Access Point

1 Storage Access Point Ethernet Port Access Point Web Cam Pen Drive Icon Ppt Slides
This Powerpoint image slide has been designed to display the storage access points in any database. This image slide contains the graphic of multiple applications and access points. We have used ethernet port, web cam and pen drive graphics to explain the concept of access point.

1 Wifi Access Point Connected To Mobile Phone And Laptop Over Wireless Network Ppt Slides
This image slide displays Wi-Fi access point connected various technology devices. This image slide has been designed with graphic of wireless router, mobile phone, laptop and computer. This image slide depicts networking. You may change size, color and orientation of any icon to your liking. Use this PowerPoint template to express views on wireless networking in your presentations. This image may also be used in computer education presentations. This image slide will impart professional appearance to your presentations.

1 Wireless Computer Networking Wifi Access Point Connected To Globe Computers Ppt Slides
This image slide displays wireless computer networking Wi-Fi access point connected to globe computers. This image slide has been designed with graphic of globe, wireless router and various technology devices. This image slide depicts networking. You may change size, color and orientation of any icon to your liking. Use this PowerPoint template to express views on global, wireless networking in your presentations. This image may also be used in computer education presentations. This image slide will impart professional appearance to your presentations.

1 Wired And Wireless Networking Shown With Router And Access Point Ppt Slide
This image slide explain the concept of wired and wireless communication. This image slide has been designed with graphic of one wired network with desktop, server and router and one wireless network with server, router and laptop. You may change color, size and orientation of any icon to your liking. Use this image slide, in your presentations to express views on different types of network, communication and technology. This image slide will help you create interesting presentations.

1 Wireles Access Point Communication With Mobile Laptop Desktop Computers Ppt Slide
This image slide displays wireless network. This image slide has been designed with graphic of laptops, desktops, mobile, router and WI-FI signal. You may change color, size and orientation of any icon to your liking. Use this image slide, in your presentations to express views on wireless networking, communication and technology. This image slide will enhance the quality of your presentations.

1 Wireless Router Access Point Icon On Internet Button Ppt Slide
This image slide displays icon of router. This image slide has been designed with graphic of router icon with text space. You may change color, size and orientation of any icon to your liking. Use this image slide, in your presentations to express views on wireless or wired networking, communication and technology. This image slide will enhance the quality of your presentations.

Business Diagram Lock Graphics For Secure Internet Access Presentation Template
This power point template has been crafted with graphic of 3d world map and lock. This PPT contains the concept of security. Use this PPT for your business and marketing related presentations.

Internet Computer World Access PowerPoint Slides And Ppt Diagram Templates
Internet computer world access PowerPoint Slides And PPT Diagram TemplatesThese high quality, editable pre-designed powerpoint slides have been carefully created by our professional team to help you impress your audience. Each graphic in every slide is vector based and is 100% editable in powerpoint. Each and every property of any slide - color, size, shading etc can be modified to build an effective powerpoint presentation. Use these slides to convey complex business concepts in a simplified manner. Any text can be entered at any point in the powerpoint slide. Simply DOWNLOAD, TYPE and PRESENT!

Table Of Contents For Open Radio Access Network Background PDF
Slidegeeks has constructed Table Of Contents For Open Radio Access Network Background PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

Zero Trust Network Access Ztna Introduction Ppt Slide PDF
This slide represents the overview of zero trust network access, including its architecture. The purpose of this slide is to demonstrate the overview and use cases of ZTNA. The primary use cases include authentication and access control and holistic control and visibility. Slidegeeks has constructed Zero Trust Network Access Ztna Introduction Ppt Slide PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.
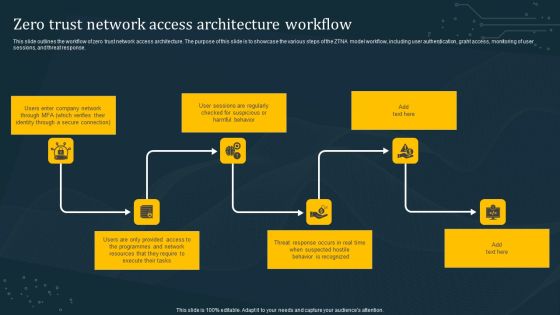
Zero Trust Network Access Architecture Workflow Microsoft PDF
This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response. Slidegeeks has constructed Zero Trust Network Access Architecture Workflow Microsoft PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Determine And Access Control Ppt PowerPoint Presentation Complete With Slides
Improve your presentation delivery using this Determine And Access Control Ppt PowerPoint Presentation Complete With Slides. Support your business vision and objectives using this well-structured PPT deck. This template offers a great starting point for delivering beautifully designed presentations on the topic of your choice. Comprising tweleve this professionally designed template is all you need to host discussion and meetings with collaborators. Each slide is self-explanatory and equipped with high-quality graphics that can be adjusted to your needs. Therefore, you will face no difficulty in portraying your desired content using this PPT slideshow. This PowerPoint slideshow contains every important element that you need for a great pitch. It is not only editable but also available for immediate download and utilization. The color, font size, background, shapes everything can be modified to create your unique presentation layout. Therefore, download it now.

Database Access Management Checklist For Businesses Formats PDF
This slide outlines the checklist for data access management in an organization. The purpose of this slide is to enlist all the crucial tasks and steps. The key points include creating an inventory, identifying data ownership and location of data, creating security groups, conducting regular data audits, and creating a certification program. Showcasing this set of slides titled Database Access Management Checklist For Businesses Formats PDF. The topics addressed in these templates are Description, Status, Comments. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Aspects Of Information System Access Control Security Auditing Diagrams PDF
The following slide highlights the aspects of information system access control security audit illustrating key headings which incudes data access control, authentication privacy, user identity, user management, password management, network access control, and login Presenting Aspects Of Information System Access Control Security Auditing Diagrams PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including User Management, Data Access Control, Network Access Control. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Critical Principles Of Zero Trust Network Access Model Graphics PDF
This slide illustrates the key principles of zero trust network access model, including their impact. The purpose of this slide is to highlight the primary principles of the ZTNA model, including least privilege access, micro-segmentation, MFA, device validation, and monitoring everything. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Critical Principles Of Zero Trust Network Access Model Graphics PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Critical Principles Of Zero Trust Network Access Model Graphics PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers

Main Pillars Of Zero Network Trust Access Sample PDF
This slide outlines the critical pillars of the zero network trust access model. The purpose of this slide is to showcase the primary pillars of ZTNA, including users, devices, networks, infrastructure, applications, data, visibility and analytics, and orchestration and automation. Presenting this PowerPoint presentation, titled Main Pillars Of Zero Network Trust Access Sample PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Main Pillars Of Zero Network Trust Access Sample PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Main Pillars Of Zero Network Trust Access Sample PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
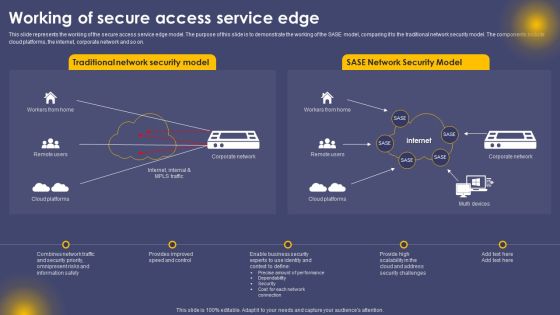
Working Of Secure Access Service Edge Ppt Summary Ideas PDF
This slide represents the working of the secure access service edge model. The purpose of this slide is to demonstrate the working of the SASE model, comparing it to the traditional network security model. The components include cloud platforms, the internet, corporate network and so on. The Working Of Secure Access Service Edge Ppt Summary Ideas PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Zero Trust Network Access Implementation Challenges Rules PDF
This slide outlines the main challenges of ZTNA implementation. The purpose of this slide is to highlight the primary challenges that organizations face while deploying ZTNA. The challenges include continual management and maintenance, low productivity, security risks, and so on. Presenting this PowerPoint presentation, titled Zero Trust Network Access Implementation Challenges Rules PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Zero Trust Network Access Implementation Challenges Rules PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Zero Trust Network Access Implementation Challenges Rules PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Training Program For Zero Trust Network Access Model Microsoft PDF
This slide outlines the training program for implementing the zero-trust network access model in the organization. The purpose of this slide is to highlight the training agenda, objectives, system requirements, mode of training and cost of the training. This Training Program For Zero Trust Network Access Model Microsoft PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Training Program For Zero Trust Network Access Model Microsoft PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Working Functions Of Zero Trust Network Access Architecture Introduction PDF
This slide gives an overview of the working features of zero trust network access architecture. The purpose of this slide is to highlight the various functions that ZTNA architecture performs, including identification, protection, detection and response to threats. Explore a selection of the finest Working Functions Of Zero Trust Network Access Architecture Introduction PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Working Functions Of Zero Trust Network Access Architecture Introduction PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Cyber Terrorism Assault Employee Access Control Protocols Diagrams PDF
This slide highlights how it is critical to limit employee rights and access in order to keep data safe and prevent it from being deleted or manipulated.This is a cyber terrorism assault employee access control protocols diagrams pdf template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Distributed Denial Of Service DDOS As Cyber Terrorism Tool You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Key Pillars Of Identify And Access Management Technique Topics PDF
This slide shows main features of an effective IAM strategy. The purpose of this strategy is to highlight major components of IAM strategy. It include features such as provisioning identities, access security certification and security management , etc. Presenting Key Pillars Of Identify And Access Management Technique Topics PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Provisioning Identities, Security Certification, Security Management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
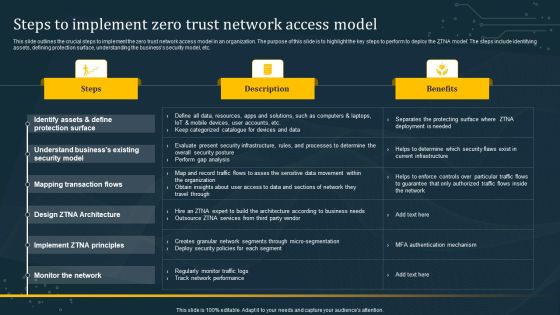
Steps To Implement Zero Trust Network Access Model Graphics PDF
This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Steps To Implement Zero Trust Network Access Model Graphics PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Zero Trust Network Access Vs Zero Trust Architecture Inspiration PDF
This slide represents the comparison between zero-trust network access and zero-trust architecture. The purpose of this slide is to highlight the key differences between ZTNA and ZTA based on definition, focus, objective, technologies, and implementation. Want to ace your presentation in front of a live audience Our Zero Trust Network Access Vs Zero Trust Architecture Inspiration PDF can help you do that by engaging all the users towards you.. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

Comparison Between ZTNA And Secure Access Service Edge Professional PDF
This slide compares the two security models, such as zero trust network architecture and secure access service edge. The purpose of this slide is to highlight the difference between ZTNA and SASE based on definition, key features, deployment, use cases, benefits and challenges. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Comparison Between ZTNA And Secure Access Service Edge Professional PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
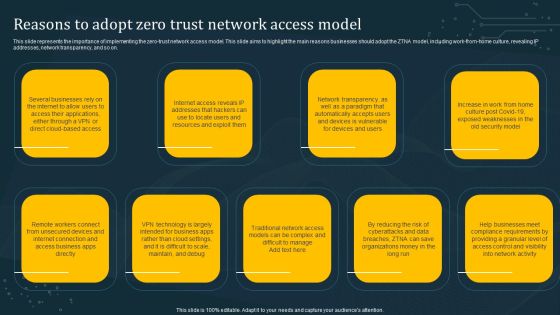
Reasons To Adopt Zero Trust Network Access Model Demonstration PDF
This slide represents the importance of implementing the zero-trust network access model. This slide aims to highlight the main reasons businesses should adopt the ZTNA model, including work-from-home culture, revealing IP addresses, network transparency, and so on. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Reasons To Adopt Zero Trust Network Access Model Demonstration PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
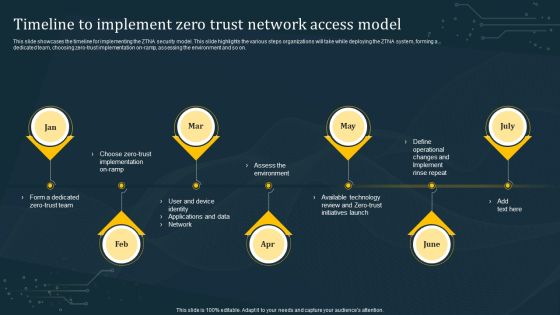
Timeline To Implement Zero Trust Network Access Model Rules PDF
This slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Timeline To Implement Zero Trust Network Access Model Rules PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Timeline To Implement Zero Trust Network Access Model Rules PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers

Cloud-Based Identify And Access Management Technique Best Practices Slides PDF
This slide shows ideal practices for IAM strategy. The purpose of this strategy is to highlight all effective practices along with concerned activities. It include practices such as defining IAM vision, building strong foundation , etc. Presenting Cloud-Based Identify And Access Management Technique Best Practices Slides PDF to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including Vision Clearly, Strong Foundation, Secure Generic Accounts. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Identify And Access Management Technique Implementation Tools Demonstration PDF
This slide show efficient tools for execution of IAM strategy. The purpose of this slide is to highlight all effective tools for executing IAM strategy in organization. It includes toll name, features, rating and prices , etc. Pitch your topic with ease and precision using this Identify And Access Management Technique Implementation Tools Demonstration PDF. This layout presents information on Tool Name, Features, Rating. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Identify And Access Management Technique Model Icons PDF
This slide shows controls management model for designing IAM strategy. The purpose of this slide is to highlight important phases with concerned stages for IAM strategy. It include phases such as prepare, develop and deliver , etc. Persuade your audience using this Identify And Access Management Technique Model Icons PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Prepare, Develop, Deliver. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
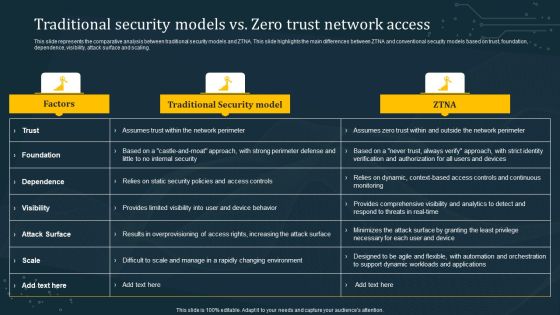
Traditional Security Models Vs Zero Trust Network Access Summary PDF
This slide represents the comparative analysis between traditional security models and ZTNA. This slide highlights the main differences between ZTNA and conventional security models based on trust, foundation, dependence, visibility, attack surface and scaling. This modern and well-arranged Traditional Security Models Vs Zero Trust Network Access Summary PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Checklist To Adopt A Cloud Access Security Broker Ppt PowerPoint Presentation File Portfolio PDF
This slide represents the main points to consider before adopting a cloud access security broker. The purpose of this slide is to showcase the key measures that organizations should keep in mind before choosing a CASB solution and the measures include conducting the trial, outlining CASB roles, and so on. Get a simple yet stunning designed Checklist To Adopt A Cloud Access Security Broker Ppt PowerPoint Presentation File Portfolio PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Checklist To Adopt A Cloud Access Security Broker Ppt PowerPoint Presentation File Portfolio PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Overview Of Cloud Access Security Broker Architecture Ppt PowerPoint Presentation Diagram Lists PDF
This slide gives an overview of cloud access security broker architecture. The purpose of this slide is to highlight architecture and its main components covering immediate enterprise core, secondary enterprise core, PaaS, SaaS, IaaS, connectivity gateway, security and compliance rules, etc. Slidegeeks has constructed Overview Of Cloud Access Security Broker Architecture Ppt PowerPoint Presentation Diagram Lists PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

Identify And Access Management Technique Ppt PowerPoint Presentation Complete Deck With Slides
Improve your presentation delivery using this Identify And Access Management Technique Ppt PowerPoint Presentation Complete Deck With Slides. Support your business vision and objectives using this well-structured PPT deck. This template offers a great starting point for delivering beautifully designed presentations on the topic of your choice. Comprising twenty this professionally designed template is all you need to host discussion and meetings with collaborators. Each slide is self-explanatory and equipped with high-quality graphics that can be adjusted to your needs. Therefore, you will face no difficulty in portraying your desired content using this PPT slideshow. This PowerPoint slideshow contains every important element that you need for a great pitch. It is not only editable but also available for immediate download and utilization. The color, font size, background, shapes everything can be modified to create your unique presentation layout. Therefore, download it now.

Secure Internet Access Security PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Secure Internet Access Security PowerPoint Templates PPT Backgrounds For Slides 0113.Download our Security PowerPoint Templates because Our PowerPoint Templates and Slides will let you Hit the target. Go the full distance with ease and elan. Present our Business PowerPoint Templates because You canTake a leap off the starting blocks with our PowerPoint Templates and Slides. They will put you ahead of the competition in quick time. Download our Technology PowerPoint Templates because You aspire to touch the sky with glory. Let our PowerPoint Templates and Slides provide the fuel for your ascent. Use our Internet PowerPoint Templates because It is Aesthetically crafted by artistic young minds. Our PowerPoint Templates and Slides are designed to display your dexterity. Download and present our Computer PowerPoint Templates because You can Connect the dots. Fan expectations as the whole picture emerges.Use these PowerPoint slides for presentations relating to The data is secure, security, business, technology, internet, computer. The prominent colors used in the PowerPoint template are Black, Gray, Yellow. You can be sure our Secure Internet Access Security PowerPoint Templates PPT Backgrounds For Slides 0113 are specially created by a professional team with vast experience. They diligently strive to come up with the right vehicle for your brilliant Ideas. Use our internet PowerPoint templates and PPT Slides are designed by a team of presentation professionals. You can be sure our Secure Internet Access Security PowerPoint Templates PPT Backgrounds For Slides 0113 have awesome images to get your point across. Customers tell us our business PowerPoint templates and PPT Slides are aesthetically designed to attract attention. We guarantee that they will grab all the eyeballs you need. People tell us our Secure Internet Access Security PowerPoint Templates PPT Backgrounds For Slides 0113 help you meet deadlines which are an element of today's workplace. Just browse and pick the slides that appeal to your intuitive senses. People tell us our business PowerPoint templates and PPT Slides help you meet deadlines which are an element of today's workplace. Just browse and pick the slides that appeal to your intuitive senses.
Folder Access Through Virtual Identity Finger Print Scanning Icon Graphics PDF
Presenting folder access through virtual identity finger print scanning icon graphics pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including folder access through virtual identity finger print scanning icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Smart Phone Finger Print Scanning To Access Virtual Identity Infographics PDF
Presenting smart phone finger print scanning to access virtual identity infographics pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including smart phone finger print scanning to access virtual identity. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Virtual Identify Biometric Access Control With Finger Print Scanner Themes PDF
Presenting virtual identify biometric access control with finger print scanner themes pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including virtual identify biometric access control with finger print scanner. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Information Security Monitor Access To Sensitive And Regulated Data Structure PDF
This slide explains we help you with data privacy by monitoring access of sensitive and regulated data, in which automation engine assists you in achieving the least privilege and compliance faster. The Information Security Monitor Access To Sensitive And Regulated Data Structure PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Managing Construction Work Construction Site Access And Layout Ppt Ideas Information PDF
The following slide displays a map of the entire construction site shows various areas such as entry point, the office space, excavation ground etc to ensure the smooth and safe functioning of the project. Deliver an awe-inspiring pitch with this creative managing construction work construction site access and layout ppt ideas information pdf bundle. Topics like construction site access and layout can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
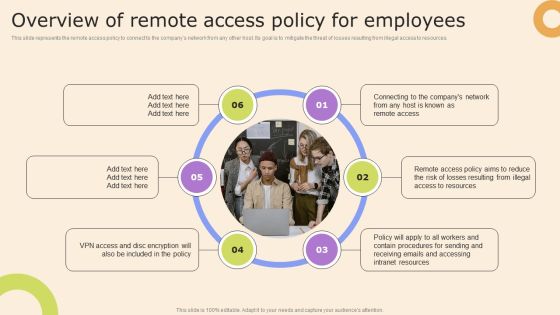
Information Technology Policy And Processes Overview Of Remote Access Policy For Employees Structure PDF
This slide represents the remote access policy to connect to the companys network from any other host. Its goal is to mitigate the threat of losses resulting from illegal access to resources. The Information Technology Policy And Processes Overview Of Remote Access Policy For Employees Structure PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Cloud Access Security Broker And Encryption Ppt PowerPoint Presentation File Example PDF
This slide describes the improved encryption with CASB version 2.0. The purpose of this slide is to showcase the various encryption features of cloud access security broker version 2.0, including security that follows the data, content access that can be revoked at any time, and multi-platform compatibility. Presenting this PowerPoint presentation, titled Cloud Access Security Broker And Encryption Ppt PowerPoint Presentation File Example PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Cloud Access Security Broker And Encryption Ppt PowerPoint Presentation File Example PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Cloud Access Security Broker And Encryption Ppt PowerPoint Presentation File Example PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
Icons Slide For Empowering Organization With Zero Trust Network Access Designs PDF
The Icons Slide For Empowering Organization With Zero Trust Network Access Designs PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
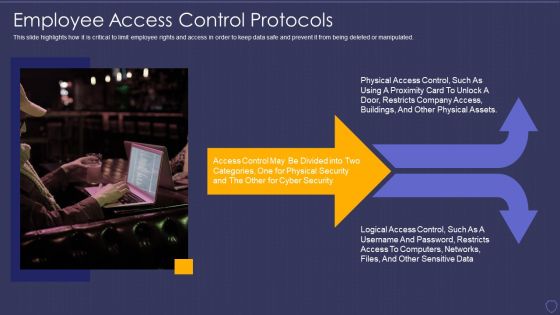
Global Cyber Terrorism Incidents On The Rise IT Employee Access Control Protocols Download PDF
This slide highlights how it is critical to limit employee rights and access in order to keep data safe and prevent it from being deleted or manipulated. Presenting global cyber terrorism incidents on the rise it employee access control protocols download pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like employee access control protocols. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Storage Access Methods Virtual Cloud Network IT Ppt Styles Slide Download PDF
This slide depicts the cloud storage access methods such as web service APIs Application Programming Interface, file based APIs, block-based APIs, and other APIs. Presenting this PowerPoint presentation, titled Cloud Storage Access Methods Virtual Cloud Network IT Ppt Styles Slide Download PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Cloud Storage Access Methods Virtual Cloud Network IT Ppt Styles Slide Download PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Cloud Storage Access Methods Virtual Cloud Network IT Ppt Styles Slide Download PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
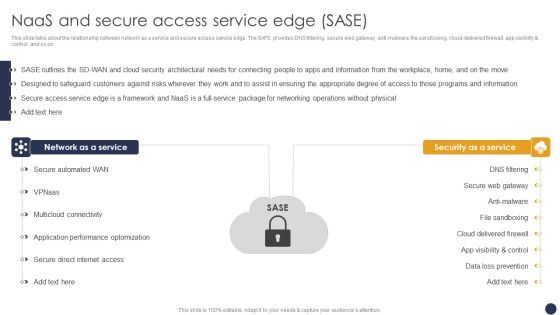
Integrating Naas Service Model Naas And Secure Access Service Edge Sase Ppt Model Picture PDF
This slide talks about the relationship between network as a service and secure access service edge. The SAFE provides DNS filtering, secure web gateway, anti-malware, file sandboxing, cloud-delivered firewall, app visibility and control, and so on. The Integrating Naas Service Model Naas And Secure Access Service Edge Sase Ppt Model Picture PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

8-Pointer Audit Checklist For Identify And Access Management Technique Background PDF
This slide shows mandatory checklist for IAM strategy and activities. The purpose of this slide is to mention all necessary activities for effectively implementing IAM strategy. It include auditing activities such as frame IAM policy and initiating documentation, etc Presenting 8-Pointer Audit Checklist For Identify And Access Management Technique Background PDF to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including Procedure Activities, Access Provided, Necessary Privileges. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

How To Effectively Manage A Construction Project Construction Site Access And Layout Microsoft PDF
The following slide displays a map of the entire construction site shows various areas such as entry point, the office space, excavation ground etc to ensure the smooth and safe functioning of the project.Deliver and pitch your topic in the best possible manner with this how to effectively manage a construction project construction site access and layout microsoft pdf. Use them to share invaluable insights on house foundation, steel depot, office space and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Open Radio Access Network IT Comparison Between Three Pillars Of Open RAN Designs PDF
This slide represents the comparison between three main pillars of an open RAN, including centralized RAN, virtualization RAN, and O RAN disaggregation. The comparison is based on baseband hardware and software, radio hardware, fronthaul interface, and interoperability. Presenting this PowerPoint presentation, titled Open Radio Access Network IT Comparison Between Three Pillars Of Open RAN Designs PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Open Radio Access Network IT Comparison Between Three Pillars Of Open RAN Designs PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Open Radio Access Network IT Comparison Between Three Pillars Of Open RAN Designs PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Benefits Of Cloud Access Security Broker 2 0 Ppt PowerPoint Presentation File Professional PDF
This slide represents the advantages of cloud access security broker version 2.0. The purpose of this slide is to highlight the main benefits of CASB 2.0, including comprehensive coverage, cost-effectiveness, enhanced security efficacy, improved visibility, app database, and so on. Create an editable Benefits Of Cloud Access Security Broker 2 0 Ppt PowerPoint Presentation File Professional PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Benefits Of Cloud Access Security Broker 2 0 Ppt PowerPoint Presentation File Professional PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Cloud Access Security Broker Pillar Threat Protection Ppt PowerPoint Presentation File Pictures PDF
This slide describes the threat protection pillar of cloud access security broker. The purpose of this slide is to highlight how CASB can help organizations to detect threats in advance through machine learning algorithms. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Cloud Access Security Broker Pillar Threat Protection Ppt PowerPoint Presentation File Pictures PDF can be your best option for delivering a presentation. Represent everything in detail using Cloud Access Security Broker Pillar Threat Protection Ppt PowerPoint Presentation File Pictures PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Leading Cloud Access Security Broker Platforms Ppt PowerPoint Presentation File Styles PDF
This slide outlines the Leading cloud access security broker platforms. The purpose of this slide is to highlight the leading CASB platforms, including G-suite, office 365, and Amazon Web Services, and it also represents the benefits and features of these cloud platforms. Are you searching for a Leading Cloud Access Security Broker Platforms Ppt PowerPoint Presentation File Styles PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Leading Cloud Access Security Broker Platforms Ppt PowerPoint Presentation File Styles PDF from Slidegeeks today.

Training Program For Cloud Access Security Broker Ppt PowerPoint Presentation File Show PDF
This slide describes the training program for employees to implement cloud access security broke in an organization. The purpose of this slide is to highlight the training schedule for CASB deployment and the main components include agenda, system requirements, mode and cost of the training. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Training Program For Cloud Access Security Broker Ppt PowerPoint Presentation File Show PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Training Program For Cloud Access Security Broker Ppt PowerPoint Presentation File Show PDF today and make your presentation stand out from the rest.

Benefits Of Cloud Access Security Broker Ppt PowerPoint Presentation File Model PDF
This slide outlines the different advantages of cloud access security broker technology. This slide highlights the pros of CASB technology, including risk visibility, cyber threat prevention, granular cloud usage control, shadow IT assessment and management, DLP, managing privileged accounts and admin and controlled data sharing. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Benefits Of Cloud Access Security Broker Ppt PowerPoint Presentation File Model PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Benefits Of Cloud Access Security Broker Ppt PowerPoint Presentation File Model PDF.
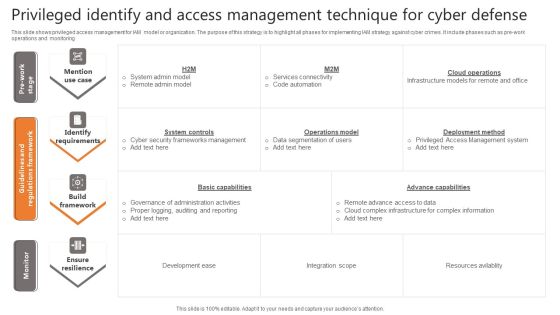
Privileged Identify And Access Management Technique For Cyber Defense Infographics PDF
This slide shows privileged access management for IAM model or organization. The purpose of this strategy is to highlight all phases for implementing IAM strategy against cyber crimes. It include phases such as pre work operations and monitoring Pitch your topic with ease and precision using this Privileged Identify And Access Management Technique For Cyber Defense Infographics PDF. This layout presents information on Identify Requirements, Build Framework, Ensure Resilience. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Open Radio Access Network IT Whos Working On Open RAN Graphics PDF
This slide outlines the organizations or groups working on open RAN, including the O-RAN Alliance Group, Nokia, and Samsung. O RAN alliance group has launched RAN intelligent controller, distributed unit, and RRU specifications. The Open Radio Access Network IT Whos Working On Open RAN Graphics PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Components Of Brand Portfolio Strategy For Better Access To New Markets And Consumers Slides PDF
This slide covers the fundamental principles of creating an effective brand communication strategy. It includes guidelines such as building and leveraging strong corporate bonds, defining strategic objectives for brands, employing simple and clear brand architecture, etc. The Components Of Brand Portfolio Strategy For Better Access To New Markets And Consumers Slides PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Uplift Capital Raising Pitch Deck Remote Access To Live Coaching And Training Ideas PDF
The following slide highlights the platform which allows athletes to have access coaching and training at remote locations. Slidegeeks is here to make your presentations a breeze with Uplift Capital Raising Pitch Deck Remote Access To Live Coaching And Training Ideas PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Cloud Access Security Broker Pillar Data Security Ppt PowerPoint Presentation File Model PDF
This slide talks about the data security pillar of the cloud access security broker pillar. This slide highlights how CASB data security can help organizations improve their IT requirements and business operations and detect security breaches before they happen. Slidegeeks is here to make your presentations a breeze with Cloud Access Security Broker Pillar Data Security Ppt PowerPoint Presentation File Model PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Extending On-Premises Cloud Identify And Access Management Technique Framework Formats PDF
This slide shows model for extending on-premises cloud IAM strategy. The purpose of this slide is to highlight all crucial steps for increasing IAM strategy. It includes steps such as scoping services, identify strategy , etc. Persuade your audience using this Cloud-Based Identify And Access Management Technique Best Practices Slides PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Scoping Services, Identify Strategy, Assessment Of Health. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

 Home
Home