Business Problem And Solution

Company Risk Assessment Plan Financial Risk Management And Assessment Framework Sample PDF
This slide covers framework to detect and manage the risks arising from the use of financial services. It includes details related to identification and measurement, strategy and policy, process and execution and monitoring and reporting of financial risks. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Company Risk Assessment Plan Financial Risk Management And Assessment Framework Sample PDF can be your best option for delivering a presentation. Represent everything in detail using Company Risk Assessment Plan Financial Risk Management And Assessment Framework Sample PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Strategies For Credit Risk Management Mitigating Credit And Control Of Risks Introduction PDF
This slide shows the mitigation credit and control of the risks such as risk based pricing, covenants, credit insurance, credit derivatives, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Strategies For Credit Risk Management Mitigating Credit And Control Of Risks Introduction PDF can be your best option for delivering a presentation. Represent everything in detail using Strategies For Credit Risk Management Mitigating Credit And Control Of Risks Introduction PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Risk Assessment Tools And Techniques For Project Risk Analysis Graphics PDF
This slide provides an overview of the techniques used for analyzing the risks. Major techniques covered are delphi method, SWOT analysis, risk register and decision tree analysis. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Risk Assessment Tools And Techniques For Project Risk Analysis Graphics PDF can be your best option for delivering a presentation. Represent everything in detail using Risk Assessment Tools And Techniques For Project Risk Analysis Graphics PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Functional Risk Mitigation Structure Financial Organization Marketing Roadmap Mockup PDF
Presenting functional risk mitigation structure financial organization marketing roadmap mockup pdf. to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like marketing roadmap In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
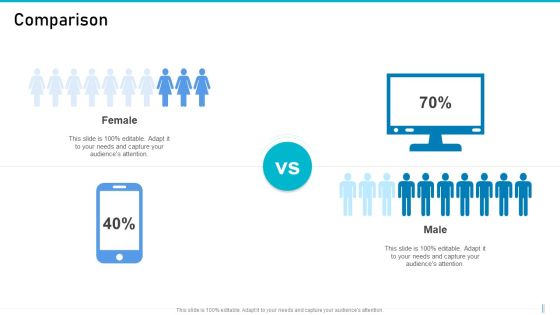
Risk Management For Organization Essential Assets Comparison Mockup PDF
Presenting risk management for organization essential assets comparison mockup pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like female, male. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Agenda Of OP Risk Management Structure PDF
Presenting agenda of op risk management structure pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like agenda of op risk management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Mitigation Strategies For Operational Threat Three Line Of Defense Model Defining Key Accountabilities Ppt Summary Styles PDF
Following slide shows three line of defense model. It defines key accountabilities of each line of defense and their outcomes. Presenting mitigation strategies for operational threat three line of defense model defining key accountabilities ppt summary styles pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like managers, risk management, audit internal and external. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Types Of Threats In IT Security IT Ppt Summary Graphics Tutorials PDF
This slide depicts the main types of threats in cyber security, such as cybercrime, cyber terrorism, and cyberattacks to an organization and the purpose of each category threat. Presenting types of threats in it security it ppt summary graphics tutorials pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like cyber crime, cyber terrorism, cyber attack. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Desktop Security Management Types Of Threats In Desktop Security Management Themes PDF
This slide depicts the main types of threats in cyber security, such as cybercrime, cyber terrorism, and cyberattacks to an organization and the purpose of each category threat. Presenting desktop security management types of threats in desktop security management themes pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like target systems, devices. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security Types Of Threats In Information Technology Security Ppt Summary Aids PDF
This slide depicts the main types of threats in cyber security, such as cybercrime, cyber terrorism, and cyberattacks to an organization and the purpose of each category threat. Presenting it security types of threats in information technology security ppt summary aids pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like cyber crime, cyber terrorism, cyber attack. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Info Security Types Of Threats In Information Security Ppt PowerPoint Presentation Gallery Layout Ideas PDF
This slide depicts the main types of threats in cyber security, such as cybercrime, cyber terrorism, and cyberattacks to an organization and the purpose of each category threat. Presenting info security types of threats in information security ppt powerpoint presentation gallery layout ideas pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like cyber crime, cyber terrorism, cyber attack. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
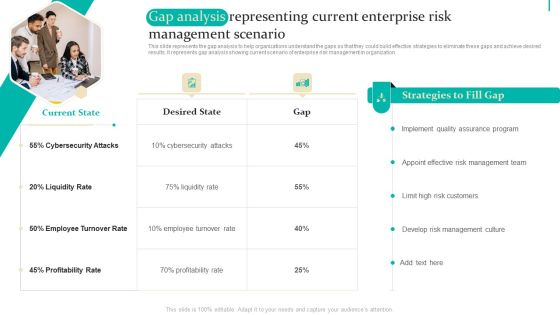
Enterprise Risk Management Gap Analysis Representing Current Enterprise Risk Demonstration PDF
This slide represents the gap analysis to help organizations understand the gaps so that they could build effective strategies to eliminate these gaps and achieve desired results. It represents gap analysis showing current scenario of enterprise risk management in organization. This modern and well-arranged Enterprise Risk Management Gap Analysis Representing Current Enterprise Risk Demonstration PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

What Concerns Firm Is Facing Regarding Lead Scoring Designs PDF
This slide provides information regarding the key concerns that have raised in context to lead scoring, as firms lead management system is not updated, so firm is facing issues regarding the lead nurturing process ultimately leading to increase in number of unsubscribes.Presenting what concerns firm is facing regarding lead scoring designs pdf. to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like improving lead management systems, high customer churn rate increase in negative behaviors, long sales cycles. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
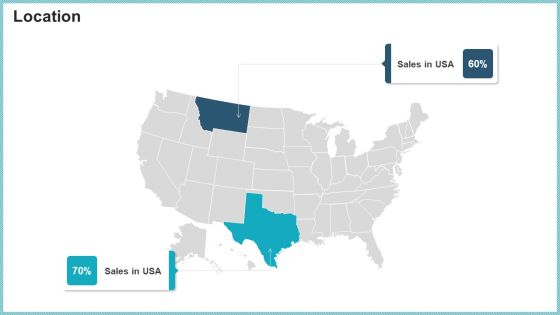
OP Risk Management Location Elements PDF
Presenting op risk management location elements pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like location. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

OP Risk Management Dashboard Template PDF
Presenting op risk management dashboard template pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like dashboard. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Building Projects Risk Landscape Comparison Designs PDF
Presenting building projects risk landscape comparison designs pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like comparison. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Building Projects Risk Landscape Financial Brochure PDF
Presenting building projects risk landscape financial brochure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like financial. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Information Security Cloud Security Threats Loss Of Data Ppt Layouts Example PDF
This slide represents the data loss threat of cloud security, it is essential to secure organization data and create backups. Presenting Cloud Information Security Cloud Security Threats Loss Of Data Ppt Layouts Example PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Provider Wisely, Procedures Strategies, Storage Locations. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Assessment Cloud Security Threats Loss Of Data Topics PDF
This slide represents the data loss threat of cloud security it is essential to secure organization data and create backups.Presenting Cloud Security Assessment Cloud Security Threats Loss Of Data Topics PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Storage Locations, Natural Disasters, Massive Impact. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Threats Shared Vulnerabilities Cloud Computing Security IT Ppt Slides Picture PDF
This slide describes how organizations and providers share vulnerabilities of a system, so each party must take precautions to protect data. Presenting cloud security threats shared vulnerabilities cloud computing security it ppt slides picture pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like organizations, cloud service, responsibility, cloud data security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
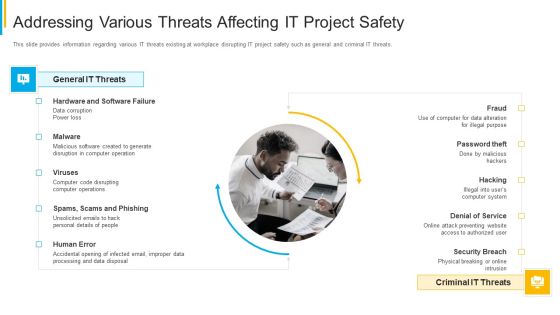
Project Security Administration IT Addressing Various Threats Affecting IT Project Safety Designs PDF
This slide provides information regarding various IT threats existing at workplace disrupting IT project safety such as general and criminal IT threats. Presenting project security administration it addressing various threats affecting it project safety designs pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like general it threats, criminal it threats. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Threats Response Playbook Categorization Worksheet For System Components Graphics PDF
This slide illustrates categorization worksheet that can be used to categorize system components. It includes information about security system such as system name, its version, system location and other general information.Presenting IT Threats Response Playbook Categorization Worksheet For System Components Graphics PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like System Accessibility, Valuable Information, Organization Boundary. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cybersecurity Risk Scorecard 8 Essential Information Security Risk Scorecard For Organization Elements PDF
Presenting cybersecurity risk scorecard 8 essential information security risk scorecard for organization elements pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like 30 60 90 days plan. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Opportunities And Threats For Penetrating In New Market Segments Porters Five Forces Analysis Elements PDF
Presenting opportunities and threats for penetrating in new market segments porters five forces analysis elements pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like threat of new entrants, bargaining of suppliers, bargaining power of buyers, threat of substitute product or service, rivalry among existing competitors. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Safety Incident Management Determine Sequence Phases For Threat Attack Rules PDF
This slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. Presenting cyber safety incident management determine sequence phases for threat attack rules pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like reconnaissance, weaponization, exploitation, delivery. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
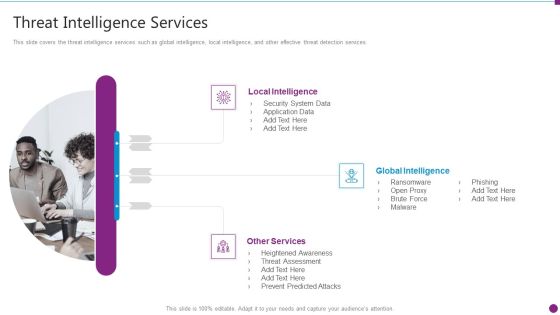
Security Information And Event Management Strategies For Financial Audit And Compliance Threat Intelligence Services Graphics PDF
This slide covers the threat intelligence services such as global intelligence, local intelligence, and other effective threat detection services. Presenting security information and event management strategies for financial audit and compliance threat intelligence services graphics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like local intelligence, global intelligence, other services. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
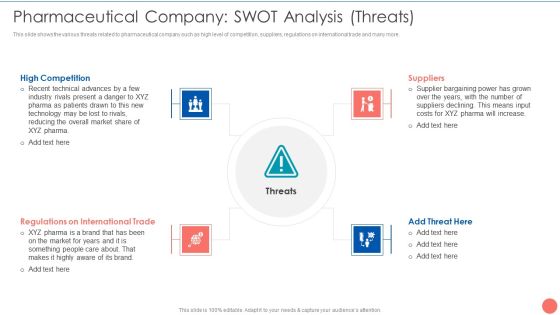
Tactics To Achieve Sustainability Pharmaceutical Company SWOT Analysis Threats Elements PDF
This slide shows the various threats related to pharmaceutical company such as high level of competition, suppliers, regulations on international trade and many more. Presenting Tactics To Achieve Sustainability Pharmaceutical Company SWOT Analysis Threats Elements PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like High Competition Threats, Regulations International Trade, Suppliers Bargaining Power. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
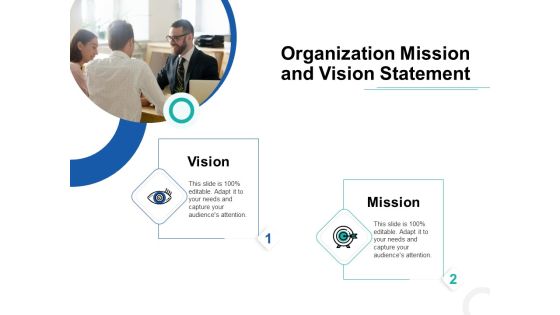
Develop Corporate Cyber Security Risk Mitigation Plan Organization Mission And Vision Statement Download PDF
Presenting develop corporate cyber security risk mitigation plan organization mission and vision statement download pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like vision, mission. In addtion, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

Decentralized Applications Demerits Of Decentralized Apps Themes PDF
This slide highlights the disadvantages of decentralized apps, including hurdles in maintenance, performance overhead, network congestion. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Decentralized Applications Demerits Of Decentralized Apps Themes PDF can be your best option for delivering a presentation. Represent everything in detail using Decentralized Applications Demerits Of Decentralized Apps Themes PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Project Risk Management And Reduction Need For Risk Management To Project Managers Structure PDF
This slide showcases the need of risk management to project managers. Major needs covered are to maximize results, evaluate entire project, be proactive, project success and communication with stakeholders. This modern and well-arranged Project Risk Management And Reduction Need For Risk Management To Project Managers Structure PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Various Ways To Manage Project Safety By Managing Threats Contd Ppt Styles Diagrams PDF
This slide provides information regarding various ways to handle threats to ensure project safety in terms of active remediation implementation, deactivating orphaned user accounts, etc. Presenting various ways to manage project safety by managing threats contd ppt styles diagrams pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like management, systems, service, resources, techniques. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Project Security Administration IT Determine Phases Of Threat Attack Disrupting Project Safety Contd Icons PDF
This slide provides information regarding various phases for threat attack disrupting IT project safety in terms of installation, command and control, actions and objectives, covering tracks. Presenting project security administration it determine phases of threat attack disrupting project safety contd icons pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like installation, command and control, actions and objectives, covering tracks. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Upgrading Total Project Safety IT Determine Phases Of Threat Attack Disrupting It Project Safety Elements PDF
This slide provides information regarding various phases for threat attack disrupting IT project safety in terms of reconnaissance, weaponization, delivery and exploitation. Presenting upgrading total project safety it determine phases of threat attack disrupting it project safety elements pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like reconnaissance, weaponization, delivery, exploitation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
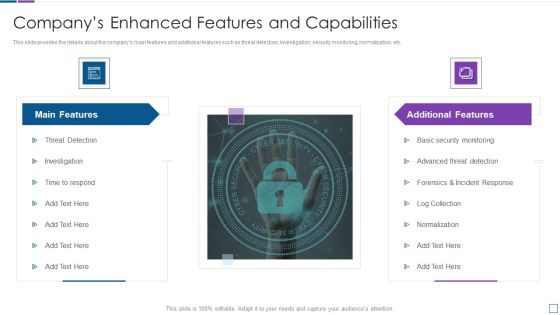
Real Time Assessment Of Security Threats Companys Enhanced Features And Capabilities Introduction PDF
This slide provides the details about the companys main features and additional features such as threat detection, investigation, security monitoring, normalization, etc. Presenting real time assessment of security threats companys enhanced features and capabilities introduction pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like main features, additional features. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Real Time Assessment Of Security Threats Security Information And Event Management Services Information PDF
This slide covers the SIEM services offered by our company such as data aggregation, correlation, security alerts, dashboards, retention, forensic analysis, IT compliance, threat detection, etc. Presenting real time assessment of security threats security information and event management services information pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like data aggregation, data correlation, security alert, dashboards, data retention. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Real Time Assessment Of Security Threats Benchmarking With Security Operations Maturity Model Infographics PDF
This slide focuses on the SOMM which measures the current security posture and understand the progress of operations readiness by visibility improvement, threats identification, etc. Presenting real time assessment of security threats benchmarking with security operations maturity model infographics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like centralized forensic visibility, mean time to detect, mean time to respond. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Real Time Assessment Of Security Threats Security Intelligence Services Formats PDF
This slide covers the security intelligence services such as cyber threat intelligence, incident and response management, cyber analytics, vulnerability management, etc. Presenting real time assessment of security threats security intelligence services formats pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like incident response and management, cyber analytics, vulnerability management, infrastructure management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
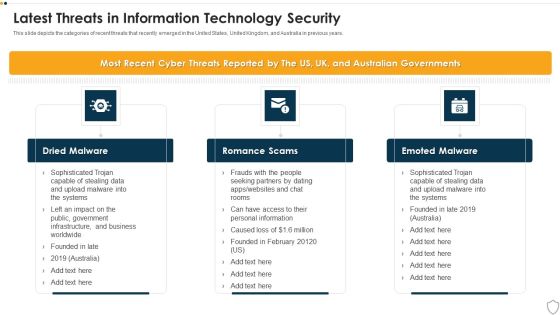
IT Security Latest Threats In Information Technology Security Ppt Slides Visuals PDF
This slide depicts the categories of recent threats that recently emerged in the United States, United Kingdom, and Australia in previous years. Presenting it security latest threats in information technology security ppt slides visuals pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like dried malware, romance scams, emoted malware. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
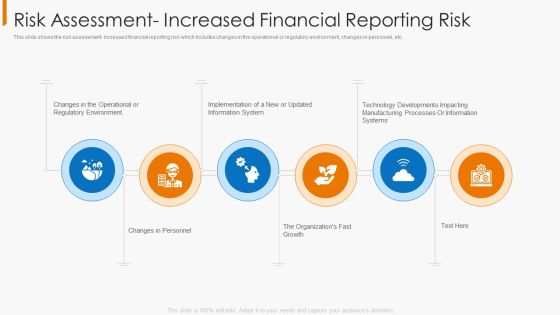
Risk Assessment Increased Financial Reporting Risk Themes PDF
This slide shows the risk assessment- increased financial reporting risk which includes changes in the operational or regulatory environment, changes in personnel, etc. Presenting risk assessment increased financial reporting risk themes pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like environment, implementation, information system, manufacturing processes. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

OP Risk Management Budget For Operational Risk Management Pictures PDF
Mentioned slide shows budget for operational risk management. It includes information such as functional department, training course, training duration, training cost, number of employees and total training cost. Presenting op risk management budget for operational risk management pictures pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like training duration, training course, employees to be trained. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Risk Based Methodology Common Quality Risk Management Tools Guidelines PDF
This slide covers most of the frequently used approaches for quality risk management including tools name, description, and applications. This modern and well-arranged Risk Based Methodology Common Quality Risk Management Tools Guidelines PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
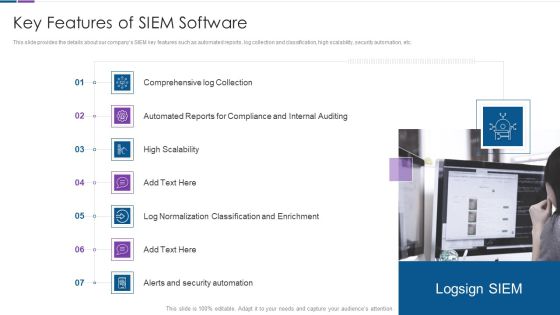
Real Time Assessment Of Security Threats Key Features Of SIEM Software Inspiration PDF
This slide provides the details about our companys SIEM key features such as automated reports, log collection and classification, high scalability, security automation, etc. Presenting real time assessment of security threats key features of siem software inspiration pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like compliance and internal auditing, high scalability, classification and enrichment, security automation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
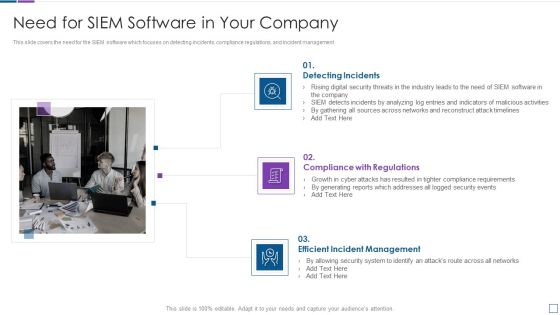
Real Time Assessment Of Security Threats Need For SIEM Software In Your Company Template PDF
This slide covers the need for the SIEM software which focuses on detecting incidents, compliance regulations, and incident management. Presenting real time assessment of security threats need for siem software in your company template pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like detecting incidents, compliance with regulations, efficient incident management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Real Time Assessment Of Security Threats Our Companys Mission Vision And Values Rules PDF
This slide provides the details of our company mission, vision and values to provide unique services to the customers. Presenting real time assessment of security threats our companys mission vision and values rules pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like our mission, our vision, our values. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
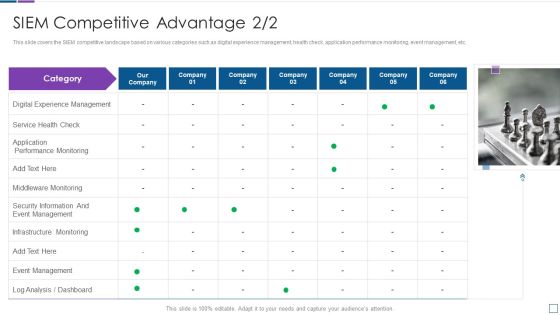
Real Time Assessment Of Security Threats SIEM Competitive Advantage Service Structure PDF
This slide covers the SIEM competitive landscape based on various categories such as digital experience management, health check, application performance monitoring, event management, etc. Presenting real time assessment of security threats siem competitive advantage service structure pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like digital experience management, service health check, application performance monitoring. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Real Time Assessment Of Security Threats Log Management Services Information PDF
This slide covers the log management services offered by our company such as collection and normalization, search speed, real time analysis, decision making process etc. Presenting real time assessment of security threats log management services information pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like collection and normalization, real time analysis, decision making process, log data filtering. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Handling Cyber Threats Digital Era Categorization Worksheet For Assets Ppt Icon Outline PDF
This slide illustrates asset categorization worksheet covering information about security system such as system name, its version, system location and other general information. Presenting handling cyber threats digital era categorization worksheet for assets ppt icon outline pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like server computer, system location, system accessibility. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Threats Response Playbook Backup Methods For Cyber Defense Planning Elements PDF
Following slide shows various backup methods as well as backup options that can be chosen for cyber defense planning. Methods covered are full, differential and incremental.Presenting IT Threats Response Playbook Backup Methods For Cyber Defense Planning Elements PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Differential, Incremental, Differential. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Technology Threat Mitigation Methods Detection And Prevention Of Management Security Controls Themes PDF
The following slide highlights the management security controls which includes preventive management security controls showcasing IT security polices and guidelines with detection management security controls. Presenting Information Technology Threat Mitigation Methods Detection And Prevention Of Management Security Controls Themes PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Preventive Management Security Controls, Detection Management Security Controls. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Technology Threat Mitigation Methods Identification And Recovery Of Technical Controls Demonstration PDF
This slide highlights identification and recovery of technical controls which includes audit, intrusion identification, proof of wholeness, recover secure state and virus detection and eradication. Presenting Information Technology Threat Mitigation Methods Identification And Recovery Of Technical Controls Demonstration PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Recover Secure State, Virus Eradication, Audit. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Technology Threat Mitigation Methods Security Criteria And Control Measures For IT System Vulnerabilities Themes PDF
This slide highlights the security criteria for information technology system vulnerabilities with security area which includes management security, operational security and technical security. Presenting Information Technology Threat Mitigation Methods Security Criteria And Control Measures For IT System Vulnerabilities Themes PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Management Security, Operational Security, Technical Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Technology Threat Mitigation Methods Preventive IT Technical Control Measures Information PDF
The following slide highlights the preventive information technical controls which includes authentication, authorization, enable control enforcement, nonrepudiation, secured communications and secured transactions. Presenting Information Technology Threat Mitigation Methods Preventive IT Technical Control Measures Information PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Authorization, Secured Communications, Authentication. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Real Time Assessment Of Security Threats Our Management Team Graphics PDF
This slide covers the details of the management team along with their job profile and brief description about their work. This is a real time assessment of security threats our management team graphics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like our management team. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Threats Response Playbook Identifying The Origin And Type Of Cyber Incident Rules PDF
Following slide portrays information about the cyber incident source of origin, their description and type. Members can use this slide to effectively identify the source and type of any cyber attack.This is a IT Threats Response Playbook Identifying The Origin And Type Of Cyber Incident Rules PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like External Removable, Malicious Attachment, Loss Valuable. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Effective Communication Plan To Address Fraud Event Appropriately Fraud Threat Administration Guide Template PDF
Following slide portrays communication plan that company is using for effectively managing cyber breaches. Sections covered here are type of fraud, description, delivery method, frequency and responsible.This is a Effective Communication Plan To Address Fraud Event Appropriately Fraud Threat Administration Guide Template PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Phishing Technique, Obtain Passwords, Communicate Through. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Vulnerability Rating For Risk Identification Cybersecurity Risk Assessment Structure PDF
This slide showcases table for allocating vulnerability rating to different class of information assets. Its shows information about severity, vulnerability score and description. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Vulnerability Rating For Risk Identification Cybersecurity Risk Assessment Structure PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
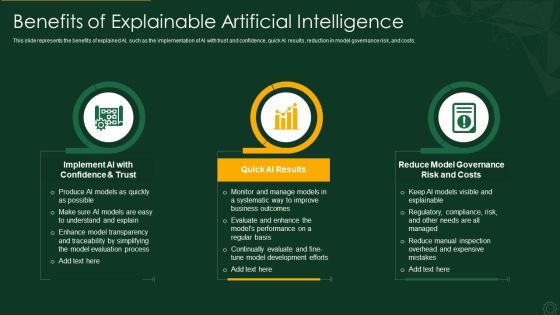
Explainable AI XAI Frameworks IT Benefits Of Explainable Artificial Intelligence Brochure PDF
This slide represents the benefits of explained AI, such as the implementation of AI with trust and confidence, quick AI results, reduction in model governance risk, and costs. This is a explainable ai xai frameworks it benefits of explainable artificial intelligence brochure pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like reduce model governance risk and costs, quick ai results, implement ai with confidence and trust. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Organization Stress Administration Practices Positive Effect From Stress Management Training Program Download PDF
This slide highlights the positive effect of stress management on organization and employees which includes reduce workplace conflicts, accidents and sexual harassment and improvement in employee productivity etc.Presenting Organization Stress Administration Practices Positive Effect From Stress Management Training Program Download PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Improvement Employee, Reduction In Sexual, Reduction Accidents In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
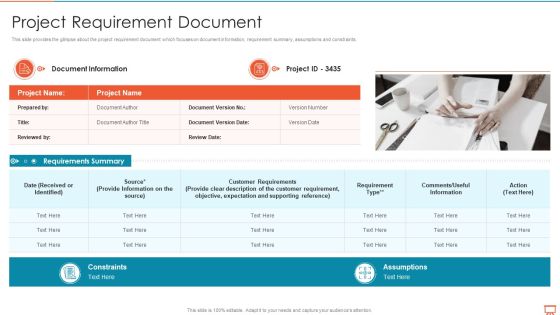
Project Management Experts Required Reports Project Requirement Document Sample PDF
This slide provides the glimpse about the project requirement document which focuses on document information, requirement summary, assumptions and constraints. Presenting project management experts required reports project requirement document sample pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like constraints, assumptions, source, action. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Executing Security Management Program To Mitigate Threats And Safeguard Confidential Organizational Data 30 60 90 Days Plan Brochure PDF
Presenting Executing security management program to mitigate threats and safeguard confidential organizational data 30 60 90 days plan brochure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like 30 60 90 days plan. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

 Home
Home