the system by offering authentication and authorization processes. It also contains the OpenSSL deployment that permit users to execute operations within the grid. Welcome to our selection of the Key Components Of Grid Computing Security Structure PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

Cloud Computing Security Networking Ppt PowerPoint Presentation Complete Deck
If designing a presentation takes a lot of your time and resources and you are looking for a better alternative, then this cloud computing security networking ppt powerpoint presentation complete deck is the right fit for you. This is a prefabricated set that can help you deliver a great presentation on the topic. All the twelve slides included in this sample template can be used to present a birds-eye view of the topic. These slides are also fully editable, giving you enough freedom to add specific details to make this layout more suited to your business setting. Apart from the content, all other elements like color, design, theme are also replaceable and editable. This helps in designing a variety of presentations with a single layout. Not only this, you can use this PPT design in formats like PDF, PNG, and JPG once downloaded. Therefore, without any further ado, download and utilize this sample presentation as per your liking.

Desktop Security Management Elements Of Computer Security Application Security Download PDF
This is a desktop security management elements of computer security application security download pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like applications, information, security, customers, required. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Desktop Security Management Elements Of Computer Security Network Security Infographics PDF
This slide represents the network security element of cyber security and different network security methods such as firewalls, email security, web security, and antivirus software. Presenting desktop security management elements of computer security network security infographics pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like network, security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Desktop Security Management Elements Of Computer Security Operational Security Themes PDF
This slide defines the operational security element of cyber security. It also shows the best practices for operational security such as change management processes, deploys automation, etc. This is a desktop security management elements of computer security operational security themes pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like management, resources, require, security, plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Desktop Security Management Elements Of Computer Security Information Security Portrait PDF
This slide depicts the information security methodology and core information security principles such as confidentiality, integrity, and availability. Presenting desktop security management elements of computer security information security portrait pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like social media, information security, organization, network. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Desktop Security Management Elements Of Computer Security Cloud Security Diagrams PDF
This slide defines the cloud security element of cyber security and various threats that can breach cloud security, such as malware injection, malicious insiders, insecure APIs, etc. This is a desktop security management elements of computer security cloud security diagrams pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like applications, service. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Computer Cyber Security Icon Infographics PDF
Presenting Computer Cyber Security Icon Infographics PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Computer Cyber, Security Icon This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Desktop Security Management It Infrastructure Computer Security Budget For Fy2022 Slides PDF
This slide represents the budget for IT infrastructure after implementing cyber security, and it also shows the amount each task will cost the company. Deliver an awe inspiring pitch with this creative desktop security management it infrastructure computer security budget for fy2022 slides pdf bundle. Topics like it infrastructure computer security budget for fy2022 can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Computer Security Incident Handling Cyber Security Governance Ppt Gallery Summary PDF
Presenting this set of slides with name computer security incident handling cyber security governance ppt gallery summary pdf. The topics discussed in these slides are senior management, business strategy, security objectives, implementation, security requirements, risk management or information security strategy. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Impact Analysis Effective Security Management Graphics PDF
Presenting this set of slides with name computer security incident handling impact analysis effective security management graphics pdf. The topics discussed in these slides are no. of systems where security requirement not met, no. of access rights authorized, revoked, reset or changed. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Selecting Security Incident Management Software Graphics PDF
Presenting this set of slides with name computer security incident handling selecting security incident management software graphics pdf. The topics discussed in these slides are software, security incident forms, automated workflows, centralized platform, access rights, cost. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Role Of Management In Effective Information Security Governance Portrait PDF
Presenting this set of slides with name computer security incident handling role of management in effective information security governance portrait pdf. The topics discussed in these slides are strategic alignment, risk management, measuring performance, value delivery, managing resource, integration. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Desktop Security Management Timeline For The Implementation Of Computer Security Sample PDF
This slide shows the timeline for cyber security model implementation in an organization and the tasks to be performed every month. Deliver and pitch your topic in the best possible manner with this desktop security management timeline for the implementation of computer security sample pdf. Use them to share invaluable insights on security documentation, system and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Desktop Security Management Managing Computer Security 90 Days Plan Professional PDF
This slide depicts the 90 days plan of the cyber security model in an organization and training compliance and methods used for communication. Deliver an awe inspiring pitch with this creative desktop security management managing computer security 90 days plan professional pdf bundle. Topics like awareness, security, information, resources can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Desktop Security Management Managing Computer Security 30 Days Plan Designs PDF
This slide depicts how the cyber security model will work in the first 30 days and the tasks the organization should focus on. Deliver an awe inspiring pitch with this creative desktop security management managing computer security 30 days plan designs pdf bundle. Topics like awareness, measured, risk, security, team can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Desktop Security Management What Is Computer Security And How Does It Work Template PDF
This slide defines the meaning of cyber security and how it helps to prevent data through different methods and techniques. Deliver an awe inspiring pitch with this creative desktop security management what is computer security and how does it work template pdf bundle. Topics like networks, systems, protect data can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Desktop Security Management Computer Security Awareness Training For Staff Template PDF
This slide represents the cybersecurity awareness training program for staff, including the name of the participants and what modules would be covered under training daily. Deliver an awe inspiring pitch with this creative desktop security management computer security awareness training for staff template pdf bundle. Topics like project managers, developers, senior executives, security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Desktop Security Management How Is Automation Used In Computer Security Elements PDF
Presenting desktop security management how is automation used in computer security elements pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like threat detection, threat response, human augmentation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Desktop Security Management Cyber Threat Landscape In Computer Security Ideas PDF
This slide depicts the cyber threat landscape based on cybercriminal roles or actors and the impacts of successful cyberattacks on business. Deliver and pitch your topic in the best possible manner with this desktop security management cyber threat landscape in computer security ideas pdf. Use them to share invaluable insights on business disruption, strategic plans, financial, reputation damage and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Desktop Security Management Managing Computer Security 60 Days Plan Ideas PDF
This slide represents the plan for 60 days after implementing the cyber security model in the organization. This slide represents the plan for 60 days after implementing the cyber security model in the organization. Deliver and pitch your topic in the best possible manner with this desktop security management managing computer security 60 days plan ideas pdf. Use them to share invaluable insights on security, team, organization, awareness and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Desktop Security Management Elements Of Computer Security End User Education Background PDF
This slide shows the end user education within the cyber security model. It also represents various factors that effective training plans should involve. This is a desktop security management elements of computer security end user education background pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like system, opportunities, security, organization, measures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Desktop Security Management Elements Of Computer Security Disaster Recovery Planning Guidelines PDF
This slide depicts the disaster recovery plan in the cyber security model and what strategies an organization needs to adopt to recover from an attack or natural disaster. Presenting desktop security management elements of computer security disaster recovery planning guidelines pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security, resources, financial budget, strategies, plans. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Desktop Security Management What Are The Benefits Of Computer Security Icons PDF
This slide depicts the different benefits of deploying a cyber security model in an organization and how it can minimize the risk and save a companys time, money, and efforts. Presenting desktop security management what are the benefits of computer security icons pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like management, environment, potential, devices, security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Desktop Security Management Common Methods Used To Threaten Computer Security Template PDF
This slide depicts the standard methods used to threaten cyber security by cybercriminals or attackers. It also shows the reasons for these threats and preventions from these threats. This is a desktop security management common methods used to threaten computer security template pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like system, information, services, network, database. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Desktop Security Management Dashboard For Threat Tracking In Computer Security Guidelines PDF
This slide depicts the dashboard for threat tracking in cyber security by covering monthly threat status, current risk status, threat based on the role, threats by owners, risk by threats, and threat report. Deliver an awe inspiring pitch with this creative desktop security management dashboard for threat tracking in computer security guidelines pdf bundle. Topics like threats by owners, risk by threats can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Desktop Security Management Requirement Of Computer Security In Different Sectors Sample PDF
This slide depicts the requirement of cyber security in different sectors and the percentage of attacks experienced in the medical, govt, military, and corporate sectors in the past 12 months. Deliver and pitch your topic in the best possible manner with this desktop security management requirement of computer security in different sectors sample pdf. Use them to share invaluable insights on information, organizations, financial, servers, internet and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Distributed Computing Security Of Data And Networks In Edge Computing Ideas PDF
This slide represents the security of data and networks in edge computing. It also shows that data is secure because data is not traveling on any network however, edge devices are vulnerable.This is a Distributed Computing Security Of Data And Networks In Edge Computing Ideas PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Conduct Analytics, Devices Themselves, Vulnerability You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Computer Security With Lock And Tick Mark Sign Ppt PowerPoint Presentation File Portrait PDF
Presenting this set of slides with name computer security with lock and tick mark sign ppt powerpoint presentation file portrait pdf. This is a three stage process. The stages in this process are computer security with lock and tick mark sign. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Vector Showing Computer Security Threats Ppt PowerPoint Presentation Ideas Introduction PDF
Persuade your audience using this vector showing computer security threats ppt powerpoint presentation ideas introduction pdf. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including vector showing computer security threats. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Locked Laptop Computer Security Concept PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Locked Laptop Computer Security Concept PowerPoint Templates PPT Backgrounds For Slides 0113.Download and present our Computer PowerPoint Templates because It will get your audience in sync. Use our Technology PowerPoint Templates because You can Connect the dots. Fan expectations as the whole picture emerges. Present our Business PowerPoint Templates because You can Channelise the thoughts of your team with our PowerPoint Templates and Slides. Urge them to focus on the goals you have set. Present our Security PowerPoint Templates because It will Strengthen your hand with your thoughts. They have all the aces you need to win the day. Use our Services PowerPoint Templates because You will get more than you ever bargained for. Use these PowerPoint slides for presentations relating to Internet cyber laptop computer security lock, services, security, business, computer, technology. The prominent colors used in the PowerPoint template are Blue, Yellow, Gray. PowerPoint presentation experts tell us our Locked Laptop Computer Security Concept PowerPoint Templates PPT Backgrounds For Slides 0113 are second to none. People tell us our services PowerPoint templates and PPT Slides are aesthetically designed to attract attention. We guarantee that they will grab all the eyeballs you need. Presenters tell us our Locked Laptop Computer Security Concept PowerPoint Templates PPT Backgrounds For Slides 0113 will impress their bosses and teams. The feedback we get is that our laptop PowerPoint templates and PPT Slides will make the presenter look like a pro even if they are not computer savvy. Customers tell us our Locked Laptop Computer Security Concept PowerPoint Templates PPT Backgrounds For Slides 0113 are topically designed to provide an attractive backdrop to any subject. People tell us our security PowerPoint templates and PPT Slides effectively help you save your valuable time.

Computer Security Shield With Bug Vector Icon Ppt PowerPoint Presentation File Professional PDF
Presenting this set of slides with name computer security shield with bug vector icon ppt powerpoint presentation file professional pdf. This is a three stage process. The stages in this process are computer security shield with bug vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Risk Assessment Ppt PowerPoint Presentation Portfolio Layouts Cpb Pdf
Presenting this set of slides with name computer security risk assessment ppt powerpoint presentation portfolio layouts cpb pdf. This is an editable Powerpoint four stages graphic that deals with topics like computer security risk assessment to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Computer Security Incident Handling Backup Maintenance Selecting Offsite Storage Facility Vendor Guidelines PDF
Presenting this set of slides with name computer security incident handling backup maintenance selecting offsite storage facility vendor guidelines pdf. The topics discussed in these slides are geographic location, accessibility, security, cost, environment. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Determining Roles And Responsibilities For Risk Handling Mockup PDF
Presenting this set of slides with name computer security incident handling determining roles and responsibilities for risk handling mockup pdf. This is a four stage process. The stages in this process are chief risk officer, chief information security officer, senior management and executive, line management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Dashboard Incident Tracking Ppt Gallery Infographics PDF
Presenting this set of slides with name computer security incident handling dashboard incident tracking ppt gallery infographics pdf. The topics discussed in these slides are application whitelisting, patch applications, patch operating systems, restrict admin privileges, user application hardening, daily backup of important data. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Analyzing IT Department On Nist Cybersecurity Framework Introduction PDF
Presenting this set of slides with name computer security incident handling analyzing it department on nist cybersecurity framework introduction pdf. The topics discussed in these slides are identify, detect, protect, respond, recover. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Impact Analysis Implementing Cybersecurity Framework Designs PDF
Presenting this set of slides with name computer security incident handling impact analysis implementing cybersecurity framework designs pdf. The topics discussed in these slides are recover, detect, respond, protect, identify. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Threats Arrow Infographics Ppt PowerPoint Presentation Gallery Background PDF
Presenting this set of slides with name computer security threats arrow infographics ppt powerpoint presentation gallery background pdf. This is a three stage process. The stages in this process are external threats, internal threats. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Ppt PowerPoint Presentation Complete Deck With Slides
Presenting this set of slides with name computer security incident handling ppt powerpoint presentation complete deck with slides. The topics discussed in these slides are dashboard, management, cybersecurity, analysis, program. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Agenda For Cybersecurity Incident Management Template PDF
Presenting this set of slides with name computer security incident handling agenda for cybersecurity incident management template pdf. The topics discussed in these slides are department, priorities, maximum allowable downtime. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Amount Spent On Cyber Fraud Settlements Portrait PDF
Presenting this set of slides with name computer security incident handling amount spent on cyber fraud settlements portrait pdf. The topics discussed in these slides are settlements, amount, average. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Backup Maintenance Assessing Different Alternate Sites Infographics PDF
Presenting this set of slides with name computer security incident handling backup maintenance assessing different alternate sites infographics pdf. The topics discussed in these slides are implementation cost, hardware equipment requirement, telecommunication connection requirement, time to setup, location. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Backup Maintenance Developing Alternate Sites Slides PDF
Presenting this set of slides with name computer security incident handling backup maintenance developing alternate sites slides pdf. This is a five stage process. The stages in this process are cold sites, hot sites, warm sites, mobile site, mirrored site. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Backup Maintenance Recovery Budget Planning Professional PDF
Presenting this set of slides with name computer security incident handling backup maintenance recovery budget planning professional pdf. The topics discussed in these slides are vendor costs, hardware costs, software costs, testing costs, supply costs, labor or contractor costs. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Budget For Effective Cybersecurity Management Clipart PDF
Presenting this set of slides with name computer security incident handling budget for effective cybersecurity management clipart pdf. The topics discussed in these slides are functional area, software, implement duration, cost of implementation. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Cybersecurity Contingency Plan Business Impact Analysis Rules PDF
Presenting this set of slides with name computer security incident handling cybersecurity contingency plan business impact analysis rules pdf. The topics discussed in these slides are business processes, vital resources, impact, recovery priorities, max allowable outage time. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Cybersecurity Risk Management Action Plan Diagrams PDF
Presenting this set of slides with name computer security incident handling cybersecurity risk management action plan diagrams pdf. The topics discussed in these slides are potential risk, risk level, reason for risk rating, action, required resources, responsible person, duration, communication. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling 30 60 90 Days Plan Ppt File Templates PDF
Presenting this set of slides with name computer security incident handling 30 60 90 days plan ppt file templates pdf. This is a three stage process. The stages in this process are 30 60 90 days plan. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Business Impact Assessment Ppt Infographics Rules PDF
Presenting this set of slides with name computer security incident handling business impact assessment ppt infographics rules pdf. The topics discussed in these slides are strengths, weaknesses, loss impact. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Categorization Of Cyber Risks Ppt Gallery Template PDF
Presenting this set of slides with name computer security incident handling categorization of cyber risks ppt gallery template pdf. This is a five stage process. The stages in this process are low risk, medium risk, high risk, severe risk, extreme risk. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Risk Assessment Matrix Ppt Show Design Ideas PDF
Presenting this set of slides with name computer security incident handling risk assessment matrix ppt show design ideas pdf. This is a four stage process. The stages in this process are minor, significant, serious, catastrophic, insignificant. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Roadmap For Process Flow Ppt Professional Slide Portrait PDF
Presenting this set of slides with name computer security incident handling roadmap for process flow ppt professional slide portrait pdf. This is a six stage process. The stages in this process are roadmap, process flow. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

 Home
Home