AI PPT Maker
Templates
PPT Bundles
Design Services
Business PPTs
Business Plan
Management
Strategy
Introduction PPT
Roadmap
Self Introduction
Timelines
Process
Marketing
Agenda
Technology
Medical
Startup Business Plan
Cyber Security
Dashboards
SWOT
Proposals
Education
Pitch Deck
Digital Marketing
KPIs
Project Management
Product Management
Artificial Intelligence
Target Market
Communication
Supply Chain
Google Slides
Research Services
 One Pagers
One PagersAll Categories
-
Home
- Customer Favorites
- Caution
Caution

Problem Template 1 Ppt PowerPoint Presentation Template
This is a problem template 1 ppt powerpoint presentation template. This is a two stage process. The stages in this process are business, strategy, marketing, success, puzzle.

Problem Template 1 Ppt PowerPoint Presentation Visuals
This is a problem template 1 ppt powerpoint presentation visuals. This is a two stage process. The stages in this process are business, marketing, communication, planning, success.

The Problem Ppt PowerPoint Presentation Good
This is a the problem ppt powerpoint presentation good. This is a four stage process. The stages in this process are business, strategy, analysis, marketing.

The Problem Ppt PowerPoint Presentation Outline Background
This is a the problem ppt powerpoint presentation outline background. This is a four stage process. The stages in this process are icons, business, marketing, planning, process.
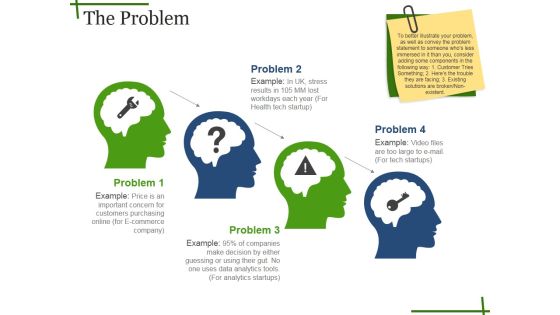
The Problem Ppt PowerPoint Presentation Outline Deck
This is a the problem ppt powerpoint presentation outline deck. This is a four stage process. The stages in this process are brain, tools, idea, marketing, strategy.

The Problem Ppt PowerPoint Presentation Layouts Ideas
This is a the problem ppt powerpoint presentation layouts ideas. This is a four stage process. The stages in this process are tools, brain, marketing, business, shapes.

The Problem Ppt PowerPoint Presentation Model Professional
This is a the problem ppt powerpoint presentation model professional. This is a four stage process. The stages in this process are business, marketing, strategy, icons, planning.

The Problem Ppt PowerPoint Presentation Layouts Layouts
This is a the problem ppt powerpoint presentation layouts layouts. This is a four stage process. The stages in this process are business, marketing, strategy, planning, maze.
Problem Statement Ppt PowerPoint Presentation Outline Designs
This is a problem statement ppt powerpoint presentation outline designs. This is a two stage process. The stages in this process are business, management, planning, strategy, marketing.

The Problem Ppt PowerPoint Presentation Pictures Skills
This is a the problem ppt powerpoint presentation pictures skills. This is a four stage process. The stages in this process are business, management, marketing.

The Problem Ppt PowerPoint Presentation Outline Ideas
This is a the problem ppt powerpoint presentation outline ideas. This is a one stage process. The stages in this process are thank you, word, greeting.
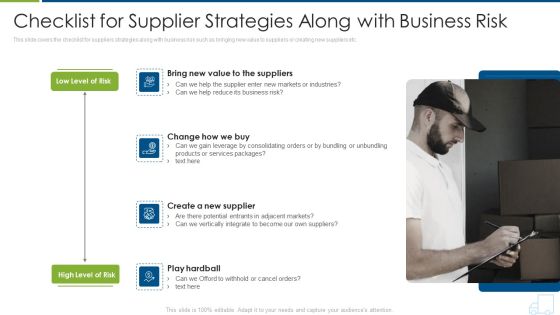
Distributor Strategy Checklist For Supplier Strategies Along With Business Risk Topics PDF
This slide covers the checklist for suppliers strategies along with business risk such as bringing new value to suppliers or creating new suppliers etc. Presenting distributor strategy checklist for supplier strategies along with business risk topics pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like business risk, industries, services, products, potential. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Assessing Startup Company Value Risk Related To Wrong Valuation Of The Startup Company Brochure PDF
This slides shows the risks which are related to wrong valuation includes too high valuation, too low valuation with their description, etc. This is a assessing startup company value risk related to wrong valuation of the startup company brochure pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like risk related to wrong valuation of the startup company. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
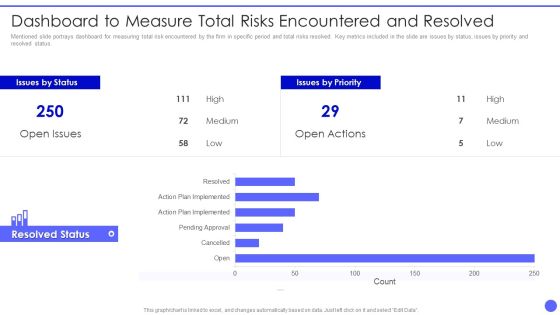
Info Safety And ISO 27001 Dashboard To Measure Total Risks Encountered Slides PDF
Mentioned slide portrays dashboard for measuring total risk encountered by the firm in specific period and total risks resolved. Key metrics included in the slide are issues by status, issues by priority and resolved status. Deliver an awe inspiring pitch with this creative Info Safety And ISO 27001 Dashboard To Measure Total Risks Encountered Slides PDF bundle. Topics like Issues by Status, Resolved Status, High, Medium, Low can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Quarterly Budget Analysis Of Business Organization Risks Faced By Organization In Outsourcing Clipart PDF
The following slide provides information regarding the key risks faced by organization in outsourcing marketing activities to a digital agency. The major risks are loss of control, hidden charges, poor customer focus, exposing confidential data, poor communication and brand identity dilution.Presenting Quarterly Budget Analysis Of Business Organization Risks Faced By Organization In Outsourcing Clipart PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Poor Customer Focus, Exposing Confidential Data, Poor Communication In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
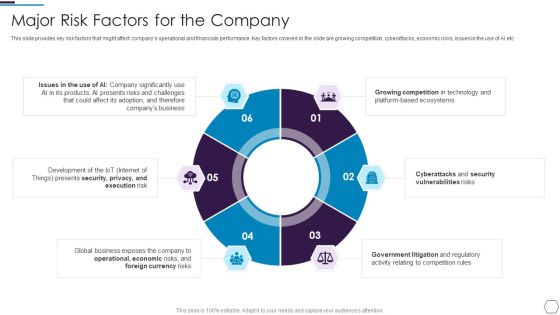
Information Technology Firm Report Example Major Risk Factors For The Company Template PDF
This slide provides key risk factors that might affect companys operational and financials performance. Key factors covered in the slide are growing competition, cyberattacks, economic risks, issues in the use of AI etc.Presenting Information Technology Firm Report Example Major Risk Factors For The Company Template PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Growing Competition, Cyberattacks Vulnerabilities, Operational Economic In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
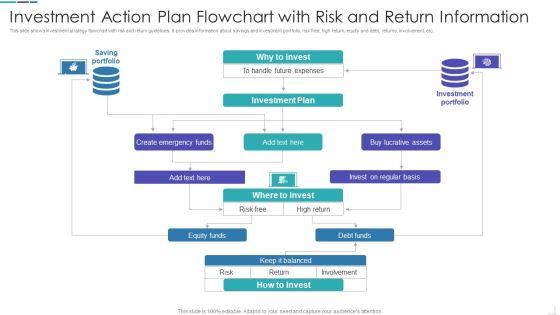
Investment Action Plan Flowchart With Risk And Return Information Microsoft PDF
This slide shows investment strategy flowchart with risk and return guidelines. It provides information about savings and investment portfolio, risk free, high return, equity and debt, returns, involvement, etc.Pitch your topic with ease and precision using this Investment Action Plan Flowchart With Risk And Return Information Microsoft PDF This layout presents information on Investment Plan, Lucrative Assets, Keep It Balanced It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Possible Risk Post Industry 4 0 Implementation In Food Manufacturing Sector Designs PDF
The purpose of this slide is to showcase the possible risks associated with implementation of industry 4.0 in food manufacturing sector. It also contains details of impact of each risk along with the corresponding mitigation strategies.Presenting Possible Risk Post Industry 4 0 Implementation In Food Manufacturing Sector Designs PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Legislation And Standardization, Technical Skills, Data Growth Rate. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Determining The Various Risk Faced By The Real Estate Investors Professional PDF
The following slide exhibits different type of risks which are faced by the real estate investors. This PowerPoint presentation covers information about the market, property, liquidity and credit debt risk. Presenting Determining The Various Risk Faced By The Real Estate Investors Professional PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Upcoming Recession, Mostly Investors, Property Lower. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Effective Company Event Communication Tactics Types Of Risks Associated With Upcoming Event Designs PDF
This slide covers various kinds of risks that can take place at upcoming events. It includes risk categories such as safety, weather, external forces, staffing, event site, ethics, and images. Presenting Effective Company Event Communication Tactics Types Of Risks Associated With Upcoming Event Designs PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Ethics Image, External Forces, Equipment Handling. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Strategical And Tactical Planning Different Levels Of Integration In Risk And Strategic Thinking Icons PDF
This template covers strategic thinking process with risk integration such as risk input into the business process, joint scenario modeling, business P and L and balance sheet simulation. Presenting Strategical And Tactical Planning Different Levels Of Integration In Risk And Strategic Thinking Icons PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Business Process, Joint Scenario Modeling, Intermediate. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Data Lake Development With Azure Cloud Software Risks Associated With Data Lake Usage Slides PDF
This slide depicts the risks of using data lake such as the higher risk involved in data lake construction, storage and computing expenses, complex tools, and so on. Presenting Data Lake Development With Azure Cloud Software Risks Associated With Data Lake Usage Slides PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Prior Analysts, Opportunity, Computing Expenses. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Assessing Risks With Gap Analysis Example Background Designs
This is a assessing risks with gap analysis example background designs. This is a five stage process. The stages in this process are evaluate effectiveness, establish a context for analysis, analyze risk, identify model potential threats, determine risk treatment, threat identification, diagram of flow.
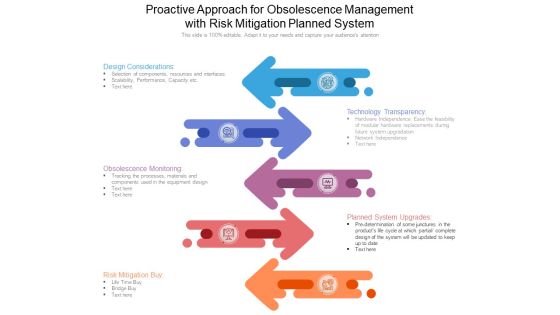
Proactive Approach For Obsolescence Management With Risk Mitigation Planned System Ppt PowerPoint Presentation Professional File Formats PDF
Presenting proactive approach for obsolescence management with risk mitigation planned system ppt powerpoint presentation professional file formats pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including design considerations, technology transparency, obsolescence monitoring, planned system upgrades, risk mitigation buy. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
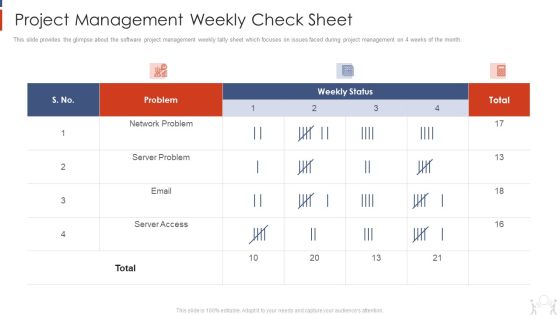
Project Management Modelling Techniques IT Project Management Weekly Check Sheet Inspiration PDF
This slide provides the glimpse about the software project management weekly tally sheet which focuses on issues faced during project management on 4 weeks of the month. Deliver and pitch your topic in the best possible manner with this project management modelling techniques it project management weekly check sheet inspiration pdf. Use them to share invaluable insights on network problem, server problem, server access and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Quarterly Information Technology Security Roadmap For Continuous Threat Analysis Download
Presenting the quarterly information technology security roadmap for continuous threat analysis download. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
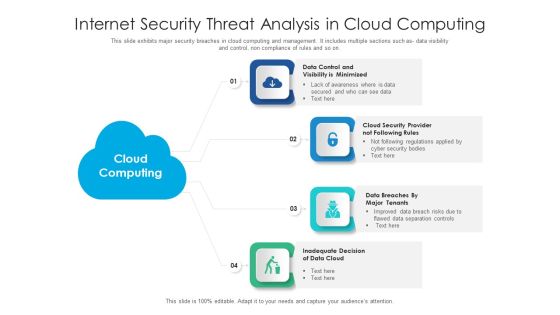
Internet Security Threat Analysis In Cloud Computing Information PDF
This slide exhibits major security breaches in cloud computing and management. It includes multiple sections such as- data visibility and control, non compliance of rules and so on. Presenting internet security threat analysis in cloud computing information pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including data cloud, cloud security, data control. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Internet Security Threat Analysis Process By Backdoor Graphics PDF
This slide exhibits data and security breach attack process conducted by hackers to get access to company data. It includes multiple activities such as link forwarding by emails, data sharing and attacking and so on. Showcasing this set of slides titled internet security threat analysis process by backdoor graphics pdf. The topics addressed in these templates are exfiltrate, stage attack, research. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Mitigation Tactics To Prevent Internet Security Threats Formats PDF
This side exhibits mitigation strategies to prevent security breach incidents. It includes multiple actions such as keeping track of all personal assets, analyzing logging process security and so on. Presenting mitigation tactics to prevent internet security threats formats pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including communication management, monitoring and alerting, logging, visibility. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
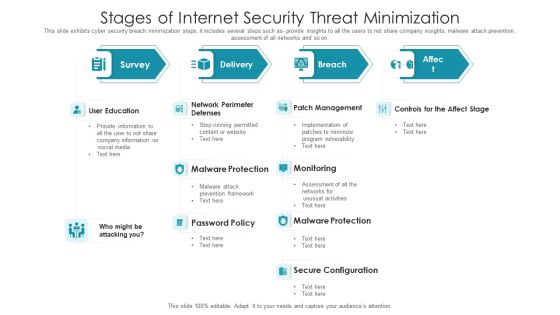
Stages Of Internet Security Threat Minimization Summary PDF
This slide exhibits cyber security breach minimization steps, it includes several steps such as- provide insights to all the users to not share company insights, malware attack prevention, assessment of all networks and so on. Pitch your topic with ease and precision using this stages of internet security threat minimization summary pdf. This layout presents information on patch management, monitoring, malware protection, secure configuration, user education. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

How To Intensify Project Threats Project Closure Report Mockup PDF
This slide provides the glimpse about the final step of issue and escalation process which covers the project closure report along with the details such as project information, benefits, key metrics, project deliverables, controls in place, shortfalls, etc. This is a how to intensify project threats project closure report mockup pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like project information, benefits, key metrics, project deliverables, controls in place, shortfalls. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

How To Intensify Project Threats Hierarchical Escalation Process Summary PDF
This slide provides the glimpse about the hierarchical escalation along with the hierarchy structure and meaning of such an escalation. This is a how to intensify project threats hierarchical escalation process summary pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like developer, service, hierarchical, organization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

How To Intensify Project Threats Functional Escalation Process Rules PDF
This slide provides the glimpse about the functional escalation along with the functional structure and meaning of such an escalation. This is a how to intensify project threats functional escalation process rules pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like developer, service, functional escalation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

How To Intensify Project Threats Project Closure Checklist Clipart PDF
This slide provides the glimpse about the final step of issue and escalation process which covers the project checklist which covers the various steps which must be focused on by the company. Presenting how to intensify project threats project closure checklist clipart pdf to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like project closure checklist. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Mitigating Cybersecurity Threats And Vulnerabilities Addressing Asset Security Elements PDF
This slide provides details regarding asset security categorization on certain parameters such as ownership, location, confidentiality, integrity and availability. This is a mitigating cybersecurity threats and vulnerabilities addressing asset security elements pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like ownership, location, integrity, security categorization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Mitigating Cybersecurity Threats And Vulnerabilities Determine Staff Training Rules PDF
The employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. This is a mitigating cybersecurity threats and vulnerabilities determine staff training rules pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like advanced software training, advanced skills training, training module. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Mitigating Cybersecurity Threats And Vulnerabilities Ensuring Vital Records Inspiration PDF
This slide provides information regarding vital record maintenance in order to store crucial information and the location where these records are kept also details about the alternate backup location of the records and the other sources through which records can be retrieved. This is a mitigating cybersecurity threats and vulnerabilities ensuring vital records inspiration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like ensuring vital records maintenance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Mitigating Cybersecurity Threats And Vulnerabilities Incident Reporting Themes PDF
This slide will help in providing an overview of the various reported incidents, average cost per incident and number of people involved in the various incidents across different departments. Presenting mitigating cybersecurity threats and vulnerabilities incident reporting themes pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like incident reporting by different departments. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
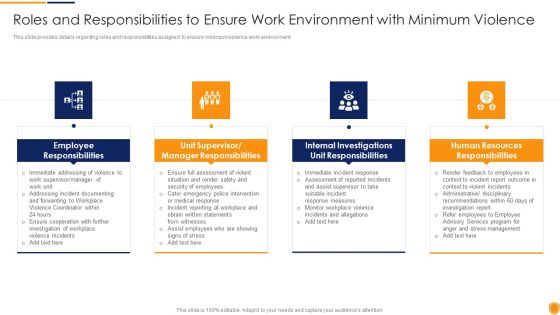
Mitigating Cybersecurity Threats And Vulnerabilities Roles And Responsibilities Introduction PDF
This slide provides details regarding roles and responsibilities assigned to ensure minimum violence work environment. This is a mitigating cybersecurity threats and vulnerabilities roles and responsibilities introduction pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employee responsibilities, manager responsibilities, unit responsibilities, human resources responsibilities. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Mitigating Cybersecurity Threats And Vulnerabilities Workplace Employee Rules PDF
The employee assistance program will help firm in enhancing their well being at workplace and enable them to handle critical situations. This program will render services like clinical services, work and life services and employer services, etc. Presenting mitigating cybersecurity threats and vulnerabilities workplace employee rules pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like clinical services, work and life services, employer services. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
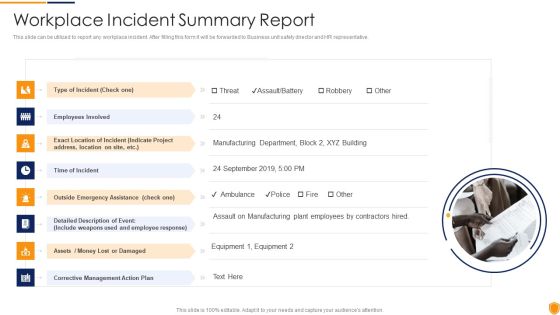
Mitigating Cybersecurity Threats And Vulnerabilities Workplace Incident Summary PDF
This slide can be utilized to report any workplace incident. After filling this form it will be forwarded to Business unit safety director and HR representative. This is a mitigating cybersecurity threats and vulnerabilities workplace incident summary pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like type of incident, time of incident, corrective management action plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
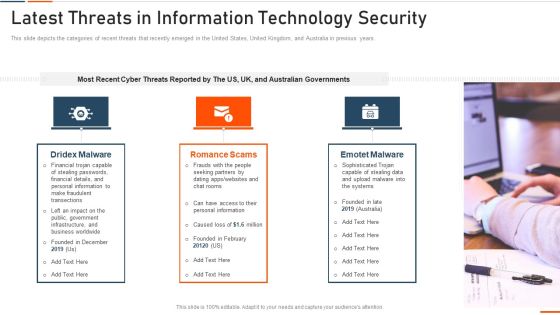
Latest Threats In Information Technology Security Ppt Pictures Designs PDF
This slide represents the different elements of Network security such as application security, network security, information security, etc. This is a latest threats in information technology security ppt pictures designs pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like network security, cloud security, application security, operational security, information security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Threat Management At Workplace Ensuring Vital Records Maintenance Demonstration Pdf
This slide provides information regarding vital record maintenance in order to store crucial information and the location where these records are kept also details about the alternate backup location of the records and the other sources through which records can be retrieved. Deliver and pitch your topic in the best possible manner with this threat management at workplace ensuring vital records maintenance demonstration pdf. Use them to share invaluable insights on primary location of records, scanned images on network drive other parties, department file cabinets and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Threat Management At Workplace Employee Assistance Program Demonstration PDF
The employee assistance program will help firm in enhancing their well being at workplace and enable them to handle critical situations. This program will render services like clinical services, work and life services and employer services, etc. Deliver and pitch your topic in the best possible manner with this threat management at workplace employee assistance program demonstration pdf. Use them to share invaluable insights on clinical services, work and life services, employer services and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
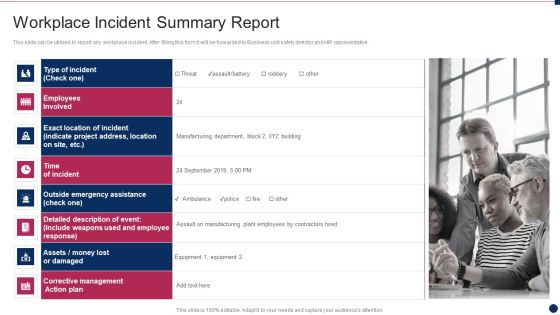
Threat Management At Workplace Incident Summary Report Ideas PDF
This slide can be utilized to report any workplace incident. After filling this form it will be forwarded to Business unit safety director and HR representative. Presenting threat management at workplace incident summary report ideas pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like time of incident, corrective management action plan, exact location of incident. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
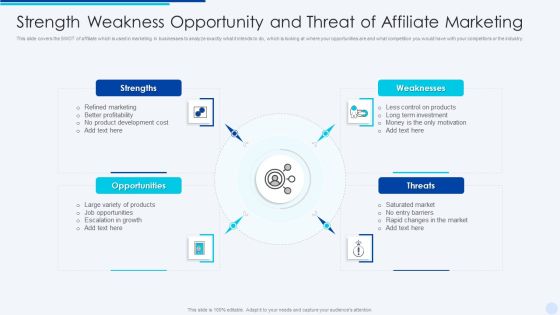
Strength Weakness Opportunity And Threat Of Affiliate Marketing Sample PDF
This slide covers the SWOT of affiliate which is used in marketing in businesses to analyze exactly what it intends to do, which is looking at where your opportunities are and what competition you would have with your competitors or the industry. Persuade your audience using this Strength Weakness Opportunity And Threat Of Affiliate Marketing Sample PDF This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Weaknesses, Opportunities, Strengths Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Supply Chain Strength Weakness Opportunity Threat Analysis Rules PDF
This slide showcases the SWOT analysis of the supply chain of n organization to provide better customer experience and deliver the goods at a fast pace. Persuade your audience using this Supply Chain Strength Weakness Opportunity Threat Analysis Rules PDF This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Opportunities, Weaknesses, Strengths Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cloud Security Assessment Cloud Security Threats Shared Vulnerabilities Icons PDF
This slide describes how organizations and providers share vulnerabilities of a system, so each party must take precautions to protect data.This is a Cloud Security Assessment Cloud Security Threats Shared Vulnerabilities Icons PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Standards, Authorization Restrictions, Providers Already. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Business Disaster Threat Cause Pie Chart Ppt Pictures Gallery PDF
The given below slide showcases the major causes of business disasters to assess and formulate recovery plan accordingly. It mainly includes software failure, data sabotage, ransomware, human error, hardware failure etc. Showcasing this set of slides titled Business Disaster Threat Cause Pie Chart Ppt Pictures Gallery PDF. The topics addressed in these templates are Key Insights, Few Possible Solutions, Implement Data Backup. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Data Breach Threats Process Flow Model Ppt Model Maker PDF
This slide covers process of data breach in an organisation. It includes steps such as researching weak points, staging attack and exfiltration of data resulting it to data breach in an organisation. Persuade your audience using this Data Breach Threats Process Flow Model Ppt Model Maker PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Research, Stage Attack, Exfiltrate, Social Engineering. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Strengths Weakness Opportunities And Threat Prioritization Structure Template PDF
The following slide presents the SWOT analysis of an organization to evaluate current status and form new strategies. It includes some activities and each activity given a plus point and post that total is evaluated. Pitch your topic with ease and precision using this Strengths Weakness Opportunities And Threat Prioritization Structure Template PDF. This layout presents information on Market Awareness, Opportunities, Organic Growth. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Ready To Eat Food Market Analysis Kellogg Threats Guidelines PDF
Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Ready To Eat Food Market Analysis Kellogg Threats Guidelines PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Effective Security Operations Tools To Prevent Cyber Threats Formats PDF
This slide includes some SecOps tools that provide a more secure working environment to organisations by improving collaboration between operations and security teams. It includes elements such as tools, pricing, features, rating, free version, and free trial. Pitch your topic with ease and precision using this Effective Security Operations Tools To Prevent Cyber Threats Formats PDF. This layout presents information on Develops, Organization Security, Compliance Requirements. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Smart Phone Security Tools For Preventing Threats Topics PDF
This slide shows latest security tools for managing phone security model. The purpose of this slide is to highlight various tools names with description for selecting most suitable tool. It include tools such as data loss prevention, identify and access management, etc. Presenting Smart Phone Security Tools For Preventing Threats Topics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Data Loss Prevention, Identity Access Management, Security Event Management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Blockchain Technology Applications For Cyber Threat Prevention Icons PDF
This slides represents various application of blockchain technology in enhancing cyber safety which helps to speed up data transfer procedures, offer secure transactions, and lower compliance expenses. Key components are IoT security, secure private messaging, etc. Presenting Blockchain Technology Applications For Cyber Threat Prevention Icons PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Prevention, Infrastructure, System . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cloud Computing Cyber Threat Prevention Flowchart Slides PDF
The below slide provides a cloud security framework which encourages security companies to clarify the roles played by the various cloud security stakeholders within their organization and enhance overall security compliance. Major stages are visibility, governance, resolve violation, etc. Showcasing this set of slides titled Cloud Computing Cyber Threat Prevention Flowchart Slides PDF. The topics addressed in these templates are Visibility, Governance, Resolve Violations. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Iot Security Technology For Cyber Threat Prevention Clipart PDF
This slide highlights multiple uses of IoT security technology which helps business to enhance cyber safety of their connected devices. The major elements are device connection, data sensing, communication, data analytics, data value and human value. Persuade your audience using this Iot Security Technology For Cyber Threat Prevention Clipart PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Human Value, Data Value, Data Analytics. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

IT Cyber Threat Prevention Technology Market Topics PDF
This slide provides the statistical data for IT security software user market to help business and organizations enhance process efficiency. Major security technology are authentication, IoT, Zero trust, Cloud, application security, etc. Pitch your topic with ease and precision using this IT Cyber Threat Prevention Technology Market Topics PDF. This layout presents information on Key Insights, Progressive Rate, Technology. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Multi Step Strategy To Implement Cyber Threat Prevention Guidelines PDF
The following slide provides a step by step strategy to monitor and reassess your organizations cybersecurity maturity which helps to strengthen the cyber safety. The process involves understand, assess, determine and document. Persuade your audience using this Multi Step Strategy To Implement Cyber Threat Prevention Guidelines PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Determine, Document, Assess. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Multiple Challenges Of Business Cyber Threat Prevention Sample PDF
The following slide represent the statistical data of various cyber safety challenges reported by business and organizations which helps to determine the most vulnerable one. Major areas are information security, business agility, automation, integration, etc. Showcasing this set of slides titled Multiple Challenges Of Business Cyber Threat Prevention Sample PDF. The topics addressed in these templates are Key Takeaways, Cyber Safety, Prevention. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
