AI PPT Maker
Templates
PPT Bundles
Design Services
Business PPTs
Business Plan
Management
Strategy
Introduction PPT
Roadmap
Self Introduction
Timelines
Process
Marketing
Agenda
Technology
Medical
Startup Business Plan
Cyber Security
Dashboards
SWOT
Proposals
Education
Pitch Deck
Digital Marketing
KPIs
Project Management
Product Management
Artificial Intelligence
Target Market
Communication
Supply Chain
Google Slides
Research Services
 One Pagers
One PagersAll Categories
-
Home
- Customer Favorites
- Business Risks
Business Risks

Keyways To Secure Cloud Infrastructure From Security Threats Inspiration PDF
Mentioned slide provides keyways to secure cloud infrastructure from security threats. It covers encryption services, security design, internet of things and internal security.Presenting Keyways To Secure Cloud Infrastructure From Security Threats Inspiration PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Encryption Services, Internal Security, Security Design. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Best Practices For Threat Modeling Procedure Themes PDF
This slide shows best practices to assure efficiency in threat modeling process. It contains points such as documentation, develop schedule, set time frame, use existing resources, integration and suitable method.Presenting Best Practices For Threat Modeling Procedure Themes PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Project Execution, Determine Budget, Existing Resources. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Five Step Procedure Of Cyber Threat Hunting Introduction PDF
This slide shows steps for effective and successful cyber security systems to prevent from threats.it contains steps hypothesis, process data, trigger, investigation and resolution. Persuade your audience using this Five Step Procedure Of Cyber Threat Hunting Introduction PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Prepare Detailed, Management Software, Management Software. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Technological Smart Homes Security Steps To Eliminate Threat Themes PDF
This side showcase the steps to reduce the threats of smart home by creating solid defense for burglary and provides cybersecurity. It includes key elements such as door security, window reinforcement, save energy, garage protection and cybersecurity. Presenting Technological Smart Homes Security Steps To Eliminate Threat Themes PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Door Security, Window Reinforcement, Efficient Utilization Energy. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Data Threats Organizational Prevention Based Strategy Infographics PDF
This slide presents threat prevention detection and correction plan for data management that could help in avoiding serious outcomes and protecting data from ongoing security issues. It includes RBAC implementation, audits and backup API for data management. Increase audience engagement and knowledge by dispensing information using Data Threats Organizational Prevention Based Strategy Infographics PDF. This template helps you present information on three stages. You can also present information on Prevention, Detection, Correction using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.

Mitigating Cybersecurity Threats And Vulnerabilities Determine Staff Training Rules PDF
The employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. This is a mitigating cybersecurity threats and vulnerabilities determine staff training rules pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like advanced software training, advanced skills training, training module. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Mitigating Cybersecurity Threats And Vulnerabilities Workplace Employee Rules PDF
The employee assistance program will help firm in enhancing their well being at workplace and enable them to handle critical situations. This program will render services like clinical services, work and life services and employer services, etc. Presenting mitigating cybersecurity threats and vulnerabilities workplace employee rules pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like clinical services, work and life services, employer services. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Four Steps Of Threat Management Process Ppt Show Inspiration PDF
Presenting this set of slides with name four steps of threat management process ppt show inspiration pdf. This is a four stage process. The stages in this process are prevention, mitigation, preparedness, response, recovery. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Mitigation Strategies For Operational Threat Location Ppt Portfolio Introduction PDF
This is a mitigation strategies for operational threat location ppt portfolio introduction pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like location. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

How To Intensify Project Threats Post It Notes Clipart PDF
Presenting how to intensify project threats post it notes clipart pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like post it notes. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
How To Intensify Project Threats Roadmap Slides PDF
Presenting how to intensify project threats roadmap slides pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like roadmap. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

How To Intensify Project Threats Timeline Themes PDF
This is a how to intensify project threats timeline themes pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like timeline, 2018 to 2021. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Threats Response Playbook SWOT Analysis Professional PDF
This is a IT Threats Response Playbook SWOT Analysis Professional PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Strengths, Weaknesses, Opportunities. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Buyer Purchasing Journey Problem Opportunity Ppt Sample
This is a buyer purchasing journey problem opportunity ppt sample. This is a four stage process. The stages in this process are buyer purchasing journey, problem opportunity, solution opportunity, short list provide.

Team Building Problem Solving Tasks Ppt Example
This is a team building problem solving tasks ppt example. This is a seven stage process. The stages in this process are problem statement, background, idea generation, idea selection, analyze benefits and concerns, work any critical concerns, action planning.

Needs Assessment Or Problem Definition Ppt Example
This is a needs assessment or problem definition ppt example. This is a three stage process. The stages in this process are needs assessment or problem definition, program revision, goals and objectives, program planning and evaluation.

Systematic Problem Solving Strategies Ppt Presentation
This is a systematic problem solving strategies ppt presentation. This is a five stage process. The stages in this process are identify root causes, select appropriate solution, root cause eliminated, implement and check impact, brainstorm alternative solutions, identify problem.
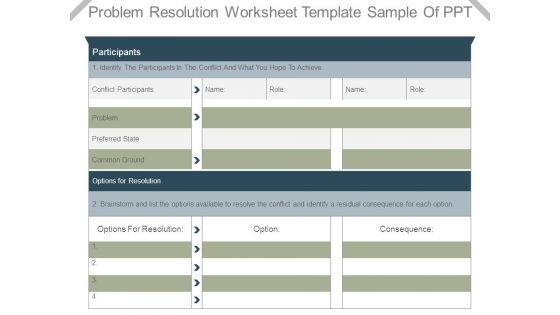
Problem Resolution Worksheet Template Sample Of Ppt
This is a problem resolution worksheet template sample of ppt. This is a two stage process. The stages in this process are conflict participants, problem, preferred state, common ground, options for resolution.

Problem Solving Skills Diagram Powerpoint Presentation Examples
This is a problem solving skills diagram powerpoint presentation examples. This is a six stage process. The stages in this process are define the problem, design a solution, settle on a course of action, troubleshoot the problem, adjust future actions, take action.

How To Intensify Project Threats Hierarchical Escalation Process Summary PDF
This slide provides the glimpse about the hierarchical escalation along with the hierarchy structure and meaning of such an escalation. This is a how to intensify project threats hierarchical escalation process summary pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like developer, service, hierarchical, organization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Supply Chain Strength Weakness Opportunity Threat Analysis Rules PDF
This slide showcases the SWOT analysis of the supply chain of n organization to provide better customer experience and deliver the goods at a fast pace. Persuade your audience using this Supply Chain Strength Weakness Opportunity Threat Analysis Rules PDF This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Opportunities, Weaknesses, Strengths Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cloud Security Assessment Cloud Security Threats Shared Vulnerabilities Icons PDF
This slide describes how organizations and providers share vulnerabilities of a system, so each party must take precautions to protect data.This is a Cloud Security Assessment Cloud Security Threats Shared Vulnerabilities Icons PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Standards, Authorization Restrictions, Providers Already. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Multi Step Strategy To Implement Cyber Threat Prevention Guidelines PDF
The following slide provides a step by step strategy to monitor and reassess your organizations cybersecurity maturity which helps to strengthen the cyber safety. The process involves understand, assess, determine and document. Persuade your audience using this Multi Step Strategy To Implement Cyber Threat Prevention Guidelines PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Determine, Document, Assess. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

PEST Analysis To Understand Market Opportunities And Threats Mockup PDF
This slide provides a framework for understanding the external environment and identifying potential opportunities and threats to help make informed decisions. The slide covers political, economic, technological and socio cultural factors. Present like a pro with PEST Analysis To Understand Market Opportunities And Threats Mockup PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Swot Analysis Threats Related To The Company Template PDF
Presenting swot analysis threats related to the company template pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like high competition, growing concerns about health, change in market trends. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

SWOT Analysis Of ADC Cosmetics Company Threats Download PDF
Presenting swot analysis of adc cosmetics company threats download pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like intense competition from similar companies, changes in consumer demand and preferences , government regulations and currency fluctuations. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Mitigating Cybersecurity Threats And Vulnerabilities Table Of Contents Infographics PDF
Presenting mitigating cybersecurity threats and vulnerabilities table of contents infographics pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like leveraging workforce, budget assessment, dashboard, impact assessment. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
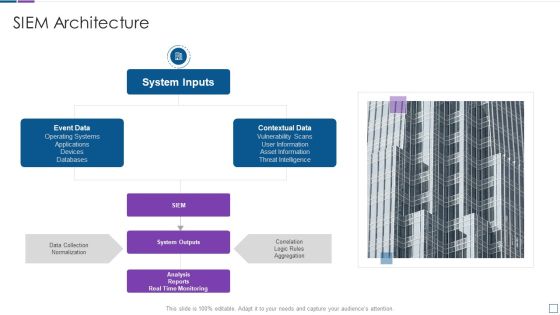
Real Time Assessment Of Security Threats SIEM Architecture Sample PDF
This is a real time assessment of security threats siem architecture sample pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like system inputs, event data, contextual data, system outputs. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Real Time Assessment Of Security Threats SIEM Integrations Slides PDF
Presenting real time assessment of security threats siem integrations slides pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security events, network logs, applications and devices, it infrastructure. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Agenda Of Threat Management At Workplace Professional Pdf
This is a agenda of threat management at workplace professional pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like digital assets, financial assets, physical security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Purpose Of IT Threats Response Playbook Professional PDF
This is a Purpose Of IT Threats Response Playbook Professional PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Standardized Cybersecurity, Future Security, Appropriate Manner. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Email Marketing Problems Analysis Ppt Powerpoint Ideas
This is a email marketing problems analysis ppt powerpoint ideas. This is a six stage process. The stages in this process are permission, privacy, reputation, preferences, expectations, compliance.
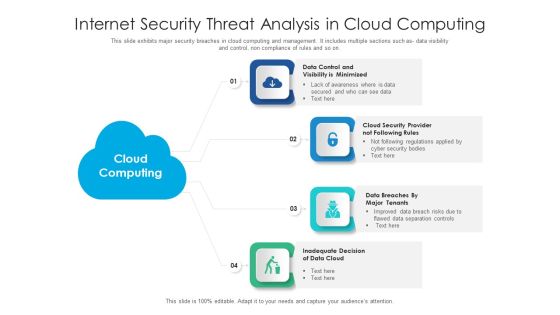
Internet Security Threat Analysis In Cloud Computing Information PDF
This slide exhibits major security breaches in cloud computing and management. It includes multiple sections such as- data visibility and control, non compliance of rules and so on. Presenting internet security threat analysis in cloud computing information pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including data cloud, cloud security, data control. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Mitigation Tactics To Prevent Internet Security Threats Formats PDF
This side exhibits mitigation strategies to prevent security breach incidents. It includes multiple actions such as keeping track of all personal assets, analyzing logging process security and so on. Presenting mitigation tactics to prevent internet security threats formats pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including communication management, monitoring and alerting, logging, visibility. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

How To Intensify Project Threats Project Closure Report Mockup PDF
This slide provides the glimpse about the final step of issue and escalation process which covers the project closure report along with the details such as project information, benefits, key metrics, project deliverables, controls in place, shortfalls, etc. This is a how to intensify project threats project closure report mockup pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like project information, benefits, key metrics, project deliverables, controls in place, shortfalls. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
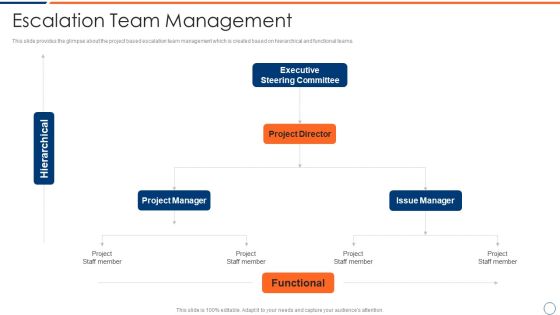
How To Intensify Project Threats Escalation Team Management Slides PDF
This slide provides the glimpse about the project based escalation team management which is created based on hierarchical and functional teams. Presenting how to intensify project threats escalation team management slides pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like project manager, issue manager, functional, project director, executive steering committee. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

How To Intensify Project Threats Functional Escalation Process Rules PDF
This slide provides the glimpse about the functional escalation along with the functional structure and meaning of such an escalation. This is a how to intensify project threats functional escalation process rules pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like developer, service, functional escalation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

How To Intensify Project Threats Project Closure Checklist Clipart PDF
This slide provides the glimpse about the final step of issue and escalation process which covers the project checklist which covers the various steps which must be focused on by the company. Presenting how to intensify project threats project closure checklist clipart pdf to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like project closure checklist. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Mitigating Cybersecurity Threats And Vulnerabilities Addressing Asset Security Elements PDF
This slide provides details regarding asset security categorization on certain parameters such as ownership, location, confidentiality, integrity and availability. This is a mitigating cybersecurity threats and vulnerabilities addressing asset security elements pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like ownership, location, integrity, security categorization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Mitigating Cybersecurity Threats And Vulnerabilities Incident Reporting Themes PDF
This slide will help in providing an overview of the various reported incidents, average cost per incident and number of people involved in the various incidents across different departments. Presenting mitigating cybersecurity threats and vulnerabilities incident reporting themes pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like incident reporting by different departments. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
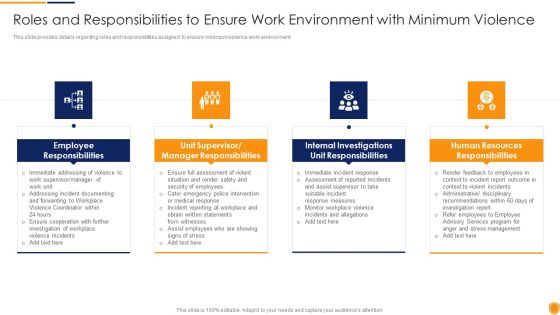
Mitigating Cybersecurity Threats And Vulnerabilities Roles And Responsibilities Introduction PDF
This slide provides details regarding roles and responsibilities assigned to ensure minimum violence work environment. This is a mitigating cybersecurity threats and vulnerabilities roles and responsibilities introduction pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employee responsibilities, manager responsibilities, unit responsibilities, human resources responsibilities. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
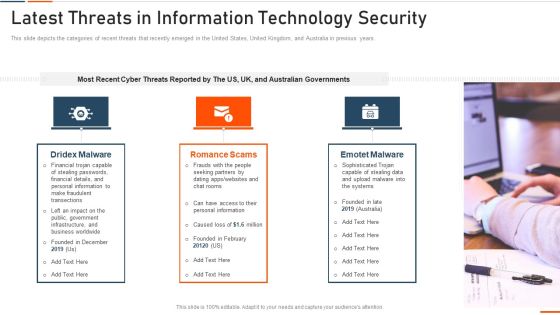
Latest Threats In Information Technology Security Ppt Pictures Designs PDF
This slide represents the different elements of Network security such as application security, network security, information security, etc. This is a latest threats in information technology security ppt pictures designs pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like network security, cloud security, application security, operational security, information security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Data Breach Threats Process Flow Model Ppt Model Maker PDF
This slide covers process of data breach in an organisation. It includes steps such as researching weak points, staging attack and exfiltration of data resulting it to data breach in an organisation. Persuade your audience using this Data Breach Threats Process Flow Model Ppt Model Maker PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Research, Stage Attack, Exfiltrate, Social Engineering. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Ready To Eat Food Market Analysis Kellogg Threats Guidelines PDF
Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Ready To Eat Food Market Analysis Kellogg Threats Guidelines PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Smart Phone Security Tools For Preventing Threats Topics PDF
This slide shows latest security tools for managing phone security model. The purpose of this slide is to highlight various tools names with description for selecting most suitable tool. It include tools such as data loss prevention, identify and access management, etc. Presenting Smart Phone Security Tools For Preventing Threats Topics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Data Loss Prevention, Identity Access Management, Security Event Management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Blockchain Technology Applications For Cyber Threat Prevention Icons PDF
This slides represents various application of blockchain technology in enhancing cyber safety which helps to speed up data transfer procedures, offer secure transactions, and lower compliance expenses. Key components are IoT security, secure private messaging, etc. Presenting Blockchain Technology Applications For Cyber Threat Prevention Icons PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Prevention, Infrastructure, System . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Network Security Management For Cyber Threat Prevention Demonstration PDF
This slide exhibits the areas where IT department need to address the network security management in order to reduce errors and promote data security. Major components are deployment, configuration, management, monitor and maintenance. Presenting Network Security Management For Cyber Threat Prevention Demonstration PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Deployment, Management, Configuration. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Cyber Threat Organizational Prevention Based Strategy Plan Template PDF
This slide presents prevention, detection and correction plan for cybersecurity and management that helps in avoiding critical situations and data loss. It includes plan for technology, processes and human activity that takes place in organisation. Introducing Cyber Threat Organizational Prevention Based Strategy Plan Template PDF. to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Technology, Processes, Human Activity, using this template. Grab it now to reap its full benefits.

Cloud Security Threats Contract Breaches With Clients Cloud Computing Security IT Ppt Ideas Introduction PDF
This slide defines the contract breaches with clients and customers that could be the biggest threat to the organizational data. Presenting cloud security threats contract breaches with clients cloud computing security it ppt ideas introduction pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like business, organization, sensitive data stored. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Puzzle Problem Solution Ppt PowerPoint Presentation Summary
Presenting this set of slides with name puzzle problem solution ppt powerpoint presentation summary. This is a five stage process. The stages in this process are puzzle, solution, problem, marketing, management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Puzzle Problem Solution Ppt PowerPoint Presentation Examples
Presenting this set of slides with name puzzle problem solution ppt powerpoint presentation examples. This is a two stage process. The stages in this process are puzzle, solution, problem, marketing, management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Puzzle Problem Ppt PowerPoint Presentation Slides Introduction
Presenting this set of slides with name puzzle problem ppt powerpoint presentation slides introduction. This is a five stage process. The stages in this process are puzzle, solution, problem, marketing, management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Puzzle Problem Ppt PowerPoint Presentation Icon Layouts
Presenting this set of slides with name puzzle problem ppt powerpoint presentation icon layouts. This is a four stage process. The stages in this process are puzzle, solution, problem, marketing, management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Puzzle Problem Ppt PowerPoint Presentation Inspiration Skills
Presenting this set of slides with name puzzle problem ppt powerpoint presentation inspiration skills. This is a four stage process. The stages in this process are puzzle, solution, problem, marketing, management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Puzzle Problem Ppt PowerPoint Presentation Portfolio Elements
Presenting this set of slides with name puzzle problem ppt powerpoint presentation portfolio elements. This is a four stage process. The stages in this process are puzzle, solution, problem, marketing, management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Puzzle Problem Ppt PowerPoint Presentation Slides Tips
Presenting this set of slides with name puzzle problem ppt powerpoint presentation slides tips. This is a four stage process. The stages in this process are puzzle, solution, problem, marketing, management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Puzzle Problem Ppt PowerPoint Presentation Infographic Template
Presenting this set of slides with name puzzle problem ppt powerpoint presentation infographic template. This is a four stage process. The stages in this process are puzzle, solution, problem, marketing, management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Problem Statement Ppt Styles Model PDF
Presenting problem statement ppt styles model pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like problem statement. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Communication Problem In Workplace Icon Themes PDF
Presenting Communication Problem In Workplace Icon Themes PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Communication Problem In Workplace Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Project Problem Mitigation Plan Icon Icons PDF
Persuade your audience using this Project Problem Mitigation Plan Icon Icons PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Project Problem Mitigation Plan Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
