AI PPT Maker
Templates
PPT Bundles
Design Services
Business PPTs
Business Plan
Management
Strategy
Introduction PPT
Roadmap
Self Introduction
Timelines
Process
Marketing
Agenda
Technology
Medical
Startup Business Plan
Cyber Security
Dashboards
SWOT
Proposals
Education
Pitch Deck
Digital Marketing
KPIs
Project Management
Product Management
Artificial Intelligence
Target Market
Communication
Supply Chain
Google Slides
Research Services
 One Pagers
One PagersAll Categories
-
Home
- Customer Favorites
- Business Risks
Business Risks
Password Protection For Cyber Security Threat Ppt PowerPoint Presentation Icon Show PDF
Persuade your audience using this password protection for cyber security threat ppt powerpoint presentation icon show pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including password protection for cyber security threat. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Vector Showing Computer Security Threats Ppt PowerPoint Presentation Ideas Introduction PDF
Persuade your audience using this vector showing computer security threats ppt powerpoint presentation ideas introduction pdf. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including vector showing computer security threats. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Network And Information Threat Safety Vector Icon Ppt PowerPoint Presentation File Example PDF
Persuade your audience using this network and information threat safety vector icon ppt powerpoint presentation file example pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including network and information threat safety vector icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Functional Process Icon With Threat Sign Ppt PowerPoint Presentation Icon Files PDF
Persuade your audience using this functional process icon with threat sign ppt powerpoint presentation icon files pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including functional process icon with threat sign. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Project Management Threat List Vector Icon Ppt PowerPoint Presentation File Microsoft PDF
Persuade your audience using this project management threat list vector icon ppt powerpoint presentation file microsoft pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including project management threat list vector icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
System Failure With Threat Symbol On Screen Icon Ppt PowerPoint Presentation Gallery Templates PDF
Persuade your audience using this system failure with threat symbol on screen icon ppt powerpoint presentation gallery templates pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including system failure with threat symbol on screen icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Employee Configuring Cloud Technology System For Eliminating Threats Ppt PowerPoint Presentation File Diagrams PDF
Persuade your audience using this employee configuring cloud technology system for eliminating threats ppt powerpoint presentation file diagrams pdf. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including employee configuring cloud technology system for eliminating threats. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Software Engineer Creating Cloud Computing Structure For Reducing Operational Threats Ppt PowerPoint Presentation File Skills PDF
Persuade your audience using this software engineer creating cloud computing structure for reducing operational threats ppt powerpoint presentation file skills pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including software engineer creating cloud computing structure for reducing operational threats. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

SWOT Analysis Threats Example Presentation For Job Interview Ppt Gallery Styles PDF
Presenting swot analysis threats example presentation for job interview ppt gallery styles pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like strengths, weaknesses, opportunities, threats. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Circle Procedure Infographic To Manage Threat Detection And Response Ppt Styles Sample PDF
Persuade your audience using this circle procedure infographic to manage threat detection and response ppt styles sample pdf. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including circle procedure infographic to manage threat detection and response. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Agenda Of Handling Cyber Threats In A Digital Era Ppt Infographics Objects PDF
This is a agenda of handling cyber threats in a digital era ppt infographics objects pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like agenda of handling cyber threats in a digital era. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
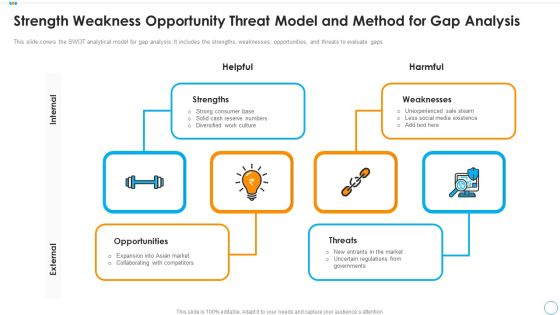
Strength Weakness Opportunity Threat Model And Method For Gap Analysis Designs PDF
This slide covers the SWOT analytical model for gap analysis. It includes the strengths, weaknesses, opportunities, and threats to evaluate gaps. Presenting strength weakness opportunity threat model and method for gap analysis designs pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including strengths, opportunities, weaknesses. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
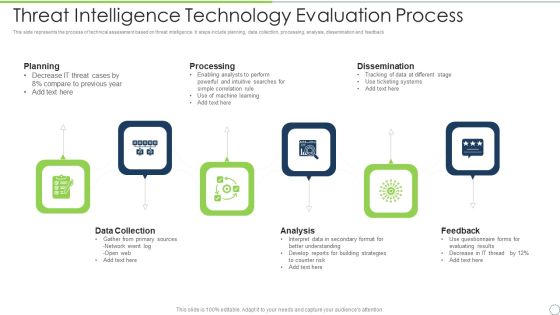
Threat Intelligence Technology Evaluation Process Ppt PowerPoint Presentation File Shapes PDF
This slide represents the process of technical assessment based on threat intelligence. It steps include planning, data collection, processing, analysis, dissemination and feedback. Presenting threat intelligence technology evaluation process ppt powerpoint presentation file shapes pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including planning, processing, dissemination, feedback, analysis, data collection. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Insider Threat In Cyber Security Detection And Prevention Framework Information PDF
This slide shows insider threat prevention and detection framework. It contains information user characteristics, attack status, vulnerability, personality, past record, motivation behind attack, etc. Presenting Insider Threat In Cyber Security Detection And Prevention Framework Information PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Actor Characteristic, Attack Characteristic, Organisation Characteristic. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Major Indicators Of Cybersecurity Insider Threat In Cyber Security Microsoft PDF
This slide shows major indicators of cybersecurity insider threat along with mitigation strategies. It contains information about behavioral, information technology IT sabotage and data theft. Presenting Major Indicators Of Cybersecurity Insider Threat In Cyber Security Microsoft PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Behavioral, IT Sabotage, Data Theft. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Threats Management Of Confidential Data Reports Icon Ppt Ideas Summary PDF
Persuade your audience using this Threats Management Of Confidential Data Reports Icon Ppt Ideas Summary PDF. This PPT design covers two stages, thus making it a great tool to use. It also caters to a variety of topics including Threats Management, Confidential Data Reports, Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Strengths Weaknesses Opportunities And Threats Analysis Of Automotive Industry Elements PDF
This slide covers the strategies that are been developed by doing the SWOT strengths, weakness, opportunities and threats analysis of an organization to help the managers or owners to make decisions accordingly.Persuade your audience using this Strengths Weaknesses Opportunities And Threats Analysis Of Automotive Industry Elements PDF This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Ineffective Marketing, Unable To Establish, Large Diversified Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cloud Information Security Cloud Security Threats Loss Of Data Ppt Layouts Example PDF
This slide represents the data loss threat of cloud security, it is essential to secure organization data and create backups. Presenting Cloud Information Security Cloud Security Threats Loss Of Data Ppt Layouts Example PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Provider Wisely, Procedures Strategies, Storage Locations. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Assessment Cloud Security Threats Loss Of Data Topics PDF
This slide represents the data loss threat of cloud security it is essential to secure organization data and create backups.Presenting Cloud Security Assessment Cloud Security Threats Loss Of Data Topics PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Storage Locations, Natural Disasters, Massive Impact. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Some Data Security Measures To Overcome Cybersecurity Threats By ABS Healthcare Company Introduction PDF
The slide shows some measures that can be adopted by the company in order to ensure data protection and restrict access such Get Customized security programs, Inculcate organizations with healthcare threat intelligence softwares, get updated with latest security management softwares, ensure insider Threat protection etc. This is a some data security measures to overcome cybersecurity threats by ABS healthcare company introduction pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like restrict data accessibility, programs and firewall softwares, security management, techniques and provide. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Opportunities And Threats For Penetrating In New Market Segments Sales Strategy Initiatives And Budget Sample PDF
Presenting opportunities and threats for penetrating in new market segments sales strategy initiatives and budget sample pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like tele marketing, online advertising, trade fairs, telemarketing, canvassing. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Collective Equity Funding Pitch Deck Problem Solution And Outcome Topics PDF
The slide provides the problem pain point of customers, solutions unique features and highlights of the product and outcome final result for the customers. This is a collective equity funding pitch deck problem solution and outcome topics pdf. template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like solution, business, problem, outcome. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Series Of Cyber Security Attacks Against Ukraine 2022 Threat Actors Supporting Russia And Ukraine Inspiration PDF
This slide shows the threat actors supporting russia and ukraine, such as hacker organization anonymous, cyber partisan hacking organization, and conti ransomware gang. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Series Of Cyber Security Attacks Against Ukraine 2022 Threat Actors Supporting Russia And Ukraine Inspiration PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
Agenda For Solution Evaluation Criteria Assessment And Threat Impact Matrix Summary PDF
This is a agenda for solution evaluation criteria assessment and threat impact matrix summary pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like analyze, determine, organization, value, severity matrix. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Various Ways To Manage Project Safety By Managing Threats Contd Ppt Styles Diagrams PDF
This slide provides information regarding various ways to handle threats to ensure project safety in terms of active remediation implementation, deactivating orphaned user accounts, etc. Presenting various ways to manage project safety by managing threats contd ppt styles diagrams pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like management, systems, service, resources, techniques. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
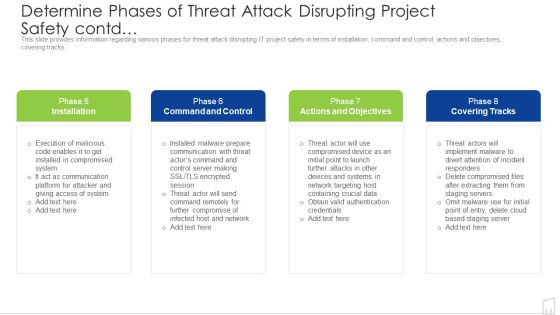
Determine Phases Of Threat Attack Disrupting Project Safety Contd Ppt Inspiration Summary PDF
This slide provides information regarding various phases for threat attack disrupting IT project safety in terms of installation, command and control, actions and objectives, covering tracks. This is a determine phases of threat attack disrupting project safety contd ppt inspiration summary pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like communication, network, data, server. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Strategies Envr Onmental Operational Challenges Pharmaceutical Company Swot Analysis Threats Graphics PDF
This slide shows the various threats related to pharmaceutical company such as high level of competition, suppliers, regulations on international trade and many more. Presenting strategies envr onmental operational challenges pharmaceutical company swot analysis threats graphics pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like high competition, regulations on international trade, suppliers. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Project Security Administration IT Various Ways To Manage Project Safety By Managing Threats Contd Sample PDF
This slide provides information regarding various ways to handle threats to ensure project safety in terms of active remediation implementation, deactivating orphaned user accounts, etc. This is a project security administration it various ways to manage project safety by managing threats contd sample pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like deactivate orphaned user accounts, develop strict access management policies, implement active remediation, investigate remote access policies. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
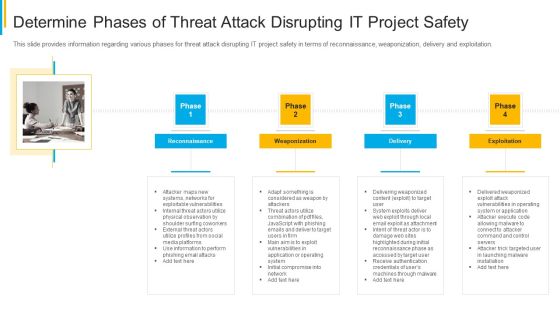
Project Security Administration IT Determine Phases Of Threat Attack Disrupting IT Project Safety Brochure PDF
This slide provides information regarding various phases for threat attack disrupting IT project safety in terms of reconnaissance, weaponization, delivery and exploitation. This is a project security administration it determine phases of threat attack disrupting it project safety brochure pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like reconnaissance, weaponization, delivery, exploitation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Project Security Administration IT Determine Phases Of Threat Attack Disrupting Project Safety Contd Icons PDF
This slide provides information regarding various phases for threat attack disrupting IT project safety in terms of installation, command and control, actions and objectives, covering tracks. Presenting project security administration it determine phases of threat attack disrupting project safety contd icons pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like installation, command and control, actions and objectives, covering tracks. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Upgrading Total Project Safety IT Determine Phases Of Threat Attack Disrupting It Project Safety Elements PDF
This slide provides information regarding various phases for threat attack disrupting IT project safety in terms of reconnaissance, weaponization, delivery and exploitation. Presenting upgrading total project safety it determine phases of threat attack disrupting it project safety elements pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like reconnaissance, weaponization, delivery, exploitation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Upgrading Total Project Safety IT Determine Phases Of Threat Attack Disrupting Project Safety Contd Elements PDF
This slide provides information regarding various phases for threat attack disrupting IT project safety in terms of installation, command and control, actions and objectives, covering tracks. This is a upgrading total project safety it determine phases of threat attack disrupting project safety contd elements pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like installation, command and control, actions and objectives, covering tracks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Threat Drivers And Emerging Technologies Impact On Cyber Security Ppt Slides Graphic Images PDF
Mentioned slide highlights information about the threat drivers like privacy loss and hardware attacks along with the impact of emerging technologies such as IoT, AI on cyber security. This is a threat drivers and emerging technologies impact on cyber security ppt slides graphic images pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security, developing, strategic, opportunities. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Security Latest Threats In Data Security Ppt Summary Slides PDF
This slide depicts the categories of recent threats that recently emerged in the United States, United Kingdom, and Australia in previous years. This is a information security latest threats in data security ppt summary slides pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like dridex malware, romance scams, emotet malware. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity Types Of Latest Threats In Electronic Information Security Ppt Portfolio Icon PDF
This slide depicts the categories of recent threats that recently emerged in the United States, United Kingdom, and Australia in previous years. This is a cybersecurity types of latest threats in electronic information security ppt portfolio icon pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like dridex malware, romance scams, emotet malware. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Addressing Various Ways To Handle Mitigating Cybersecurity Threats And Vulnerabilities Template PDF
This slide provides details regarding various ways to handle insider cyber threats in terms of active remediation implementation, deactivating orphaned user accounts, etc. This is a addressing various ways to handle mitigating cybersecurity threats and vulnerabilities template pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like user accounts, implement active remediation, management policies. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Mitigating Cybersecurity Threats And Vulnerabilities Various Types Of Workplace Download PDF
This slide provides details regarding various types of workplace violence threats created by people in terms of stalking, physical assault, harassment or intimidation, etc. This is a mitigating cybersecurity threats and vulnerabilities various types of workplace download pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like threatening behavior, stalking, assault harassment, property damage. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Safety Incident Management Different Kinds Of Insider Digital Threats Download PDF
This slide provides details regarding various kinds of insider digital threats such as malicious insider, negligent insider, third party insider, etc. This is a cyber safety incident management different kinds of insider digital threats download pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like malicious insider, negligent or careless insider, third party insider. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Safety Incident Management Impact Analysis Of Successful Threat Management Implementation Summary PDF
This slide depicts the impact of successful implementation of threat management in terms improved incident management and customer satisfaction and depicts that how much the focus area has been improved from the previous state. This is a cyber safety incident management impact analysis of successful threat management implementation summary pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like focus area, past state, present state, benefit. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Safety Incident Management Various Types Of Workplace Violence And Threats Infographics PDF
This slide provides details regarding various types of workplace violence threats created by people in terms of stalking, physical assault, harassment or intimidation, etc. This is a cyber safety incident management various types of workplace violence and threats infographics pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like stalking, physical assault, harassment or intimidation, property damage, weapon assault . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
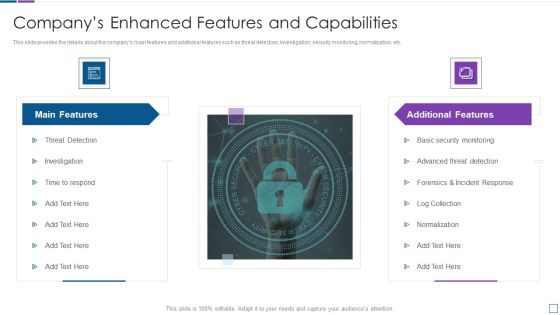
Real Time Assessment Of Security Threats Companys Enhanced Features And Capabilities Introduction PDF
This slide provides the details about the companys main features and additional features such as threat detection, investigation, security monitoring, normalization, etc. Presenting real time assessment of security threats companys enhanced features and capabilities introduction pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like main features, additional features. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Real Time Assessment Of Security Threats Security Information And Event Management Services Information PDF
This slide covers the SIEM services offered by our company such as data aggregation, correlation, security alerts, dashboards, retention, forensic analysis, IT compliance, threat detection, etc. Presenting real time assessment of security threats security information and event management services information pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like data aggregation, data correlation, security alert, dashboards, data retention. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
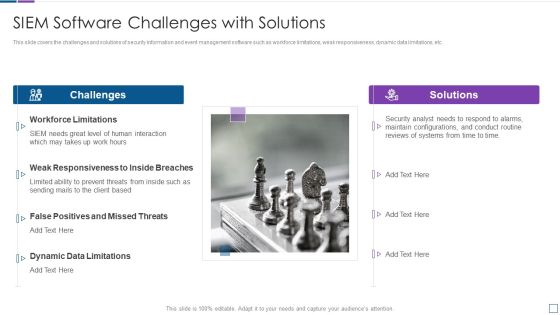
Real Time Assessment Of Security Threats SIEM Software Challenges With Solutions Inspiration PDF
This slide covers the challenges and solutions of security information and event management software such as workforce limitations, weak responsiveness, dynamic data limitations, etc. This is a real time assessment of security threats siem software challenges with solutions inspiration pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like challenges, solutions, workforce limitations, false positives and missed threats. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Real Time Assessment Of Security Threats Benchmarking With Security Operations Maturity Model Infographics PDF
This slide focuses on the SOMM which measures the current security posture and understand the progress of operations readiness by visibility improvement, threats identification, etc. Presenting real time assessment of security threats benchmarking with security operations maturity model infographics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like centralized forensic visibility, mean time to detect, mean time to respond. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Real Time Assessment Of Security Threats Security Intelligence Services Formats PDF
This slide covers the security intelligence services such as cyber threat intelligence, incident and response management, cyber analytics, vulnerability management, etc. Presenting real time assessment of security threats security intelligence services formats pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like incident response and management, cyber analytics, vulnerability management, infrastructure management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
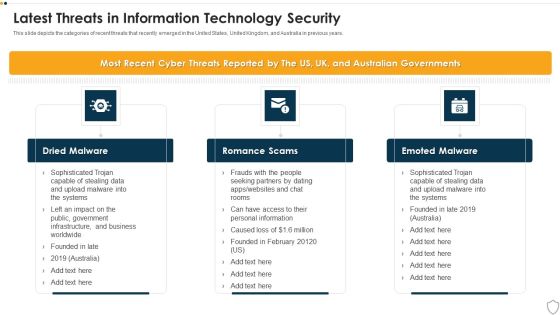
IT Security Latest Threats In Information Technology Security Ppt Slides Visuals PDF
This slide depicts the categories of recent threats that recently emerged in the United States, United Kingdom, and Australia in previous years. Presenting it security latest threats in information technology security ppt slides visuals pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like dried malware, romance scams, emoted malware. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
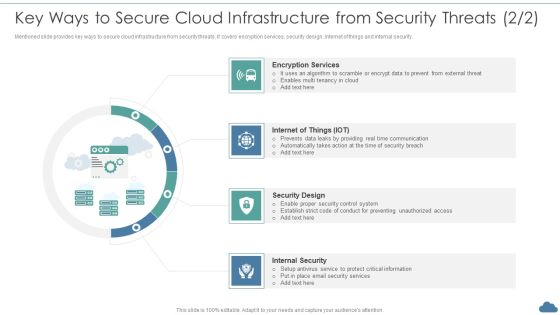
Cloud Optimization Infrastructure Model Key Ways To Secure Cloud Infrastructure From Security Threats Elements PDF
Mentioned slide provides key ways to secure cloud infrastructure from security threats. It covers encryption services, security design, internet of things and internal security.This is a Cloud Optimization Infrastructure Model Key Ways To Secure Cloud Infrastructure From Security Threats Elements PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Encryption Services, Security Design, Internal Security You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Various Cyber Security Threats And Strategies To Manage Network Service Solutions Ppt File Portrait PDF
This slide highlights different types of cybersecurity threat such as malware, phishing, trojan horse and rootkit. The template also provides information about various strategies which will assist IT department to manage its network services. Persuade your audience using this Various Cyber Security Threats And Strategies To Manage Network Service Solutions Ppt File Portrait PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Malware, Phishing, Rootkit, Trojan Horse. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Kill Chain For Insider Threat In Cyber Security Slides PDF
This slide shows cyber kill chain for insider threats. It provides information about investigation, weaponization, delivery, exploitation, installation, command and control, action, etc. It can be helpful for companies in being aware and proactive for preventing such attacks in future. Presenting Cyber Kill Chain For Insider Threat In Cyber Security Slides PDF to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including Investigation, Delivery, Installation, Exploitation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Key Initiatives To Detect Insider Threat In Cyber Security Designs PDF
This slide shows best practices for detecting insider threats. It provides information such as heavy screening of new hires, apply user access management, conduct security awareness training, monitor employee behavior, etc. Presenting Key Initiatives To Detect Insider Threat In Cyber Security Designs PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Screen Carefully, Secure Access, Conduct Training. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Key Monitoring Strategies To Counter Insider Threat In Cyber Security Demonstration PDF
This slide shows vital monitoring strategies for countering insider threat. It provides information about monitoring, protecting sensitive data, ascertaining user access, implementing least privilege model, applying security analytics and training employees. Persuade your audience using this Key Monitoring Strategies To Counter Insider Threat In Cyber Security Demonstration PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Monitoring User Data, Protecting Sensitive Data, Protecting Sensitive Data. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Mitigation Techniques To Reduce Insider Threat In Cyber Security Rules PDF
This slide shows mitigation techniques for reduction of insider threats. It provides information such as precise data managed, user access reduction and maintaining vigilance. Presenting Mitigation Techniques To Reduce Insider Threat In Cyber Security Rules PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Manage Data Precisely, Limit User Access, Maintain Vigilance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Most Effective It Security Tools For Protection Against Insider Threat In Cyber Security Inspiration PDF
This slide shows most effective IT security tools for protection against insider threats. It provides information about data loss prevention DLP, user and entity behavior UEBA, identity and access management IAM and security information and event management SIEM. Persuade your audience using this Most Effective It Security Tools For Protection Against Insider Threat In Cyber Security Inspiration PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Data Loss Prevention, Identity And Access, Management. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Process Flow For Detecting Insider Threat In Cyber Security Mockup PDF
This slide shows insider threat detection process flow. It contains information such as administrator, personal devices, behavior, detection system, behavior analysis, security auditing, terminating user access, etc. Presenting Process Flow For Detecting Insider Threat In Cyber Security Mockup PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including User Authentication, Insider Attacker, Administrator, Controlled Access. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
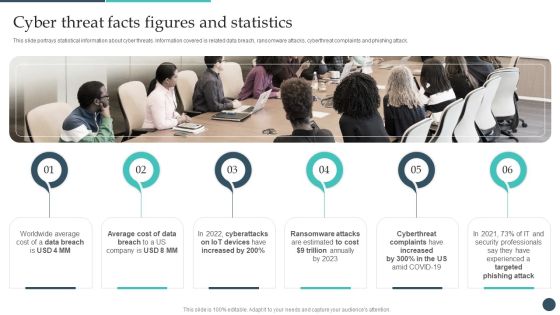
Safety Breach Response Playbook Cyber Threat Facts Figures And Statistics Demonstration PDF
This slide portrays statistical information about cyber threats. Information covered is related data breach, ransomware attacks, cyberthreat complaints and phishing attack. Boost your pitch with our creative Safety Breach Response Playbook Cyber Threat Facts Figures And Statistics Demonstration PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you dont have to invest time in any additional work. Just grab the template now and use them.

Confidential Data Theft Threats Mitigation Heat Map Ppt Portfolio Microsoft PDF
This slide covers heat map depicting data theft mitigation strategies and task prioritization. It includes process such as to discover employees roles and access levels, analyse threats and execute plan to reduce or eliminate data theft. Presenting Confidential Data Theft Threats Mitigation Heat Map Ppt Portfolio Microsoft PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Discover, Analyze, Execute And Educate. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Threat Facts Figures And Statistics Improving Cybersecurity With Incident Icons PDF
Find highly impressive Cyber Threat Facts Figures And Statistics Improving Cybersecurity With Incident Icons PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Cyber Threat Facts Figures And Statistics Improving Cybersecurity With Incident Icons PDF for your upcoming presentation. All the presentation templates are 100precent editable and you can change the color and personalize the content accordingly. Download now.

Various Cyber Threats Existing At Workplace Ppt Infographic Template Designs Download PDF
This slide provides information regarding various types of cyberthreats existing at workspace in terms of malware, ransomware, etc. The sources of cyber threats include criminal groups, hackers, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Various Cyber Threats Existing At Workplace Ppt Infographic Template Designs Download PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Various Types Of Workplace Violence And Threats Ppt Pictures Outline PDF
This slide provides details regarding various types of workplace violence threats created by people in terms of stalking, physical assault, harassment or intimidation, etc. Present like a pro with Various Types Of Workplace Violence And Threats Ppt Pictures Outline PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Table Of Contents Overview On Mitigating Workplace IT Threats Slides PDF
Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Table Of Contents Overview On Mitigating Workplace IT Threats Slides PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Table Of Contents Overview On Mitigating Workplace IT Threats Slides PDF.
